Abstract
The ability of states to exploit private resources at an international level is an increasingly salient political issue. In explaining the mechanisms of this shift, the framework of Weaponized Interdependence has quickly risen to prominence, arguing that those states that are centrally placed in global networks can exploit their centrality given the appropriate domestic institutions. Building on this framework, I suggest that the relationship between states and the private corporations holding the resources states seek to exploit is more dynamic and contested than assumed. Drawing on developments in the industry for constructing and operating submarine cables, I find that a paradigm shift in the market has significantly limited the authority of states vis-à-vis key market players. The contribution of this finding is to expand Weaponized Interdependence as a framework, paying closer attention to the relationship between private companies and states. This expansion allows for the utilization of Weaponized Interdependence as a framework for a broader set of cases, explaining not only when a network is prone to weaponization but also the limitations states face when they seek to do so.
Introduction
On December 15, 2020 the TAT-14 fiberoptic cable was decommissioned after 19 years of service1. The cable – connecting the United States directly to Denmark and the United Kingdom, with branches to Germany, the Netherlands, and France – was constructed by a consortium of 48 different telecommunication providers, many of them fully or partly state-owned, pooling their resources to complete an expensive long-term investment (Starosielski, Citation2015, pp. 42–54; TAT-14, Citation2001). Once promoted as a state-of-the-art project, by 2020 the cable was regarded as inefficient with inadequate capacity to serve as one of the key highways of global connectivity (Telegeography, Citation2020b). In the wake of fundamental shifts in the market for global connectivity, both the technology and the funding model had become obsolete.
Only a few weeks before TAT-14 transmitted its last beam of light, another cable, built along a similar route between Denmark and the US, transmitted its first (Bulk Infrastructure, Citation2021). The Havfrue/AEC-2 cable was one of many new cables funded in part or wholly by global companies such as Facebook, Google, and Amazon - also known as ‘hyperscalers’. After years of overcapacity, investment in submarine cables has surged as existing systems are no longer able to serve the growing needs of global connectivity. During this recent boom, cloud providers and other digital companies have become the new masters of the industry: driving the investment, setting the terms, and shaping the structure of the network (Telegeography, Citation2017).
Paradigm shifts in the submarine cable market matter, not least because these networks have never been apolitical infrastructures only serving commercial interests. On both sides of the Atlantic, submarine cables have been revealed to be vital strategic resources underpinning global surveillance and espionage systems (Farrell & Newman, Citation2019). As global interconnected networks of commerce, communications, and finance have become more overt and prominent resources of state power (Cartwright, Citation2020; Gertz & Evers, Citation2020; Nye, Citation2020), a structural shift in associated underlying markets such as the one for submarine cables cannot be ignored. Examining this shift can shed light on an increasingly important question: under what conditions can state authorities leverage private resources at the international level?
Addressing such intersections between economics and security, the framework of Weaponized Interdependence (WI) has risen in prominence as a research agenda (Farrell & Newman, Citation2019). The framework depicts how economic networks become sources of dependency, power, and influence in the international system, offering a parsimonious theory with substantial explanatory power that has rapidly been embraced as a way forward for International Political Economy (IPE) and International Relations (Nye, Citation2020; Oatley, Citation2021). WI theorizes that as economic forces centralize global networks they create hubs of outsized importance that are critical to the networks’ functioning. The resulting asymmetric structure in turn becomes a potential instrument of power for states that hold central positions in the networks (Farrell & Newman, Citation2019).
However, the framework rests on assumptions of alignment between the state and private companies that need stronger grounding in empirical cases to be generalizable more widely. The ability of states to mobilize their domestic companies is eroding in significant areas (Seabrooke & Wigan, Citation2017; Weiss & Thurbon, Citation2018), and accounting for this development is paramount for WI to accurately capture the fluidity of private networks as a source of power. With global corporations strengthening their positions vis-à-vis states – transforming authority in the international political economy (Petry et al., Citation2021) – the ability of states to reach into and mobilize the resources of said companies is diminished, challenging the proposition that states are the primary agents in the international system. A closer examination of the companies that construct and own these networks can reveal the different and dynamic ways in which network structures change, in turn altering the relationship and shifting the authority between state and market. This calls for going beyond observing that these networks are centralized and instead examining how and by whom they were centralized.
To capture the dynamics between states and companies this article expands the framework of WI, showing how for submarine cables four key mechanisms have changed the relationship. As the economic drivers and market power of the key companies have changed, the ability of states to enact their authority over private companies has been eroded. This highlights the crucial links between structural power in the global economy and authority domestically (Mann, Citation1984; Weiss & Thurbon, Citation2018). Secondly, changes in the market have not only altered the distribution of power between states and companies but also severed informal ties, resulting in diverging values and interests. Thirdly, writing at the intersection of IPE and Science and Technology Studies (STS) has highlighted the role of infrastructure as independent factors to be reckoned with (Bernards & Campbell-Verduyn, Citation2019; Campbell-Verduyn et al., Citation2017, Citation2019). For submarine cables, as physical components of the global internet, the changing materiality and practices of the network has also moved control away from states and towards private corporations by limiting what is politically possible (Tusikov in Drezner et al., Citation2021). Such a change is not only reflected in shifts in who has authority, but also by changing how authority works and thus its legitimacy. By highlighting how different forms of power work through and are supported by economic networks, this allows WI to enter into dialogue with literature on the role of sovereign territories in rooting power (Barry, Citation2006; Lambach, Citation2019; Munn, Citation2020; Sassen, Citation2018).
By comparing the two distinct construction booms for transatlantic submarine internet cables, I will illustrate the utility of expanding WI with a greater focus on the agency of private companies. While the two booms resulted in networks that were superficially similar in terms of centralization, the underlying dependencies, practices, and actors have all undergone a dramatic shift. Seemingly ripe for state exploitation as digital infrastructures become more critical, the second incarnation of the network has instead empowered private corporations and given them greater ability to resist state attempts at weaponization. As the network is built anew, this realignment of the state–private dynamic is being hardwired into the network itself, restraining the agency of states by making weaponization contingent on corporate support.
Private infrastructure in WI
With the realization that complex mutual dependencies provide strategic benefits for some states over others, scholars have recently started re-examining the effects of interdependence on international relations (Drezner et al., Citation2021; Farrell & Newman, Citation2019; Nye & Keohane, Citation1971). The risk that such dependencies could be exploited has placed questions of supply chain security, next-generation mobile networks, and digital intrusions high on the political agenda (Cartwright, Citation2020; Drezner, Citation2020; Gertz & Evers, Citation2020; Lairson, Citation2020). Arguably, no depiction of contemporary geopolitics can avoid the realization that competition between states is tightly integrated with global economic networks and markets. This competition is both over who gets to dominate those markets and networks (Gertz & Evers, Citation2020), and the exploitation of these networks for strategic aims.
Henry Farrell and Abraham Newman (Farrell & Newman, Citation2019) first established WI as the primary framework utilized to make sense of this development. Farrell and Newman argue that global economic networks, under certain conditions, create avenues for exploitation by states. There are two main strategic mechanisms through which states can exploit such networks: the panopticon effect – wherein states are given access to more relevant and timely information about developments globally; and the chokepoint effect – wherein states (threaten to) cut other states off from the economic networks they are dependent on (Farrell & Newman, Citation2019).
WI takes as the starting point the structures of economic networks and the impact they have on politics. First and foremost, they note the tendency of these networks to ‘generate ever more asymmetric topologies in which exchange becomes centralized’ (Farrell & Newman, Citation2019) as a consequence of strong economic forces such as preferential attachment (Barabasi & Albert, Citation1999), network effects (Uzzi, Citation1996), or learning by doing (Gulati, Citation1999). As these key economic networks become centralized and asymmetrical, influence over these networks coalesces in ‘hubs’ that are essential for the networks to function. These hubs can in turn be exploited for geostrategic objectives (Farrell & Newman, Citation2019).
Such exploitation hinges on a second enabling variable: the domestic institutional environment. Even when a state is well placed to exploit global networks, doing so depends on ‘variation in domestic institutions in terms of capacity and key norms’ that ‘may limit their ability to use these coercive tools’ (Farrell & Newman, Citation2019). The understanding of domestic institutions flows primarily from the legal and normative frameworks within a given state, both of which are hypothesized to be fairly stable as ‘domestic actors may fear that the new capacities will be turned against them as well as foreign adversaries’ (Farrell & Newman, Citation2019). While the domestic institutional environment might be able to slowly change, the ‘stickiness’ of institutions, at least in the medium term, ensures that they principally act as a relatively stable variable enabling or constraining weaponization.
As a framework for understanding the increased intersection between economics and security, WI has been rightfully praised for its ability to provide a simple and parsimonious depiction that also offers great explanatory power. First and foremost, the framework is able to describe the conditions under which economic interdependence becomes a source of power (Hameiri, Citation2020; Nye, Citation2020; Winecoff, Citation2020). This in turn allows for explanation of the renewed state attention towards economic networks as a site for geopolitical rivalries to play out (Cartwright, Citation2020; Gertz & Evers, Citation2020), a shift to structural explanation that has been highlighted as a possible way forward for IPE more broadly (Oatley, Citation2021). The ability of WI to explain a diverse set of contemporary political issues has seen it utilized as a key framework to understand and analyze everything from the diminishing influence of the European Union (Leonard et al., Citation2019) to common conceptualizations of world order (Colgan, Citation2019; Paris, Citation2020).
Structure and agency in WI
Undoubtedly, WI has furthered the research agenda regarding the interactions between economic networks and geopolitics. However, on the role markets play in structuring geopolitics it relies on simplistic assumptions that can be problematic. In its approach to state–market relations, WI currently verges on methodological nationalism by implicitly assuming that states can act autonomously and are the sole actors that matter (Wimmer & Glick Schiller, 2002). As a result, the agency of non-state actors is not really taken into account, something Farrell and Newman acknowledge (Farrell and Newman in Drezner et al., Citation2021, pp. 313–316).
This assumption is unproblematic so long as states hold the upper hand vis-à-vis global corporations and can largely impose their will. Yet it is by no means given that the relationships between states and corporations adhere to such strict hierarchies (Mikler, Citation2018; Wilks, Citation2013). The structure of state–private relationships has been identified as a key variable for understanding the limitations of economic statecraft (Drezner, Citation2015), and undoubtedly impacts the ability of states to mobilize private resources for their strategic goals. WI depicts a form of power that flows through the mobilization of non-state actors - private companies - making the limits of such mobilization essential to the framework. WI is a form of power that acts through the relationships between states and the non-state actors it can control, and therefore the framework needs to depart from statist assumptions to examine the interactions between states and their constituents nationally or supranationally (Braun, Citation2020).
The extent to which states can mobilize the organizations that own and maintain the centralized nodes in turn determines the scope and limits of weaponization. WI is a function both of a state’s structural position in the global network and its relationship vis-à-vis the companies of importance in that network. A state in a structurally strong position globally cannot exploit its structural position if it has to contend with a reluctant private sector from a disadvantaged position (Gholz & Hughes, Citation2021; Weiss & Thurbon, Citation2018). Contra conceptions of this relationship as given, with the state entrenched as a dominant and autonomous actor, global corporations can resist and potentially challenge the ability of states to be the primary agents in the international system (Mann, Citation1984; Schwartz, Citation2019; Seabrooke & Wigan, Citation2017).
This relationship is neither static nor necessarily permanent. Both the structure of the networks and public–private relationships are constantly (re)produced by the underlying market logics and actors (Farrell and Newman in Drezner et al., Citation2021, p. 317; Strange, Citation1989, pp. 25–40). Furthermore, not only are the ability of states to mobilize companies and the structure of the network dynamic, they are also linked. Depicting these two variables as distinct obscures the extent to which they are intertwined and impact one another. A network might be asymmetrical in a way that empowers the state vis-à-vis companies, or it might be asymmetrical in a way that is hard for the state to exploit. Moreover, a network structure and its asymmetries might be aligned with established notions of what a state is, or it might not be. Assuming that all network structures are equal, bar their degree of centralization, neglects many interesting questions, not least how evolving market conditions might result in networks that are superficially similar but pose radically different political dynamics.
If the underlying paradigm of a market changes, as it has in the transmission of data, then the relationship between companies owning the global networks and the states that seek to exploit them is correspondingly realigned. What is needed is a framework that allows for the analysis of how changes in market conditions might impact this relationship, and how that in turn can have significant implications for the ability of states to weaponize those networks. Addressing and mitigating these shortcomings has the dual benefit of both enhancing the descriptive and explanatory potential of the framework and making it dynamic and responsive to change.
Examining this relational evolution also necessitates a deeper engagement with network infrastructures, one that goes beyond superficial similarities. The structure of, and practices surrounding, global networks are important components of the public–private relationship, and ought to be treated as such. In the research agenda on weaponization the focus has largely been on the extent to which networks are asymmetrical, while assuming that all asymmetries are alike. The problem with such tacit assumptions is that they disregard how different forms of centralization and asymmetry might produce different outcomes. As the distribution of power shifts and interests diverge, the position of states as the primary actors that matter is undermined and challenged by another increasingly powerful and autonomous agent: the global corporation. Expanding the framework of WI to account for such shifts makes it generalizable across more cases, without sacrificing the parsimonious explanatory force of the original framework.
Power, alignment, legitimacy, and materiality
If both companies and states have the political autonomy to operate within WI, a key agenda for the framework going ahead is to parse how the two sets of actors relate to one another. For WI, there are four key mechanisms of importance that shape how this relationship plays out. These are the power asymmetries between the state and the companies it seeks to exploit; their alignment in values and interests; the material affordances of the network, its structure, and the practices surrounding it; and the legitimacy of the authority states attempt to exert. All these different mechanisms can in various ways impair or strengthen the ability of states to exploit private resources for their strategic goals.
The first key determinant is the extent to which states hold leverage over the companies whose resources they seek to exploit. Departing from the assumption that states can always have their way, this becomes ultimately a question of authority and power. In the state–market relationship, authority and power can reside with the latter as much as they do with the former. Private enterprises might in many instances hold more ‘political authority over society and economy’ than states (Strange, Citation1996, p. 4). This turns our attention to the sources of influence and authority private corporations hold, and the extent to which they can resist or even challenge state authority (Mikler, Citation2018).
This situation is particularly likely when a limited number of corporations take on an outsized role in the national economy (Atal, Citation2021), and the resource to be exploited is a global and interdependent network. As states’ power and influence stems from their ability to lure companies and economic resources within their borders, states have to walk a fine line: push too hard and companies might relocate or disinvest if the cost of complying is perceived to outweigh that of abandoning the market (Moore & Tambini, Citation2018, p. 5). The relationship is dynamic and dependent on the fluctuations of the market and the actors within it. Unpacking who dictates the terms of the relationship is essential to finding the limits of authority and thus weaponization (Weiss, Citation2000).
Secondly, states and companies are not always competing and clashing. Frequently their interests align and intersect, reflecting that companies are embedded in their domestic social settings (Mikler, Citation2011) and how a shared sense of meaning helps create shared cultures across organizations (M. Barnett & Finnemore, Citation2004). If the interests of a company and the interests of a state are aligned, who holds the authority is far less important as they by and large want the same thing. Sharing a worldview, culture, or ideals can build a foundation of willing collaboration. Such ties do not need to occur at the level of the organization, as shared employment histories, revolving-door dynamics, or similar backgrounds can facilitate exchange and cooperation at the level of the individual (Bühlmann et al., Citation2012; Seabrooke & Tsingou, Citation2021). When a state is attempting to weaponize economic networks the extent of informal ties and ideational overlap can be equally as influential as leverage in its success and limitations.
Thirdly, the economic networks themselves also influence politics. The materiality of a network allows some forms of politics and closes off others, so WI needs to take into account how technological change makes certain forms of politics possible (Bernards & Campbell-Verduyn, Citation2019; Campbell-Verduyn et al., Citation2019). Taking a cue from the growing social science interest in the interplay between the ideational and the material, scholars have taken ideas from STS and placed a renewed emphasis on material objects as solidifiers of ideas, power relations, and other intangible structures (Mukerji, Citation2015). This includes, not least, how both tangible and intangible infrastructures locate power in complex systems through centralizing authority in the hands of discrete entities (Genito, Citation2019). Paying closer attention to the persistent role different forms of technological infrastructures play in maintaining centuries-old patterns of exploitation and asymmetry, studies have revealed how infrastructures are hardwiring power relations into material objects that in turn support these power relations (Goede, Citation2020).
But infrastructures do more than simply locate power, they can transform power as they ‘shape the way core functions are undertaken’, taking on a semi-independent role in structuring politics (Bernards & Campbell-Verduyn, Citation2019). Different iterations of infrastructural systems might facilitate new exertions of power by altering both who is given a central position and how that centrality works, similar to how technological change brings to the fore new modes of governance (Campbell-Verduyn et al., Citation2017). Materiality and infrastructures, understood broadly as the combination of objects and practices that act in the background, are structuring relations through enabling some forms of actions and constraining others. They are therefore potent forces in international politics that are only starting to get the attention they merit. How infrastructures look and work is therefore a key contextual factor for understanding different distributions of power.
The final, and related, determinant is the extent to which the exercise of authority by states is perceived as legitimate. A state is associated with certain ways of acting and being, and acting in alignment with those characteristics might make their coercive attempts at weaponization more acceptable (Beetham, Citation1995, pp. 12–13; Hurd, Citation1999). Paying attention not only to how infrastructures centralize and create nodes of power, but also if the exploitation of the asymmetries is understood as legitimate, opens new avenues for understanding the role of economic networks. Implicitly, Farrell and Newman seem to adopt an understanding of centralization as territorially grounded, noting how hubs ‘are typically territorially concentrated in the advanced industrial economies’ (Farrell & Newman, Citation2019, p.53). Yet centralization might equally occur at the level of the corporation or technology. A network centralized along these differing modes of centrality might make power less legitimate, and therefore affect politics unequally.
Capturing such differences requires engaging with the infrastructures in question, examining how digital infrastructures and their materiality have distinct political effects. Different iterations of digital technologies enable different modes of exercising power. A key distinction is between power based upon the territorial state, defined by a physical boundary and sovereign control, and power exercised by establishing technological standards, enforcing terms of service, algorithmic governance, and utilizing intermediaries ‘usually large corporations that provide specialized services in cyberspace’ (Lambach, Citation2019, p. 5). This distinction highlights a duality of digital power and its tension with common understandings of what a state is and ought to do (Amoore, Citation2018; Barry, Citation2006; Munn, Citation2020; Sassen, Citation2018, p. 9).
Being sensitive to these different modes of power illuminate how modern states’ attempts to exercise power over digital spaces occurs through the Janus-faced power of the sovereign state: on the one hand, states are using their autonomy and territorial boundedness to exercise authority over corporations, physical infrastructures, and their citizens; on the other hand, such exercises of authority permeate through a global network to reach into other states. Both sides of the sovereign state exist at the same time: one is limited spatially, aligned with ideas of the legitimate territorially sovereign states, and (potentially) unbounded in its ability to exercise authority; while the other can operate globally but is both far more controversial and vulnerable to resistance from the intermediaries it attempts to exercise power through.
If states are not the sole actors with agency and influence in WI, conceptualizing the relationship between states and the companies they attempt to act through is essential. States need leverage to impose their authority on private companies, or alternatively their ideals and goals must broadly align with the companies whose networks they wish to weaponize. Furthermore, the network itself matters; the technologies and practices deployed and the possibilities they afford, as well as where authority is located and its legitimacy. Essentially, how companies structure and centralize the network is important both for the type of power that can be exerted, and the dynamics between the state and those companies when attempting to exercise said power.
This structuring effect is not static or permanent, it can be highly dynamic, not least so for digital technologies where the pace of innovation is rapid. Because markets evolve and change, economic networks are frequently remade and offer new possibilities. Examining such changes calls for greater awareness of the market conditions that structure global economic networks. Doing so is necessary for unpacking the relationship between the state and corporations in WI, which limits the extent of weaponization by determining how far corporations are willing to go to align themselves with the states they operate from and within. The merits of expanding the framework in this manner can be shown through an examination of the shifting paradigm in one of the most essential markets structuring global connectivity: the market for constructing and operating submarine fiberoptic cables.
The undersea network
Submarine internet cables have long been neglected as an area of study in the international political economy, even as other aspects of digitalization have received substantial attention (Bueger & Liebetrau, Citation2021). Submarine cables carry over 95% of transoceanic internet communications and remain critical to the functionality of digital services (Liu et al., Citation2020). While the construction and operation of submarine cables do not usually draw public attention, submarine cables determine the topology of the physical internet to a great extent (Goldsmith & Wu, Citation2006; Malecki, Citation2002; Starosielski, Citation2015, p. 5).
As submarine cables are largely invisible in politics, interest in their workings is almost exclusively shared within a small and tight-knit industry community (Davenport, Citation2012). The political implications of these cables, and their impact on the topology of the network, has therefore received scant scholarly attention (for notable exceptions see Flensburg & Lai, Citation2021; Parks & Starosielski, Citation2015; Starosielski, Citation2015), and few have attempted to link the market for cable construction to broader trends in international politics (Bueger & Liebetrau, Citation2021; Munn, Citation2020; Parks & Starosielski, Citation2015; Sherman, Citation2021; Winseck, Citation2017 are exemptions). Both in academia and in the broader media landscape, attention has mostly focused on the risk of cables being cut or tampered with, either by sharks (a persistent myth) or by Russian submarines (Ankel, Citation2020; Clark, Citation2016).
Beyond the concerns that cables can be cut and tampered with, however, submarine cables have broader political implications ‘and their effects on media industries, user experiences, and the politics of circulation occur unevenly around the world’ (Starosielski, Citation2015, p. 93). As economic networks increasingly become more central to international politics, submarine cables and their role in shaping global communications networks offer an intriguing lens to analyze the interplay between markets and politics. For the purposes of this article such an analysis will center on the market for transatlantic submarine cable construction, which has seen the most pronounced changes over the last 25 years (Telegeography, Citation2020a).
Method and approach
The research on which this article is based draws from multiple sources. A key source of information has been participation in several industry conferences and bodies during 2020–21, such as the Submarine Networks EMEA and World, as well as meetings at industry groups and other media events. Material gathered from these discussions was invaluable as conversations flowed more freely, sensitive topics were covered, and multiple stakeholders were involved. Extensive notes were taken at the presentations and during the conversations at these conferences which formed the basis for initial hypothesizing. Testing of initial assumptions and ideas was undertaken through 28 semi-structured interviews with industry insiders, independent experts, and public officials, ranging from network engineers to CEOs.2 Where possible, tentative findings were then further tested against historical material and presentations from key venues, such as the SubOptic, Pacific Telecommunications Council, Submarine Networks World, and Capacity conferences. Other secondary sources utilized were the SubTel Forum, the TeleGeography blog, industry publications, and mainstream news coverage dating back to 2001, accessed through the Wayback machine of the Internet Archive. Beyond these written sources, data material on the cable systems was gathered from the GitHub repository of TeleGeography. Data from these sources was again supplemented and checked against FCC filings on submarine cable licenses.3
Data on the actual shape and features of the submarine cable network was gathered from existing literature and open-source material. Statements relating to decisions, shifting paradigms, and concerns were primarily gathered from conference presentations and interviews. Where open-source material was identified this was referenced, but all such statements were verified by at least one interviewee as well. For statements hinging solely on interviews a principle of data saturation was adopted. While the exact number of interviewees needed to verify a statement varied, a principle of three unsolicited mentions of the same phenomena and/or five to six confirmations of a statement was adopted (Guest et al., Citation2006).
Two booms and a bust: building the global internet
The construction of transatlantic submarine cables has occurred primarily through two distinct phases: one occurring around the turn of the millennium, and the other starting in the early 2010s that is still underway. This delineation into two distinct periods is largely the result of chance and the fallout of the boom and bust of the dotcom bubble. The growth in digital technologies during the latter half of the 1990s followed the development of fiberoptic cables in the 1980s (Starosielski, Citation2015, pp. 45–47) and the concurrent privatization of telecoms (Rodine-Hardy, Citation2015). The combination of new market entrants, speculation, and a recently developed capacity for transmitting large quantities of data spurred investment based on unrealistic assumptions of growth. When the bubble burst at the turn of the millennium, companies were left with vast overcapacity, falling prices, and squeezed profit margins that ‘reset the market’ (Interview, 09.03.2020). Several key companies in the industry filed for bankruptcy, and both the appetite for new projects and the capital to finance them plummeted. Large-scale building projects were largely halted as demand for bandwidth lagged behind supply which, due to a combination of overinvestment and improved transmission technologies, continued to be abundant (Starosielski, Citation2015, pp. 52–54).
The result was a halt in the construction of cables across the Atlantic for more than a decade. After the Apollo cable was finalized in 2003, no new cable came into operation until 2015, and in the meantime the rationales for data transmission had started to change (Hardy, Citation2015). During the first construction boom, occurring in the late 1990s to early 2000s, construction was based on the business model of connecting regions to sell capacity and data transmission, or transit. Providers of transit, commonly referred to as carriers, carved out a business in the transmission of data across the globe (Starosielski, Citation2015, pp. 28–31). The nascent internet opened up opportunities for carriers that could base their business on transmitting data between countries and across continents (Huston, Citation2016). The architecture that soon emerged was one of semi-hierarchical networks segregated in tiers, with the upper tier dominated by a dozen or so large telecommunications companies (G. A. Barnett et al., Citation2017; Ruiz & Barnett, Citation2015). Connectivity as constructed during the first building boom was therefore to a large extent anchored in the existing privatized telecommunication companies. As late as 2009 they accounted for more than 75% of the global bandwidth market, eclipsing any other form of company (Mauldin, Citation2019).
The second construction boom, starting around 2010 and still ongoing, has increasingly been driven by the growing demand for data transmission capacity from large internet companies. With the consolidation of the digital sphere and the rise of cloud computing and Content Delivery Networks (CDNs), the relationship between users and the data they were accessing changed as data storage moved closed to the end user (Feldman, Citation2019). In this structure individual users do not depend on accessing data transmitted over long distances to the same extent. Instead the largest cloud companies and CDNs need to connect their regional locations to large corporate networks (Huston, Citation2016). As these companies have started taking over growing shares of data traffic they are also investing in the construction of cables and infrastructure; first as major buyers of capacity and now increasingly also as owners of cables they construct themselves (Telegeography, Citation2017).
This shift in the market paradigm is reverberating throughout the industry, and as a result impacting how the politics of cable networks plays out. During the first boom, cable projects shared the same underlying rationale of connecting metropolitan centers and locations that could offer the greatest connectivity to other networks. These market drivers saw network effects and preferential attachments exert a gravitational pull on the submarine cable network. Connecting to established sites with existing customer bases and other market players offered the safest return on investment: terrestrial networks able to transmit large amounts of traffic, internet exchanges for transferring data between networks, and secondary infrastructures like electricity and a trained workforce to ensure a smooth operation (Blum, Citation2013, pp. 110–113; Starosielski, Citation2015, pp. 2–11). While this resulted in frequent reuse of existing landing sites and multiple cables to the same location, far from ideal from a resiliency point of view, economic risk aversion and business rationales outweighed these considerations.
With giant-sized digital corporations (or hyperscalers) being the new drivers of investment, the market has reoriented towards their preferred routes. These major players are less interested in connecting metropolitan areas and have the means to pursue more costly alternative routes (Interview 02/06/20). Their primary concern is to establish resilient high-capacity connections between their global data centers, ensuring that data can flow freely within these private networks. As one participant argued ‘The development, design and geographic routing of systems today are heavily influenced to deliver optimal performance for the largest Cloud Service Providers (CSPs). The traditional drivers of connecting key metropolitans have therefore changed significantly’ (Interview 23/09/20).
More than simply introducing a new set of actors with different preferences, the changing paradigm has altered several cost-benefit calculations on various geographic, social, and historical variables and contingencies. Underwater geographies are not equal, and some types of seabed come with far fewer risks attached. Submarine fiberoptic cables are preferentially laid in certain terrains, like abyssal plains, while areas with high levels of biodiversity and fishing activity are avoided as much as possible (Carter et al., Citation2014). Compliance and regulatory approaches have also been important - especially licensing, which can be a cumbersome process depending on the government. As one industry insider argued ‘when we drink beers at the end of the day we often discuss the best and worst markets to operate in, it is very important’ (Interview 24/04/20). Navigating both existing and potential political frictions is a way of managing delays as ‘the more noise you make the more people asks for compensation’ (Interview 02/06/20).
All of these variables exerted a strong influence on the network in the first boom, while political inattention and a ‘hands-off approach with regards to submarine cables’ (Interview, 30/09/20) by most states allowed the network to centralize in a few tried and tested locations under the maxim of ‘You go between major population centers and try to minimize length and shallow areas that are riskier’ (Interview 24/05/2020).
With hyperscalers driving the market, another set of factors has influenced the locations that are considered attractive. Data centers are large complexes housing vast amounts of expensive equipment and data – downtime and disruptions can have significant ramifications (Rosemain & Satter, Citation2021). Political stability and the absence of earthquakes, floods, and other natural hazards are therefore significant factors. In addition, the electricity requirements for large data centers are enormous, mainly to cool equipment, making power capacity and prices important factors. Finally, land and local regulatory contexts are also of great importance, both because data centers need ample space and because a business-friendly host nation is valued (Christensen et al., Citation2018).
These pull factors have made new geographical regions more important in the global network. The Nordic countries and Ireland, with various combinations of cold weather, tax incentives, and political stability, are examples of states that have managed to attract significant investment in data centers and, in their wake, reinvestment in submarine cable infrastructure that shifts the structure of the global network to their advantage (PA Consulting, Citation2021).
Pursuing new locations is also the result of more political attention, as states are recognizing their dependence on digital technologies. The increased criticality of internet connectivity has resulted in heightened scrutiny from government bodies acknowledging that cable construction has ‘historically been a market with little government involvement, but now issues are getting more attention and being recognized’ (Interview 09/03/2020 A). Partly, governments are adapting counterstrategies to reduce their dependencies within global networks, such as the ‘Team Telecom’ review process in the US that has denied licenses to projects that connect directly to China (Crichton, Citation2020). Moreover, the growth in data localization regulation requires that some data be stored locally, shielding sensitive data from the possibility of interception en route (Irion, Citation2012; Sargsyan, Citation2016). Such political constraints and conditions require the development of new routes.
Network structures and centralization
As outlined at the outset, the key structural feature enabling economic networks to be weaponized by states has been their asymmetries. Those economic networks that adopt an asymmetric structure are ripe for exploitation, while those that remain diversified are not. Looking at the submarine cable network, however, allows us to parse the effects of different modes of centralization. In both construction booms the primary forces structuring the global network have been the market and business interests of private corporations, albeit with a stronger state involvement the second time around. During the first boom the major pull factors were the desire to interconnect and proximity to large metropolitan centers. Combined with historical contingencies, limitations on the routes available, and the additional costs associated with establishing a new landing site, the result was a network that grew to become ‘relatively centralized—far from the early vision of the Internet as a rhizomatic and distributed network’ (Starosielski, Citation2015, p. 2).
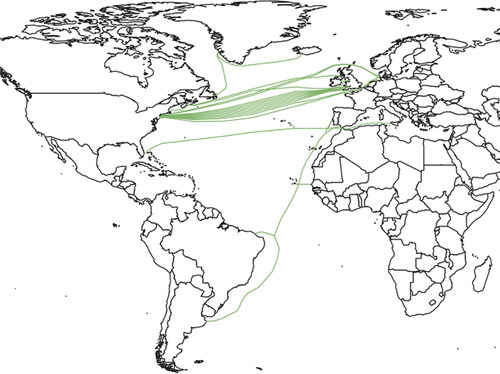
outlines the routes of the transatlantic cables built during the first construction boom that were still in operation in May 2020, according to TeleGeography. As the map shows, the network was pulled together in a few discrete locations. Sites like Porthcurno (the landing point in the western UK for transatlantic cables), Virginia (a key hub and exchange point for the many cables landing on the eastern US seaboard), and Miami (connecting Latin America to the submarine highway in the North Atlantic) became critical hubs in the global network (Telegeography, Citation2020a). Most cables illustrated on the map served this UK–US connection, either exclusively or as part of bigger circuits. A limited number of sites and cities became central to the functioning of transatlantic connectivity, thus creating bottlenecks in the transit of global data traffic (Goldsmith & Wu, Citation2006; Winseck, Citation2017). The two exceptions to the North Atlantic route in either connected to the US – the Columbus III cable connecting Florida with Portugal, Spain, and Italy – or had limited capacity. The sole cable in the South Atlantic – the Atlantis-II cable between the Iberian Peninsula and Brazil – was based on out-of-date technology and offered such limited capacity to buyers that it had next to no value in the network (Interview 10/11/20). The map therefore illustrates how whole continents like South America became reliant on exchanging data with Europe through the US, as the geography of the network created centralized exchanges.
In this centralized network, physical hubs become one of many sites for manipulation and control (Deibert, Citation2010; Mathew, Citation2016). The beneficiaries were mainly coastal states in Europe and the US, and even more narrowly the UK and the US, as the connection between the western part of the UK and the US became the de facto highway for global connectivity. Crucially, this centralization occurred at distinct spatial locations, creating hubs anchored in physical territories under the jurisdiction of sovereign states and operated by legacy telecommunication companies. Territorial centralization positioned economic networks within a familiar geography of territorial states demarcated by borders. On the business side, corporations based in the US were also dominant, but this centralization was less pronounced than the physical centralization as data transmission was still largely based on legacy telecommunication companies with worldwide roots (Ruiz & Barnett, Citation2015).
The second boom, however, has been driven by corporations with different business models and risk calculations. The primary driver in the current market is the desire to connect data centers, and the geographies that matter for data centers differ. This has been compounded by the companies driving investment having vastly deeper pockets.
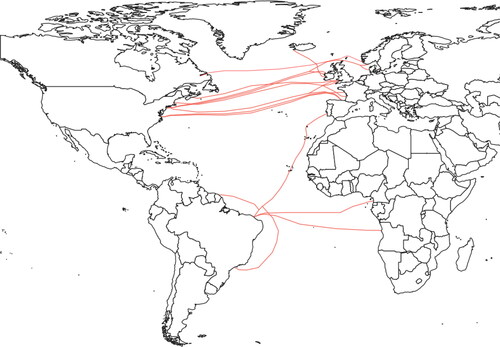
The map in depicts the transatlantic cables that were built between January 2010 and May 2020 as part of the revitalized boom in construction that is still ongoing. As in the map in , the physical layout of the network sees the US in a dominant position, albeit now far less central. Diversification in the South Atlantic is starting to offer real alternatives for South America for the first time with cables not only to Europe but also to Angola and Cameroon. Similarly, cable landings in Europe have clearly diversified beyond the UK, landing in France, Spain, and Portugal, in addition to cables connecting to the Nordics. This trend mirrors other physical infrastructures of the internet, where the central position of the US is weakening, although still dominant (Winseck, Citation2017). Many of the diversifying cables illustrated resulted from projects with politically motivated sources of funding – such as Irish investment in AquaComms (Ireland Strategic Investment Fund, Citation2016) or the European investment fund Marguerite II supporting a Brazil–EU cable (Marguerite, Citation2018) – which catalyzed the selection of different locations and routes. Yet while the territorial structure of the network seemingly weakens the position of the US and the UK, the industry is now controlled by a limited number of US corporations that drive almost all investment.
The most important shift is not this declining geographical centralization itself but the corresponding centralization occurring at the level of ownership and control. As the physical paths are becoming more resilient and diversified, ownership and market power are being consolidated. A simple glance at the owners and initiators of cable projects reveals the extent to which the likes of hyperscalers such as Google and Facebook call the shots in the industry. Not only have they increasingly become the largest users of transmission capacity, their roles have transformed from being customers to sole owners of cable projects (Telegeography, Citation2017).
Cable projects are expensive undertakings, with a large portion of capacity having to be sold upfront to secure loans for financing. In the current market, hyperscalers are the only actors interested in and capable of committing such large sums of money upfront, often allowing them to dictate terms for their project partners (Interview, 24/04/20, 18/05/20, 18/09/20). The real extent of control and influence, therefore, goes beyond ownership, as hyperscalers have been able to secure beneficial terms, decide the routes that get picked, and influence the technologies that get utilized. The extent of this control is also likely to increase in the years ahead as obsolete cable systems are decommissioned or eclipsed by newer systems with vastly larger capacity (Telegeography, Citation2020b). Rather than territorial centralization, corporate centralization is rapidly becoming the most important structural aspect of the network.
Networks, infrastructure, and power
The submarine cable industry continues to produce a network that is asymmetrical, with discrete entities having outsized control and influence. As the strategic value of data is increasing, the potential for weaponization appears plentiful. For a long time this held true: for the US and the UK, their central position within the global networks provided a ‘home-field advantage’ for their respective signals intelligence agencies (MacAskill & Rushe, Citation2013). Other states and their intelligence agencies benefitted as well: US surveillance programs relied upon the cooperation of intelligence agencies not only in the UK, but also other European allies such as Germany (Staff, Citation2014) and Denmark (Mortensen, Citation2020). Yet, with the market operating under a different paradigm the foundations of this home-field advantage might be eroding.
The changing paradigms of the submarine cable market have affected all the mechanisms discussed above. Firstly, the power asymmetries have to a significant extent shifted, even if the same states hold the most important positions in the network. In the first incarnation of the boom, the state–market nexus was clearly tilted towards the former. One reason for this was the business need to interconnect and reach metropolitan centers, as explained by one participant: ‘if the regulatory environment on shore does not support competitive access and there is no backhaul alternatives, the cable will make little difference [to opening up new opportunities locally]’ (Interview, 18/11/2020). The precarious position of companies dependent on such connections left them with little choice but to comply with state regulations and any strings attached.
The key pressure point in this regard is the need for companies to obtain landing licenses, a cumbersome process that can involve significant additional costs and often stall projects (Interview 02/06/20). Landing licenses can also involve mandated cooperation with state intelligence services, making such licenses a key instrument for state exploitation. One participant mentioned how a project ended with a ‘two-three-month period after the cable was finalized where you had to look away while the equipment was installed’ (Interview, 18/11/2020). As long as access to physical hubs determined whether a network was profitable, states had a strong position vis-a-vis the companies that owned and constructed the cables.
In the current paradigm, corporations have more discretion in picking the locations where they place their infrastructure and investments. While the mobility of data centers is limited by their geographical needs, a paradigm of connecting data centers offers more mobility than connecting population centers. Avoiding regions and states that try to exert firm control over the internet has long been a concern for the industry, but the new paradigm makes it far easier to avoid states that are perceived to overstep their boundaries (Interviews 24/05/20, 25/05/20). Important in this regard also is hyperscalers’ significant financial means compared to traditional market actors. Whereas submarine cable investment posed a significant financial risk for legacy telecommunications companies, the revenue of a company like Alphabet provides far greater liberty for developing new routes.
Rather than corporations following state instruction, the increased mobility of the infrastructure sees states increasingly compete to attract investment in infrastructure and data centers, tilting the power dynamic towards the market (Interviews 09/03/20B, 14/05/20, 24/04/20). While it is too early to assert that the biggest market players are now clearly in the ascendancy, the privileged position of states is at least challenged. This shift in the power dynamic is in turn further exacerbated as the value alignment between corporations and the states they operate in is shifting.
The legacy telecommunication companies that dominated the first boom were characterized by strong and persistent institutional and historical ties to their home states. A large proportion of the companies were recently privatized companies, maintaining relations with and having identities tied to their home states (Interview 24/11/20). The connection between AT&T, Bell Labs, and US strategic interests was a feature throughout the 20th century (Wu, Citation2011), a pattern repeated across the globe as ‘many of the companies remain aligned with, though not beholden to, national governments’ (Starosielski, Citation2015, p. 61). The domestic environment was not only characterized by states having a position of strength vis-à-vis the key companies, but by the active participation of those companies. Cooperation was underpinned by an alignment in ideas and values (Interviews 18/11/20, 24/11/20).
For states seeking to weaponize their centrality in the networks, close ties allow for greater exploitation than would otherwise be possible. As an example, any internet company must cooperate with surveillance programs that are covered by the US Foreign Intelligence Surveillance Act (FISA). Yet, leaked material has shown how the NSA and GCHQ through the PRISM program went beyond the FISA process and sought cooperation from telecommunications companies that owned and operated fiberoptic cables to gain more extensive access. This allowed the collection of data as it flowed between the data centers of the large internet companies, a much larger haul than would have been otherwise possible (Buchanan, Citation2020, pp. 56–57). The willingness of the established telecommunications providers to go further in their cooperation appears at least partly related to a history of close formal and informal ties that allowed a deeper and more extensive weaponization of the network (Wyden, Citation2019).
Veterans in the industry observed clear differences between the current situation and the close ties that used to exist between telecoms and the state (Interviews 24/11/20, 02/06/20). Today the institutional ties between the companies dominating the industry and their home states are less clear-cut than they used to be (Tibbles, Citation2017). This is more acute on the European side of the Atlantic, where telecommunication companies with strong ties or even state ownership stakes have been partly replaced by US hyperscalers. Yet even in the US the relationship has changed as the infrastructure moves into the hands of corporations with a more independent outlook. While these companies are not beyond the reach of the state to regulate, they have publicly staked their reputations on avoiding the type of cooperative legal interpretations that underpinned programs such as PRISM (Buchanan, Citation2020, p. 59; Perlroth, Citation2021, p. 8; Smith & Browne, Citation2019, pp. 12–15).
This shift in the relationship of power and lack of alignment is further exacerbated by the changing structure and materiality of the network, from a centralization characterized by physical locations to one characterized by global corporate networks. This shift in the form of centralization in turns impacts how legitimate state attempts at exerting authority are. A network that is territorially centralized paves the way for control through territorial jurisdiction based on the idea of the sovereign state. Physical spatiality of global communications has therefore been identified as a way for states to exercise ‘easy’ authority (Dunn Cavelty, Citation2015). While the surveillance of data traffic as it crosses borders might be unpopular, it is in many ways no different than other forms of control and authority occurring at the border of a state (Amoore & Hall, Citation2009).
Exploiting the global networks of corporations, however, is a more contested proposition. Weaponizing corporate centralization can necessitate the development of controversial extraterritorial legislation undermining the sovereignty of other states. As submarine cable networks become a part of the global networks of private corporations, attempts at weaponizing them take the form of regulation that, while rooted in territorial jurisdictions, is noteworthy for its extraterritorial reach and impact. The controversies over evolving security legislation in China and the US Cloud Act, two prominent examples, both revolved around the extraterritorial reach of domestic regulation (Brier, Citation2017; Fischer, Citation2018; Svantesson & Gerry, Citation2015).
This shifting relationship is also likely to have effects for prolonged periods of time. The change outlined above is occurring simultaneously with the submarine cable network being constructed anew, entrenching the relationship in the materiality and practices of the network itself. The increasing political attention to surveillance, cybersecurity, and digital sovereignty drives policy initiatives like data localization and ‘national clouds’ that attempt to shield sensitive data from possible interception. Digital companies seeking access to markets across the globe have to develop solutions to mitigate these concerns (Rosemain, Citation2021), yet such mitigations also entrench companies as arbiters of weaponization.
This position partly comes from the diversification of the network, which beyond making the network resilient also makes it harder for any single state to exert control based on physical hubs. More importantly, the growing use of end-to-end encryption has limited the utility of surveilling digital networks altogether, at least until decryption capabilities take a quantum leap ahead. Attempts by lawmakers to undermine encryption, the EARN IT Act in the US being one prominent example, are evidence of these tensions (Newton, Citation2020). As submarine cables increasingly serve private networks they also facilitate the development of new communication protocols and other technical solutions preferred by hyperscalers (Herr, Citation2020). Beyond technical countermeasures, the publication of transparency reports, initiated by Google, increases insights into the scope of government surveillance efforts (Smith & Browne, Citation2019, pp. 30–35). That is not to say that weaponization is now impossible, but it is forced to take place with greater transparency and with stricter judicial oversight, both of which limit the extent of WI. As such, it is indicative of a new reality where weaponization is limited not only by more confrontational relationships between corporations and their home states (Zegart & Childs, Citation2018), but where corporations hardwire their strong bargaining position into the network.
Today the broad patterns of network centralization in the submarine cable network are unchanged, yet beneath the superficial similarities important shifts have occurred in the relationship between the largest market players and their home states. Firstly, the power dynamic has shifted, giving market actors more scope to resist state attempts at exploitation. Secondly, the interests of companies and their home states are diverging, and informal ties are weakening. Thirdly, the changing materiality of the network is making taking control harder by shifting state authority from accepted forms of authority to more contested ones. All these changes have made weaponization more challenging, albeit not impossible, by limiting the ability of states to mobilize private corporations for their own interests. Finally, the fast pace of digital technological innovation and the cyclical nature of submarine cable construction gives companies ample opportunity to entrench their dominant position. Encryption, transparency reports, and route resiliency are all cementing global corporations as arbiters of state exploitation, a position that might be increasingly difficult to challenge.
Conclusion
Global communications networks are increasingly fraught and contested infrastructures. The framework of WI has offered a vantage point to analyze and make sense of the many controversies surrounding these networks. For submarine cables, the benefits of a network centralized in physical locations gave the UK and the US vast and unrivalled intelligence capabilities.
Largely because of changes in the underlying market and its drivers, the situation today looks different. Ownership and control over infrastructure have for many states moved from domestic companies to globalized corporations. Such a globalization of the infrastructure threatens to erode the leverage states hold over said corporations, undercut informal but essential ties between states and key market players, and make exercising authority more controversial and contested. Even for the US, the home state of the now dominant hyperscalers, industry insiders have noted how these are global enterprises with interests and ideals that are increasingly their own. Depicting the trend as a solidification of US structural power must consider the corresponding weakening of the position of authority of the US government domestically.
The ability of states to reach into, mobilize, and benefit from their centrality in the network has therefore weakened as corporations gain in relative strength. The strong position of the market players in turn affords them greater agency to pursue their own interests, that are often at odds with the interests of states. Simply by staking their reputation on limiting cooperation with states, these companies are displaying a form of agency that the framework of WI must consider. More substantially, the newly gained position of power held by market actors is in turn made permanent through embedding the power relationships into the network: by construction of infrastructure and through establishing practices of transparency and encryption that give corporations an entrenched position as middlemen and arbiters of state power.
As a case this underlines the merits of expanding the framework of WI in two key ways. Firstly, by parsing the mechanisms influencing the public–private relationship and recognizing the independent agency private corporations hold, WI becomes not only a question of structural power internationally but authority domestically. Secondly, by examining how changes in markets affect these mechanisms, scholars interested in the geopolitical effects of economic networks ought to pay attention to the dynamic and precarious nature of states exploiting privately owned resources. A changing paradigm in data transmission has triggered a reorientation of the submarine cable network, leading to a different form of centralization with different political effects and implications. Seemingly similar network structures afford different opportunities for exploitation and resistance, and privilege certain actors over others.
Applying these expansions has also given greater scope for understanding weaponization of networks as more than a binary situation. Agreements between private corporations and their home states ought not to be taken for granted; they are dynamic relationships determined by the distribution of power and convergence of interests, supported by the possibilities afforded by the materiality of the networks in question. WI is a negotiation between the states enjoying a privileged position within the network and the private corporations they attempt to act through. These negotiations occur not only behind locked doors and in closed meetings but also through public statements, technological decisions, and even the routes that are chosen to be part of the global network.
Paying attention to these trends does not rob WI of its explanatory power, nor does it undermine its parsimony. Rather, it asks us to reconsider the assumptions underpinning the panopticon and chokepoint effects, making the framework applicable to a broader range of cases. Of relevance are not only those instances where states succeed in exploiting their privileged position, but also the instances where they do not. With economic interdependence set to raise essential questions about national security and geopolitical rivalry in the years to come, this pushes the research agenda ahead and calls for in-depth depictions of the interplay between states and global markets in shaping contemporary exercises of power.
Supplemental Material
Download PDF (204.5 KB)Disclosure statement
No potential conflict of interest was reported by the authors.
Additional information
Notes on contributors
Lars Gjesvik
Lars Gjesvik is a Doctoral Research Fellow at the Norwegian Institute of International Affairs and the University of Oslo. He studies the ability of states to weaponize and secure digital technologies, and the role non-state actors play in enabling or constraining those efforts.
Notes
1 See the Federal Communications Commission: https://docs.fcc.gov/public/attachments/DA-20-369A1.pdf
2 An anonymized table of interviewees is included in the appendix
3 Licenses available at https://fcc.report/IBFS/Filing-List/SCL-LIC.
References
- Amoore, L. (2018). Cloud geographies. Progress in Human Geography, 42(1), 4–24. https://doi.org/10.1177/0309132516662147
- Amoore, L., & Hall, A. (2009). Taking people apart: Digitised dissection and the body at the border. Environment and Planning D: Society and Space, 27(3), 444–464. https://doi.org/10.1068/d1208
- Ankel, S. (2020). Russian agents went to Ireland to inspect undersea cables: report - Business Insider. Business Insider. https://www.businessinsider.com/russian-agents-went-to-ireland-to-inspect-undersea-cables-report-2020-2?utm_source=reddit.com&r=US&IR=T
- Atal, M. R. (2021). The Janus faces of Silicon Valley. Review of International Political Economy, 28(2), 336–350. https://doi.org/10.1080/09692290.2020.1830830
- Barabasi, A. L., & Albert, R. (1999). Emergence of scaling in random networks. Science (New York, NY), 286(5439), 509–512. https://doi.org/10.1126/science.286.5439.509
- Barnett, G. A., Ruiz, J. B., Xu, W. W., Park, J. Y., & Park, H. W. (2017). The world is not flat: Evaluating the inequality in global information gatekeeping through website co-mentions. Technological Forecasting and Social Change, 117, 38–45. https://doi.org/10.1016/j.techfore.2017.01.011
- Barnett, M., & Finnemore, M. (2004). Rules for the world: International organizations in global politics. Cornell University Press. http://doi.org/10.7591/j.ctt7z7mx
- Barry, A. (2006). Technological Zones. European Journal of Social Theory, 9(2), 239–253. https://doi.org/10.1177/1368431006063343
- Beetham, D. (1995). The legitimation of power (3rd print). Issues in political theory. Macmillan.
- Bernards, N., & Campbell-Verduyn, M. (2019). Understanding technological change in global finance through infrastructures. Review of International Political Economy, 26(5), 773–789. https://doi.org/10.1080/09692290.2019.1625420
- Blum, A. (2013). Tubes: A journey to the center of the Internet. (First Ecco paperback edition). Ecco an imprint of HarperCollins Publishers.
- Braun, B. (2020). Central banking and the infrastructural power of finance: the case of ECB support for repo and securitization markets. Socio-Economic Review, 18(2), 395–418. https://doi.org/10.1093/ser/mwy008
- Brier, T. F. Jr (2017). Defining the limits of governmental access to personal data stored in the cloud: An analysis and critique of Microsoft Ireland. Journal of Information Policy, 7, 327. https://doi.org/10.5325/jinfopoli.7.2017.0327
- Buchanan, B. (2020). The hacker and the state: Cyber attacks and the new normal of geopolitics. Harvard University Press.
- Bueger, C., & Liebetrau, T. (2021). Protecting hidden infrastructure: The security politics of the global submarine data cable network. Contemporary Security Policy, 42(3), 391–323. https://doi.org/10.1080/13523260.2021.1907129
- Bühlmann, F., David, T., & Mach, A. (2012). The Swiss business elite (1980–2000): how the changing composition of the elite explains the decline of the Swiss company network. Economy and Society, 41(2), 199–226. https://doi.org/10.1080/03085147.2011.602542
- Campbell-Verduyn, M., Goguen, M., & Porter, T. (2017). Big Data and algorithmic governance: the case of financial practices. New Political Economy, 22(2), 219–236. https://doi.org/10.1080/13563467.2016.1216533
- Campbell-Verduyn, M., Goguen, M., & Porter, T. (2019). Finding fault lines in long chains of financial information. Review of International Political Economy, 26(5), 911–937. https://doi.org/10.1080/09692290.2019.1616595
- Carter, L., Gavey, R., Talling, P., & Liu, J. (2014). Insights into submarine geohazards from breaks in subsea telecommunication cables. Oceanography, 27(2), 58–67. https://doi.org/10.5670/oceanog.2014.40
- Cartwright, M. (2020). Internationalising state power through the internet: Google, Huawei and geopolitical struggle. Internet Policy Review, 9(3). https://doi.org/10.14763/2020.3.1494
- Christensen, J. D., Therkelsen, J., Georgiev, I., & Sand, H. (2018). Data centre opportunities in the nordics: An analysis of the competitive advantages. Nordic Council of Ministers. https://web.archive.org/web/20210608092700/http://norden.diva-portal.org/smash/get/diva2:1263485/FULLTEXT02.pdf
- Clark, B. (2016). Undersea cables and the future of submarine competition. Advance online publication. Bulletin of the Atomic Scientists, 72(4), 234–237. https://doi.org/10.1080/00963402.2016.1195636
- Colgan, J. D. (2019). Three visions of international order. The Washington Quarterly, 42(2), 85–98. https://doi.org/10.1080/0163660X.2019.1621657
- Crichton, D. (2020). The US is formalizing Team Telecom rules to restrict foreign ownership of internet and telecom assets. TechCrunch. https://techcrunch.com/2020/04/06/the-u-s-is-formalizing-team-telecom-rules-to-restrict-foreign-ownership-of-internet-and-telecom-assets/
- Davenport, T. (2012). Submarine communications cables and law of the sea: Problems in law and practice. Ocean Development & International Law, 43(3), 201–242. https://doi.org/10.1080/00908320.2012.698922
- Deibert, R. (2010). Access controlled: The shaping of power, rights, and rule in cyberspace. Information revolution & global politics. MIT Press.
- Drezner, D. W. (2015). Targeted sanctions in a world of global finance. International Interactions, 41(4), 755–764. https://doi.org/10.1080/03050629.2015.1041297
- Drezner, D. W. (2020). The song remains the same: International relations after COVID-19. International Organization, 74(S1), E18–E35. https://doi.org/10.1017/S0020818320000351
- Drezner, D. W., Farrell, H., & Newman, A. (2021). The uses and abuses of weaponized interdependence. Brookings Institution Press.
- Dunn Cavelty, M. (2015). Die materiellen Ursachen des Cyberkriegs Cybersicherheitspolitik jenseits diskursiver Erklärungen. Journal of Self-Regulation and Regulation, 1(2015), 167–184. https://doi.org/10.11588/JOSAR.2015.0.23486
- Farrell, H., & Newman, A. L. (2019). Weaponized interdependence: How global economic networks shape state Coercion. International Security, 44(1), 42–79. https://doi.org/10.1162/isec_a_00351
- Feldman, S. (2019). The cloud market keeps moving upwards. https://www.statista.com/chart/19039/cloud-infrastructure-revenue/
- Fischer, C. (2018). The CLOUD Act: A dangerous expansion of police snooping on cross-border data. https://www.facebook.com/eff. https://www.eff.org/deeplinks/2018/02/cloud-act-dangerous-expansion-police-snooping-cross-border-data
- Flensburg, S., & Lai, S. S. (2021). Networks of power. Analysing the evolution of the Danish internet infrastructure. Internet Histories, 5(2), 79–22. https://doi.org/10.1080/24701475.2020.1759010
- Genito, L. (2019). Mandatory clearing: the infrastructural authority of central counterparty clearing houses in the OTC derivatives market. Review of International Political Economy, 26(5), 938–962. https://doi.org/10.1080/09692290.2019.1616596
- Gertz, G., & Evers, M. M. (2020). Geoeconomic competition: Will state capitalism win? The Washington Quarterly, 43(2), 117–136. https://doi.org/10.1080/0163660X.2020.1770962
- Gholz, E., & Hughes, L. (2021). Market structure and economic sanctions: the 2010 rare earth elements episode as a pathway case of market adjustment. Review of International Political Economy, 28(3), 611–624. https://doi.org/10.1080/09692290.2019.1693411
- Goede, M. de. (2020). Finance/security infrastructures. Review of International Political Economy, 28(2), 1–18. https://doi.org/10.1080/09692290.2020.1830832
- Goldsmith, J. L., & Wu, T. (2006). Who controls the Internet? Illusions of a borderless world. Oxford University Press. http://search.ebscohost.com/login.aspx?direct=true&scope=site&db=nlebk&db=nlabk&AN=169236
- Guest, G., Bunce, A., & Johnson, L. (2006). How many interviews are enough? Field Methods, 18(1), 59–82. https://doi.org/10.1177/1525822X05279903
- Gulati, R. (1999). Network location and learning: The influence of network resources and firm capabilities on alliance formation. Strategic Management Journal, 20(5), 397–420. http://www.jstor.org/stable/3094162 https://doi.org/10.1002/(SICI)1097-0266(199905)20:5<397::AID-SMJ35>3.0.CO;2-K
- Hameiri, S. (2020). Institutionalism beyond methodological nationalism? The new interdependence approach and the limits of historical institutionalism. Review of International Political Economy, 27(3), 637–657. https://doi.org/10.1080/09692290.2019.1675742
- Hardy, S. (2015). Hibernia Express transatlantic submarine cable network ready for service. Lightwave. https://www.lightwaveonline.com/network-design/high-speed-networks/article/16651312/hibernia-express-transatlantic-submarine-cable-network-ready-for-service
- Herr, T. (2020). Four myths about the cloud: The geopolitics of cloud computing. https://www.atlanticcouncil.org/in-depth-research-reports/report/four-myths-about-the-cloud-the-geopolitics-of-cloud-computing/#thereisnocloud
- Hurd, I. (1999). Legitimacy and authority in international politics. International Organization, 53(2), 379–408. https://doi.org/10.1162/002081899550913
- Huston, G. (2016). The death of transit? APNIC. https://blog.apnic.net/2016/10/28/the-death-of-transit/
- Infrastructure, B. (2021). Live Systems: Havfrue. https://web.archive.org/web/20201026163408/https://bulkinfrastructure.com/digital-infrastructure/fiber-networks/systems#havfrue
- Ireland Strategic Investment Fund. (2016). Ireland strategic investment fund announces €57 million of connectivity fund investments [Press release]. https://isif.ie/news/press-releases/ireland-strategic-investment-fund-announces-57-million-of-connectivity-fund-investments
- Irion, K. (2012). Government cloud computing and national data sovereignty. Policy & Internet, 4(3–4), 40–71. https://doi.org/10.1002/poi3.10
- Lairson, T. D. (2020). The international political economy of Huawei’s global and domestic environment. In W. Zhang, I. Alon, & C. Lattemann (Eds.), Huawei goes global: Volume I: Made in China for the world (pp. 13–40). Springer International Publishing. https://doi.org/10.1007/978-3-030-47564-2_2
- Lambach, D. (2019). The territorialization of cyberspace. International Studies Review, 22(3), 482–506. Article viz022, 19. https://doi.org/10.1093/isr/viz022
- Leonard, M., Pisani-Ferry, J., Ribakova, E., Shapiro, J., & Wolff, G. (2019). Securing Europe’s economic sovereignty. Survival, 61(5), 75–98. https://doi.org/10.1080/00396338.2019.1662148
- Liu, S., Bischof, Z. S., Madan, I., Chan, P., & Bustamante, F. E. (2020). Out of sight, not out of mind: A user-view on the criticality of the submarine cable network [Paper presentation]. Proceedings of the ACM Internet Measurement Conference.
- MacAskill, E., & Rushe, D. (2013). Snowden document reveals key role of companies in NSA data collection. The Guardian. https://www.theguardian.com/world/2013/nov/01/nsa-data-collection-tech-firms
- Malecki, E. J. (2002). The economic geography of the internet's infrastructure. Economic Geography, 78(4), 399–424. https://doi.org/10.1111/j.1944-8287.2002.tb00193.x
- Mann, M. (1984). The autonomous power of the state: its origins, mechanisms and results. European Journal of Sociology, 25(2), 185–213. http://www.jstor.org/stable/23999270 https://doi.org/10.1017/S0003975600004239
- Marguerite. (2018). Infrastructure investor Marguerite II joins the EllaLink submarine cable as financial sponsor [Press release]. https://www.marguerite.com/2018/05/infrastructure-investor-marguerite-ii-joins-the-ellalink-submarine-cable-as-financial-sponsor/
- Mathew, A. J. (2016). The myth of the decentralised internet. Internet Policy Review, 5(3). https://doi.org/10.14763/2016.3.425
- Mauldin, A. (2019). Telegeography goes back to the future. Pacific Telecommunications Council, Honolulu, Hawaii. https://blog.telegeography.com/2019-telecom-networks-update-summary-ptc-submarine-cables
- Mikler, J. (2011). Sharing sovereignty for policy outcomes. Policy and Society, 30(3), 151–160. https://doi.org/10.1016/j.polsoc.2011.07.007
- Mikler, J. (2018). The political power of global corporations. Polity.
- Moore, M., & Tambini, D. (Eds.). (2018). Digital dominance: The power of Google, Amazon, Facebook, and Apple. Oxford University Press.
- Mortensen, H. (2020). Spionernes guldaeg. Weekendavisen. https://www.weekendavisen.dk/2020-35/samfund/spionernes-guldaeg
- Mukerji, C. (2015). The material turn. In M. Buchmann, S. M. Kosslyn, & R. A. Scott (Eds.), Emerging trends in the social and behavioral sciences: An interdisciplinary, searchable, and linkable resource (pp. 1–13). John Wiley & Sons. https://doi.org/10.1002/9781118900772.etrds0109
- Munn, L. (2020). Red territory: forging infrastructural power. Territory, Politics, Governance, 37(1), 1–20. https://doi.org/10.1080/21622671.2020.1805353
- Newton, C. (2020). A sneaky attempt to end encryption is worming its way through Congress. The Verge. https://www.theverge.com/interface/2020/3/12/21174815/earn-it-act-encryption-killer-lindsay-graham-match-group
- Nye, J. S. (2020). Power and interdependence with China. The Washington Quarterly, 43(1), 7–21. https://doi.org/10.1080/0163660X.2020.1734303
- Nye, J. S., & Keohane, R. O. (1971). Transnational relations and world politics: An introduction. International Organization, 25(3), 329–349. http://www.jstor.org/stable/2706043 https://doi.org/10.1017/S0020818300026187
- Oatley, T. (2021). Regaining relevance: IPE and a changing global political economy. Cambridge Review of International Affairs, 1–10, 34(2), 318–327. https://doi.org/10.1080/09557571.2021.1888880
- PA Consulting. (2021). Data centre growth in the Nordics. https://www.paconsulting.com/insights/data-centre-growth-in-the-nordics/
- Paris, R. (2020). The right to dominate: How old ideas about sovereignty pose new challenges for world order. International Organization, 74(3), 453–489. https://doi.org/10.1017/S0020818320000077
- Parks, L. D., & Starosielski, N. (Eds.). (2015). The geopolitics of information. Signal traffic: Critical studies of media infrastructures. University of Illinois Press. http://search.ebscohost.com/login.aspx?direct=true&scope=site&db=nlebk&AN=992537
- Perlroth, N. (2021). This is how they tell me the world ends: The cyber weapons arms race. Bloomsbury Publishing Plc.
- Petry, J., Fichtner, J., & Heemskerk, E. (2021). Steering capital: the growing private authority of index providers in the age of passive asset management. Review of International Political Economy, 28(1), 152–176. https://doi.org/10.1080/09692290.2019.1699147
- Rodine-Hardy, K. (2015). Globalization, international organizations, and telecommunications. Review of Policy Research, 32(5), 517–537. https://doi.org/10.1111/ropr.12137
- Rosemain, M. (2021). France embraces Google, Microsoft in quest to safeguard sensitive data. Reuters. https://www.reuters.com/technology/france-embraces-google-microsoft-quest-safeguard-sensitive-data-2021-05-17/
- Rosemain, M., & Satter, R. (2021). Millions of websites offline after fire at French cloud services firm. Reuters. https://www.reuters.com/article/us-france-ovh-fire-idUSKBN2B20NU
- Ruiz, J. B., & Barnett, G. A. (2015). Who owns the international Internet networks? The Journal of International Communication, 21(1), 38–57. https://doi.org/10.1080/13216597.2014.976583
- Sargsyan, T. (2016). Data localization and the role of infrastructure for surveillance, privacy, and security. International Journal of Communication, 10(2016), 17. https://ijoc.org/index.php/ijoc/article/view/3854
- Sassen, S. (2018). Embedded borderings: making new geographies of centrality. Territory, Politics, Governance, 6(1), 5–15. https://doi.org/10.1080/21622671.2017.1290546
- Schwartz, H. M. (2019). American hegemony: intellectual property rights, dollar centrality, and infrastructural power. Review of International Political Economy, 26(3), 490–519. https://doi.org/10.1080/09692290.2019.1597754
- Seabrooke, L., & Tsingou, E. (2021). Revolving doors in international financial governance. Global Networks, 21(2), 294–319. https://doi.org/10.1111/glob.12286
- Seabrooke, L., & Wigan, D. (2017). The governance of global wealth chains. Review of International Political Economy, 24(1), 1–29. https://doi.org/10.1080/09692290.2016.1268189
- Sherman, J. (2021). Cyber defense across the ocean floor: The geopolitics of submarine cable security. https://www.atlanticcouncil.org/in-depth-research-reports/report/cyber-defense-across-the-ocean-floor-the-geopolitics-of-submarine-cable-security/
- Smith, B., & Browne, C. A. (2019). Tools and weapons: The promise and the peril of the digital age. Hodder.
- Staff, S. (2014). Spying Together: Germany's Deep Cooperation with the NSA. DER SPIEGEL. https://www.spiegel.de/international/germany/the-german-bnd-and-american-nsa-cooperate-more-closely-than-thought-a-975445.html
- Starosielski, N. (2015). The undersea network". SST, Sign, storage, transmission. Duke University Press.
- Strange, S. (1989). States and markets (Reprinted.). Pinter.
- Strange, S. (1996). The Retreat of the state: The diffusion of power in the world economy. Cambridge studies in international relations (Vol. 49). Cambridge University Press. https://doi.org/10.1017/CBO9780511559143
- Svantesson, D., & Gerry, F. (2015). Access to extraterritorial evidence: The Microsoft cloud case and beyond. Computer Law & Security Review, 31(4), 478–489. https://doi.org/10.1016/j.clsr.2015.05.007
- TAT-14. (2001). General Committee. https://web.archive.org/web/20010221215619/http://www.tat-14.com/gclist.jsp.
- Telegeography. (2017). A complete list of content providers' submarine cable holdings. https://blog.telegeography.com/telegeographys-content-providers-submarine-cable-holdings-list
- Telegeography. (2020a). Submarine cable map. https://www.submarinecablemap.com/#/submarine-cable
- Telegeography. (2020b). Out with the old cables, in with the new. https://web.archive.org/save/https://blog.telegeography.com/out-with-the-old-cables-in-with-the-new
- Tibbles, J. (2017). Submarine cables, security and the state. Submarine Telecoms Forum, 94, 22–31.
- Uzzi, B. (1996). The sources and consequences of embeddedness for the economic performance of organizations: The network effect. American Sociological Review, 61(4), 674. https://doi.org/10.2307/2096399
- Weiss, L. (2000). Globalization and state power. Development and Society, 29(1), 1–15.
- Weiss, L., & Thurbon, E. (2018). Power paradox: how the extension of US infrastructural power abroad diminishes state capacity at home. Review of International Political Economy, 25(6), 779–810. https://doi.org/10.1080/09692290.2018.1486875
- Wilks, S. (2013). The political power of the business corporation. Edward Elgar Publishing. http://search.ebscohost.com/login.aspx?direct=true&scope=site&db=nlebk&db=nlabk&AN=551299
- Wimmer, A., & Glick Schiller, N. (2002). Methodological nationalism and beyond: nation-state building, migration and the social sciences. Global Networks, 2(4), 301–334. https://d1wqtxts1xzle7.cloudfront.net/2059675/Methodological_Nationalism_and_Beyond__Global_Networks_Wimmer_and_Glick_Schiller_2002_-with-cover-page-v2.pdf?Expires=1632732697&Signature=BrHBkqYwAvPwAwrN-JJqyHjxT1u6tNg994LYnzyK1J30gnKD2fQkCu9z5aR8yCd7IG75DLUV6wa4UnkSDGuQZ5VBBq4KZjqQ2CM1TBrw-EHxEjIePmKjWIKBatYujzSusNyknjf8W0KVQbNJDCnNWlscBZqWBg13i6deTRRTrNzW5eEQhKuXSOUlWDxn9∼zwqjvr4qLGlDivcPyswyc2ThS5PZqUvNqiH3aI71kyANVBGT7yoWFPgej∼Akn8zAM4CLhtbd1j78DfzkKdV6i8AiCOeVnuqHtCbcmLO2AQl53CWixj9dCLb60lAemOCW6OG8X9TDp2jQRtW3giuK6D7Q__&Key-Pair-Id=APKAJLOHF5GGSLRBV4ZA https://doi.org/10.1111/1471-0374.00043
- Winecoff, W. K. (2020). The persistent myth of lost hegemony,” revisited: structural power as a complex network phenomenon. European Journal of International Relations, 26(1_suppl), 209–252. https://doi.org/10.1177/1354066120952876
- Winseck, D. (2017). The geopolitical economy of the global internet infrastructure- CRUCIAL TEXT. Journal of Information Policy, 7(1), 228–267. https://doi.org/10.5325/jinfopoli.7.2017.0228
- Wu, T. (2011). The master switch: The rise and fall of information empires (1. Vintage Books ed.). Vintage Books.
- Wyden, R. (2019). Can You Track Me Now? Why the phone companies are such a privacy disaster. DEFCON. https://media.defcon.org/DEF%20CON%2027/DEF%20CON%2027%20audio/DEF%20CON%2027%20conference%20audio%20flac/DEF%20CON%2027%20Conference%20-%20US%20Senator%20Ron%20Wyden%20-%20Can%20You%20Track%20Me%20Now%20Why%20The%20Phone%20Companies%20Are%20Such%20A%20Privacy%20Disaster.txt
- Zegart, A., & Childs, K. (2018). The divide between Silicon Valley and Washington is a national-security threat. The Atlantic. https://www.theatlantic.com/ideas/archive/2018/12/growing-gulf-between-silicon-valley-and-washington/577963/