?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
Human activity tracking plays a vital role in human–computer interaction. Traditional human activity recognition (HAR) methods adopt special devices, such as cameras and sensors, to track both macro- and micro-activities. Recently, wireless signals have been exploited to track human motion and activities in indoor environments without additional equipment. This study proposes a device-free WiFi-based micro-activity recognition method that leverages the channel state information (CSI) of wireless signals. Different from existed CSI-based micro-activity recognition methods, the proposed method extracts both amplitude and phase information from CSI, thereby providing more information and increasing detection accuracy. The proposed method harnesses an effective signal processing technique to reveal the unique patterns of each activity. We applied a machine learning algorithm to recognize the proposed micro-activities. The proposed method has been evaluated in both line of sight (LOS) and none line of sight (NLOS) scenarios, and the empirical results demonstrate the effectiveness of the proposed method with several users.
1. Introduction
Human motion and activity analysis has received increasing attention in recent decades because of advances in computing and sensing technologies as well as interest in action and gesture recognition applications such as security and surveillance, human–computer interaction, and gaming (Campbell et al. Citation2008). Information collected from target objects and target environments can be exploited to identify an appropriate action (Campbell et al. Citation2008). Therefore, human motion and activity analysis is realized by combining sensing and reasoning to deliver context-aware data that can be employed to provide personalized support in many applications (Chen et al. Citation2012). Traditional human activity recognition (HAR) approaches have proposed various novel methods which are applied in different sensing areas, such as security, entertainment, and healthcare (Lara and Labrador Citation2013; Poppe Citation2010). Vision-based techniques generally require the installation of cameras in the perceived environments to track human motion; therefore, vision-based (or camera-based) systems require adequate light conditions and cannot traverse through physical barriers such as walls. The primary drawbacks of sensor-based sensing mechanisms are the burdens imposed by installation in test areas or the human body as well as inconvenient usage, particularly for the patients or elderly.
The shadowing effects produced by a moving object in the line of sight (LOS) between a wireless transmitter and a receiver in a home wireless network can be used to track object motions in indoor environments (Woyach, Puccinelli, and Haenggi Citation2006; Youssef and Mah Citation2007). The received signal strength indicator (RSSI) of a wireless signal fluctuates due to the object movements in indoor environments. Therefore, such fluctuations can be used to track object motions without requiring burden equipment. This observation has opened a new avenue for sensing technologies that depend on only wireless signals. Many studies have proposed human localization, human motion detection, macro HAR, and micro-activity recognition methods that use RSSI and channel state information (CSI).
Device-free CSI-based methods outperform RSSI-based methods relative to localization accuracy of <1 m, wherein RSSI is >1 m (Yang, Zhou, and Liu Citation2014). CSI-based methods can detect an anomaly which is affected by environmental changes and can reflect the varying multipath reflection caused by an intruder’s presence due to its frequency diversity (Bhartia et al. Citation2011). RSSI and CSI are coarse- and fine-grained channel information, respectively. The main differences are that (1) RSSI is the average value of the signals received, whereas CSI contains more information about the fading channel through amplitude and phase and (2) RSSI is severely affected by multipath effects.
Herein, the CSI of wireless physical layer is leveraged to track human micro-activities in indoor environments such as dodge, push, strike, circle, punch, bowl, drag, pull and kick. An efficient method is proposed to extract both amplitude and phase information from CSI. Each unique motion is observed to have different impacts on wireless CSI; therefore, each action has a unique pattern. However, exposing the unique patterns of each micro-activity is challenging. This study proposes an effective method to extract patterns from amplitude and phase information. Then, a machine learning algorithm is employed to classify nine micro-activities.
The main contributions of this paper are summarized as follows.
A device-free micro-activity recognition method is proposed that uses ubiquitous wireless devices, thereby eliminating the need for additional hardware installation.
Differing from previous methods, the proposed method exploits both phase and amplitude information in CSI.
An efficient pattern recognition method is proposed to expose the start and end points of a given activity.
The efficiency of the proposed method is verified via empirical results.
2. Related work
2.1. RSSI
Over the last decade, RSSI has been used in human localization, human motion detection, and human activity recognition research. For human motion detection (Kosba, Saeed, and Youssef Citation2012; Moore et al. Citation2010; Yang et al. Citation2010), RSSI has been leveraged to capture environmental changes that become anomalous when an intruder enters an observed environment. Moore et al. (Citation2010) presented a system positioned human motion that considers changes in the standard deviation of the received signal strength between stationary wireless transmitters and receivers at fixed locations. Kosba, Saeed, and Youssef (Citation2012) utilized RSSI to track environmental changes that fluctuate when a moving object (i.e. a human) enters an area of interest. Yang et al. (Citation2010) proposed an RSSI-based joint intrusion learning method that simultaneously classifies several human intrusion patterns. Booranawong, Jindapetch, and Saito (Citation2018) presented a human motion detection and tracking method that uses RSSI. This method defined two functions: one function to enhance the collecting and measuring process of RSSI signals affected by human motion and a second function that uses a predefined threshold and zone selection method for human motion detection in indoor environments.
Over the recent years, device-free RSSI-based technology has developed to recognize human macro human activity, such as sitting, walking, lying, and standing (Gu, Quan, and Ren Citation2014; Scholz et al. Citation2013; Sigg et al. Citation2014). Scholz et al. (Citation2013) presented a device-bound and device-free HAR system that can classify four macro activities (standing, walking, lying, and sitting). The proposed system used 802.15.4 RSSI for HAR in two different methods. In the first method, the target user carries a wireless node (device-bound); in the second method, the target user moves in a wireless sensor network (WSN) without a WSN node (device-free). They performed 10-fold cross-validation with all nodes and achieved accuracies of 0.896 (device-bound), 0.894 (device-free), and 0.88 using an accelerometer. However, this method requires the target user to carry wireless devices or install wireless sensor nodes in the target environments. Therefore, such a system cannot be considered device-free because the system implementation requires special devices to be carried by the target object or to be installed in the test environment. Sigg et al. (Citation2014) presented a human activity recognition system that considers the fluctuation in radio signals caused by human activities. The proposed system can track several human activities such as lying, walking, standing, and crawling. Their system achieved high accuracy under different conditions. Although this method leveraged RSSI to track human activities, it was implemented using software defined radio with special devices such as universal software radio peripherals. Gu, Quan, and Ren (Citation2014) proposed a WiFi-assisted HAR method primarily aiming to utilize data mining technique to abstract fingerprints of several activities in the radio signal strength data. They tested sitting, standing, and walking activities in a static environment and achieved an accuracy of 0.75 using a KNN classifier and 91% using a proposed fusion algorithm (Gu, Quan, and Ren Citation2014).
Some studies have recently presented micro-activity recognition systems such as hand gesture recognition (Abdelnasser, Youssef, and Harras Citation2015; Melgarejo et al. Citation2014). A hand gesture recognition scheme was previously proposed based on readily deployable ubiquitous WLAN devices using a sophisticated WARP v3 board equipped with two RE14P directional patch antennas (Melgarejo et al. Citation2014). The proposed scheme was implemented and tested in two different scenarios: gesture-based electronic activation from a wheelchair (tested up to 25 gestures and achieved 92% accuracy) and gesture-based control of a car infotainment system (average accuracy of 84%).
WiGest (Abdelnasser, Youssef, and Harras Citation2015) is a device-free gesture recognition system that leverages the fluctuation in RSSI caused by human hand motions in test movements. WiGest recognized several hand gestures and achieved an accuracy of 87.5% using a single transmitter and an average accuracy of 96% using three overhead transmitters.
However, RSSI-based device-free sensing technique has a limitation due to the variability of RSSI caused by environmental changes that may cause false detections.
2.2 CSI
Recently, CSI was leveraged for indoor localization and activity recognition. A device-free WiFi-based localization method was proposed by utilizing changes in CSI across multiple wireless link subcarriers (Wu et al. Citation2012). In a CSI-MIMO fingerprint positioning system (Chapre et al. Citation2014), MIMO information, CSI amplitude, phase information of each subcarrier were comprehensively utilized to obtain accurate position information. Zhou et al. (Citation2014) modeled the CSI subcarrier amplitude as a histogram. They then applied the empirical mode decomposition (EMD) algorithm for signal classification and constructed a fingerprint database to design a passive omnidirectional human detection system (Omni-PHD), which can effectively detect the full range of human emergence. Xi et al. (Citation2014) proposed a device-free crowd counting system (FCC). FCC observes the variation in CSI and its relation with the number of moving people. Han et al. (Citation2018) leveraged CSI to track human motion in an indoor environment using the multiple antenna voting method. A home intruder system based on the CSI of WiFi signals was also presented (Al-qaness et al. Citation2016b). This method tracks door intrusion by tracking the fluctuations of human motion in an indoor environment. Lv et al. (Citation2017) also presented an indoor intrusion system based on CSI. This system uses a hidden Markov model to classify human intrusion actions.
Wang et al. (Citation2014) proposed the E-eyes indoor activity recognition system. The E-eyes system divides human activities into in-place activities, such as cooking in the kitchen or bathing in the bathroom, and walking activities such as walking while talking on the phone. E-eyes uses a WiFi access point and common family WiFi devices to construct an activity recognition system that identifies a fixed-position activity (i.e. in-place activities) and walking movements. This system can identify different activities in the same location, such as standing while washing dishes, and human walking activities, such as walking while talking on the phone. This system is based on the fact that different activities have a different CSI amplitude histogram distribution, and this histogram distribution is used to construct human activity feature information profiles in a semi-supervised manner. Then, human activities are identified using pattern matching algorithms. Wei et al. (Citation2015) proposed HAR by analyzing CSI at the receiver end of the communication system to classify four activities (walking, standing, lying, and sitting). They demonstrated the manner in which radio frequency interference (RFI) can impact device-free HAR applications. They proved that conducting experiments in environments with RFI caused significant impact on CSI vectors. In the absence of RFI, different activities yield different CSI vectors that can be differentiated visually. The results obtained in an environment without RFI showed good accuracy; however, in the presence of RFI, accuracy gradually decreased. This system was evaluated using a pair of Wireless Ad hoc System for Positioning (WASP) nodes.
De Sanctis et al. (Citation2015) proposed the HAR system, known as WIBECAM, which recognizes walking, sitting, and standing. WIBECAM periodically collects beacon frames sent by WiFi access points. WIBECAM works like snapshots by observing the received beacon frames and calculates frequency domain spectral metrics of each observed frame.
Wang et al. (Citation2017) presented a CSI-based activity recognition scheme known as CRAM. CRAM recognizes several human activities, such as running, walking, sitting down, opening a refrigerator, falling, pushing, and boxing. CRAM considers the correlation between the collected CSI value and the implemented activity. Dong et al. (Citation2018) proposed a CSI-based HAR scheme that incorporates correlation-based fusion, Doppler spread spectrum, and moving variance segmentation methods. Furthermore, other studies (Al-qaness et al. Citation2016a; Li et al. Citation2016) have proposed different methods to avoid stream different sensitivities to human motion since each CSI stream has a different sensitivity to human motion, so, some streams may have more sensitivity, while others may have not enough sensitivity to human motions. To avoid false detection, insensitive CSI streams must be eliminated. A so-called bad stream elimination algorithm was previously proposed (Al-qaness et al. Citation2016b) to eliminate so-called bad streams (insensitive streams). Principal component analysis (PCA) was also applied across all CSI streams (Li et al. Citation2016). However, CSI-based HAR is still in its nascent stages and requires improvement.
More so, CSI has been leveraged in various human micro-activity recognition studies. For example, Nandakumar, Kellogg, and Gollakota (Citation2014) presented a CSI-based hand gesture recognition method that classifies four hand gestures in LOS and simple non-line-of-sight (NLOS) scenarios with average accuracies of 91% and 89%, respectively. He et al. (Citation2015) presented a WiFi-based hand gesture recognition system known as WiG that can classify four hand gestures in both LOS and NLOS scenarios, demonstrating accuracies of 92% and 88%, respectively. Sun et al. (Citation2015) proposed the in-air handwriting recognition system known as WiDraw. They used the angle of arrival of the received signals at the wireless receiver part to track the direction of the target hand. WiDraw classified several in-air handwriting actions at an average accuracy of 91%. Another study (Al-qaness and Li Citation2016) presented the WiGeR: WiFi-based gesture recognition system that extracts CSI and employs wavelet analysis and short-time energy to expose unique patterns produced by unique hand motions in a specific duration. WiGeR classified 13 hand gestures under different scenarios and achieved an average accuracy of 92% in several scenarios. Tian et al. (Citation2018b) presented a hand gesture recognition scheme that leverages the CSI of WiFi signals. The basic idea to build a virtual antenna from the reflected signals due to hand motions. They adopted support vector machine (SVM) to recognize each hand motion. The proposed scheme was evaluated with 6 hand gestures and achieved an average accuracy of 97%. A hand gesture recognition method based on CSI, namely, WiCatch was presented (Tian et al. Citation2018b). Wicatch also adopted SVM to classify nine hand gestures and achieved an accuracy of 96%.
3. Methodology
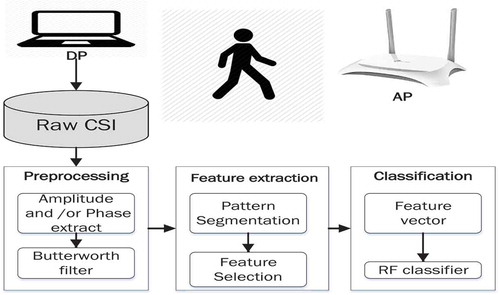
The proposed method includes four stages: data collection and normalization, pattern segmentation, feature selection, and activity classification. shows a workflow of the proposed method. First, CSI is collected at detection point (DP) (i.e. wireless receiver), which is a laptop installed with Ubuntu and the open source CSI-Tool (Halperin et al. Citation2011). The collected CSI data are then preprocessed to adopt the adequate CSI data and to remove noise by applying a Butterworth filter and PCA. Then, the proposed method extracts several features and builds a feature vector for input to a machine learning classifier. Random forest (RF) algorithm is then used to recognize the proposed micro-activities. Each stage is illustrated in detail in the following sections.
3.1. Data collection and normalization
CSI is a collection of information that describes the state of a channel and includes amplitude as well as phase information. The CSI-Tool (Halperin et al. Citation2011) can be used to extract CSI from commodity wireless network interface controllers (NIC).
Herein, CSI data collected from a wireless network that composed of a transmitter with two transmitted antennas (WiFi router) as an access point (AP) and a laptop installed IWL 5300 NIC as a DP with three received antennas. Therefore, according to OFDM, each collected packet had CSI streams (6 streams). Each stream has 30 subcarriers, as reported by the IWL 5300 NIC (Halperin et al. Citation2011). Thus, the gathered CSI can be described using Equation 1 as follows:
where H is the raw CSI and each element in the CSI matrix is represented as follows:
where is the amplitude of CSI,
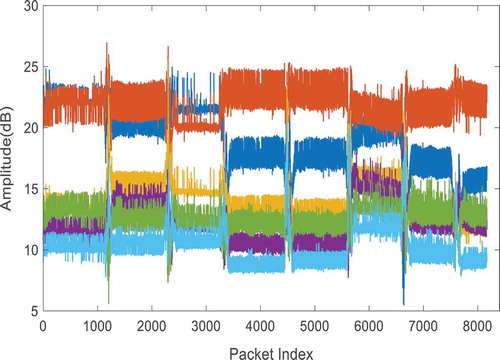
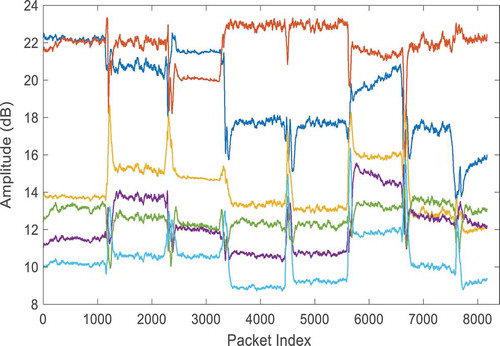
is the phase information of the CSI, and i refers to the number of streams, where j refers to the numbers of subcarriers. The gathered CSI is affected by surrounding electromagnetic noise, as shown in ; therefore, a lowpass Butterworth filter is applied to filter noise ().
Therefore, for reported CSI streams, we perform PCA to obtain p principle components (PCs) as follows.
Data collection: The system collects N CSI packets and removes noise using Butterworth filters. Then, the system obtains an N × Sn matrix Ht,r.
where Ht,r(n) represents a vector containing Sn × 1-dimensional CSI values from all Sn streams at the (t,r) antenna pair for the nth collected CSI packet.
Covariance matrix: The system normalizes Ht,r to obtain the normalized version Zt,r with zero mean and unit variance. Then, the system calculates the covariance matrix.
Eigen decomposition: The system calculates eigenvectors by eigen decomposition of the correlation matrix.
Principal components: The system constructs and obtains the top p PCs as follows:
where represents the eigenvectors and p represents the principal components.
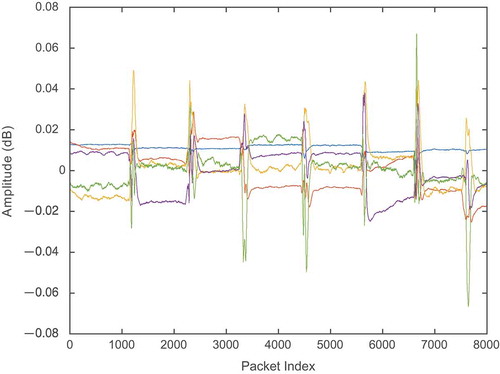
Due to the high correlation of CSI, noises are primarily captured in the first PC; thus, the system removes the first component and retains the remaining PCs ().
3.2. Pattern segmentation
An envelope extraction method based on the Huang–Hilbert transform (Huang et al. Citation1998) is used herein to determine the width of the dynamic time window. Huang et al. (Huang et al. Citation1998) proposed the EMD algorithm. EMD is a self-adaptive signal processing method; thus, it is suitable for application in non-stationary signal processing scenarios. EMD decomposes data into intrinsic mode functions (IMFs) to solve problems involving non-stationary data for which the Hilbert transform cannot be used. Each IMF can represent a type of oscillatory mode embedded in the signal.
Moreover, each IMF should satisfy the following conditions: 1) the number of extreme and zero-crossing points must either be equal or differ by at most one among the entire dataset and 2) the mean value of the envelope is defined by the local maxima, and the local minima must be zero at any point in the dataset. The EMD algorithm for signal X(t) can be represented as follows: .
Initialize
.
Initialize
.
Calculate the upper and lower envelopes of hik via cubic spline interpolation in its local maxima and minima.
Calculate the mean value hik(t) of the upper envelop and lower envelop; then, let
(5) If hi(k+1) satisfies the above conditions, it becomes an IMF; thus, set ci (t) = hi(k+1) (t); otherwise, k = k + 1 and the step number 4 are repeated.
The residue is calculated as . If ri+1 (t) contains at least two extremes, it is treated as input to derive the following IMF. Otherwise, the process completes and ri+1(t) is denoted as the final residue rf.
(6) The original signal X(t) should be decomposed into a set of IMFs ci (t) and a residue rf as
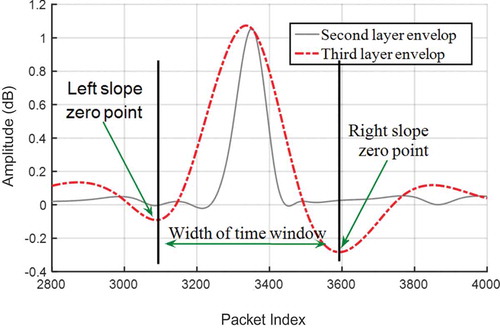
shows that the width of the peak is very precise. In the third layer of the envelope curve, the left and right slope zero points are clearly identifiable. The time between the two zero points is the width of the dynamic time window.
3.3. Feature extraction and activity classification
The proposed method extracts six features (mean, maximum value, standard deviation, percentiles, median absolute deviation, and entropy) for both the amplitude and phase of CSI to classify micro-activities.
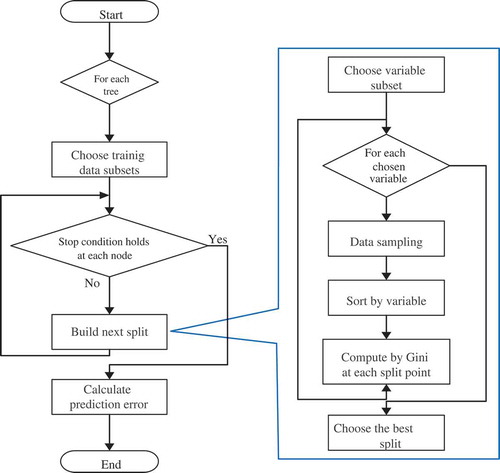
RF classification algorithm (Breiman Citation2001) is employed to classify the proposed micro-activities. shows the workflow of the RF algorithm. RF is used to rank the importance of variables in the classification problem.
To measure variable importance in a given dataset, the RF must first be fitted to the data. The system records out-of-bag errors for each data point and averaged over the forest during this process. The importance of the jth feature after training is measured by permuting the values of the jth feature among the training data and by computing the out-of-bag error on the perturbed dataset. Then, the system computes an importance score for the given feature by averaging the difference in out-of-bag error before and after permutation over all trees. This score is normalized by the standard deviation of the difference. Herein, the system ranks the features with large values for the estimated score as more important than the other features.
4. Results
4.1. Experimental setup
Test experiments were conducted in an apartment having a lot of furniture. The experimental hardware comprised one TP-LINK TL-WR842N router as an AP and one Lenovo laptop installed with Ubuntu 14.04. AP and DP were placed in the LOS of each other at a distance of 3 m. DP and AP were placed at the top-left and bottom-right corners of the room, respectively. The proposed activities were implemented at a fixed position because the signal values at each position differed. The door and windows were closed to ensure stability in the test environment. We implemented nine micro-activities discussed in the literature (Pu et al. Citation2013), i.e. push, dodge, strike, pull, drag, kick, circle, punch (twice), and bowl, that were labeled as nine classes (C1–C9, respectively). shows additional details about the experimental factors.
Table 1. Experimental details.
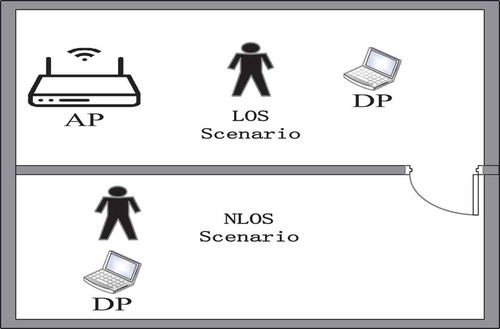
The proposed method was evaluated under two scenarios, i.e. LOS and NLOS (). In the LOS scenario, the user, AP, and DP were located in the same room. In the NLOS scenario, the user and DP were in the same room and the DP was in another room.
4.2. Evaluation results
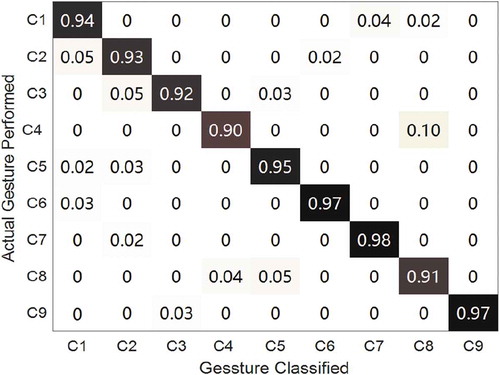
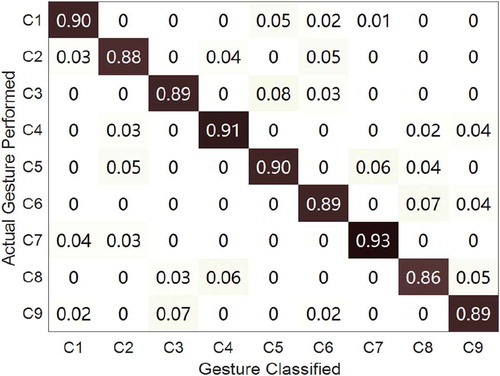
The evaluation experiments were conducted in indoor environments described above with up to 10 users performing the proposed micro-activities individually. We collected 300 samples of each micro-activity across 10 sessions. In each session, each user was asked to perform each micro-activity 30 times at a fixed position. The proposed method measured the 10th cross-validation. The confusion matrix was used to show the achieved results, as shown in .
The precision, recall, and F-measure metrics were used to evaluate the proposed method. Precision is a positive predictive value calculated as follows:
where TP and FP represent true positive and false positive, respectively. Recall (or sensitivity) is calculated as follows:
where FN represents false negative. F-measure is the weighted average of recall and precision. F-measure is calculated as follows:
shows the precision, recall, and F-measure results for each activity.
Table 2. Precision, recall, and F-measure results.
In the NLOS scenario, the user and DP (laptop) were in the same room and the AP (WiFi router) was in another room. shows the confusion matrix of the NLOS scenario. The overall accuracy of the NLOS scenario was 89.147%.
Moreover, precision, recall, and F-measure were also used to evaluate the proposed method under the NLOS scenario. Results are shown in .
Table 3. Precision, recall, and F-measure of each activity in NLOS scenario.
Overall, the evaluation results demonstrated that the proposed method achieved high accuracy for each activity in both the LOS and NLOS scenarios. In future, we plan to extend this study to overcome current challenges primarily related to testing two or more users simultaneously due to the sensitivity of CSI to human motion.
5. Conclusions
This study proposed a device-free CSI-based human micro-activity recognition method that uses the CSI of an indoor ubiquitous wireless infrastructure. We described recent advances of device-free human sensing technology and proposed an effective method to address challenges, including CSI filtering, pattern segmentation, and micro-activity classification. The proposed method was evaluated in a complex indoor environment, and it classified nine human micro-activities. The proposed method was evaluated in both LOS and NLOS scenarios with 10 users, and the empirical results demonstrate that the proposed method reached high accuracy. Currently, device-free WiFi-based sensing technologies (including both RSSI and CSI) have achieved good performance relative to sensing single human activities; however, such technologies are limited when tracking two or more people movements. Therefore, tracking multiple people activities requires further investigation in the future.
Acknowledgments
We would like to thank the committee chair of the 2018 Ubiquitous Positioning, Indoor Navigation and Location-Based Services (UPINLBS) and the reviewers for their insightful comments and suggestions that improved the quality of this manuscript. We would like to thank them for recommending this article. We also thank the editorial staff and reviewers of GSIS for their consideration and valuable comments.
Additional information
Notes on contributors
Mohammed A. A. Al-qaness
Mohammed A. A. Al-qaness received the B.S., M.S., and Ph.D. degrees in information and communication engineering from the Wuhan University of Technology in 2010, 2014, and 2017, respectively. He is currently a Lecturer at the School of Computer Science, Wuhan University, Wuhan, China. He has published over ten papers in wireless and mobile computing and indoor human tracking and activity recognition. His current research interests include wireless sensing, mobile computing, machine learning, and image classification.
References
- Abdelnasser, H., M. Youssef, and K. A. Harras. 2015. “WiGest: A Ubiquitous WiFi-based Gesture Recognition System.” Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Hong Kong, 26 April–1 May. doi:10.1109/INFOCOM.2015.7218525
- Al-qaness, M., and F. Li. 2016. ““Wiger: WiFi-Based Gesture Recognition System.” ISPRS International Journal of Geo-Information 5 (6): 92. doi:10.3390/ijgi5060092.
- Al-qaness, M., F. Li, X. Ma, Y. Zhang, and G. Liu. 2016a. “Device-Free Indoor Activity Recognition System.” Applied Sciences 6 (11): 329. doi:10.3390/app6110329.
- Al-qaness, M. A. A., F. Li, X. Ma, and G. Liu. 2016b. “Device-Free Home Intruder Detection and Alarm System Using Wi-Fi Channel State Information.” International Journal of Future Computer and Communication 5 (4): 180–186. doi:10.18178/ijfcc.2016.5.4.468.
- Bhartia, A., Y.-C. Chen, S. Rallapalli, and L. Qiu. 2011. “Harnessing Frequency Diversity in Wi-Fi Networks.” Proceedings of the 17th Annual International Conference on Mobile Computing and Networking (Mobicom ’11), Las Vegas. September 19–23. doi:10.1145/2030613.2030642
- Booranawong, A., N. Jindapetch, and H. Saito. 2018. “A System for Detection and Tracking of Human Movements Using RSSI Signals.” IEEE Sensors Journal 18 (6): 2531–2544. doi:10.1109/JSEN.2018.2795747.
- Breiman, L. 2001. ““Random Forests.” Machine Learning 45 (1): 5–32. doi:10.1023/A:1010933404324.
- Campbell, A. T., S. B. Eisenman, N. D. Lane, E. Miluzzo, R. A. Peterson, H. Lu, X. Zheng, M. Musolesi, and G. S. Ahn. 2008. “The Rise of People-Centric Sensing.” IEEE Internet Computing 12 (4): 12–21. doi:10.1109/MIC.2008.90.
- Chapre, Y., A. Ignjatovic, A. Seneviratne, and S. Jha. 2014. “CSI-MIMO: Indoor Wi-Fi Fingerprinting System.” Proceedings of the IEEE 39th Conference on Local Computer Networks (LCN), Edmonton, September, 8–11. doi:10.1109/LCN.2014.6925773
- Chen, L., J. Hoey, C. D. Nugent, D. J. Cook, and Z. Yu. 2012. “Sensor-Based Activity Recognition.” IEEE Transactions on Systems, Man and Cybernetics Part C(Applications and Reviews) 42 (6): 790–808. doi:10.1109/TSMCC.2012.2198883.
- De Sanctis, M., E. Cianca, S. Di Domenico, D. Provenziani, G. Bianchi, and M. Ruggieri. 2015. “WIBECAM: Device Free Human Activity Recognition through WiFi Beacon-Enabled Camera.”Proceedings of the 2nd Workshop on Workshop on Physical Analytics (WPA), Florence. May, 19–22. doi:10.1145/2753497.2753499
- Dong, Z., F. Li, J. Ying, and K. Pahlavan. 2018. “Indoor Motion Detection Using Wi-Fi Channel State Information in Flat Floor Environments versus in Staircase Environments.” Sensors 18 (7): 2177. doi:10.3390/s18072177.
- Gu, Y., L. Quan, and F. Ren. 2014. “WiFi-assisted Human Activity Recognition.” Proceedings of the APWiMob 2014: IEEE Asia Pacific Conference on Wireless and Mobile, Bali, August, 28–30. doi:10.1109/APWiMob.2014.6920266
- Halperin, D., W. Hu, A. Sheth, and D. Wetherall. 2011. ““Tool Release: Gathering 802.11n Traces with Channel State Information.” ACM SIGCOMM Computer Communication Review 41 (1): 53. doi:10.1145/1925861.1925870.
- Han, C., Q. Tan, L. Sun, H. Zhu, and J. Guo. 2018. ““ CSI Frequency Domain Fingerprint-Based Passive Indoor Human Detection. “.” Information (Switzerland) 9 (4): 95. doi:10.3390/info9040095.
- He, W., K. Wu, Y. Zou, and Z. Ming 2015. WiG: WiFi-based Gesture Recognition System.” Proceedings of the International Conference on Computer Communications and Networks, ICCCN, Las Vegas, August, 3–6. 10.1109/ICCCN.2015.7288485
- Huang, N. E., Z. Shen, S. R. Long, M. C. Wu, H. H. Shih, Q. Zheng, N. C. Yen, C. C. Tung, and H. H. Liu. 1998. “The Empirical Mode Decomposition and the Hubert Spectrum for Nonlinear and Non-Stationary Time Series Analysis.” Royal Society A: Mathematical, Physical and Engineering Sciences 454 (1971): 903–995. doi:10.1098/rspa.1998.0193.
- Kosba, A. E., A. Saeed, and M. Youssef 2012. “Robust WLAN Device-Free Passive Motion Detection.” Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Lugano, March, 19–23. 10.1109/WCNC.2012.6214375
- Lara, Ó. D., and M. A. Labrador. 2013. “A Survey on Human Activity Recognition Using Wearable Sensors.” IEEE Communications Surveys and Tutorials 15 (3): 1192–1209. doi:10.1109/SURV.2012.110112.00192.
- Li, F., M. A. A. Al-qaness, Y. Zhang, B. Zhao, and X. Luan. 2016. “A Robust and Device-Free System for the Recognition and Classification of Elderly Activities.” Sensors 16 (12): 2043. doi:10.3390/s16122043.
- Lv, J., D. Man, W. Yang, X. Du, and M. Yu. 2017. “Robust WLAN-Based Indoor Intrusion Detection Using PHY Layer Information.” IEEE Access 6: 30117–30127. doi:10.1109/ACCESS.2017.2785444.
- Melgarejo, P., X. Zhang, P. Ramanathan, and D. Chu 2014. Leveraging Directional Antenna Capabilities for Fine-Grained Gesture Recognition. Proceedings of the 2014 ACM International Joint Conference on Pervasive and Ubiquitous Computing (UbiComp 2014), Seattle, September, 13–17. 10.1145/2632048.2632095
- Moore, R., R. Howard, P. Kuksa, and R. P. Martin 2010. A Geometric Approach to Device-Free Motion Localization Using Signal Strength.“ Technical Report, Rutgers University DCS-TR-674.
- Nandakumar, R., B. Kellogg, and S. Gollakota. 2014. “Wi-Fi Gesture Recognition on Existing Devices.” ArXiv Preprint ArXiv 1411.5394 (2): 1–6.
- Poppe, R. 2010. “A Survey on Vision-Based Human Action Recognition.” Image and Vision Computing 28 (6): 976–990. doi:10.1016/j.imavis.2009.11.014.
- Pu, Q., S. Gupta, S. Gollakota, and S. Patel 2013. “Whole-Home Gesture Recognition Using Wireless Signals.” Proceedings of the 19th Annual International Conference on Mobile Computing and Networking, Miami, September 30–October 30–October 4. 10.1145/2500423.2500436
- Scholz, M., T. Riedel, M. Hock, and M. Beigl 2013. “Device-Free and Device-Bound Activity Recognition Using Radio Signal Strength.” Proceedings of the 4th Augmented Human International Conference, Stuttgart, March 7-8. 10.1145/2459236.2459254
- Sigg, S., M. Scholz, S. Shi, Y. Ji, and M. Beigl. 2014. ““Rf-Sensing of Activities from Non-Cooperative Subjects in Device-Free Recognition Systems Using Ambient and Local Signals.” IEEE Transactions on Mobile Computing 13 (4): 907–920. doi:10.1109/TMC.2013.28.
- Sun, L., S. Sen, D. Koutsonikolas, and K.-H. Kim 2015. “WiDraw: Enabling Hands-Free Drawing in the Air on Commodity WiFi Devices.” Proceedings of the 21st Annual International Conference on Mobile Computing and Networking (MobiCom ’15), Paris, September 7–11. 10.1145/2789168.2790129
- Tian, Z., J. Wang, X. Yang, and M. Zhou 2018a. “Device-Free Hand Gesture Recognition System Based on Commercial Wi-Fi Devices.” Proceedings of the 5th IEEE Conference on Ubiquitous Positioning, Indoor Navigation and Location-Based Services, UPINLBS 2018, Wuhan, March, 22–23. 10.1109/UPINLBS.2018.8559715
- Tian, Z., J. Wang, X. Yang, and M. Zhou. 2018b. “WiCatch: A Wi-Fi Based Hand Gesture Recognition System.” IEEE Access 6: 16911–16923. doi:10.1109/ACCESS.2018.2814575.
- Wang, W., A. X. Liu, M. Shahzad, K. Ling, and S. Lu. 2017. “Device-Free Human Activity Recognition Using Commercial WiFi Devices.” IEEE Journal on Selected Areas in Communications 35 (5): 1118–1131. doi:10.1109/JSAC.2017.2679658.
- Wang, Y., J. Liu, Y. Chen, M. Gruteser, J. Yang, and H. Liu 2014. “E-Eyes: Device-Free Location-Oriented Activity Identification Using Fine-Grained WiFi Signatures.”.Proceedings of the 20th annual international conference on Mobile computing and networking, Maui, September 7–11. 10.1145/2639108.2639143
- Wei, B., W. Hu, M. Yang, and C. T. Chou 2015. “Radio-Based Device-Free Activity Recognition with Radio Frequency Interference.” Proceedings of the 14th International Conference on Information Processing in Sensor Networks (IPSN ’15), Seattle, April 14–16. 10.1145/2737095.2737117
- Woyach, K., D. Puccinelli, and M. Haenggi 2006. “Sensorless Sensing in Wireless Networks: Implementation and Measurements.” Proceedings of the 4th International Symposium on Modeling and Optimization in Mobile, Ad Hoc and Wireless Networks, Boston, April 3–6. 10.1109/WIOPT.--2006.1666495
- Wu, K., J. Xiao, Y. Yi, M. Gao, and L. M. Ni 2012. “FILA: Fine-Grained Indoor Localization.” Proceedings of the IEEE INFOCOM, Orlando, March, 25–30. 10.1109/INFCOM.2012.6195606
- Xi, W., J. Zhao, X. Y. Li, K. Zhao, S. Tang, X. Liu, and Z. Jiang 2014. “Electronic Frog Eye: Counting Crowd Using WiFi.” Proceedings of IEEE INFOCOM, Toronto, April 27– May 27– May 2. 10.1109/INFOCOM.2014.6847958
- Yang, J., Y. Ge, H. Xiong, Y. Chen, and H. Liu 2010. “Performing Joint Learning for Passive Intrusion Detection in Pervasive Wireless Environments.” Proceedings of the IEEE INFOCOM, San Diego, March 14-19. 10.1109/INFCOM.2010.5462148
- Yang, Z., Z. Zhou, and Y. Liu. 2014. “From RSSI to CSI: Indoor Localization via Channel Response.” ACM Computing Surveys 46 (2): 434–442. doi:10.1145/0000000.0000000.
- Youssef, M., and M. Mah 2007. “Challenges : Device-Free Passive Localization for Wireless.” Proceedings of the 13th Annual ACM International Conference on Mobile Computing and Networking, Montreal, September 9–14. 10.1145/1287853.1287880
- Zhou, Z., Z. Yang, C. Wu, L. Shangguan, and Y. Liu. 2014. “Omnidirectional Coverage for Device-Free Passive Human Detection.” IEEE Transactions on Parallel and Distributed Systems 25 (7): 1819–1829. doi:10.1109/TPDS.2013.274.