Abstract
Results to assist in the application of the ellipsoidal bounds provided by standard state-bounding algorithms are presented. They include derived bounds on scalar state-dependent quantities and the state values which determine them, tests of intersection and inclusion of ellipsoids, measures of how much an ellipsoid may be changed without altering its inclusion in another, and an ellipsoidal inner bound for the set reachable in the worst case from an ellipsoidal set by ellipsoidally bounded forcing, in a linear system. Approximations are suggested for the most computationally demanding result. Ways in which these results might be employed in aerospace interception problems are discussed to illustrate their utility.
1. Introduction
Recursive updating of bounds on the state of a dynamical system is a long-established alternative to probabilistic state estimation [Citation1 – Citation Citation Citation Citation Citation Citation Citation8]. At each observation instant, the error in a vector of observed output variables is assumed to have known bounds, so bounds on the outputs at that instant can be inferred from the observations. They are translated, via the observation equation, into bounds on the current state. The discrete-time state equation also imposes time-updated bounds on the state, by combining bounds on the state at the previous sampling instant and specified bounds on the effects of forcing inputs since then. The feasible set of state values consistent with all observations up to the present is found by combining the time-updated bounds and the new observation-derived bounds.
As new observations add state bounds, the feasible set becomes inconveniently complicated. A simpler outer-bounding approximation is therefore usually updated, the most popular choice being an ellipsoid. The ellipsoidal bound
Batch algorithms for ellipsoidal state bounding also exist [Citation7]. They usually produce much tighter bounds than do the recursive algorithms but are, of course, less suited to real-time use. The results in this paper are applicable to ellipsoids generated by either batch or recursive algorithms.
Ellipsoidal state bounds can be used for two purposes for which they are better suited than probabilistic state estimation yet which have received less attention than they deserve. The first is to produce bounds on practically significant, scalar functions of state. Bounds on certain variables may be needed for control or decision support when the state coordinate system does not give them directly, being chosen instead to give a simple model. For example, Cartesian coordinates are often convenient for modelling motion, while polar variables may be preferred for guidance or collision avoidance. Section 2 shows that bounds on scalar functions of state can be found from ellipsoidal state bounds in several important cases. By contrast, the mean and covariance of a nonlinear function of state cannot generally be derived from the estimated state mean and covariance, and are not readily found even if the state pdf is Gaussian.
The second potential use of ellipsoidal state bounds is to check whether the future state, subject to uncertainty, can meet some desired condition. Examples are checking whether the future state can definitely be brought into a specified desirable region, true if its feasible set is contained in that region; checking if two objects can be made to meet or to miss in future, as in interception or collision avoidance; and unequivocal fault detection when the feasible set is outside the ‘no fault’ region. It is fairly straightforward to detect whether two ellipsoids intersect or one contains the other. If they do not intersect, the smallest change (translation, expansion or contraction) required to make one ellipsoid intersect or contain the other can also be found readily. This may show, for example, what action is necessary for the whole range of uncertain predicted position of a target to be reachable, ensuring interception. Similarly, when one set contains the other, it is easy to find the largest expansion or contraction factor for which that remains true.
The next section gives results for bounds on state-derived scalar quantities. Section 3 considers the intersection and inclusion of ellipsoids, and ellipsoidal reachable sets. Section 4 illustrates their utility by outlining applications in aerospace interception.
2. Bounds on scalar functions of state
2.1 Linear functions
The extremes of a scalar, linear function
By use of Equationequation (3), the usual ellipsoid-updating state-bounding algorithms [Citation1 – Citation Citation Citation Citation Citation6] can be modified to make the state bounds as tight as possible in any nominated direction (e.g. that of a particular crucial state variable). However, this is at the cost of bound looseness in other directions, so a better idea is to find the feasible set as the intersection of a number of ellipsoids, each tight in a different direction. A refinement would be first to find the minimum-volume bounding ellipsoid by the standard algorithm, then to update the ellipsoids tightest in the axis directions of that ellipsoid.
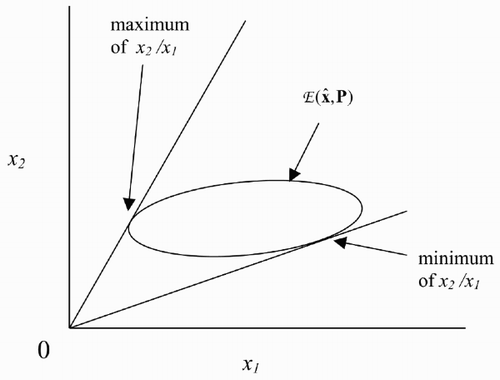
2.2 Ratio of two state variables
This case covers derivation of bounds on azimuth or elevation θ from joint bounds on Cartesian position components and their derivatives. For instance, for a target bounded by
As x 2/x 1 is constant on a hyperplane and is monotonic in the slope of the hyperplane, its extremes are the points of tangency of such hyperplanes with
2.3 Product of two state variables
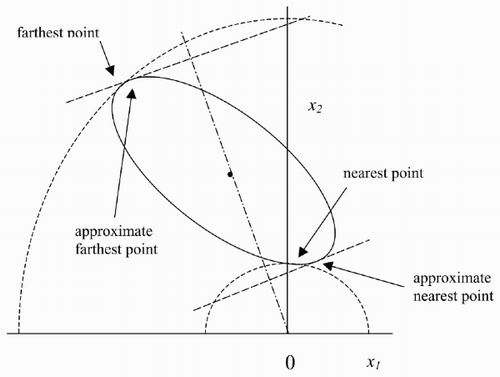
This covers, for instance, derivation of bounds on the vertical velocity component of a target from bounds on its velocity and the cosine of the angle of the velocity to the local vertical, convenient state variables in ballistic flight. To find the extremes of x 1 x 2 over
Figure 2. Points corresponding to roots of Equationequation (13).
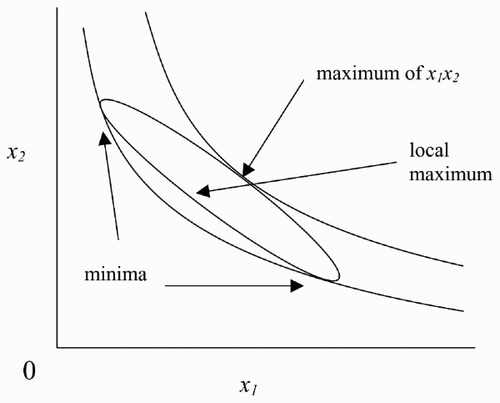
Example. The extreme points of x 1 x 2 on the boundary of
2.4 Positive-semidefinite quadratic form
The extremes of x T Qx on the boundary of the ellipsoid
The case where
The inverse in Equationequation (17) exists unless λ is an eigenvalue of PQ. In that case, the origin, the centre
In the generic case, premultiplying ∂L/∂x = 0 by
Computational cost may inhibit the use of Equationequations (19) and Equation(20) in conjunction with recursive state estimators at high update rates, so economical approximations may be useful. A very cheaply computed one is found by noticing that the terms of degree 2n and 2n – 1 in λ in the polynomial equation obtained by rationalizing Equationequation (19) are those of |PQ – λI|2, namely λ 2n ,− 2tr(PQ)λ2 n – 1. Hence, for a dominant root | λ| >> 1 an approximate solution is
The points of
Example. The points of
The simplest approximation
3. Operations on state-bounding ellipsoids
3.1 Test for intersection and inclusion of ellipsoids
Results Equation(17), Equation(19) and Equation(20) provide tests for inclusion and intersection of general ellipsoids
Test 3.1.1
Does
Moreover, if tests Equation(25) and Equation(26) are passed, the largest factor by which
The following complementary test to Test 3.1.1 reuses the affine transformation.
Test 3.1.2
Does
If Test 3.1.2 is passed, the largest ratio by which
Test 3.1.3
Does
Test 3.1.4
Are
The smallest factor by which
3.2 Largest expanded ellipsoid of given shape in a given ellipsoid
The problem is to find
By symmetry,
Example. Given
The eigenvalues of
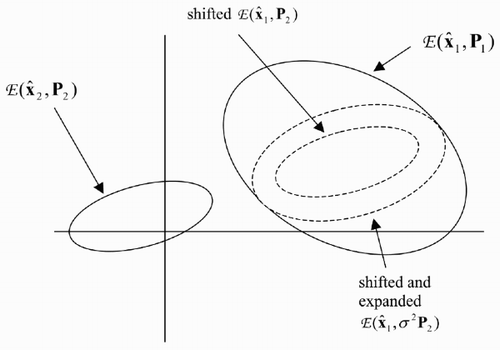
3.3 Worst-case-reachable set
The worst-case-reachable set comprises all future state values reachable, by the exercise of bounded forcing, from every point in the current feasible set. If the effect of forcing is additive (as in any system which is linear in additive forcing), the set is
That is, every point in
Denoting the vector sum of sets
The largest ellipsoid
To permit an analytical solution for
The width
With gs > 0 and gf ⩾ 0,Equationequation (39) requires at least one of α/β and 1/β to be greater than unity. It is easy to confirm that Equationequation (40) is satisfied by
The final step is to find the value of p maximizing the hypervolume of
As |R| is not zero, the trace in Equationequation (43) must be zero, giving
Noting that tr(A + B) = tr(A) + tr(B), this yields
A root-finder solves this polynomial equation for p; then, Equationequation (42) gives R for each positive root, and the one giving the largest |R| is selected. Δ
4. Illustrative use of results
4.1 Interception subject to uncertainty in threat trajectory
Terminal-phase guidance laws for ballistic-missile interceptors do not take account of longer-range factors such as target selection or economical use of fuel for manoeuvring. Control schemes with the potential to include these factors in mid-course navigation of the interceptor, through periodically updated constrained optimization of the interceptor's planned trajectory, are approaching computational practicability. In such schemes, the performance of the interceptor may be made less sensitive to uncertainty in the predicted target trajectory by two strategies. One is to rely on the feedback provided by periodic correction, reoptimizing the interceptor trajectory in the light of up-to-date observation of the target and applying each successive optimized control sequence only up to the next observation. The second strategy is to account explicitly for the uncertainty during the optimization. This is desirable if a number of candidate targets must still be considered, weighted by their perceived threat and the uncertainty in their trajectories, or if the uncertainty is large enough to pose a large risk, if ignored, that the control action is inappropriate even in the short term.
When uncertainty is included in the optimization, a worst-case optimality criterion suits interception. The predicted situation closer to interception is to be optimized in the most difficult case over the bounded uncertain future state of the threat. This has some similarity to employing a game-theory formulation of the problem [Citation10], but the connection will not be pursued here. The uncertain threat state prediction may be updated relatively easily, as new sensor measurements arrive, if it is in the form of an ellipsoidal feasible set
4.2 Interception with uncertainty in trajectories of both threat and interceptor
If the interceptor state is also significantly uncertain, worst-case-optimal guidance requires the maximum difference between the two states over both feasible sets. Generalizing Section 2.4 to find the maximum, over two ellipsoids, of a non-negative-definite quadratic form in the state difference is algebraically and computationally complex. Instead, the simpler strategy of making the predicted interceptor feasible set (usually much the smaller) first intersect that of the threat then be contained in it, positioned by some subsidiary criterion, is attractive. This requires the tests in Section 3.1.
4.3 Gauging of requirements to meet the control objective
The results of Section 3.2 indicate what nominal final state maximizes the permissible uncertainty about this value while still meeting a terminal control condition, expressed as an ellipsoidal set of acceptable final state values. It also gives the size of that uncertainty. It could, for instance, be used to indicate the change in nominal future interceptor state and the reduction in its uncertainty required to ensure that the interceptor comes close enough to the threat to guarantee successful interception.
4.4 Interception employing worst-case-reachable set
Computation of the worst-case-reachable set of the interceptor at each update allows the control sequence and choice of target to be optimized in full knowledge of the range of outcomes achievable. In the early stages of an engagement, the control can aim to keep as many objects as possible within reach of the interceptor or to keep specific objects reachable for as long as possible. Once the target is selected, a simple worst-case-optimal strategy is to make the reachable set at the predicted interception time cover, in the subspace of the state variables appearing in the control objective (including position components), as large an expanded version of the threat's feasible set as possible. That is, the range of future threat behaviour (about its predicted, perhaps optimistic, feasible set) over which interception is guaranteed is maximized.
Section 3.3 gives the largest ellipsoidal internal approximation to the set reachable in the worst case from an ellipsoidal feasible set by additive, ellipsoidally bounded forcing.
5. Conclusions
A number of results, with some approximations to reduce computational load, have been presented for deriving bounds on scalar state-dependent quantities from the ellipsoidal bounds produced by standard state-bounding algorithms. Tests of intersection and inclusion of ellipsoids have been based on them. An algorithm for computing an ellipsoidal worst-case-reachable set has also been obtained, and some ways in which these results might be employed in interception problems have been discussed to illustrate their potential.
Acknowledgements
This material results in part from work supported by the UK Ministry of Defence. The advice and encouragement provided by Martyn Bennett of dstl, Farnborough, are gratefully acknowledged.
References
References
- Chernous'ko , F . 1981 . Optimal guaranteed estimates of indeterminacies with the aid of ellipsoids. I, II . Engineering Cybernetics , 18 : 1 – 9 .
- Chernousko FL 1994 State Estimation for Dynamic Systems Boca Raton FL CRC Press
- Durieu C Polyak BT Walter E 1996 Paper presented at Proceedings of the 13th Triennial IFAC World Congress San Francisco CA
- Kurzhanski AB Valyi I 1997 Elliposidal Calculus for Estimation and Control Boston MA Birkhäuser
- Maksarov , DG and Norton , JP . 1996 . State bounding with ellipsoidal set description of the uncertainty . International Journal of Control , 65 : 847 – 866 .
- Maksarov , DG and Norton , JP . 2002 . Computationally efficient algorithms for state estimation with ellipsoidal approximations . International Journal of Adaptive Control & Signal Processing , 16 : 411 – 434 .
- Pronzato , L and Walter , E . 1994 . Minimum-volume ellipsoids containing compact sets: application to parameter bounding . Automatica , 30 : 1731 – 1739 .
- Schweppe , FC . 1968 . Recursive state estimation: unknown but bounded errors and system inputs . IEEE Transactions on Automatic Control , AC-13 : 22 – 28 .
- O'Connor JJ Robertson EF 1996 Quadratic, cubic and quartic equations Available online at: http://www-history.mcs.st-andrews.ac.uk/history/HistTopics/Quadratic_etc_equations.html (accessed 16 December 2003)
- Anonymous news release: New research analyzes the game of missile interception 10 July 2000 Available online at: American Technion Soc, http://www.ats.org/news.php?id = 13 (accessed 10 March 2004)