ABSTRACT
‘Interoperability’ means the ability for two different and independent information and communication technology (ICT) systems to exchange information and use that information. Whether or to what extent ICT interoperability needs to be regulated vis-a-vis the new technological challenges, poses a compelling question for the law and policy makers. Given this overarching question, this study first attempts to evaluate the issue from a multidisciplinary legal viewpoint and secondly examines the architectural settings of cloud computing and the Internet of Things (IoT). It is concluded that a layered regulatory model can respond to the ICT interdependent layers, as peculiarities of both the cloud and the IoT architectures are all-encompassed by such a model. It is also considered that a bottom-up, ex-ante and holistic approach developed under the layered regulatory model could address wide-ranging gatekeeping activities, responding not only competition concerns but also techno-social concerns, which constitute the main thread of ICT interoperability and accompanying problems. Finally, it is proposed this model can be transposed into the EU law, and to that end, it is suggested that the model replace the core measures of the electronic communications regulatory framework, along with a set of principles i.e. transparency, fairness, accountability and corresponding remedies.
KEY WORDS:
1. Introduction
‘Interoperability’ means the ability for two different and ICT systems to exchange information and use that information.Footnote1 Interoperability is crucial for running ICT networks and services, serving as a central thread for meeting the ICT-inclusive needs of the society. It is remarkable that interoperability centric measures are embodied under pertinent rules i.e. intellectual property legislation, competition law and electronic communications regulatory framework (ECRF) in the EU law, for various concerns like protecting competition or consumers or enhancing compatibility of computer programs.
Each body of the legal regulations has different objectives and means to accomplish their respective objectives. For instance, pre-defined tools and mechanisms under the EU copyright regime e.g. regarding reverse engineering, aim to ensure interoperability between computer programs.Footnote2 EU competition law, on the other hand, focuses on consumer welfare and protecting competition most often by means of ex-post interventions, such as remedies addressing ‘abuse of dominance’.Footnote3 Under the ECRF, one would come across more specific objectives e.g. ensuring ‘end-to-end connectivity’ and obligations e.g. regarding network interconnection, along with consummate ex-ante powers granted to the national regulatory authorities (NRAs). While EU competition law does not acknowledge interoperability as a directly applicable principle or rule, ECRF mandates interoperability in a variety of situations e.g. when necessary to ensure end-to-end connectivity.Footnote4
Although interoperability has so far figured as one of the important policy items of the EU agenda, it has not been translated into regulatory governance at the equivalent level. While the ICT-based transformation, being echoed in the fourth industrial revolution or Web 4.0 paradigm, has unravelled new challenges e.g. surrounding AI, cloud computing, the IoT, these have yet to be resolved from a broader perspective incorporating interoperability-based concerns. From this point of view, whether or to what extent interoperability needs to be regulated from a holistic perspective poses an overarching research question for the EU policy makers. While this arises a matter for all the policy makers and regulators globally, wider set of rules and remedies adopted and implemented under EU law offers a more convenient medium for research for the purpose of this study.Footnote5
Pursuing a holistic perspective means the ICT networks and services being considered not only from the technical interoperability perspective but also from a future-proof regulatory viewpoint. Having said that, the current EU legal framework firstly needs to be evaluated from the multidisciplinary legal viewpoint. Secondly, interoperability-related concerns need to be revitalized reflecting on the current and emerging ICTs. Given this, first and foremost, interoperability regulations under the intellectual property legislation, competition law and ECRF are investigated within this article. This is followed by an examination of the architectural underpinnings of cloud computing and the IoT, considering these widely represent the emerging technologies posing very interoperability needs and challenges.
Doctrinal analysis of the EU law i.e. concerning intellectual property legislation, competition law and ECRF, denote disaggregated rules for ‘interoperability’, along with partial solutions and shortcomings against the underlying concerns e.g. lock-in, innovation, information flows. In this regard, the aim of the study covers not only unveiling status quo based on the distinctive rules of the EU law, but also ensuring that findings from the multi-disciplinary legal analysis are complemented by an architectural review of the emerging technologies, i.e. cloud computing and the IoT. Behind this aim lies the idea that the underlying architectural elements serve as the gateways to consumers’ online activities and would pose potential challenges as to the ICT interoperability.
It is found through this second component of the research that, interoperability cuts across the interdependent layers which mean building blocks for the ICT landscape, not limited to cloud computing and the IoT. Not only the internal elements i.e. ‘infrastructure’, ‘platform’ and ‘application’ layers for the cloud computing and ‘perception’, ‘access’ and ‘application’ layers for the IoT, but also the external elements i.e. ‘content’ layer mean a great many interdependencies. This entails both ‘competition’ and ‘cooperation’ across the layers as particularly manifested in the cloud ecosystems and would be echoed with ‘coopetition’. As the cloud ecosystems manifest, interoperability-related concerns largely disappear in the case of coopetition; yet, the degree to what extent coopetition prevails would turn the tide, as could be seen through the case of the IoT. These complementary, but not conflicting, findings offer a broadly comparable picture for the ICT settings in general, as the layering is applicable to all the ICT platforms and networks.
This study then focuses on the question of what regulatory policy would effectively deal with the interdependent layers, which is key to ICT interoperability. Against this background question, the ‘layering theory’ has been examined and ‘layering’ as a concept is found to be able to respond the layer interdependencies for its very responsive and adaptive nature.Footnote6 In this vein, the layers of the (Internet Protocol) IP stack, from the bottom to the top, have been revisited, elaborated and then embedded into an ex-ante regulatory model called ‘layered regulatory model’.
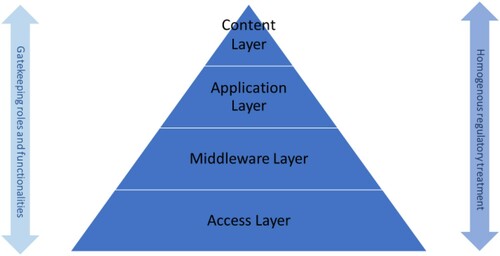
According to this newly proposed model, the ‘access’, ‘middleware’, ‘application’ and ‘content’ layers build up the layout for the needed holistic and technologically neutral treatment of interoperability-related concerns. It is considered that this ‘layered regulatory model’ is fit-for-purpose in dealing with such concerns from a broadly minded vision given the cross-layer problems and the activities depicted by the ‘network gatekeeping’ or simply ‘gatekeeping’.Footnote7
While ‘network gatekeeping’ is developed to mean ‘the process of controlling information as it moves through a gate (a network or its sections)’ (Barzilai-Nahon Citation2008, 1496), the pervasiveness of gatekeeping activities across the interdependent layers compels the regulatory mindset to be expanded against the interoperability related concerns. Within this study, such concerns have been categorized as comprising; (i) competition concerns and (ii) techno-social concerns.Footnote8 Under this broadened mindset, whereas the former focuses on consumer welfare from the perspective of competition law and policy, the latter entails discriminatory, biased and non-ethical layer activities, often being represented by AI-driven manipulations. At this point, this study suggests ‘gatekeeping’ finds its true and widest meaning under the proposed model whereby AI-based manipulations that affect consumer behaviours and decisions are encompassed and addressed alongside other restrictions over interoperability, i.e. based on exploitation of IPRs and technological protection measures (TPMs).Footnote9
Summing it up, the proposed ‘layered regulatory model’ is found to respond to the ICT interdependencies, having a forward-looking character against the so-called gatekeeping activities. By reinvigorating ‘gatekeeping’ along with ‘layering’ it is considered the ‘layered regulatory model’ can effectively deal with broadly minded concerns surrounding ICT interoperability, including the AI algorithms that are biased, discriminatory or unfairly selective. To ensure such activities run over these algorithms as well as other interoperability restrictions are addressed, a bottom-up perspective is upheld ending up an overarching legal framework within which it is proposed the core measures of the ECRF be replaced with a set of principles and corresponding remedies. This proposal emanates from the normative framework structured within the layered model, considering it all addresses the infrastructural and behavioural aspects that are underlaid with gatekeeping roles and functionalities across the ICT layers. Given the wide-ranging competition and techno-social concerns surfacing in this context and the response developed by the proposed model, it is concluded this model should have a supra role to play against the existing ex-ante and ex-post competition rules, except for their exclusive areas of regulation, i.e. universal service obligations or merger reviews.
2. Regulation of interoperability under EU law: status quo
Concerning interoperability, the EU legal frameworks i.e. intellectual property legislation, competition law and sector-specific regulations, embody distinctive rules and measures in their respective domains. This results in disparate bodies of law, incorporating distinct goals and accompanying instruments pursued by each of them. Below, these legal frameworks are examined with a view to investigate whether the existing legal system can cope with the lack of ICT interoperability and related competition and techno-social concerns.
2.1. Intellectual property legislation
From the viewpoint of the intellectual property rights (IPRs), the interoperability debate revolves around rightsholders concealing the interface specifications, and using the legal mechanisms e.g. copyright, patent and anti-circumvention laws to prevent any decryption or decompilation which aims at uncovering such specifications (Band and Katoh Citation2011, 184). In each side of the Atlantic, interoperability needs of the software developers are acknowledged and echoed with a legal response in that exceptions are created under the copyright regimes both in the USA and the EU concerning the computer programs.
In the EU, the copyright regime regarding the computer programs is governed by the Directive 2009/24/EC (Software Directive Citation2009). Under Article 6(1) of the Software Directive is acknowledged an exception to the copyright protection of the computer programs known as ‘decompilation’ aiming at mutual functionality of non-interoperable computer programs. According to this provision, authorization from the rightsholder of a computer program is not required for reproduction or translation of the program in question, provided that these acts are ‘indispensable to obtain the information necessary to achieve the interoperability of an independently created computer program with other programs’.Footnote10 Another exception to the copyright protection of the computer programs is the ‘reverse engineering’, as acknowledged under Article 5 of the Software Directive, where interoperability is not sought as a pre-requisite. Article 5(3) of the Directive allows any person ‘to observe, study or test the functioning of the program in order to determine the ideas and principles which underlie any element of the program’ without the authorization of the rightsholder. Notwithstanding, the designated acts i.e. decompilation to achieve interoperability are permitted within certain boundaries i.e. code not to be disseminated, alongside the idea-expression dichotomy and other rules regarding the copyrightability of software.
For over a decade, there is an ongoing debate over the ‘functional’ behaviours of a computer program that covers the APIs and whether such interfaces could be deemed as an exception, as ideas and/or principles underlying the computer program in question. This question is remarkably important as the APIs would then be imitated or reproduced, if not copied, by third parties who could create derivative software on top of the existing ones.
Regarding this issue, the Court of Justice of the EU (CoJ)’s ruling in SAS Institute Inc v World Programming Ltd (SAS v WPL Citation2012) is a landmark decision, where the Court held that ‘neither the functionality of a computer program nor the programming language and the format of data files used in a computer program in order to exploit certain of its functions constitute a form of expression’.Footnote11 However, APIs were not classified as one of the non-copyrightable elements falling outside the remit of copyright protection for computer programs under the EU law as per this ruling.Footnote12 Copyrightability of interfaces being left unsettled both under the Directive and the CoJ’s jurisprudence, the functional character of APIsFootnote13 and the merging of ideas and expression on them,Footnote14 blur the distinction based on the so-called dichotomy, with respect to the APIs which are of key importance as to interoperability.
Under the EU law, patentability of software, including interfaces, is less controversial. Under the European Patent Convention (EPC) and the relevant case-law, there is no bar to patent protection for the inventions that are implemented through computer programs, if that implementation represents the solution to a technical problem (Zingales Citation2016, 9). Given the fact that patents are application-specific, when access to the information contained in the interfaces does not imply the ‘making’ or the ‘using’ of the patented invention, there would be no patent infringement (Otero Citation2015, 82–83). On the other hand, patent protection for a single software component could prevent the ‘making’ or ‘using’ of the whole of a complex program including the temporary uses required for decompilation or reverse engineering (Weston Citation2015, 241). From this point of view, patentability of computer programs would have unpredictable effects of hindering interoperability. Moreover, within a computer program there often exists patented applications/inventions and copyrighted software elements. The more complex a program is, the more difficult it will be to access interfaces through reverse engineering (Samuelson Citation2009, 1961). This complexity is augmented by subordinated IPRs such as sui generis databases, trade secrets, etc. as well as TPMs which reside and operate collectively in the creation and implementation of the software.
In fact, implementation of copyrights, patents and other IPRs might have hazardous effects on market competition, innovation and information flows,Footnote15 as a result of hindered interoperability. Whereas each of the access denied IPR and TPM would pose some barriers against the ICT interoperability, their cumulative effect should also not be disregarded. In the enclosed world with IPRs and TPMs, a massive amount of internet content and information is excluded from the public domain,Footnote16 along with far-reaching implications reaching out to lessened cultural production and participatory democracy being not limited to traditional ‘consumer harm’. From a broader point of view, interoperability is of a key role in connecting the networks, services and their users, and potentially diminishing the gatekeeping roles and functionalities that are often shielded by IPRs and TPMs. Having said that, it is hard to conclude whether EU IPR rules respond well to interoperability-related concerns, incorporating follow-on innovation, aftermarket competition and free flow of information.
2.2. EU competition law
Lack of interoperability would likewise pose a situation in contradiction with the competition law. Particularly, exclusionary abusive conducts e.g. the refusal to supply interoperability information, perpetuated by dominant players, would create lock-in that is hazardous to consumer welfare, thus creating a contradiction with the EU competition rules. This concern has so far led the EU Courts and the Commission to intervene in many cases by mandating access to interface specifications, such as in Microsoft.Footnote17 Not only refusal to deal, or other abusive behaviours, but also collaborative and concentrative undertakings are covered by the EU competition law tools, when they affect competitive markets by degrading intra, or inter-platform, interoperability.
From the competition law perspective, the question thus turns into whether lack of interoperability in different settings e.g. unilateral, collaborative and concentrative acts, would result in exclusion of the competitors in a particular market. The pioneering concerns or the so-called theories of harm, as highlighted in many decisions of the European Commission, are signified within the entry barriers or competition constraints created by the hindered, usually IPR-protected, APIs for the relevant markets. Concerning the likelihood of market foreclosure, the Commission has intervened in various cases finding abuse of dominance for the hindered interoperability under Article 102 of the Treaty on the Functioning of the European Union (TFEU). For instance, in Microsoft, Microsoft was found to have abused their dominant position by leveraging market power in a downstream market i.e. client PC OS market to an upstream market e.g. server OS market resulting in likely consumer harm for the withdrawn/hindered interfaces towards the latter.
Under the light of the case-law i.e. Magill (Citation1995), IMS Health (Citation2004), Microsoft (Citation2007), for an antitrust liability, it is key to witness an extension of market power via hindrance of new (or improved) products that would otherwise be created in the downstream market. Despite some deviation under IMS Health and Microsoft, antitrust liability remains firm on the basis of two-tiered market approach along with other requisite elements i.e. indispensable input, elimination of effective competition, lack of objective justification (Unver Citation2018, 105), which constitute ‘exceptional circumstances’ warranting an antitrust obligation under Article 102 to mandate a dominant firm to disclose their interoperability information, i.e. APIs that close off the adjacent market(s).
On the other hand, the so-called exceptional circumstances test, albeit with the consolidation under the Commission’s Guidance (Citation2009),Footnote18 has posed uneven conditions throughout the case-law from Magill to Microsoft. Not only the uneven criteria for disclosure/access obligations, but also competition authorities often lacking competency for a timely, industry-wide and holistic intervention would mean additional risks for the stakeholders. The Microsoft case illustrates such an unbearably long and burdensome enforcement process, which lasted for over a decade including the Commission’s investigation, and only had a binding effect on the affected parties.
On this note, it is acknowledged by a number of recent reports (CMA Citation2020; ACCC Citation2019; Crémer, de Montjoye, and Schweitzer Citation2019; Digital Competition Expert Panel Citation2019; Stigler Center Citation2019), EU competition law tools are not capable enough to cope with the digital era problems, particularly in view of the semi-structural, enduring gateway problems. In fact, the Commission wants to exceed the established case law not confining itself within the boundaries of ‘exceptional circumstances’ and obviating any adjustment for the ‘consumer welfare’ standard which requires finding consumer harm by weighing up benefits and costs. Rather, European Commission prefers a more straightforward regime and has revealed this intention with publication of the Digital Market Act (DMA) Proposal in December 2020 with regard to regulation of digital platforms. Given the political willingness behind this, it seems the DMA Proposal (Citation2020) will be enacted in near future, also marking a remarkable shift towards ex ante regulation of the so-called semi structural architectural problems including the perceived interoperability problems.Footnote19
To sum up, case-specific nature of competition law remedies, the requirement of dominance and other thresholds for any intervention i.e. ‘exceptional circumstances’ along with the lengthy enforcement processes would make competition law less appealing and befitting for the ICT markets. Therefore, although having a pro-interoperability nature, competition law interventions fall limited against the ever fast changing ICT dynamics.
2.3. Electronic communications regulatory framework
Ex-ante instruments placed under the ECRF for the achievement of interoperability add another dimension to the debate over ICT interoperability, with particular respect to electronic communications. This dimension is of a central importance given the role the ECRF plays to secure the well-being of EU citizens and consumers in relation to the ever fast increasing usage of ICTs. Aiming at regulation of electronic communications network and services, the ECRF itself is originally structured and built on the notion of achieving interoperability between these networks and services from a consumer-oriented perspective.
This consumer-oriented perspective is well represented and embedded in the ECRF, in particular regarding access and interconnection, with a focus on the end-to-end connectivity. In this regard, ‘interoperability’ between the operators that interconnect their networks is secured by means of industry-wide, usually de jure, standards e.g. SS7 protocols, and if necessary through obligations imposed on the market players, sometimes regardless of their market power, e.g. in the case of ‘conditional access system’ (CAS) and ‘interconnection’.
For instance, CAS obligation set out under the European Electronic Communications Code (EECC Citation2018) signifies a regulatory solution by which all broadcasters are enabled to have their content received and viewed by the analogue TV users which rely on set-top boxes, namely the CASs.Footnote20 This ECRF obligation contemplates a remedy with no requirement or burden of proof regarding any actual or potential anti-competitive effect. Notably, this generic and symmetric obligation is applicable to all transmission providers, irrespective of their market powers.Footnote21 This obligation is a remarkable example of an interoperability-based access remedy, demonstrating the reach of the ECRF for other reasons than competition, i.e. media pluralism and cultural diversity.
‘Net neutrality’ also illustrates another area under the ECRF, denoting the extent of comparable obligations with no primary motive of promoting competition. To guarantee net neutrality, the EU Regulation 2015/2120 (EU Net Neutrality Regulation Citation2015) symmetrically obliges all the internet service providers (ISPs) to ‘treat all traffic equally, when providing internet access services, without discrimination, restriction or interference’.Footnote22 In a broader understanding, this would mean more than a simply ban of non-discrimination as the affected market(s) are related to not only ‘transmission’ but also ‘content’ side, and the foreseeable impact extends beyond market competition involving the freedom to expression, innovation and flow of information through the net.Footnote23
From this point of view, interoperability arises as a key element of the ECRF, although often being envisioned as a subordinate obligation to achieve the envisaged objectives.Footnote24 In remarkable cases as exemplified above, the underlying aim of the access and interoperability obligations moves from the goal of promoting competition. This situation, while responding growing needs of ICT usage and connectivity, also suggests considering the interoperability and related problems from a wider perspective. This remarkable point signifies the readiness of the EU authorities to regulate the upper ICT layers, where necessary by expanding the boundaries of conventional limits of the ECRF. Notwithstanding, it should be reminded that the ECRF, even after the revision in December 2018, has a limited remit as is focused on electronic communications.
3. Interoperability from a broader vision: building up a new mindset and perspective
There are several implications to be derived from the examination of the EU legal system regarding ICT interoperability. First and foremost, ‘interoperability’ is regulated under distinctive rules of each legal framework. While the emergence of this risk of some overlaps and gaps, the main shortcoming seems to be lack of a holistic regulatory approach against the ever fast changing ICT dynamics and usage. Related to this, ‘interoperability’ needs to be considered broadly and be secured via necessary safeguards pursuing the broadly minded notion of ‘gatekeeping’.
At this point, inspirational point(s) can be derived from the ECRF whereby some of the gatekeeping activities i.e. discriminatory, non-transparent traffic management, are already captured and banned, if not from a holistic viewpoint. Having said that, the consumer oriented perspective which is embedded under the ECRF would be upheld in building up a holistic approach. Although the remit of the ECRF is limited, the perspective underlying this regulatory framework can be transposed in a broader regulatory approach as implicated in this study. Following this mindset, it would be possible to address not only the competition problems but also other problems involving traffic and data management - so to speak all gatekeeping activities - that result in restricted consumer choices and freedom.
Against this background, it is worth emphasizing that, the ECRF is invoked to eliminate structural barriers aiming at new entries to the market or ensuring competition with a focus on electronic communications. So often, it is considered, even regardless of the behavioural aspects, key network facilities i.e. local loop operated by the incumbents are made available to third parties considering their structural nature that can affect potential competition and consumer welfare. In this framework, interoperability finds a place to itself also under the SMP regime that aims to ensure competition in relevant markets through ex-ante remedies following market analysis.Footnote25
Notwithstanding, the consumer-oriented perspective portraying the ECRF – which supplements and goes beyond this market-specific notion – needs to be prioritized as it emphasizes interoperability based on to end-to-end connectivity, media pluralism and cultural diversity rather than competition. The emerging ICT landscape should thus be evaluated from a wider perspective comprising the gatekeeping activities – some of which are already addressed under the ECRF, as explained above. Following on this, a normative framework and finally a holistic regulatory model dealing with gatekeeping activities from a consumer-oriented perspective, needs to surface on the EU agenda.
Below, the architectures of cloud computing and the IoT are examined, with a view to enrich the above findings, given potential further inputs that would help an appropriate regulatory design. In other words, it is considered examination of these emerging technologies would forge new complementary inputs, which would broaden horizons before shaping out a normative framework and regulatory model.
4. An architectural outlook to the interoperability: examples of cloud computing and the IoT
Interoperability, from an industry-specific perspective, is destined to be dealt with through standards. This approach is however doomed to fail for the narrow-minded perspective underlying this approach. From this standpoint, rather than delving into the standards setting organizations (SSOs) and their endeavours, this part of the research aims to explore the architectural components of cloud computing and the IoT systems, with a view to have a more in-depth view as to interoperability relations and gaps.
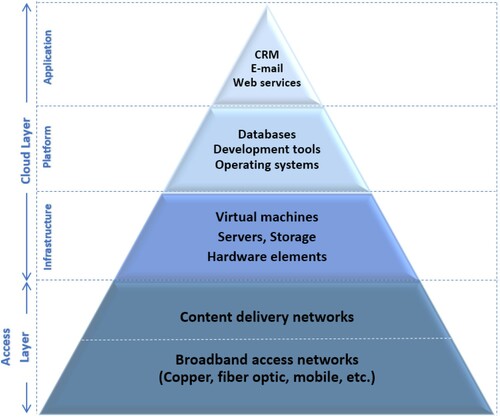
Architectural layers of the ICT systems constitute the gateways for the players. Particularly from the interoperability perspective, all the constituent layers and elements should interoperate with each other ending up with a successful and thriving ICT ecosystem based on the interdependencies among such elements. Cloud computing ecosystems which rely on internal and external elements, illustrate well the so-called layer interdependencies, as manifested in .
As can be seen through , not only the cloud components, namely the ‘internal’ elements themselves, but also the ‘external’ elements which constitute the ‘access layer’, denote a multi-layered structure. From this multi-layered viewpoint, every element, whether internal or external, is interdependent/interlinked to each other both structurally and functionally. These inter-links within and across the cloud layers are achieved by means of ‘interoperability’, namely the ‘interfaces’ agreed upon between the players/stakeholders. However, except with a few standard interfaces i.e. Open Virtualization Format (OVF) that ensure interoperability at the infrastructure layer, common standards do not exist in the cloud industry. Industry-led findings and solutions to achieve interoperability, whether based on standardization e.g. NIST’s efforts to create vendor-agnostic technologies, or architectural solutions e.g. microservices, containers, mitigate the problem of lacking standards (Unver Citation2019, 164–165). Also, the fact that clouds serve as utility type networks and the ever fast increasing cloud adoption have the potential to further mitigate the problem of lacking (interoperability) standards.Footnote26
Technically speaking, the interdependencies between the underlying layers becomes a matter of cloud governance, as far as the internal elements are considered. That is to say, all the internal elements are managed by the cloud provider in the organizational and technical sense. These interdependencies expand when the external elements are incorporated into the cloud setting. In this latter case, a single cloud management no longer exists as the outer boundaries often end up with the ecosystem features. Given the layer interdependencies, interoperability within the cloud architectures should not be separated from, and need to be analysed with, the associated layers or external elements.
Along the same lines, the IoT interoperability entails the products and services offered by the IoT stakeholders i.e. manufacturers, software developers and sensor/chipset suppliers, operating in their respective marketplaces based on the mutually acknowledged protocols/standards towards the same goal of achievement. For instance, interoperability in the setting of smart ‘home appliances’ means lightbulbs, windows, thermostats and other smart appliances speaking to each other, even though they are produced by different manufacturers.Footnote27 This means cross-layer interoperability for and within the IoT settings.
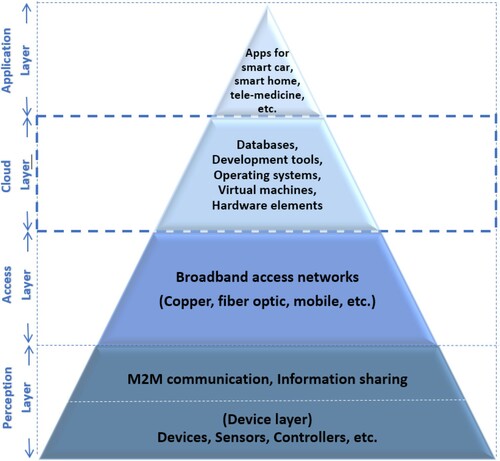
Underlying architecture of the IoT systems depends on the widely acknowledged three interdependent layers, which are classified as (i) perception layer, (ii) network (access) layer and (iii) application layer,Footnote28 as illustrated in .
Alike with the cloud layers, the IoT layers across this architecture and the corresponding players rely upon each other to provide the relevant services. On the other hand, many IoT service providers and manufacturers build up their respective proprietary ecosystems by closing off the gateways (interfaces) to third parties, to maximize the profits to be reaped from an installed consumer base. As recently identified by the European project Unify-IoT, there are more than 300 IoT platforms in the marketplace, among which Amazon (AWS), Cisco (Jasper), IBM (Watson), Apple (HomeKit), Google (Brillo), Microsoft (Azure) and Qualcomm (AllJoyn) represent the forerunners (European Commission Citation2016, 91–93; Noural, Atiquzzaman and Gaedke Citation2019, 796). There are currently many different OSs developed specifically for IoT devices such as Contiki, RIOT9, TinyOS and OpenWSN, each having several versions, to deliver services to users (Noural, Atiquzzaman and Gaedke Citation2019, 796). Likewise, Apple HomeKit supports its own open-source language Swift, Google Brillo uses Weave and Amazon AWS IoT offers SDKs for embedded C and NodeJS (Noural, Atiquzzaman and Gaedke Citation2019, 796). Each of these service or platform providers promotes their own IoT infrastructure, proprietary protocols and interfaces, incompatible standards, formats and semantics which constitutes closed ecosystems or truly speaking ‘walled gardens’, sometimes called ‘stove pipes’ or ‘silos’ (Noural, Atiquzzaman and Gaedke Citation2019, 796).
IoT settings e.g. smart city, smart energy, public transport, telemedicine and industrial processes, being so diverse and fragmented, make the related SSO processes develop on an unintegrated basis. Furthermore, stakeholders are pushing their own standard and/or protocol for the IoT systems, trying to gain a significant advantage from the potential markets. As a result, walled garden structures and vendor lock-in cases are far more seen in the IoT settings, comparing to the cloud settings. Along the same lines, coopetitive and symbiotic relationships could hardly be attributed to the IoT settings e.g. transport, smart city and telemedicine, as opposed to the cloud settings. This, however, creates significant challenges for the emergence of IoT ecosystems in effect.
While both cloud and the IoT settings are fraught with the absence of multi-layered common standards, clouds are typified by utility and bottleneck characteristics, bridging the interoperability gaps as the major hubs for the ICT interconnectivity and usage. This and other aspects of cloud computing e.g. ever fast increasing cloud adoption and strong inter-relationship with the external elements e.g. CDN, broadband access networks, bring clouds closer to the true understanding of ‘ecosystem’.
Hence, against diverse scenarios that can be implicated from other ICT settings, the legal system should be flexible enough to respond both ecosystem and non-ecosystem settings, in that cross-layer interdependencies need to be embodied. While ecosystems ostensibly represent the widest organizational supply structure, other supply structures thus need to be incorporated within a holistic regulatory design. From this viewpoint, technologically neutral and widely applicable layers would provide a well-functioning layout for construction of a holistically designed regulatory model.
5. Mapping and responding the relevant concerns: building up a normative model
As implied above, ‘interoperability’ can be a source of a great many problems echoing in ‘gatekeeping’ activities. While lack of interoperability arouses competition concerns e.g. based on vendor lock-in, such problems represent one side of the coin. On the other side of the coin exist socio-technical problems led or surrounded by traffic or data management, most of which are often triggered by AI-based algorithms and do not necessarily capture any competition concern, although being related to interoperability.
Against this background, the regulatory approach needs to be comprehensive and responsive enough to address all interoperability related concerns. In this respect, the consumer-oriented perspective embedded in the ECRF needs to be transposed into a sustainable normative framework, also reflecting on the architectural inputs from the cloud and the IoT settings as shown above. That being said, below, the discussion is taken further delving into the concepts of ‘layering’ and ‘gatekeeping’ based on the findings so far.
5.1. Layering
As could be inferred from the cloud and the IoT architectures, interdependent layers mean an indispensable layout for the ICT networks and services. This multi-layer structure, offering the building blocks for the IP based operations, also helps reconsidering the ICT settings, whether denoting ecosystem characteristics or not. An ecosystem would entail coopetitive relationships, whereas within non-ecosystem structures such relationships are hardly available across the underlying layers. Responding to both type of structures, ICT layers not only constitute the building blocks of the IP stackFootnote29 but also mean the interdependent value chains for the economic activities of the stakeholders.
The difference between the cloud and the IoT settings is noteworthy here as the interdependencies between the IoT players are usually not equivalent to those among the cloud players or stakeholders. Notwithstanding, regardless of the question of whether ‘coopetition’ or myriad interactions prevail, the layered structure across these settings offers a common layout on which interoperability gaps can be worked out. In fact, co-existence of both competitive and co-operative relationships, makes it very difficult to define or demarcate an ICT market as opposed to what is expected of competition law and policy.
Given this fact, an appropriate regulatory model would ideally build upon a layered approach, comprising both ecosystem and non-ecosystem relationships. Considering this, ‘layering’ needs to be elaborated further. As a baseline, the layering theory,Footnote30 which was developed by the US scholars to deal with the market failures in the field of ICTs, is explored below.
Layering theory was first invented as an instrumental tool for examining policy implications on technology and later evolved into a policy model to promote a technically neutral view of the various emerging network platforms. The layered approach has been usually credited, as it allows that each module or layer of the whole ICT system could be analysed in a self-contained division, whilst acknowledging the interdependence among the layers, namely the ‘physical’, ‘logical’, ‘application’ and ‘content’ layers, as widely accepted (Nuechterlein and Weiser Citation2013, 164; Whitt Citation2003, 592). Main arguments of the policy proponents for layering models evolved on the; (i) differentiated treatment for each horizontal layer along with a lighter regulation in the higher layers and (ii) adoption of a more technology-neutral and refined regulatory treatment for the respective ICT networks and services.
While these layers are acknowledged as laying the ground for a regulatory model, the regulatory approach proposed in this study diverges from the previous ones with the underlying homogenous regulatory treatment, considering the need to a holistic design as well as to avoid a fragmented approach for the gatekeeping activities. From the holistic viewpoint, no differentiated approach should exist among the layers with regard to regulatory governance of the interoperability related problems within the meaning of gatekeeping activities. That is to say, the concept of ‘gatekeeping’ represents another crucial part of the intended model, as implicated above.
In the past, lower layer infrastructures were considered to pose greater threats in terms of new entries and market competition, whereas it was widely acknowledged that upper layers should be immune from ex ante regulation. However, shift of the locus of the economic activities from the bottom to the upper layers makes it inevitable to revisit this policy approach towards homogenous regulatory treatment of the layers.Footnote31 Although the upper layer activities have been subjected to a heightened antitrust scrutiny in the last decade, this trend does not change the fact that there is neither a harmonized nor a holistic regulatory treatment for the ICT layers under the EU law.
From a broader viewpoint, both competition and the so-called techno-social concerns are considered underlying the proposed layered model, which captures gatekeeping activities in general. This is mainly to respond to the restrictions over the consumers, either taking the form of anti-competitive behaviours or non-quantitative harm to the consumers, i.e. cognitive bias and discrimination. Crucially, techno-social concerns often co-exist with the competition concerns potentially guiding us for a homogenous regulatory treatment across the ICT layers.Footnote32
These concerns are not mutually exclusive and are intertwined with each other. To emphasize, many of the ICT operations might have discriminatory, biased and/or non-ethical elements which are most often not captured by competition law. Whereas the upper layer services e.g. digital platforms create an online habitat for users, behind the scene is an opaque, largely unknown and sometimes dehumanizing architecture that can create path dependencies - which might be unfairly selective, biased or discriminatory. Through the controlling gateways (interfaces), underlying architectural designs i.e. based on AI, deep learning, manipulative/persuasive technologies, could affect consumers’ freedom to choose, communicate and access the information, along with far-reaching implications over the human dignity and autonomy as well as democratic culture.Footnote33 Remarkably, such techno-social concerns do not necessarily overlap the elements that restrict competition in the relevant markets but do affect consumers’ dignity and autonomy, most often through hidden ways of algorithmic (AI-based) manipulation. Hence, tackling both competition and techno-social concerns is highly important in the ultimate regulatory design and understanding of the proposed model, and reconceptualization of the notion of ‘gatekeeping’ appears key to this aim.
5.2. Gatekeeping
5.2.1. Original theory and reconceptualization
‘Gatekeeping’, an originally theorized concept, has nowadays become a buzzword echoed with various undesirable activities of ICT players particularly the digital platforms. ‘Network gatekeeping’ was first developed by Barzilai-Nahon (Citation2008) to mean ‘the process of controlling information as it moves through a gate (a network or its sections)’ (Barzilai-Nahon Citation2008, 1496). This notion of ‘gated’ and controlling access to it is of a key role to play in Barzilai-Kahon’s ‘network gatekeeper theory’ that was built upon the concept of ‘information control’ (Barzilai-Nahon Citation2008, 1493–1512).Footnote34 Based on this premise, gatekeeping activities, according to Barzilai-Nahon (Citation2008), include, among others, selection, addition, withholding, display, channelling, shaping, manipulation, repetition, timing, localization, integration, disregard and deletion of information (Barzilai-Nahon Citation2008, 1498).Footnote35
While the original theory revolves around access to ‘information’ itself, in scholarly discourse, two major types of gatekeepers can be roughly distinguished: (i) gatekeepers which control access to information and (ii) gatekeepers which have a facilitating role through control of critical intermediary resources or services that are necessary to link users and content, to mediate between the different players in the information chain, to produce, transport and distribute content, etc (Helberger, Kleinen-von Königslöw and Van der Noll Citation2015, 52). Whereas the former is represented by those who are in the position to have an editorial control over the information to be published either online or offline, the latter means more structural network gatekeepers i.e. cable or set-top box (CAS) providers, or the ISPs that control the means of access to the information.
In view of the human rights to be invoked by the gated and the emerging impact on the ‘democratic culture’, Laidlaw (Citation2015, 47) constructs a new definition of ‘gatekeeping’ developing a model of ‘internet information gatekeepers’. This rights-oriented notion of gatekeeping builds upon the original gatekeeping concept, together with a classification of micro and macro gatekeepers to be determined according to the extent to which (i) the information has democratic significance and (ii) the reach or structure of the communicative space (Laidlaw Citation2015, 57).
It is important to remind of the fact that techno-social concerns are coupled with competition concerns that underlie the cross-layer gatekeeping activities. At this point, it becomes also necessary to look at the interoperability related problems from a broadly minded gatekeeping notion. While gatekeeping activities are partially dealt with under the ECRF e.g. concerning net neutrality, techno-social concerns are not all-encompassed, although they are also crucial to understand multi-layered interoperability. ‘Gatekeeping’ on a cumulative basis plays out a key role within the proposed normative framework under which a regulator has to designate and assess the gatekeepers’ cross-layer practices effectively.
While the ICT layers represent the value chains as well as underlying software (architectural) codes, gatekeepers are considered to be in the position to allow or deny access to such architectural gateways. This understanding is embedded in the proposed ‘layered regulatory model’ so as to capture AI manipulation alongside other (IPR and TPM inclusive) restrictions, reflecting on the techno-social concerns. From this understanding, as gatekeeping first and foremost means controlling access and interoperability, restrictive acts against third-party access and interoperability should be deemed unacceptable, as representing a gatekeeping activity.
While ‘gatekeeping’ or ‘network gatekeeping’ is not surfaced as a technical term within the EU legislation or precedents so far, this concept is more than instrumental to define a range of controlling powers in the ICT landscape. In relation to regulation of digital platforms or ‘core platform services’ broadly speaking, this concept has been underpinned by the EU authorities in the recent consultation process of the DMA Proposal (Citation2020) in highlighting certain problems surrounding network effects, controlling the access to data and technology, consumer lock-in, etc.Footnote36 These mainly competition problems, being upheld by the ‘gatekeeping’ concept, seem to have driven the consultation process for DMA to facilitate access to informational and infrastructural resources, with particular regard to the digital platforms.
Notwithstanding, a wider spectrum of gatekeeping activities would take place within the ICT landscape incorporating discriminatory, biased, non-ethical or unfair treatment of the consumers, which potentially have a restrictive nature on consumers’ freedom to access to the information and/or apps, services, products, etc. that provide the communication medium for the consumers. Such access/interoperability restrictions would incorporate either software and hardware e.g. middleware, including search engines, application stores and browsers, or infrastructural elements underlying software/hardware elements. Having said that, ICT players’ activities of such a restrictive nature are key to defining a gatekeeping role, whether competition or techno-social concerns are at stake.
5.2.2. Far-reaching boundaries of the ‘gatekeeping’
Against the above background, every ICT player that operates in one or more of the layers would be deemed to have a gatekeeper role, when positioned to be able to restrict choices of the consumers, being not limited to their welfare from the competition law understanding. That is to say, gatekeeping problems would not necessarily mean losses in consumer surplus yet include a wider understanding of harms, including the scenarios whereby individuals’ autonomy and dignity are affected. Restrictive activities, having the potential to affect consumers’ autonomy and dignity, would not necessarily have an anti-competitive effect but often results in ‘unfair outcomes’ or ‘transformative effects’, as framed by Mittelstadt et al. (Citation2016, 4). Although a wide range of concerns are attributed to algorithmic/AI-driven transformation,Footnote37 the referred two normative categories, namely ‘unfair outcomes’ and ‘transformative effects’, are key to understand the so-called techno-social concerns.
According to the framework drawn by Mittelstadt et al. (Citation2016, 5 and 8), unfair outcomes mean the consequences brought by the actions driven by the algorithms that can be assessed according to numerous ethical criteria and principles, and are found to have an unfair nature. Within this category are included not only indirect discrimination but also unfavourable results against neutrality. At the access (infrastructural) layer, one would come across non-neutral activities performed by the ISPs, as usually involving throttling, delaying and prioritising the net traffic. Moving to the upper layers, one can witness filtered results to be conveyed to the end-users such as in Google’s discriminatory ranking,Footnote38 and other online platforms’ exclusionary behaviours,Footnote39 which illustrate the gatekeeping activities at the middleware layer. Last but not least, Facebook filtering the news feeds to be featured in users’ customized account pages could be given as an example matching the application and content layers.Footnote40 Notably, while these examples entail unfair outcomes within the meaning of techno-social concerns, this does not exclude competition concerns as are also embodied within the conception of ‘gatekeeping’. While the latter concerns have been well established through the EU (competition law) precedents, there exists no holistic legal framework governing the unfair outcomes implicated through the former concerns, within the meaning of gatekeeping activities. In addition, sorting out the techno-social concerns separately from the competition concerns would mean extra cost and complexity as they are often intertwined.
When it comes to transformative effects, two challenges emerge:
challenges to autonomy in the sense that (often personalization) algorithms reduce the diversity of information user encounters by excluding content deemed irrelevant or contradictory to the user’s beliefs. The subject can be pushed to make the institutionally preferred action rather than their own preference.
challenges for informational privacy in the sense that the individual’s informational identity is breached by meaning generated by algorithms that link the subject to others within a dataset (Mittelstadt et al. Citation2016, 9–10).
The transformative effects might overlap the unfair outcomes. Here, information flows and adverse consequences to cultural production and democratic culture or participation surface, as having crucial stakes. On the overall ground of IPRs, TPMs and AI algorithms, information flows are often affected by the challenges to autonomy and for informational privacy. The combination of these challenges has the potential to have transformative effects over data subjects making them exposed to restricted/filtered information flows.Footnote41
‘Gatekeeping’, entailing both unfair outcomes and transformative effects alongside anti-competitive effects, builds on the key positions architecturally designed by the ICT players, from the bottom to the top layer. One can, referring to the abovementioned net neutrality and CAS obligations, conclude that such positions do not necessarily mean holding an essential facility or a market power.Footnote42 Rather, it implicates various means to control user activities via prioritization, manipulation, discrimination and/or unfair treatment. Given this fact, every ICT player would potentially be a ‘gatekeeper’ regardless of market power they have. For instance, at the infrastructural layer a gatekeeper e.g. an ISP can perpetrate non-neutral and discriminatory activities such as delaying, blocking or throttling. Considering AI algorithms tend to be the ‘norm’ all across the layers, one can also conclude that homogenous regulatory treatment is required to embody the gatekeeping activities, incorporating techno-social concerns and accompanying challenges such as unfair outcomes and transformative effects.Footnote43
Under the light of above information, gatekeeping could emerge across one or more of the ICT layers as revealing diverse restrictions on consumers’ choices and behaviours, which often implicate unfair outcomes and transformative effects, as explained above. illustrates the most potential gatekeeping activities and the gatekeepers at each layer of the proposed model as reflected in .
Table 1. Potential gatekeepers and gatekeeping activities across the layers Source: Constructed by the author.Footnote44
6. Conclusion: building up positive rules on the normative ground
This study proposes the ‘layered regulatory model’ against the interoperability based problems and concludes that this model can effectively cope with the related concerns, namely competition and techno-social concerns, from a consumer-oriented perspective and based on the four-layer model as manifested in . Herein, interoperability is broadly minded as cutting across all the ICT layers within the four-layer structure or IP stack where ‘gatekeeping’ activities take place. The proposed model is thus built on two key concepts: (i) layering and (ii) gatekeeping.
While ‘layering’ provides the necessary layout for the regulatory governance, ‘gatekeeping’ refers to the activities that arouse ‘competition’ and ‘techno-social’ concerns which need to be addressed from a broader regulatory point of view. Behind this normative framework lies the fact that ensuring interoperability is key to the ICT landscape and needs to be elaborated with other related problems echoed with ‘gatekeeping’ from a holistic and layered perspective. It is considered this normative framework would be transformed into a regulatory model as proposed through this article.
This model is built upon an ex-ante regulatory approach, considering the shortcomings of competition law remedies and IPR safeguards against the interoperability-related problems. This follows the idea that the proposed model becomes more responsive and effective if the model maintains a holistic, ex-ante and multi-layered structure. This requires appropriate regulatory safeguards ensuring a homogenous regulatory treatment across the layers, as reflected in .
Against this background, it is considered that a bottom-up approach based on a set of principles would be more appropriate and feasible for the intended regulatory governance. In this context, ‘gatekeeping’ is referred to mean the digital gateways employed across the IP layer(s) through which users’ access to informational or infrastructural resources are controlled. From a holistic and multi-layered perspective, exploitation of various controlling mechanisms i.e. IPRs, TPMs, AI algorithms for restricting consumer choices, signifies a capability of gatekeeping across the layers.
Following this bottom-up approach, the proposed model aims at addressing the gatekeeping activities following four governing principles according to which, the gatekeepers must:
- not restrict access and/or interoperability at the expense of limiting consumer choices (access and interoperability),
- report their management of data and traffic across the layers to the regulator(s) (transparency),
- refrain from biased or unfairly selective supply of layered services or components unless justified on an objective ground (fairness) and
- ensure that the software management e.g. AI-driven processes underlying the layered services or components, rely on ethical, accountable and democratically justifiable reasons (accountability).
Crucially, these proposed principles mean the key instructions which all the gatekeepers should adhere to, regardless of their market power. As long as these principles are complied with, there is no need to intervene on the part of the regulatory authority i.e. European Commission at the EU level and NRAs at the national level. Conversely, in case the principles are breached and certain restrictions took place over the consumers’ behaviours and choices, appropriate obligations should be imposed on the gatekeepers by the regulator(s). Following on the given principles, it is suggested that the potential obligations include, but not limited to, the following:
- Access and interoperability: Consumers’ access to infrastructural/informational resources might be affected when a gatekeeper denies or delays the demands for access to and interoperability with their (access, middleware, application or content) layer services or components. In that case, access and interoperability remedies would need to be imposed on the gatekeeper(s) to make the relevant service or component accessible to the third parties.
- Transparency: A gatekeeper might be subject to transparency obligations when the same-layer or cross-layer operations carried out by them reveal a gatekeeping activity in view of the restricted consumer behaviours and choices, and the opaque aspects of underlying software and algorithms.
- Fairness: In case certain restrictions by means of discrimination and bias e.g. selective ranking, filtering, prioritising take place across certain layer(s) resulting in a gatekeeping activity, the gatekeeper could then be ordered to carry out their activities in an unbiased and ethically justified manner.
- Accountability: In the case of consumers being manipulated to use or select certain content, apps, services, etc. the gatekeeper involved in that activity might be required to redesign their underlying software and algorithms for the associated layer services or components.
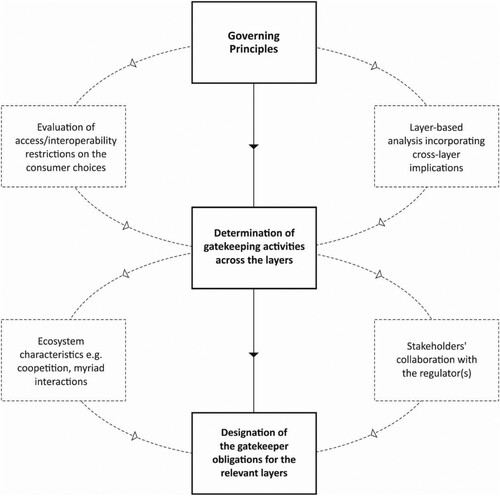
Following this regulatory framework, the extent to which the gatekeepers are to be exposed to the given obligations will be determined under the guidance of governing principles. According to this bottom-up approach reflected in , gatekeepers’ collaboration with the regulator(s) as well as among themselves is of key importance, and potentially minimize any need to intervention. Even the introduction of this regulatory model is expected to avert the gatekeeping activities and to reduce the need to the obligations.
Furthermore, as long as a self-regulatory ecosystem structure exists within and across particular layer(s), this would alleviate the follow-up process along with the minimized access and interoperability remedies applicable to relevant layer(s). Nonetheless, transparency, fairness and accountability obligations would still be applicable even where the access and interoperability relationships are widespread obviating any access/interoperability obligation. Remarkably, ecosystem players could meet at an equilibrium point where they could continue non-transparent, unfair and non-ethical activities. This means residual effect of such activities yet need to be resolved even in the presence of access and interoperability relationships. Thus, attention should be paid to every kind of gatekeeping activities, no matter interoperability gaps and problems are diminished through self-regulatory ecosystems or principles. Mirroring these details, sequential steps envisaged in the overall process are manifested in the figure below.
As could be seen above, the proposed model has a dynamic and evolving nature. For the smooth and better functioning of the model, top-down measures are avoided at all. Given the central tenets of the proposed model i.e. homogenous regulatory treatment, holistic and multi-layered nature, there would no longer be a need to the existing access related measures of the ECRF e.g. SMP remedies, nor to the competition law remedies that aim to designate and penalize the abusive behaviours such as denial of access, etc. in relation to such layer services and components. Hence, all the ICT-inclusive competition concerns already captured by either the ECRF or EU competition law should then be dealt with through the ‘layered regulatory model’ for its wider scope and overarching nature. It is therefore suggested the proposed principles and obligations supersede the competition-oriented ECRF rules e.g. SMP remedies and have precedence over the EU competition rules.
The proposed model would effectively replace the (core principles and remedies of the) former for its very nature and the consumer oriented perspective, bringing out new interfaces vis-à-vis the EU competition law as well as the IPR rules. Given the wide-ranging competition and techno-social concerns surfacing in this context and the response developed by the proposed model, this model should have a supra role to play against the pertinent ex-ante and ex-post competition rules. On the other hand, these legal frameworks need to be maintained for other compelling reasons i.e. merger control under the EU competition law or universal service obligations under the ECRF, within the meaning of exclusive areas of regulation under these bodies of law. This proposal emanates from the governing normative framework of the model, considering it all addresses the gatekeeping roles and functionalities across the ICT layers.
Remarkably, the layered regulatory model offers a simplified yet effective response to the interoperability related problems, going beyond the disaggregated and narrow-minded EU legal frameworks. In fact, the proposed model has a scope and effect that would have an overarching place and enforceability against the relevant bodies of law, i.e. IPR legislation, competition law and ECRF. Ultimately, jurisdictional choice of the EU law should not be deemed as a significant limitation for the ends of this research as the findings are generalizable for the very nature of the proposed model. That is to say, the constituent elements of the ‘layered regulatory model’ are adjustable to every jurisdiction for the adaptive and self-standing nature of the model. Notwithstanding, it is always welcome to see future efforts in this field of research delving further into the regulatory frontiers of the proposed model, including un-ethical and democratically unjustifiable aspects of the gatekeeping activities with a more focus on the AI-based algorithms and processes.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Notes
1 Scholarly there exist different definitions made so far. Among these, Sutor’s definition is notable which refers to ‘[t]he ability for two different and independent software applications to exchange information without loss of data, semantics or metadata’ (Sutor Citation2011, 215). One can also refer to Samuelson’s definition: ‘[t]he capability to communicate, execute programs, or transfer data among various functional units in a manner that requires the user to have little or no knowledge of the unique characteristics of those units’ (Samuelson Citation2009, 1946–1947). For the definition introduced by the Institute of Electrical and Electronics Engineers (IEEE) see IEEE Standards Glossary (Citation2016).
2 See Software Directive, Arts. 5(3) and 6.
3 Competition law is widely invoked under the EU law so as to ensure interoperability, particularly where an abuse of dominance was found to have taken place or in case any kind of collaboration between the undertakings, i.e. vertical and horizontal agreements and concerted practices, is anti-competitive. Respectively, Articles 101 and 102 of the TFEU are relied on with regards to these cases, namely for the abuses of dominant position and anti-competitive agreements. Likewise, there might be a case denoting effective competition being significantly impeded because of a merger/acquisition, which can end up with interventions, i.e. rejection or clearing conditions, under EU Merger Regulation.
4 Interoperability based rules and remedies can be found under the 2018 European Electronic Communications Code (EECC) which constitutes the EU regulatory framework for electronic communications. For instance, Article 62(1) of the EECC imposes an interoperability obligation on broadcasters to ensure that technical services (e.g. conditional access) enabling ‘digitally-transmitted services to be received by viewers’ be given to all access seekers in a non-discriminatory way. Secondly, the interconnection obligation, which enables end-to-end connectivity as well as interoperable Europe-wide networks and services, is given special emphasis under various provisions e.g. Article 61(2) of the EECC. Thirdly, SMP undertakings might be subject to the obligations of ‘grant[ing] open access to technical interfaces, protocols or other key technologies that are indispensable for the interoperability of services or virtual network services’ and ‘prov[ision] of specific services needed to ensure interoperability of end-to-end services to users, or roaming on mobile networks’ according to the EECC (EECC, Art. 73/1(f, h)). While the first two obligations are envisaged for all the relevant undertakings regardless of their market powers, the last one is envisaged specifically for dominant operators.
5 Originally, many EU rules and principles are often based on or inspired of their US law counterparts such as some exceptional rights under IPR law, essential facilities doctrine under competition law or access obligations under sector-specific regulations. EU law and institutions, however, forge ahead by enacting newer remedies, e.g. right to data portability, net neutrality obligations which pose a widened legal response and measures. More clustered and detailed measures come up with certain challenges of fragmentation as well as risk of false positives. From this point of view, not only is a multi-disciplinary field of research possible but also revisiting of the regulatory frontiers is better enabled on wider contours of the EU system.
6 The internet layers and governing protocols i.e. developed under Open Systems Interconnection (OSI) or TCP/IP stacks lay the ground for development of the ‘layering theory’, which generally means adapting the IP layers to policy and regulatory approaches. The vital role of the protocol layering within the IP ecosystem came to the fore in the late 1990s and had a remarkable influence on the literature with regards to the reconstructing of the regulatory policies.
7 In a layered model, where the layers are to be dealt with on a regulatory basis, ‘gatekeeping’ emerges as another key concept. While the abovementioned layers provide the necessary layout for ex ante regulation, the ‘gatekeeping’ refers to the activities that capture ‘competition’ and ‘techno-social’ concerns which need to be addressed within the layered regulatory model.
8 ‘Techno-social’ is one of the key attributes used in this study inspired by the work of Frischmann, and Selinger who authored a book called ‘Re-Engineering Humanity’. In their book, they define and frequently refer to the term of ‘techno-social engineering’. According to their definition, techno-social engineering refers to ‘processes where technologies and social forces align and impact how we think, perceive and act’ (Frischmann and Selinger Citation2018, 4–5). Based on this definition, the ‘techno-social concerns’ is conceptualized to mean the concerns mostly manifested in algorithmic/AI-driven software that manipulates online users affecting their behaviours and choices leading up to unfair outcomes and/or transformative effects.
9 The legal definition of a TPM is given under Article 6(3) of the Directive 2001/29/EC (InfoSoc Directive Citation2001) which basically states that a TPM is any technology (software or hardware) which restricts access to a copyrighted material without the consent of the copyright holder.
10 Software Directive, Art 6(1).
11 SAS v WPL judgement para 39.
12 In the following period, while SAS has succeeded with their claims as to breach of contract based on the original contract terms under the local state (North Carolina) law, their subsequent attempt for extraterritorial enforcement orders to compel WPL to make payments from England failed. Regarding the recent Court of Appeal’s decision (anti-suit injunction) to block US extraterritorial enforcement measures, see SAS Institute Inc v World Programming Limited (Citation2020) EWCA Civ 599.
13 See Vezzoso (Citation2012, 159) reading; ‘ … [t]he functional character of APIs, being even stronger than with computer programs in general, would very often place them well below the originality threshold, and the general support in favour of interoperability expressed by the Software Directive could possibly present a further counterargument [against copyrightability of interfaces]’.
14 See Otero (Citation2015, 86) reading; ‘Since a computer program’s form of expression is functional, variations of its expression will not matter because these possible variations come from utility reasons and not the ’aesthetic freedom’ or whim of its developer. Therefore, expression and function merge. … ’.
15 Regarding the latter issue of free flow of information, see Elkin-Koren (Citation2002, 79–106) where it is argued that ‘control rather than remuneration becomes the focus of legal disputes concerning copyright’ (Elkin-Koren Citation2002, 84) and ‘this transforms copyright law from a law that sought to serve policy goals and secure incentives for creators into a law that facilitates control in information markets’ (Elkin-Koren Citation2002, 106).
16 Boyle (Citation2008, 46); Lessig (Citation2006, 186).
17 Case COMP/C-3/37.792 - Microsoft [2004] OJ L 32/23 (‘Commission’s Microsoft decision’), upheld in Case T-201/04 Microsoft v Commission [2007] ECR II-3601 (‘GC’s Microsoft judgement’).
18 Commission’s Guidance para 81.
19 The DMA Proposal includes a set of ex-ante prohibitions as well as a ‘market investigation tool’ to ensure competition and increase market contestability across the digital platforms. Once an undertaking is designated gatekeeper within the meaning of the DMA, then that particular gatekeeper will be subject to certain prohibitions and obligations as enshrined under Articles 5 and 6. Under this framework are existing certain proposed measures in order to enhance access and interoperability, such as ‘allow[ing] business users and providers of ancillary services access to and interoperability with the same operating system, hardware or software features that are available or used in the provision by the gatekeeper of any ancillary services’ (DMA Proposal, Art 6(f)).
20 EECC, Art 62(1).
21 Operators not enjoying significant market power (SMP) being covered by this obligation signifies the key role attributed to the CASs under the EECC, which explicitly acknowledges ‘Competition rules alone may not be sufficient to ensure cultural diversity and media pluralism in the area of digital television’ (Preface EECC, Recital 159).
22 EU Net Neutrality Regulation, Art 3(3).
23 For similar views see (Maniadaki Citation2019, 485–488; Audibert and Murray Citation2016, 126–132).
24 Crucially, policy objectives of the ECRF have also been expanded with the enactment of the EECC, which stipulates that the competent authorities e.g. NRAs and the Commission, shall:
promote connectivity and access to, and take-up of, very high capacity networks,
promote competition in the provision of electronic communications networks and associated facilities,
contribute to the development of the internal market and
promote the interests of the citizens of the Union (EECC, Art 3(2)).
25 Article 67 of the EECC sets out the procedure for ‘market analysis’, involving market definition, SMP assessment and selection of remedies. A few interoperability related remedies, as envisaged under the Article 73(1) of the EECC, can be imposed on SMP undertakings should there exist potential market failures that require ex ante intervention as per Article 67 of the same Directive (EECC).
26 According to Cisco’s forecast for the period of 2016 to 2021, global cloud IP traffic will account for 95% of total data center traffic by 2021 and will be more than triple (3.3-fold) over the next 5 years with a 27% increase rate (CAGR) (Cisco Citation2018). Furthermore, 94% of workloads and compute instances will be processed by cloud data centres, whereas 6% will be processed by traditional data centres, according to the same forecast for the given period (Cisco Citation2018).
27 This could be extended to the broader industrial settings like the ‘connected (smart) home’ market which includes not only connected appliances but also automated lighting, HVAC (heating, ventilation and air conditioning), entertainment and security (Porter and Heppelmann Citation2014). In the broadest setting, which could be described as a hyper-connected marketplace, smart homes and the integrated devices, appliances, etc. are supposed to be interoperable with the smart cars, smart city components, etc.
28 See (Sehgal, Patrick and Rajpoot Citation2014, 711–712; De la Guía, Lozano, and Penichet Citation2013; Hwang, Fox and Dongarra Citation2012, 579).
29 The internet is standardized by the Internet Engineering Task Force (IETF), based on the TCP/IP stack, or simply saying IP stack, which relies on a unique ‘protocol layering’. The ‘TCP’ part of the TCP/IP stack governs the assembly and reassembly of the data at each end, including checking for errors such as missing data, whereas the ‘IP’ part is responsible for routing data from one node to another. These elements of the internet enable a computer in one corner of the world to find a different computer in another corner of the world and exchange information that can be understood by the applications software loaded onto the computers at each end of the transmission (Nuechterlein and Weiser Citation2013, 167).
30 IP stack laid the ground for development of the ‘layering theory’, which generally means adapting the IP layers to policy and regulatory approaches. Particularly in the USA, layering theory was found to pave the way for an environment whereby regulatory rules against distinct networks, e.g. cable, the PSTN and services, for example VoIP and voice telephony, were to be filtered on the basis of convergence across the internet layers (TCP/IP) on a technologically neutral basis. See (Kariyawasam Citation2007, 87–117; Kariyawasam Citation2005, 587; Werbach Citation2005, 66–67; Werbach Citation2002, 39–54; Whitt Citation2003, 587–672; Mindel and Sicker Citation2006, 136–148; Sicker and Mindel Citation2002, 69–94).
31 It appears that the locus where demand and supply meet is increasingly moving from the legacy telecommunications networks (lower layers) to ‘digital platforms’ or broadly speaking, upper layers. While IP convergence functions as the catalyst of both the demand and supply of ICT networks and services, minimized regulatory pressure over the supply of the upper layers could be said to have contributed to the so-called shift. Along the same lines, it could be advanced the upper-layer companies have utilized the regulatory forbearance maximizing the benefits to be reaped from the IP convergence so far.
32 Notably, against the ever fast changing ICT dynamics including the shifting locus mentioned above, the users are increasingly exposed to the techno-social problems, which do not necessarily have any competition dimension.
33 See (Helbing Citation2018, 47–72; Royakkers, Timmer, Kool and Van Est Citation2018, 127–114).
34 According to Barzilai-Nahon (Citation2008) network gatekeeping is best conceptualized through information control lenses, and carries three main goals: (a) a ‘locking-in’ of gated inside the gatekeeper’s network; (b) protecting norms, information, gated and communities from unwanted entry from outside and (c) maintaining ongoing activities within network boundaries without disturbances (Barzilai-Nahon Citation2008, 1496).
35 The mechanisms include, for example, channelling i.e. search engines, hyperlinks; censorship i.e. filtering, blocking, zoning; security i.e. authentication controls, integrity controls and access controls; value-adding i.e. contextualization, customization, personalization; infrastructure i.e. network access, network configuration; user interaction i.e. add-on, navigation tools; editorial mechanisms i.e. technical controls, content controls, design tools of information content (Barzilai-Nahon Citation2008).
36 The EU Commission seeks to identify a number of ‘gatekeepers’ that provide ‘core platform services’, which are defined within Article 2(2) of the DMA Proposal. Once an undertaking is designated gatekeeper within the meaning of the DMA, then that particular gatekeeper will be subject to certain prohibitions and potential obligations. See also supra note 35. While the enshrined obligations are mostly competition oriented, other objectives can also be derived from the Proposal, which sets out the following aims for regulation of the core platform services:
addressing market failures to ensure contestable and competitive digital markets for increased innovation and consumer choice,
addressing gatekeepers’ unfair conduct and
enhancing coherence and legal certainty in the online platform environment for a preserved internal market (DMA Proposal Citation2020, 58).
37 See Yeung (Citation2019, 21–48); Scantamburlo, Charlesworth and Cristianini (Citation2019, 49–81); Olhede and Wolfe (Citation2018).
38 Google’s discriminatory ranking in online shopping comparison services, is an exemplary case for such subtle and exclusionary behaviours, driven by AI and data based manipulation. Following a 7-year investigation process, in June 2017, Google was fined 2.4 billion EUR for abusing its dominant position in the ‘online search’ market, to hamper the competition ‘online shopping comparison’ market during the years between 2008 and 2013. Google thereby was ordered by the Commission to ensure ‘equal terms’ for all competitors in the online shopping comparison market based on the fact that they favoured their own services with the result being restricting the users’ freedom to choose among the available options. (See European Commission Press release, Citation2017).
39 Platforms’ exclusionary behaviours would have far-reaching impact on the app providers and their services. Apple’s exclusion of the ‘Drone +’ application from its app store and exclusion of ‘Disconnect’ from Google Play illustrate this (Belli and Zingales Citation2017, 88–91). In the former instance, Apple rejecting an app providing real-time alerts of drone strikes, called ‘Drone+’, to be placed in its app store, was the conflict between the parties. The app provider was given two reasons for this rejection, respectively for it was ‘not useful’ and on the ground that it was ‘objectionable and crude’. While not clear-cut unlike with the former, Google’s rejection of Disconnect, a privacy enhancing technology app provider, implicates an allegedly unfair discrimination among the software provided by them and Google’s subsidiary. While in the first instance is exemplified a platform’s arbitrary reasoning for an exclusion, the latter instance would potentially be representative of an unfair discrimination in favour of a platform’s own software also creating a competitive advantage for himself.
40 See Dredge (Citation2014); Usher-Layser (Citation2016, 18–21).
41 It could be argued that even in the presence of data protection tools and safeguards, the transformative effects at stake could not be mitigated easily for the persistent nature of the gatekeeping activity that reach out to individuals’ dignity. While the individuals grant their consent as an autonomous/independent person, this does not deter the possibility that the unfairly selective content being reached to themselves through the underlying algorithms.
42 See Lynskey (Citation2017, 10); Edwards (Citation2018, 66).
43 Conversely, such upper-layer activities reach out to the consumers in ways they would hardly realize, like in the way they would be captured via personalized recommendations, prices, customized products, etc. Likewise, individuals’ participation on the social media and other information platforms could be captured and affected by the diverse gatekeeping roles and functionalities that are driven by AI and related algorithms. In the end, ‘consumer welfare’ seems unharmed, whereas the access and interoperability channels get restricted and the consumers’ dignity and autonomy affected. See also Van Dijck, Nieborg and Poell (Citation2019, 4).
44 Partly inspired by Easley, Guo and Kraemer (Citation2017, 26).
References
- Audibert, L. C., and A. D. Murray. 2016. “A Principled Approach to Network Neutrality.” SCRIPTed 13 (2): 1118–1143. doi:https://doi.org/10.2966/scrip.130216.118.
- Australian Competition and Consumer Commission. 2019. “Digital Platforms Inquiry – Final Report”, www.accc.gov.au/publications/digital-platforms-inquiry-final-report.
- Band, J., and M. Katoh. 2011. Interfaces on Trial 2.0. Cambridge: The MIT Press.
- Barzilai-Nahon, K. 2008. “Toward a Theory of Network Gatekeeping: A Framework for Exploring Information Control.” Journal of the American Society for Information Science and Technology 59 (9): 1493–1512.
- Belli, L., and N. Zingales. 2017. How Platforms are Regulated and How They Regulate Us - Official Outcome of the UN IGF Dynamic Coalition on Platform Responsibility. United Nations Internet Governance Forum.
- Boyle, J. 2008. The Public Domain: Enclosing the Commons of the Mind. New Haven, CT: Yale University of Press.
- Case C-406/10, SAS Institute Inc v World Programming Ltd. 2012. 3 CMLR 4 (‘SAS v WPL judgement’).
- Case C-418/01 IMS Health GmbH & Co OHG v. NDC Health GmbH& Co KG. 2004. ECR I-5039, 4 CMLR 1543 (‘IMS Health judgement’).
- Case T-201/04 Microsoft v Commission. 2007. ECR II-3601 (‘GC’s Microsoft judgement’).
- Cisco. 2018. “Cisco Global Cloud Index: Forecast and Methodology.” 2016–2021 White Paper. http://www.cisco.com/c/en/us/solutions/collateral/service-provider/global-cloud-index-gci/white-paper-c11-738085.html.
- Consumer and Markets Authority (CMA). 2020. “Online platforms and digital advertising market study.” www.gov.uk/cma-cases/online-platforms-and-digital-advertising-market-study.
- Council Directive. 2009/24/EC of the European Parliament and of the Council of 23 April 2009 on the legal protection of computer programs (‘Software Directive’).
- Council Directive (EC) 2001/29 on the harmonisation of certain aspects of copyright and related rights in the information society. 2001. L167/10 (‘InfoSoc Directive’).
- Council Directive (EU) 2018/1972 of the European Parliament and of the Council of 11 December 2018 establishing the European Electronic Communications Code (‘European Electronic Communications Code’ or ‘EECC’). 2018. OJ L 321/36.
- Crémer, J., Y. de Montjoye, and H. Schweitzer. 2019. “Competition Policy for the Digital Era.” (Report to the EU Commission Directorate-General for Competition) http://ec.europa.eu/competition/publications/reports/kd0419345enn.pdf.
- De la Guía, E., M. D. Lozano, and V. M. R. Penichet. 2013. Interacting with Objects in Games through RFID Technology. London: Intechopen.
- Digital Competition Expert Panel. 2019. “Unlocking Digital Competition: Report of the Digital Competition Expert Panel” (Furman Review) https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/785547/unlocking_digital_competition_furman_review_web.pdf.
- Dredge, S. 2014. “How Does Facebook Decide What To Show In My News Feed?” Guardian. Accessed August 1, 2014. www.theguardian.com/technology/2014/jun/30/facebook-news-feed-filters-emotion-study.
- Easley, R., H. Guo, and J. Kraemer. 2017. “From Network Neutrality to Data Neutrality: A Techno-Economic Framework and Research Agenda” SSRN. https://ssrn.com/abstract=2666217.
- Edwards, D. 2018. “Circulation Gatekeepers: Unbundling the Platform Politics of YouTube’s Content ID.” Computers and Composition 47: 61–74.
- Elkin-Koren, N. 2002. “It’s all About Control: Rethinking Copyright in the new Information Landscape.” In In The Commodification of Information, edited by Niva Elkin-Koren and Neil Weinstock Netanel, 79–106. The Hague: Kluwer Law International.
- European Commission. “Antitrust: Commission Fines Google €2.42 billion for Abusing Its Dominance as a Search Engine by Giving an Illegal Advantage To Its Own Comparison Shopping Service” Press release (IP/17/1784). Accessed August 1, 2021, http://europa.eu/rapid/press-release_IP-17-1784_en.htm.
- European Commission. “Guidance on the Commission’s Enforcement Priorities in Applying Article 82 of the EC Treaty to Abusive Exclusionary Conduct By Dominant Undertakings.” (Commission Guidance) (2009/C 45/02) [2009] OJ C 45.
- European Commission. 2016. UNIFY-IoT Project. http://www.internet-of-things-research.eu/pdf/D03_01_WP03_H2020_UNIFY-IoT_Final.pdf.
- European Commission. 2020. “Proposal for a Regulation of the European Parliament and of the Council on Contestable and Fair Markets in the Digital Sector.” Digital Markets Act (DMA) Proposal, COM(2020) 842 final 2020/0374 (COD).
- Frischmann, B., and E. Selinger. 2018. Re-Engineering Humanity. Cambridge: CUP.
- Helberger, N., K. Kleinen-von Königslöw, and R. Van der Noll. 2015. “Regulating the New Information Intermediaries as Gatekeepers of Information Diversity.” Info 17 (6): 50–71.
- Helbing, D. 2018. Towards Digital Enlightenment: Essays on the Dark and Light Sides of the Digital Revolution. Cham, Switzerland: Springer.
- Hwang, K., G. C. Fox, and J. J. Dongarra. 2012. Distributed and Cloud Computing: Form Parallel Processing to the Internet of Things. Oxford: Elsevier.
- Institute of Electrical and Electronics Engineers (IEEE). 2016. Standards Glossary Accessed August 1, 2021. https://www.standardsuniversity.org/article/standards-glossary/.
- Joined cases C-241/91 P and C-242/91 P, Radio Telefis Eireann (RTE) and Independent Television Publications Ltd (ITP) v Commission. 1995. ECR I-743, [1995] 4 CMLR 718 (Magill judgement).
- Kariyawasam, R. 2005. “Defining Dominance for Bits and Bytes: A New Layering Theory for Significant Market Power?” European Competition Law Review 26 (10): 581–594.
- Kariyawasam, R. 2007. International Economic Law and the Digital Divide: A New Silk Road. Northamton, MA: Edward Elgar.
- Laidlaw, E. B. 2015. Regulating Speech in Cyberspace; Gatekeepers, Human Rights and Corporate Responsibility. Cambridge: CUP.
- Lessig, L., and Code. 2006. Version 2.0, Basic Books.
- Lynskey, O. 2017. “Regulating ‘Platform Power’” LSE Law, Society and Economy Working Papers 1/2017, http://eprints.lse.ac.uk/73404/1/WPS2017-01_Lynskey.pdf.
- Maniadaki, K. 2019. “Net Neutrality Regulation in the EU: Competition and Beyond.” Journal of European Competition Law & Practice 10 (7): 479–488. https://academic.oup.com/jeclap/article-abstract/10/7/479/5588728.
- Mindel, J. L., and D. C. Sicker. 2006. “Leveraging the EU Regulatory Framework to Improve a Layered Policy Model for US Telecommunications Markets.” Telecommunications Policy 30: 136–148.
- Mittelstadt, B. D., P. Allo, M. Taddeo, S. Wachter, and L. Floridi. 2016. “The Ethics of Algorithms: Mapping the Debate.” Big Data & Society 3 (2). doi:https://doi.org/10.1177/2053951716679679.
- Noural, M., M. Atiquzzaman, and M. Gaedke. 2019. “Interoperability in Internet of Things: Taxonomies and Open Challenges.” Mobile Networks and Applications 24: 796–809.
- Nuechterlein, J. E., and P. J. Weiser. 2013. Digital Crossroads: Telecommunications Law and Policy in the Internet Age. 2nd edn. Cambridge, MA: The MIT Press.
- Olhede, S. C., and P. J. Wolfe. 2018. The Algorithms Ubiquity of Algorithms in Society: Implications, Impacts and Innovations. The Royal Society. doi:https://doi.org/10.1098/rsta.2017.0364.
- Otero, B. G. 2015. “Compelling Disclosure of Software Interoperability Information: A Risk for Innovation or a Balanced Solution?” In In Intellectual Property and General Legal Principles: Is IP a Lex Specialis?, edited by Graeme B. Dinwoodie, 69–90. Cheltenham: Edward Elgar.
- Porter, M. E., and J. E. Heppelmann. 2014. “How Smart, Connected Products Are Transforming Competition” Harvard Business Review. https://hbr.org/2014/11/how-smart-connected-products-are-transforming-competition.
- Regulation (EU). 2015/2120 of the European Parliament and of the Council of 25 November 2015 Laying Down Measures Concerning Open Internet Access And Amending Directive 2002/22/EC on Universal Service and Users’ Rights Relating to Electronic Communications Networks and Services and Regulation (EU) No 531/2012 on Roaming on Public Mobile Communications Networks within the Union (EU Net Neutrality Regulation) [2015] OJ L 310.
- Royakkers, L., J. Timmer, L. Kool, and R. Van Est. 2018. “Societal and Ethical Issues of Digitization.” Ethics and Information Technology 20: 127–114.
- Samuelson, P. 2009. “Are Patents on Interfaces Impeding Interoperability.” Minnesota Law Review 93: 1943–2019.
- SAS Institute Inc v World Programming Limited. 2020. EWCA Civ 599.
- Scantamburlo, T., A. Charlesworth, and N. Cristianini. “Machine Decisions and Human Consequences.” In In Algorithmic Regulation, edited by Karen Yeung and Martin Lodge, 49–81. Oxford: OUP.
- Sehgal, V. K., A. Patrick, and L. Rajpoot. 2014. “A Comparative Study of Cyber Physical Cloud, Cloud of Sensors and Internet of Things: Their Ideology, Similarities and Differences.” IEEE International Advance Computing Conference (IACC) 2014: 708–716.
- Sicker, D., and J. Mindel. 2002. “Refinements of a Layered Model for Telecommunications Policy.” Journal on Telecommunications and High Technology Law 1: 69–94.
- Stigler Center. 2019. Stigler Committee on Digital Platforms Final Report, https://www.chicagobooth.edu/-/media/research/stigler/pdfs/digital-platforms—committee-report—stigler-center.pdf.
- Sutor, Robert S. 2011. “Software Standards, Openness, and Interoperability.” In In Opening Standards: The Global Politics of Interoperability, edited by Laura DeNardis, 209–217. Cambridge, MA: The MIT Press.
- Unver, M. B. 2018. “Turning the Crossroad for a Connected World: Reshaping the European Prospect for the Internet of Things.” International Journal of Law and Information Technology 26 (2): 93–118.
- Unver, M. B. 2019. “What Cloud Interoperability Connotates for EU Policy Making: Recurrence of Old Problems or New Ones Looming on the Horizon?” Telecommunications Policy 43: 154–170.
- Usher-Layser, Nikki. 2016. “Newsfeed: Facebook, Filtering and News Consumption.” Phi Kappa Phi Forum 96 (3): 18–21.
- Van Dijck, J., D. Nieborg, and T. Poell. 2019. “Reframing Platform Power.” Internet Policy Review 8 (2): 4. doi:https://doi.org/10.14763/2019.2.1414.
- Vezzoso, S. 2012. “Copyright, Interfaces, and a Possible Atlantic Divide.” Jipitec 2: 153–161.
- Werbach, K. 2002. “A Layered Model for Internet Policy.” Journal on Telecommunications & High Technology Law 1: 37–68.
- Werbach, K. 2005. “Breaking the Ice: Rethinking Telecommunications Law for the Digital Age.” Journal on Telecommunications and High Technology Law 4: 59–96.
- Weston, S. 2015. “The Legal Regulation of Interoperability in an Oligopolistic Market.” PhD diss. Bournemouth University.
- Whitt, R. S. 2003. “A Horizontal Leap Forward: Formulating a New Public Policy Framework Based on the Network Layers Model.” Federal Communications Law Journal 56 (3): 587–672.
- Yeung, K. 2019. “Why Worry About Decision-Making by Machine?” In Algorithmic Regulation, edited by Karen Yeung and Martin Lodge, 21–48. Oxford: OUP.
- Zingales, N. 2016. “Of Coffee Pods, Videogames, and Missed Interoperability: Reflections for EU Governance of the Internet of Things.” TILEC Discussion Paper DP, 2015–2026.