ABSTRACT
The theoretical framework of complexity is beginning to attract wider attention in research on the armed forces, and consequently the views of those who face complexity on the ground should be explored in more detail. Failure to do so risks complexity remaining only a top-level theory lacking adequate connection to practice. This article seeks to address this issue through analyzing the views of Finnish military officers. Data for the research were gathered using a deliberation and data collection method called a security café. A total of 74 people, most of them holding the rank of captain in the army or air force or lieutenant senior grade in the navy, attended the security café. The data used in this research were elicited from 47 idea rating sheets, evaluated during the security café, and include both quantitative and qualitative data. The article analyzes those data to address the following questions in relation to the theoretical framework of the article: What kind of perceptions of the complexity of the security environment do officers hold? What kind of practices do officers consider fit the presumed complexity of the security environment?
Introduction
“The international situation is the most complex and demanding that I have seen in all my years of service, and that’s over four decades.”
–General (ret.) Jim Mattis (Citation2017)
Several high-level military leaders have made reference to the growing complexity of the world. These include retired Generals Denis Mercier and Stanley McChrystal. Mercier (Citation2018) considers that the world has transitioned from being merely complicated to being complex and McChrystal et al. (Citation2015) note that the complicated challenges of the past were vastly different from today’s complex challenges. Both generals highlight an ability to rapidly adapt as a key requirement for anyone working in a complex operating environment, and the military is clearly not exempt from that requirement. A similar awareness of complexity is evident in official military documents, such as a 2015 U.S. Army publication, The Army Vision: Strategic Advantage in a Complex World and a 2012 Australian Army publication Adaptive Campaigning – Future Land Operating Concept. The former, for example, states that “over the next 10 years, it is likely the United States will face an unstable, unpredictable, increasingly complex global security environment” (U.S. Army Citation2015, 4). The latter includes the assessment, “while war has always been complex, the complexity of future wars will take a new form, necessitating greater adaptability from those actors that wish to be successful” (Australian Army, Citation2012, 23).
This matter has also been increasingly addressed in military science. Research has introduced readers to complexity science (e.g., Ryan Citation2009; Blouin Citation2013), deepened the understanding of complex adaptive systems (e.g., Dent and Holt Citation2001; Say and Pronk Citation2012), presented complexity embracing leadership tasks (e.g., Paparone et al. Citation2008; Hanén Citation2017) and also offered a critique of the over-popularization of system and complexity thinking (e.g., Thomas Citation2019). However, there is a research gap concerning how members of the military in general perceive complexity as a scientific concept. Given that the theoretical framework of complexity is beginning to attract wider attention in the armed forces, the views of those who face complexity on the ground need to be explored in more detail. Failure to do so risks complexity remaining a top-level theory lacking adequate connection to practice. This article seeks to address this issue through analyzing the views of Finnish military officers.
Research data were collected through a security café. A security café is a deliberation and data collection method developed for security authorities and researchers to access the opinion of the general public on issues of importance to their safety and security (see Puustinen et al. Citation2020). In this case, the method was modified to gather the views of the Finnish Defence Forces officers on complexity. However, the structure of the security café remained essentially the same as in the standard version of the model. Over a period of four hours, 74 café participants first received information on the topic of the event (i.e., complexity science), then deliberated in small groups of six to eight people and, as the last step, evaluated the ideas and arguments that emerged during the small group discussions, using the idea rating sheet method (see Zhang et al. Citation2016). The data used in this research were elicited from 47 idea rating sheets and encompass both quantitative and qualitative data. The data elicited were analyzed to address the following questions in relation to the theoretical framework of the article:
What kind of perceptions of the complexity of the security environment do [Finnish] military officers hold?
What kind of practices do [Finnish] officers consider fit the presumed complexity of the security environment?
The article is structured as follows. The article begins with a review of literature related to complexity, the armed forces, and warfare. Thereafter, the data and methods are described in more detail. This section also includes a brief description of the Finnish context. Then, the study moves on to analyze the perspectives of Finnish military officers on complexity. Finally, a discussion section binds these results to the theoretical framework of the article, and the conclusion section outlines potential research questions.
Complexity, the armed forces, and warfare
Defining the complexity (of warfare)
The essence of complexity lies in two core properties: variety and interdependence (Ryan Citation2009, see also Mitleton-Kelly Citation2003). Variety refers here to the many possible alternative states of the system and its parts, and interdependence to the intricate intertwining or interconnectivity between different actors and components within a system and between a system and its environment. As both Mercier (Citation2018) and McChrystal et al. (Citation2015) point out, complexity is a fundamentally different issue than complication (see also Cilliers Citation2011). Ryan (Citation2009) illustrates this point with the following example: A complicated problem is one involving an infantry mobility vehicle breaking down. Such a problem is reasonably straightforward for a subject matter expert to solve. First, the cause of the breakdown is diagnosed, perhaps necessitating some dismantling of the vehicle. Then the individual parts of the vehicle are repaired or replaced, after which the vehicle is reassembled into a functional unit. In the case of a complicated problem, it is also easy to evaluate whether or not the problem was solved. A complex problem could be represented by an infantry mobility vehicle breaking down in a hostile area. Due to time and context sensitivity, the problem cannot be solved by reductionist approaches. Instead a holistic approach that acknowledges the trade-offs and interrelationships would be required. Moreover, in the case of complex problems blueprints have a limited application as every problem is unique and the outcome of a problem-solving process is always uncertain (see Glouberman and Zimmerman Citation2002).
Complexity-oriented military scientists seem to agree on the complexity of warfare (e.g., Ryan Citation2009; Say and Pronk Citation2012; Rousseau Citation2003; Maher Citation2014). They also acknowledge that complexity is not a new feature of warfare, but one previously recognized by military strategists and theorists such as Sun Tzu and Carl von Clausewitz (Dent and Holt Citation2001). An interesting development is that the complexity of warfare is generally viewed as increasing. This is mainly due to two core factors (Ryan Citation2009; Say and Pronk Citation2012; Maher Citation2014). First, the operating environment is becoming more and more connected, especially because of increased globalization and the development of information and communications technology. As a result, local phenomena can be very effective in influencing issues and phenomena, even globally. This relates to the concept of the strategic corporal which raises the possibility that actions of one individual at the tactical level can have dramatic and unforeseen impacts on operational and strategic scales (see e.g., Storr Citation2003). Second, the increasing amount of information, its ambiguity, and the speed of information flows pose significant challenges to the ability to handle the uncertainty and instability of the operating environment. As Say and Pronk (Citation2012, 120) summarize, “things are happening faster, and the activities of seemingly distant actors are now having a more rapid and often more significant impact.”
Looking at how warfare has changed over time can help understand this perceived increase in complexity. Zweibelson et al. (Citation2017) define three different war movements. First, the classical military movement starting in ancient times and peaking in the late 1600s–1800s. At that time, states prosecuted limited wars, following the mechanistic logic of linear decision-making. During this period, it was possible to start and conclude wars within the period of a single battle. The second period is referred to as the modern military movement, and it spans the 1800–1990 period. Warfare became attrition-based total war. Complexity began to increase and approaches such as engineering, science, reductionism, and hierarchical command and control to dominate. Very few conflicts would be resolved by single battles. Next came the post-modernist military movement, which began in the 2000s; wars became highly asymmetric as the role of non-state actors and networks increased (see Marion and Uhl-Bien Citation2003; Bousquet Citation2012). In this complex and emergent post-modern security environment, many issues became blurred, including, among others, the line between war and peace and the areas of operation of the armed forces. As Zweibelson et al. (Citation2017, 91) state, “many of the non-military phenomenon seem to be linked in complex and non-linear ways with those that are decidedly in the purview of an Armed Forces.” In a similar temporal fashion, Bousquet (Citation2008) defines four regimes within the scientific way of warfare. These regimes and their paradigmatic technologies are mechanistic warfare and the clock; thermodynamic warfare and the engine; cybernetic warfare and the computer; and chaoplexic (a combination of chaos and complexity) warfare and the network.
Nevertheless, the assertion that complexity is increasing is not universally accepted. Tourish (Citation2018) wonders whether the challenges humanity faced in the past – such as the Great Depression in the 1930s and rebuilding Europe after World War II – were truly less complex than the challenges faced today. Tourish surmises that every new generation might imagine the problems it faces are more challenging, faster-paced, and complex than those faced by previous generations. On the other hand, it is also worth noting that the view of increasing complexity may be colored by the expanding awareness of the complex nature of warfare (see Ryan Citation2009). The discussion about increasing complexity is also challenged by the fact that there is no agreed definition of complexity; thus, there is not even complete certainty over what any measure of the perceived growth of complexity should encompass (Lineweaver et al. Citation2010).
Another interesting discussion is the extent to which complexity can be taken out of the equation. Can, for example, the uncertainty caused by complexity be reduced or eliminated entirely with the advancement of information and communications technology? More specifically, the question is if the sources of uncertainty are not fundamental but stem from limits to the available technology (see Ryan Citation2009). Rousseau (Citation2003) discusses the issue from the perspective of battlespace visibility. He states that non-linear dynamics make war uncertain in a fundamental way: “Uncertainty is not merely an initial environmental condition that can be reduced by gathering information and displaying it on a computer screen. It is not that we currently lack the technology to gather enough information but will someday have the capability.” (Rousseau Citation2003, 37) Similarly, Richardson et al. (Citation2000, 39) consider that the incompressibility of complex systems problematizes military operational analysis, that is, due to sensitivity to initial conditions and the blurring of boundaries, “it is impossible to have an account of a complex system that is less complex than the system itself.” Additionally, Ryan (Citation2009) shares a Clausewitzian view that more information can, in reality, often increase uncertainty and be false or contradictory. Storr (Citation2003), among others, states that information and communications technology can make war and armed conflict even more complex and dynamic, as it increases and intensifies the connectivity between people. Finally, Zweibelson (Citation2016a, pp. 29–30) introduces the concept of Jominian Hindsight, which depicts the fundamental complexity of warfare and the harmful habit of abstracting it out:
According to [Antoine-Henri] Jomini, a military leader would win any military conflict with the proper combination of his principles, be it mass and surprise and speed, or perhaps x, y, and z. If any commander applied them and failed, the ‘Jominian Hindsight’ responds with, “You did not apply my principles correctly.” These endless cycles of methodological tinkering remain superficial, in that they fail to address the deeper issues that plague accurate sensemaking and anticipation of complex military scenarios. We are most apt to critique (or fire) the military leader, fiddle with the methodology, and reboot with the same processes in play wearing slightly different clothing.
Operating in a complex security environment
Kopsch and Fox (Citation2016) highlight the role of problem framing. It is important to not only identify the right problem, but also to be aware of the type of the identified problem and its possible connections to other problems. Misidentifying the problem at hand – for example seeing a complex problem as a merely complicated one – can easily lead to the wrong approach to the right problem and severely hinder the implementation of an effective operational approach. The military leader should then be careful not to tame complex problems (see Churchman Citation1967), but also not to step into a complexity trap, to overcomplicate everything (see Raisio and Lundström Citation2015). Therefore, a complexity-aware leader ought to be able to separate routine management issues from the more complex variants.
In addition, one of the central principles of operating in a complex environment is that the complexity of the system and the system environment should in a sense be in balance. The basis for this notion has been ascribed to Ross Ashby’s law of requisite variety, the central message of which can be summarized as “only variety can destroy variety” (Ashby Citation2011, 206). The development of complexity sciences has allowed Ashby’s law to be modified into a law of requisite complexity, according to which the complexity of the system should correspond to the complexity of the system’s environment (Boisot and McKelvey Citation2011). A related notion is that of Bar-Yam (Citation2004, Citation2015) who distinguishes between conventional and complex conflicts and warfare. Conventional conflicts – such as the Gulf War – necessitate tightly coordinated and hierarchically controlled large-scale military behavior. In complex conflicts – such as the war in Afghanistan – high variety behavior becomes important. Such fine-scale behavior is semi-autonomous and weakly coordinated, able to take advantage of the “space of possibilities” (Bar-Yam 2004, Citation2015; see also Blouin Citation2013). Structures of military organizations should then ideally match the tasks to be accomplished, that is, to have matching complexity profiles. As stated by Bar-Yam (Citation2004, 43), in relation to Al-Qaeda, “the asymmetric war against terrorists is generally understood to be highly complex, and the large number of possible actions that might have to be taken is a clear indicator of the variety necessary of the system that might effectively oppose them” (see also McChrystal et al. Citation2015; Norman and Bar-Yam Citation2018).
Mercier (Citation2018) aptly describes, in the context of NATO’s adaptation in an age of complexity, this tense relationship between large-scale and fine-scale behavior. In this context, large-scale behavior could be understood to refer to NATO’s ability to manage the requirements of a large-scale, all-out conflict. Fine-scale behavior is then more about NATO’s flexibility to be able to adapt to the evolutions of the operational environment. March (Citation1991) originally described this as a tension between exploitation and exploration. Exploitation is characterized as refining, selecting, implementing, and executing operations, whereas exploration is an activity based on searching, risk taking, experimenting, discovering, and innovating. While exploitation rests on established routines, exploration emphasizes the identification of new opportunities and alternatives. Ideally, any military organization would need to be able to operate simultaneously, or ambidextrously, and thus balance on the “edge of chaos” (Mercier Citation2018, see also Uhl-Bien and Arena Citation2018).
In addition to the need for detailed problem framing and the importance of having matching complexity profiles, more specific modes of action to operate in a complex security environment have also been mentioned in the literature. One such operating model is the mission command. The term relates to “decentralisation and local flexibility within the overall intent [of the superior commander]” (Storr Citation2003, p. 126, see also Rousseau Citation2003). The premise is that when subordinates are not restricted by overly strict orders, they can be creative, make independent decisions, and adapt to changing circumstances. The superior commander’s intent then serves as a guiding principle, but with the minimum of control measures. The same applies to military organizations in general. If military organizations are understood as complex adaptive systems, their self-organizing potential should not be unduly restricted, as to do so would hinder their capacity to adapt to a changing environment. Instead, organizational values and visions – in a similar fashion to a commander’s intent – would “provide the organization with a strong anchor that will enable self-renewal without experiencing chaos” (Dent and Holt Citation2001, 104).
The literature also highlights whole-of-government approaches, such as the Swedish Total Defence concept (see e.g., Zweibelson et al. Citation2017) and the Finnish Comprehensive Security concept (see e.g., Puustinen et al. Citation2020). These approaches are based on the idea that complexity ought to be addressed by a range of actors, instead of by any single authority. Complex problems, in a sense, exist between the spaces of different actors, resulting in the problem no longer belonging to any one actor alone. Roles blur as armed forces are becoming more involved in what are termed military operations other than war and as civil agencies are working more closely with the military organizations. Ideally, deeper cooperation within the armed forces as well as between the armed forces and other actors would lead to more holistic approaches rather than actors being limited to strictly defined areas of responsibility (Dent and Holt Citation2001; Zweibelson et al. Citation2017).
Context, data, and methods
The Finnish context
The Finnish approach to security has evolved over time to reflect changes to the international security environment and new approaches to it. The idea of expanding security as a concept, both vertically and horizontally, is a global phenomenon, especially in the Western security mindset. However, there are some features in the Finnish context that influence the development of the Finnish security approach and its current character.
Finland has a long history of being located between East and West, having for hundreds of years been part of the Kingdom of Sweden, and later an autonomous region of Tsarist Russia, and for the last hundred years an independent state. The society has been carefully moving toward alignment with Western Europe but still balancing a position in the sphere of influence of the Soviet Union, and later integrating into European institutions and anchoring in the West – and the whole time far in the North, at the edge of Europe. The survival of a small state has required adaptable solutions at quite different times.
Finland’s geopolitical situation has been reflected in the processes of Finlandization, a product of Finland’s Agreement of Friendship, Cooperation, and Mutual Assistance with the Soviet Union. Finlandization can be defined here for example as “a voluntary foreign policy strategy or, in a lesser sense, a foreign policy instrument that aims to reassure a more powerful state, usually a neighbour, either through bilateral politics or other means such as reinforcing regional stability through a neutralist foreign policy posture.” (Juntunen Citation2017, 65). In general, Finland’s security policy has always involved a process of balancing; avoiding provocation and strengthening international norms and institutions, with Russia’s strength or weakness in any particular period influencing the direction and strength of the movement. During the Cold War, Finland declared itself a neutral country, and accepted responsibility for its own defense.
Since the end of the Cold War, the wording Finland uses to describe its status has changed to militarily non-aligned and defense cooperation has increased internationally, including through participation in a range of peacekeeping operations both traditional and otherwise. Finland has historically emphasized the importance of foreign policy as a means of influencing its security environment. In this sense, the traditional Finnish approach is aligned with increased international cooperation (especially with Sweden, see e.g., Lundqvist and Widen Citation2016; Møller Citation2019; Wither Citation2020) and an attempt to influence security beyond the state’s own borders or the near abroad. On the other hand, Finland is still preparing for highly unlikely but serious consequences of traditional national defense scenarios that must be confronted with a national set of tools.
Another feature that has a direct impact on security thinking is the fact that Finland’s military defense is still based on conscription and a large body of reservists (see Kosonen et al. Citation2019). Military conscription has a relatively high level of acceptance and even today around 65% of men in the required age group complete military service. The maintenance of conscription means the defense forces address the issue of their acceptability in society in a direct interaction with a large part of the population. The conscripts and their relatives get an idea of the use of armed forces and military threats, and the defense forces also confronted with their trainees’ views on various security situations.
As the perspective on security broadens, the notion of comprehensive security offers at least a partial solution to potential security issues. Comprehensive security is a widely accepted starting point for a model in which important functions of society are protected and sustained cross-functionally in all circumstances and in the face of various crises or disruptions (see The Finnish Government Citation2017; Griffith Citation2018; Wither Citation2020). The Finnish Concept for Comprehensive Security is worthy of mention owing to its two specific features: In Finland, exceptionally well-established and far-reaching cooperation between different actors is sought and a very large number of actors have been successfully integrated. In addition to the authorities, representatives of industry, academia, and non-governmental organizations, as well as individual citizens, are actively involved in the Finnish model. In Finland, the notion of security is commonly understood to refer to both individual safety and collective security. The vertical widening of the security concept down from governmental or even inter-governmental level down through organizations and individuals therefore feels natural even if the broadening of perspectives seems to add to the complexity of the matter.
A security café as a data collection method
The security café is an adjusted deliberative democratic method deriving from the ideals of deliberative democracy and deliberative mini-publics (Puustinen et al. Citation2020). Deliberative democracy is a form of democracy that values discussion, reflection, and consideration over simply voting or responding to a questionnaire (e.g., Yankelovich Citation1991; Chambers Citation2003), and is often seen as an umbrella term for a wide variety of innovative deliberative democratic processes (e.g., Nabatchi Citation2010). These are commonly called deliberative mini-publics (Grönlund et al. Citation2014). The security café is a combination of the traditional citizens’ jury and world café methods, and as such, can be positioned between the intermediate and expansive definition categories of deliberative mini-publics (see Ryan and Smith Citation2014).
A security café typically lasts for three to five hours and involves receiving information, facilitated small group deliberations, and the use of idea rating sheets. In previous projects, the security-café method has been used to involve ordinary citizens in deliberations on issues related to the domains of safety and security (e.g., asylum seeker policy and hybrid threats), and also to harvest the viewpoints of local and regional public authorities and NGO representatives on the co-creation of safety and security in Finland (see Puustinen et al. Citation2020).
In this case, the security-café method was modified specifically to gather the views of Finnish military officers on complexity. The aim was to keep the structure as similar as possible to the original model. Ideally, security cafés aim to enroll a large number of people and to choose a diverse group of around 25–30 participants. This time, however, the participants were pre-selected. Participants were students on a general staff officer course, and the security café was inserted into their course. A total of 74 people attended the security café and all but one were military officers.Footnote1 Of the 73 officers, most were captains in the army or air force or lieutenants (senior grade) in the navy, although there were also a few participants holding the rank of major and lieutenant commander. Seven officers of the national border guard were also part of this group.
The four-hour event, implemented in August 2019, began with an introduction of the security-café method, which was followed by an hour-long lecture on complexity thinking conducted by the two authors of the article. The lecture covered the differences between the mechanistic Newtonian paradigm and the complex‐systems paradigm, and we placed particular emphasis on the concepts of non-linearity, self-organization, emergence, and the edge of chaos. The participants were offered the opportunity to ask specific questions at the end of the lecture. Next, the participants were divided randomly into groups of six or seven people. Unlike traditional security cafés, the groups did not have external facilitators, but for practical reasons, the participants selected the facilitators themselves. The café consisted of three rounds of deliberations: 1) complexity and the global security environment, 2) complexity and the Finnish security environment and 3) how complexity should be taken into account, for example, in the preparation and implementation of national security and defense policy. In practice the themes and rounds overlapped during the deliberations.
An important part of a security café is the use of idea rating sheets (see Zhang et al. Citation2016). During the small group deliberations, each group was provided with five blank idea rating sheets. Each time an idea/statement emerged that the group wanted the whole café to evaluate, they wrote it on the sheet (see the top left corner of the sheet in ). Idea rating sheets are a method for recognizing points of agreement among a large number of people. Participants simply record their level of agreement with any given idea on the sheets. This results in a graph-like visual representation of the group’s collective opinion. (Diceman Citation2014, p. 4.)
Figure 1. An example of an idea rating sheet from a previous security café (originally Diceman Citation2014)
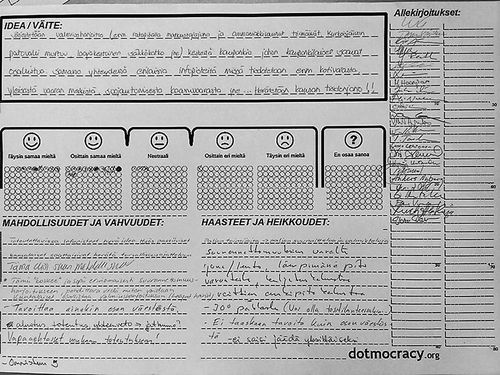
During the last step of the security café, idea rating sheets were collected and spread on tables to allow the participants to evaluate them. First, participants rated their views on the ideas on a 6-point Likert scale anchored with strongly agree and strongly disagree, and with a do not know option offered too. Commenting on the idea rating sheets follows the basic logic of a SWOT (Strengths, Weaknesses, Opportunities, and Threats) analysis, in that each participant could comment on each sheet, write about the opportunities and strengths plus the weaknesses and threats related to the presented idea (see the bottom left corner of the sheet in ). Due to the large number of café participants and the limited size of the sheet (A3), participants could also post their comments on sticky notelets and such contributes were considered part of the content of the ranking sheet. A total of 42 idea rating sheets were generated and evaluated during the café event, and the participants were also asked to contribute to five idea rating sheets prepared in advance by the researchers. The purpose of those five sheets was to enable specific comparisons to be made if similar security cafés were arranged in the future. The café participants were not able to see these pre-prepared idea rating sheets until the end of the café event when they evaluated the entire collection of 47 sheets. The contents of the pre-prepared sheets thus had no effect on the small group discussions.
All 47 idea rating sheets were transcribed. Participants were not required to contribute to all the sheets, so the number of respondents ranged from 33 to 61, with an average of 47 responses per sheet. The number of sheets may have caused some rating fatigue among the participants, and we cannot be certain that some sheets were not just overlooked by some respondents. The responses on a Likert scale constitute the quantitative data of this article. The sheets contained between eight and 29 comments, with an average of 17 comments per sheet. These comments, and the ideas/statements themselves, constitute the qualitative data of the article.
The analysis began with a detailed review of the transcribed idea rating sheets so as to derive an overall view of the data. Next, in order to facilitate the processing of the sheets, ideas were deductively combined into concrete themes, broadly divided under the two research questions: For example, ideas/statements related to the cooperation between public authorities, the role of citizens, and the Finnish Concept for Comprehensive Security formed a main category (theme) labeled whole-of-government approaches. After the themes had been formulated, the comments on the sheets associated with each theme were categorized meaning the comments were not analyzed by sheet but by theme. This approach permitted a broader understanding, especially since the ideas/statements within each theme were broadly similar.
Owing to the large number of idea rating sheets, the following results section will not explicitly review them all, and the focus is more on themes rather than individual sheets. In addition, due to the length of ideas/statements presented on the idea rating sheets, it is not possible to present them in their entirety, for example as a tabulated part of the text. However, the ideas/statements explicitly mentioned in the text are reproduced in full, with frequency distributions, in the endnotes. For direct quotes, the texts of the idea rating sheets were translated from Finnish to English. For the sake of clarity, we will mainly use the term statement in the next results section when describing an idea or statement written on an idea rating sheet during small group discussions (i.e., the top left corner of the sheet in ). Similarly, we mainly use the term comment when describing participants’ individual assessment of ideas or statements made in the idea rating sheets (i.e., the bottom left corner of the sheet in ).
When analyzing and interpreting the results of this security café, it is important to bear in mind the possible effects of the context (the general staff officer course at the National Defence University) and the potential normative authority the military context may impose on the deliberation. The small groups only consisted of officers of similar rank (as described earlier), but most importantly, they worked as classmates, not as part of a hierarchical chain of command. None of the participants’ senior officers were present in the groups, nor were their teachers or the researchers, thus ensuring as neutral and open a discussion space as possible. Due to the potential for normative authority to appear in military contexts we might assume a reasonably homogenous distribution of both ideas presented in the deliberations and opinions expressed when rating those ideas; however, ideas and opinions were widely dispersed, as will be demonstrated in the results. The situation permits us to cautiously infer that the ideas and opinions expressed are the genuine opinions of the individuals, and not only statements echoing the normative military canon.
Results
The results are presented following the logic of the two research questions. First, we report the perceptions of the officers on the complexity of the security environment (the first research question), after which the practices that the officers associated with working in complex contexts are analyzed (the second research question).
Perceived complexity
One of the idea rating sheets prepared in advance by the researchers presented a statement that the current security environment is complex. The majority of the respondents (92%) declared themselves partly or fully in agreement with this statement.Footnote2 However, the comments in the sheet emphasized that this is not a new feature, as exemplified by the comment: “The security environment has always been complex!” Complexity was considered to be ever present wherever human beings are, though the perceived difference is that “ … now we are just more aware of its inevitable existence.”
The café participants expressed more diverse views on the recent growth of complexity. One idea rating sheet included a statement that the level of complexity does not really change, that is, complexity only appears to be growing over the course of time, particularly owing to increased volumes of data and accelerated data transfer.Footnote3 As one participant commented, “transmission systems do not add complexity, but do make it visible.” Several other idea rating sheets did however challenge that view. Four sheets, albeit using different wording in their statements, explicitly highlighted how digitalization increases the complexity of the global security environment; a statement agreed upon by a clear majority of respondents contributing to each sheet. Social media was seen as a “fierce catalyst”.Footnote4 Other factors mentioned included information overload, real-time decision-making and the lack of delay, and limited human data processing capability.Footnote5
The aforementioned idea ratings sheets, clustered around the theme of digitalization, provided detailed commentary on how digitalization might be hoped to aid operating in a complex security environment. As an opportunity provided by digitalization, the development of analytical tools – especially artificial intelligence – was highlighted as a way to facilitate better and faster interpretation of data and information, and to develop foresight: “Humans have limited cognition. Artificial intelligence will make up for it.” “There is more information, but it is getting easier and easier to manage.” “The fact that something cannot be controlled now does not mean that it cannot be controlled [in the future].” Digitalization can then be perceived as a double-edged sword. While more sophisticated analytical techniques seem to be expected to reduce complexity, many other issues related to digitalization can in turn increase it. Examples offered of such issues included network security vulnerabilities, and the increase in the number of actors in the operating environment. This latter issue was explicitly commented on: “Social media and digitalization will increase the number of potential influencers as information sharing is easy.”
The impact of globalization on complexity – as in the increasing global level intertwining and interconnectivity – was also addressed on several idea rating sheets. One sheet contained a statement that Finland would no longer be “a land of milk and honey” and that many global threats currently affect Finland’s security environment.Footnote6 A large majority of the respondents (88%) agreed with this statement. The statements on two idea ratings sheets even claimed that Finland’s security environment today is – in its fractal nature – the same as the global security environment. However, the respondents’ views were divided on those two sheets; a slight majority (59% and 64%) believed that the Finnish security environment still has its own special features that seem to create a sensitivity to initial conditionsFootnote7.Footnote8 These features were, among others, “location on the map” and maintaining a large military reserve force. As one café participant commented, “[national] states also face internal and regional threats and challenges, all of which may not be reflected far and wide.”
In a reference to globalization, one idea rating sheet claimed the diversification of threats increased disruptions in the global security environment.Footnote9 This was a view supported by a slight majority of the respondents (57%); an example of a comment indicating such support being: “complexity is created by non-state actors and their interests.” However, just as the “novelty” of the complexity of the security environment was questioned above, so too was the notion of the diversification of threat. A comment asked for example, if people thought that terrorism had not existed before the current time. Other contributions suggest that today we might just be more aware of possible threats than in the past and this awareness itself triggers the perception of increasing and diversifying risks, while the actual situation may not have changed significantly from that of the past.
In the context of the somewhat divided debate above, it is important to consider whether the emphasis on increasing complexity only makes issues more complex than they actually are. This issue was addressed in the content of one of the idea rating sheets prepared in advance by the researchers. The sheet included a statement that we often step into a complexity trap, that is, we tend to make the problems we face more complex than they are.Footnote10 A majority of respondents (68%) agreed with this statement. One café participant warned that perceiving issues as too complex carries the danger that we fall into “paralyzing relativism.” However, another comment noted that we often succumb to simplifying issues and drawing conclusions too quickly, or as one of the café participants stated, “to understand issues, the human/soldier tends to simplify, not to complicate (as there is no time).” Moreover, comments added to another pre-prepared sheet strongly questioned whether only complex solutions can solve the problems of a complex operating environment.Footnote11
Practices for operating in a complex security environment
Concepts and policies
One pre-prepared idea rating sheet addressed the general question of whether the concepts of complexity help to improve understanding of the security environment.Footnote12 The majority of the respondents (71%) agreed with that they did. These concepts were seen as broadening thinking, supporting complexity leadership, and “[helping] to understand that not everything can be understood.” Here, however, the difficulty in understanding the concepts was perceived as a complicating factor. In addition, one participant commented that “the concepts of complexity are, in part, just a terminology gimmick.” At its worst, concepts of complexity were seen to adversely affect the clarity needed for decision-making.
At the macro level, café participants working in small groups discussed the importance of safety and security related policies and their suitability to a complex operating environment. The views of the respondents were almost evenly divided as to whether Finland’s policies would be appropriate to address the country’s complex security environment.Footnote13 This particular theme was also accompanied by a statement made on another idea rating sheet that Finnish security policy aims to respond to a complex security environment by maintaining options (e.g., the NATO option).Footnote14 The majority of respondents (71%) partially agreed with the statement. This stance of maintaining options attracted the most comments in relation to safety and security related policies and complexity. Maintaining options was seen as a way to preserve the ability to respond to multiple situations and to increase adaptability: “Not everything can be predicted, but adaptivity helps to react.” Then again, this stance was also strongly criticized. Some participants stated that too many options stifle action and could lead to aims and objectives becoming hazy, and thus to indecision. Café participants pointed out that “despite the complexity, decisions have to be made” and that “‘indecision’ is the better word to describe the maintenance of options.”
The whole-of-government approaches and resilience
In the spirit of holistic whole-of-government approaches, one of the idea rating sheets contained a statement that rather than producing separate security and defense policy related reports to guide Finland’s policies, the Finnish Government should produce only a Comprehensive Security report.Footnote15 However, the majority of respondents (66%) were critical of this idea, and the reasoning offered included that such a holistic report could easily become too general and extensive, which in turn would make planning its execution more difficult and not give sufficient direction for the development of defense policy. At the operational level, however, the café participants’ attitude toward the Comprehensive Security policy was significantly more positive. A total of nine idea rating sheets, one of which had been formulated beforehand by the researchers, dealt directly with this theme.
A large majority of respondents (90%) considered the Finnish Concept for Comprehensive Security to be Finland’s response to the challenges of the complex security environment.Footnote16 All of the respondents strongly or partially agreed that the cooperation between public authorities would increase the resilience of society and its ability to respond to a complex operating environment.Footnote17 The content of one idea rating sheet did, however, emphasize that the Comprehensive Security model must be adaptive to respond to the complexity of the security environment.Footnote18 The reality of this statement could be evaluated through the pre-prepared idea rating sheet,Footnote19 which included a claim that the Finnish concept of Comprehensive Security is adaptive, that is, adaptable to the challenges of a complex operating environment. Respondents were relatively positive about this, with only 22% holding a critical or neutral view.
In their comments, participants particularly highlighted the diversity of capacities as a positive aspect of the Finnish Comprehensive Security model. It was considered that “Comprehensive Security harnesses many different capabilities [in society]” and thus “increases the range of means to respond to a broad threat base.” Furthermore, the agility of the model was mentioned. When prompted to consider developments, respondents advocated that the boundaries between organizations should be lowered further than currently. This was seen as particularly related to the development of legislation. The participants also pointed out that it is too restrictive to consider the issues of comprehensive security and societal resilience solely from the point of view of the public authorities: “In addition to cooperation between authorities, it is important to strengthen the resilience of citizens” and put another way, “Resilience comes from the people, not the authorities.”
The preceding issues of resilience and citizen involvement were addressed on three idea rating sheets. Café participants were rather divided on whether resilience should be strengthened by committing each citizen to the tasks of comprehensive security as a way of responding to a more complex operating environment.Footnote20 They, for example, expressed doubts about the citizens’ commitment to genuine action. The participants were slightly more united in feeling that safety and security issues should be communicated better throughout society than they are currently, which they thought might be achieved through introducing security issues into education and reinforced during upbringingFootnote21 .Footnote22 As one participant commented, “The Comprehensive Security model and the resilience of society should be incorporated into the education of every citizen.” However, there was some concern expressed in the appended comments over citizens’ capability to understand complex issues: “Understanding extreme complexity requires years of familiarity. Also, in the future, the majority of the population will not reach this [level of] understanding.”
Reducing hierarchy and enabling self-organization
A distinct group of four idea rating sheets included statements on the need to reduce hierarchy levels and enable self-organization. The majority of the respondents (75%) considered that bureaucratic and hierarchical command structures make it difficult to adapt in a complex operating environment.Footnote23 Accordingly, complexity should be taken into account in the implementation of the Comprehensive Security model by delegating power to authorities at the lower levels of the hierarchy, increasing the freedom of action of executive authorities and establishing a cooperative relationship at ever lower levels of authority.Footnote24 A strong majority of the respondents (85%) supported that approach either fully or partially. Another sheet included the statement that moving the decision-making power as low down the hierarchy as possible would require everyone to act in accordance with the mission command to achieve the common objective (i.e., Comprehensive Security) .Footnote25 Another sheet contained the proposal that having a mission command is a way to handle complexity, a statement with which a majority of the respondents (81%) agreed.Footnote26
In the comments, the benefits of relatively flat hierarchies and self-organization were particularly associated with increased agility and adaptability. As café participants commented, “organizational hierarchy does not encourage adaptability” and “a lack of freedom of action kills adaptability” However, the participants did not see this as an either-or issue but saw merit in a relatively tall hierarchy too. The respondents were aware that in the security context the actors at the lower levels may not always see the whole picture, and hence, “overly autonomous lower-level leaders may, from their own perspective, make excellent decisions, but, those decisions may not be the most efficient and effective for the whole.” A mission command was seen – as long as the objectives are clearly defined and understood throughout the organization – as facilitating agile action in unexpected situations by enabling leaders to perform the task in the way they see fit. The counter opinion expressed was that an over emphasis on a mission command structure could also be seen as commanding officers escaping responsibility.
Resources involved in responding to complexity
The last broader theme, represented through four idea rating sheets, dealt with the issue of the resources Finland could draw upon to respond to complexity. Although each sheet used slightly different terminology to reflect a range of views, those views were fairly evenly divided.Footnote27 The central debate in the comments concerned whether a small country could survive in the complex world alone or whether it should form alliances with others. Some commented that no one could survive without alliances in a complex world, that is, alliances were seen to unlock enhanced resources to deal with complex problems. However, others viewed complexity as an advantage for a small country, in that, a small country can be more adaptive and thus more capable of responding to changes in an operating environment.
Discussion
With regard to the first research question of the study, the perceptions of the Finnish military officers who attended the security café were quite similar to the perspectives presented in the theory section of this article. The majority of the café participants considered the concepts of complexity useful, indicating that complexity thinking does not seem to be only top-level theorizing conducted by generals or academics lacking adequate connections to real-world contexts. First, the café participants and researchers (e.g., Ryan Citation2009; Say and Pronk Citation2012) concur that the security environment is a complex one, albeit the abovementioned research addresses the narrower field of the complexity of warfare. Both cohorts also saw complexity as a long-standing phenomenon that we are only now beginning to understand. However, Finnish officers seemed to be slightly more critical about the increase of complexity than academics have been (cf. also McChrystal et al. Citation2015; Mercier Citation2018). Despite digitalization and globalization being mentioned as influencing factors, the security-café participants did not unreservedly accept that complexity in absolute terms was increasing. Interestingly, in their comments, some of the café participants proposed that the uncertainty caused by complexity could be reduced or controlled with the advances in analytical tools and especially artificial intelligence. This is – due to the incompressibility of complex systems – in stark contrast to the points made in theory (e.g., Rousseau Citation2003).
The Finnish military officers also pointed out that the discussion about increasing complexity may in fact contribute to making things seem more complex than they actually are. This relates to the role of problem framing, highlighted for example by Kopsch and Fox (Citation2016). As theory and practice show, military personnel should be careful not to step into a complexity trap, however, neither should they succumb to simplifying issues and drawing conclusions too quickly. The results also showed a clear contrast with the law on requisite complexity. While the theory indicates that the complexity of the system should correspond to the complexity of the system’s environment, that is, the relevant complexity profiles should match (see e.g., Bar-Yam Citation2004; Ashby Citation2011; Boisot and McKelvey Citation2011) café participants were highly skeptical that only complex solutions could solve the problems of a complex operating environment. However, as one of the café participants commented, the explanation for this skepticism may be that the word only used in the statement and presented on an idea rating sheet was considered to present too stark a description.
With regard to the second research question of the study, the issue of balancing at the edge of chaos (see e.g., Mercier Citation2018; Uhl-Bien and Arena Citation2018) emerged from the empirical data in two instances especially. First in relation to how café participants evaluated the suitability of Finnish policies in a complex security environment. There was debate over whether the maintenance of options was to help preserve the ability to respond to multiple situations and to increase adaptability, or whether too many options stifle action and introduce a certain haziness and indecision into the aims and objectives. The second was related to the need to reduce hierarchy levels and enable self-organization. Although participants strongly supported this as an approach suitable for a complex operating environment, they did not consider this an either-or issue, but saw value in both hierarchies and self-organization. This view is in line with March’s (Citation1991) perspective on positive tensions between exploitation and exploration and Mercier’s (Citation2018) on the struggle involved in operating and adapting simultaneously.
Both academic literature (see e.g., Zweibelson et al. Citation2017) and the gathered empirical data highlight that a complex security environment necessitates whole-of-government approaches. Finnish officers particularly emphasized the Finnish Concept for Comprehensive Security, which was seen as Finland’s attempt to meet the challenges presented by complexity. Complexity is then confronted by the actions of multiple actors; a group that the café participants underlined extends beyond civil agencies working closely with armed forces, but also encompasses citizens with strengthened resilience.
Conclusions
The key points arising from the study are that the issue of the complexity of the security environment is neither just appearing as we speak nor is it dissipating – it has been present since humans first formed communities and is likely to grow due to increasing connectivity and interdependence, although there are contrasting views. Responding to the complexity of the operating environment seems to rely on a capability for adaptation. Importantly, complexity is essentially not about an either/or but a both/and mindset. Dichotomies (such as hierarchies vs. self-organization) do not work well in the era of complexity, hence actors must have multiple operational capabilities available simultaneously, that is, their strategies must be ambidextrous (see March 1991). It is also vital not to fall into a complexity trap but equally important not to oversimplify issues or draw hasty conclusions. Therefore, working and leading in a complex operating environment has been referred to as both tuning (Hanén Citation2017) and maneuvering (Puustinen Citation2017).
The topic of complexity is unlikely to decline in popularity in the 2020s. Initiatives such as the Global Risks Reports (World Economic Forum Citation2019, Citation2020) and the UN Global Assessment Report on Disaster Risk Reduction (GAR Citation2019) highlight that an increasing amount of systemic risk and geopolitical turbulence will become the new normal. Consequently, complexity research seems likely to thrive in the future. It is however important that complexity research retains its critical acuity and does not become an excessive trend. Otherwise there is a risk of research related to complex‐systems paradigms suffering the same fate as the heavily popularized chaos theory and not always being regarded as a credible scientific approach (see Hanén Citation2017). The data analyzed for this article do contain some suggestion that credibility is under threat, in that a café participant warned of the concepts of complexity research being mere terminological gimmicks. We should also bear in mind that even though it is very natural for members of the military to operate in a complex operating environment this does not mean that there is not room for improvement. As stated by Maher (Citation2014, 67), “[western militaries] intuitively grasp the utility of complexity science, however, we struggle cognitively to naturalise its application.”
With regard to the four regimes of the scientific way of warfare described in the theory section of this article (Bousquet Citation2008), the data suggest that none should be disregarded. Although, it can be claimed that we are in an era of chaoplexic, networked warfare, with growing systemic risks and interdependencies, the mechanistic, the thermodynamic, and the cybernetic forms of warfare still prevail. Complexity does not imply the absolute replacement of any previous paradigm, but the holistic understanding of many intertwined phenomena. This goes along with the notion of different schools of complexity thinking itself (see e.g., Richardson et al. Citation2000, Thomas Citation2019). The harder, mathematical, and computational techniques of analyzing the security environment and the softer, metaphorical approaches of understanding complexity are best used in combination, both in research and in practice (see also Zweibelson Citation2016b).
This study narrows the research gap on how members of the military in general perceive complexity as a scientific concept. Doing so involved clarifying the connection between the theory of complexity and the practice of acting in a complex security environment. By analyzing the views of Finnish military officers, we have showed that the complex‐systems paradigm is not alien to the military. In reality, many existing operating models – such as mission command and whole-of-government approaches – are very similar in terms of the kind of activity often expected in a complex operating environment.
The data indicate that future research on complexity, in the context of the security environment, could beneficially focus more closely on examining the different whole-of-government approaches. The positive views expressed by the military officers in this article on the Finnish Comprehensive Security model require further detailed empirical research before it would be feasible to draw any stronger conclusions on the applicability of the model to a complex operating environment. It could also be worthwhile, in the spirit of the Comprehensive Security approach, to look at how complexity is perceived among other security authorities, such as the fire and rescue services and the police.
Disclosure statement
No potential conflict of interest was reported by the authors.
Additional information
Notes on contributors
Harri Raisio
Harri Raisio, PhD, is a Senior Researcher in Social and Health Management at the University of Vaasa and Adjunct Professor at the University of Eastern Finland. His research has focused on the topics of wicked problems, complexity sciences, and public deliberation. He has published in journals such as Landscape and Urban Planning, Policy Sciences, Administration & Society, Journal of Health Organization and Management, Public Administration Quarterly, and Scandinavian Journal of Public Administration.
Alisa Puustinen
Alisa Puustinen is a social psychologist, having a PhD. in public administration. She works as a senior researcher at the Emergency Services Academy Finland. Puustinen also holds the title of docent (adjunct professor) in complexity and management at the National Defense University. Her research focuses on security studies, complexity, management, social networks, civil society, operating environment and foresight.
Jaakko Jäntti
Jaakko Jäntti, commander GS, is a senior lecturer of military strategy at the National Defence University of Finnish Defence Forces.
Notes
1. Other public authorities working in the domains of safety and security can also attend courses.
2. Idea/statement: The current security environment is complex. n = 61. Frequency distributions: strongly agree 59%, partially agree 33%, neutral 3 %, partially disagree 5 %.
3. Idea/statement: Complexity just seems to increase in the international and national security environments with increased data and information, and accelerated data transfer. The same complexity has always prevailed. Complexity is subjectively experienced, relative, and non-measurable. n = 38. Frequency distributions: strongly agree 47%, partially agree 32%, neutral 3 %, partially disagree 18%.
4. Idea/statement: High-speed communication and social media have increased complexity in the security environment. Social media is or can be a fierce catalyst. High-speed communication also enables the intentional shaping of the global security environment. n = 42. Frequency distributions: strongly agree 67%, partially agree 24%, partially disagree 7%, strongly disagree 2 %.
5. Idea/statement: Digital data transfer has increased the complexity of the global security environment, as real-time action, the amount of information, a lack of delay, and actors and variables increase the challenges of decision making. Further explanations: difficulty in analysis, flood of information, and human data processing capability. n = 37. Frequency distributions: strongly agree 54%, partially agree 30%, neutral 3 %, partially disagree 8 %, strongly disagree 5 %.
6. Idea/statement: Finland is no longer a land of milk and honey. Many global threats or their repercussions also affect Finland’s security environment. n = 45. Frequency distributions: strongly agree 64%, partially agree 24%, partially disagree 11%.
7. Idea/statement. The Finnish security environment is no longer distinguishable from the global security environment, but the same threats and challenges apply to all. n = 59. Frequency distributions: strongly agree 14%, partially agree 27%, partially disagree 59%.
8. Idea/statement: Finland’s security environment is the same as the global security environment – the scale is only smaller. n = 60. Frequency distributions: strongly agree 8 %, partially agree 28%, partially disagree 42%, strongly disagree 22%.
9. Idea/statement: Diversification of threats has increased disruptions in the global security environment. n = 52. Frequency distributions: strongly agree 17%, partially agree 40%, neutral 10%, partially disagree 27%, strongly disagree 4%, do not know 2%.
10. Idea/statement: We often step into a so-called complexity trap, that is, we make the problems we face seem more complex than they are. n = 58. Frequency distributions: strongly agree 28%, partially agree 40%, neutral 7%, partially disagree 24%.
11. Idea/statement: Only complex solutions can solve the problems of a complex operating environment. n = 59. Frequency distributions: strongly agree 3%, partially agree 8%, partially disagree 42%, strongly disagree 46%.
12. Idea/statement: The concepts of complexity help to increase understanding of the security environment. n = 55. Frequency distributions: strongly agree 42%, partially agree 29%, neutral 7%, partially disagree 22%.
13. Idea/statement: Finland’s foreign, security and defense policies are correct in Finland’s complex security environment. n = 57. Frequency distributions: strongly agree 5 %, partially agree 37%, neutral 7%, partially disagree 39%, strongly disagree 7%, do not know 5 %.
14. Idea/statement: Finland’s security policy aims to respond to a complex security environment by maintaining alternatives (maintaining adaptive space). n = 45. Frequency distributions: partially agree 71%, neutral 16%, partially disagree 13%.
15. Idea/statement: Instead of security and defense policy reports, ONLY a comprehensive security report should be produced. n = 41. Frequency distributions: strongly agree 10%, partially agree 17%, neutral 7%, partially disagree 12%, strongly disagree 54%.
16. Idea/statement: The Finnish concept for comprehensive security is Finland’s attempt to meet the challenges of the complex security environment. n = 48. Frequency distributions: strongly agree 48%, partially agree 42%, neutral 4%, partially disagree 4%, strongly disagree 2%.
17. Idea/statement: Cooperation between public authorities will increase the resilience of society and its ability to respond to a complex operating environment. n = 46. Frequency distributions: strongly agree 65%, partially agree 35%.
18. Idea/statement: The comprehensive security model must be adaptive to respond to the complexity of the security environment. n = 60. Frequency distributions: strongly agree 93%, partially agree 3%, neutral 2%, partially disagree 2%.
19. Idea/statement: The Finnish concept for comprehensive security is adaptive, i.e. adaptable to the challenges of a complex operating environment. n = 50. Frequency distributions: strongly agree 16%, partially agree 62%, neutral 8%, partially disagree 14%.
20. Idea/statement: Strengthening resilience by committing each citizen to the tasks of comprehensive security is a way to respond to a more complex modern world. n = 42. Frequency distributions: strongly agree 19%, partially agree 40%, neutral 5 %, partially disagree 29%, strongly disagree 7%.
21. Idea/statement: Complexity should be taken into account in national preparedness through education, upbringing, and information sharing. These important steps will increase citizens’ awareness, broaden the circle of people in the information community, and strengthen media literacy. n = 39. Frequency distributions: strongly agree 33%, partially agree 28%, neutral 15%, partially disagree 23%.
22. Idea/statement: More transparent communication on the security situation improves society’s ability to understand the complex security policy environment. n = 43. Frequency distributions: strongly agree 21%, partially agree 63%, neutral 7%, partially disagree 9%.
23. Idea/statement: Bureaucratic and hierarchical command structures make it difficult to adapt in a complex operating environment. n = 59. Frequency distributions: strongly agree 39%, partially agree 36%, neutral 8%, partially disagree 15%, strongly disagree 2%.
24. Idea/statement: Complexity should be taken into account in the implementation of comprehensive security by delegating power to authorities at the lower levels of hierarchy, increasing the freedom of action of executive authorities and establishing a cooperative relationship at ever lower levels of authority. n = 46. Frequency distributions: strongly agree 50%, partially agree 35%, neutral 11%, partially disagree 2%, do not know 2%.
25. Idea/statement: Decision-making power should be moved as low down the hierarchy as possible, especially in government, to ensure that the response is timely in a complex operating environment. Provided that everyone acts according to mission command to achieve a common objective (comprehensive security). Justification: Currently, for example, decision-making, preparedness management and responsibility is distributed to many upper levels, cyber as a model example. n = 44. Frequency distributions: strongly agree 32%, partially agree 39%, neutral 9%, partially disagree 20%.
26. Idea/statement: A mission command is a way to handle complexity. n = 47. Frequency distributions: strongly agree 36%, partially agree 45%, neutral 4%, partially disagree 13%, strongly disagree 2%.
27. Idea/statement: National resources may not be adequate to respond to the complexity. n = 48. Frequency distributions: strongly agree 10%, partially agree 38%, partially disagree 38%, strongly disagree 15%.
References
- Ashby, W. R., 2011. Variety, Constraint, And The Law Of Requisite Variety. Emergence: Complexity and Organization, 13 (1–2), 200–207. (originally published in 1968).
- Australian Army, 2012. Adaptive Campaigning – Army’s Future Land Operating Concept. Re-release. Available from: https://researchcentre.army.gov.au/sites/default/files/acfloc_2012_main.pdf [Accessed 15 Jan 2020
- Bar-Yam, Y., 2004. Multiscale Variety in Complex Systems. Complexity, 9 (4), 37–45. doi:10.1002/cplx.20014
- Bar-Yam, Y., 2015. Global Civilization and Counterterrorism. CTC Sentinel, 8 (7), 17–22.
- Blouin, S., 2013. Is Your World Complex? An Overview of Complexity Science and Its Potential for Military Applications. Canadian Military Journal, 13 (2), 26–36.
- Boisot, M., and B. McKelvey, 2011. Complexity and Organization—Environment Relations: Revisiting Ashby’s Law of Requisite Variety. In Allen, P., S. McGuire, and B. McKelvey, edited by. The SAGE Handbook of Complexity and Management. London: Sage, 279–298.
- Bousquet, A., 2008. Chaoplexic Warfare or the Future of Military Organization. International Affairs, 84 (5), 915–929. doi:10.1111/j.1468-2346.2008.00746.x
- Bousquet, A., 2012. Complexity Theory and the War on Terror: Understanding the Self-organising Dynamics of Leaderless Jihad. Journal of International Relations and Development, 15 (3), 345–369. doi:10.1057/jird.2011.24
- Chambers, S., 2003. Deliberative Democratic Theory. Annual Review of Political Science, 6 (1), 307–326. doi:10.1146/annurev.polisci.6.121901.085538
- Churchman, C. W., 1967. Wicked Problems. Management Science, 14 (4), 141–142.
- Cilliers, P., 2011. Complexity, Poststructuralism and Organization. In Allen, P., S. McGuire, and B. McKelvey, edited by. The SAGE Handbook of Complexity and Management. London: Sage, 142–154.
- Dent, E. B., and C. G. Holt, 2001. CAS in War, Bureaucratic Machine in Peace: The US Air Force Example. Emergence, 3 (3), 90–107. doi:10.1207/S15327000EM0303_6
- Diceman, J., 2014. Idea Rating Sheets: Facilitator’s Handbook. Available from: http://idearatingsheets.org/wp-content/uploads/2017/09/idea_rating_sheets_handbook_2-5f.pdf [Accessed 9 Dec 2019]
- The Finnish Government, 2017. The Security Strategy for Society. Government Resolution/2.11.2017. Helsinki: Security Committee.
- GAR, 2019. Global Assessment Report on Disaster Risk Reduction. Geneva: UN Office for Disaster Risk Reduction.
- Glouberman, S., and B. Zimmerman, 2002. Complicated and Complex Systems: What Would Successful Reform of Medicare Look Like? Discussion Paper no. 8. Commission on the Future of Health Care in Canada. Available from: https://www.alnap.org/system/files/content/resource/files/main/complicatedandcomplexsystems-zimmermanreport-medicare-reform.pdf [Accessed 29 Jan 2020]
- Griffith, M. K., 2018. Comprehensive Cyber Security Approach: Bolstering Cybersecurity Capacity through Industrial Policy. BASC working paper series, working paper 2018-07. Berkeley APEC Study Center. University of California, Berkeley. Available from: https://basc.berkeley.edu/wp-content/uploads/2018/09/BWP18-07.pdf [Accessed 29 Jan 2020]
- Grönlund, K., A. Bächtiger, and M. Setälä, eds., 2014. Deliberative Mini-Publics: Involving Citizens in the Democratic Process. Colchester: ECPR Press.
- Hanén, T., 2017. Yllätysten edessä: kompleksisuusteoreettinen tulkinta yllättävien ja dynaamisten tilanteiden johtamisesta [Faced with the Unexpected – Leadership in Unexpected and Dynamic Situations: An Interpretation Based on Complexity Theory]. Helsinki: The National Defence University.
- Juntunen, T., 2017. Helsinki Syndrome: The Parachronistic Renaissance of Finlandization in International Politics. New Perspectives, 25 (1), 55–83. doi:10.1177/2336825X1702500103
- Kopsch, T., and A. Fox, 2016. Embracing Complexity: Adjusting Processes to Meet the Challenges of the Contemporary Operating Environment. Army Press Online Journal, Aug 22. Available from: https://www.armyupress.army.mil/Journals/Military-Review/Online-Exclusive/2016-Online-Exclusive-Articles/Embracing-Complexity-Adjusting-Processes/ [Accessed 2 Feb 2020].
- Kosonen, J., A. Puustinen, and T. Tallberg, 2019. Saying No to Military Service—obligation, Killing and Inequality as Experienced Problems in Conscription Based Military in Finland. Journal of Military Studies, 8, 46–57. doi:10.2478/jms-2019-0005
- Lineweaver, C. H., P. Davies, and M. Ruse, 2010. What Is Complexity? Is It Increasing? In Lineweaver, C. H., P. Davies, and M. Ruse, edited by. Complexity and the Arrow of Time. Cambridge, UK: Cambridge University Press, 3–16.
- Lundqvist, S., and J. J. Widen, 2016. Swedish–Finnish Naval Cooperation in the Baltic Sea: Motives, Prospects and Challenges. Defence Studies, 16 (4), 346–373. doi:10.1080/14702436.2016.1220805
- Maher, A., 2014. The Application of Complex Adaptive Systems Concepts to Contemporary Special Operations. Australian Defence Force Journal, 193, 66–76.
- March, J. G., 1991. Exploration and Exploitation in Organizational Learning. Organization Science, 2 (1), 71–87. doi:10.1287/orsc.2.1.71
- Marion, R., and M. Uhl-Bien, 2003. Complexity Theory and Al Qaeda: Examining Complex Leadership. Emergence, 5 (1), 54–76. doi:10.1207/S15327000EM0501_06
- Mattis, J., 2017. Remarks by Secretary Mattis at the Association of the U.S. Army Exposition on Building Readiness in Washington, D.C. Available from: https://www.defense.gov/Newsroom/Transcripts/Transcript/Article/1337675/remarks-by-secretary-mattis-at-the-association-of-the-us-army-exposition-on-bui/ [Accessed 15 Jan 2020]
- McChrystal, S., T. Collins, D. Silverman, and C. Fussell, 2015. Team of Teams: New Rules of Engagement for a Complex World. New York: Penguin Publishing Group.
- Mercier, D., 2018. NATO’s Adaptation in an Age of Complexity. PRISM, 7 (4), 2–11.
- Mitleton-Kelly, E., 2003. Ten Principles of Complexity & Enabling Infrastructures. In Mitleton-Kelly, E., edited by. Complex Systems & Evolutionary Perspectives of Organisations: The Application of Complexity Theory to Organisations. Oxford: Elsevier Science Ltd., 23–50.
- Møller, J. E., 2019. Trilateral Defence Cooperation in the North: An Assessment of Interoperability between Norway, Sweden and Finland. Defence Studies, 19 (3), 235–256. doi:10.1080/14702436.2019.1634473
- Nabatchi, T., 2010. Addressing the Citizenship and Democratic Deficits: The Potential of Deliberative Democracy for Public Administration. The American Review of Public Administration, 40 (4), 376–399. doi:10.1177/0275074009356467
- Norman, J., and Y. Bar-Yam, 2018. Special Operations Forces: A Global Immune System? In Morales, A., C. Gershenson, D. Braha, A. Minai, and Y. Bar-Yam, edited by. Unifying Themes in Complex Systems IX. ICCS 2018. Cham: Springer, 486–498.
- Paparone, C. R., R. A. Anderson, and R. R. McDaniel Jr, 2008. Where Military Professionalism Meets Complexity Science. Armed Forces & Society, 34 (3), 433–449. doi:10.1177/0095327X07310337
- Puustinen, A., 2017. Voiko Verkostoa Johtaa? [Can Networks Be Managed?]. Dissertations in Social Sciences and Business Studies, 149. Kuopio: University of Eastern Finland.
- Puustinen, A., H. Raisio, and V. Valtonen, 2020. Security Cafés: A Deliberative Democratic Method to Engage Citizens in Meaningful Two-way Conversations with Security Authorities and to Gather Data. In Lehtimäki, H., P. Uusikylä, and A. Smedlund, edited by. Society as an Interaction Space: A Systemic Approach. Heidelberg: Springer, 311–330.
- Raisio, H., and N. Lundström, 2015. Real Leaders Embracing the Paradigm of Complexity. Emergence: Complexity & Organization, 17 (3), 1–5.
- Richardson, K. A., G. Mathieson, and P. Cilliers, 2000. The Theory and Practice of Complexity Science: Epistemological Considerations for Military Operational Analysis. SysteMexico, 1 (1), 25–68.
- Rousseau, C., 2003. Complexity and the Limits of Modern Battlespace Visualization. Canadian Military Journal, 4 (2), 35–44.
- Ryan, A., 2009. The Foundation for an Adaptive Approach: Insights from the Science of Complex Systems. Australian Army Journal, 6 (3), 69–90.
- Ryan, M., and G. Smith, 2014. Defining Mini-publics. In Grönlund, K., A. Bächtiger, and M. Setälä, edited by. Deliberative Mini-Publics. Colchester: ECPR Press, 9–26.
- Say, M., and B. Pronk, 2012. Individual Decision-Making in Complex Environments. Australian Army Journal, 9 (3), 119–140.
- Storr, J., 2003. A Command Philosophy for the Information Age: The Continuing Relevance of Mission Command. Defence Studies, 3 (3), 119–129. doi:10.1080/14702430308405081
- Thomas, M. A., 2019. Spaghetti: Systems Thinking and the US Army. Defence Studies, 19 (2), 149–169. doi:10.1080/14702436.2019.1596741
- Tourish, D., 2018. Is Complexity Leadership Theory Complex Enough? A Critical Appraisal, Some Modifications and Suggestions for Further Research. Organization Studies, 40 (2), 219–238. doi:10.1177/0170840618789207
- U.S. Army. 2015. The Army Vision: Strategic Advantage in a Complex World. Available from: https://usacac.army.mil/publication/the_army_vision [Accessed 15 Jan 2020]
- Uhl-Bien, M., and M. Arena, 2018. Leadership for Organizational Adaptability: A Theoretical Synthesis and Integrative Framework. The Leadership Quarterly, 29 (1), 89–104. doi:10.1016/j.leaqua.2017.12.009
- Wither, J. K., 2020. Back to the Future? Nordic Total Defence Concepts. Defence Studies, 20 (1), 61–81. doi:10.1080/14702436.2020.1718498
- World Economic Forum, 2019. The Global Risks Report 2019. Geneva: World Economic Forum.
- World Economic Forum, 2020. The Global Risks Report 2020. Geneva: World Economic Forum.
- Yankelovich, D., 1991. Coming to Public Judgment: Making Democracy Work in a Complex World. Syracuse: Syracuse University Press.
- Zhang, L., Q. Wang, and L. Hanks, 2016. A Comparison of Plurality Voting Sheets and Idea Rating Sheets in Judgement-making: A Participatory Architectural Design in the Nottingham Natural History Museum, Wollaton Hall. Museum Management and Curatorship, 31 (2), 103–140. doi:10.1080/09647775.2015.1118355
- Zweibelson, B., 2016a. Linear and Non-Linear Thinking: Beyond Reverse-Engineering. Canadian Military Journal, 16 (2), 27–35.
- Zweibelson, B., 2016b. Rose-tinted Lenses: How American Functionalist Strategy Inhibits Our Appreciation of Complex Conflicts. Defence Studies, 16 (1), 68–88. doi:10.1080/14702436.2016.1147924
- Zweibelson, B., L. Hedström, M. Lindström, and U. Pettersson, 2017. The Emergent Art of Military Design Swedish Armed Forces and the Contemporary Security Environment. Krigsvetenskapsakademiens Handlingar Och Tidskrift, 3, 83–97.
