ABSTRACT
With the ubiquity of digital media, managing personal data has become part of our daily lives. Teachers have to manage not only their own data, they also manage students’ sensitive data and furthermore have to teach data protection to students. In Switzerland, teacher education colleges have hence started to educate students about privacy and data protection. To do this effectively, it is important to understand pre-service teachers’ attitudes about online privacy and to assess their knowledge about protection strategies. Therefore, we tested whether existing scales for attitudes (perceived severity, perceived vulnerability, self-efficacy) about online privacy in social networks can be applied to pre-service teachers and be extended to e-mail and cloud storage. We then explored how these attitudes relate to protection strategies. Except for perceived vulnerability regarding social networks, we succeeded in reliably measuring the three different attitudes in the three domains. Priming did not change the attitudes. However, we did find that self-efficacy was related to the degree to which students report using data protection strategies. This suggests that to motivate pre-service teachers to engage in data protection, teaching them these strategies is more effective than making them more aware of their vulnerability and the severity of data breaches.
Introduction
Managing and protecting personal data has become part of our daily lives. Policy makers have responded by implementing data managing and protecting skills in curricula as fundamental learning objectives (e.g. DigCompEdu; Redecker, Citation2017). These skills are important for everybody living in a digital and data-driven world. But they are particularly relevant for teachers for three reasons. First, teachers deal with sensitive data of students and their families. For example, grades, promotions, health, and socio-economic circumstances. Second, in Switzerland, as required by the national curriculum, primary and secondary education teachers must teach data protection strategies to their students. Finally, as a role model, they should be conscious about the personal data they make available as they may be seen by their pupils and their employers. When pre-service teachers transition from their role as students into the role of a professional educator, their online identities become more scrutinized as colleagues, employers, students, and parents may look up their profiles. Each of these groups adds additional expectations on how and what data teachers should handle, making it difficult for teachers to fulfill all expectations simultaneously and therefore limiting the scope of their behavior (Kimmons & Veletsianos, Citation2014). Furthermore, teachers’ behavior varies across platforms. On Twitter, for example, most of them keep a professional focus (Carpenter et al., Citation2019), whereas on Instagram many mix professional and personal postings (Carpenter et al., Citation2020).
In contrast to learning domains such as mathematics, reading and biology, pre-service primary teachers start their teacher education with only limited knowledge about Media and Computer Science as these domains were not part of their own schooling (Döbeli Honegger & Hielscher, Citation2017). In addition, there have been rapid developments in the technologies used in Media and Computer Science and implementation processes vary widely across countries, requiring both targeted and flexible instruction of pre-service teachers and continued professional development of in-service teachers (Frau-Meigs et al., Citation2017; Hermida & Schmid, Citation2019).
In Switzerland, where we conducted our study, most primary school teachers regard privacy and data protection as important topics that they are keen to teach (Hermida, Citation2019). On an international level, Fraillon et al. (Citation2020) reported that teachers across 12 countries try to develop their students’ awareness about consequences of making information available online. At the same time, Marín et al. (Citation2021) have found that although teachers find it important to teach about data privacy, they are not aware or do not have a lot of knowledge about the privacy policies of the services they use and the local laws on using those services during their jobs.
In response to this situation, teacher education colleges have started to educate their students about privacy and data protection strategies, which is the first prerequisite for teaching the domains (e.g. Ball et al., Citation2001). However, to effectively teach pre-service teachers in this area, it is important to understand their attitudes about online privacy and develop a baseline idea about their knowledge about protection strategies. This study aims to gain an impression of pre-service teachers’ attitudes about privacy protection and their use of privacy protecting strategies and the relation between them. We investigate attitudes and protection strategies in three different domains: social networks, e-mail and cloud storage. We chose these services because social networks are used by most young adults (79% of 15–29 year-olds; BFS - Bundesamt für Statistik, Citation2021) and because e-mail and the nationwide use of cloud storage by students and teachers are part of Switzerland’s digitization strategy in education (EDK – Schweizerische Konferenz der kantonalen Erziehungsdirektoren, Citation2018).
According to Lwin et al. (Citation2007) adults use three different strategies to protect their privacy: fabrication: providing fictitious or false information; protection: using tools and technology to safeguard one’s privacy; and withholding: refusing to provide information (see Hichang, Citation2010 for a more elaborate description of different types of privacy protection strategies). However, strategy knowledge does not automatically mean application; there must also be motivation to use them. To provide a theoretical framework for this Adhikari and Panda (Citation2018) integrated Rogers’ (Citation1975) Protection Motivation Theory (PMT) and Bandura’s theory of self-efficacy. PMT postulates that an individual will be motivated to protect themselves from risks when they feel vulnerable (perceived vulnerability). This motivation is modulated by the perceived severity of the risks and their perceived self-efficacy (Bandura, Citation1977), that is, how confident they are about their ability to apply data protection strategies. In other words, an individual will be more likely to apply a protection strategy when they feel vulnerable to a specific risk (perceived vulnerability); estimate the risk’s consequences as severe (perceived severity); and feel confident they have the ability to act to prevent the said risk (self-efficacy). In his research with adults in Singapore, Hichang (Citation2010) showed that personally perceived vulnerability, perceived severity and self-efficacy are positively related to privacy concern. Privacy concern, in turn, was directly related to protection strategies. Hichang distinguished between three types of privacy protecting strategies: opt-out, proactive protection and use of privacy-enhancing technologies (‘PET’). It was found that personally (as opposed to societally) perceived vulnerability and self-efficacy were also directly related to use of the PET strategy, but not to the other two strategies. Focusing on privacy protection in social media, Adhikari and Panda (Citation2018) and Sedek et al. (Citation2018) partly replicated and built on these outcomes with university students from India and Malaysia. In contrast to Hichang, they also found a direct relation between self-efficacy and privacy concerns. They used items from questionnaires previously used and developed by Woon et al. (Citation2005; all three constructs), LaRose et al. (Citation2005; self-efficacy), Crossler (Citation2010; perceived severity and self-efficacy) and Dinev and Hart (Citation2004; perceived severity and perceived vulnerability). We will use the same items to assess the attitudes, behaviors, and motivations of our pre-service teacher population.
In contrast to the previous studies, we did not measure privacy concern (as an intermediate construct), but directly investigated the relation between the three motivational constructs (perceived vulnerability, perceived severity, and self-efficacy) and protection strategies. As mentioned above, Hichang (Citation2010) also found a direct relation between protection strategies and perceived vulnerability and efficacy respectively. In his study, the direct relation with perceived severity and protection strategies was not significant, but in that study perceived severity was measured with only one question, whereas we will use a four-item scale just like Adhikari and Panda (Citation2018) and Sedek et al. (Citation2018). To measure protection strategies, we formulated three withholding items based on the scale of Lwin et al. (Citation2007) and formulated four ‘everyday-life’ protection strategy questions for each of the three domains in our study (see Materials section).
Generalizing the perceived vulnerability, perceived severity and self-efficacy constructs
We first need to verify if the scales used by Adhikari and Panda (Citation2018) and Sedek et al. (Citation2018) reliably assess the three key constructs/attitudes (perceived vulnerability, perceived severity and self-efficacy) in western teacher education students. We will then examine if they can be expanded to email and cloud storage. In short, we will address the following two questions:
Can the scales of Adhikari and Panda (Citation2018) be used for Swiss teacher-education students?
Do we replicate the motivation constructs found for social networks (Adhikari & Panda, Citation2018) for email and cloud storage?
As far as we are aware, there have not been any studies about pre-teachers’ motivations to use email-protection strategies. Results from an earlier study from Arpaci et al. (Citation2015) demonstrated that the intention to use cloud services is positively related to how Turkish pre-service-teachers perceive their security and privacy. This study, however, did not distinguish between self-efficacy, perceived vulnerability and perceived severity and focused more broadly on attitude and behavioral intention within the framework of Ajzen’s (Citation1991) Theory of Planned Behaviour.
Priming awareness of vulnerability, severity and self-efficacy
Adhikari and Panda’s (Citation2018) scales consist of general questions about the privacy concerns of social networks users (e.g. ‘Losing information privacy through social networks would pose serious problems for me’). We hypothesized that such questions might seem too abstract for our population and that their answers might be different when we prime their awareness by making the question more concrete. Prior research suggests that pre-service teachers tend to reduce the amount of personal data shared online when made aware that this could interfere with their future role as a teacher (Mikulec, Citation2012). Therefore, we developed additional sets of questions for perceived vulnerability, perceived severity and self-efficacy with which we tried to make a more explicit connection to the everyday lives of the students. Importantly, we did not aim to develop new scales for the constructs. Our aim was to use these interleaved questions to prime our subjects addressing the research question:
Does the priming of perceived severity and perceived vulnerability consequences or thoughts about self-efficacy lead to higher scores on the scales?
The relationship between pre-service teachers’ concerns about and use of privacy protection strategies
We asked the students if they used specific data protection strategies. First, we took the data fabrication questions from Lwin et al. (Citation2007). As described above, data fabrication is a general strategy that can be used when signing up for virtually any online services by providing incorrect data (e.g. date of birth, phone number). The second questionnaire consisted of our own data protection strategy questions. With these questions we aim to answer the following two research questions:
Do perceived vulnerability, perceived severity and self-efficacy positively correlate with the use of data protection strategies?
Does the strength of this correlation differ for the three domains of social networks, email and cloud storage?
Methods
Participants
Ninety-nine students from a teacher education university were asked to participate in this study. The questionnaires were presented as part of a Media literacy education unit, which students typically take during the 3rd year of their studies. All but two participants consented for their data to be used for the purposes of this study and two students did not fill out the questionnaires resulting in a total sample of 95 students (72 female, 23 male). This gender ratio has been fairly stable at the teacher education university over the last three years (75–80% female). The mean ages of the participants was 25.2 (SD = 4.3).
Materials
Online questionnaires consisted of seven different types of questions. The questions were presented in the following order, but not every student was asked to answer all types of questions. Details about allocation of question types is described in the procedure section below. The questions, in German and English, can be found on the Open Science Framework (‘Appendix A’, https://osf.io/aqxk6/?view_only=983e8b9b872a47a88771cdbfd3821aa9).
General and background questions
Permission to use the data for the study, identifier, gender and year of birth (Questions 1–4).
(2) General attitude to data protection measures
Three general questions to get an impression about the students’ attitude to data protection (Questions 5–7).
(3) Media use
Which social networks, email and cloud storage services the students were using, in order to exclude students who did not use these services (Questions 8–10).
(4) Perceived Severity, Perceived Vulnerability and Self-efficacy Scales of Adhikari and Panda (Citation2018).
German translation of the Perceived Severity, Perceived Vulnerability and Self-efficacy Scales used by Adhikari and Panda (Citation2018) (taken from Woon et al., Citation2005). In addition to the original questions referring to social networks, we also rephrased them for email and cloud storage.
(5) Additional ‘everyday life’ Perceived Severity, Perceived Vulnerability and Self-efficacy Priming items.
Our own sets of questions for perceived vulnerability, perceived severity and self-efficacy for all three domains (social networks, email and cloud). With our questions we aimed to establish an explicit connection to students’ everyday lives. For example, (Perceived Severity in Social Networks scale:) ‘I have posted pictures and comments that could negatively influence a potential future job application, when my future potential boss would see them’, whereas the original scales consist of more general questions such as: ‘If my data in my social networks was no longer protected, this could lead to serious problems for me’.
Known and used data protection strategies
Based on Adhikari and Panda (Citation2018) (privacy protection behavior) and Lwin et al. (Citation2007) (data fabrication) we formulated three specific data-protection-strategy questions related to data fabrication and asked the students to what degree they knew and used these strategies. Data fabrication is a general strategy that can be used when signing up for online services. We included questions about one’s date of birth, phone number and gender. In addition, we used the data protection strategies we used for our ‘everyday’ self-efficacy items (questions 23, 25 and 27). These questions were answered by half of the students (from the priming condition, see procedure below).
(6) Knowledge about passwords and data protection of future students
Because this research was conducted during an actual unit, the lecturers also requested to include questions about other unit contents. Half of the students completed these questions at the beginning of the unit, a quarter of the students completed the questions both at the beginning and the end of the unit and a quarter of the students only completed them at the end of the course. The questions always appeared at the end of the questionnaire or in a separate questionnaire at the end of the unit. These data will not be considered in this paper (Questions 30–39).
Procedure
We created different links to different versions of the online questionnaires in Google Forms. Three classes (‘condition A: priming’), consisting of, respectively, 13, 19 and 24 students, were allocated to questionnaire 1, which contained all type 1–6 questions in the following order: 1, 2, 3, 5, 4, 6. Two other classes (‘condition B: no priming’), consisting of 18 and 25 students, were allocated to questionnaire 2, which contained all type 1–4, 6 questions. The questionnaire links were sent to the students by their teachers (authors 2 and 3), and they were requested to fill them out within seven days.
Answer options on the Likert scales
All questions of the scales of Adhikari and Panda (Citation2018) had a 7-point Likert scale. The newly developed Perceived Severity questions were scored on a 4-point Likert scale, the Perceived Vulnerability questions on a 7-point Likert scale and the Self-efficacy questions on a 5-point Likert scale. The Strategy questions were scored on a 5-point Likert scale. The scales’ ranges were chosen according to what seemed a reasonable number of steps for the corresponding question and to not exceed the assumed discriminatory capacity of the subjects as well as staying in the optimal range of 4 to 7 items (Lozano et al., Citation2008). Alternating between even and odd response options seems to have no relevant influence on internal consistency (Simms et al., Citation2019) and because we used correlational and factor analyses to answer research questions in which items from different Likert scales were used, the different number of answer options on the Likert scale will not influence the interpretation of the results.
Results
Below we will describe the results in order of the research questions as presented in the Introduction. The data and R-scripts can be found on the Open Science Framework (https://osf.io/aqxk6/?view_only=983e8b9b872a47a88771cdbfd3821aa9).
General impression about the students’ attitude to data protection
Most participants (57.9%) indicated that they protect their data adequately from unauthorized persons and the majority (69.5%) disagree that data protection is unimportant to them. Half of the participants (49.5%) rated their data protection efforts to be on par with those of their peers. And over a third (37.9%) thinks they protect their data better (see ). As far as we are aware, there have not been comparable studies with pre-service teachers to which we can compare our results. However, considering that the data in show a nice distribution of scores, it does not seem our sample in general holds extreme attitudes toward data protection.
Table 1. Percentages of answers to questions on data protection (n = 95).
Generalizing the perceived vulnerability, perceived severity and self-efficacy constructs – research questions 1 & 2
To analyze if the social network scales of Adhikari and Panda (Citation2018) could be reliably used for our population of pre-service teachers, we conducted an exploratory factor analysis to check if the same questions loaded on the same constructs. Next, we calculated the internal consistency (Cronbach’s Alpha) for each of the constructs.
Before running the analyses, three participants who did not have a social media account were removed, reducing the sample size from 95 to 92. We then performed a Parallel Analysis which suggested a three-factor solution, matching Adhikari and Panda’s number of dimensions. Finally, we performed the factor analysis using the generalized weighted least squares method and the Oblimin rotation, as we expect the dimensions to be somewhat correlated. The factor loadings are shown in .
Table 2. Factor loadings for social network items (n = 92).
We found the same dimensions as Adhikari and Panda. However, for our population one item from the perceived vulnerability scale (Factor 2) loaded on the factor for perceived severity (Factor 1). Both scales showed a good alpha level of 0.80. However, for the self-efficacy scale we found an overall value of ⍺ = 0.58. This is much lower than that which was found by Adhikari & Panda (⍺ = 0.88). While some authors suggest that values below 0.7 are not acceptable (Kline, Citation2000), others emphasize the importance of the number of items (more items in a scale lead to higher alpha values), suggesting scales with a low number of items could also be considered with lower alpha values (Cortina, Citation1993). We will return to this in the Discussion section.
Next, we conducted the same analyses for the domains of email and cloud storage. For the email domain we could use all participants (n = 95). For the cloud storage analyses we removed four participants who indicated that they did not use any form of cloud storage (n = 91). We again performed a Parallel Analysis with all items to determine the recommended number of factors (again a three-factor solution) and an exploratory factor analysis. The results are shown in .
Table 3. Factor loadings for e-mail items (n = 95).
Table 4. Factor loadings for cloud storage items (n = 91).
For both domains we found the same factors as for social networks and the same item diverged from the perceived vulnerability scale (Factor 2) and loaded on the perceived severity scale (Factor 1). All scales, including Self-efficacy, showed good alpha levels ranging from 0.84 to 0.91.
Priming awareness of vulnerability, severity and self-efficacy – research question 3
To test if priming the participants led to enhanced privacy concerns, we calculated mean scores for each scale (perceived severity, perceived vulnerability and self-efficacy) and each domain (social networks, email and cloud) and tested for differences between the primed and unprimed group of participants. We found no significant differences in participants’ level of privacy concerns between the two groups (see ). It is also interesting to note that our Swiss pre-teacher student sample scores are lower on all three scales than the Indian university students of Adhikari and Panda (Citation2018). In particular, the perceived severity of our population is much lower.
Table 5. Mean comparison of unprimed and primed participants for social networks, email and cloud storage. We also present the means and standard deviations found by Adhikari and Panda (Citation2018).
The relationship between pre-service teachers’ concerns about privacy and use of privacy protection strategies – research questions 4 & 5
In we present the answer percentages to the data fabrication questions. Participants were most protective of their phone number: 32% reported providing an incorrect phone number often and 10% reported doing so all the time. Almost a third of the participants are also very protective of their date of birth: 24% reported that they often provided an incorrect date of birth and 7% indicated that they always do so. Participants were the least protective about their gender: 62% reported that they would know how to provide a false gender, but typically do not do it.
Table 6. Percentages of answers per category to the three data-fabrication strategies.
In the next step we calculated the correlations between the three motivational constructs and data-fabrication scores. For this analysis we combined the first two answer options (‘I do not know how to do this, and I know how to do this, but I don’t do it; see ) into one category. Then we correlated these scales (now consisting of four levels) with the mean scores on the perceived severity, perceived vulnerability and self-efficacy scales (for means, see ). We did not find any significant correlations for social networks and email. For cloud storage we only found a significant correlation between self-efficacy and providing an incorrect phone number. This means that the higher their self-efficacy regarding cloud storage, the more likely someone is to provide an incorrect phone number (see ).
Table 7. Correlations between fabrication strategies and perceived severity, perceived vulnerability and self-efficacy for each of the three domains (social networks, email and cloud storage).
Half of the participants were also asked about data protection strategies as part of our efforts to prime their responses to the self-efficacy questions of Adhikari and Panda (Citation2018). They filled out questionnaires about four different strategies for each media type (see for an overview). For social networks, properly checking who is behind a friend request was the most widely used strategy (>96%). The least used strategy was preventing others from tagging the participants in photos, which only 40% do often or always. For emails, 87% reported to often or always recheck the recipients before sending them. On the other hand, two-factor authentication was a data protection strategy for e-mails for which 41% reported that they do not know how to do it. Cloud storage was the only media type for which every single data protection strategy was done on a regular basis by more than half of the participants. Most (71%) often or always refrain from posting links to their files on publicly accessible websites, followed by 67% who often or always adjust the permissions others have for their shared files (viewing, editing, downloading).
Table 8. Percentages of answers to the data protection questions.
Finally, we calculated the correlations between perceived severity, perceived vulnerability, self-efficacy and how often our participants used the specific data-protection strategies in each domain (see ). For social media we found no relationship between participants’ perceived severity, perceived vulnerability and the frequency with which they deployed the data protection strategies. However, there were significant correlations with self-efficacy. Participants with higher self-efficacy more often adjusted who can view or comment on their posts, delete old posts that didn’t reflect their views anymore and prevented others from tagging them in pictures.
Figure 1. Correlations between perceived vulnerability, self-efficacy, perceived severity and the use of protection strategies.
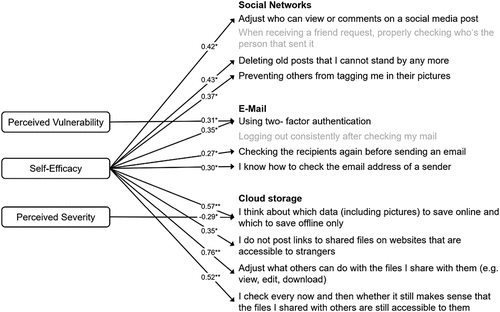
For email there were no significant correlations between participants’ perceived severity and the use of the data protection strategies. Perceived vulnerability showed a significant correlation with the frequency of using two-factor authentication only. Again, we found significant correlations between participants’ self-efficacy and the use of two-factor authentication, rechecking the recipients of emails and the ability to check the email address of a sender.
Finally, for cloud storage participants’ perceived severity correlated negatively with the frequency with which participants thought about which files to save online and which to save offline. There were no significant correlations between perceived vulnerability and the data protection strategies. But again, there were significant correlations between self-efficacy and the protection strategies, where adjusting what others can do with one’s file showed the strongest correlation.
Self-efficacy was positively correlated with 12 of the 14 protection strategies we investigated, showing its significance across the three different domains. Even those two protection strategies that correlated with perceived vulnerability and severity did correlate with self-efficacy, too.
Discussion
The aim of this study was to investigate pre-service teachers’ concerns about and their use of privacy protection strategies. First, we tested if we could reliably use the motivational scales, also used by Adhikari and Panda (Citation2018), to measure the concerns and attitudes of our target group. This worked out well: with only one exception (self-efficacy, in social networks), we could reliably measure perceived severity, perceived vulnerability and self-efficacy in relation to data security. Whereas previous research (e.g., Adhikari & Panda, Citation2018) focused on social networks only, we expanded our findings to the domains of email and online data saving services (cloud). Interestingly, our population consisting of Swiss teacher education students indicated to have lower perceived severity, perceived vulnerability and self-efficacy in relation to their perception of security in social networks compared to the Indian university students in the study of Adhikari and Panda. We had hypothesized that the scores on the questionnaires could be increased by priming the students with more concrete scenarios before answering the questions. However, priming our students did not change their scores.
After establishing that we could reliably measure the privacy concerns of our population, we examined the correlations between the three motivational constructs and privacy protection strategies. For data fabrication strategies, we only found a significant positive correlation between providing a fake telephone number and self-efficacy in the domain of cloud storage. As all the other correlations were not significant, we are careful with the interpretation of this solitary significant result. Overall, it seems that the use of data fabrication strategies is not linked to data privacy concerns of pre-service teachers. Next, we examined correlations between the three motivational constructs and the four specific data protecting strategies we formulated for our self-efficacy priming questions for each of the three domains. Here we saw the same pattern of significant positive correlations across all three domains: self-efficacy correlated with at least three of the four data protection strategy questions of each of the three domains. For the constructs perceived severity and perceived vulnerability we found a correlation with only one question for each. The fact that the use of strategies seems to be mostly linked to self-efficacy and not so much to perceived severity and perceived vulnerability seems to support the idea that self-efficacy is a more important factor than perceived severity or vulnerability in determining if students will use data protection strategies . This result partly converges with the outcomes of Hichang (Citation2010), who also found a significant relation between one of the privacy protection strategies (‘use software programs that protect your privacy’). However, in his study there was no significant relation between self-efficacy and the two other privacy protection scales: opt-out and proactive self-protection (three items). For opting out no skills are needed, therefore it does not seem surprising that there is no link with self-efficacy. However, with proactive self-protection, one could have imagined that self-efficacy would have played a role, for instance, for items like ‘erasing cookies after an online session’. It should be noted, however, that the study of Hichang (Citation2010) focused on the use of the Internet in general and that our study specifically focused on internet apps (social networks, email and cloud), which could form an alternative explanation for the different outcomes. Finally, it needs to be stressed that all studies so far, including our own, have correlational designs and that intervention studies are needed to examine whether improving self-efficacy indeed leads to more use of data protection strategies as compared to increasing participants’ perceived vulnerability or severity.
We translated the items of the scales of Adhikari and Panda (Citation2018) from English to German. The first thing we noticed after collecting the data and the first analyses were finished, were the low alphas, in particular for the social network domain. Low alphas on previously successful scales can be a result of multiple factors, including cultural differences between the samples, the translation of the questionnaires or new events leading to changes in how people interpret the questions. We therefore conducted an Exploratory Factor Analysis to examine if the structure of the scales were the same. We then discovered that the perceived vulnerability item ‘I could potentially suffer from malicious online security issues (e.g., privacy intrusions, virus attacks, etc.) in social networks/ email/ cloud storage’ loaded on the perceived severity scale for our sample. Adhikari and Panda conducted a Confirmatory Factor Analysis, in which the items were already allocated to each of the scales. It could therefore be that their alphas for the perceived severity and vulnerability scales would also increaseif this item were swapped. Nevertheless, they already found good alphas for both scales (.86 and .84 respectively) without this change, whereas the alphas of our scales for the social network domain greatly improved with this change (PS before: .76; PS after: .80, PV before: .35; PV after: .80). Importantly, the same pattern was found across social networks, email and cloud. So, what could explain this different pattern?
It might be that recent trust shattering events like the Cambridge Analytica scandal, which had voters being manipulated on an industrial scale by using their personal information from social media (Rosenberg et al., Citation2018), have altered people’s perception and actions regarding personal data. In this incident the data were compromised through no fault of the users, a situation that is not limited to social networks. There have been similar incidents for market-leading email providers and cloud-storage providers (e.g. Cimpanu, Citation2019; Turner, Citation2016) where users had their data exposed because of security breaches at the company level and not because of the users’ wrongdoing. It is possible that this could lead users to believe that although they do everything right to protect their data, there is always a chance of a security breach over which they have no control. Therefore, one possible explanation could be that the meaning of the item I could potentially suffer from malicious online security issues (e.g., privacy intrusions, virus attacks, etc.) in social networks/ email/ cloud storage would be interpreted differently now than it would have been in 2016. Specifically, in 2016 it would have been regarded as an issue of vulnerability, whereas today, as it has become clear that sooner or later anyone is susceptible to these kinds of threats, they may be less associated with a potential vulnerability and more with their extent and therefore their severity. So, to potentially suffer from a malicious online security issue becomes less an aspect that varies with vulnerability – since everyone is vulnerable to this kind of threat. But instead it becomes more an aspect of how severe (therefore it varies with perceived severity) it would be when one is inevitably confronted with it.
We found very good alphas for the perceived severity and perceived vulnerability scales. The self-efficacy scale also looked good for email and cloud (0.90 and 0.87 respectively) but not for the social network dimension (0.55), which in the sample of Adhikari and Panda was 0.88. What could explain this deviation? A closer look at the self-efficacy in social network questions in quickly reveals that one item in particular had a very low factor loading (Question 16a: I am able to protect my personal data in social networks). Just like the interpretation of the perceived vulnerability item, as discussed above, it might be that this is a poor item because it can be interpreted in different ways. For social networks in particular, participants might have thought: ‘Well, I know about how to handle the privacy settings, but still, without my control, the social network companies might jeopardize or misuse my data’. Having a self-efficacy scale with low reliability needs to be considered when interpreting the follow-up analyses in which this scale was used. Concretely, we looked at the correlations between the motivational constructs and the data protection strategies. However, as the correlations between self-efficacy for email and cloud (for which we found good reliability) and the data protection strategies showed the same pattern, we do not think that the low reliability has influenced our results in a significant or unexpected way. If anything, it would have suppressed the correlations between self-efficacy and the strategy questions in the social network domain.
Conclusion
This study was the first to assess and prime pre-service teachers’ attitudes (perceived severity, perceived vulnerability and self-efficacy) about online privacy and to explore if and how these attitudes related to their protection strategies for social networks, email and data cloud storage. Except for perceived vulnerability in the domain of social networks, we succeeded in reliably measuring the three attitudes in the three domains. Although priming did not change reports of perceived severity, vulnerability and self-efficacy, we did find that self-efficacy was related to the degree to which students report using data protection strategies. Replication of the results with a training study is needed to draw causal conclusions. However, for now our findings seem to suggest that to encourage pre-service teachers to use more data protection strategies, their education should first focus on teaching them these strategies and not on making them more aware of their vulnerability and the severity of possible data security breaches.
Disclosure statement
No potential conflict of interest was reported by the author(s).
All authors declare that they have no financial or non-financial competing interests to report.
Additional information
Notes on contributors
Martin Hermida
Martin Hermida is a senior researcher and lecturer of media education at the Schwyz University of Teacher Education. His research focuses on media education in primary and secondary schools as well as children’s and adolescents’ media use and literacy. He developed and has been leading the university's master’s degree program 'Media and Computer Science Education' in which he also teaches courses on media education and knowledge transfer.
Nina Imlig-Iten
Nina Imlig-Iten is a Lecturer of Media Education and established and leads the unit for human resource development at the Schwyz University of Teacher Education. She has been researching learning with digital media and games for more than 5 years and teaches courses for pre- and in-service teachers.
Iwan Schrackmann
Iwan Schrackmann is a lecturer of media education at the Schwyz University of Teacher Education. He is in charge of the subject core group ‘Media and Computer Science’ and developed and leads the university’s bachelor curriculum for ‘Media and Computer Science Education’. He teaches media education courses for pre- and in-service teachers. He also works as an ICT specialist at the office for elementary schools and sport of the canton of Schwyz, where he has been developing the digital transformation framework for the compulsory primary and first three years of the secondary schools in the Canton of Schwyz.
Eva Marinus
Eva Marinus is a Professor at the Institute for Media and School at the Schwyz University of Teacher Education in Switzerland. Her research focuses on computer science and media education of children and pre-service teachers. She also develops and teaches courses on research & development and educational technology in the university's master’s degree program 'Media and Computer Science Education'.
References
- Adhikari, K., & Panda, R. K. (2018). Users’ information privacy concerns and privacy protection behaviors in social networks. Journal of Global Marketing, 31(2), 96–110. https://doi.org/10.1080/08911762.2017.1412552
- Ajzen, I. (1991). The theory of planned behavior. Organizational Behavior and Human Decision Processes, 50(2), 179–211. https://doi.org/10.1016/0749-5978(91)90020-T
- Arpaci, I., Kilicer, K., & Bardakci, S. (2015). Effects of security and privacy concerns on educational use of cloud services. Computers in Human Behavior, 45, 93–98. https://doi.org/10.1016/j.chb.2014.11.075
- Ball, D. L., Lubienski, S. T., & Mewborn, D. S. (2001). Research on teaching mathematics: The unsolved problem of teachers’ mathematical knowledge. In V. Richardson (Ed.), Handbook of Research on Teaching (Vol. 4, pp. 433–456). New York: Macmillan.
- Bandura, A. (1977). Self-efficacy: toward a unifying theory of behavioral change. Psychological Review, 84(2), 191–215. https://doi.org/10.1037/0033-295X.84.2.191
- BFS – Bundesamt für Statistik. (2021). STAT-TAB database. Neuchâtel. Schweizerische Eidgenossenschaft.
- Carpenter, J. P., Kimmons, R., Short, C. R., Clements, K., & Staples, M. E. (2019). Teacher identity and crossing the professional-personal divide on twitter. Teaching and Teacher Education, 81, 1–12. https://doi.org/10.1016/j.tate.2019.01.011
- Carpenter, J. P., Morrison, S. A., Craft, M., & Lee, M. (2020). How and why are educators using Instagram? Teaching and Teacher Education, 96, 103149. https://doi.org/10.1016/j.tate.2020.103149
- Cimpanu, C. (2019). Microsoft discloses security breach that impacted some Outlook accounts. ZDNet. https://www.zdnet.com/article/microsoft-discloses-security-breach-impacting-some-outlook-accounts/
- Cortina, J. M. (1993). What is coefficient alpha? An examination of theory and applications. Journal of Applied Psychology, 78(1), 98–104. https://doi.org/10.1037/0021-9010.78.1.98
- Crossler, R. E. (2010). Protection motivation theory: Understanding determinants to backing up personal data. 2010 43rd Hawaii International Conference on System Sciences, 1–10.
- Dinev, T., & Hart, P. (2004). Internet privacy concerns and their antecedents—Measurement validity and a regression model. Behaviour & Information Technology, 23(6), 413–422. https://doi.org/10.1080/01449290410001715723
- Döbeli Honegger, B., & Hielscher, M. (2017). Vom Lehrplan zur LehrerInnenbildung—Erste Erfahrungen mit obligatorischer Informatikdidaktik für angehende Schweizer PrimarlehrerInnen. INFOS 2017, E-Learning Fachtagung Informatik, Lecture Notes in Informatics (LN) - Proceedings Series of the Gesellschaft Für Informatik (GI), 97–107.
- EDK – Schweizerische Konferenz der kantonalen Erziehungsdirektoren. (2018). Digitalisierungsstrategie. Strategie der EDK vom 21. Juni 2018 für den Umgang mit Wandel durch Digitalisierung im Bildungswesen.
- Fraillon, J., Ainley, J., Schulz, W., Friedman, T., & Duckworth, D. (2020). . In IEA international computer and information literacy study 2018 international report Springer https://doi.org/10.1007/978-3-030-38781-5
- Frau-Meigs, D., Velez, I., & Michel, J. F. (2017). Mapping media and information literacy policies. New perspectives for the governance of MIL. In D. Frau-Meigs, I. Velez, & J. F. Michel (Eds.), Public policies in media and information literacy in Europe: Cross-country comparisons (pp. 19–88). London: Routledge.
- Hermida, M. (2019). EU Kids Online Schweiz. In Schweizer Kinder und Jugendliche im Internet: Risiken und Chancen. Goldau: Pädagogische Hochschule Schwyz.
- Hermida, M., & Schmid, R. (2019). Fachdidaktik Medien und Informatik: Professionalisierung der Medienpädagogik in der Schweiz. Ludwigsburger Beiträge zur Medienpädagogik, 19(20), 1–13. https://doi.org/10.21240/lbzm/20/06
- Hichang, C. (2010). Determinants of behavioral responses to online privacy: The effects of concern, risk beliefs, self-efficacy, and communication sources on self-protection strategies. Journal of Information Privacy and Security, 6(1), 3–27. https://doi.org/10.1080/15536548.2010.10855879
- Kimmons, R., & Veletsianos, G. (2014). The fragmented educator 2.0: Social networking sites, acceptable identity fragments, and the identity constellation. Computers & Education Vol. 72. (pp.292–301). https://doi.org/10.1016/j.compedu.2013.12.001
- Kline, P. (2000). The Handbook of Psychological Testing. Routledge.
- LaRose, R., Rifon, N., Liu, S., & Lee, D. (2005). Online safety strategies: A content analysis and theoretical assessment. The 55th Annual Conference of the International Communication Association.
- Lozano, L. M., García-Cueto, E., & Muñiz, J. (2008). Effect of the number of response categories on the reliability and validity of rating scales. Methodology, 4(2), 73–79. https://doi.org/10.1027/1614-2241.4.2.73
- Lwin, M., Wirtz, J., & Williams, J. D. (2007). Consumer online privacy concerns and responses: A power–responsibility equilibrium perspective. Journal of the Academy of Marketing Science, 35(4), 572–585. https://doi.org/10.1007/s11747-006-0003-3
- Marín, V. I., Carpenter, J. P., & Tur, G. (2021). Pre-service teachers’ perceptions of social media data privacy policies. British Journal of Educational Technology, 52(2), 519–535. https://doi.org/10.1111/bjet.13035
- Mikulec, E. A. (2012). Professional faces: Pre-service secondary teachers’ awareness of issues of self-disclosure on social-networking sites. Current Issues in Education, 15(3), 1–14. https://cie.asu.edu/ojs/index.php/cieatasu/article/view/938
- Redecker, C. (2017). European framework for the digital competence of educators: DigCompEdu. Publications Office of the European Union.
- Rogers, R. W. (1975). A protection motivation theory of fear appeals and attitude change1. The Journal of Psychology, 91(1), 93–114. https://doi.org/10.1080/00223980.1975.9915803
- Rosenberg, M., Confessore, N., & Cadwalladr, C. (2018, March 17). How Trump consultants exploited the Facebook data of millions. New York Times Online. https://www.nytimes.com/2018/03/17/us/politics/cambridge-analytica-trump-campaign.html
- Sedek, M., Ahmad, R., & Othman, N. F. (2018). Motivational factors in privacy protection behaviour model for social networking. MATEC Web of Conferences, 150, 05014. https://doi.org/10.1051/matecconf/201815005014
- Simms, L. J., Zelazny, K., Williams, T. F., & Bernstein, L. (2019). Does the number of response options matter? Psychometric perspectives using personality questionnaire data. Psychological Assessment, 31(4), 557–566. https://doi.org/10.1037/pas0000648
- Turner, K. (2016). Hacked Dropbox login data of 68 million users is now for sale on the dark Web. The Washington Post Online. https://www.washingtonpost.com/news/the-switch/wp/2016/09/07/hacked-dropbox-data-of-68-million-users-is-now-or-sale-on-the-dark-web/
- Woon, I., Tan, G.-W., & Low, R. (2005). A protection motivation theory approach to home wireless security. Proceedings of the 26th International Conference on Information Systems, 367–380.
