?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
We address the nonlinear inverse source problem of identifying multiple unknown time-dependent point sources occurring in a two-dimensional evolution advection–dispersion–reaction equation. Provided to be available within the monitored domain interfaces for recording the generated state and its flux crossing each suspected zone where a source could occur, we establish a constructive identifiability theorem based on an introduced dispersion-current function that yields uniqueness of the unknown elements defining all occurring sources. Then, the established theorem leads to develop a detection-identification method that goes throughout the monitored domain to detect in each suspected zone whether there exists or not an occurring source. Once a source is detected, the developed method determines lower and upper bounds of the mean value discharged by its unknown time-dependent intensity function. Thereafter, the method localizes the sought position of the detected source as the unique solution of an equation satisfied by the introduced dispersion-current function and identifies its unknown intensity function from solving an associated deconvolution problem. Ultimately, the unknown number of occurring sources is deduced as the sum of all detected-identified active sources. Some numerical experiments on a variant of the surface water BOD pollution model are presented.
1. Introduction
Non-linear inverse source problems are usually known to be somewhat delicate since in general there is no identifiability (uniqueness) of unknown sources under an abstract form using only local boundary or/and internal measurements related to the associated state, see [Citation1] for a counterexample. In the literature, to overcome this difficulty authors generally assume to be available some a priori information on the form of the sought source: for example, time-independent sources are treated by Cannon [Citation2] using spectral theory, then by Engl et al. [Citation3] using the approximated controllability of the heat equation. The results of this last paper are generalized by Yamamoto in [Citation4] to sources of separated time and space variables where the time-dependent part is assumed to be known and null at the initial time, then recently in [Citation5] to sources where the known time-dependent part of the sought source could also depend on the space variables and the involved differential operator is a time fractional parabolic equation. Hettlich and Rundell addressed in [Citation6] the two-dimensional (2D) inverse source problem for the heat equation with as a source the characteristic function associated to a subset of a disk. El Badia and Hamdi treated in [Citation7,Citation8] the case of a time-dependent point source occurring in a one-dimensional (1D) evolution transport equation with constant coefficients. Then, Hamdi and Mahfoudhi extended this study in [Citation9] to the case of equations with spatially varying coefficients and Ben Belgacem et al. [Citation10,Citation11] to the case of a moving time-dependent point source. A detection-identification method for multiple unknown time-dependent point sources in a one-dimensional evolution transport equation was recently developed by Hamdi in [Citation12]. Hamdi and Mahfoudhi treated in [Citation13] the identification of a single time-dependent point source in a two-dimensional evolution advection–dispersion–reaction equation. El Badia et al. studied in [Citation14] the case of multiple time-dependent moving point sources in a two-dimensional evolution advection–diffusion–reaction equation.
The present study is motivated by the results established in the two recent papers.[Citation12,Citation14] Firstly, in [Citation14] authors reported some difficulties encountered by the proposed identification procedure that consists of minimizing the two objective functions least squares and Kohn–Vogelius. In fact, the identifiability result in [Citation14] is based on the unique continuation Theorem that suggests to identify the unknown elements defining whatever finite number of time-dependent point sources using only local boundary measurements taken at any non-empty part of the boundary. In our view, that is an ideal theoretical framework which doesn’t give any visibility on how to proceed in terms of identification and in practice doesn’t take into account the flow properties: for example, the case of an advection dominant flow would imply that using only data reaching back the inflow boundary doesn’t enable to cover the entire activity of downstream occurring sources as well as the case of a flow defined by a velocity field fulfilling the no mass penetrate a solid interface and no-slip conditions along the lateral boundaries which leads to a similar conclusion for using only data reaching these boundaries. Moreover, in terms of identification although in [Citation14] the authors employed measurements taken on the whole boundary of the considered domain, the least squares approach doesn’t enable to identify more than one active source whereas the Kohn–Vogelius approach identifies two sources only under some particular conditions: sources should be well separated and diffusion coefficient should be very small to avoid rapid intermixing. Secondly, the recent results established in [Citation12] prove that in the case of a one-dimensional advection–diffusion–reaction equation, local measurements taken only upstream and/or downstream all occurring sources don’t yield uniqueness of the unknown elements defining more than one time-dependent point source.
The originality of the present study consists in establishing a constructive identifiability theorem that leads to develop a detection-identification method able to identify accurately multiple unknown time-dependent point sources occurring in a two-dimensional evolution advection–dispersion–reaction equation from some local measurements taking into account the flow properties. A motivation for our study is a typical problem associated with environmental monitoring that aims to identify unknown pollution sources occurring in surface water. For example, in a river the involved unknown pollution sources can be identified from measuring the BOD (Biochemical Oxygen Demand) concentration which represents the amount of dissolved oxygen consumed by the micro-organisms during the oxidation process.[Citation15,Citation16] The paper is organized as follows: Section 2 is devoted to stating the problem, assumptions and proving some technical results for later use. In Section 3, based on an introduced dispersion-current function, we establish a constructive identifiability theorem that yields uniqueness of the unknown elements defining the occurring sources. Section 4 is reserved to develop a detection-identification method that goes throughout the monitored domain to detect the presence of all occurring active sources. Once a source is detected, the developed method determines lower and upper bounds of the mean value discharged by its unknown time-dependent intensity function, localizes its sought position and identifies its intensity function. Some numerical experiments on a variant of the surface water BOD pollution model are presented in Section5.
2. Problem statement
Let be a final monitoring time and
be a bounded and connected open subset of
with a sufficiently smooth boundary
where
denotes the inflow boundary,
designates the outflow boundary whereas
regroups the two lateral lower and upper boundaries
. The evolution of the BOD concentration, denoted here by u, is governed by the following equation, see [Citation15,Citation17,Citation18]:
(1)
(1)
where F represents the set of all occurring pollution sources and L is the second-order linear parabolic partial differential operator defined as follows:(2)
(2)
where D represents the hydrodynamic dispersion tensor, V is the flow velocity field and R is a real number that designates the first-order decay reaction coefficient. The velocity field V is defined by where
and
are two Lipschitz functions in an open subset
of
containing
i.e.
that satisfy:
(3)
(3)
The two first conditions in (Equation3(3)
(3) ) imply that the flow is incompressible and irrotational. Hydrodynamic dispersion occurs as a consequence of two processes: molecular diffusion resulting from the random molecular motion and mechanical dispersion which is caused by non-uniform velocities. The summation of these two processes defines as follows the hydrodynamic dispersion tensor [Citation19]:
(4)
(4)
where is a positive real number that represents the molecular diffusion coefficient,
is the
identity matrix and the coefficients
are such that, see [Citation17,Citation20]:
(5)
(5)
where are two positive real numbers that represent the mean transverse and longitudinal dispersion coefficients. Moreover, using (Equation4
(4)
(4) )-(Equation5
(5)
(5) ) the hydrodynamic dispersion tensor D can be rewritten as follows:
(6)
(6)
for all . Hence, (Equation6
(6)
(6) ) implies that D is uniformly elliptic and bounded.
For later use and as in view of (Equation6(6)
(6) ) the matrix D is invertible then, there exists a unique vector field X solution of the linear system
in
. Moreover, we have
(7)
(7)
Furthermore, according to (Equation5(5)
(5) ) we find
(8)
(8)
Thus, using the results (Equation8(8)
(8) ) to substitute the associated terms in the right-hand side of the second equation in (Equation7
(7)
(7) ) gives
. Since from (Equation3
(3)
(3) ) it holds
in
then, X is a gradient field derived from a scalar potential
that solves
(9)
(9)
Hence, the potential that yields
where
is defined by
(10)
(10)
In addition, using the vector we consider the following equation:
(11)
(11)
The second equation in (Equation11(11)
(11) ) is obtained using similar techniques as in (Equation7
(7)
(7) ) and (Equation8
(8)
(8) ). Moreover, as from (Equation3
(3)
(3) ) we have
in
then, the scalar potential
that solves (Equation11
(11)
(11) ) with
is defined by
(12)
(12)
Therefore, from (Equation9(9)
(9) )–(Equation11
(11)
(11) ) and according to (Equation3
(3)
(3) ) it follows that the three following functions:
(13)
(13)
where is a real number, solve the adjoint equation
(14)
(14)
Lemma 2.1:
Provided (Equation3(3)
(3) ) holds true, the dispersion-current function
defined by
(15)
(15)
is injective.
Let ) and
be two elements of
. For the clearness of our proof, we proceed in two steps. Step 1: We prove that we have
(16)
(16)
To this end, using the definition of the function introduced in (Equation10
(10)
(10) ), we obtain
(17)
(17)
Therefore, using Chasles’s relation by introducing the variable on the integral over
in (Equation17
(17)
(17) ), we obtain
(18)
(18)
Moreover, since ,
are two Lipschitz functions in
and
in
which implies
for all
it follows using Fubini’s rule that
(19)
(19)
Thus, from substituting the last term in (Equation18(18)
(18) ) by its value obtained in (Equation19
(19)
(19) ) we find the first equation announced in the system (Equation16
(16)
(16) ). Besides, from (Equation12
(12)
(12) ) we get
(20)
(20)
Then, using Chasles’s relation by introducing on the integral over
in (Equation20
(20)
(20) ) gives
(21)
(21)
In addition, as ,
are two Lipschitz functions in
and
in
which implies
for all
it follows using Fubini’s rule that
(22)
(22)
Hence, from substituting the last term in the right hand-side of (Equation21(21)
(21) ) by its value found in (Equation22
(22)
(22) ), we obtain the second equation in the system (Equation16
(16)
(16) ).
Step 2: Since from (Equation3(3)
(3) ) we have
and
a.e. in
, it follows that the four integrals defining the system (Equation16
(16)
(16) ) are all null either because
or because the two left-hand side terms have the same sign whereas the two right-hand side terms have two opposite signs. That implies
and
which means
.
Besides, to (Equation1(1)
(1) ) and (Equation2
(2)
(2) ) one has to append initial and boundary conditions. We could consider without loss of generality that there is no pollution occurring at the initial monitoring time and thus, use a null initial BOD concentration. As far as the boundary conditions are concerned, an homogeneous Dirichlet condition on the inflow boundary
seems to be reasonable since the convective transport generally dominates the diffusion process. However, other physical considerations suggest using rather a Neumann homogeneous condition on the two remaining parts
and
of the boundary
. Therefore, we employ the following initial and boundary conditions:
(23)
(23)
where is the unit outward vector normal to
. Notice that due to the linearity of the operator L introduced in (Equation2
(2)
(2) ) and according to the superposition principle, the use of a non-zero initial condition and/or inhomogeneous boundary conditions do not affect the results established in this paper.
As far as F is concerned, we are interested in the case of multiple time-dependent point sources occurring in the main problem (Equation1(1)
(1) ), (Equation2
(2)
(2) ) and (Equation23
(23)
(23) ) i.e. F is defined as follows:
(24)
(24)
where ,
denotes the Dirac mass,
are N distinct interior locations in
that represent the positions of the occurring sources and
designate their associated time-dependent source intensity functions that satisfy:
(25)
(25)
Then, using the transposition method introduced by Lions [Citation21] it follows that the problem (Equation1(1)
(1) ), (Equation2
(2)
(2) ) and (Equation23
(23)
(23) ), (Equation24
(24)
(24) ) admits a unique solution u that belongs to
(26)
(26)
For later use, given , let
be sufficiently smooth interfaces in
such that by setting
,
and
the open subdomains of
defined by
, the three following criteria hold true:
(27)
(27)
is the lateral boundary
situated between
and
whereas
denotes the cardinality of a set. The criteria
in (Equation27
(27)
(27) ) are well satisfied if the
interfaces
are taken distinct and, for example, "parallel” to the inflow and outflow boundaries
and
such that the involved sources
occur upstream
.
The present study is motivated by the inverse source problem of identifying accidental pollution sources in surface water. That is the case where the unknown pollution sources occur in some given suspected zones within the monitored domain and thus, interfaces for measuring data generated by the occurring unknown sources coming in and out of each suspected pollution zone can be available. For example, in a monitored portion of a river, pollution is usually the consequence of discharging wastewater by one or several sources among industrials, farmers and city sewers occurring in some suspected zones that can be separated by interfaces for measuring the generated data crossing each interzone. In the remainder, we denote the suspected pollution zones in the monitored domain
and assume the interfaces
to be available for measuring the state and its flux crossing each interzone. In addition, we consider that at most only one pollution source could occur in each
(we rediscuss this assumption later in the outlook). Therefore, the source positions
defining F in (Equation24
(24)
(24) ) are assumed to be such that:
(28)
(28)
Developing an accurate identification method that leads to localize the responsable(s) and to determine the amount of each discharged accidental pollution would be of great use namely ecologically: by treating wastes to preserve the aquatic biodiversity, sanitary: by alerting downstream drinking water stations, legislatively: by holding accountable the responsable(s) and imposing penalties to prevent all not allowed future discharges, etc.
Besides, since in view of (Equation28(28)
(28) ) the source positions
are interior locations in
where
it follows that the state u solution of the problem (Equation1
(1)
(1) ), (Equation2
(2)
(2) ) and (Equation23
(23)
(23) ), (Equation24
(24)
(24) ) is smooth enough on
as well as on the
interfaces
. That allows to define the following observation operator:
(29)
(29)
where ,
for
and
. This is the so-called forward problem.
The inverse problem with which we are concerned here is: assuming (Equation25(25)
(25) ) and (Equation28
(28)
(28) ) hold true and given the measurements
of
on
,
of u on
and
of
on
, determine the unknown elements N,
and
defining F in (Equation24
(24)
(24) ) that yield
(30)
(30)
Remark 2.2:
If along the lateral boundary the flow velocity field V fulfils:
as mass cann’t penetrate a solid interface and
which is the no-slip condition [Citation22], where
is a unit vector tangent to
then,
on
and thus, the observation operator M[F] in (Equation29
(29)
(29) ) does not require any measurement related to the state u along
.
Besides, for later use we recall the following technical lemma established in [Citation13]:
Lemma 2.3:
For all , there exists two boundary controls
and
that maintain the solution v of the system:
(31)
(31)
(32)
(32)
3. Identifiability
In this section, we prove that under some reasonable assumptions the observation operator M[F] introduced in (Equation29(29)
(29) ) determines in a unique manner the unknown elements N,
and
defining in (Equation24
(24)
(24) ) the sought source F occurring in the problem (Equation1
(1)
(1) ), (Equation2
(2)
(2) ) and (Equation23
(23)
(23) ). This result is given by the following identifiability theorem:
Theorem 3.1:
Let be
unknown time-dependent point sources occurring in the problem (Equation1
(1)
(1) ), (Equation2
(2)
(2) ) and (Equation23
(23)
(23) ). Given
, let
and
be as in (Equation27
(27)
(27) ). Provided Lemmas 2.1 and 2.3 apply,
satisfy (Equation25
(25)
(25) ) and
fulfill (Equation28
(28)
(28) ), the observation operator M[F] in (Equation29
(29)
(29) ) determines uniquely the unknown elements N,
and
defining F.
For , let
be the state solution of the problem (Equation1
(1)
(1) ), (Equation2
(2)
(2) ) and (Equation23
(23)
(23) ) involving the source
where
,
and
satisfy (Equation25
(25)
(25) ) and (Equation28
(28)
(28) ). We denote
the associated observation operator as in (Equation29
(29)
(29) ). Then, from setting
, the variable
satisfies
(33)
(33)
The aim is to prove that implies . Since for
the source positions
satisfy (Equation28
(28)
(28) ), it follows that for all
we have in
one of the three following cases: Case 1. There is no source occurring in
and thus,
in
. Case 2. There is a source
from
and a source
from
occurring in
. Case 3. There is an only one source
where
occurring in
. We start by treating Case 2. which leads to deduce that Case 3. is absurd in view of (Equation25
(25)
(25) ). In Case 2. and according to (Equation33
(33)
(33) ), the variable w solves
(34)
(34)
Then, multiplying the first equation in (Equation34(34)
(34) ) by z introduced in (Equation13
(13)
(13) ) that solve the adjoint equation (Equation14
(14)
(14) ) and integrating by parts over
using Green’s formula and (Equation33
(33)
(33) ) gives
(35)
(35)
for all . Besides, according to
of (Equation27
(27)
(27) ), w solves in
a system similar to (Equation34
(34)
(34) ) where the first equation becomes homogeneous. That implies
in
which, in view of (Equation25
(25)
(25) ) and by considering the problem solved by w in
gives from applying the unique continuation Theorem in [Citation23] that
in
. Therefore, by integrating (Equation35
(35)
(35) ) over (0, T) we obtain
(36)
(36)
Hence, employing in (Equation36(36)
(36) ) the functions
for
,
and
leads to
(37)
(37)
where . Furthermore, the second equation in (Equation33
(33)
(33) ) implies that either
or
on
. Consequently, from (Equation9
(9)
(9) )–(Equation11
(11)
(11) ) the term
on
. Thus, it follows from (Equation37
(37)
(37) ) that
and
are subject to:
(38)
(38)
The function and the implication in (Equation38
(38)
(38) ) are given by Lemma 2.1. We set
in (Equation34
(34)
(34) ). Let
and
be such that the solution v of (Equation31
(31)
(31) ) yields (Equation32
(32)
(32) ) for
i.e.
a.e. in (0, T). Then, given
the variable
solves
(39)
(39)
Furthermore, from multiplying the first equation in (Equation34(34)
(34) ) by
and integrating by parts over
using Green’s formula and (Equation33
(33)
(33) ), we find
(40)
(40)
According to Titchmarsh’s Theorem on convolution of functions [Citation24] and since it holds
a.e. in (0, T), the equation (Equation40
(40)
(40) ) implies that
a.e. in (0, T). Hence, in Case 2. we get also
in
. Besides, in Case 3. w solves a system similar to (Equation34
(34)
(34) ) where in the right-hand side of the first equation occurs only the source
where
. Then, using the same techniques employed in Case 2., we obtain from (Equation37
(37)
(37) ) for
that
which is absurd since
satisfy (Equation25
(25)
(25) ). Therefore, it follows that
in
for all
.
4. Detection-identification method
Given , let
be the interfaces introduced in (Equation27
(27)
(27) ) and
be the source suspected zones defined by
where
. Then, assuming the unknown elements
and
defining in (Equation24
(24)
(24) ) F involved in the problem (Equation1
(1)
(1) )-(Equation2
(2)
(2) ) and (Equation23
(23)
(23) ) to be such that (Equation25
(25)
(25) ) and (Equation28
(28)
(28) ) hold true, we focus in this section on developing from the observation operator M[F] introduced in (Equation29
(29)
(29) ) a detection-identification method that goes throughout the monitored domain
to detect for all
whether there exists or not an active source occurring in the suspected zone
. Once a source is detected, the developed method determines lower and upper bounds of the mean value discharged by its unknown time-dependent intensity function
. Thereafter, it localizes the position
of the detected source as the unique solution of an equation satisfied by the dispersion-current function introduced in (Equation15
(15)
(15) ) and identifies the historic of
. Ultimately, the unknown number N of occurring sources is deduced as the sum of all detected-identified active sources. We proceed as follows:
4.1. Detection of active sources
For and in view of (Equation28
(28)
(28) ), multiplying the main equation (Equation1
(1)
(1) )–(Equation2
(2)
(2) ) in
by the adjoint function
for
that solves the adjoint equation introduced in (Equation14
(14)
(14) ), and integrating by parts using Green’s formula gives
(41)
(41)
where and the coefficient
is defined by
(42)
(42)
The notation introduced in (Equation41
(41)
(41) ) is what we refer to in the remainder as the Source Detection index. Notice that for
, the coefficient
obtained in (Equation42
(42)
(42) ) can be completely determined from the measurements M[F]. Then, according to (Equation41
(41)
(41) ) and since
satisfies (Equation25
(25)
(25) ) which implies that
it follows that whether
is null or not corresponds to whether there is no or there is an active source occurring in
. Moreover, if the source intensity function
keeps a constant sign, for example,
a.e. in (0, T) and the reaction coefficient
then, we have
in (0, T). Therefore, from (Equation41
(41)
(41) ) we deduce the following lower and upper bounds of the mean value discharged by
:
(43)
(43)
In practice, usually the reaction coefficient R is small enough and thus, (Equation43(43)
(43) ) provides an approximation of the mean value discharged by the involved unknown time-dependent source intensity function
without having to identify its historic. The active source detection procedure yields a useful tool that in practice leads to decide whether to go further with the identification of a detected source or to consider that it is not a significant source since the mean value discharged by its unknown intensity function remains below a certain tolerance/criterion. Besides, the knowledge of the time active limit
in (Equation25
(25)
(25) ), using for example the results established in [Citation25], improves the lower bound in (Equation43
(43)
(43) ).
4.2. Identification of the detected source occurring in 

Once an active time-dependent point source is detected to be occurring in i.e. in (Equation42
(42)
(42) ) the coefficient
, we apply the following identification procedure to determine the two unknown elements
and
defining the involved source: From multiplying Equations (Equation1
(1)
(1) )–(Equation2
(2)
(2) ) in
by the adjoint functions
introduced in (Equation13
(13)
(13) ) that solve the adjoint Equation (Equation14
(14)
(14) ) and integrating by parts using Green’s formula, we obtain
(44)
(44)
Since on we have
then, from substituting in (Equation44
(44)
(44) )
by the adjoint functions
,
and
introduced in (Equation13
(13)
(13) ) it follows that the unknown elements
and
defining the detected source occurring in
are subject to:
(45)
(45)
where is as defined in (Equation42
(42)
(42) ) and the two coefficients
,
are such that
(46)
(46)
Hence, in view of (Equation45(45)
(45) ) and (Equation46
(46)
(46) ) it follows that the sought source position
solves
(47)
(47)
where is the injective dispersion-current function introduced in (Equation15
(15)
(15) ). Then, to determine the two unknown elements
and
defining the time-dependent point source detected to be occurring in
, we proceed in the two following steps:
4.2.1. Step 1: Localization of the sought source position 

Since the coefficients defined in (Equation42
(42)
(42) )–(Equation46
(46)
(46) ) and involved in (Equation47
(47)
(47) ) can be completely determined from the measurements M[F] then, due to the injectivity of the dispersion-current function
introduced in (Equation15
(15)
(15) ) one could perform Newton’s iterations to determine the unique solution
of the last equation in (Equation47
(47)
(47) ) as the zero of the associated vector function. To this end, we compute the determinant
of the
Jacobian matrix
associated to the function
. Then, from (Equation15
(15)
(15) ) and using the expressions of
and
given in (Equation9
(9)
(9) ) and (Equation11
(11)
(11) ) we obtain in
(48)
(48)
whereas established in (Equation8(8)
(8) ) the determinant of the uniformly elliptic matrix D introduced in (Equation4
(4)
(4) )-(Equation6
(6)
(6) ) is
and
from (Equation3
(3)
(3) ). Thus, the
Jacobian matrix
is invertible in
and we have
(49)
(49)
That leads to perform the following Newton’s iterations to determine the unique solution of the last equation in (Equation47(47)
(47) ): given an initial guess
in
, we iterate
(50)
(50)
Remark 4.1:
Since in the state u is subject to only knowledge of its value and the value of its flux on the interfaces
it follows that the developed active source detection procedure as well as the localization of the unknown detected source are not yet available due to the not given term
involved in the coefficients
,
and
.
To determine the final state in
of the main problem (Equation1
(1)
(1) ), (Equation2
(2)
(2) ) and (Equation23
(23)
(23) ), (Equation24
(24)
(24) ), we employ the change of variables
in
. Then, since
satisfy (Equation25
(25)
(25) ) it follows that the variable
solves for all
the system:
(51)
(51)
where . Besides, in view of the condition
in (Equation27
(27)
(27) ), the variable
solves in
a system similar to (Equation51
(51)
(51) ) where the initial condition becomes
in
and the first boundary condition is replaced by
on
, whereas the last boundary condition is same and holds on
. Therefore, given measurements of the state u on
we employ a numerical method to compute u in
. Then, we consider the data assimilation problem [Citation26] of determining the final state
in
of the problem (Equation1
(1)
(1) )-(Equation2
(2)
(2) ) and (Equation23
(23)
(23) )-(Equation24
(24)
(24) ) from the computed data u in
. To this end, we establish the following result:
Proposition 4.2:
Let u be the solution of the problem (Equation1(1)
(1) ), (Equation2
(2)
(2) ) and (Equation23
(23)
(23) ), (Equation24
(24)
(24) ),
in
and
be the open subdomain of
introduced in (Equation27
(27)
(27) ). Provided the assertion (Equation25
(25)
(25) ) holds true, the data u in
where
determines in a unique manner the final state
in
and we have
(52)
(52)
where C is a Carleman constant [Citation27] that does not depend on .
See the Appendix 1.
To determine the final state in
using the data u in
, we denote
the normalized eigenfunctions of the following problem:
(53)
(53)
that form a complete orthonormal family of , see [Citation13]. Then, the solution of the problem (Equation51
(51)
(51) ) is expressed as follows:
(54)
(54)
where is the eigenvalue associated to
and
denotes the inner product in
. Therefore, from trancating the series in (Equation54
(54)
(54) ) using a sufficiently large number K of initial terms, we determine the coefficients
for
from solving the following least squares problem:
(55)
(55)
That leads using the change of variables in
and in view of (Equation54
(54)
(54) ) to deduce the following approximation of the final state
in
associated to the main problem (Equation1
(1)
(1) ), (Equation2
(2)
(2) ) and (Equation23
(23)
(23) ), (Equation24
(24)
(24) ):
(56)
(56)
4.2.2. Step 2: Identification of the unknown time-dependent intensity 

Assuming now the position of the detected active source occurring in
to be already localized, we focus here on identifying the historic of its unknown time-dependent intensity function
. To this end, let
and
be two boundary controls that lead the solution v of the problem (Equation31
(31)
(31) ) to satisfy the assertion (Equation32
(32)
(32) ) for
. Then, from multiplying the main Equations (Equation1
(1)
(1) )–(Equation2
(2)
(2) ) in
by the solution
of the system (Equation39
(39)
(39) ) and integrating by parts using Green’s formula, we obtain
(57)
(57)
where the coefficient is defined as follows:
(58)
(58)
Therefore, the identification of the unknown time-dependent intensity function can be transformed into solving the deconvolution problem in (Equation57
(57)
(57) )–(Equation58
(58)
(58) ). To this end, given a desired number of time steps M, we employ the regularly distributed discrete times
for
where
. Then, using the trapezoidal rule we get
(59)
(59)
where according to (Equation31(31)
(31) ), we used
and
. Thus, using the notation
and in view of (Equation59
(59)
(59) ) we obtain a discrete version of the deconvolution problem defined from (Equation57
(57)
(57) )–(Equation58
(58)
(58) ) that leads to the following recursive formula:
(60)
(60)
For the clearness of our presentation, we summarize the different steps of the developed detection-identification method in the following algorithm:
5. Numerical experiments
We carry out numerical experiments in the case of a rectangular domain defined by
with the associated boundaries:(61)
(61)
where and
. Then, we consider a flow defined by a unidirectional mean velocity vector
where
. Therefore, from setting
in (Equation10
(10)
(10) )–(Equation12
(12)
(12) ) it follows that the dispersion-current function
introduced in (Equation15
(15)
(15) ) is defined for all
as follows:
(62)
(62)
Furthermore, in view of (Equation4(4)
(4) )-(Equation5
(5)
(5) ) the hydrodynamic dispersion tensor D is reduced to the
diagonal matrix defined by
. To generate the boundary and internal measurements defining in (Equation29
(29)
(29) ) the observation operator M[F], we solve the problem (Equation1
(1)
(1) )-(Equation2
(2)
(2) ) and (Equation23
(23)
(23) ), where F is as introduced in (Equation24
(24)
(24) )-(Equation25
(25)
(25) ) for
time-dependent point sources located at
and loading the intensity functions defined in
by
(63)
(63)
whereas for all
. In (Equation63
(63)
(63) ),
is the characteristic function and the coefficients are such that:
,
,
,
,
,
and
,
,
. Moreover, the mean values of the source intensity functions introduced in (Equation63
(63)
(63) ) are given as follows:
(64)
(64)
where is the Gauss error function. Besides, we employ the following approximation of the Dirac mass
where
:
(65)
(65)
with in (Equation65
(65)
(65) ). As far as the interfaces
introduced in (Equation27
(27)
(27) ) are concerned, we set
and consider
(66)
(66)
That implies for
. Notice that provided the involved source positions
are occurring upstream
and do not lie on
then, the three criteria
introduced in (Equation27
(27)
(27) ) are well satisfied.
To identify the unknown elements and
defining in (Equation24
(24)
(24) ) F that generated the observations M[F], we apply the detection-identification method developed in the previous section by following the steps described in Algorithm. Therefore, we start in view of the criterion
by solving numerically the forward problem satisfied by the state u in
. Then, using the computed data u in
, we solve the least squares problem introduced in (Equation55
(55)
(55) ) to determine the final state
in
. To this end, we compute the normalized eigenfunctions
of the problem (Equation53
(53)
(53) ) for a mean velocity vector
and thus, a reduced dispersion tensor
with
. That gives
(67)
(67)
where for all , the coefficient
is determined from solving the equation
(68)
(68)
and the coefficient is defined by
(69)
(69)
is the eigenvalue associated to
.
To carry out numerical experiments and as far as the discretization of is concerned, we employ uniform mesh sizes:
,
with a time-step
and use a 5-points finite differences Crank–Nicholson scheme for
,
and
. Then, we set
(4 hr ),
(3 hr ) and use mean longitudinal and transverse dispersion coefficients
,
with a molecular diffusion
,
and
. To generate the measurements defining in (Equation29
(29)
(29) ) the observation operator M[F], we solve the problem (Equation1
(1)
(1) )-(Equation2
(2)
(2) ) and (Equation23
(23)
(23) ) using F as defined in (Equation24
(24)
(24) ) for
time-dependent point sources located at
,
,
and loading the intensity functions introduced in (Equation63
(63)
(63) ). To identify the final state
in
, we use the records of the state u on
and solve by employing a 5-points finite differences Crank–Nicholson scheme the forward problem satisfied by u in
. That leads to generate the data u in
. Then, using the Conjugate Gradient Method, we solve the minimization problem introduced in (Equation55
(55)
(55) ) and thus, we define the identified final state as given in (Equation56
(56)
(56) ). The obtained numerical results are presented by drawing in a same graphic both identified and simulated final states. We indicate for each experiment the
relative error computed from
. We carried out numerical experiments for
and different values of
and
.
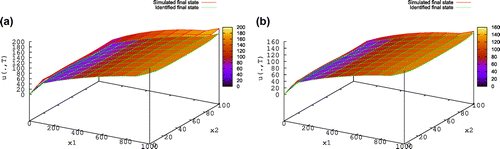
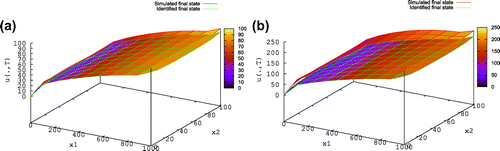
The numerical results presented in Figures and show that the procedure described in (Equation51(51)
(51) )–(Equation56
(56)
(56) ) identifies accurately the final state
in
associated to the main problem (Equation1
(1)
(1) )–(Equation2
(2)
(2) ) and (Equation23
(23)
(23) )–(Equation24
(24)
(24) ). The analysis of those results indicates that the
relative error on the identified final state depends on the dimensionless Peclet number
. In fact, the reconstruction of
in
is more accurate for smaller Peclet number.
Then, we apply the developed detection-identification method to identify the unknown elements and
defining in (Equation24
(24)
(24) ) the sought source F occurring in
that generated the measurements M[F] given in (Equation29
(29)
(29) ). To this end, we employ the developed active source detection procedure to go throughout
by detecting for all
whether there is or not an active source occurring in the subdomain
. Therefore, we compute for
the Source Detection index
from (Equation41
(41)
(41) )-(Equation42
(42)
(42) ) and determine as in (Equation43
(43)
(43) ) the estimated lower and upper bounds of the mean value loaded by the unknwon intensity function
occurring in
. To carry out numerical experiments, we use
,
and generate the simulated measurements M[F] defined in (Equation29
(29)
(29) ) using
point sources loading the time-dependent intensity functions
introduced in (Equation63
(63)
(63) ) for different source locations
. As far as the obtained numerical results are concerned, we present in a same table for each simulated measurements the computed Source Detection index
in
for
, the interval
obtained in (Equation43
(43)
(43) ) and the corresponding mean value of the intensity function
, used for simulation, computed from (Equation64
(64)
(64) ) for
. We give in the caption of each table the three source positions
used to generate the simulations.
Table 1. Source Detection: simulation with .
Table 2. Source Detection: simulation with .
Table 3. Source Detection: simulation with .
Table 4. Source Detection: simulation with .
The analysis of the numerical experiments presented in Tables – shows that the developed active source detection procedure determines accurately throughout the monitored domain whether there is or not an active source occurring in each
. Furthermore, in view of (Equation43
(43)
(43) ) this procedure provides estimated lower and upper bounds
and
of the mean value loaded by the unknwon time-dependent intensity function
of the deceted source occurring in
. In Tables –, the two estimated frame bounds appear to be accurate and yield an approximation of the mean value loaded by the unknown time-dependent intensity function
without having to identify its historic.
Besides, once an active time-dependent point source is detected in where
, we employ the developed identification procedure to localize its position
from (Equation47
(47)
(47) )-(Equation50
(50)
(50) ) and to identify its time-dependent intensity function
using the recursive formula (Equation60
(60)
(60) ). To carry out numerical experiments, we use for example the simulations M[F] generated for the experiments in Table 4. Since the results of the detection procedure presented in Table 4 indicate that the involved sources are occurring in
for
then, we apply the identification procedure to determine for each
the two unknown elements
and
defining the detected source occurring in
. To this end, we compute for
the coefficients
,
,
from (Equation42
(42)
(42) ) and (Equation46
(46)
(46) ). Then, according to (Equation47
(47)
(47) ) and in view of (Equation62
(62)
(62) ), the two unknown coordinates
and
defining the position
of the detected source occurring in
are localized as follows:
(70)
(70)
Furthermore, using the localized source position we identify its time-dependent intensity function
from (Equation60
(60)
(60) ). To this end, we need to solve the boundary control problem introduced in (Equation31
(31)
(31) )–(Equation32
(32)
(32) ) for
. By considering the following adjoint problem:
(71)
(71)
and using similar techniques as in [Citation13] it follows that setting on
and
on
leads the solution of the problem (Equation31
(31)
(31) ) to yield the assertion (Equation32
(32)
(32) ) for
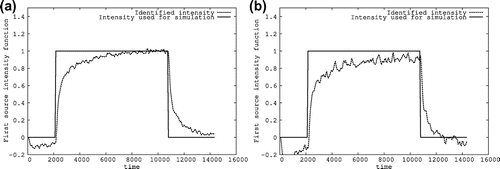
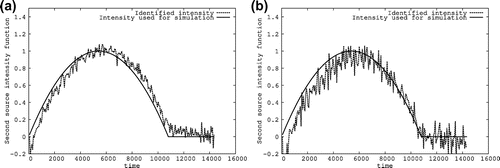
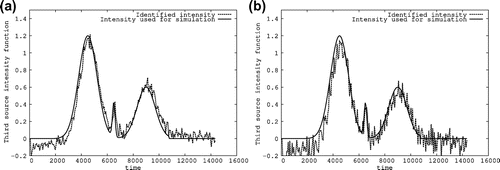
. We present the obtained identification results for the three detected sources in Table 4 while introducing a Gaussian noise on the used simulations. We give for each introduced intensity noise the three identified source positions and present on a same graphic for each involved source, the intensity function used for simulation given in (Equation63
(63)
(63) ) and the identified intensity computed from (Equation60
(60)
(60) ). We indicate also for each drawing the
-relative error computed from
.
The identified source positions are as follows: For a Gaussian noise , we obtained
,
and
. For a Gaussian noise
, we found
,
and
.
The numerical results obtained for the localization of the sought source positions as well as for the identification of their unknown time-dependent intensity functions presented in Figures – show that the developed identification procedure determines accurately the unknown elements defining the occurring sources and is relatively stable with respect to the introduction of a Gaussian noise on the used measurements.
6. Conclusion and outlook
We addressed the non-linear inverse source problem of identifying multiple unknown time-dependent point sources occurring in a two-dimensional evolution advection–dispersion–reaction equation. We developed a source detection procedure that goes throughout the monitored domain to detect the presence of all occurring active sources. Once a source is detected, this procedure determines lower and upper bounds of the mean value discharged by its unknown time-dependent intensity function without having to identify the historic of this latest. In practice, this procedure leads to decide whether to go further with the identification of a detected source or to consider that it is not a significant source since the mean value discharged by its unknown intensity function remains below a certain tolerance/criterion. Then, we developed an identification method that localizes the sought position of a detected source as the unique solution of an equation satisfied by the introduced dispersion-current function and identifies its intensity function from solving an associated deconvolution problem. Some numerical experiments on a variant of the surface water BOD pollution model were carried out. The obtained numerical results show that the developed detection–identification method is accurate and relatively stable with respect to the introduction of a Gaussian noise on the used measurements.
6.1. Outlook
We carried out some numerical experiments where the assumption (Equation28(28)
(28) ) is not respected. That is we considered a domain
containing an only one suspected zone
i.e.
where multiple point sources could occur. Then, we applied the detection–identification method using measurements generated firstly by one, secondly by two and thirdly by three point sources occurring in
by discharging three different positive constants. The obtained numerical results are as follows: in the case of one point source: the localized position
and
are accurate. In the case of two point sources: the localized position
is between the two involved source positions. In the case of three point sources: the localized position
is in the triangle of summits the three involved source positions. Moreover, in these two last cases, the localized position
seems to be nearer to the source position of biggest discharge constant. However, in all cases the determined
corresponds to the sum of all discharged amounts.
Although it is expected, as in (Equation41(41)
(41) )–(Equation42
(42)
(42) ), that the computed
corresponds to the sum of all amounts discharged by the different involved point sources, it is not clear whether the localized source position is always in the polygon of summits the occurring source positions. An outlook of the present study could be to investigate this claim which would give another application of the developed detection–identification method: to be applied on a monitored domain
containing suspected zones
where multiple time-dependent point sources of known positions could occur. Then, the method determines the total amount discharged by all sources occurring in
. The localized position would be interpreted as follows: (1) if it coincides with one among the already known positions then, it is the unique source responsible of the detected pollution; (2) If it is in a polygon of summits some of the known source positions then, there were more than one active source among the already known positions (the number of active sources is it the number of summits?); (3) Otherwise, the responsable of the detected pollution is rather a new unknown source(s).
Notes
No potential conflict of interest was reported by the authors.
References
- Hamdi A. Inverse source problem in a 2D linear evolution transport equation. Inverse Prob Sci Eng. 2012;20:401–421.
- Cannon JR. Determination of an unknown heat source from overspecified boundary data. SIAM J Numer Anal. 1968;5:275–286.
- Engl HW, Scherzer O, Yamamoto M. Uniqueness of forcing terms in linear partial differential equations with overspecified boundary data. Inverse Prob. 1994;10:1253–1276.
- Yamamoto M. Conditional stability in determination of densities of heat sources in a bounded domain. Int Ser Numer Math. 1994;18:359–370. Birkhuser, Verlag Basel.
- Sakamoto K, Yamamoto M. Inverse source problem with a final overdetermination for a fractional diffusion equation. Math Control Related Fields. 2012;1:509–518.
- Hettlich F, Rundell W. Identification of a discontinuous source in the heat equation. Inverse Prob. 2001;17:1465–82.
- El Badia A, Ha-Duong T, Hamdi A. Identification of a point source in a linear advection-dispersion-reaction equation: application to a pollution source problem. Inverse Prob. 2005;21:1121–39.
- Hamdi A. The recovery of a time-dependent point source in a linear transport equation: application to surface water pollution. Inverse Prob. 2009;25:75006–75023.
- Hamdi A, Mahfoudhi I. Inverse source problem in a one-dimensional evolution linear transport equation with spatially varying coefficients: application to surface water pollution. Inverse Prob Sci Eng. 2013;21:1007–1031.
- Andrle M, Ben Belgacem F, El Badia A. Identification of moving pointwise sources in an advection–dispersion–reaction equation. Inverse Prob. 2011;27:025007.
- Ben Belgacem F. Uniqueness for an ill-posed reaction-dispersion model. Application to organic pollution in stream-waters (One-dimensional model). Inverse Prob Imaging. 2012;6–2:163–181.
- Hamdi A. Detection and identification of multiple unknown time-dependent point sources occurring in 1D evolution transport equations. Inverse Prob Sci Eng. 2016;1–23. doi:10.1080/17415977.2016.1172224.
- Hamdi A, Mahfoudhi I. Inverse source problem based on two dimensionless dispersion-current functions in 2D evolution transport equations. J Inverse Ill Prob. 2016;24:663–685. doi:10.1515/JIIP-2014-0051.
- Andrle M, El Badia A. Identification of multiple moving pollution sources in surface waters or atmospheric media with boundary observations. Inverse Prob. 2012;28:075009.
- Cox BA. A review of currently available in-stream water-quality models and their applicability for simulating dissolved oxygen in lowland rivers. Sci Total Environ. 2003;314–316:335–77.
- Brown LC, Branwell TO. The enhanced stream water quality models QUAL2E and QUAL2E-UNCAS: Documentation and user manual. EPA: 600/3-87/007. 1987.
- Myung L, Won S. 2D Finite element pollutant transport model for accidental mass release in rivers. KSCE J Civil Eng. 2010;14:77–86.
- Akira Okubo. Diffusion and ecological problems: mathematical models. New York (NY): Springer-Verlag; 1980.
- Bear J, Bachmat Y. Introduction to modeling of transport phenomena in porous media. Dordrecht: Kluwer Academic Publishers; 1991.
- Oelkers EH. Physical and chemical properties of rocks and fluids for chemical mass transport calculations. In: Lichtner PC, Steefel CC, Oelkers EH, Editors. Reactive transport in porous media. Washington (DC): The Mineralogical Society of America. 1996. p. 131–191.
- Lions JL. Pointwise control for distributed systems in control and estimation in distributed parameters systems. In: Banks HT, Editor. Frontiers in Applied Mathematics. Philadelphia: Edited by Banks H. T. SIAM; 1992. p. 1–39.
- Lauga E, Brenner PM, Stone AH. Microfluidics: the no-slip boundary condition, Chapter 15 in Handbook of Experimental Fluid Dynamics. New-York (NY): Springer; 2005.
- Lin FH. A uniqueness theorem for parabolic equations. Commun Pure Appl Math. 1990;43:125–136. MR 90j:35106.
- Titchmarsh EC. Introducton to the theory of Fourier Integrals. London: Oxford University Press; 1939.
- Hamdi A, Mahfoudhi I, Rejaiba A. Identification of the time active limit with lower and upper bounds of the total amount loaded by unknown sources in 2D transport equations. J Eng Math. 2015;97:101–17.
- Garca G, Osses A, Puel J-P. A null controllability data assimilation methodology applied to a large scale ocean circulation model. M2AN Math Model Numer Anal. 2011;45:361–386.
- Fernandez-Cara E, Guerrero S. Global Carleman inequalities for parabolic systems and applications to controllability. SIAM J Control Optim. 2006;45:1395–1446.
- Fursikov A, Imanuvilov OY. Controllability of evolution equations. Lecture notes: Research Institute of Mathematics, Seoul National University, Korea; 1996.
- Rasmussen JM. Boundary control of linear evolution PDEs-continuous and discrete [Ph.D. thesis]. Technical University of Denmark, 2004.
Appendix 1
Here, we establish the proof of Proposition 4.2:
In view of [Citation28], we consider the null controllability problem of determining a distributed control that to a given initial state
drives the solution
of the following system:
(A1)
(A1)
(A2)
(A2)
where is the characteristic function of
. Multiplying the first equation in (EquationA1
(A1)
(A1) ) by
the solution of the adjoint problem that to a given
associates
(A3)
(A3)
and integrating by parts over using Green’s formula gives
(A4)
(A4)
Therefore, a distributed control solves the null controllability problem introduced in (EquationA1
(A1)
(A1) )–(EquationA2
(A2)
(A2) ) if and only if it yields
(A5)
(A5)
The necessary condition in (EquationA5(A5)
(A5) ) is implied by (EquationA4
(A4)
(A4) ) whereas the sufficient condition is obtained from observing that if the solution
of (EquationA1
(A1)
(A1) ) with a given
satisfies (EquationA5
(A5)
(A5) ) then, from (EquationA4
(A4)
(A4) ) we get
for all
. That leads to
in
and thus,
solves the null controllability problem (EquationA1
(A1)
(A1) )–(EquationA2
(A2)
(A2) ).
Besides, let be the solution of the adjoint problem introduced in (Equation71
(71)
(71) ) using the initial data
that yields the minimizer of the functional
which to a given
associates, for the coercivity and the strict convexity of J see [Citation13,Citation29]:
(A6)
(A6)
Then, for all
and thus, in view of (EquationA5
(A5)
(A5) ) the so-called Hilbert Uniqueness method (HUM) distributed control defined by:
in
solves the null controllability problem (EquationA1
(A1)
(A1) )–(EquationA2
(A2)
(A2) ). Furthermore, from setting
in (EquationA5
(A5)
(A5) ) the HUM distributed control fulfills
(A7)
(A7)
where C is a Carleman constant [Citation27]. Let in
where
is the solution of the null controllability problem (EquationA1
(A1)
(A1) )–(EquationA2
(A2)
(A2) ) involving the HUM distributed control
in
. Then, from multiplying the first equation in (Equation51
(51)
(51) ) by
and integrating by parts over
using Green’s formula we find
(A8)
(A8)
Moreover, using in
and according to (EquationA7
(A7)
(A7) )–(EquationA8
(A8)
(A8) ) we get
That is the result announced in Proposition 4.2.