?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
Since patient diagnostic data such as X-rays, MRIs, CT scans, etc. contain very sensitive information about a patient's health, it must be encrypted to prevent unauthorized access. In chaotic-based image encryption methods, the lower-dimensional chaotic maps are insufficient because they can be estimated through some signal estimation technologies; therefore, a higher-order novel 5D logistic chaotic map along with DNA encoding and the Arnold map for medical image encryption is presented to overcome the vital medical breaching that could cost a life. In this work, the advantages of DNA principles and high-dimensional chaotic maps are used to develop an efficient encryption method for the protection of medical images. The strategy is useful due to the fact that the higher order makes the system more complicated and tough to penetrate. The large keyspace up to, anti attack capabilities, and comparison of various standard parameters with different literatures illustrate the algorithm's superiority.
Introduction
Telemedicine is a rapidly expanding discipline that provides remote medical services to individuals when the patient and the medical professional are in distinct locations. For that, sensitive patient data, such as clinical images, is transferred over the different forms of communication available. A modernized health sector needs a practical framework designed to store these clinical images, which can be constantly available only to authorized individuals located at any geographical location [Citation1,Citation2]. Cloud storage systems may offer a service like this; nevertheless, these arrangements are prone to cyber security threats, especially when created in a manner that falls short of security requirements. The Internet is a massive network where many participants exchange large amounts of digital information. Unfortunately, strategies for achieving the necessary protection for sensitive information, including both storage and communication networks have lingered slightly. Various compression techniques combined with encryption techniques may be useful in providing better speed performance in terms of storage and transmission, but their application is limited to non-medical images because even the smallest detail in a medical image may contain vital information that cannot be lost [Citation3]. In this circumstance, one method of preserving medical images is necessary which facilitates strong security and worthless to users who do not have cryptographic credentials.
Among the many cryptographic algorithms, the chaos-based ones are dominant. The chaotic phenomenon is used by many scientists. It is followed by applying dynamical arrangements that are incredibly responsive towards primary values and have randomized values that are predictable, having ergodicity, structural intricacy, a larger key area, pliability, and remarkable periodicity. As a result, the outcome dependent on the initial conditions might vary so significantly that the behaviour cannot be anticipated [Citation4,Citation5]. Different chaos maps, such as Henon, Baker, Piecewise, Gauss, Tinkerbell, Chebyshev map, Lorenz system, Sine, Tent, Arnold, and Logistic maps, are utilized in image encryption [Citation6–12].
In actual practice, maps based on chaos, i.e. chaotic maps are the backbone of chaos-driven cryptographic methods. Because the confusion and complexity lie in its equation and dimension, it can be classified as one-dimensional and multidimensional. A one-dimensional chaotic map has the disadvantage of having fewer system parameters and thus simpler phase space trajectories. As a result, chaos based signal estimation methods can forecast their initial properties and trajectories. On the other hand, multidimensional or higher-order maps have more parameters, therefore, offering greater complexity than a one-dimensional map with fewer orders. As a result, the higher-order maps can be an exemplary model for visual cryptography. Various researchers have previously used 3D Chebyshev maps [Citation13], 3D logistic maps [Citation14], 3D Lorenz maps [Citation15], double chaotic logistic maps [Citation16], and 4D Henon maps [Citation17] for incremental complexity.
Patient diagnostic data such as X-rays, MRIs, CT scans, etc. are very important information, especially when the patient is suffering from a very serious disease. In this case, a minor alteration or change in this vital information could result in a life-threatening situation for the patient. Consider a situation where a patient is treated through telehealth or telemedicine, and in the exchange of these vital health records, some fisheries participate anonymously and alter the information. In this instance, the doctor on the other side will get altered information, which may cause the wrong treatment or may cause a health or life hazard. As a result, the level of security in this application must be higher than usual, yet low-dimensional chaos map architectures are considerably simpler, since there have fewer system constituents. System characteristics and starting values can be anticipated using chaotic signal estimating algorithms. In contrast, high-dimensional chaotic structures exhibit outstanding chaotic behaviour and a complicated architecture [Citation18].
So to overcome the low dimensional map problem discussed above, we have proposed a high-dimensional chaotic map, i.e. a novel 5D logistic map. Furthermore, to increase security, we are also using the Arnold map and DNA encoding with the 5D logistic map.
The overall structure of the paper is as follows: Section ‘Related work’ introduces the related work or literature survey. Section ‘Underlying principle’ explains underlying principles such as: 1D logistic map, the Arnold map, and DNA encoding. In Section ‘Proposed methodology’, the 5D logistic map generator, along with its Lyapunov exponent, pixel shuffling, and proposed encryption method, are explained. In Section ‘Simulation result and security analysis’, the simulation results and security analysis of this proposed method are examined. The conclusion is addressed in Section ‘Conclusion’.
Related work
Images are among some of the information that may be protected by converting an actual image into such an encrypted one with an appropriate key that could only be retrieved by decryption. Furthermore, this was very well implemented in the past by many researchers. Some very recent and prominent work is discussed further. M. Gafsi et al. provided a superior approach that relies on permutation, substitution, as well as diffusion features to encode the confidential image [Citation19]. The image elements are permuted arbitrarily in the first phase with a matrix formed by the Pseudorandom Number Generator (PRNG). The pixel's bit is then permuted through an intricate system. These pixels are replaced with two separate S-boxes, each with a unique internal state. In order to obtain a cipher-text, the image is diffused in the last phase via XORing image elements with the PRNG-generated key-stream. To improve the intricacy of security, R cycles of encryption could be performed. In one Discrete wavelet transform (DWT) based approach, S. Jeevitha et al. presented a block-based DWT scrambling technique for medical image cryptography that uses edge maps taken from an input image [Citation20]. The approach is divided into three primary stages: DWT decomposition, edge map sequencing, and DWT-level scrambling. The images are first fragmented into multiple DWT planes. The edge detector technique was proposed in the second phase to predict the edge maps and must be of equal size to the DWT-bit scales. The DWT-level scrambling has been used to separate nearby image elements into distinct rows and columns, weakening the high association between surrounding pixels.
M.A. Hajjaji et al. proposed Artificial Neural Networks and a chaos encryption compression-dependent method. The method employs ANN for compression, as well as Arnold and Piecewise maps to change the value of the hidden layer and encrypt [Citation21]. Wang et al. also suggested a technique for image encryption that integrates the chaotic map and the Josephus issue. The permutation-diffusion approach is the foundation of the whole decoding procedure. The permutation operation might employ the double chaotic cycle shift method, which is an improved version of the chaotic shift transform strategy. The primary purpose of the dissemination phase of the endeavour is to retain the diversity of the Josephus sequence. The authors actually do this by broadening the description of the Josephus problem to include the use of a chaotic map [Citation22].
Tsafack et al. [Citation23] introduced a basic chaotic system-based image cryptosystem. An electronic network built on a dynamic, four-dimensional chaotic system is created to obtain the encryption key. This approach mostly lengthens the computational time. First, PRNG was used to generate the substitute S-box and a key sequence. The S-box was then used to replace the image's pixels. Finally, the encrypted image was obtained by XORing the resulting pixels with the key sequence.
On the basis of three-dimensional orthogonal Latin squares (3D-OLS) and a matching matrix, Zhou [Citation24] proposed an image cryptosystem. To begin, three chaotic action sequences were produced using the 3D sine map. In the next step, they used the chaotic sequences to generate a 3D orthogonal Latin square (OLS) and a corresponding matrix. Next, they combined the matching matrix with the 3D-OLS to perform a permutation on the original image. The permuted matrix's planes were then each partitioned into sixteen equal units. A location matrix was constructed by sorting the chaotic pattern. A new matrix was constructed by connecting and shifting the blocks on each plane in accordance with the position matrix. In the end, a diffusion operation was performed on the new matrix to produce the encrypted image.
In low dimensional method, Li et al. [Citation25] proposed a chaotic scheme based on the two-dimensional Sine Logistic Modulation Map (2D-SLMM) and the two-dimensional Henon-Sine Map (2D-HSM). The encryption approach used in this study involves zigzag scan scrambling, pixel grey value change, and dynamical diffusion.
In transform domain method, a novel medical cryptographic technique based on the fractional discrete cosine transform (FrDCT) was presented by Kumar et al. [Citation26]. In this method, the image was run through FrDCT, and then the FrDCT coefficients were passed to a chaotic mapping to encrypt the image. In [Citation27], Li et al. introduced a Lorenz and logistic transform-based technique for encrypting images in two dimensions. To secure the image, chaotic patterns are generated in two dimensions using the Lorenz chaotic model. A multi-chaotic cryptographic technique based on the Arnold Map and Logistic-Sine-Coupling Map (2DLSCM) was also presented by Jain et al. [Citation11] for use with medical images. To do this, the pixels of the input image are rotated and translated using an Arnold map in accordance with the key, and a chaotic matrix is then generated using a 2D-LSCM map. Furthermore, unlike the majority of image encryption systems, which only employ a single map, this scheme successfully counteracts the non-deal behaviour patterns of the various chaotic maps.
For the purpose of protecting medical images, Belazi et al. [Citation28] presented a refined version of the Sine-Tangent chaotic map. A tri-layer encryption method was used to create this work. In the beginning, they bitwise XOR the image with a chaotic matrix, which removes any connections between neighbourhood pixels. To fix the bit error, the resulting pixels are randomly rotated clockwise. The source image's rows and columns are also moved clockwise (one pixel at a time). Lastly, the shifted image is scrambled using a bitwise eXOR process, which both increases sensitivity to plaintext and removes any lingering correlation between neighbouring pixels.
Encrypting medical images with deoxyribonucleic acid (DNA) was proposed by Wu et al. [Citation29]. For this work, they came up with a content-aware permutation and diffusion module, as well as a random DNA encoding with sets of DNA rules. Bit-replacing techniques, chaos based systems, and DNA encoding algorithms are all components of the solution suggested by Yousif et al. [Citation30]. By doing so, they may represent each pixel in the image as a purely binary integer, made up of ones and zeros. Two zeros replace the one bit, and two ones replace the zero bit. Two unique images will result from repeating the process of swapping out every bit in every pixel. High-dimensional chaotic systems based on the idea of permutation and diffusion operations are used to encrypt pictures in order to scramble the coordinates and values of the pixels in an image. Finally, they use the principles of the DNA algorithm to encode the combined images and use the DNA addition operation to combine the encrypted images. Deciphering the encoded DNA images yields a final image with a hidden message.
By integrating a scan approach, the El-Gamal public key cryptosystem, and chaotic systems, Yousif et al. [Citation31] established a novel approach to image security. It all starts with a zigzag and a spiral scan to build a twisted image. The image is encrypted using the El-Gamal technique, then in the last phase of confusion and diffusion, Lorenz and Rössler chaotic sequences are used to jumble up the pixel values.
P. Mishra et al. [Citation32] described a unique approach for hiding images preceding encryption that is keyless but assists in boosting the unpredictability of the input images. Confusion and diffusion are then applied to the concealed image, resulting in an encrypted image containing no perceptual or statistical content. The technique employs an extended version of Cat Map for the sake of clarity. A unique diffusion technique that works at both the pixel and DNA-plane levels has been presented. It includes all potential DNA encoding and rules chosen at random depending on the chaotic 2D-Logistic Sine Coupling Map.
Although all the method discussed above contributed well in this area but there were some shortcoming which might be improved. The major drawbacks of the methods discussed above are:
Compared to higher-dimensional maps, low-dimensional chaotic maps feature fewer system parameters and simpler structures. As a result, chaotic signal estimating methods may be used to make predictions about the system's parameters and initial value.
Low-key space makes systems easier to attack and less secure.
The output of the encrypted images via conventional encryption methods is usually complex, which increases the burden of storage and transformation.
Furthermore, the aforementioned encryption approaches introduce the most widely used techniques for safely transmitting visual data using chaotic maps. However, their security is entirely dependent on the chaotic behaviour of the maps, which is in turn dependent on the initial parameters chosen and the structure of the encryption method. For highly sensitive data transfer, such as in telemedicine, the encryption system and map employed should exhibit optimum behaviour at all times. Therefore, there is a requirement of a multi-chaotic map-based encryption system that eliminates the non-ideal behaviour of the individual maps and exhibits high randomness across a wider range of initial parameter values.
Fulfilling the requirement stated above, the following are the key highlights of the proposed methodology:
The encryption complexity of the first-ever proposed novel 5D logistic map is significantly increased owing to its intensive shuffling operation.
The histograms of the encrypted image are evenly spread out, and their entropy values are much closer to their bit depth.
The correlation coefficients of the encrypted images are very low; this demonstrates that the key in the work is sensitive to the encryption scheme's variables and security.
The technique allows a significantly large key space up to 2448, which is sufficiently large to resist a crypto attack. Furthermore, the suggested algorithm's keyspace is considerably superior to that of numerous current works.
For the purpose of demonstrating the suggested method's effectiveness, several security and performance evaluations have been carried out, including NIST's successful randomization test.
A computational time analysis is performed and compared with distinct other literatures to evaluate the speed performance of the proposed method.
The results of the successful cropping, noise, rotation, translation, and scaling attacks are evidence of the security of the proposed method.
The outcomes clearly show that the proposed cryptosystem is significantly more effective and secure than the various image cryptosystems that are currently in use, and this conclusion was reached by comparing the relevant quality metrics of the encrypted image to the evaluation indicators of the decrypted image.
Underlying principle
Logistic map
It is a fundamental nonlinear expression that scientists often utilize because of its simple yet effective encryption properties [Citation33]. Mathematically, it is given by the following equation:
(1)
(1)
(2)
(2)
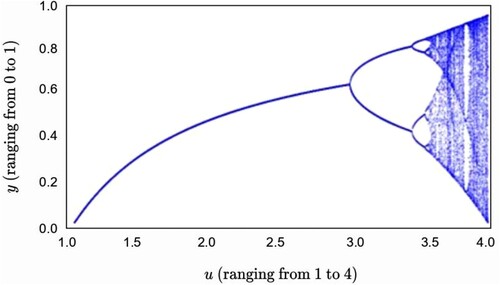
depicts the u vs. y graph of equation (1). In this equation, y represents the population at any given time n, and u represents the rate of growth. Logistic Map is used as a model or a data source for many diversified applications such as life sciences, chemistry, computer vision, etc. Many notable successes in biology have already been achieved by many biologists if they could predict the growth rate of living things so precisely that population size fluctuates between preset values over a timeframe of 2, 4, or 8 years. Also, it may find applications where it is used to model specific chemical processes, such as those described by Malek and Gobal [Citation34]. Because of its essential qualities, such as responsiveness to the starting condition or controlling parameters, the logistic map is widely used for creating novel cryptographic systems to suit the needs of secure image transfer also [Citation35].
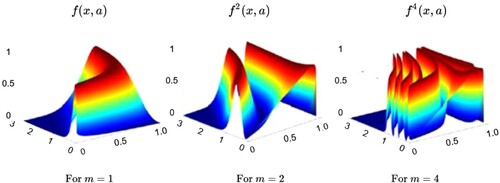
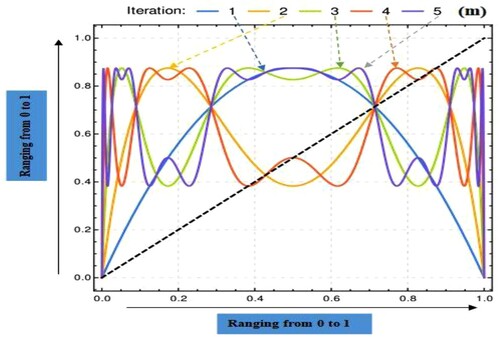
Traditionally, the logistic map chaos technique is a quadratic equation with a y = 0.5 peak and α = 1. Assuming f(x, u, α) = u* yα *(1-yα), the peak of this function appears at x = xp = α√0.5. It expands monotonically as it rises. In the α-x plane for u = 4.0, the generalized f's surface is a function which is shown in , and the curves move with the variation. For equation (2), the effect of the function iteration fm for m = {1, 2, 4} is expressed in by the surface plot. Here, the parameter u's range is predetermined (u = 4) in this generalized logistic map [Citation36]. also depicts the 2D plot of the logistic function f (blue) and its iterated variants f2, f3, f4 and f5 for various values of m and this time for u = 3.5.
Arnold cat map
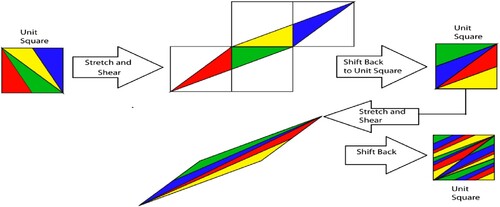
Vladimir Arnold created the approach and demonstrated its results using a cat drawing in 1967. As shown in , the Arnold Cat Map algorithm is an iterative series of stretching with the shear of a unit square and translation back to the unit square. The mapping retains and combines regions, and it is reversible. It is also often used in cryptography and may be described as:
(3)
(3)
Arnold's map employs linear algebra methods to manipulate the location of the pixels [Citation37]. It is generalizable and may be used to reorder digital image pixels or images of size N. The generalized Arnold map (GAM) is represented as a matrix as shown in equation (4) [Citation38]:
(4)
(4)
In equation (3) above, pixel positions are (i, j) = 1, 2, 3 … N, controlling parameters are (a, b), and new pixel coordinates in the reordered image are (i, j).
DNA encoding
The technique of mapping the nucleotide sequence comprising a DNA strand is termed ‘DNA sequencing’. The four bases that make up genetic coding are: adenine (A), thymine (T), guanine (G), and cytosine (C). ‘A’ binds with ‘T’ and ‘G’ binds with ‘C’ [Citation39]. We understand that each pixel in a digital image can also be represented using 8-bit binary integers [Citation40]. The complementary digital numbers of the pair 0–3 and 1–2 are used for the four deoxynucleotides ‘A,’ ‘T,’ ‘G,’ and ‘C’ and their combinations to express the digital numbers ‘00,’ ‘11,’ ‘01,’ and ‘10’. For instance, any pixel value of 206 can be expressed in the corresponding binary as ‘11001110’. This binary is ‘TATC’ in DNA coding with the above rules. The four nucleotides can be combined in 24 different ways. Only eight encoding permutations are, though, compatible with the complementary principle. , illustrates and summarizes these rules.
Table 1. DNA sequencing conversion rules.
Proposed methodology
Novel five dimensional logistic map generation
This section explains the first ever proposed 5D Logistic Map for medical image encryption. The proposed higher dimensional map is highly secure with the use of three distinct parameters, quadric, cubic, and quadratic coupling and extensive shuffling operations. The basic formula for deriving the 5D logistic map is taken from 1D logistic map (Equation (1)). The proposed five dimensional logistic map is expressed as:
(5)
(5)
(6)
(6)
(7)
(7)
(8)
(8)
(9)
(9)
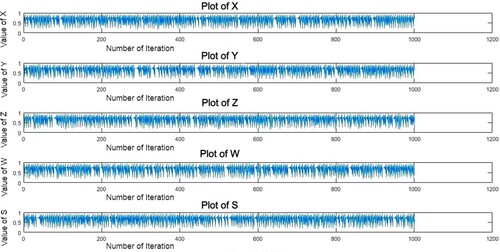
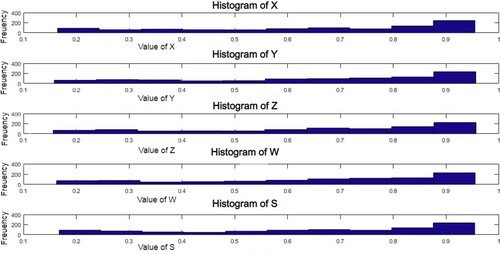
The presence of a quadric, cubic, and quadratic coupling, as well as three constant coefficients, namely, a, b, and c, makes this system even more complicated and robust. and demonstrate the plotting and histogram of the x, y, z, w, and s variables. These graphs explain the value range of x, y, z, w, and s plots, in which the horizontal axis represents the number of iterations and the vertical axis represents the component range.
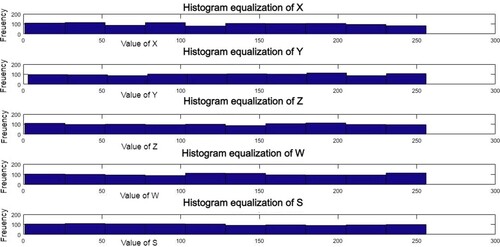
Throughout this technique, Chaotic Generator generates a 5D logistic map. It generates chaotic sequences using equations (5)–(9) with beginning values of x1 = 0.3250, y1 = 0.4250, z1 = 0.5250, w1 = 0.4350, s1 = 0.5350, a = 0.0135, b = 0.0177, and c = 3.7500. The initial values of the variables may be any value between zero and one. clearly shows a non-uniform distribution. We have to normalize the histogram for increased security. is used to represent histogram equalization for the above values. For instance, if the image size is M × N, the histogram equalization is provided by the formula below:
(10)
(10)
(11)
(11)
(12)
(12)
(13)
(13)
(14)
(14)
An arbitrary integer is substituted for each alphabet letter in the following formula: A, B, C, D, and E. We can also consider A, B, C, D, and E to be equal for simplicity. The equalized histogram was created by using A = B = C = D = E = 100,000 and M = N = 256.
Pixel shuffling
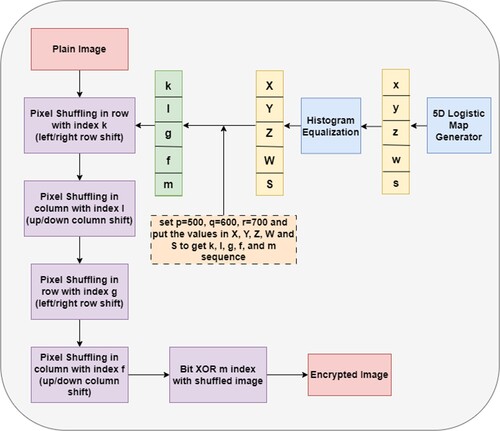
To achieve pixel shuffling, first we select P, Q, and R as random numbers. Then, by the use of these figures and equations (10)–(14), we generate five sequences: k, l, m, g, and f. For transformation, we rotate right if the chaos number, k, or g, is even and left if it is odd. We rotate up whenever the chaos, or l or f value, is even. Likewise, if the chaos value is odd, we rotate down. In this process, we rotate the image four times according to the values of chaos k, l, g, and f. The concluding or diffusion stage of this encryption approach is the XOR operation of the shuffled or key image (which is obtained by the Arnold map) with the m index. The XOR method is employed to transform the pixel intensities to a newer one that cannot be reversed until the chaos key is utilized. shows a flow diagram that represents the above-mentioned cryptographic procedure using a 5D logistic map.
Lyapunov exponent of the 5D logistic map:
The sensitive dependence on the starting circumstances typifies the characteristics of chaos. A slight change in the starting situation produces distinct dynamic results. The Lyapunov exponent demonstrates chaotic exponent divergence. A Lyapunov exponent is a value that indicates how sensitive a system is and assesses the chaotic system's behaviour [Citation41]. As a result, we have additional knowledge regarding whether or not the system has a butterfly effect. depicts the Lyapunov exponent of the 5D logistic map. The diagram shows that the maps are suitable for encrypting data delivered over an unsecured network after processing.
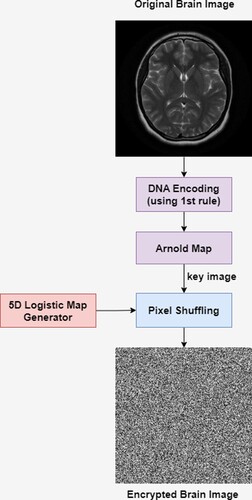
Proposed encryption algorithmIn this novel proposed approach, the DNA encoding and Arnold cat map are combined with a 5D logistic generator. The DNA encoding scheme's addition and subtraction operations are obtained via coding rule 1. The Arnold map is used to generate the corresponding key image when the key K is entered. To improve the algorithm's performance during the diffusion phase, we apply the XOR operation to a 5D logistic map and the key image. The proposed encryption technique is explained in detail in and in the algorithm as well. The plaintext image is deployed initially, followed by the DNA encoding and Arnold cat map, and subsequently the five-dimensional logistic map, which produces the cipher text image.
Simulation result and security analysis
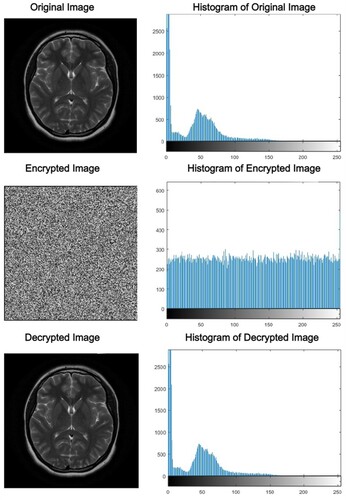
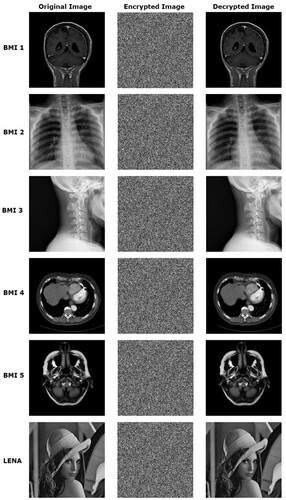
This section discusses different performance evaluation metrics, results obtained using the proposed approach, and performance comparisons with state-of-the-art methods. The computations were done on the MATLAB platform to assess and test the proposed work's efficacy. As a simulation result, illustrates the original, encrypted, and decrypted 256 × 256 brain image as well as the accompanying histograms.
Histogram analysis
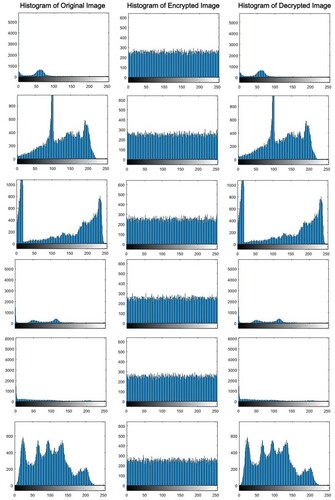
One of the most basic methods for demonstrating image encryption quality is cipher text image histogram analysis. In order to visualize the distribution of pixels in an image, a histogram is created by graphically plotting the number of pixels at each level of grayscale. According to the histogram analysis, the encrypted image should have a uniform distribution of values that is radically different from the plain image [Citation42]. The distribution of gray scales in the encrypted image should be fairly uniform for good encryption. The visual results of some test images are shown in and their histograms in , which clearly show the uniform distribution of histogram. The Chi-square test is also employed as a quantitative indicator of the level of uniformity for different encrypted images. The uniformity of the histogram is established by finding that all of the P-values for the encrypted image are more than 0.05 (5% significant) as shown in . These outcomes demonstrate that the suggested cryptosystem performs well against statistical attacks.
Table 2. Different performance metrics results for different test images.
Keyspace analysis
In image cryptography algorithm's keyspace must be large enough to make brute-force searches difficult. However, the proposed method's keyspace is hypothetically infinite. But, when the true value is used, the correctness is reduced owing to computing efficiency and precision constraints in practical implementations. The following nine cryptographic keys are used in the proposed system: a, b, c, x1, y1, z1, w1, s1, and K (key used in the Arnold map). The IEEE floating-point norm is generally useful for quantifying the full keyspace which is given by equation (15) below for the proposed method.
(15)
(15) The accompanying equation (15) shows that the algorithm's keyspace is sufficiently large to survive a crypto attack.
Information entropy
Unpredictability is measured and approached using information entropy (IE). The amount of entropy may always be used to define the output of plain and cipher-text integrity in any image [Citation43]. The higher informational entropy indicates the higher defense. A score of 8 for the IE of the encrypted image indicates that the images are extremely close to random distribution and the protection is higher. The entropy values of the several test images are shown in , and all the values are very near the score of 8 consistently, which clearly specifies the efficiency of the proposed method.
Table 3. Information Entropy for different test images.
NPCR and UACI
The values of NPCR and UACI may be used to conduct a test to determine how resistant the encryption algorithm is to a differential attack. When there is a shift in the value of a pixel in the original image, there is a corresponding shift in the encrypted image. This shift is indicated by the number of pixel change rate, or NPCR. The unified average change of intensity (UACI) shows both how significantly the value of a pixel in the original image changed and how much it changed in relation to other pixels in the encrypted image [Citation44,Citation45]. Generalized mathematical expression for NPCR and UACI are shown by equations (16) and (17) below.
(16)
(16)
(17)
(17) When referring to an image, M refers to its width, and N refers to its height. In addition, a1 represents the cipher image, whereas a2 represents the modified cipher image that results when one of the pixel values in the original image is altered. NPCR and UACI often fall around 99.95% and 33.52%, respectively. The NPCR and UACI values of the test images are shown in clearly satisfies the above mentioned standard values, which establishes the proposed method's resistance against differential attack.
Table 4. Different performance metrics results for different test images.
Image quality analysis
To figure out the quality, authenticity, and strength of the proposed algorithm, the mean square error (MSE) and peak signal-to-noise ratio (PSNR) is calculated. Another statistic that evaluates image quality is the structural similarity index, often known as the SSIM index. For cryptographic reliability, PSNR and SSIM should always be greater [Citation46]. While the discrepancy between the input image and the decoded image i.e. MSE should be small.
We evaluated over 100 distinct biomedical and standard test images and obtained results, namely PSNR, SSIM and MSE, which are listed in . The method's success and stability are established by the infinite PSNR, zero MSE value, and unity SSIM for specific biomedical as well as general grayscale images.
Correlation coefficient
The strength of a linear relationship between two variables or images could well be quantified statistically using the correlation coefficient. When there is weak relationship between neighbouring pixels in the cipher text image, encryption algorithms are able to function more efficiently At different levels, it is possible to figure out the horizontal, vertical, and diagonal correlation between the plaintext and cipher text images [Citation44,Citation47]. The correlation coefficient can have negative or positive values. The correlation values for the proposed method are indicated in . For example the Brain image in shows the horizontal, vertical and diagonal components as −0.0077, −0.0164, and −0.0123, indicating that there is no association between the original and encrypted image, as also seen in . This demonstrates that the key in this work is susceptible to the cryptographic strategy's settings and protection.
Figure 15. Illustration exhibiting the correlation coefficients of the original (a) and encrypted (b) Brain image.
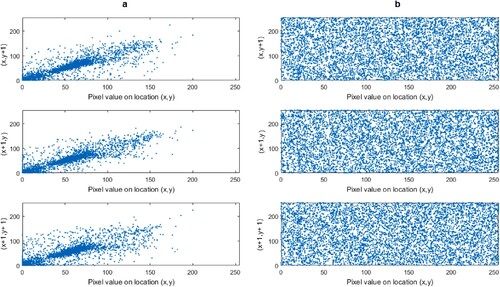
Table 5. Correlation coefficient values of original and encrypted test images.
NIST testing
The NIST SP800-22 test specifies the randomness of any sequence. In this context, the NIST SP800-22 here is used to assess the unpredictability of the sequences generated by the 5D logistic system (see ). The P value is the performance indicator in the NIST test. The P value for each test can be anywhere between 0 and 1. If the value of P is higher than a threshold that has already been set, this means that the chaotic sequence passes the evaluation [Citation1]. illustrates the NIST test results for the proposed algorithm. and clearly show the positive results from the NIST assessments.
Table 6. Randomness test for the 5D Logistic system's sequences.
Table 7. NIST test for the proposed algorithm.
Comparative study and dataset
The above-mentioned standard metrics results, such as key space, information entropy, and correlation coefficient, are compared with the different literatures in this section. All of the standard test images used in the analysis of the proposed solution were obtained from the USC-SIPI Image Database [Citation48]. The medical images utilized in the investigation were obtained from open-access medical image sources organized by Dr. Stephen R. Aylward [Citation49].
A cryptosystem's security is proportional to the size of its key space. A message with a larger keyspace is more resistant to decryption attempts (cryptanalytic attack) since an attacker will try all possible key combinations to decrypt the message. is the comparison of proposed algorithm's keyspace with other literatures. The outcome demonstrates that the proposed algorithm has a significantly more secure keyspace compared to the competing works.
Table 8. Comparative Study for key space.
and exhibit the correlation coefficients and entropy of the test images, respectively. Based on this result, it can be said that for the test images, the suggested encryption method has a low correlation between nearby pixels.
Table 9. Comparative study of correlation coefficient for different test images.
Table 10. Comparative study of information entropy for different test images.
Attacks
When transferred via the web or any other transmission method, the encrypted images might be distorted by interference and cropping threats, making it difficult to recover the plain images. As a consequence, the suggested algorithm's capability must be examined under various threats to establish its efficacy. To demonstrate the proposed algorithm's superiority, the Brain's 256 × 256 pixel encryption image has been modified by adding cropping (6.25 per cent data loss), Salt-Pepper noise (noise density 0.005), rotation (10%), translation, and scaling, as seen in . However, given the little PSNR fluctuation seen in , the data imply that the attacks had little effect on image resolution.
Figure 16. Results of the encrypted brain image with cropping, noise, rotation, translation and scaling attacks.
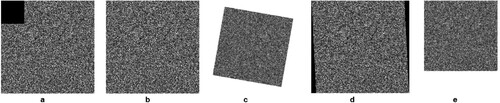
Table 11. PSNR values of decrypted Brain image after attacks.
However, results displayed in and demonstrate that the proposed algorithm does not alter the original information of the input image, during the encryption-decryption process. Although, some data loss occurs as a result of various attacks, as shown in . In this case, it is clear that the image has been altered or attacked, and such images may be discarded by physicians while examining the images for diagnosis for patient safety.
Efficiency analysis
In order to be effective, a cryptographic system must make efficient use of both time and hardware. The proposed algorithm is compared to others similar methods in the literature in , in terms of CPU usage, elapsed time and throughput. Here the comparative results show the superiority of the proposed method with compared literatures.
Table 12. Efficiency analysis.
Test U01
Increased efficiency in computation means that newly developed randomness systems need to be tested to an even higher standard. To ensure the suggested 5D logistic system randomness, we use the Uo1 test. It is possible to see that the percentages of passed tests range between 76.47 and 94.11% [Citation50]. According to [Citation51], a randomness generator or system that passes all NIST tests can still fail Test U01, although this is rare. As a result, Test U01 is a stricter and more extensive statistical test suite. illustrates the Test U01 analysis for the 5D logistic map; the results here are within the appropriate range as discussed above.
Table 13. Test U01 analysis.
Conclusion
In this paper, a novel 5D logistic map for clinical image encryption is proposed. This map is paired with DNA encoding and the Arnold Cat map for additional functionality. The most distinguishing feature of the method is its fundamentally nonlinear and high-dimensional architecture, which, despite its ease of construction, proves to be quite challenging in practice to decode. This is primarily attributable to the rigorous shuffling operations of rows and columns, which are carried out on an even and odd number basis, respectively. The PSNR, MSE, SSIM, entropy, correlation coefficient, NIST test and U01 test are the metrics that are used to evaluate the success of the proposed algorithm. The fact that the coefficient of correlation has values that are negative is evidence that there is no connection between the encrypted and the input image which satisfied in the proposed approach. In addition to this, the approach provides a relatively large keyspace, particularly in contrast to the keyspace provided by other methods. The algorithm performs well despite being subjected to various attacks. The results of this experiment may provide some insight on the process of creating such more 5D chaotic maps, which may be used to better protect the image and visual data for biomedical and normal grayscale images. Furthermore, the proposed method can be extended to improve the complexity and security of other chaotic maps with a similar topology. Furthermore, the proposed encryption system can be upgraded in the future to encrypt various media types, such as audio and video.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Notes on contributors
Bharti Ahuja
Bharti Ahuja is a Ph.D research scholar in the Department of Information Technology, National Institute of Technology Raipur. She has completed her master's from RGPV, Bhopal. Her area of research includes Image Encryption, Bio Medical Image security and applications of chaos theory in Cryptography. She is also a member of IE, ISTE, and IAENG.
Rajesh Doriya
Rajesh Doriya is currently working as an Assistant Professor with the Department of Information Technology, National Institute of Technology Raipur. He has completed his master's and Ph.D from IIIT, Allahabad. His area of research includes Distributed Computing, Cloud Computing, Artificial Intelligence, Robotics, Soft Computing Techniques and Network Security.
Sharad Salunke
Sharad Salunke is a Ph.D Scholar at the Department of Electronics and Communication Engineering at Amity University Madhya Pradesh, Gwalior and is also worked as an Assistant Professor in the Department of Electrical and Electronics Engineering at various institutes of RGPV, Bhopal. He is also a member of IE, ISTE, and IAENG. His research area includes Digital Signal Processing, Image Processing, and Bio Medical Image Processing.
Md. Farukh Hashmi
Md. Farukh Hashmi is currently serving as an Assistant Professor at the Department of Electronics and Communication Engineering, National Institute of Technology, Warangal. His current research interests are Computer Vision, Embedded System, Circuit Design, Image Processing, and Digital IC Design, etc. He is a member of IEEE, ISTE, and IAENG.
Aditya Gupta
Aditya Gupta is currently working as a postdoc in dept. of Information and Communication Technology, University of Agder, Norway. He has completed his Ph.D from the Electronics and Communication Dept., Visvesvaraya National Institute of Technology, India in 2019. His area of research is Artificial Intelligence for Aquaculture, Bio-Medical Signal Processing, Medical Image Processing using machine learning, and Water Resource Management for smart cities using data predictions and Machine learning techniques.
References
- Masood F, Driss M, Boulila W, et al. A lightweight chaos-based medical image encryption scheme using random shuffling and XOR operations. Wirel Pers Commun. 2021;127:1405–1432. doi:10.1007/s11277-021-08584-z.
- Wang H, Zhang D, Ding S, et al. Rib segmentation algorithm for X-ray image based on unpaired sample augmentation and multi-scale network. Neural Comput Appl. 2021:1–15 . doi:10.1007/s00521-021-06546-x.
- Gou J, Sun L, Yu B, et al. Multi-Level attention-based sample correlations for knowledge distillation. IEEE Trans Ind Informatics. 2022;XX(Xx):1–11. doi:10.1109/TII.2022.3209672.
- Stalin S, Maheshwary P, Shukla PK, et al. Fast and secure medical image encryption based on Non linear 4D logistic Map and DNA sequences (NL4DLM_DNA). J Med Syst. 2019;43(8):1–17. doi:10.1007/s10916-019-1389-z.
- Thoms GRW, Muresan R, Al-Dweik A. Chaotic encryption algorithm with key controlled neural networks for intelligent transportation systems. IEEE Access. 2019;7:158697–158709. doi:10.1109/ACCESS.2019.2950007.
- Bisht A, Dua M, Dua S, et al. A color image encryption technique based on bit-level permutation and alternate logistic maps. J Intell Syst. 2020;29(1):1246–1260. doi:10.1515/jisys-2018-0365.
- Elshamy AM, Hussein AI, Hamed HFA, et al. Color image encryption technique based on chaos. Procedia Comput Sci. 2019;163:49–53. doi:10.1016/j.procs.2019.12.085.
- Hu Y, Zhu C, Wang Z. An improved piecewise linear chaotic map based image encryption algorithm. Sci World J. 2014;2014. doi:10.1155/2014/275818.
- Sahay A, Pradhan C. Gauss iterated map based RGB image encryption approach. Proceedings of the 2017 IEEE International Conference on Communication and Signal Processing, ICCSP 2017, vol. 2018-Janua; 2018. doi:10.1109/ICCSP.2017.8286437.
- Krishna PR, Teja CVMS, Renuga Devi S, et al. A Chaos Based Image Encryption Using Tinkerbell Map Functions. Proceedings of the 2nd International Conference on Electronics, Communication and Aerospace Technology, ICECA 2018; 2018. doi:10.1109/ICECA.2018.8474891.
- Jain K, Aji A, Krishnan P. Medical image encryption scheme using multiple chaotic maps. Pattern Recognit Lett. 2021;152:356–364. doi:10.1016/j.patrec.2021.10.033.
- Akkasaligar PT, Biradar S. Medical image compression and encryption using chaos based DNA cryptography. Proceedings of B-HTC 2020 - 1st IEEE Bangalore Humanitarian Technology Conference; 2020. doi:10.1109/B-HTC50970.2020.9297928.
- Alabaichi A, Al-Dabbas MAAK, Salih A. Image steganography using least significant bit and secret map techniques. Int J Electr Comput Eng. 2020;10(1):935–946. doi:10.11591/ijece.v10i1.pp935-946.
- Sathiyamurthi P, Ramakrishnan S. Speech encryption algorithm using FFT and 3D-lorenz–logistic chaotic map. Multimed Tools Appl. 2020;79(25–26):17817–17835. doi:10.1007/s11042-020-08729-5.
- Safi HW, Maghari AY. Image encryption using double chaotic logistic map. Proceedings - 2017 International Conference on Promising Electronic Technologies, ICPET 2017; 2017. doi:10.1109/ICPET.2017.18.
- Dai J-Y, Ma Y, Zhou N-R. Quantum multi-image compression-encryption scheme based on quantum discrete cosine transform and 4D hyper-chaotic Henon map. Quantum Inf Process. 2021;20(7):1–24. doi:10.1007/s11128-021-03187-w.
- Hamdi M, Boudriga N. Four dimensional chaotic ciphers for secure image transmission. 2008 IEEE International Conference on Multimedia and Expo, ICME 2008 – Proceedings; 2008. doi:10.1109/ICME.2008.4607465.
- Li P, Xu J, Mou J, et al. Fractional-order 4D hyperchaotic memristive system and application in color image encryption. Eurasip J Image Video Process. 2019;2019(1):1–11. doi:10.1186/s13640-018-0402-7.
- Gafsi M, Abbassi N, Hajjaji MA, et al. Improved chaos-based cryptosystem for medical image encryption and decryption. Sci Program. 2020;2020:1–22. doi:10.1155/2020/6612390.
- Jeevitha S, Amutha Prabha N. Novel medical image encryption using DWT block-based scrambling and edge maps. J Ambient Intell Humaniz Comput. 2021;12(3):3373–3388. doi:10.1007/s12652-020-02399-9.
- Hajjaji MA, Dridi M, Mtibaa A. A medical image crypto-compression algorithm based on neural network and PWLCM. Multimed Tools Appl. 2019;78(11):14379–14396. doi:10.1007/s11042-018-6795-6.
- Wang R, Deng GQ, Duan XF. An image encryption scheme based on double chaotic cyclic shift and Josephus problem. J Inf Secur Appl. 2021;58:102699. doi:10.1016/j.jisa.2020.102699.
- Tsafack N, Kengne J, Abd-El-Atty B, et al. Design and implementation of a simple dynamical 4-D chaotic circuit with applications in image encryption. Inf Sci (Ny). 2020;515:191–217. doi:10.1016/j.ins.2019.10.070.
- Zhou J, Zhou N-R, Gong L-H. Fast color image encryption scheme based on 3D orthogonal Latin squares and matching matrix. Opt Laser Technol. 2020;131:106437. doi:10.1016/j.optlastec.2020.106437.
- Li S, Zhao L, Yang N. Medical image encryption based on 2D zigzag confusion and dynamic diffusion. Secur Commun Networks. 2021;2021:1–23. doi:10.1155/2021/6624809.
- Kumar S, Panna B, Jha RK. Medical image encryption using fractional discrete cosine transform with chaotic function. Med Biol Eng Comput. 2019;57(11):2517–2533. doi:10.1007/s11517-019-02037-3.
- Li T, Du B, Liang X. Image encryption algorithm based on logistic and two-dimensional Lorenz. IEEE Access. 2020;8:13792–13805. doi:10.1109/ACCESS.2020.2966264.
- Belazi A, Kharbech S, Nazish Aslam M, et al. Improved sine-tangent chaotic map with application in medical images encryption. J Inf Secur Appl. 2022;66:103131. doi:10.1016/j.jisa.2022.103131.
- Wu Y, Zhang L, Berretti S, et al. Medical image encryption by content-aware DNA computing for secure healthcare. IEEE Trans Ind Informatics. 2022;19(2):2089–2098. doi:10.1109/TII.2022.3194590.
- Yousif SF, Abboud AJ, Alhumaima RS. A new image encryption based on bit replacing, chaos and DNA coding techniques. Multimed Tools Appl. 2022;81(19):27453–27493. doi:10.1007/s11042-022-12762-x.
- Yousif SF, Abboud AJ, Radhi HY. Robust image encryption with scanning technology, the El-Gamal algorithm and chaos theory. IEEE Access. 2020;8:155184–155209. doi:10.1109/ACCESS.2020.3019216.
- Mishra P, Bhaya C, Pal AK, et al. A medical image cryptosystem using bit-level diffusion with DNA coding. J Ambient Intell Humaniz Comput. 2021: 1–22. doi:10.1007/s12652-021-03410-7.
- Ahuja B, Doriya R. A novel hybrid compressive encryption cryptosystem based on block quarter compression via DCT and fractional Fourier transform with chaos. Int J Inf Technol. 2021;13:1837–1846. doi:10.1007/s41870-021-00759-y.
- Malek K, Gobal F. Application of chaotic logistic Map for the interpretation of anion-insertion in poly-ortho-aminophenol films. Synth Met. 2000;113(1):167–171. doi:10.1016/S0379-6779(00)00194-6.
- Ferdush J, Begum M, Uddin MS. Chaotic lightweight cryptosystem for image encryption. Adv Multimed. 2021;2021:1–16. doi:10.1155/2021/5527295.
- Radwan AG. On some generalized discrete logistic maps. J Adv Res. 2013;4(2):163–171. doi:10.1016/j.jare.2012.05.003.
- Mansouri A, Wang X. Image encryption using shuffled Arnold map and multiple values manipulations. Vis Comput. 2021;37(1):189–200. doi:10.1007/s00371-020-01791-y.
- Abdulbaqi AS, Obaid AJ, Mohammed AH. ECG signals recruitment to implement a new technique for medical image encryption. J Discret Math Sci Cryptogr. 2021;24(6):1663–1673. doi:10.1080/09720529.2021.1884378.
- Zhang J, Fang D, Ren H. Image encryption algorithm based on DNA encoding and chaotic maps. Math Probl Eng. 2014;2014:1–10. doi:10.1155/2014/917147.
- Wang S, Peng Q, Du B. Chaotic color image encryption based on 4D chaotic maps and DNA sequence. Opt Laser Technol. 2022;148:107753. doi:10.1016/j.optlastec.2021.107753.
- Hua Z, Zhou B, Zhou Y. Sine-transform-based chaotic system with FPGA implementation. IEEE Trans Ind Electron. 2018;65(3):2557–2566. doi:10.1109/TIE.2017.2736515.
- Akkasaligar PT, Biradar S, Biradar S. Multilevel security for medical image using heterogeneous chaotic map and deoxyribonucleic acid sequence operations. Concurr Comput Pract Exp. 2022;34(24):1–21. doi:10.1002/cpe.7222.
- Shahna KU, Mohamed A. Novel hyper chaotic color image encryption based on pixel and bit level scrambling with diffusion. Signal Process Image Commun. 2021;99:116495. doi:10.1016/j.image.2021.116495.
- Dong Y, Zhao G, Ma Y, et al. A novel image encryption scheme based on pseudo-random coupled map lattices with hybrid elementary cellular automata. Inf Sci (Ny). 2022;593:121–154. doi:10.1016/j.ins.2022.01.031.
- Yasser I, Khalifa F, Mohamed MA, et al. A new image encryption scheme based on hybrid chaotic maps. Complexity. 2020;2020. doi:10.1155/2020/9597619.
- Tayachi M, Mulhem S, Adi W, et al. Tamper and clone-resistant authentication scheme for medical image systems. Cryptography. 2020;4(3):19. doi:10.3390/cryptography4030019.
- Yadav A, Saini B, Verma VK, et al. A joint medical image compression and encryption using AMBTC and hybrid chaotic system. J Discret Math Sci Cryptogr. 2021;24(8):2233–2244. doi:10.1080/09720529.2021.2011102.
- SIPI Image Database. Available from: http://sipi.usc.edu/database/database.php
- Aylward SR. Open-Access Medical Image Repositories; 2021. Available from: https://www.aylward.org/notes/open-access-medical-image-repositories
- Trujillo-Toledo DA, López-Bonilla OR, García-Guerrero EE, et al. Real-time RGB image encryption for IoT applications using enhanced sequences from chaotic maps. Chaos, Solitons Fractals. 2021;153:111506. doi:10.1016/j.chaos.2021.111506.
- Li J, Zheng J, Whitlock P. Efficient deterministic and non-deterministic pseudorandom number generation. Math Comput Simul. 2018;143:114–124. doi:10.1016/j.matcom.2016.07.011.