Abstract
This study traced a deployed real IT system to enhance occupational safety for a polluted confined space. By incorporating wireless technology, it automatically monitors the status of workers on the site and upon detected anomalous events, managers are notified effectively. The system, with a redefined standard operations process, is running well at one of Formosa Petrochemical Corporation's refineries. Evidence shows that after deployment, the system does enhance the safety level by real-time monitoring the workers and by managing well and controlling the anomalies. Therefore, such technical architecture can be applied to similar scenarios for safety enhancement purposes.
1. Introduction
1.1. Background
The principle of human protection in working environments applies to confined spaces,[Citation1] which are often badly ventilated or completely airtight and not suitable for a lengthy stay.[Citation2]
If the confined space is polluted, the working condition is even dangerous. In addition to the long stay, risk may result from oxygen or sensory deprivation and a worker may suffer life-threatening events because he may not easily recognize the gradual changes, such as the increase of a poisonous gas, and may ignore the physiological responses of the body. In practice, a polluted confined space is usually permit-required and securing workers in such a space is more critical than in unpolluted (normal) confined spaces.
This is an occupational safety issue about which most petroleum and chemical industries are concerned.[Citation3] For example, when the catalyst within a residuum desulfurization (RDS) reactor loses its function, workers need to enter it for catalyst replacement. The inside space is a typical polluted confined space that is filled with grease and harmful substances. Working risks include not only normal long-stay risks, but life-threatening events like suffocation due to bad ventilation, toxic gas poisoning, explosions, electrocutions and, possibly, plummeting from heights.
Supervisor's visual monitoring is a traditional approach to mitigate these risks. However, except for the high cost, such an approach can be too unrefined and prone to human error. Fortunately, the evolvement of modern technologies can help to improve this safety management problem.
1.2. The studied case
This paper studied an IT system of the Formosa Petrochemical Corporation (FPC), which incorporates radio frequency (RF) technology and has been deployed in one of FPC's oil refineries located at Mailiao, Taiwan. After running for years, it is shown to improve the safety level by effectively monitoring the workers and appropriately detecting/reporting the anomalies.
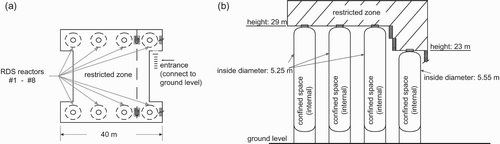
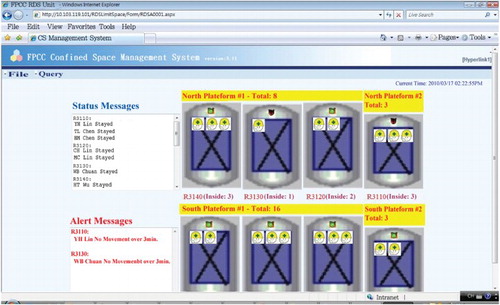
In the refinery, there are eight RDS reactors as shown in . Each reactor has a closed and tube-shaped inside space with a 30cm-thick iron walled, with one opening gate at the top ((b)). A platform connects all the reactor gates and an entrance/exit stairs is attached.
At the bottom of each reactor, there is a catalyst rib. Because a new rib holds its chemical function for 1 year, every half year, four ribs inside a row of reactors are replaced after reactor's shutdown and relevant jobs (i.e., waste-cleaning, wall-maintaining and rib-replacing) are performed. During the period, the whole platform area, the stairs and the spaces inside the reactors are designated as the ‘restricted zone’, as defined in (a).
After shutdown, gas-withdrawing is performed because a running reactor has gradually polluted the confined space due to the chemical reactions. But this does not guarantee that the harmful substances are completely withdrawn. So a worker can suffer ‘pollution risks’. Besides, the irregularly-shaped tall space equipped with a multiplicity of complex pipes also makes it likely that workers will face ‘falling risks’. Moreover, such a confined space inherits other risky properties from an unpolluted confined space. Non-immediate or mental-harmful events like oxygen deprivation, unresponsiveness, sensory-deprivation, coma or losing consciousness, can occur due to a long stay. These bring up ‘normal risks’. To mitigate these risks, supervisors are responsible for inspecting working conditions, checking workers’ eligibility, monitoring their safety and work time, identifying/reporting anomalies and launching rescue actions when necessary.
However, a worker may faint before he can call for help and the supervisors or standby workers on the platform might not immediately recognize such an event, losing the chance to save the worker in time. This motivated FPC to design and deploy the IT system to effectively monitor and update the status of every worker and to automatically detect and report any anomalies.
Incorporating RF technology is reasonable because it has been used for a long time. It was used for the first time to detect whether an approaching airplane is an enemy or not [Citation4] and the literature is now abundant with RF applications.[Citation5–11] In particular, Helmus [Citation12] suggests using it to ensure availability and reliability of personal life-sustaining apparatuses. So the case adopts RF technology because it is without job intervention or body infringement.
2. The system
2.1. Main functions
2.1.1. Monitoring
The system monitors the status of each worker/supervisor in the restricted zone.
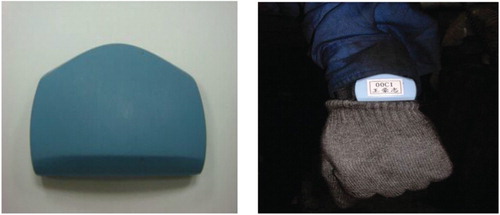
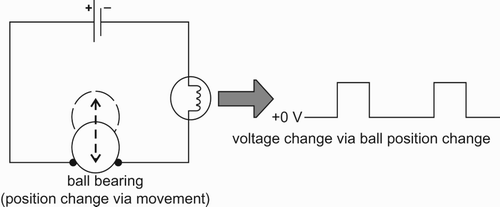
On the user side, each worker is required to wear a RF transmitter wristband for motion detection (), inside which is a small ball-bearing (). The ball-bearing trembles if the wristband moves. A ‘status bit’, which is encoded by high/low voltages physically, changes according to the current position. Every second, the wristband transmits its unique radio frequency identification (RFID) followed by a status bit.
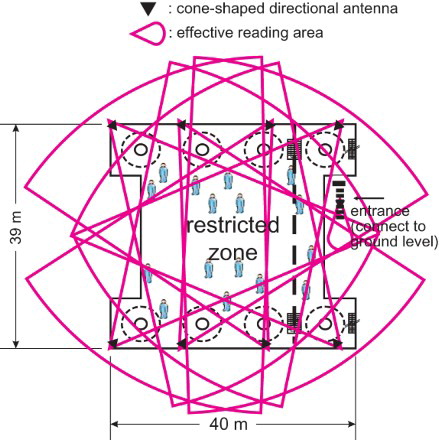
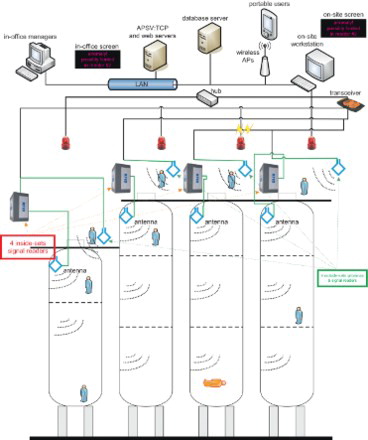
On the system side, a ‘cone-shaped’ RF antenna () is installed at the ceiling of each confined space, while its signal reader is set up outside. These are to receive and recognize data carried by the wireless signals, then for the application server (APSV) to collect and identify the wristband wearer and its status, so as to judge for any possible anomalous events.
2.1.2. Authorization
An additional RF-antenna-reader set and two infrared detectors are installed at the entrance stairway. They serve two purposes. The authentication function is for anonymous detection, where the anonymous can be any legal worker or supervisor who is not carrying a wristband, or can be any unwelcome intruders. If somebody is passing the entrance stair (detected by the infrared detectors) but no RFID can be read, there is an anonymous-entering event (perhaps protocol-obliging). The other count-and-compare function is for counting the authenticated persons who have entered the area, NA, which is to be compared with the number of exclusively collected RFID codes, NR. If NR > NA, there is somebody who is wearing a wristband similar to the wristbands worn by the workers. If NR < NA, there might be an antenna coverage gap or a malfunctioning legal wristband (perhaps battery-short). If NR and NA are inconsistent and the above mentioned are not the reason, perhaps some worker has left behind his wristband before entrance to the restricted area.
2.1.3. Deliberate designs
At first, the RF antenna and the signal reader are separated, although they are ‘a set’. Due to the fact that electricity in the space may cause explosion, the antenna inside each RDS reactor is made of explosion-proof material and is positioned to cover a 55° angle. But because of metal-shielding, the only signals it can capture are limited to those inside the confined space.
The second design is that in addition to the eight ‘internal sets’ and the above-mentioned ‘stairway set’, there are eight ‘external sets’ dispersedly installed on the platform edges (). Such layout is to completely cover the restricted zone (to ‘see’ all workers on the platform) and to help reconfirm who is inside a specific reactor if its top gate is opened, which is the usual case when anybody is working inside.
2.1.4. Accounting function
The system records the following events:
Entrance/exit events of the restricted-zone;
Entrance/exit events of the gates of RDS reactor;
Anomalous (alarm) events detected by the APSV.
Since the system keeps these records, subsequent analysis, report printing or further data mining can be performed.[Citation13]
2.1.5. Anomaly-detection and message-dispatching
The system detects alarm events and sends out messages if any worker is possibly in danger, for immediate response or rescue actions within ‘golden minutes’.
Alarm events are categorized as ‘non-moving’, ‘long-working’ and ‘insufficient rest’ events. The predefined ‘anomaly taxonomy’ adopted by FPC for asserting alarm events is summarized in . These criteria were applied for a long time previously before the system was deployed. However, with the IT system, these events can be detected accurately and immediately, because the application server (APSV) judges these events by its pre-programmed algorithms manifested by the business rules stored in the database.
Table 1. Criteria asserting alarm events.
Once any alarm event is detected, the system composes short and clear messages to alert both the on-duty supervisors and the in-office managers. These messages are sent or displayed via multiple channels like on-site and in-office monitors, SMS messages, e-mails, real-time-refreshed web contents, instant messages or any combinations of the above. The multi-channel mechanism ensures a fast response time.
2.2. System architecture and flexibility issues
The screenshot of the system's Web interface and the overall system architecture are shown in Figures and , respectively.
For flexibility concerns, many parts of the system are configurable, designed as amendable sets of business rules stored in the database. The taxonomy of event types, the per-event-type definition of alarm-messaging channels and the multiple recipients to whom a message is sent are all configurable.
3. Consequences
With system deployment, operational regulations and relevant standard processes have been altered. Major changes are in:
On-site preparation. Everyone must wear a RF wristband before entering the restricted zone.
Working period. The wristband must be worn anytime, at everywhere of in the zone.
Working protocol and Regulations. Regulations are instrospected perpetually and altered. For example, now a worker is allowed to enter a reactor only when there is 1 one standby worker with 1 one supervisor on the platform near the gate. Otherwise, protocol-oblidging is warned.
Minor changes are mainly due to the anomaly-detection function. For example, reasons resulting in a non-moving event are many-fold, as shown in . While (P2) and (P3) are perhaps life-threatening, related actions are case by case. For example, a (P2) case can involve physical or physiological experiences or professions at the very first moment to decide if the worker is suffering symptoms. Subsequent progresses might involve on-site paramedics, calling for doctors or hospital emergency-room sending. As the flow must be faithfully recorded by the system, it brings up minor changes. Except for non-moving, anomaly-detections of long-working and insufficient-rest also change the standard process.
Table 2. Possibilities for a ‘non-moving’ event.
4. Impacts
Instead of RF technology, FPC once considered using oxygen-level detection sensors. However, such a solution seems difficult to apply. A worker must carry burdensome tools and life-support apparatus and the warning messages might be easily neglected by a worker focusing on his task. In addition, neither can it detect the gradual increase of harmful substances, nor can it time how long a worker has been in the confined space.
In contrast, adopting the RF-based solution has the following observed advantages: (A1) Real-time monitoring; (A2) Mobility of workers; (A3) System transparency; (A4) Automatic event detection; (A5) Full-ranged event detection; and (A6) Effective job tracing.
For these reasons, FPC adopted this solution and developed the IT system in 2009. It was deployed in late 2010. Until the writing of this paper, it has been used with the catalyst-replacement process 5 times. The advantages of this system have been observed:
| (O1) | Only one worker has ever got fainted since 2010; | ||||
| (O2) | Positive impacts to internal regulastions; | ||||
| (O3) | Supervisors/workers adhering to the safety protocol; | ||||
| (O4) | Wearing a wristband improves worker morale and increases worker faith. | ||||
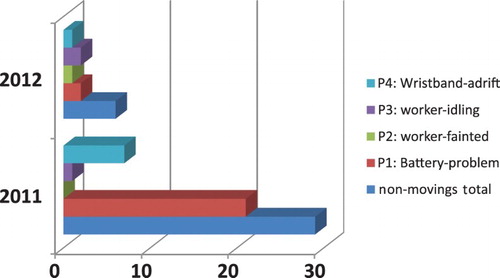
However, as seen in , there were still 29 non-moving events in 2011. Most cases were (P1) (battery-problem, 21 times) and (P4) (wristband-adrift, 7 times, among which six cases occured when the wristband was intentionally taken-off while only one was when it unintentionally fell off).
To improve this, in early 2012, FPC restated the internal regulation to prohibit any worker removing the wristband and a new SOP requiring supervisors to bring additional batteries has been addressed. This took effect immediately. In 2012, only six non-moving events were detected, among which there were two (P1) cases (decreased by 19), one (P2) (one worker fainted and rescued), two (P3) (a worker was sleeping on the platform and a supervisor was ‘meditating’) and one case of (P4) (decreased by 6).
5. Conclusion
The RF-technology-incorporated IT system studied in this paper is a real-time, transparent and computerized monitoring and event-detecting system, for the polluted confined space inside RDS reactors wherein the workers are more at risk. It has improved the safety management level at FPC.
The case demonstrates the laudable effort of a company in the East Asian Island Arc, where super catastrophic events are frequent but companies have nothing to do with these risks.[Citation14] However, there is a way without much cost [Citation15] to mitigate the ‘controllable part’ of the risks. This inspires further thoughts for companies facing similar occupational safety issues.
Finally, as the system has enhanced the safety level at FPC, portions of the IT system functions may contribute to the enhancement and the various organizational efforts after deployment (e.g., regulation changes, etc.) can contribute and are future topics worthy of study.
Disclosure statement
No potential conflict of interest was reported by the authors.
References
- Occupational Safety and Health Administration (OSHA). U.S. Department of Labor. Confined space [cited 2013 Oct 29]. https://www.osha.gov/SLTC/confinedspaces/.
- Pettit T, Linn H. A guide to safety in confined spaces. In: DHHS (NIOSH) Publication. Washington (DC): Government Printing Office; 1987. p. 87–113.
- Pośniak M, Kozieł E, Jeżewska A. Occupational exposure to harmful chemical substances while processing phenol-formaldehyde resins. Int J Occup Saf Ergon. 2001;7(3):263–276. DOI:10.1080/10803548.2001.11076490
- Stockman H. Communication by means of reflected power. Proc IRE. 1948;36(10):1196–1204. doi: 10.1109/JRPROC.1948.226245
- Tsai C, Huang H. A real-time scheduling and rescheduling system based on RFID for semiconductor foundry FABs. J Chin Inst Ind Eng. 2007;24:437–445.
- Chow HKH, Choy KL, Lee WB, Lau KC. Design of a NRFID Case-based resource management system for warehouse operations. Expert Syst Appl. 2006;30:561–576. doi: 10.1016/j.eswa.2005.07.023
- Sae-Ueng S, Pinyapong S, Ogino A, Kato T. Personalized shopping assistance service at ubiquitous shop space. Proceedings of 22th International Conference on – AINAW, 2008 Mar 25–28. Washington (DC): IEEE Computer Society; 2008. p. 838–843.
- Ngai EWT, Cheng TCE, Au S, Lai KH. Mobile commerce integrated with RFID technology in a container depot. Decis Support Syst. 2007;43(1):62–76. doi: 10.1016/j.dss.2005.05.006
- Hsu CI, Shih HH, Wang WC. Applying RFID to reduce delay in import cargo customs clearance process. Comput Ind Eng. 2009;57(2):506–519. doi: 10.1016/j.cie.2008.02.003
- Goodrum PM, McLaren MA, Durfee A. The application of active radio frequency identification technology for tool tracking on construction job sites. Automat Constr. 2006;15(3):292–302. doi: 10.1016/j.autcon.2005.06.004
- Rach NM. RFID applications spread in upstream operations. Oil Gas J. 2008;21:37–45.
- Helmus M. Application fields of RFID in health safety and environment management. Proceedings of 1st Annual RFID Eurasia Conference, Sep 5–6, 2007. Piscataway (NJ): IEEE; 2007. p. 1–3.
- Ejdys J, Lulewicz-Sas A. An OH&S management system as a source of information. Int J Occup Saf Ergon. 2010;16(4):445–454. DOI:10.1080/10803548.2010.11076859
- Chang CT, Chou YY, Zhuang ZY. A practical expected-value-approach model to assess the relevant procurement costs. J Oper Res Soc. 2015;64(4):539–553. doi: 10.1057/jors.2014.16
- Rzepecki J. Cost and benefits of implementing an occupational safety and health management system (OSH MS) in enterprises in Poland. Int J Occup Saf Ergon. 2012;18(2):181–193. DOI:10.1080/10803548.2012.11076927