Abstract
Drawing upon the mobile technology acceptance model (MTAM), this study addresses this conspicuous gap by identifying the necessary conditions for fostering trust and usage intention of mobile payment (m-payment) gateways. Data collected from 218 users of mobile-payment from Malaysia were analyzed using partial least squares structural equation modeling (PLS-SEM) to identify the should-have factors for perceived trust and intention to use mobile payment gateways. In addition, necessary condition analyses (NCA) are utilized to identify the must-have factors for perceived trust and intention to use mobile payment gateways. Results revealed that other factors of mobile usefulness, perceived security, and user mobility explained perceived trust except for mobile ease of use. In turn, mobile usefulness, user mobility, perceived security, mobile ease of use, and perceived trust established a positive relationship with intention to use. The NCA complemented these results showing that mobile usefulness, mobile ease of use, and user mobility qualified as necessary and sufficient conditions for perceived trust with medium-sized effect and mobile usefulness is qualified as a medium-sized necessary and sufficient condition for intention to use. This is the first few article that extends earlier literature by offering arguments on the different aspects of MTAM. By using NCA, we provide theoretical and methodological evidences, we identify which are the essential ones that enhances trust and usage.
1. Introduction
Mobile phones with intelligent-based software packages, social networking sites, and various mobile applications have taken over the global market. The development of these technologies has led to a mushroom of applications that support users to obtain goods and services and exchange information. Due to their ubiquity, localization, personalization, and convenience, mobile phones are now preferred over traditional media in carrying out transactions, such as making payments (Qin et al., Citation2018). This practice is also known as mobile payment (m-payment) gateways.
An evaluation made from the existing literature saw that most of the areas relative to the research topic have somewhat tried to be connected with increased venture creation tendency with social media (Qin et al., Citation2018), multidisciplinary usage, and the impact of mobile phones on online shopping (Flatraaker, Citation2013), the role of mobile applications and health (Pai & Alathur, Citation2019), and the negative and positive experience of the customers (Zhang et al., Citation2019). A commonality among these articles is leveraging Ooi and Tan (Citation2016) mobile technology acceptance model (MTAM). MTAM is a theoretical framework used to understand and predict individuals’ acceptance and adoption of mobile technologies (Ooi & Tan, Citation2016). It is an extension of TAM which was developed to explain users’ acceptance of information technology systems and has been widely used in various contexts including sports (Dwivedi et al., Citation2016), hospitality (Lew et al., Citation2020), and learning (Norazah Mohd & Norbayah Mohd, Citation2011). MTAM specifically focuses on mobile technologies, such as smartphones, tablets, and wearable devices, which have unique characteristics compared to traditional desktop or laptop computers. These characteristics include mobility, ubiquity, context-awareness, and personalization.
Despite this, a conspicuous research gap within MTAM is the absence of identifying necessary conditions. This gap is evident in a recent study where Richter et al. (Citation2023) mentioned that the next logical stage on expanding the MTAM is to identify the essential factors that are necessary that influence its outcomes. Besides, filling this gap would lead to a more comprehensive and nuanced understanding of the mechanisms underlying technology acceptance. By identifying necessary conditions, researchers can better explain variations in acceptance behavior across users. Additionally, understanding the necessary conditions for technology acceptance can inform the design of interventions and strategies aimed at promoting adoption and usage. In summary, addressing the research gap concerning the absence of necessary conditions within MTAM is essential for advancing both theoretical understanding and practical applications in the field of technology acceptance. From methodological perspective, the multi-analytical approach that amalgamates the use of PLS-SEM and NCA can provide a broader view in regard to the data.
Concomitantly, our review shows that several mobile technology articles have referred to the concept of necessary conditions but fell short of testing it appropriately. Most authors, such as Lew et al. (Citation2020), used structural equation modeling techniques, which, in Richter et al. (Citation2020) opinion, follows a sufficiency argument but not a necessity one. Likewise, Loh et al. (Citation2020) examined push and pull factors in examining the reasons for consumers to switch from cash to m-payment gateways but, again, did not provide more information on which are factors are necessary. A reason for the inadequate implementation of this analysis is the lack of a proper guiding framework. Another reason for such deficiency is that NCA is only made recently available (Dul et al., Citation2023). Besides, the perceived complexity and difficulties involved in the research design, data collection and analysis, and result interpretation and presentation may have hindered researchers from conducting NCA.
2. Necessary condition analysis
A necessary condition is a critical factor of an outcome (Richter et al., Citation2020). Expression of necessary condition X for outcome Y has been expressed in different literature as “X is needed for Y,” “X is critical for Y,” or “X must be present for Y to happen.” Such statements reflect necessity thinking as it infers that the outcome can achieve provided a specific condition of X is fulfilled (Dul, Citation2015; Dul, Citation2016). A necessary condition is also known by Dul (Citation2020) as a constraint, a bottleneck, or a critical factor that must be satisfied for the desired outcome to manifest. The absence of the necessary condition means a guaranteed failure, and other determinants cannot compensate for this.
In this regard, the NCA explains why the desired outcome did not materialize and, accordingly, identifies the required “must-have” factors to avert guaranteed failure (Dul, Citation2020). NCA is an approach and tool for identifying necessary conditions in data sets. NCA provides the logic and a methodological tool for finding or testing necessary conditions in existing or new data sets. NCA has been deployed in different contexts of studies, including supply chain management (Knol et al., Citation2018), tourism (Tóth et al., Citation2019), strategic management (Shahjehan et al., Citation2019), and buyer-seller relationship (van der Valk et al., Citation2016). As a result, NCA analysis is needful given its contributions to the users.
Building upon the work of Richter et al. (Citation2020), our study proceeds to develop the hypotheses using the sufficiency and necessity logic. Following this, we will establish the reliability and validity of the measurement model, before evaluating the structural model. Finally, we leverage NCA to examine the necessity effect size (d) and its associated statistical significance, before interpretating it.
Putting these together, our study takes on a crucial role as one of the first few articles identifying the necessary conditions within the MTAM. By doing so, we are responding to Tew et al. (Citation2021) calls to extend and further enhance our understanding of MTAM. We further argue that paying more attention to NCA can lead to more rigor in theoretical thinking, improve the theory-method fit in the field, and provide results of high relevance to practitioners. By combining the results from equation analysis and NCA, this study offers novel insights into the relationship between consumer motivations and intention to use by revealing which factors are indispensable for m-payment gateways implementation. The ability of this study to identify necessary conditions expands theoretical knowledge in this area underscores the significance and novelty of this study. At the same time, this study offers insights to managers about the necessary, priority and marginal conditions for the successful implementation of m-payment gateway.
3. Literature review and hypotheses development
3.1. m-payment
The recent boom of commerce activities has enhanced the development of wireless communications and technology, such as m-payment that enables payments via point of sale during the purchase of goods and services (Sahi et al., Citation2021). m-payment is utilized to facilitate payments in financial value for the exchange of goods and services via mobile device that comprises the processes of initiating, authorizing, and confirming (Thakur, Citation2013). However, the regulatory gaps lead to the concerns in the forms of privacy and financial for m-payment although mobile services do contribute to the ease to live a stress-free life for customers (Sahi et al., Citation2021; Yang et al., Citation2015). On the other hand, m-payment services providers undergone speedy sign-up, minimal usage, and low retention (Haritha, Citation2023). Consequently, the concerns from users as well as services providers worth further investigation in this study.
3.2. Mobile technology acceptance model (MTAM)
The Technology Acceptance Model (TAM) developed by Davis (Citation1989) has been widely used to study new technology adoption behavior. TAM is designed to examine consumers’ acceptance and use of technology by investigating how perceived usefulness and mobile ease of use affect attitude (Pham & Ho, Citation2015). Across different studies, the TAM has explained the acceptance of technologies in various information technology contexts (Di Pietro et al., Citation2015). Based on the study of Sahi et al. (Citation2021), TAM is the most frequently used model, in which the investigation focuses on identifying the interconnectedness of perceived usefulness, perceived ease of use, attitude, and adoption intention. Some other models, such as the (Venkatesh et al., Citation2003) Unified Theory of Acceptance and Use of Technology (UTAUT) also have been developed for the investigation of user technology adoption within the organizational context and subsequently extend to the end-users’ context in UTAUT2 (Jayarathne et al., Citation2022). UTAUT also supported moderating variables, such as gender, age, experience, and voluntariness of use to be included in the investigation (Lisana, Citation2024). Moghavvemi et al. (Citation2021) has investigated the m-payment from the merchants’ point of view. The context has been evolved from organizational to end users across various models. Most of the models are applicable to numerous technologies. Although the initial application of these theories was for technology adoption in organizations, it was found inadequate to explain the adoption of mobile-related technologies (Di Pietro et al., Citation2015). For instance, Lew et al. (Citation2020) found that existing theories could not fully elucidate the adoption of mobile-related technologies due to their unique characteristics, such as mobility, personalization, and constant connectivity. While UTAUT and its extension incorporates key constructs like performance expectancy, effort expectancy, social influence, and facilitating conditions, it may not sufficiently capture the intricacies of mobile technology adoption, such as the role of location, context, and real-time interaction (Ooi & Tan, Citation2016). Therefore, the adaptation or development of more comprehensive frameworks, specifically tailored for mobile technology adoption, became necessary.
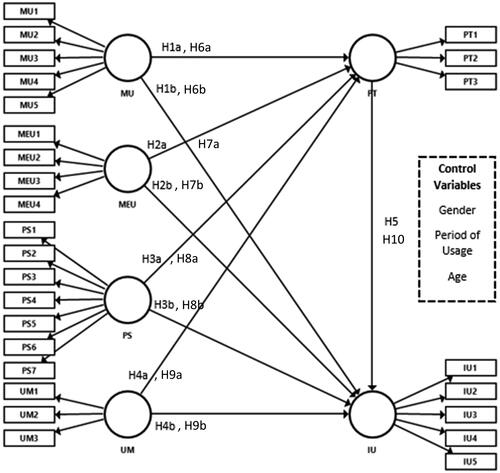
In this regard, Ooi and Tan (Citation2016) developed a new base model termed MTAM that includes relevant mobile technology constructs. The MTAM is developed to address two primary limitations of existing technological theories. First and foremost, the TAM is confined within an organizational context (Tew et al., Citation2021). Second, Ooi and Tan (Citation2016) argued that researchers who purely adopt variables from studies of other related fields, such as computing for the context of mobile technology, are not ideal in terms of applicability as many users respond differently to an electronic and mobile setting. In other words, the MTAM is tailored to explicitly “meet the needs of the mobile environment for information technology research” (Ooi & Tan, Citation2016). Different from other models, MTAM is modified to attempt to mobile context by incorporating significant emphasis on cyber security and trust (Ooi & Tan, Citation2016). Given the above arguments and our research context, it is natural that we adopted the MTAM as our theoretical framework for this study (see ).
3.3. Mobile usefulness
Mobile usefulness explains the extent to which perceived performance improvement when using mobile technology or service (Lew et al., Citation2020). It is a reflection of which the users deem that using a system can boost their performance and, therefore, positively influence their intention to use the system (Ajzen, Citation1991). Amin et al. (Citation2014) have found that mobile usefulness positively impacts perceived trust. Likewise, the study by Singh and Sinha (Citation2020) also found a positive relationship with perceived trust in the context of m-payment gateways. Putting these literatures together, we have sufficient grounds to believe that the same observations can be seen from our study, leading us to the first hypothesis:
H1a: Mobile usefulness is positively associated with perceived trust.
A payment process that is useful will eventually persuade users to use m-payment in which the advantage includes the time reduction in making payments that allows users to accomplish other activities and therefore mobile usefulness positively related to behavioral intention (Tew et al., Citation2021). The findings by Liébana-Cabanillas et al. (Citation2020) also showed that mobile usefulness positively influences behavioral intention. In their study, they explained that when the use of a particular technology helps achieve a specific outcome, it will, in turn, influence the intention to adopt (Liébana-Cabanillas et al., Citation2020). Based on the past literature, the hypothesis postulated is:
H1b: Mobile usefulness is positively associated with the intention to use m-payment gateways.
3.4. Mobile ease of use
Mobile ease of use is the level of perceived easiness when learning and using mobile technology or service that requires the least amount of effort (Lew et al., Citation2020). It is about the users’ perception of the mental effort required to perform the technical task (Ajzen & Fishbein, Citation1980). Pai et al. (Citation2018) revealed that ease of use had an impact on perceived trust. They explained that users find it tough to use m-payment gateways without a vibrant layout and ineffective navigation in the mobile interface. In addition, users may then question the ability of mobile service providers to deliver quality services (Zhou, Citation2011). Consequently, the users’ trust is affected (Pai & Alathur, Citation2019). The arguments lead to the development of the following hypothesis:
H2a: Mobile ease of use is positively associated with perceived trust.
The m-payment that is user-friendly as well as portrayed less learning effort will enhance the adoption due to these benefits, in which mobile ease of use was found positively affecting behavioral intention (Tew et al., Citation2021). Technology has the potential to improve users’ performance or assist them accomplish a goal (Abbasi, Citation2011). Various other studies demonstrate that mobile ease of use is a vital consideration in influencing the intention to use the technology (Lew et al., Citation2020; Tew et al., Citation2021; Leong et al., Citation2020). Conversely, Yadav et al. (Citation2016) found the absence of significant relationship between perceived ease of use and intention to use m-commerce. Based on the above arguments, the following hypothesis is developed:
H2b: Mobile ease of use is positively associated with the intention to use m-payment gateways.
3.5. Perceived security
The appearance of m-payment gateways changes the purchasing landscape environments (McKinsey, Citation2020). Perceived security refers to the amount of confidence a user expects the platform or channel for a transaction ought to be secure (D. Gefen et al., Citation2003). Using m-payment gateways requires users to open an account at a designated bank and receive a payment instrument linked to that account to pay merchants online (Dahlberg et al., Citation2008). Hence, it is not exaggerating that users would have more significant security concerns on m-payment gateways over other forms of payment.
However, what is relevant to building trust and accepting m-payment gateways is not the objective security of the electronic channel as a transaction medium but the users’ subjective perception (Wong et al., Citation2019). Hence, businesses not only must develop a user-friendly payment gateway, but they must also assure the public that processes are in place to resolve the possible vulnerabilities and risks. In this regard, we developed the following hypotheses reflecting our belief that an increased expectation on perceived security will improve perceived trust and intention to use.
H3a: Perceived security is positively associated with perceived trust.
The acceptance of a new payment system is relied on the control on security perception (Almaiah et al., Citation2022). Liébana-Cabanillas et al. (Citation2021) found that self-perceived security is a predictor for the m-payment systems usage intention except for the case of QR m-payment. This view is supported by Merhi et al. (Citation2019), who writes that security is the most important factor that motivates consumers in adopting m-payment gateways. Interestingly, Morosan and DeFranco (Citation2016) showed alternate results indicating that perceived security is not that critical in influencing usage intention. Given these inconsistencies, it warrant additional investigation where we hypothesized that:
H3b: Perceived security is positively associated with the intention to use m-payment gateways.
3.6. User mobility
The advancement of technology has facilitated mobility that benefits users by providing access to time-critical information and services anytime and anywhere (Anckar & D’Incau, 2002; Kim, Mirusmonov, et al., Citation2010). Combining the spatial and temporal components of mobility allow users to have access to information, services, and communication from anywhere at any time (Kim, Mirusmonov, et al., Citation2010). Such mobility is consistent with the contemporary lifestyle where people are more mobile and demand real-time information. Hence, the conveniences of allowing people to perform transactions anytime, anywhere are particularly appealing (Liébana-Cabanillas et al., Citation2021). In this regard, Au and Kauffman (Citation2008) further discovered that mobility is a crucial characteristic that enables the integration of various m-payment gateways into a single mobile platform. Studies have found that mobility is critical to improving customers’ trust (Shao et al., Citation2019). Yet, there are some inconsistencies with this argument, where Kim, Mirusmonov, et al. (Citation2010) found that mobility is not a strong predictor of trust or intention to use. Given these, it warrants additional examination with the following postulations:
H4a: User mobility is positively associated with perceived trust.
At the same time, user mobility provides seamless access to m-payment gateways regardless of their location, enabling quick and effortless transactions on the go (Kim, Mirusmonov, et al., Citation2010). Moreover, the flexibility and convenience offered by m-payment gateways align with the needs and preferences of mobile users, leading to a natural inclination toward adopting these technologies (Norazah Mohd & Norbayah Mohd, Citation2011). However, Liébana-Cabanillas et al. (Citation2014) revealed the absence of mobility on user intention. Therefore, we proposed that:
H4b: User mobility is positively associated with the intention to use m-payment gateways.
3.7. Perceived trust
Trust is another predictor that affects the adoption of new technology (Braun, Citation2013) and is a feeling of confidence derived from the integrity and trustworthiness of a different party (David Gefen et al., Citation2003). In this study, trust refers to the overall users’ perception regarding the trustworthiness of m-payment gateways. In uncertain environments, for instance, in e-commerce, trust is a significant predictor that affects consumer behavior toward a distinctive technology (Zarmpou et al., Citation2012). According to Braun (Citation2013), new communication technology’s acceptance depends on trust as computer-based communication is considered personal; therefore, user privacy protection is critical. Various studies, such as Merhi et al. (Citation2019) and Pai et al. (Citation2018) have also highlighted the importance of trust as an instrument to influence intention to use. Trust was not shown to be significant in Belanger et al. (Citation2002) when it related to user intention to use m-commerce. Due to the inconsistency of the previous findings, further investigation is deliberated with the proposed hypothesis:
H5: Perceived trust is positively associated with the intention to use m-payment gateways.
3.8. Factors in the MTAM as necessary conditions
As highlighted earlier, NCA is applied in this study to complement the analysis of PLS-SEM. By integrating sufficiency logic via PLS-SEM and necessity logic via NCA in hypothesis testing, this approach aids in identifying both necessary and significant factors influencing a specific outcome. This combined method not only enables the determination of essential variables but also provides a comprehensive understanding of their interrelationships (Dul et al., Citation2023).
MTAM is used to explain the relationships between the different predictors, such as mobile usefulness, mobile ease of use, perceived security, and the adoption of m-payment gateways (Ooi & Tan, Citation2016). Interpretations of empirical results commonly use a sufficiency logic, such as mobile usefulness is positively associated with technology adoption. The higher the mobile usefulness, the higher the technology adoption (Shao et al., Citation2019). However, authors in the field of technology acceptance likewise referred to necessities involved in technology acceptance. For instance, Holden and Rada (Citation2011) assume that usefulness is a prerequisite for technology acceptance. Usefulness needs to be in place for technology acceptance to materialize. To further illustrate, Leong et al. (Citation2020) may highlight that mobile usefulness increases usage intention. Without it, usage intention may decrease, but it does not mean that mobile usefulness is the necessary condition. In this study, we investigate the hypothesis as follow:
H6: Mobile usefulness is a necessary condition for (a) perceived trust and (b) intention to use m-payment gateways.
The same applies to other conditions, such as perceived ease of use and perceived security. Factors such as mobile ease of use, perceived security, user mobility, and perceived trust have been argued by different scholars as must-have conditions in technology adoption. Li et al. (Citation2020) offered another perspective, saying that ease of use is the most essential in e-commerce retailing among the different factors. They reasoned that consumers would leave if a mobile application cannot present its main business contents or reply to consumers’ concerns, making them lose trust in it and turn their attention to other modes of payment (Li et al., Citation2020). From this viewpoint, Li et al. (Citation2020) concluded that ease of use of mobile applications in e-commerce retailing is necessary to build consumers’ trust and use the mobile application. Thus, the hypothesis developed is:
H7: Mobile ease of use is a necessary condition for (a) perceived trust and (b) intention to use m-payment gateways.
In the same vein, Zhang et al. (Citation2019) have also highlighted that perceived security remains a fundamental and most significant concern for users to establish trust and continued usage. From this perspective, Zhang et al. (Citation2019) argued that if users perceive the system to be insecure, it is logical that users will not trust it and will not use it. In order to safeguard the security from the perspectives of customer transactions and confidence generation, a new security mechanism is necessary for a new e-payment method (Liébana-Cabanillas et al., Citation2020). The investigation of the necessary condition for perceived security is postulated in the hypothesis:
H8: Perceived security is a necessary condition for (a) perceived trust and (b) intention to use m-payment gateways.
Awa et al. (Citation2016), on the other hand, claimed that technological mobility is critical for users to build trust and embrace new technologies. One of the primary advantages of mobile technology is mobility, and this also affects consumers’ intentions for using m-commerce. Different from usefulness, mobility merely encompasses mobile technology’s benefits. To satisfy the lifestyles and needs of customers, Jamshidi et al. (Citation2018) shared that the criteria such as convenience, flexibility, and control play a critical role in fulfilling customers’ need to trust the system and be willing to adopt it. Therefore, we posted the hypothesis below:
H9: User mobility is a necessary condition for (a) perceived trust and (b) intention to use m-payment gateways.
Trust is a key element in the business world, and research in the area of marketing over the past few decades has demonstrated how essential it is for parties to possess trust in order to maintain their relationships with one another (Gefen, Citation2000). Trust refers to the willingness and desire to act according to a certain pattern and this factor will dictate how successfully new technologies are adopted (Liébana-Cabanillas et al., Citation2014). From these works, it is critical to investigate the necessary conditions for establishing perceived trust and usage intention via the following hypothesis:
H10: Perceived trust is a necessary condition for intention to use m-payment gateways.
While we can glean insights on the needed conditions, all these studies suffer from the fact that they leveraged the sufficiency-type hypothesis to determine their outcomes. Such explanations overlook the fact that a sufficient condition does not mean necessary. Given the inconsistent findings and a lack of empirical evidence, this study aims to make a significant contribution by conducting the NCA to identify which are the necessary conditions.
4. Methodology
4.1. Data collection
In our study, the respondents are m-payment users in Malaysia. We chose to employ a non-probability sampling method, specifically a snowball sampling approach as the population of m-payment users in Malaysia may not be easily accessible through traditional probability sampling methods, such as random sampling or stratified sampling. This is because m-payment users may not be evenly distributed across the population, and there is a lack of comprehensive list available for selecting participants randomly. By leveraging existing social networks and relationships within the m-payment user community, we can identify and recruit participants who may not be readily identifiable through other sampling methods.
Through the questionnaire, participants will be directed to a covering note informing that ethical approval was obtained from Human Research Ethics Office (HRE2024-0084). At the same time, this note will highlight the study background, objective, the voluntary nature of participation, anonymity and confidentiality assurance, and emphasizing the importance of honest responses. Researchers’ contact information are provided for any queries. Subsequently, participants will be prompted to give informed consent before proceeding to the initial filter question.
To ensure that only bona-fide respondents responded to the survey, we set a filter question where only m-payment gateway users are allowed to participate in the study. Out of all the data collected, only 218 responses were usable for the analysis after data cleaning (e.g., eliminating cases based straight-lining patterns through visual identification and making use of graphical method). The result of these steps led to a reliable and valid model that is appropriate for subsequent analysis.
4.2. Sample size
The sample size is determined using the power analytic technique (Cohen, Citation1988) and Kock and Hadaya (Citation2018) recommendation. Compared to the traditional “rule of thumb” method of determining sample size based on a ratio of the number of cases to predictors, power analytics is a more robust technique that is unlikely to design studies that have “insufficient power because of too few samples or excessive power because of too many samples” (Green, Citation1991, p. 509). Using G*Power, we set the medium effect size to 0.15, the alpha level to 0.05, and the power 0.8. These parameters are recommended based on Cohen (Citation1992). Besides, the review of the literature shows that these parameters have been commonly observed in different study contexts including human resources (Tan, Gim, et al., 2023), technology adoption (Leong et al., Citation2020), education (Sim et al., Citation2020), and consumer behavior (Tan, Hii, et al., 2023). This approach helped us ensure that our study would have adequate sensitivity to detect significant findings and avoid Type II errors (Cohen, Citation1988). These settings generated a minimum sample size of 85 with a maximum of four predictors.
Additionally, considering our research falls within the domain of information systems (IS) and we leveraged PLS-SEM, it is logical that we followed Kock and Hadaya (Citation2018) recommendation for sample size determination specifically tailored for PLS-SEM analyses in this research context. They proposed a sample size recommendation of 160 based on the inverse square root method, which accounts for the complexity of the model and the number of constructs included in the analysis. The final sample size 218 responses exceeded the thresholds.
4.3. Common method variance
To mitigate potential bias resulting from common method variance, we took the following steps in designing our study (see Podsakoff et al., Citation2012). First, we assured confidentiality and were motivated for honest answers. Second, we cross-checked the measurement items to prevent issues, such as double-barrelled questions. Additionally, we created a temporal separation by placing the demographic questions between the predictor and criterion variables. Finally, we also assessed the threat of common method bias by using Harman’s single factor test (Podsakoff et al., Citation2012, Podsakoff & Organ, Citation1986). This test is commonly used to assess the extent to which variance in the data can be attributed to a single underlying factor, which could indicate the presence of common method bias (Fuller et al., Citation2016). The procedure involved conducting a factor analysis on all items included in the study, regardless of their theoretical constructs (Podsakoff et al., Citation2003). If a single factor emerged that explained a large proportion of the variance, it would suggest that common method bias might be influencing the results (Podsakoff et al., Citation2003). The results revealed no “general factor” (the sum of square percentage variance was 29.4%, i.e., below the 50% benchmark value) in the data, indicating that common-method bias was not a threat to the validity of our findings.
4.4. Measurement instrument
The survey consisted of three sections. The first section was designed to collect data on the demographic background of the respondents. The second and third sections were questions regarding the predictors and outcome variables, respectively. The items used to measure our antecedent and outcome variables were taken or adapted from the literature. We used five items from Davis (Citation1989) and Leong et al. (Citation2013) to measure mobile usefulness; four items to measure mobile ease of use from Davis et al. (Citation1989) and Tan et al. (Citation2014); seven items to measure perceived security from Tan et al. (Citation2014) and Oliveira et al. (Citation2016); three items to measure user mobility from (Kim, Mirusmonov, et al., Citation2010); three items to measure perceived trust from Leong et al. (Citation2013); and finally five items to measure the intention to use from Leong et al. (Citation2013). A 7-point Likert scale ranging from 1 (fully disagree) to 7 (fully agree) was used for the rating on all scales. The survey is presented in English. It is deemed acceptable due to the linguistic diversity in Malaysia, with English as one of the languages used in the educational system (The Star Online, Citation2018). Besides, pre-testing was conducted to eliminate ambiguity in question wordings and ensure that the respondents understood the questions in the way they were designed (Memon et al., Citation2017). All items are reflective in nature.
4.5. Control variables
The inclusion of control variables is essential to minimize the possibility of confounded results that affect the model’s explanatory power (Atinc et al., Citation2011). Prior research has shown that age, length of usage, and gender may affect one’s decision to adopt m-payment gateways (Alalwan, Citation2020; Wong et al., Citation2020; Tan et al., Citation2019; Shao et al., Citation2019). In this regard, holding these variables as control variables is a natural choice in identifying if these variables may extraneously affect the relationships that are being investigated. On this note, shows that none of them displayed any significant relationships with the endogenous variables.
4.6. Analysis techniques
We used the PLS-SEM to test our hypotheses. PLS-SEM has been deployed in technology-based studies including augmented reality (Cheng et al., Citation2023), mobile technology (Leong et al., Citation2020), and generative automated intelligence (Foroughi et al., Citation2023). Besides, through PLS-SEM, we are able to perform two additional extension techniques. First, we performed predictive analysis using the PLS predict technique (Shmueli et al., Citation2016) and second, NCA through the combined usage of PLS-SEM which Richter et al. (Citation2020, p. 2245) agreed that “PLS-SEM is the correct approach to identify the determinants that can increase an outcome”.
In other words, the interpretation of findings from a PLS-SEM model follows a sufficiency logic, answering hypotheses that take the form “mobile usefulness is positively associated with intention to use.” Hence, using PLS-SEM, we can determine the should-have factors to increase trust and usage intention (see Richter et al., Citation2020). We obtained the PLS-SEM results using the following settings in all steps of the analysis: path weighting scheme, 300 iterations, and stop-criterion 0.0000001. We determined significance by applying the bootstrapping procedure (see Henseler et al., Citation2009, Chin, Citation1998) with the following settings: 5000 bootstrapping subsamples, as many observations per subsample as in the original sample, and the no sign change option.
Furthermore, we applied NCA using SmartPLS version 4 (Bönningstedt, Germany), which we argued that an antecedent is necessary but not sufficient. Without the necessary antecedent (for instance, mobile ease of use), there is guaranteed failure (for instance, no usage intention). A necessary cause is a constraint that must be managed to allow the desired outcome to exist. The absence of a necessary condition cannot be compensated. Hence in its absence, there is no outcome (Dul, Citation2016). As such, the NCA provides a valuable additional understanding of the critical role of mobile usefulness, mobile ease of use, perceived security, and user mobility for perceived trust and intention to use, and of perceived trust for intention to use. It assesses the must-have or bottleneck factors for perceived trust and usage intention. We obtained the NCA results using the following settings (Richter et al., Citation2020): ceiling envelopment–free disposal hull ceiling technique (ce-fdh) ceiling line, which is the preferred technique due to the scaling of our variables (see Dul, Citation2020), and 10,000 permutations to reflect a balance between computational efficiency and statistical robustness (Dul et al., Citation2018). Excessively large numbers of permutations can lead to computational burdens and may not yield substantial improvements in results beyond a certain point (Richter et al., Citation2020). By selecting 10,000 permutations, the analysis aims to strike a balance between achieving sufficient statistical power and maintaining computational feasibility (Dul et al., Citation2023).
5. Analysis and findings
5.1. Respondents’ profiles
provides an overview of the profiles of our respondents. Of 63.8% of female respondents, while 36.2% of respondents were male. Most of our respondents were aged between 21 and 25 years. This is a young sample that represents the key target population where many of the young population in Malaysia are digital natives (WARC, Citation2019). Most of the respondents had less than three years of experience using the m-payment gateway.
Table 1. Profile of respondents.
5.2. Evaluation of measurements
We first evaluated the reliability and validity of measurement models using quality criteria defined in a PLS-SEM context relevant to both analyses, PLS-SEM and NCA (Richter et al., Citation2020). Following Hair et al. (Citation2019), all our measurement models met the relevant quality criteria defined in a PLS-SEM context as given in (loadings > 0.708, average variance extracted (AVE) > 0.5, and composite reliability > 0.7). Two items had loadings below 0.7 yet above 0.5 (MPT3 with the loading of 0.561; MUM with the loading of 0.678) are retained as all AVE and CR values met the thresholds (Hair et al., Citation2017).
Table 2. Assessment of measurement model.
Discriminant validity has been achieved as all measures met the heterotrait-monotrait (HTMT) assessment criteria of not exceeding the threshold value of 0.85 (Hair et al., Citation2017) and none of the HTMT confidence intervals included a value of 1 ().
Table 3. Discriminant validity (HTMT).
5.3. Structural model results from PLS-SEM
shows the results for the structural model. The variance inflation factor (VIF) score is less than 3.3 indicating that multicollinearity is not an issue in this model. From the results, mobile usefulness is positively related to perceived trust (H1a. β = 0.358, p < 0.001) and intention to use (H1b. β = 0.345, p < 0.001). At the same time, the relationship between mobile ease of use and perceived trust is insignificant (H2a. β = −0.074, p = 0.155), but not with intention to use (H2b. β = 0.152, p < 0.05). Similar to mobile usefulness, perceived security establish significant relationships with perceived trust (H3a. β = 0.311, p < 0.001) and intention to use (H3b. β = −0.147, p < 0.01). Likewise, user mobility positively influence perceived trust (H4a. β = 0.165, p < 0.05) and intention to use (H4b. β = 0.168, p < 0.01). Finally, perceived trust showed a positive relationship with intention to use (H5. β = 0.175, p < 0.01). Hence, H1a, H1b, H2b, H3a, H3b, H4a, H4b, and H5 are supported.
Table 4. Assessment of structural model.
We further analyzed the effect sizes (f2), coefficient of determination (R2), and predictive relevance of the model.
Following Cohen (Citation1992), results in Tabe 4 revealed that most of the various predictors demonstrate a f2 in producing the R2 for perceived trust and intention to use.
We finally assessed the predictive relevance of our model using the PLS predict. The results in showed that the root mean square error (RMSE) values of intention to use are lower than corresponding value from the linear model. This provides substantial evidence for the strong predictive capabilities of the models when forecasting the outcomes of new cases (Sarstedt & Danks, Citation2021).
5.4. NCA results
shows the estimated effect sizes by means of NCA and the p values, indicating their significance. In interpreting the effect sizes, we follow Dul (Citation2020) who offered the following benchmarks: 0 < d < 0.1 indicates a small effect, 0.1 ≤ d < 0.3 a medium effect, 0.3 ≤ d < 0.5 a large effect, and d ≥ 0.5 a very large effect.
Table 5. NCA results.
For the outcome of perceived trust, other than perceived security, all other constructs of mobile usefulness (d = 0.272; p < 0.001), mobile ease of use (d = 0.163; p < 0.05), and user mobility (d = 0.136; p < 0.01) qualified as a medium-sized necessary condition. Thus, H6a, H7a, and H9a are supported.
For intention to use, we found one necessary condition: mobile usefulness which qualified as a medium-sized necessary condition for intention to use (d = 0.252; p < 0.001). The other four predictors did not qualify as necessary conditions following an alpha level of 5 percent. Hence, H6b is supported, while H7b, H8b, H9b, and H10 are not supported.
6. Discussion
To accomplish the objective of identifying necessary conditions in MTAM, our work leverages both PLS-SEM and NCA, where we offer several findings. First, the results indicated that mobile usefulness, mobile ease of use, and user mobility are necessary conditions for companies to establish perceived trust in their m-payment gateways. These results are consistent with previous studies, such as Zhang et al. (Citation2019), Leong et al. (Citation2020), and Tan et al. (Citation2019). A probable reason is the growing usage of mobile phones as a large part of our everyday life.
Besides a portable storage device, a mobile phone is also a mobile bank and a social network hub. Mobility free users from temporal and spatial constraints that enable them to conduct transactions over mobile phones anytime and anywhere (Kim, Mirusmonov, et al., Citation2010). Mobile phones provide users with more opportunities for users to use m-payment gateways and increase their number of operations. Furthermore, mobile phones supported users to complete their tasks faster, enhancing their effectiveness and efficiency, in turn increasing their perception of trust. In the same vein, the increased number of functions to a mobile phone has made users realize how important it is to protect the information stored within it. Taken together, mobile security, along with other latent variables of mobile usefulness and user mobility, are critical constructs toward building trust in m-payment gateways.
However, our results show that perceived security is not a necessary condition toward fostering perceived trust. A plausible reason is the profile of the respondents. As highlighted earlier, participants of this study are young individuals. These individuals are familiar with new technologies and would have relatively lesser difficulties adapting to them. This argument aligns with Zhou et al. (Citation2013) where they found younger users perceived mobility (such as internet access and the connection between mobile phones and other devices) as much more critical. Besides, in today’s cybersecurity landscape, the widespread adoption of advanced encryption technologies, and secure authentication methods has bolstered confidence in the security of m-payment platforms among users. Additionally, the convenience and efficiency offered by these platforms often outweigh perceived security concerns for many users, especially when compared to traditional payment methods. Furthermore, the increasing normalization of digital transactions across various aspects of daily life has led to a gradual acceptance of certain levels of risk associated with m-payments, with users prioritizing convenience and accessibility over absolute security.
NCA also reveals that among the different exogenous constructs, only mobile usefulness is a must-have condition to increase usage of m-payment gateways. Businesses should focus on this condition of providing better m-payment gateways to the users. After all, the intention to use information technology is predicated, to a large degree, on the usefulness of the system (Davis, Citation1989). Our results corroborated with other studies, such as Tew et al. (Citation2021), Buabeng-Andoh (Citation2018), Sathye et al. (Citation2018), Kim, Mirusmonov, et al. (Citation2010), and Kim, Tao, et al. (Citation2010), demonstrating that for users to continue to use m-payment gateways, the primary emphasis would be to design in delivering value to them. The interpretation of the findings are summarized in and .
Table 6. Overview of findings for PT.
Table 7. Overview of findings for IU.
7. Implications
7.1. Theoretical implications
This study applies a theoretical necessity model to an m-payment context. The findings are new with the NCA approach because existing knowledge in m-payment gateways is general and based mainly on sufficiency-based research. In fact, Jain et al. (Citation2022) highlighted that NCA has been incorporated into the field of m-payment gateways as a novel approach to empirically analyze data. Advocates of NCA anticipate its increasing significance as a supplementary method to traditional approaches, aiming to gain deeper insights into causal relationships within comparative analyses (Dul et al., Citation2023). Additionally, prominent journals, such as International Journal of Consumer Studies and Review of Managerial Sciences have envisioned the growing utilization of NCA in conjunction with established traditional methods (Dul et al., Citation2023; Jain et al., Citation2022).
Authors, such as Kim, Mirusmonov, et al. (Citation2010) these seem to allude to necessity thinking and eventually conduct and present results based on sufficiency-based models. In this regard, we have made a methodological contribution in showing that some relationships are better analyzed using a necessary perspective rather than a probabilistic perspective.
Additionally, we have extended the MTAM literature by recognizing that not all factors are necessary. In other words, some factors are sufficient but not necessary, and others are necessary but not sufficient. For instance, to achieve perceived trust, we found that there needs to be a certain minimum level of mobile ease of use to manifest perceived trust. However, any further increase beyond the minimum would not increase the manifestation of the outcome. More importantly, we also identify factors in the MTAM literature that are relevant determinants and necessary conditions for trust and intention to use. This can be seen in mobile usefulness where the manifestation of perceived trust would require mobile usefulness and a further increase in it will increase perceived trust. Similarly, we found several situations where the factors are not relevant determinants but constitute necessary conditions. This outcome is a relevant complement to advance our understanding of the factors involved in MTAM. Hence, the contribution of this study is the additional insights, which are not limited to the significant determinant for intention to adopt, but the necessary and sufficient conditions. In sum, the necessity perspective further contributes to advancing the theoretical arguments around the MTAM by creating a stronger fit between the theoretical arguments in the field and the empirical evidence.
7.2. Managerial implications
The findings of this study offer valuable insights for m-payment gateway providers, with specific implications for enhancing perceived trust and increasing intention to use. First, our research identifies three primary conditions driving perceived trust: mobile ease of use, mobile usefulness, and user mobility. Among these, mobile usefulness emerges as a necessary condition for increasing intention to use m-payment gateways.
Therefore, m-payment gateway providers should prioritize efforts to ensure the stability and quality of their systems. However, the technical complexity of upgrading systems and ensuring stability poses a significant hurdle, especially given the rapid pace of technological advancements. Moreover, ensuring robust security measures to protect users’ financial information is essential for maintaining trust, but balancing security requirements with user convenience can be challenging. Hence, there is a need to provide training to ensure that manpower is kept updated with the relevant knowledge. At the same time, periodical checks and updates are essential to maintain system stability and prevent disruptions that could erode trust.
Additionally, businesses should actively engage users in the design and testing of their platforms to ensure that the services provided are perceived as useful and valuable. This is essential as user adoption and resistance could impede progress, as users may resist changes to the platform, particularly if they are accustomed to a certain interface or workflow. Regulatory compliance adds another layer of complexity, as m-payment gateway providers must adhere to a complex set of data protection and financial regulations. Concrete steps to address these challenges include conducting prototype testing and involving users in the design process to gather feedback and insights. This user-centric approach can help identify areas for improvement and ensure that the platform meets the evolving needs and expectations of users.
Furthermore, in cases where performance falls below desired levels, providers should focus on strengthening the necessary conditions identified in our study. This may involve allocating resources to address specific pain points or bottlenecks that inhibit user trust and adoption. Conversely, organizations that have over-invested in certain conditions may need to reassess their priorities and reallocate resources to more critical areas. By focusing on addressing the essential conditions for trust and intention to use, providers can optimize their efforts and resources to achieve the desired outcomes effectively.
8. Limitations and future directions
Like any study, there are limitations in this piece of work that future researchers may want to take note of. First, the scope and size of this study are limited to only one country – Malaysia. While the sample size has met the required number needed for analysis, a larger sample size from that population is often desired for statistical inference (van der Valk et al., Citation2016). Likewise, replications using different samples from other countries are encouraged, as different samples may yield different results given the differences in culture. Besides, using different samples, especially considering different socio-economic factors could enhances the confidence in the necessary conditions that were found and enabled further demarcation of the domain in which the conditions apply. Despite we have controlled these variables that demonstrated no impact to the model; we cannot preclude the fact that difference in such factors, such as income levels, education, and occupation might shape users’ perceptions and behaviors.
Furthermore, future research could use the NCA approach to perform comparative studies across different types of users (e.g., lead users and lagged users, older users, younger users, and users from developed and developing countries) and different forms of m-payment gateways. The results could further identify whether different success factors are necessary and how they increase operational performance and continued usage intention. Finally, cross-sectional data limits our ability to establish causation or capture changes over time. This design constraint necessitates caution in interpreting the findings, as it precludes the examination of temporal relationships between variables. Future research should consider adopting longitudinal studies to address this limitation and capturing changes in user perceptions over time as well as identifying causal relationships. It will provide a more robust understanding of the dynamics underlying trust and intention to use m-payment gateways.
9. Conclusions
M-payments are experiencing rapid growth as consumers increasingly use wireless devices as part of modern dynamic lifestyles. This study demonstrates how NCA complements associations between variables that can help in advancing theorization and identifying underlying mechanisms that fit mobile technology acceptance phenomena in general and in specific contexts. It can assist in reducing the complexity that is involved in mobile technology acceptance by identifying the critical factors that must be in place not to fail.
Disclosure statement
The authors report there are no competing interests to declare.
Data availability statement
Data would be made available upon reasonable request from the corresponding author.
Additional information
Notes on contributors
Kim-Lim Tan
Kim-Lim Tan is a lecturer at JCUS Business School, James Cook University. His research interest lies primarily in contemporary human resource issues and consumer behavior across different contexts, such as technology adoption, hospitality, and tourism. More information about Kim-Lim: https://research.jcu.edu.au/portfolio/kimlim.tan/
Choi-Meng Leong
Choi-Meng Leong is an Assistant Professor at the Graduate Business School, UCSI University. She holds a PhD from Universiti Malaysia Sarawak. Her research interests are in behavioral studies including behavioral finance and consumer behavioral. Her works have appeared in Asia Pacific Journal of Marketing and Logistics and Young Consumers.
Nicole Franziska Richter
Nicole Franziska Richter is a Full Professor at the University of Southern Denmark. Her research focuses on international management, emphasizing cross-cultural and diversity management. She is one of the leading experts in partial least squares- structural equation modeling and necessary condition analysis. More information about Nicole: https://portal.findresearcher.sdu.dk/en/persons/nicole
References
- Abbasi, M. S. (2011). Culture, demography and individuals’ technology acceptance behaviour: A PLS based structural evaluation of an extended model of technology acceptance in South-Asian country context (pp. 397–397). Brunel University.
- Ajzen, I. (1991). The theory of planned behavior. Organizational Behavior and Human Decision Processes, 50(2), 179–211. https://doi.org/10.1016/0749-5978(91)90020-T
- Ajzen, I., & Fishbein, M. (1980). Understanding attitudes and predicting social behavior. Prentice-Hall.
- Alalwan, A. A. (2020). Mobile food ordering apps: An empirical study of the factors affecting customer e-satisfaction and continued intention to reuse. International Journal of Information Management, 50, 28–44. https://doi.org/10.1016/j.ijinfomgt.2019.04.008
- Almaiah, M. A., Al-Rahmi, A., Alturise, F., Hassan, L., Lutfi, A., Alrawad, M., Alkhalaf, S., Al-Rahmi, W. M., Al-Sharaieh, S., & Aldhyani, T. H. H. (2022). Investigating the effect of perceived security, perceived trust, and information quality on mobile payment usage through near-field communication (NFC) in Saudi Arabia. Electronics, 11(23), 3926. https://doi.org/10.3390/electronics11233926
- Amin, M., Rezaei, S., & Abolghasemi, M. (2014). User satisfaction with mobile websites: The impact of perceived usefulness (PU), perceived ease of use (PEOU) and trust. Nankai Business Review International, 5(3), 258–274. https://doi.org/10.1108/NBRI-01-2014-0005
- Anckar, B., & D'Incau, D. (2002). Value creation in mobile commerce: Findings from a consumer survey. The Journal of Information Technology Theory and Application, 4(1), 43–65.
- Atinc, G., Simmering, M. J., & Kroll, M. J. (2011). Control variable use and reporting in macro and micro management research. Organizational Research Methods, 15(1), 57–74. https://doi.org/10.1177/1094428110397773
- Au, Y. A., & Kauffman, R. J. (2008). The economics of mobile payments: Understanding stakeholder issues for an emerging financial technology application. Electronic Commerce Research and Applications, 7(2), 141–164. https://doi.org/10.1016/j.elerap.2006.12.004
- Awa, H. O., Uko, J. P., & Ukoha, O. (2016). An empirical study of some critical adoption factors of ERP software. International Journal of Human–Computer Interaction, 33(8), 609–622. https://doi.org/10.1080/10447318.2016.1265828
- Belanger, F., Hiller, J. S., & Smith, W. J. (2002). Trustworthiness in electronic commerce: The role of privacy, security, and site attributes. The Journal of Strategic Information Systems, 11(3–4), 245–270. https://doi.org/10.1016/S0963-8687(02)00018-5
- Braun, M. T. (2013). Obstacles to social networking website use among older adults. Computers in Human Behavior, 29(3), 673–680. https://doi.org/10.1016/j.chb.2012.12.004
- Buabeng-Andoh, C. (2018). Predicting students’ intention to adopt mobile learning. Journal of Research in Innovative Teaching & Learning, 11(2), 178–191. https://doi.org/10.1108/JRIT-03-2017-0004
- Cheng, A., Ma, D., Pan, Y., & Qian, H. (2023). Enhancing museum visiting experience: investigating the relationships between augmented reality quality, immersion, and TAM using PLS-SEM. International Journal of Human–Computer Interaction, 1–12. https://doi.org/10.1080/10447318.2023.2227832
- Chin, W. W. (1998). The partial least squares approach to structural equation modeling. In G.A. Marcoulides (Ed.), Modern methods for business research (pp. 295–336). Lawrence Erlbaum Associates Publishers.
- Cohen, J. (1988). Statistical power analysis for the behavioral siences (2nd ed.), Lawrence Erlbaum Associates.
- Cohen, J. (1992). A power primer. Psychological Bulletin, 112(1), 155–159. https://doi.org/10.1037//0033-2909.112.1.155
- Dahlberg, T., Mallat, N., Ondrus, J., & Zmijewska, A. (2008). Past, present and future of mobile payments research: A literature review. Electronic Commerce Research and Applications, 7(2), 165–181. https://doi.org/10.1016/j.elerap.2007.02.001
- Davis, F. D. (1989). Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Quarterly, 13(3), 319–340. https://doi.org/10.2307/249008
- Davis, F. D., Bagozzi, R. P., & Warshaw, P. R. (1989). User acceptance of computer technology: A comparison of two theoretical models. Management Science, 35(8), 982–1003. https://doi.org/10.1287/mnsc.35.8.982
- Di Pietro, L., Guglielmetti Mugion, R., Mattia, G., Renzi, M. F., & Toni, M. (2015). The Integrated Model on Mobile Payment Acceptance (IMMPA): An empirical application to public transport. Transportation Research Part C: Emerging Technologies, 56, 463–479. https://doi.org/10.1016/j.trc.2015.05.001
- Dul, J. (2015). Necessary condition analysis (NCA). Organizational Research Methods, 19(1), 10–52. https://doi.org/10.1177/1094428115584005
- Dul, J. (2016). Necessary condition analysis (NCA): Logic and methodology of "necessary but not sufficient" causality. Organizational Research Methods, 19(1), 10–52. https://doi.org/10.1177/1094428115584005
- Dul, J. (2020). Conducting Necessary Condition Analysis., Sage.
- Dul, J., Hauff, S., & Bouncken, R. B. (2023). Necessary condition analysis (NCA): review of research topics and guidelines for good practice. Review of Managerial Science, 17(2), 683–714. https://doi.org/10.1007/s11846-023-00628-x
- Dul, J., van der Laan, E., & Kuik, R. (2018). A statistical significance test for necessary condition analysis. Organizational Research Methods, 23(2), 385–395. https://doi.org/10.1177/1094428118795272
- Dwivedi, Y. K., Shareef, M. A., Simintiras, A. C., Lal, B., & Weerakkody, V. (2016). A generalised adoption model for services: A cross-country comparison of mobile health (m-health). Government Information Quarterly, 33(1), 174–187. https://doi.org/10.1016/j.giq.2015.06.003
- Flatraaker, D. I. (2013). Mobile payments changing the landscape of retail banking: Hype or reality. Journal of Payments Strategy & Systems, 7(2), 150–158.
- Foroughi, B., Senali, M. G., Iranmanesh, M., Khanfar, A., Ghobakhloo, M., Annamalai, N., & Naghmeh-Abbaspour, B. (2023). Determinants of intention to use ChatGPT for educational purposes: Findings from PLS-SEM and fsQCA. International Journal of Human–Computer Interaction, 1–20. https://doi.org/10.1080/10447318.2023.2226495
- Fuller, C. M., Simmering, M. J., Atinc, G., Atinc, Y., & Babin, B. J. (2016). Common methods variance detection in business research. Journal of Business Research, 69(8), 3192–3198. https://doi.org/10.1016/j.jbusres.2015.12.008
- Gefen, D. (2000). E-commerce: The role of familiarity and trust. Omega, 28(6), 725–737. https://doi.org/10.1016/S0305-0483(00)00021-9
- Gefen, D., Karahanna, E., & Straub, D. (2003). Trust and TAM in online shopping: An integrated model. MIS Quarterly, 27(1), 51–90. https://doi.org/10.2307/30036519
- Gefen, D., Karahanna, E., & Straub, D.W. (2003). Trust and TAM in online shopping: An integrated model. MIS Quarterly, 27(1), 51–90. https://doi.org/10.2307/30036519
- Green, S. B. (1991). How many subjects does it take to do A regression analysis. Multivariate Behavioral Research, 26(3), 499–510. https://doi.org/10.1207/s15327906mbr2603_7
- Hair, J. F., Hult, T. M., Ringle, C. M., & Sarstedt, M. (2017). A primer on partial least squares structural equations modeling (PLS-SEM). Sage.
- Hair, J. F., Risher, J. J., Sarstedt, M., Ringle, C. M., Svensson, G., & Svensson, G. (2019). When to use and how to report the results of PLS-SEM. European Business Review, 31(1), 2–24. https://doi.org/10.1108/EBR-11-2018-0203
- Haritha, P. H. (2023). Mobile payment service adoption: Understanding customers for an application of emerging financial technology. Information & Computer Security, 31(2), 145–171. https://doi.org/10.1108/ICS-04-2022-0058
- Henseler, J., Ringle, C. M., & Sinkovics, R. R. (2009). The use of partial least squares path modeling in international marketing. In R.R. Sinkovics & P.N. Ghauri (Eds.), Advances in international marketing (pp. 277–320). Emerald Group Publishing Limited.
- Holden, H., & Rada, R. (2011). Understanding the influence of perceived usability and technology self-efficacy on teachers’ technology acceptance. Journal of Research on Technology in Education, 43(4), 343–367. https://doi.org/10.1080/15391523.2011.10782576
- Jain, N. K., Kaushik, K., & Sharma, A. (2022). What drives customers toward proximity payment services? An integrated theory of planned behavior perspective. International Journal of Consumer Studies, 47(3), 1095–1111. https://doi.org/10.1111/ijcs.12890
- Jamshidi, D., Keshavarz, Y., Kazemi, F., & Mohammadian, M. (2018). Mobile banking behavior and flow experience. International Journal of Social Economics, 45(1), 57–81. https://doi.org/10.1108/IJSE-10-2016-0283
- Jayarathne, P. G. S. A., Chathuranga, B. T. K., Dewasiri, N. J., & Rana, S. (2022). Motives of mobile payment adoption during COVID-19 pandemic in Sri Lanka: A holistic approach of both customers’ and retailers’ perspectives. South Asian Journal of Marketing, 4(1), 51–73. https://doi.org/10.1108/SAJM-03-2022-0013
- Kim, C., Mirusmonov, M., & Lee, I. (2010). An empirical examination of factors influencing the intention to use mobile payment. Computers in Human Behavior, 26(3), 310–322. https://doi.org/10.1016/j.chb.2009.10.013
- Kim, C., Tao, W., Shin, N., & Kim, K. S. (2010). An empirical study of customers’ perceptions of security and trust in e-payment systems. Electronic Commerce Research and Applications, 9(1), 84–95. https://doi.org/10.1016/j.elerap.2009.04.014
- Knol, W. H., Slomp, J., Schouteten, R. L. J., & Lauche, K. (2018). Implementing lean practices in manufacturing SMEs: Testing ‘critical success factors’ using Necessary Condition Analysis. International Journal of Production Research, 56(11), 3955–3973. https://doi.org/10.1080/00207543.2017.1419583
- Kock, N., & Hadaya, P. (2018). Minimum sample size estimation in PLS-SEM: The inverse square root and gamma-exponential methods. Information Systems Journal, 28(1), 227–261. https://doi.org/10.1111/isj.12131
- Leong, C. M., Tan, K. L., Puah, C. H., & Chong, S. M. (2020). Predicting mobile network operators users m-payment intention. European Business Review, 33(1), 104–126. https://doi.org/10.1108/EBR-10-2019-0263
- Leong, L. Y., Hew, T. S., Tan, G. W. H., & Ooi, K. B. (2013). Predicting the determinants of the NFC-enabled mobile credit card acceptance: A neural networks approach. Expert Systems with Applications, 40(14), 5604–5620. https://doi.org/10.1016/j.eswa.2013.04.018
- Lew, S., Tan, G. W., Loh, X. M., Hew, J. J., & Ooi, K. B. (2020). The disruptive mobile wallet in the hospitality industry: An extended mobile technology acceptance model. Technology in Society, 63, 101430. https://doi.org/10.1016/j.techsoc.2020.101430
- Li, X., Zhao, X., Xu, W., & Pu, W. (2020). Measuring ease of use of mobile applications in e-commerce retailing from the perspective of consumer online shopping behaviour patterns. Journal of Retailing and Consumer Services, 55, 102093. https://doi.org/10.1016/j.jretconser.2020.102093
- Liébana-Cabanillas, F., Japutra, A., Molinillo, S., Singh, N., & Sinha, N. (2020). Assessment of mobile technology use in the emerging market: Analyzing intention to use m-payment services in India. Telecommunications Policy, 44(9), 102009. https://doi.org/10.1016/j.telpol.2020.102009
- Liébana-Cabanillas, F., Molinillo, S., & Japutra, A. (2021). Exploring the Determinants of Intention to Use P2P Mobile Payment in Spain. Information Systems Management, 38(2), 165–180. https://doi.org/10.1080/10580530.2020.1818897
- Liébana-Cabanillas, F. J., Sánchez-Fernández, J., & Muñoz-Leiva, F. (2014). Antecedents of the adoption of the new mobile payment systems: The moderating effect of age. Computers in Human Behavior, 35, 464–478. https://doi.org/10.1016/j.chb.2014.03.022
- Lisana, L. (2024). Understanding the key drivers in using mobile payment among Generation Z. Journal of Science and Technology Policy Management, 15(1), 122–141. https://doi.org/10.1108/JSTPM-08-2021-0118
- Loh, X. M., Lee, V. H., Tan, G. W. H., Ooi, K. B., & Dwivedi, Y. K. (2020). Switching from cash to mobile payment: What’s the hold-up? Internet Research, 31(1), 376–399. https://doi.org/10.1108/INTR-04-2020-0175
- McKinsey (2020). Perspectives on retail and consumer goods. www.,mckinsey.com (accessed 21 June 2021).
- Memon, M. A., Ting, H., Ramayah, T., Chuah, F., & Cheah, J.-H. (2017). A review of the methodological misconceptions and guidelines related to the application of structural equation modeling: A malaysian scenario. Journal of Applied Structural Equation Modeling, 1(1), i–xiii. https://doi.org/10.47263/JASEM.1(1)01
- Merhi, M., Hone, K., & Tarhini, A. (2019). A cross-cultural study of the intention to use mobile banking between Lebanese and British consumers: Extending UTAUT2 with security, privacy and trust. Technology in Society, 59, 101151. https://doi.org/10.1016/j.techsoc.2019.101151
- Moghavvemi, S., Mei, T. X., Phoong, S. W., & Phoong, S. Y. (2021). Drivers and barriers of mobile payment adoption: Malaysian merchants’ perspective. Journal of Retailing and Consumer Services, 59, 102364. https://doi.org/10.1016/j.jretconser.2020.102364
- Morosan, C., & DeFranco, A. (2016). It’s about time: Revisiting UTAUT2 to examine consumers’ intentions to use NFC mobile payments in hotels. International Journal of Hospitality Management, 53, 17–29. https://doi.org/10.1016/j.ijhm.2015.11.003
- Norazah Mohd, S., & Norbayah Mohd, S. (2011). User’ behaviour towards ubiquitos M-learning. The Turkish Online Journal of Distance Education, 12(3), 118–129.
- Oliveira, T., Thomas, M., Baptista, G., & Campos, F. (2016). Mobile payment: Understanding the determinants of customer adoption and intention to recommend the technology. Computers in Human Behavior, 61, 404–414. https://doi.org/10.1016/j.chb.2016.03.030
- Ooi, K. B., & Tan, G. W. H. (2016). Mobile technology acceptance model: An investigation using mobile users to explore smartphone credit card. Expert Systems with Applications, 59, 33–46. https://doi.org/10.1016/j.eswa.2016.04.015
- Pai, C. K., Wang, T. W., Chen, S. H., & Cai, K. Y. (2018). Empirical study on Chinese tourists’ perceived trust and intention to use biometric technology. Asia Pacific Journal of Tourism Research, 23(9), 880–895. https://doi.org/10.1080/10941665.2018.1499544
- Pai, R. R., & Alathur, S. (2019). Determinants of individuals’ intention to use mobile health: Insights from India. Transforming Government: People, Process and Policy, 13(3–4), 306–326. https://doi.org/10.1108/TG-04-2019-0027
- Pham, T. T. T., & Ho, J. C. (2015). The effects of product-related, personal-related factors and attractiveness of alternatives on consumer adoption of NFC-based mobile payments. Technology in Society, 43, 159–172. https://doi.org/10.1016/j.techsoc.2015.05.004
- Podsakoff, P. M., MacKenzie, S. B., Lee, J. Y. Y., & Podsakoff, N. P. (2003). Common method biases in behavioral research: A critical review of the literature and recommended remedies. The Journal of Applied Psychology, 88(5), 879–903. https://doi.org/10.1037/0021-9010.88.5.879
- Podsakoff, P. M., MacKenzie, S. B., & Podsakoff, N. P. (2012). Sources of method bias in social science research and recommendations on how to control it. Annual Review of Psychology, 63(1), 539–569. https://doi.org/10.1146/annurev-psych-120710-100452
- Podsakoff, P. M., & Organ, D. W. (1986). Self-reports in organizational research: Problems and prospects. Journal of Management, 12(4), 531–544. https://doi.org/10.1177/014920638601200408
- Qin, L., Kim, Y., & Tan, X. (2018). Understanding the intention of using mobile social networking apps across cultures. International Journal of Human–Computer Interaction, 34(12), 1183–1193. https://doi.org/10.1080/10447318.2018.1428262
- Richter, N. F., Hauff, S., Kolev, A. E., & Schubring, S. (2023). Dataset on an extended technology acceptance model: A combined application of PLS-SEM and NCA. Data in Brief, 48, 109190. https://doi.org/10.1016/j.dib.2023.109190
- Richter, N. F., Schubring, S., Hauff, S., Ringle, C. M., & Sarstedt, M. (2020). When predictors of outcomes are necessary: Guidelines for the combined use of PLS-SEM and NCA. Industrial Management & Data Systems, 120(12), 2243–2267. https://doi.org/10.1108/IMDS-11-2019-0638
- Sahi, A. M., Khalid, H., Abbas, A. F., & Khatib, S. F. A. (2021). The evolving research of customer adoption of digital payment: Learning from content and statistical analysis of the literature. Journal of Open Innovation: Technology, Market, and Complexity, 7(4), 230. https://doi.org/10.3390/joitmc7040230
- Sarstedt, M., & Danks, N. P. (2021). Prediction in HRM research–A gap between rhetoric and reality. Human Resource Management Journal, 32(2), 485–513. https://doi.org/10.1111/1748-8583.12400
- Sathye, S., Prasad, B., Sharma, D., Sharma, P., & Sathye, M. (2018). Factors influencing the intention to use of mobile value-added services by women-owned microenterprises in Fiji. The Electronic Journal of Information Systems in Developing Countries, 84(2), e12016. https://doi.org/10.1002/isd2.12016
- Shahjehan, A., Afsar, B., & Shah, S. I. (2019). Is organizational commitment-job satisfaction relationship necessary for organizational commitment-citizenship behavior relationships? A Meta-Analytical Necessary Condition Analysis. Economic Research-Ekonomska Istraživanja, 32(1), 2657–2679. https://doi.org/10.1080/1331677X.2019.1653784
- Shao, Z., Zhang, L., Li, X., & Guo, Y. (2019). Antecedents of trust and continuance intention in mobile payment platforms: The moderating effect of gender. Electronic Commerce Research and Applications, 33, 100823. https://doi.org/10.1016/j.elerap.2018.100823
- Shmueli, G., Ray, S., Velasquez Estrada, J. M., & Chatla, S. B. (2016). The elephant in the room: Predictive performance of PLS models. Journal of Business Research, 69(10), 4552–4564. https://doi.org/10.1016/j.jbusres.2016.03.049
- Sim, A. K. S., Tan, K. L., Sia, J. K. M., & Hii, I. S. H. (2020). Students’ choice of international branch campus in Malaysia: A gender comparative study. International Journal of Educational Management, 35(1), 87–107. https://doi.org/10.1108/IJEM-01-2020-0027
- Singh, N., & Sinha, N. (2020). How perceived trust mediates merchant’s intention to use a mobile wallet technology. Journal of Retailing and Consumer Services, 52, 101894. https://doi.org/10.1016/j.jretconser.2019.101894
- Tan, G. W. H., Ooi, K. B., Chong, S. C., & Hew, T. S. (2014). NFC mobile credit card: The next frontier of mobile payment? Telematics and Informatics, 31(2), 292–307. https://doi.org/10.1016/j.tele.2013.06.002
- Tan, K. L., Gim, G., Hii, I., & Zhu, W. (2023). STARA fight or flight: A two-wave time-lagged study of challenge and hindrance appraisal of STARA awareness on basic psychological needs and individual competitiveness productivity among hospitality employees. Current Issues in Tourism, 1–19. https://doi.org/10.1080/13683500.2023.2224550
- Tan, K. L., Hii, I. S. H., Lim, X. J., & Wong, C. Y. L. (2023). Enhancing purchase intentions among young consumers in a live-streaming shopping environment using relational bonds: Are there differences between “buyers” and “non-buyers”? Asia Pacific Journal of Marketing and Logistics, 36(1), 48–65. https://doi.org/10.1108/APJML-01-2023-0048
- Tan, K. L., Memon, M. A., Sim, P. L., Leong, C. M., Soetrisno, F. K., & Hussain, K. (2019). Intention to use mobile payment system by ethnicity: A partial least squares multi-group approach. Asian Journal of Business Research, 9(1), 36–59. https://doi.org/10.14707/ajbr.190055
- Tew, H. T., Tan, G. W. H., Loh, X. M., Lee, V. H., Lim, W. L., & Ooi, K. B. (2021). Tapping the next purchase: Embracing the wave of mobile payment. Journal of Computer Information Systems, 62(3), 527–535. https://doi.org/10.1080/08874417.2020.1858731
- Thakur, R. (2013). Customer adoption of mobile payment services by professionals across two cities in India: An empirical study using modified technology acceptance model. Business Perspectives and Research, 1(2), 17–30. https://doi.org/10.1177/2278533720130203
- The Star Online. (2018). Redesigning Malaysia’s higher education system. www.thestar.com.my (accessed 8 August 2018).
- Tóth, Z., Dul, J., & Li, C. (. (2019). Necessary condition analysis in tourism research. Annals of Tourism Research, 79, 102821. https://doi.org/10.1016/j.annals.2019.102821
- van der Valk, W., Sumo, R., Dul, J., & Schroeder, R. G. (2016). When are contracts and trust necessary for innovation in buyer-supplier relationships? A necessary condition analysis. Journal of Purchasing and Supply Management, 22(4), 266–277. https://doi.org/10.1016/j.pursup.2016.06.005
- Venkatesh, V., Morris, M.G., Davis, G.B. and Davis, F.D. (2003). User acceptance of information technology: Toward a unified view. MIS Quarterly, 27(3), 425–478. https://doi.org/10.2307/30036540
- WARC. (2019). The war of Malaysia’s e-wallets. https://www.warc.com/newsandopinion/news/the-war-of-malaysias-e-wallets/42990.
- Wong, L. W., Tan, G. W. H., Hew, J. J., Ooi, K. B., & Leong, L. Y. (2020). Mobile social media marketing: A new marketing channel among digital natives in higher education? Journal of Marketing for Higher Education, 32(1), 113–137. https://doi.org/10.1080/08841241.2020.1834486
- Wong, W. P. M., Tan, K. L., Inkgo, I. A., & Lim, C. Y. (2019). The effect of technology trust on customer e-loyalty in online shopping and the mediating effect of trustworthiness. Journal of Marketing Advances and Practices, 1(2), 39–52.
- Yadav, R., Sharma, S. K., & Tarhini, A. (2016). A multi-analytical approach to understand and predict the mobile commerce adoption. Journal of Enterprise Information Management, 29(2), 222–237. https://doi.org/10.1108/JEIM-04-2015-0034
- Yang, Y., Liu, Y., Li, H., & Yu, B. (2015). Understanding perceived risks in mobile payment acceptance. Industrial Management & Data Systems, 115(2), 253–269. https://doi.org/10.1108/IMDS-08-2014-0243
- Zarmpou, T., Saprikis, V., Markos, A., & Vlachopoulou, M. (2012). Modeling users’ acceptance of mobile services. Electronic Commerce Research, 12(2), 225–248. https://doi.org/10.1007/s10660-012-9092-x
- Zhang, J., Luximon, Y., & Song, Y. (2019). The role of consumers’ perceived security, perceived control, interface design features, and conscientiousness in continuous use of mobile payment services. Sustainability, 11(23), 6843. https://doi.org/10.3390/su11236843
- Zhou, J., Rau, P. L. P., & Salvendy, G. (2013). Age-related difference in the use of mobile phones. Universal Access in the Information Society, 13(4), 401–413. https://doi.org/10.1007/s10209-013-0324-1
- Zhou, T. (2011). The effect of initial trust on user adoption of mobile payment. Information Development, 27(4), 290–300. https://doi.org/10.1177/0266666911424075