?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
This study proposes new higher-order discretization methods of forward-backward stochastic differential equations. In the proposed methods, the forward component is discretized using the Kusuoka–Lyons–Ninomiya–Victoir scheme with discrete random variables and the backward component using a higher-order numerical integration method consistent with the discretization method of the forward component, by use of the tree based branching algorithm. The proposed methods are applied to the XVA pricing, in particular to the credit valuation adjustment. The numerical results show that the expected theoretical order and computational efficiency could be achieved.
1. Introduction
1.1. Problem
This study focuses on the discretization methods of forward-backward stochastic differential equations (FBSDEs). In particular, numerical methods for the following Equations (1) are discussed.
Let be a probability space with a Brownian filtration
, and
where
and
be the
-dimensional standard
-Brownian motion. We also let
denote the space of
-valued smooth functions defined on
whose derivatives of any order are bounded. We consider the following stochastic differential equations (SDEs):
where ,
, and
and
are appropriately smooth functions. Here, the forward component
is written in the Stratonovich form and the backward component
in the Ito form. Here,
denotes the Stratonovich integral and
the Ito integral respectively. Our aim is the numerical evaluation of
.
1.2. Background
The framework of FBSDE was first introduced by Bismut (Bismut Citation1973). Pardoux and Peng proved the existence and uniqueness of FBSDE in (Pardoux Citation1990) and established the Feynman–Kac formula in the general case in (Pardoux and Peng Citation1992). Since then, many researchers have investigated this field from both the theoretical and practical points of view. The smoothness of the solutions to FBSDEs was proved in (Crisan and Delarue Citation2012). The correspondence between FBSDEs and fully nonlinear partial differential equations (PDEs) was proved in (Cheridito et al. Citation2007). There are also substantial studies on financial applications of FBSDEs (Cvitanić and Karatzas Citation1993; Karoui, Pardoux, and Quenez Citation1997; Carmona Citation2008). Recently, the XVA pricing problems, that is to say, various valuation adjustments for derivative instruments, are formulated using FBSDEs in a unified manner (Piterbarg Citation2010; Burgard and Kjaer Citation2011; Haramiishi Citation2013a, Citation2013b; Lesniewski and Richter Citation2016; Borovykh, Pascucci, and Oosterlee Citation2018). Although we can formulate complicated problems using FBSDEs, it is not easy to solve the practical problems formulated by FBSDEs due to the difficulty of numerical treatments.
A number of numerical methods for FBSDEs have been proposed. They are classified into three categories. Methods in the first follow the nonlinear PDE approach. In this approach, we use the nonlinear Feynman–Kac formula to reduce the problem to numerical calculation of the corresponding nonlinear PDEs. This approach is also called the four-step scheme (Jin, Protter, and Yong Citation1994) and has been extensively studied in (Douglas, Jin, and Protter Citation1996; Jin, Shen, and Zhao Citation2008, Citation2008); in particular, higher-order discretization methods of forward SDEs were applied in (Milstein and Tretyakov Citation2006). The second category consists of the methods that follow the probabilistic approach, which is also called the simulation. As described below, in the simulation approach, the calculations consists of discretization and integration. A discretization method of backward SDEs was first discussed in (Nakayama Citation2002) then a discretization method for general class of FBSDEs was introduced in (Bouchard and Touzi Citation2004; Zhang Citation2004). The third category involves expansion techniques (Fujii and Takahashi Citation2015; Takahashi and Yamada Citation2016; Briand and Labart Citation2014; Pierre Citation2012). Some methods in this category are practically feasible and can derive some meaningful calculation formulas. However, we cannot know the true value when using these methods.
This study focuses on the methods in the second category, i.e., the simulation. In the simulation approach, the calculation is proceeded following two steps: the discretization step and the integration step. In the discretization step, a set of random variables (
) that approximates the processes
is constructed. Then in the integration step, we numerically calculate the conditional expectations of
. Since
usually depends on the conditional expectations of
, the numerical integration of
by naive Monte Carlo method that draws
samples from
to calculate
for every
would include
draws. This is practically infeasible. This problem is called nested simulation problem or multiple Monte Carlo problem. To overcome the problem, many methods have been proposed for both of the discretization and the integration steps, e.g., the quantization tree (Bally and Gilles Citation2003), the Malliavin integration by parts formula (Bouchard and Touzi Citation2004; Zhang Citation2004), the least square Monte Carlo method (Gobet, Lemor, and Warin Citation2005), the Picard iteration (Bender and Denk Citation2007), the sparse grid method (Zhang, Gunzburger, and Zhao Citation2013), the multistep method (Zhao, Zhang, and Lili Citation2010; Chassagneux Citation2014), the cubature method combined with the tree based branching algorithm (TBBA) (Crisan and Manolarakis Citation2012, Citation2014), the Runge–Kutta method (Chassagneux and Crisan Citation2014), and the numerical Fourier method (Maria and Cornelis Citation2016). In (Zhao, Zhang, and Lili Citation2010; Crisan and Manolarakis Citation2014; Chassagneux and Crisan Citation2014), higher-order discretization methods of FBSDEs have been proposed.
In this paper, a discretization method of order denotes the construction of sets of random variables
(
) such that
holds for all
. When
, we call the methods of higher-order.
Before the discretization methods of FBSDEs are studied, some studies had been conducted for higher-order discretization methods of forward SDEs (Kloeden and Platen Citation1999). Milstein proposed a higher order method for SDEs driven by one dimensional Brownian motion (Milstein Citation1975). Talay and Tubaro proved the applicability of Romberg extrapolation to the Euler–Maruyama (E–M) method (Talay and Tubaro Citation1990). In particular, Kusuoka (Kusuoka Citation2001) introduced a new higher-order discretization framework called KLNV-scheme (Kusuoka Citation2013) that enables higher-order weak approximations for the very general class of SDEs driven by multi-dimensional Brownian motions. Since then, the KLNV-scheme have been developed in (Ninomiya Citation2003a; Kusuoka Citation2004; Lyons and Victoir Citation2004; Ninomiya and Victoir Citation2008; Ninomiya and Ninomiya Citation2009); especially the efficiency of combining the higher order methods with the TBBA (Crisan and Lyons Citation2002) or the quasi–Monte Carlo method (QMC) (Niederreiter Citation1992; Ninomiya and Tezuka Citation1996) is noteworthy. Specifically, certain discretization methods have been proposed using discrete random variables (Lyons and Victoir Citation2004; Ninomiya Citation2003a). When we use these methods iteratively along the time steps, the support of the intermediate measures grows exponentially as the number of partitions increases. To overcome this problem, the TBBA (Crisan and Lyons Citation2002) was applied to these methods in (Ninomiya Citation2003b; Ninomiya and Mitsuzono Citation2004; Ninomiya Citation2010; Crisan and Ortiz-Latorre Citation2013). On the other hand, using the framework of KLNV-scheme and the Gaussian random variables, the Ninomiya–Victoir (N–V) (Ninomiya and Victoir Citation2008) and Ninomiya–Ninomiya (N–N) (Ninomiya and Ninomiya Citation2009) methods have been proposed as practically feasible second-order methods, and the method (Shinozaki Citation2016, Citation2017) as a third order method. Note that the N–V and N–N methods are implemented by using only substitutions and linear combinations in the same way as explicit Runge–Kutta methods are and are free from symbolic calculations. Hereinafter, these three methods are referred to as the Gaussian type KLNV-scheme. As mentioned in Remark 1.4 and Remark 1.5 of (Ninomiya and Victoir Citation2008), and Remark 6.2 of (Ninomiya and Ninomiya Citation2009), higher-order discretization methods enables significantly fast calculations especially when combined with QMC or similar techniques. We also note that the extrapolation techniques enables us to increase the order of some discretization methods of SDEs. It is proved that the arbitrary higher order can be achieved by combining with Romberg extrapolation (Kusuoka Citation2013) or Richardson extrapolation (Fujiwara Citation2006; Oshima, Teichmann, and Dejan Citation2012).
1.3. Results
In this paper, we present second and third order discretization methods of FBSDEs using the KLNV-scheme, the higher-order numerical integration methods, and the TBBA, by extending the works of Crisan and Manolarakis (Crisan and Manolarakis Citation2012, Citation2014). In particular, we achieve the third order method and the applicability to the problems driven by multidimensional Brownian motion. To overcome the difficulty of nested simulation, it is required to reduce the calculation cost significantly. To this end, we reduce the dimension of the integration by using the higher order discretization methods. In our proposed methods, the forward component is discretized using the Gaussian type KLNV-scheme with discrete random variables, and the backward component
using a higher-order numerical integration method suitable for the discretization method of the forward component; specifically, the N–V and N–N methods combined with the trapezoidal rule attain the second-order and the
method combined with the Simpson’s the third-order. In these methods, we construct random variables
on a discrete probability space. We approximate the law of
using the TBBA. We remark that we implemented TBBA method by using the depth-first tree traversal algorithm. This technique is essential for practical implementation, because memory explosion might occur without this technique.
In addition, we discuss the applications of the proposed methods to the XVA pricing, particularly to the credit valuation adjustment (CVA). Using the proposed methods, we calculate the CVA prices formulated by FBSDEs under the Black–Scholes and Heston models, which are usually considered to be hard to solve numerically. Our numerical results show that the expected theoretical order and computational efficiency are achieved. Moreover, we could observe the effectiveness of higher-order methods rather than the case of SDEs.
2. Notation and previous studies
In this section, we introduce some notations and previous studies on KLNV-scheme and FBSDE.
2.1. Notation
Let be a set of indices of vector fields and Brownian motion, and let
denote the set of all words consisting of elements of A (i.e., the free monoid generated by
,
). The empty word
is the identity of
. Let
be the free
-algebra with basis
and let
be the set of all
-coefficient formal series with basis
(i.e.,
and
). For
, we define the length of
as
, the order of
as
where
denotes the cardinality of a set
. We denote
for
.
For , let the product
be defined by
and the inner product by
and let . The Lie bracket is defined as
. We define
as the set of Lie polynomials in
, i.e., the smallest
-submodule of
including
and closed under the Lie bracket.
can be identified as a smooth vector field on
via
Let be the homomorphism from
to the
-algebra consisting of smooth differential operators over
such that
Here is the identity operator. For smooth vector fields
, we define the Lie bracket of vector fields as
. It is well known that
is also a smooth vector field on
, and thus
is a vector field for
. We denote
for
and
for
.
For a smooth vector field and
,
denotes the solution
to the following ODE:
By virtue of the chain rule is well-defined. We remark that
is a map from
to
. In addition, we have the following relation:
for , from the Taylor expansion formula.
2.2. KLNV-scheme for forward SDE
In this subsection, we introduce the discretization methods, which we use for the forward component .
denotes the space of Lipschitz functions defined on
,
denotes the Lipschitz norm, i.e.,
and denotes the uniform norm, i.e.,
for . Let us define a semigroup of linear operators
on
by
.
At first, we present an approximation theorem for the KLNV-scheme, based on (Kusuoka Citation2001, Citation2003) and (Kusuoka Citation2004).
Definition 1 (l-UFG condition (Kusuoka Citation2003)). Let be an integer. The vector fields
are said to satisfy the
-UFG condition, if for all
, there exists
satisfying
Then, we define the condition of approximation operators as follows.
Definition 2 (m-similar operator). Markov operator is said to be an
-similar operator if there exist
-valued random variables
such that
and
Here is defined for
as follows:
The intuitive understanding of this definition is that an -similar operator approximates the stochastic Taylor expansion of the solution to an SDE up to order
. Note that this definition has been slightly extended from the original definition used in (Kusuoka Citation2001, Citation2003; Kusuoka Citation2004).
Theorem 1 (Approximation theorem for the KLNV-scheme (Kusuoka Citation2004)). Assume that the vector fields of the SDE satisfy the -UFG condition and
is an
-similar operator. Then there exist positive constants
and
which depend only on
and the vector fields
and satisfy
and
for all .
Remark 1 (The regularity assumption on Φ). In the initial work of Kusuoka (Kusuoka Citation2001; Kusuoka Citation2004), Theorem 1 is proved on the assumption of . It is easily seen that this assumption can be relaxed to
, as pointed out in Section 3 of (Lyons and Victoir Citation2004).
Next, we introduce the discretization methods that follow the KLNV-scheme, particularly the Gaussian type KLNV-scheme from (Ninomiya and Victoir Citation2008; Ninomiya and Ninomiya Citation2009; Kusuoka Citation2013) and (Shinozaki Citation2017). For a comparison of these methods from the viewpoint of implementation and performance, refer to Section 4 of (Shinozaki Citation2017).
Theorem 2 (N–V (Ninomiya and Victoir Citation2008; Kusuoka Citation2013), N–N (Ninomiya and Ninomiya Citation2009; Kusuoka Citation2013) methods). Let and
be independent standard normal random variables,
Here, the parameters of are defined as follows:
by some .
Then, are 5-similar operators, and the N–V method
and N–N method
are discretization methods of order 2.
We denote by the composition
of
and
hereinafter.
Theorem 3 ( method (Shinozaki Citation2017)). Let
be a set of independent standard normal random variables and
Then is a 7-similar operator with
.
Remark 2 (Dimension of the 7-similar operator). As described in Remark 3.7 in (Shinozaki Citation2017), we can construct 7-similar operators for arbitrary by using the 7-moment similar family given in Theorem 3.1 of (Shinozaki Citation2017), although we give the explicit construction of a 7-similar operator only in the case of
there to avoid presenting a complicated long formula due to the complexity of
We can discuss the third order method for arbitrary in this paper therefore.
Remark 3 (Constructions of operators). As described in (Shinozaki Citation2017), the method is constructed based on a moment similar family (Kusuoka Citation2001) and the formula derived in (Takanobu Citation1995). On the other hand, the N–V and N–N methods are construed based on other ideas such as the splitting method of ordinary differential equations (ODEs)
In the following sections, denotes a 1 step discretization by the N–V method, i.e.,
or the N–N method, i.e.,
and by the
method, i.e.,
In addition, , and
denote the random variables required for the 1 step calculation in each method.
2.3. Forward-backward SDE
In this subsection, we introduce some known results about FBSDEs, which are used in the subsequent sections, from (Pardoux and Peng Citation1992) and (Crisan and Delarue Citation2012).
Theorem 4 (Nonlinear Feynman–Kac formula (Pardoux and Peng Citation1992)). Assume that in (1) are continuous. Then, there exists a continuous solution
to the following nonlinear PDE in viscosity sense,
and holds.
We denote by the solution to (3) hereinafter.
Theorem 5 (Estimation of derivative of u (Crisan and Delarue Citation2012)). Assume that the vector fields satisfy the
-UFG condition,
, and
. Then there exists a positive constant
, which depends on
,
and the vector fields
and not on
, such that
holds for and
, if
.
Remark 4. As noted in (Crisan and Delarue Citation2012), in the case when does not exist at point
,
will be understood as
where stands for the volume of the
-dimensional ball of radius
.
3. Discretization method of FBSDE
In this section, we present higher-order discretization methods for FBSDEs by combining the higher-order KLNV-schemes and some numerical integration methods. Specifically, we define the discrete KLNV-schemes for the forward component in Section 3.1 and describe the algorithms of higher-order discretization methods using higher-order rules such as the trapezoidal and Simpson’s rules for the backward non linear driver part
in Section 3.2. Then we estimate the discretization errors in Section 3.3.
3.1. Discretization method of the forward component: discrete KLNV-scheme
To define the discrete KLNV-schemes, we first define the discrete random variables. Let be a discrete probability space and
denotes the expectation under
.
Definition 3 (Discrete KLNV-scheme). Let ,
be the following discrete random variables on
:
We define ,
, and
by replacing
of
,
, and
with
respectively. We also define
and
by replacing
of
and
with
respectively.
and
are called discrete KLNV-scheme.
The following equations:
hold.
Remark 5 (Number of supports of and
). The numbers of supports of the random variables
, and
are summarized in . Hereinafter, we denote by
the number of support of
.
Table 1. Number of supports of ,
.
In addition, we define a filtration and
for
. Then,
,
are
-adapted random variables on
. Hereinafter, we denote by
the
th time interval
. The linear operators
and
on
are defined as follows:
3.2. Discretization method of the backward component
Given and
, we can construct
-adapted random variables
and
on
by implicitly solving the following equations:
for and
for , respectively.
Remark 6 (Approximation of process). In this paper, we propose the higher order discretization methods for FBSDEs whose drivers
are independent of
. For FBSDEs whose drivers
depend on
, our algorithms work only for the case where
is expressed as a function of
e.g., FBSDE (4.3) in (Crisan and Manolarakis Citation2012).
Note that in (Crisan and Manolarakis Citation2014), they successfully construct a second-order method in the case where depends on
, by using the algebraic structure of the cubature method on Wiener space. In the cubature method on Wiener space, the iterated Wiener integrals are directly replaced with the integrals of paths, as a result, one can retrieve the algebraic relations between the iterated Wiener integrals, i.e.,
where denotes the symmetric group of degree
. On the other hand, our algorithms cannot retrieve this algebraic structure, because we only match the moments of the iterated Wiener integrals by using appropriate polynomials of Gaussian random variables in the N–V, N–N, and
methods. Our algorithms cannot be easily extended in the same way as (Crisan and Manolarakis Citation2014) thus.
3.3. Estimation of the discretization error
For , we denote by
the map
. Let
and
be the 1 step discretization operators for the backward component defined as
and
for . We also define
as
for , and
as
for , backward inductively.
Then we have the following theorem, which claims that is the second-order method and
the third-order.
Theorem 6 (Main theorem). Assume that and the vector fields:
satisfy the
-UFG condition.
I. Let and
be the partition of
defined as
If , then there exist a polynomial
, which depends on
and the vector fields
and not on
, such that
II. Let and
be the partition of
defined as
for . If
, then there exist a polynomial
, which depends on
and the vector fields
and not on
, such that
Since the proof for the second-order method is essentially the same as that for the third-order method, we give the proof only for the third-order method.
To prove the theorem, let us first prepare the notation and some inequalities. We define for
and
. First, we estimate the discretization error of the forward component.
Lemma 1. There exist independent of
such that
hold for .
Proof. From Definition 3, are 5-similar operators and
7-similar. Using Theorem 1, we have the statement. □
Lemma 2. For , there exist
independent of
such that
and
hold for .
Proof. For ,
From Lemma 1 and from the Lipschitz property of , we have
Thus we have the following inequality:
when and
are small enough. Similarly, the following estimation:
holds. Using these inequalities iteratively, we have
Moreover, from the Lipschitz property of and Lemma 1,
This completes the proof. □
We denote by the largest integer less than or equal to
hereinafter. The following lemma shows the 1 step discretization error of the backward component.
Lemma 3. There exist polynomials and
, which depend on
and the vector fields
and not on
, such that
for and
for .
Proof. First, we decompose the left hand side as follows:
From the Lipschitz property of and Lemma 1, we have
where
and
Using stochastic Taylor expansion of around
, we have
Note that the equality is used here. In the same way, from the Lipschitz property of
and Lemma 1, we have,
where is a polynomial. Note that the last inequality hold since
.
Combining this inequality, the Lipschitz property of , and Lemma 1, we have
Inequalities (8) and (10), Theorem 5, and the definition of the partition (7) lead us to the following inequalities:
Note that the last inequality hold since . This completes the proof. □
Proof of Theorem 6. The discretization error can be decomposed as a telescopic sum and follows the inequality:
where if
is even and
if is odd. Using Lemma 2, we have
The last term is estimated as follows. From the definition of ,
From the Lipschitz property of , Lemma 1, 3, and (9), we have
where is a polynomial. From Lemma 3, we have
In the similar way, we have
We complete the proof of Theorem 6. □
Remark 7. From the proof of Theorem 6, it is easily seen that
holds. Therefore, in the third order method, it is also possible to use the trapezoidal rule to calculate the midpoint of the Simpson’s rule. Note that similar methods are discussed in (Chassagneux Citation2014).
Remark 8. (The conditions on ) In Theorem 6, we impose the conditions of
for the second order method and
for the third one. These conditions are relaxed compared to the conditions of
for the forward SDEs established in (Kusuoka Citation2001), since only the lower terms of stochastic Taylor expansion should be taken into consideration in the case of FBSDE as in (8).
4. TBBA
In this section, we introduce the TBBA (Crisan and Lyons Citation2002) and its efficient implementation for our problem. The TBBA was applied to the weak approximation problem of SDEs in (Ninomiya Citation2003b, Citation2010; Crisan and Ortiz-Latorre Citation2013).
In the last section, we constructed
as random variables on
; however, it becomes difficult to compute these random variables as
increases because
. Here
denotes the cardinality of a set
.
The TBBA solves this problem by randomly sampling important nodes from a huge tree. Let . Given the number of samples
, the aim of the TBBA is to construct a random measure
defined on some probability space
such that
where denotes the expectation under
and
the variance.
For the implementation, refer to the structured code in Appendix A.
4.1. Algorithm
To describe the construction of , we prepare the notation of a labeled tree as given in (Béla Citation1979).
Definition 4. A labeled tree is a pair of finite sets
that satisfy the following conditions:
1. , and
.
2. For each , if
and
, then
.
3. For two distinct elements , one of the followings holds:
(a) There exists a path from to
,
(b) There exists a path from to
,
(c) For some , there exist paths
to
and
to
,
where the path from to
denotes the sequence:
For each , there exists a unique vertex
such that for any
, there exists a path from
to
;
is called the root of
. We define a set of descendant nodes of the vertex
as
. Let
be a function from
to
. Then, the weight function
and the depth function
can be defined as follows:
We also define a set of leaves of as
. In this paper, we consider the labeled tree
such that
Here, denotes the number of support of
and
as described in Section 3.1.
Now, we present the algorithm. First, for , we define the random variable
as
We remind that denotes the largest integer less than or equal to
. We also let
. Given the number of samples
, let us define
as follows:
where . Then, we can define random variables
as
then, . In the previous studies on the TBBA, the following two propositions had been proved.
Theorem 7 (Crisan and Lyons Citation2002). satisfies the minimum variance property (13).
Theorem 8 (Ninomiya Citation2003b). For a bounded function ,
4.2. Efficient implementation
In addition, we use the technique for avoiding memory explosion: the depth-first tree traversal. Straightforward implementation of the TBBA causes memory explosion, even though the important nodes are sampled. We can overcome this problem by constructing with the depth-first tree traversal. For details of the algorithm, refer to Appendix A; the algorithm can be implemented easily by recursive programming techniques. In this technique, we do not require to keep information of all the nodes at once. Actually, we need to keep the information of
number of nodes for the second-order method, and
nodes for the third-order method.
5. Numerical results: XVA pricing
In this section, we first present the formulation of XVA pricing using the FBSDE without proof. Then, we describe the numerical results.
5.1. XVA pricing
The XVA is a valuation adjustment for the financial derivative to take various costs into consideration. Here, ‘X’ represents letters, ‘C’, ‘D’, ‘M’, ‘F’, and ‘K’. The major XVAs are listed in .
Table 2. Major XVAs.
The XVA pricing can be formulated using the nonlinear PDE (Piterbarg Citation2010; Burgard and Kjaer Citation2011), FBSDE (Lesniewski and Richter Citation2016; Borovykh, Pascucci, and Oosterlee Citation2018). In this paper, we introduce the formulation given by (Borovykh, Pascucci, and Oosterlee Citation2018). We can formulate the general XVA pricing by reflecting various adjustments to in (1). Consider a derivative contract between a bank and its counterparty. Under the no-arbitrage assumption,
is the underlying asset and
is the derivative price to the bank including the XVA, where
The parameters and functions of (15) are summarized in .
Table 3. Parameters of XVA.
In the following numerical experiments, we consider the CVA pricing problem with , i.e., the counterparty pays nothing if they default. Also we assume that the bank has only one transaction with the counterparty.
5.2. Black–Scholes model
First, we consider the pricing of an Asian option including CVA under the Black–Scholes model, i.e., the calculation of where,
Here we set the payoff function so that
. Setting
, and
, we consider the true value in this experiment as follows:
. This value was estimated using the third-order method with the number of partitions
and the sample number of TBBA as
. The accuracy of this value was validated using another method, specifically, the difference between this value and the estimated value using the second-order method (N–V) where
was less than
.
Remark 9 (UFG condion in the Black–Scholes model case). in (16) is the solution to the following Stratonovich form SDE:
where
Then, it is easily seen that for with
,
,
holds. Thus the vector fields satisfy the 3-UFG condition.
Remark 10 (Partitions of time). In the following numerical experiment, we use the even partitions, i.e., , instead of (6) and (7). As discussed in Remark 4.1 of (Shinozaki Citation2017), this is justified only for the N–V and N–N methods of the forward SDEs, however the following numerical experiments show that it also works for our case.
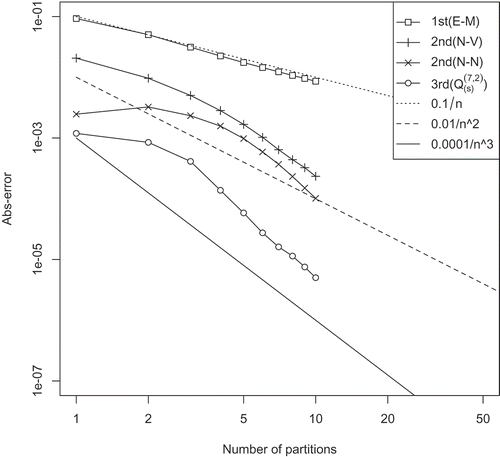
The relations between the discretization error and the number of partitions are plotted in . To obtain these results, we used the TBBA with . indicates that the expected theoretical orders are obtained using each method.
In addition, the calculation costs for the accuracy are summarized in . The higher-order methods are more effective rather than the case of forward SDEs. In fact, if we use the E–M method, it seems to be required to set in the
range from and a tree is too big to converge; as a result, the TBBA didn’t converge even if we set
. In addition, the second and the third order methods enable us to make enough small trees to be integrable without the TBBA in this case.
Remark 11 (The current industry practices). Banks usually calculate the XVA for each netting set, i.e., a set of transactions with the counterparty which is usually several hundreds of derivative instruments. This increases the dimension of the XVA calculation, hence it becomes hard to calculate the XVA especially when we formulate by the FBSDEs as (15). Therefore, in the current financial industry practice, the XVA is calculated by assuming that the derivative contracts satisfy some conditions. For example, the CVA can be formulated as the solution to the following equations by assuming the risk-free closed-out, i.e., the mark-to-market values of the derivatives do not include the CVA:
Table 4. CVA pricing under the BS model – Requirements for accuracy.
This type of formulation was first introduced by (Darrell and Huang Citation1996) and analyzed for the modern setting for the CVA calculation in (Fujii and Takahashi Citation2013). It can be seen that the risk-free closed-out CVA is approximated as a first order sensitivity of the CVA formulated by (16), which is called the risky closed-out CVA, with respect to the credit spread.
The quantitative impact of the assumption is investigated in (Brigo and Morini Citation2011; Burgard and Kjaer Citation2011; Gregory and German Citation2013; Piterbarg Citation2015). In our setting, the differences of the risky closed-out CVA (16) and the risk-free closed-out CVA (17) under the Black–Scholes model are summarized in . Here, we calculate where
, setting
, and using the third order method with
.
Table 5. CVA pricing under the BS model – Requirements for accuracy.
These values are calculated using the third-order method with the number of partitions and the sample number of TBBA as
.
5.3. Heston model
Next, we consider the pricing of an Asian option including the CVA under the Heston model (Heston Citation1993), i.e., the calculation of where,
Here we set the payoff function again. Setting
, and
, we consider the true value as follows in this experiment:
. This value was estimated using the third-order method with the number of partitions
and the sample number of TBBA
. We validated the accuracy of this value using another method, the difference between this value and the estimated value using the 2nd order method (N–V) where
was less than
.
Remark 12 (UFG condion in the Heston model case). in (18) is the solution to the following Stratonovich form SDE:
where
Setting
we see that
From these equations we have the following algebraic relations:
Thus we can see that the vector fields satisfy the 3-UFG condition. We note that this algebraic structure (19) of the Heston model is also discussed in (Morimoto and Sasada Citation2017).
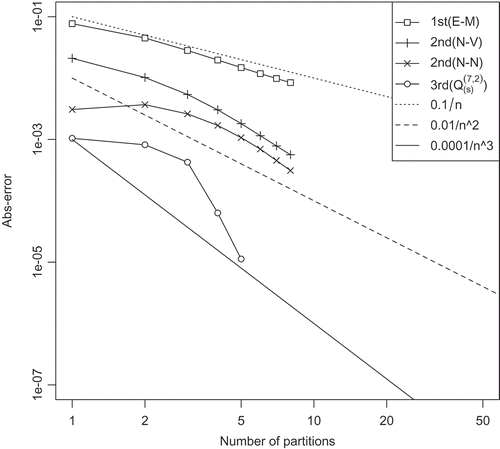
The relations between the discretization error and the number of partitions are plotted in . To obtain these results, we used the TBBA with . indicates that the expected theoretical orders are obtained using each method again.
Also, the calculation costs for accuracy are summarized in . As mentioned in Remark 4.6 of (Shinozaki Citation2017), the N–V method has analytical or approximate solutions to the ODEs for the Heston model; this ensures the efficient calculation. In addition, in the N–V method, the number of random variables in the 1-step calculation is less, which makes the tree small and increases the efficiency. On the other hand, the third-order method needs a larger number of random variables than the Black–Scholes case, which decreases the efficiency.
Table 6. CVA pricing under the Heston model – Requirements for accuracy.
Correction Statement
This article has been republished with minor changes. These changes do not impact the academic content of the article.
Disclosure statement
No potential conflict of interest was reported by the authors.
Additional information
Funding
References
- Bally, V., and P. Gilles. 2003. “A Quantization Algorithm for Solving Multidimensional Discrete- Time Optimal Stopping Problems.” Bernoulli 9 (6): 1003–1049. doi:10.3150/bj/1072215199.
- Béla, B. 1979. Graph Theory: An Introductory Course. Graduate texts in mathematics. New York: Springer Verlag.
- Bender, C., and R. Denk. 2007. “A Forward Scheme for Backward SDEs.” Stochastic Processes and Their Applications 117 (12): 1793–1812. doi:10.1016/j.spa.2007.03.005.
- Bismut, J. M. 1973. “Conjugate Convex Functions in Optimal Stochastic Control.” Journal of Mathematical Analysis and Applications 44 (2): 384–404. doi:10.1016/0022-247X(73)90066-8.
- Borovykh, A., A. Pascucci, and C. W. Oosterlee. 2018. “Efficient Computation of Various Valuation Adjustments under Local Lévy Models.” SIAM Journal on Financial Mathematics 9 (1): 251–273. doi:10.1137/16M1099005.
- Bouchard, B., and N. Touzi. 2004. “Discrete-time Approximation and Monte-Carlo Simulation of Backward Stochastic Differential Equations.” Stochastic Processes and Their Applications 111 (2): 175–206. doi:10.1016/j.spa.2004.01.001.
- Briand, P., and C. Labart. 2014. “Simulation of BSDEs by Wiener Chaos Expansion.” The Annals of Applied Probability 24 (3): 1129–1171. doi:10.1214/13-AAP943.
- Brigo, D., and M. Morini. 2011. “Close-out Convention Tensions.” Risk Magazine 24 (12): 74–78.
- Burgard, C., and M. Kjaer. 2011. “PDE Representations of Derivatives with Bilateral Counterparty Risk and Funding Costs.” The Journal of Credit Risk 7: 75–93. doi:10.21314/JCR.2011.131.
- Carmona, R. 2008. Indifference Pricing: Theory and Applications. Princeton, NJ: Princeton University Press.
- Chassagneux, J.-F. 2014. “Linear Multistep Schemes for BSDEs.” SIAM Journal on Numerical Analysis 52 (6): 2815–2836. doi:10.1137/120902951.
- Chassagneux, J.-F., and D. Crisan. 2014. “Runge–Kutta Schemes for Backward Stochastic Differential Equations.” The Annals of Applied Probability 24 (2): 679–720. doi:10.1214/13-AAP933.
- Cheridito, P., H. Mete Soner, N. Touzi, and N. Victoir. 2007. “Second-order Backward Stochastic Differential Equations and Fully Nonlinear Parabolic PDEs.” Communications on Pure and Applied Mathematics 60 (7): 1081–1110. doi:10.1002/(ISSN)1097-0312.
- Crisan, D., and F. Delarue. 2012. “Sharp Derivative Bounds for Solutions of Degenerate Semi- Linear Partial Differential Equations.” Journal of Functional Analysis 263 (10): 3024–3101. doi:10.1016/j.jfa.2012.07.015.
- Crisan, D., and K. Manolarakis. 2012. “Solving Backward Stochastic Differential Equations Using the Cubature Method: Application to Nonlinear Pricing.” SIAM Journal on Financial Mathematics 3 (1): 534–571. doi:10.1137/090765766.
- Crisan, D., and K. Manolarakis. 2014. “Second Order Discretization of Backward SDEs and Simulation with the Cubature Method.” Annals of Applied Probability 24 (2): 652–678. doi:10.1214/13-AAP932.
- Crisan, D., and S. Ortiz-Latorre. 2013. “A Kusuoka–Lyons–Victoir Particle Filter.” In Proc. R. Soc. A. Mathematical, Physical and Engineering Sciences, 469, 20130076. Royal Society.
- Crisan, D., and T. Lyons. 2002. “Minimal Entropy Approximations and Optimal Algorithms.” Monte Carlo Methods and Applications 8 (4): 343–356. doi:10.1515/mcma.2002.8.4.343.
- Cvitanić, J., and I. Karatzas. 1993. “Hedging Contingent Claims with Constrained Portfolios.” The Annals of Applied Probability 3: 652–681. doi:10.1214/aoap/1177005357.
- Darrell, D., and M. Huang. 1996. “Swap Rates and Credit Quality.” The Journal of Finance 51 (3): 921–949. doi:10.1111/j.1540-6261.1996.tb02712.x.
- Douglas, J., M. Jin, and P. Protter. 1996. “Numerical Methods for Forward-backward Stochastic Differential Equations.” The Annals of Applied Probability 6 (3): 940–968. doi:10.1214/aoap/1034968235.
- Fujii, M., and A. Takahashi. 2013. “Derivative Pricing under Asymmetric and Imperfect Collateralization and CVA.” Quantitative Finance 13 (5): 749–768. doi:10.1080/14697688.2012.738931.
- Fujii, M., and A. Takahashi. 2015. “Perturbative Expansion Technique for Non-linear FBS- DEs with Interacting Particle Method.” Asia-Pacific Financial Markets 22 (3): 283–304. doi:10.1007/s10690-015-9201-7.
- Fujiwara, T. 2006. “Sixth Order Methods of Kusuoka Approximation.” PreprintSeries, Graduate School of Mathematical Sciences, Univ. Tokyo
- Gobet, E., J.-P. Lemor, and X. Warin. 2005. “A Regression-based Monte Carlo Method to Solve Backward Stochastic Differential Equations.” The Annals of Applied Probability 15 (3): 2172–2202. doi:10.1214/105051605000000412.
- Gregory, J., and I. German. 2013. “Closing Out DVA?” Risk Magazine 26 (1): 96–100.
- Haramiishi, M. 2013a. “Probabilistic Methods for Inversion Problems of CVA Using the Interacting Particle Method (in Japanese).” IMES Discussion Paper Series, Bank of Japan, (J-12)
- Haramiishi, M. 2013b. “Probabilistic Methods for Inversion Problems of CVA Using the Marked Branching (in Japanese).” IMES Discussion Paper Series, Bank of Japan, (J-11).
- Heston, S. 1993. “A Closed-form Solution for Options with Stochastic Volatility with Applications to Bond and Currency Options.” Review of Financial Studies 6 (2): 327–343. doi:10.1093/rfs/6.2.327.
- Jin, M., J. Shen, and Y. Zhao. 2008. “On Numerical Approximations of Forward-backward Stochastic Differential Equations.” SIAM Journal on Numerical Analysis 46 (5): 2636–2661. doi:10.1137/06067393X.
- Jin, M., P. Protter, and J. Yong. 1994. “Solving Forward-backward Stochastic Differential Equations Explicitly―a Four Step Scheme.” Probability Theory and Related Fields 98 (3): 339–359. doi:10.1007/BF01192258.
- Karoui, N. E., E. Pardoux, and M. C. Quenez. 1997. “Reflected Backward SDEs and American Options.” Numerical Methods in Finance 13: 215–231.
- Kloeden, P., and E. Platen. 1999. Numerical Solution of Stochastic Differential Equations. New York: Springer.
- Kusuoka, S. 2001. “Approximation of Expectation of Diffusion Process and Mathematical Finance.” In Proceedings of Final Taniguchi Symposium, volume 31 of Advanced Studies in Pure Mathematics, 147–165. Nara, Japan.
- Kusuoka, S. 2003. “Malliavin Calculus Revisited.” Journal of Mathematical Sciences University of Tokyo 10 (2): 261–277.
- Kusuoka, S. 2004. “Approximation of Expectation of Diffusion Processes Based on Lie Algebra and Malliavin Calculus.” Advances in Mathematical Economics 6: 69–83.
- Kusuoka, S. 2013. “Gaussian K-scheme: Justification for KLNV Method.” Advances in Mathematical Economics 17: 71–120.
- Lesniewski, A., and A. Richter. 2016. Managing counterparty credit risk via BSDEs
- Lyons, T., and N. Victoir. 2004. “Cubature on Wiener Space.” In Proceedings of the Royal Society of London A: Mathematical, Physical and Engineering Sciences, 460, 169–198.
- Maria, J. R., and W. O. Cornelis. 2016. “Numerical Fourier Method and Second-order Taylor Scheme for Backward SDEs in Finance.” Applied Numerical Mathematics 103: 1–26. doi:10.1016/j.apnum.2015.12.003.
- Milstein, G. 1975. “Approximate Integration of Stochastic Differential Equations.” Theory of Probability & Its Applications 19 (3): 557–562. doi:10.1137/1119062.
- Milstein, G., and M. Tretyakov. 2006. “Numerical Algorithms for Forward-Backward Stochastic Differential Equations.” SIAM Journal on Scientific Computing 28 (2): 561–582. doi:10.1137/040614426.
- Morimoto, Y., and M. Sasada. 2017. “Algebraic Structure of Vector Fields in Financial Diffusion Models and Its Applications.” Quantitative Finance 17 (7): 1–13.
- Nakayama, T. 2002. “Approximation of BSDE’s by Stochastic Difference Equation’s.” Journal of Mathematical Sciences University of Tokyo 9: 257–277.
- Niederreiter, H. 1992. Random Number Generation and quasi-Monte Carlo Methods. Philadelphia: SIAM.
- Ninomiya, M. 2010. “Application of the Kusuoka Approximation with a Tree-based Branching Algorithm to the Pricing of Interest-rate Derivatives under the HJM Model.” LMS Journal of Computation and Mathematics 13: 208–221. doi:10.1112/S146115700800048X.
- Ninomiya, M., and S. Ninomiya. 2009. “A New Higher-order Weak Approximation Scheme for Stochastic Differential Equations and the Runge–Kutta Method.” Finance and Stochastics 13 (3): 415–443. doi:10.1007/s00780-009-0101-4.
- Ninomiya, S. 2003a. “A New Simulation Scheme of Diffusion Processes: Application of the Kusuoka Approximation to Finance Problems.” Mathematics and Computers in Simulation 62 (3): 479–486. doi:10.1016/S0378-4754(02)00251-3.
- Ninomiya, S. 2003b. “A Partial Sampling Method Applied to the Kusuoka Approximation.” Monte Carlo Methods and Applications 9 (1): 27–38. doi:10.1163/156939603322587443.
- Ninomiya, S., and M. Mitsuzono. 2004. “A Partial Sampling Method for Approirnation of Expectation of Diffusion Processes by Using the Exotic Filters.” preprint.
- Ninomiya, S., and N. Victoir. 2008. “Weak Approximation of Stochastic Differential Equations and Application to Derivative Pricing.” Applied Mathematical Finance 15 (2): 107–121. doi:10.1080/13504860701413958.
- Ninomiya, S., and S. Tezuka. 1996. “Toward Real-time Pricing of Complex Financial Derivatives.” Applied Mathematical Finance 3 (1): 1–20. doi:10.1080/13504869600000001.
- Oshima, K., J. Teichmann, and V. Dejan. 2012. “A New Extrapolation Method for Weak Approximation Schemes with Applications.” Annals of Applied Probability 22 (3): 1008–1045. doi:10.1214/11-AAP774.
- Pardoux, E. 1990. “S Peng and Others. Adapted Solution of Backward Stochastic Differential Equations.” Systems & Control Letters 4: 55–61. doi:10.1016/0167-6911(90)90082-6.
- Pardoux, E., and S. Peng. 1992. “Backward Stochastic Differential Equations and Quasilinear Parabolic Partial Differential Equations.” In Stochastic Partial Differential Equations and Their Applications, 200–217. Boston, MA: Springer.
- Pierre, H.-L. 2012. “Cutting CVA’s Complexity.” Risk 25 (7): 67.
- Piterbarg, V. 2010. “Funding beyond Discounting: Collateral Agreements and Derivatives Pricing.” Risk 10 (2): 97–102.
- Piterbarg, V. 2015. “A Nonlinear PDE for XVA by Forward Monte Carlo.” Risk 10.
- Shinozaki, Y. “Higher Order K-scheme and Application to Derivative Pricing.” In Proceedings of the 47th ISCIE International Symposium on Stochastic Systems Theory and Its Applications, Honolulu, December 2015, 137–143, 2016.
- Shinozaki, Y. 2017. “Construction of a Third-order K-scheme and Its Application to Financial Models.” SIAM Journal on Financial Mathematics 8 (1): 901–932. doi:10.1137/16M1067986.
- Takahashi, A., and T. Yamada. 2016. “An Asymptotic Expansion for Forward–Backward SDEs: A Malliavin Calculus Approach.” Asia-Pacific Financial Markets 23 (4): 337–373. doi:10.1007/s10690-016-9220-z.
- Takanobu, S. 1995. “Multiple Stochastic Integrals Appearing in the Stochastic Taylor Expansions.” Journal of the Mathematical Society of Japan 47 (1): 67–92. doi:10.2969/jmsj/04710067.
- Talay, D., and L. Tubaro. 1990. “Expansion of the Global Error for Numerical Schemes Solving Stochastic Differential Equations.” Stochastic Analysis and Applications 8 (4): 483–509. doi:10.1080/07362999008809220.
- Zhang, G., M. Gunzburger, and W. Zhao. 2013. “A Sparse-grid Method for Multidimensional Backward Stochastic Differential Equations.” Journal of Computational Mathematics 31 (3): 221–248. doi:10.4208/jcm.1212-m4014.
- Zhang, J. 2004. “A Numerical Scheme for BSDEs.” Annals of Applied Probability 14 (1): 459–488. doi:10.1214/aoap/1075828058.
- Zhao, W., G. Zhang, and J. Lili. 2010. “A Stable Multistep Scheme for Solving Backward Stochastic Differential Equations.” SIAM Journal on Numerical Analysis 48 (4): 1369–1394. doi:10.1137/09076979X.
Appendix
Appendix a structured program for the implementation of the third order method.
The proposed third order method can be implemented recursively. As an example, a structured code is presented in this appendix.
Input : Number of partitions (Maxdepth), Number of samples
(Particles), Vector fields
,
Output : in (5)
1 Function Main ():
2 root = NewNode(Particles, 0, 1);
3 TBBAtraverse(root);
4 return root.BwdVal
1 Struct Node contains
2 int particle;
3 int depth;
4 int prob;
5 struct Node **children;
6 int chidrenNum;
7 double fwdval;
8 double bwdval;
9 end
10 Function NewNode (Particle , Depth
, Prob
): /*Setter*/
11 Node *node;
12 node = (Node *)malloc(sizeof(Node));
13 node.particle = ;
14 node.depth = ;
15 node.prob = ;
16 node.childrenNum = 0;
17 return node;
1 Function TBBATraverse (Node node): /*Main body of the algorithm*/
2 if node,depth = = Maxdepth then
3 node.BwdVal = (node
FwdVal); /*Set the terminal condition*/
4 else
5 int NumP;
6 NumP = node.particle;
7 for do
8 Generate a scenario of with probability
9 /*Definition 3*/
10 if j = = k then
11 NumPDec = Nump
12 else
13 Generate a random variable TBBA (, Nump) in (14);
14 NumPDec = TBBA (, Nump);
15 end
16 if NumPDec ! = 0 then
17 node.childnum ++;
18 node.child[childnum] = Newnode(NumPDec, node.depth+1, node.prob*);
19 node.child.FwdVal = 1stepFwd(node.FwdVal, );
20 TBBATraverse(node.child)/*Call TBBATraverse recursively*/
21 node.children[node.childnum] = node.child;
22 NumP = NumP-NumPDec;
23 else
24 node.BwdVal = 1stepBwd(node);
25 end
26 end
27 end
1 Function 1stepBwd(node) (Node node):
2 if node.depth = = Maxdepth-1 then
3 = 0;
4 = 0;
5 for do
6 + =
(node.children[j].BwdVal);
7 + =
f(node.children[j].FwdVal,node.children[j].BwdVal);
8 end
9 Solve (5) implicitly;
10 else
11 = 0;
12 = 0;
13 = 0;
14 = 0;
15 for do
16 + =
(node.children[j].BwdVal);
17 + =
f(node.children[j].FwdVal,node.children[j].BwdVal);
18 for do
19 + =
(node.children[j].children[k].BwdVal);
20 + =
21 f(node.children[j].children[k].FwdVal,node.children[j].children[k].BwdVal);
22 end
23 end
24 Solve (5) implicitly;
25 end
26 Function 1stepFwd(FwdVal, ) FwdVal,
:
27 Generate from
,
;
28 return
Appendix B Convergence of the TBBA
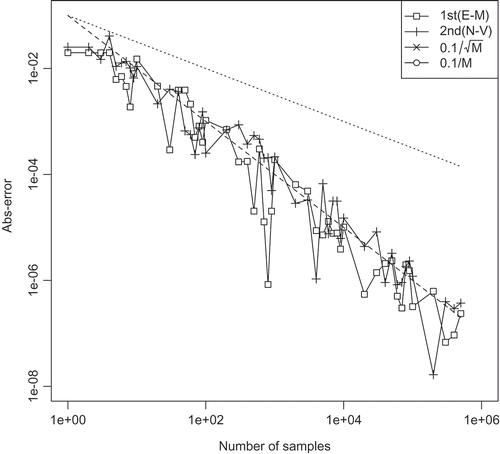
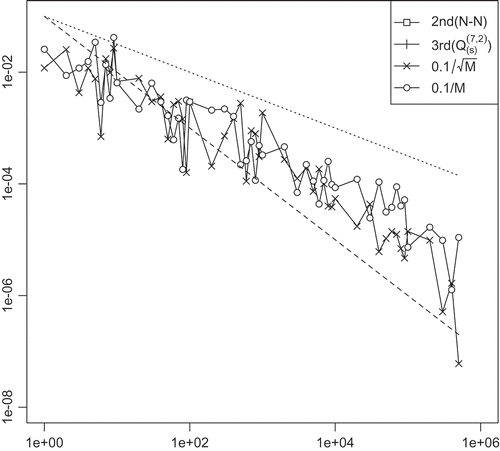
In this Appendix, we present the numerical result of convergence of the TBBA. The relations between the integration error and the sample number of TBBA
of each method with
are plotted in , .
We can see that the expected theoretical orders given in Theorem 8 are obtained in each method.