Abstract
Employers and employees continue to be highly vulnerable to negative consequences that may result from e-mail privacy intrusions. Given their potentially differing perceptions, there is a need to understand the privacy issues associated with e-mail use. This article first reviews the U.S. legal system to reveal the lack of e-mail privacy protection. A framework is presented to identify the potential consequences under varying circumstances in the workplace, exemplified by classic e-mail privacy cases. The conclusion drawn is that employee e-mail within U.S. organizations is never private, contrary to employee behavior. This contrast indicates a need for change in e-mail user behavior and management policies. In response, suggestions for developing user practices and proper management of e-mail are provided.
INTRODUCTION
On average, employees send or receive about 50 e-mail messages per day, which is an equivalent of more than 1,200,000 messages a year for an organization of 100 employees (Rothstein, Hedges, and Wiggins 2007). The privacy issues associated with employee e-mail within U.S. organizations have not been well defined, presenting a challenging environment for both employers and employees. The line between personal and professional use is not clearly drawn. Employee behavior demonstrates a lack of understanding of where to draw the line. A dedicated loyal employee who works long hours may provide friends and family with a work e-mail address to increase the flexibility of managing his schedule. If the employee then uses his own laptop during his lunch hour to quickly e-mail several friends that he will be late for a dinner engagement because a meeting was rescheduled, is the communication a personal or business use of the company's e-mail system? Does this distinction matter, as it does for a telephone conversation, in determining whether the employer can legally monitor e-mail messages?
Clearly, employers bear the responsibility for managing organizational resources appropriately. In response, increasing numbers of organizations are monitoring e-mail. A 2007 survey of employer monitoring within U.S. companies revealed that 43 percent monitor employee outgoing and incoming e-mail (American Management Association Citation2007). Such a widespread practice has an impact on employee relations. Employees are challenging such monitoring, based on common law, statutes, and constitutional legal theories, in an attempt to maintain their privacy (Hornung Citation2005). Users and organizations who are naive about societal pressure for ethical conduct and the legal parameters concerning e-mail privacy are highly vulnerable to negative consequences that may result from intrusions.
The purpose of this article is investigative, to formulate a framework that identifies the major factors confronting employers and employees in their e-mail communications and the legal consequences in terms of the employee's expectation of privacy. The U.S. legal system is first reviewed to reveal the lack of e-mail privacy protection currently provided. This review focuses on the fundamental issue of whether the employee's expectation of privacy in e-mail communications is legally protected. Based on this review, a framework is presented to identify the potential consequences under varying circumstances in the workplace. Example e-mail privacy cases are discussed, within the context of the framework, to illustrate issues associated with e-mail privacy intrusions. The conclusion drawn is that employee e-mail within U.S. organizations is never private, indicating a need for change in e-mail user behavior, management policies, or the U.S. legal system.
EMPLOYEE E-MAIL PRIVACY PROTECTION IN THE U.S. LEGAL SYSTEM
An extensive review of e-mail privacy protection concluded that none of the elements currently within the U.S. legal system seems to offer significant protection for the privacy of employees in their e-mail communications (Sipior and Ward 1995). E-mail monitoring is not specifically addressed in any of the current components of the U.S. legal system. Consequently, issues of e-mail privacy must be assessed through protections established for employee privacy in general. An analysis of these protections as applied to e-mail is reviewed below and summarized in Table to provide the reader with an understanding of the legal elements, including federal and state constitutional law, state common law, federal and state statutes, and judicial decisions, under which e-mail privacy cases may be filed.
TABLE 1 Employee Privacy Protection Within the United States for E-mail Communications
U.S. Constitutional Privacy Protection
The U.S. Constitution, in part, defines the relationship between the U.S. government and its citizens. Regarding privacy, the Fourth Amendment provides that “The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated.…” Although the words “the people” would seem to include all employees, it is usually only public sector employees who have privacy protection (Griffin Citation1991). Constitutional protection can be extended to private sector employees only in instances where they can successfully demonstrate sufficient governmental involvement, referred to as “state action.”
Public sector employees' privacy protection under the Fourth Amendment is not unlimited. In a precedent-setting employee privacy case, O'Connor v. Ortega (1987), the U.S. Supreme Court ruled in favor of the employer, based on (1) whether or not the employee, Ortega, had a reasonable expectation of privacy, and (2) whether or not the employer's search of his office was unreasonable. Since Ortega had a private office, he did have a reasonable expectation of privacy. However, the search of his office was found to be reasonable since it was related to the operations of the state-run hospital. The important conclusion is that the government's need to ensure efficient operation of the workplace outweighs an employee's expectation of privacy, even if the privacy expectation is reasonable. For e-mail communications, the extent of constitutional protection is unclear. E-mail is not like a locked desk or file cabinet. The employer not only has access to all messages on the system, but holds the responsibility for questionable message content. It could, therefore, be argued that the public sector employee's legitimate expectations of privacy in e-mail communications are lessened.
State Constitutional Privacy Protection
Some state constitutions specifically grant individuals an explicit right to privacy (Baumhart Citation1992; Griffin Citation1991). Again, this right usually applies to protection for public sector, not private sector, employees. However, in California, for example, the state constitution was amended to include privacy protections, and California appellate courts have specifically held that the right of privacy applies to both public and private sector interests. Further, the case of Soroka v. Dayton Hudson Corporation (1992) reaffirmed this and held that an employer may not invade the privacy of its employees without a compelling interest. In Soroka, the invasive action by the employer was the administration of a psychological screening test to job applicants. Similarly, some compulsory employee drug testing was held in Luck v. Southern Pacific Transportation Company (Citation1990) to violate this state's constitutional privacy right. In what way this applies to e-mail, if at all, remains to be decided.
State Common Law Privacy Protection
Common law is a continuously changing system of law, developed and updated by court decisions based on precedent and societal values, rather than on written laws (i.e., statutory law). The common law privacy claim most likely to be asserted in response to the monitoring of employee e-mail is the tort of invasion of privacy, more specifically, intrusion upon seclusion (Griffin Citation1991). This theory considers privacy as based broadly on concepts of individual human dignity and respect rather than a separate independent value (Harvard Law Review Citation1991).
To apply the tort of inclusion upon seclusion to e-mail privacy, an employee whose e-mail has been unknowingly monitored must demonstrate (1) an intrusion, (2) that the intrusion was into a private matter, and (3) that the intrusion would be highly offensive to a reasonable person (Restatement (Second) of Torts 1977). The undisclosed monitoring of e-mail would seem to be an intrusion, but are messages on an employer's e-mail system private, since the system is for the employers' business purposes? The answer is unclear, but courts have extended privacy protection to the analogous areas of wiretapping telephone calls and intercepting written communications (Griffin Citation1991). Regarding the third aspect, whether e-mail monitoring would be highly offensive to a reasonable person, the same rationale would seem to apply. This monitoring is done on equipment owned by the employer, used ostensibly for the employer's purposes, by a compensated employee. It is arguable that this environment would not foster a reasonable expectation of privacy. To date, there is no definitive answer to whether this tort applies to the monitoring of e-mail.
Federal Statutory Privacy Protection
Constitutional law and common law protections of e-mail privacy are, at best, vague. As part of the heated ethical and political debate over privacy issues, specific statutory protections have been enacted and/or proposed by the U.S. Congress. The most important among these for e-mail privacy is the Electronic Communications Privacy Act (ECPA) of 1986, since internal company e-mail systems were not covered by any federal statute prior to this act (Office of Technology Assessment 1985). The purpose of the ECPA is to extend existing privacy protections against wiretapping to new forms of electronic communications, such as electronic mail, cellular telephones, and data transmission, from improper interception. Broadly, the ECPA prohibits the interception and subsequent disclosure or use of wire, oral, or electronic communication. The statute's broad definition of electronic communication clearly includes e-mail within its scope.
Two exceptions in the ECPA make it unclear as to whether e-mail monitoring by private sector employers is covered. The first, referred to as the business use or business extension, is a common defense in cases filed under the ECPA (Griffin Citation1991). To be an effective defense against an employee's claim of e-mail privacy invasion, the employer must demonstrate, as established by Watkins v. L. M. Berry & Company (1983), that a business use was the reason for the interception and that monitoring was conducted within the ordinary course of business. In Watkins, the employer notified the employee that telephone sales calls were being monitored. This notification was interpreted to mean that the specific interception was in the ordinary course of business. The business purpose ended when it became apparent that the telephone communication was personal. Although this exception has been applied to telephone communication, it would seem to apply equally to e-mail. If an employer wants to ensure that its e-mail system is used solely for work-related purposes, then routine monitoring of e-mail messages might fall under this exception. Interesting is the question of whether monitoring should cease when e-mail content is determined to be personal.
The second exception in the ECPA, called the prior consent exception, may actually permit telephone and e-mail monitoring. Under this exception, employers may be able to protect themselves against the risk of liability merely by notifying one of the parties that his e-mail may be examined. Such consent may be expressly granted or implied, but is limited to the scope of the consent. In Watkins, the consent was only to the monitoring of business calls. The court refused to extend this consent to all telephone calls. A review of relevant legal research seems to conclude that the ECPA does not provide significant privacy protection to employees' e-mail communications (Sipior and Ward 1995).
State Statutory Privacy Protection
Privacy protections of electronic communications vary from state to state, but are primarily regulated at the federal level by the ECPA. Most states have addressed these issues through either wiretapping legislation or electronic monitoring legislation or both (Griffin Citation1991). Generally, these state efforts have not been effective in protecting an employee's e-mail privacy. In California, an attempt was made to find employee e-mail privacy protection within the state's criminal laws in Shoars v. Epson America, Inc. (1990). The California Penal Code prohibits wiretapping without the consent of all parties involved. A California Superior Court judge dismissed the lawsuit since this code does not specifically refer to e-mail.
A FRAMEWORK FOR EMPLOYEE E-MAIL PRIVACY WITHIN THE UNITED STATES
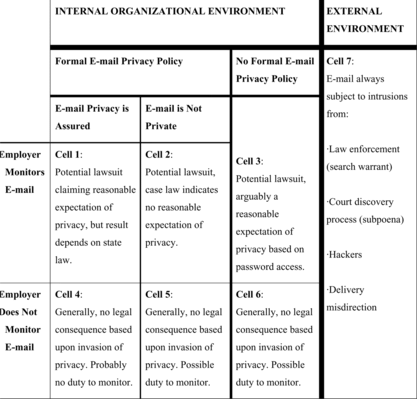
Depending on the circumstances within the workplace, legal actions based on e-mail privacy intrusions may be filed by employees under various legal theories. A framework is presented based on observations from actual cases (see Figure ), which identifies the major factors confronting employers and employees in e-mail communications and the legal consequences. Although each case is unique, the fundamental issue is whether the employee has a legitimate expectation of privacy. Factors present in the work environment may heighten or diminish this expectation for U.S. employees who spend an estimated 25 percent of the workday attending to e-mail (Herbert Citation2008). These cases, coupled with widespread use, exemplify the persistence of the privacy issue and the potential serious consequences, underscoring the need for change. Our framework serves to focus attention on considerations important to determine what change in e-mail user behavior, management policy, or the U.S. legal system is appropriate.
As shown in Figure , intrusions may occur inside or outside of an organization. Within an organization, a formal e-mail policy may or may not have been established. Further, this policy may either provide employees with assurances that e-mail will remain private, or alternatively, inform employees that the company reserves the right to monitor communications. Intrusions from various sources external to an organization are a continuous threat, from both legal agents and illegal perpetrators. To illustrate the consequences for each of the cells depicted in Figure , the following sections discuss classic example cases of e-mail privacy, which are summarized in Table .
TABLE 2 Example Classic Cases of Employee E-mail Privacy Classified According to the Framework in Figure
Cell 1: Assurances of Privacy Communicated via a Formal E-mail Policy
If a privacy policy, explicitly assuring e-mail to be private within an organization, were formally established and communicated (Cell 1), employees would rightfully have a heightened expectation that e-mail will remain unseen by organizational members other than the intended recipient(s). The legal consequence for monitoring employee e-mail under these conditions is likely to be a lawsuit against the employer based upon the employee's reasonable expectation of privacy. This expectation seems well-founded; however, the outcome is surprisingly not so clear.
The Pillsbury Company in Pennsylvania repeatedly assured employees that all e-mail was confidential, and further, that it could not be intercepted and used against them. Relying on this policy, Michael A. Smyth, a regional operations manager, responded to e-mail he received at home from his supervisor. Contrary to the assurances, the e-mail correspondence was intercepted and Smyth was terminated for inappropriate and unprofessional statements in his messages. In response, Smyth filed a wrongful discharge suit, Smyth v. The Pillsbury Co. (1996). Applying the Pennsylvania tort of invasion of privacy, more specifically, intrusion upon seclusion, the court found there was no reasonable expectation of privacy since the e-mail correspondence was voluntary, even though privacy had been assured. The company's need to prevent inappropriate or even illegal message content was found to outweigh any expectation of privacy the employee may have had, regardless of assurances to the contrary. It must be noted that Pennsylvania's employment case law is very employer friendly. A different outcome might occur in another state, such as California.
Cell 2: Employer's Right to Monitor E-Mail Communicated via a Formal E-mail Policy
A company may inform employees that it reserves the right to monitor e-mail messages (Cell 2). The employer has the responsibility to appropriately manage this resource, since he can be held liable for its inappropriate use by employees. Indeed, e-mail and other electronic information are considered to be sources of discovery in lawsuits (Ward et al. 2009), as will be exemplified through cases presented in the discussion of intrusions from external sources (Cell 7). Other reasons for monitoring e-mail include tracking employee work performance, safeguarding the security of company resources against theft or espionage, resolving technical problems, and containing costs, among others. Even when an employer explicitly communicates its e-mail monitoring practices, employees may still expect their e-mail messages to remain private. This may be attributable to the perception that e-mail has the same legal protections as those associated with postal mail and telephone use (Herbert Citation2008).
In the case of Nissan Motor Corporation in California, employees Bonita B. Bourke and Rhonda L. Hall were hired to implement and maintain an internal e-mail system between Nissan and its Infiniti dealerships. The two believed messages were confidential since the e-mail accounts were password protected. In the process of training dealers, the e-mail correspondence became friendly. A supervisor, who printed and read the messages, threatened to discharge them. Bourke claims to have been forced to resign; Hall was fired. The ensuing case, Bourke v. Nissan Motor Corporation in U.S.A., alleged invasion of privacy and wrongful termination in violation of California statutes (Traynor 1994). The California intermediate appellate court upheld the judgment in favor of the employer. The employees had no reasonable expectation of privacy because they had signed a user registration form stating that company policy restricted use of the company's e-mail system to company business and that e-mail was periodically monitored.
Cell 3: No Formal E-mail Privacy Policy
In a legal manual written for systems personnel, it was stated that in the absence of a formal e-mail policy, an employer may implicitly assure e-mail is private by not monitoring it. “[I]f an employer knowingly allows private employee electronic mail to grow and flourish on the company system without opposing it, then an implied agreement can be established, under which employees have a right to expect their private transmissions to remain private” (Rose and Wallace 1992, 101–102). Case law has not supported this nascent contention. Nonetheless, employees have acted under the assumption that e-mail is private, even though their employer never formally established that it is. As indicated in Cell 3, this lack of a communicated formal policy may create a reasonable expectation of privacy based on characteristics of e-mail system use that reinforce this expectation, such as password access.
At Epson America, Inc., in California, Alana Shoars, Office Systems Programmer Analyst, was responsible for installing and training for an office e-mail system. In this capacity, she assured employees that e-mail communications were private. However, her supervisor, Robert Hillseth, the manager of the mainframe that routed messages, placed a tap on the gateway to print messages for his perusal. Shoars discovered the tap and sent a message to the Manager of Network Software and E-mail Administrator requesting an e-mail account to which Hillseth would not have access. Hillseth intercepted the message and fired her. Shoars filed a $75 million class action suit, Flanagan v. Epson America, Inc. (1991), on behalf of herself, about 700 Epson employees, and approximately 1,800 outside the organization, but the court rejected the class certification. Shoars also filed a $1 million wrongful discharge suit, Shoars v. Epson America, Inc. (1990), claiming Epson had violated California Code by invading its employees' privacy and wrongfully terminating her. The Los Angeles County Superior Court judge dismissed the lawsuit, ruling California's privacy statutes were not intended to include e-mail. The company's right to intercept messages in the process of managing its systems was recognized. The Shoars case was subsequently appealed (Shoars v. Epson America, Inc. 1991), resulting in an affirmation of the Superior Court's decision.
Cells 4, 5, and 6: Legal Consequences of Not Monitoring E-mail
It would seem that for an employer who never monitors e-mail, regardless of whether a formal policy has been formulated (Cells 4, 5, and 6), the threat of legal liability is non-existent. Obviously, nothing would prompt an employee to claim invasion of privacy. What is not so obvious are the hidden issues that may arise as a result of new situations created by technologies, such as e-mail, for which the legal system has no precedent.
A possible hidden issue is whether an employer has a duty or responsibility to monitor the organization's e-mail. For example, if an employer's e-mail system was used for electronic harassment, stalking, racial discrimination, defamation, copyright infringement, conspiracy, whistle-blower retaliation, or to engage in some other illegal activity, could the employer be liable for failing to monitor messages for improper content? This risk is certainly present. In publicly traded companies, for example, it is the company's responsibility to assure that employees abide by Securities and Exchange Commission rules. In this instance, a company failing in its responsibility to monitor e-mail messages sent to external destinations might be negligent in its duty to protect trade secrets and proprietary information. This breach of duty, or failure to act reasonably, is generally referred to as negligence. There is no reported case law based specifically on the failure of an employer to reasonably monitor e-mail that would provide guidance in determining employer responsibility. It would seem that an employer with a formal policy of e-mail privacy might have no, or little, responsibility to monitor. The possibility of liability arises when there is a formal policy that e-mail is monitored, or when there is no stated policy. If an employer has expressed or implied a right to monitor e-mail, does it then have a responsibility to do so? Without knowledge of improper use of this company resource, the answer is probably no. However, “deep pockets” are often sought when determining who is to be named in a lawsuit. Not surprisingly, the “deep pocket” is often the employer.
To determine whether reserving the right to monitor employee e-mail implies a responsibility on the part of the employer to monitor, the analogous cases of electronic bulletin board defamation may be examined to provide insight. In a clear example of suing the deep pocket, an allegedly defamed party sued not only the individual who posted the alleged defamatory statement, but also the online service provider. It would seem unreasonable to hold the service provider responsible for the actions of a subscriber. With a message volume of more than one every two seconds, how can the provider realistically monitor content? In a 1995 defamation lawsuit, Stratton Oakmont, Inc. v. Prodigy Services Co., this volume defense was not successful. In a pre-trial motion, Prodigy argued that with a volume of 65,000–75,000 messages per day, it was merely a distributor of information, not a publisher as required for defamation. This argument was rejected by the court which indicated that Prodigy's retention of the editorial right to screen and delete offensive messages from the bulletin board made Prodigy a publisher, not just a distributor, and therefore, responsible for the content. It is arguable that by retaining the right to monitor e-mail explicitly or implicitly, as in Cells 5 and 6, respectively, the employer might, by analogy, be legally liable for the content of employee e-mail.
Cell 7: External Threats to E-mail Communications
Organizations are not only confronted with conditions that prevail internally, but must also contend with the complexity of the external environment. The possibility of privacy intrusions from external sources, including law enforcement, court discovery, hackers, and delivery misdirection, is a constant threat (Cell 7). Law enforcement agencies investigating illegal activities may present a search warrant granting them access to search organizational property, including e-mail messages in transit, stored on disk or in paper form, backed-up to tape, or even those that have been deleted and overwritten. Similarly, through court discovery processes, a subpoena may be issued to require organizations to comply with requests to examine e-mail in its various forms. E-mail is increasingly being examined as a source of the “smoking gun” to substantiate claims that, otherwise, have no supporting documentation. E-mail is also subject to illegal access by hackers who gain entrance to company resources. Finally, e-mail messages may be misdirected, either by malfunctioning software, or intentionally or unintentionally by the (re)sender. Many e-mail users send the same e-mail to multiple recipients, who forward it to other recipients (Sedona Principles 2007).
Court Discovery Process: Subpoena
Although some employees report awareness that their e-mail messages are not private, they may not be prepared to publicly discuss them. A classic example is the exchange of comments via e-mail by two White House secretaries, Linda Tripp and Deborah Gorham, about their respective bosses, former White House counsel Bernard Nussbaum and former White House deputy counsel Vincent W. Foster, Jr. During questioning at the Senate Whitewater hearings, Sen. Christopher J. Dodd (D., CT) remarked, “Obviously, neither of you ever imagined, I presume, when you were sending those e-mails, that we would be sitting here talking about it at a congressional hearing” (Cannon Citation1995, A4). Tripp sheepishly responded that while she was aware that White House messages were stored, “they weren't intended to be shared” (Cannon, A4). Even casual correspondence becomes a part of the organization's documented internal communications, subject to subpoena.
Corporations generally have paper retention and destruction policies for company records, which are not necessarily applied to computer records. It is now estimated that over 99 percent of information created and stored is done electronically (Isom Citation2005). Further, estimates indicate that 60 percent of all critical business information is stored within the corporate e-mail system. The inattention to proper management of e-mail retention can prove to be quite costly for companies subjected to court discovery (Ward et al. 2009).
Even in cases where astute employees delete e-mail messages of a questionable nature, the messages may still reside on the system. Perhaps the most infamous example of retrieval of deleted messages occurred during the Iran-Contra investigations (Kallman and Sherizen Citation1992). Deleted IBM Professional Office System (PROFS) e-mail correspondences between Oliver North and John Poindexter, then National Security Advisor, were retrieved from White House back-up tapes. During testimony at the Senate hearings, Oliver North was quoted as saying, “We all sincerely believed that when we sent a PROFS message to another party and punched the button ‘delete' that it was gone forever. Wow, were we wrong!” (National Public Radio 1992).
It is not necessarily only the employee who may be negatively impacted by retrieval of deleted messages. In a sexual harassment case, a female employee's boss contended her firing was due to economic considerations. John H. Jessen, of Electronic Evidence Discovery Inc. based in Washington, expertly recovered an e-mail message that had been deleted by its sender and then overwritten. The company president had written to the head of personnel, her direct manager, “I want you to get that tight-[redacted] out of here. I don't care what you have to do” (Lavalle Citation1994, B1). The corporation agreed to settle her case for $250,000. The cost to the employer can be quite high. Four female employees received a settlement of $2.2 million from Chevron Corporation for a sexual harassment case. While Chevron denied the charges, the women claimed, among other things, to have been subjected to offensive e-mail messages. Retrieved messages supported their claim (Himelstein Citation1995). In a similar discrimination lawsuit, Owens v. Morgan Stanley & Co., Inc. (1997), two African American employees alleged offensive racist jokes were disseminated through e-mail messages. The employees sought $5 million in compensatory damages and $25 million in punitive damages. The case was later settled.
In a $150 million securities fraud case, Siemens Solar Industries v. Atlantic Richfield Co. (1994), Siemens contended that ARCO fraudulently misrepresented the value of their solar energy subsidiary in the sale of the subsidiary to Siemens. Entered into evidence were ten previously deleted but retrieved e-mail messages, sent prior to the acquisition, which Siemens claimed revealed shortcomings of the subsidiary's main product. ARCO claimed the messages were taken out of context and that Siemens was fully informed about the subsidiary. Siemens' federal securities claims were ultimately dismissed as untimely.
In a trade-secrets allegation, Vermont Microsystems Inc. (VMI) alleged that a program developed for Autodesk Inc. was similar to one that a former VMI engineer had created for VMI. The suspicious nature of permanent file deletions from the engineer's hard drive, coupled with his e-mail message content, led a judge to rule in favor of VMI in Vermont Microsystems Inc. v. Autodesk Inc. (1996), awarding them $25.5 million in damages. Similarly, Procter & Gamble was ordered to pay Amway $10,000 for spoliation of evidence for deleting the e-mail of five individuals relevant to a lawsuit (The Procter & Gamble Co., et al., Plaintiffs, v. Randy L. Haugen, et al., Defendants 1998).
Despite media attention to the negative consequences suffered by both employers and employees from intrusions, e-mail messages are still composed and managed imprudently. For example, UOP in Illinois, a joint venture of AlliedSignal Inc. and Union Carbide Corp., filed a $100 million suit against Andersen Consulting alleging breach of contract and fraud (MacDonald Citation1997). In support of UOP's claims are e-mail messages left behind on its hard drives after Andersen was fired. One Andersen consultant wrote to another about a colleague's capabilities, “He should be taking classes at a community college, not charging for this.” Andersen responded, not with claims of invasion of privacy, but by filing a libel suit against UOP, charging defamation for public statements made in relation to the case and violation of the ECPA. Andersen's ECPA violation claim was dismissed in 1998.
Example Cases Occurring Under Other Conditions
Factors in the U.S. legal environment are much more complex than the simplistic depiction in Figure . All cases of e-mail privacy intrusions will not fit neatly into the cells presented in the framework. Reported facts may be incomplete, especially for cases settled out of court. Even legal cases on record may not provide a comprehensive report of the facts. Further, new circumstances may arise. Thus, the framework is not universally applicable.
An example case that does not fit into the framework is that of an employee who wrongly granted himself the right to monitor e-mail. At the Los Angeles Times Moscow bureau, correspondents became suspicious when they discovered, through the system's log, that entry to their accounts via password had occurred at times they themselves had not logged on (Sims 1993). In a sting operation set up by the newspaper, Michael Hiltzik implicated himself as the interceptor of the messages. It was not reported exactly how the co-workers' passwords were obtained. The Los Angeles Times recalled the correspondent for reassignment to an undisclosed position.
Another unusual case entails misusing e-mail to send a message appearing to have been sent by another person (Alper Citation2008). An e-mail was purportedly sent to CEO Larry Ellison from employee Adelyn Lee's supervisor, stating “I have terminated Adelyn per your request.” Using this e-mail as evidence, Lee filed a sexual harassment lawsuit and was awarded a settlement of $100,000. An investigation revealed that Lee gained access to her supervisor's password-protected e-mail account to send the e-mail, so that it would appear the e-mail came from him. Lee was convicted and sentenced to one year in prison for perjury and record falsification. Further, she was forced to return the $100,000 settlement.
As circumstances change, the framework may prove useful in identifying the focus upon which to evaluate the change. For example, as employees come to recognize the internal and external threats to the privacy of e-mail messages, they may smartly seek to avoid adding their messages to corporate memory. Keeping one's e-mail private presents quite a challenge. An employee may attempt to avoid utilizing organizational resources by subscribing to an external e-mail service. The e-mail service is thereby not owned by his employer. However, messages may nonetheless be subject to scrutiny if read, composed, or sent using company resources. An employee may unknowingly be utilizing his employer's disk cache to access and read messages, other employees may read the screen while a message is being read or composed, or the message may be sent by way of the employer's gateway. In utilizing Internet mail, the distinction between the employer's private network and the public Internet is blurred. Do such circumstances validate the focus on an employee's reasonable expectation of privacy?
OBSERVATIONS BASED ON THE FRAMEWORK
A number of observations can be drawn from the various cases upon which the framework is based. First, the fundamental issue in all cases of employee privacy is whether the employee has a reasonable expectation of privacy. Employees use e-mail as if it were private, indicating that they make the assumption that a “right to privacy” exists within the workplace. Second, e-mail user behavior developed under this assumption, as e-mail use evolved into a common communication medium. Finally, an obvious conflict exists between the assumption of a right to privacy coupled with current e-mail user behavior and the lack of e-mail privacy protection afforded by the U.S. legal system. Based on these conclusions, it seems apparent that e-mail is never private, indicating a need for change in e-mail user behavior, management policies, or within the U.S. legal system. What is not so obvious is what change is needed in which one or all of these areas.
An Assumed “Right to Privacy” and Current E-mail User Behavior
Regardless of whether a formal policy assures employee e-mail privacy or not, the actions of the employees indicate an assumption of a “right to privacy” in e-mail use. Currently, the U.S. legal system does not recognize an expectation of privacy for e-mail communications in particular. The interests of the employer in managing this communication resource outweigh the employees' expectation of privacy. The example cases also reveal that the employer may be held financially liable for the content of employees' e-mail. Since it is the employer who bears the responsibility to conduct its affairs in an ethically and legally appropriate manner, should the employer retain the right to monitor e-mail? E-mail communications occur on the employer's premises, with the employer's equipment, on the employer's time, at the employer's expense, to further the employer's objectives. Do employees have a reasonable expectation of privacy? What is reasonable? There are no definitive answers. What is certain, however, is that a “right to privacy” for employee e-mail communications is currently an erroneous assumption.
The seriousness of this assumed right is demonstrated in the increasing number of cases dealing with compromised e-mail privacy, despite media attention to the negative consequences suffered by both employers and employees. The usage and conventions associated with e-mail use must mature in the same way as e-mail itself, now a widely available and commonly used form of business communication, has matured. E-mail is viewed by the legal system as a formal means of record-keeping, documenting business activities and thereby serving as an important source of evidence in civil and criminal cases (Ward et al. 2009).
Change in E-mail User Behavior and Management Practices
Organizations, as owners of this resource, can take proactive action by formulating and adhering to a formal policy addressing appropriate e-mail usage. The development of a formal e-mail policy can promote improved e-mail use, especially if reinforced by communicating that policy, and conducting education, training, and re-training sessions. Most important within the e-mail policy is an explicit statement indicating that e-mail communications are never private. The employee should be made aware that the security of an e-mail system, against access by either internal or external intrusions, cannot be guaranteed. The policy should acknowledge the inherent need and desire for privacy in e-mail communications but clearly inform employees that the employer reserves the right to monitor communications in the course of responsibly conducting business. This is a separate issue from engaging in a routine practice of e-mail monitoring. Rather, an employer, as the owner of the resource, holds the ultimate responsibility and legal liability for appropriate use. The policy should clearly state that employees must avoid improper communications that may lead to corporate liability (Hornung Citation2005). Employees should recognize and respect the employer's responsibility to appropriately manage workplace e-mail. In return for this recognition, the employer should responsibly exercise the monitoring function. If an organization does engage in routine monitoring, the policy should clearly state this with a provision indicating the reasons for monitoring, how and when monitoring will transpire, and how information gained from monitoring will be used. The policy should also include statements that restrict e-mail to business use only and prohibit inappropriate language and conduct. E-mail has the appearance of a casual means of communication, but its use creates business records. The need to use the same care, discretion, and level of restraint, in the composition and distribution of e-mail, as with physical business documents, must be emphasized.
The e-mail usage policy also must provide guidelines for deletion, back-up, and retention of messages based on legally acceptable practices. If a large company has 100,000 employees, the company could be storing up to 1.5 billion e-mails annually (Rothstein et al. 2007). Companies should institute e-mail retention programs that periodically delete electronic documents. Substantive messages should be retained for a reasonable period of time. However, what is substantive and reasonable is open to interpretation as the preservation of data has become a complex issue (Ward et al. 2009). An organization must create its own appropriate set of detailed specifications, including what type of messages are to be saved, for how long, where and in what form, and which messages can be deleted. Employees should be warned that deletions of potentially relevant messages, once a legal case has begun, can raise suspicions, serve as incriminating evidence, or be an illegal act itself. Although easily overlooked, deleted messages can become part of the information requested for legal perusal. Thus, the technological requirement of permanently erasing deleted messages by overwriting the messages multiple times with a “shred” program should be included.
Thorough and well-drafted policies are ineffective if not accompanied by education and training coupled with internal procedures to ensure compliance, especially since e-mail user behavior has already developed under the assumption that e-mail is private. Education and training should emphasize the threat posed by the legal discovery process. Employers should also initiate internal procedures. For example, user interaction could be moderated by presenting a subtle reminder when users sign on, such as a pop-up screen presenting company policy, usage rules, and online etiquette regarding e-mail use. Additionally, employees could be encouraged to attend to message retention management.
CONCLUSION
As demonstrated in the example cases of employee e-mail privacy intrusions, e-mail is never private. Nonetheless, an obvious conflict exists between employee perceptions of e-mail privacy protection and those actually afforded to employers by the U.S. legal system. Given that the existing legal system has not kept pace with technological advances, the responsibility to reduce the risks associated with privacy in e-mail communications currently falls upon employers and employees alike. Both are faced with multiple risks in e-mail use. As the number of users and different systems continue to grow, the risks associated with privacy concerns, access security, and message archival and retention also increase. To minimize the risks, organizations must develop and implement effective e-mail usage and retention policies. Employers and employees must understand and be prepared for the revealing and incriminating nature of this essential business communication tool. E-mail is always subject to the specter of scrutiny.
Notes
Source: Sipior and Ward (1995).
REFERENCES
- Alper , B. 2008 . Managing the electronic workplace . Computer and Internet Lawyer April : 1 – 9 .
- American Management Association . 2007 . 2007 electronic monitoring and surveillance survey. http://www.amanet.org/news/177.aspx (accessed December 2, 2009) .
- Baumhart , J. T. 1992 . The employer's right to read employee e-mail: Protecting property or personal prying? The Labor Lawyer 8 ( 4 ): 923 – 948 .
- Cannon , A. 1995 . Whitewater panel airs e-mail messages . Philadelphia Inquirer , August 2, A4 .
- Flanagan v. Epson. America, Inc . 1991 . Calif. Super. Ct. No. BC 007036, March 12 .
- Griffin , J. J. 1991 . The monitoring of electronic mail in the private sector workplace: An electronic assault on employee privacy rights . Software Law Journal ( IV ): 493 – 527 .
- Harvard Law Review . 1991 . Addressing the new hazards of the high technology workplace . Harvard Law Review ( 104:8 ): 1898 – 1916 .
- Herbert , W. A. 2008 . The electronic workplace: To live outside the law you must be honest . Employee Rights and Employment Policy Journal 12 : 49 .
- Himelstein , L. 1995 . The snitch in the system . Business Week , April 17 , 104 – 105 .
- Hornung , M. X. 2005 . Think before you type: A look at email privacy in the workplace . Fordham Journal of Corporate and Financial Law 11 : 115 .
- Isom , D. K. 2005 . Electronic discovery primer for judges. Fed. Cts. L. Rev. 1.(2005), quoting Peter Lyman and Hal R. Varian, How Much Information 2003? at http://www.sims.berkely.edu/research/projects/how-much-info-2003
- Kallman , E. A. , and S. Sherizen . 1992 . Private matters . Computerworld , November 23 , 85 – 87 .
- Luck v. Southern Pacific Transportation Company . 1990 . 267 Cal. Rptr. 618 (Ct. App. 1990), cert. denied, 111 S. Ct. 344 .
- MacDonald , E. 1997 . E-mail trail could haunt consultant in court . Wall Street Journal , June 19, B1 .
- Lavalle , M. 1994 . Digital information boom worries corporate counsel. The National Law Journal, May 30(16:39): B1 .
- National Public Radio, news broadcast, 1992 .
- O'Connor v. Ortega . 1987 . 480 U.S. 709 .
- Office of Technology Assessment (OTA). 1985. Federal government information technology: Electronic surveillance and civil liberties. Available at http://govinfo.library.unt.edu/ota/allota.htm#85 (accessed December 2, 2009).
- Owens v. Morgan Stanley & Co., Inc . 1997 . U.S.D.C. S.D.N.Y., July 17 .
- The Procter & Gamble Co., et al., Plaintiffs, v. Randy L. Haugen, et al., Defendants . 1998 . No. 1:95 CV 0094 K., United States District Court, D. Utah, Central Division, April 17 .
- Restatement (Second) of Torts § 652B . 1977 .
- Rose , L. , and J. Wallace . 1992 . The sysops legal manual, 101–102 . Winona , MN .
- Rothstein , B. , R. Hedges , and E. Wiggins . 2007 . Managing discovery of electronic information: A pocket guide for judges . Washington , DC : Federal Judicial Center .
- Sedona Principles . 2007 . Best practices, recommendations and principles for addressing electronic document production. , 2nd ed . A project of the Sedona Conference® working group on electronic document retention & production (working group 1), http://www.thesedonaconference.org/content/miscFiles/TSC_PRINCP_2nd_ed_607.pdf (accessed December 2, 2009).
- Shoars v. Epson. America, Inc . 1990 . No. SWC 112749 (Cal. Sup. Ct. filed July 30) .
- Shoars v. Epson. America, Inc . 1991 . No. BC 007036 (Cal. Sup. Ct. filed March 12) .
- Siemens Solar Industries v. Atlantic Richfield Co . 1994 . WL 86368 (S.D.N.Y.) .
- Sims , C. 1993 . Reporter disciplined for reading his co-workers' electronic mail. New York Times, December 6, B9 .
- Sipior , J. C. , and B. T. Ward . 1995 . The ethical and legal quandary of e-mail privacy . Communications of the ACM 38 ( 12 ): 48 – 54 .
- Smyth v. The Pillsbury Co . 1996 . No. Civ. A. 95-5712 United States District Court, January 23 .
- Soroka v. Dayton Hudson Corporation . 1992 . 7 Cal. App. 4th 203, review granted, 4 Cal. Rptr. 2d 180 .
- Stratton Oakmont, Inc. v. Prodigy Services Co. 1995 . WL 323710 (N.Y. Sup) .
- Traynor , M. 1994 . Computer e-mail privacy issues unresolved . The National Law Journal , January 31, S2–S4 .
- Vermont Microsystems Inc. v. Autodesk Inc . 1996 . 88 F.3D 142 .
- Ward , B. T. , C. Purwin , J. C. Sipior , and L. Volonino . 2009 . Recognizing the impact of e-discovery amendments on electronic records management . Information Systems Management 26 ( 4 ): 350 – 356 .
- Watkins v. L. M. Berry & Company . 1983 . 704 F2d 577 (11th Cir.) .