?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
Structural damage detection is a key part of structural health monitoring. The generalized flexibility matrix approach is an effective method for damage detection. Compared with the flexibility matrix approach, it requires less number of natural frequencies and corresponding mode shapes. In this paper, the approach is improved by considering the nonnegativity of the damage extent. The error bound of two solutions calculated by the improved approach using natural frequencies and corresponding mode shapes without and with noises is derived. Numerical examples with different damage scenarios show that compared with the original generalized flexibility matrix approach, our proposed method works better.
1. Introduction
Many engineering structures such as bridges, tall buildings and offshore platforms are designed to have long life spans. During their service life-cycles, they may be subjected to the deterioration due to environmental influences, changes in load characteristics and some random actions [Citation1]. These factors often result in structural damages. Damages are main causes of structural failure in mechanical structures [Citation2]. If they cannot be found immediately, they will become more and more serious, and may lead to a disaster. Thus, detecting damages at the early stage is very important [Citation3]. It is a key part of structural health monitoring [Citation4].
Various detection methods have been proposed during the last few decades. Among these methods, a type of methods named vibration-based method has attracted much attention. Vibration-based method makes full use of the difference in dynamic features of the structure before and after the damage. Changes in natural frequencies, mode shapes and its curvatures, modal flexibility and its derivatives, modal strain energy and frequency response function can be utilized [Citation5]. This type of method can present a global damage assessment, and detect damages which are not on the surface of the structure.
Changes in the first lower natural frequencies are frequently used in damage detection, because frequencies can be measured more easily and exactly than corresponding mode shapes. For example, Li et al. detected damages by the generalized flexibility matrix (GFM) and changes in natural frequencies [Citation3]. Zhang et al. used changes in the first three natural frequencies to detect damages of continuum structures [Citation6]. They presented a level set model, which can perfectly describe the shape of damage regions and can deal with damage regions with complex shapes. Based on the measured natural frequencies of structures, Wang et al. identified damages by interval analysis technique [Citation7]. In addition, frequency response function has also been extensively used for damage detection [Citation8–12]. Yu et al. used frequency response function and fuzzy clustering to diagnose damages of a six bay truss bridge [Citation9]. Using frequency response function, Guo et al. transferred the identification problem to a nonlinear optimization problem whose objection function is the constitutive relation error [Citation10].
Besides natural frequency, the vibration mode is fundamental and important in damage detection. It provides more abundant information than frequency. For example, Pandey et al. proposed the mode shape curvature method and successfully applied the method to detect damage in cantilever and simply supported beam [Citation13]. The basic idea of their method is that changes in mode shape curvature at nodes related to damage elements are significant before and after the damage. Cao et al. utilized the improved form of the mode shape curvature to detect cracks in beams [Citation14]. Yan and Ren derived the close form of the sensitivity of modal flexibility, and used it to detect damage locations and extents [Citation15]. Seyedpoor and Montazer proposed a flexibility-based damage probability index and used it for damage identification [Citation16]. Lu and Wang proposed an enhanced response sensitivity approach for structural damage detection [Citation17]. Shahri and Ghorbani-Tanha used the closed-form sensitivity matrix of modal kinetic energy change ratio to detect the damage [Citation18]. Hosseinzadeh et al. employed Neumann series expansion-based model reduction technique for damage identification with sparse sensor measurements [Citation19]. Cui et al. proposed a damage detection method based on strain modes [Citation20]. Bernagozzi et al. gave a detection method for buildings, their approach is based on modal flexibility deflections [Citation21]. Dahak et al. presented a method for predicting the damage location and severity based on the frequency contour method [Citation22]. The contour lines are plotted by the values of changes in measured frequencies and the curvature mode shapes of the intact structure. Their method is simpler than other similar methods. In addition, Ghadimi and Kourehli detected cracks in beam structures under moving mass using extreme learning machine and the least square support vector machine [Citation23].
Besides above methods, some researchers presented two-stage method for damage detection [Citation24–27]. This kind of method first locates potential damage elements by a damage indicator. Then, the extent of damage elements is achieved by solving an optimization problem. The number of optimization variables is equal to that of damage elements that are determined by the first step. Therefore, such an optimization problem is usually small in scale, and its solution is relatively easy.
In 2010, Li et al. first presented the definition of GFM [Citation28]. The advantage of their method is that the effect of truncating higher-order modes can be reasonably reduced. Compared with the original flexibility matrix method [Citation29,Citation30], it requires less number of natural frequencies and corresponding mode shapes. Thus, the idea of the GFM has been extensively used for damage detection [Citation3,Citation28,Citation31–33]. However, their method does not take into account the nonnegativity of the damage extent. In this paper, the approach is improved by considering the boundedness of the damage extent.
The remainder of the paper is organized as follows. In Section 2, the problem is formulated. The GFM approach (GFMA) is reviewed and our method is presented in Section 3. The error bound of two solutions calculated by our proposed method using natural frequencies and corresponding mode shapes without and with noises is derived in Section 4. Numerical examples are employed to illustrate the effectiveness of the method in Section 5 and conclusions are drawn in Section 6.
2. Preliminaries
2.1. Problem formulation
In this paper, it is assumed that the structural damage only results in a reduction of structural stiffness, the structural mass and the number of degrees of freedom (DOFs) remains unchanged. Under this assumption, the structural damage detection problem can be stated as follows [Citation28]. Let and
be the
global stiffness matrix of the undamaged and damaged structures, respectively.
is the
stiffness matrix corresponding to the
element of the undamaged structure. Then, the matrix
can be expressed as follows
(1)
(1)
where
is the change of the global stiffness matrix. By the finite element method,
is the summation of changes of some elemental stiffness matrices, i.e.
(2)
(2)
where
is the number of total elements of the structure,
stands for the damage extent of the
element
.
indicates that the
element is undamaged. Due to the inevitable measurement noise, small
may be produced even if the
element is intact. Thus, small
can not demonstrate that the
element is damaged. In this paper, the
element is regarded as a damaged one if
. The same limitation was also adopted in Ref. [Citation28]. The purpose of structural damage detection is to find all damage locations and extents, i.e. calculate
by using the measured data.
2.2. The definition of the vec operation
Definition 2.1
([Citation34,Citation35]): Let be a matrix with size
. Its column partitioning is
(3)
(3)
Then
is an
-by-1 vector obtained by stacking columns of
, i.e.
(4)
(4)
It can be observed that the vec operation is linear. In addition, the vec operation has the following property
(5)
(5)
The above equation can be easily verified by definition 1.
3. The improved GFMA
In this section, the existing GFMA is first reviewed [Citation28]. Then, our proposed method is given.
3.1. The GFMA
Substituting Equation (2) into Equation (1), and differentiating with respect to , we have
(6)
(6)
Let
be the
flexibility matrix for the damaged structure, i.e.
(7)
(7)
where
is the
identity matrix. Differentiating Equation (7) with respect to
yields
(8)
(8)
Post-multiplying Equation (8) by
and substituting Equation (6) into it, we can obtain
(9)
(9)
Based on the mode shape normalization with respect to the mass matrix, the GFM is introduced. It is defined as follows
(10)
(10)
where
is the mass matrix, it remains unchanged before and after the damage,
is a vector consisting of the damage extent of all elements,
and
are the mode shape matrix and diagonal matrix of natural frequency squared for the damaged structure, respectively. Equation (10) indicates that a larger
can cause a reduced contribution of higher-order modes. For
, Equation (10) reduces to the original flexibility matrix, i.e.
. For
, the GFM in Equation (10) becomes
(11)
(11)
In this paper, only
is used. Differentiating Equation (11) with respect to
yields
(12)
(12)
Substituting Equation (9) into Equation (12) and setting
, we get
(13)
(13)
where
is the
flexibility matrix corresponding to the undamaged structure. So far, sensitivity analysis of the GFM is achieved. In practice, the number of damaged elements is usually small compared with the number of structural elements, i.e. most components of
are zeros. Even for the damage elements, the damage extent can not be very large in most cases, i.e. nonzero components of
are not very large. Thus,
in Equation (10) can be approximated by the first-order Taylor’s series expansion, i.e.
(14)
(14)
Combining (13) and (14), we have
(15)
(15)
where
,
is the change of the GFM, and
(16)
(16)
Equation (11) indicates that the GFM can be approximated by only a few of lower frequency modes. Thus,
(17)
(17)
where
is the number of measured modes,
and
are the
smallest frequency and corresponding mode shape for the damaged structure,
and
are the
smallest frequency and corresponding mode shape for the undamaged structure. Combining (15) and (17), and ignoring the error, we have
(18)
(18)
By vec operation, the above equation can be transferred to be a linear system with
equations and
unknowns, that is
(19)
(19)
Equation (19) can be written as
(20)
(20)
where
, and
. Solving the linear system (20) by the least square method, both damage locations and extents can be achieved.
3.2. Our proposed method
As has been said in Section 2, the damage extent of the element should be nonnegative, i.e.
. However, the above GFMA does not consider this property of damage extents. In this paper, the following optimization model is employed for the damage detection
(21)
(21)
This is a bound-constrained least square (BLS) problem. As to the method of solving this problem, we refer readers to Refs. [Citation36–38].
4. The error bound of two solutions calculated by our proposed method using the measured data without and with noise
During the process of the structural dynamic test, measured natural frequencies and corresponding mode shapes are often contaminated. In this section, the error bound of two solutions calculated by our proposed method using the measured data without and with noise is presented. For this purpose, the linear complementarity problem (LCP) is first reviewed.
The LCP is to calculate a vector such that
(22)
(22)
where
,
, and the notation ‘
’ represents the componentwise defined partial ordering between two vectors. In the following, problem (22) and its solution are denoted by LCP (
) and
, respectively. Many problems in scientific computing and engineering applications need to solve the LCP. For example, the market equilibrium problem, the contact problem and the Nash equilibrium point problem of a bimatrix game are eventually transformed into LCPs [Citation39,Citation40]. In addition, the LCP also constitutes the Karush-Kuhn-Tucker optimality condition of the quadratic programming problem. Let’s consider the following the quadratic programming problem:
(23)
(23)
where
,
is a symmetric matrix. Then, we have the following result.
Lemma 4.1
([Citation39]): Let be the solution of problem (23). Then, there exist vector
and slack vectors
such that
together satisfy
(24)
(24)
i.e.
is the solution of LCP
.
Some theoretical analyses and algorithms for the LCP have already been proposed [Citation39–41]. Several results related to our problem are given as follows.
Lemma 4.2
([Citation40]): If is a symmetric positive definite (SPD) matrix, then for any
, the LCP (
) has a unique solution.
Lemma 4.3
([Citation41]): If is a SPD matrix,
, then
Lemma 4.4:
Let be the solution of the BLS problem (21). Then, there exists
such that
is the solution of LCP
.
Proof:
See the appendix.
Theorem 4.1:
Assume ,
.
is the solution of the following BLS problems
,
. Then,
Proof:
See the appendix.
The following theorem gives the error bound of two solutions calculated by natural frequencies and corresponding mode shapes without and with noise.
Theorem 4.2:
Assume and
are the
smallest frequency and the corresponding mode shape of the damaged structure without noise,
and
are the
smallest frequency and the corresponding mode shape of the damaged structure with noise
.
and
are solutions of our proposed method calculated by the uncontaminated and contaminated measured data, respectively. Then, the following inequality holds
where
is a positive number given in the following.
(25)
(25)
Proof:
See the appendix.
Remark 4.1:
From the above theorem, it can be observed that for a given noise, the error bound of two solutions of our method is mainly determined by .
5. Numerical examples
In this section, two examples are presented to show the effectiveness of the proposed method, each example includes four damage scenarios. Here, damage is simulated by reducing the stiffness of specified elements. All BLS problems in these examples are solved by the command lsqlin in Matlab (R2016b).
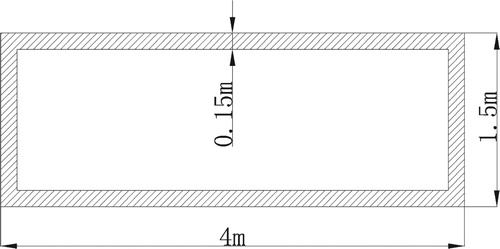
Example 1: A hollow beam bridge model is studied in this example. The length and width of the bridge are and
, respectively. The size of the cross section is given in Figure . The bridge is simplified as a plane beam and is discretized into a finite element model with 22 elements and 23 nodes, as shown in Figure . Axial displacements of all nodes are ignored. Thus, every node has 2 DOFs except two constrained nodes. The total number of DOFs in the structure is 42. The material and geometric parameters are as follows: Young’s modulus
, Poisson’s ratio
, density
, length
, and second moment of area
. Four damage cases are considered, as shown in Table .
Table 1. Damage cases in Example 1.
In this example, only the first frequency and the corresponding mode shape are employed to calculate damage locations and extents, i.e. solving the BLS problem (21) with to achieve
. For comparison, damage locations and extents are also calculated by the GFMA with
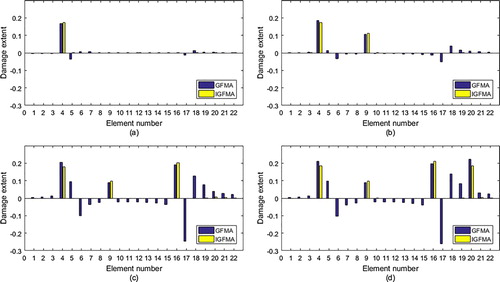
, where GFMA is the abbreviation of generalized flexibility matrix approach. The results of two approaches are given in Figure . It can be observed that negative entries with larger absolute value are produced by the GFMA, which are opposed to the fact
. This is because GFMA does not consider the nonnegativity of damage extent. Our method utilizes the nonnegativity of damage extent and avoids this deficiency of the GFMA. In addition, for the last two damage cases, misjudgements for elements 18 and 19 are made by the GFMA. Our method, i.e. improved GFMA (IGFMA), does not produce the misjudgement.
Figure 3. Calculated results for all damage cases in Table : (a) Case 1; (b) Case 2; (c) Case 3; (d) Case 4.
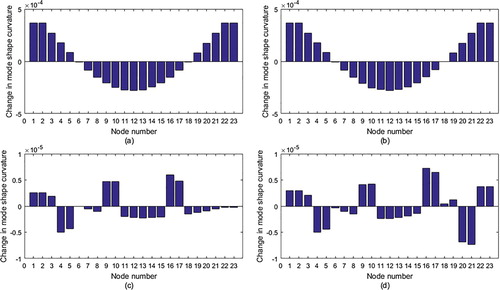
In addition, our method is compared with the mode shape curvature method. The mode shape curvature method detects damaged elements by changes in mode shape curvature of structural nodes before and after the damage. If the change in mode shape curvatures of a node is large, the element connected to this node is deemed as a damage one. The mode shape curvature in this paper is calculated by the central difference approximation. Figure presents changes in mode shape curvatures of every node for all damage cases in Table . From Figure , it can be observed that the mode shape curvature method can exactly find damage locations for the last two damage cases. For the first two damage cases, it cannot give the right results. In addition, the method cannot provide damage extents.
Figure 4. Mode shape curvatures for all damage cases in Table : (a) Case 1; (b) Case 2; (c) Case 3; (d) Case 4.
Our method has been carried out in the noise environment. The noise level of the natural frequency is , and the corresponding mode shape are contaminated with
,
, and
random noises. The assumed noise environment is produced by following formulas [Citation18,Citation42]:
(26)
(26)
(27)
(27)
where
and
are natural frequencies of the damaged structure without and with noise,
and
are Gaussian random numbers with mean
and variance
,
and
are noise levels of the natural frequency and the mode shape, respectively.
and
are the
components of mode shapes of the damaged structure without and with noise, and
is the largest absolute value among mode shape components. For every noise level, the contaminated natural frequency and the corresponding mode shape are produced by Equations (26) and (27). Subsequently, our method is implemented using each group of contaminated data to achieve the damage extent vector
. The procedure is repeated 1000 times. The mean value vector
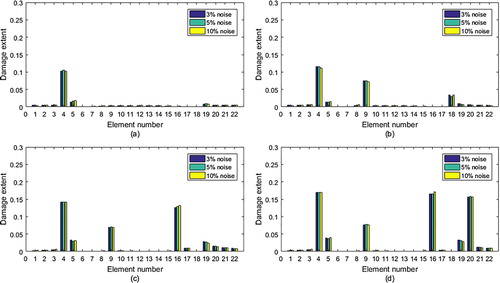
is obtained by the above 1000 calculated damage extent vectors. Figure presents the mean value vectors for all damage cases in Table . It can be seen that the IGFMA works well for these three noise levels.
Figure 5. Calculated results for all damage cases in Table with three level noises: (a) Case 1; (b) Case 2; (c) Case 3; (d) Case 4.
Example 2: Consider a three-span beam structure as shown in Figure . The structure has 24 elements and 25 nodes and its length is . The cross section of the beam is square, and its size is
. Axial displacements of all nodes are ignored. Thus, every node has 2 DOFs except four constrained nodes. The two intermediate nodes are only constrained by the vertical direction, and each of them has 1 DOF. The total number of structural DOFs is 44. The material and geometric parameters of each element are as follows: Young’s modulus
, Poisson’s ratio
, density
, length
, and second moment of area
. Four damage cases are considered, as shown in Table .
Table 2. Damage cases in Example 2.
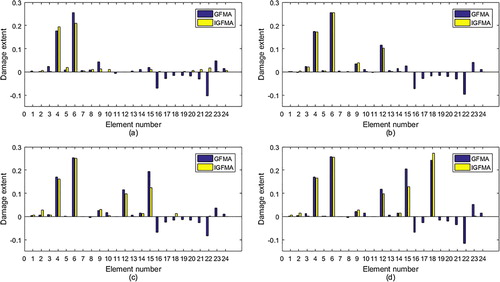
In this example, damage locations and extents are achieved by using first two frequencies and corresponding mode shapes. Calculated results of GFMA and IGFMA are listed in Figure . It can be observed that GFMA produces negative entries with larger absolute value. It also gives the misjudgement for element 23 for the first and last cases. These two shortcomings are overcome by the present method.
Figure 7. Calculated results for four damage cases in Table : (a) Case 1; (b) Case 2; (c) Case 3; (d) Case 4.
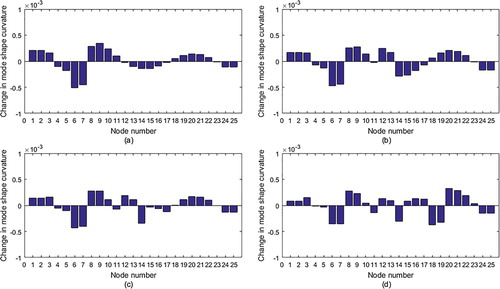
Our proposed method is also compared with the mode shape curvature method. Figure gives changes in mode shape curvatures of every node for all damage cases in Table . It can be seen that the mode shape curvature method does not work well.
Figure 8. Mode shape curvatures for all damage cases in Table : (a) Case 1; (b) Case 2; (c) Case 3; (d) Case 4.
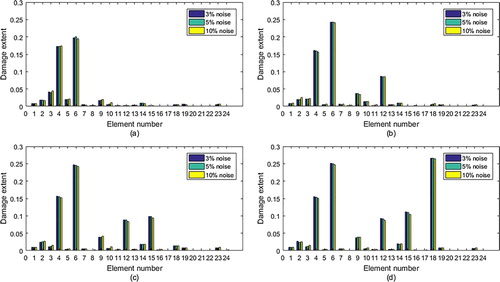
The IGFMA has been carried out in the noise environment. The method of imposing the noise and the noise level are the same as those in Example 1, see Equations (26) and (27). For every noise level, 1000 calculations have been done by the IGFMA. Then, the mean value vector for 1000 calculated damage extent vectors are computed. Figure gives mean value vectors for all damage cases in Table . It can be seen that the IGFMA can also work for these three noise levels.
Figure 9. Calculated results for four damage cases in Table with three level noises: (a) Case 1; (b) Case 2; (c) Case 3; (d) Case 4.
From these two examples, it can be observed that our proposed method can successfully identify the damaged locations, even in the presence of noise. In addition, the damage extent is simultaneously achieved. Our method is superior to the GFMA and mode shape curvature method.
6. Conclusions
The IGFMA is presented for structural damage detection problem. It is based on the GFM. The boundedness of the damage extent is considered and a BLS model is used. Thus, damage extents calculated by our method are all between 0 and 1. This is consistent with the fact. In addition, the perturbation theory of LCP is utilized to derive the error bound of two solutions calculated by the IGFMA using natural frequencies and corresponding mode shapes without and with noise. Part of our result (Theorem 4.1) can be applied to other detection approaches related to the BLS problem, so that the error bound of two solutions calculated by the corresponding approach using the measured data without and with noise can also be achieved.
The proposed method has been verified by numerical experiments with different damage scenarios. The calculated results show that the method can exactly find locations and extents of damage elements using only a few frequencies and mode shapes. This is an advantage of our method. When the data is with noise, our method also work. Compared with the GFMA and mode shape curvature method, our approach can achieve more accurate results and reduce the number of misjudgements. The future work is to generalize the proposed method to damage detection problem with incomplete mode shapes.
Disclosure statement
No potential conflict of interest was reported by the authors.
Additional information
Funding
References
- Shih HW, Thambiratnam DP, Chan THT. Vibration based structural damage detection in flexural members using multi-criteria approach. J Sound Vib. 2009;323:645–661. doi: 10.1016/j.jsv.2009.01.019
- Gomes GF, Mendez YAD, da Silva Lopes Alexandrino P, et al. The use of intelligent computational tools for damage detection and identification with an emphasis on composites-a review. Compos Struct. 2018; 196:44–54. doi: 10.1016/j.compstruct.2018.05.002
- Li J, Li ZG, Zhong HX, et al. Structural damage detection using generalized flexibility matrix and changes in natural frenquencies. AIAA J. 2012;50:1072–1078. doi: 10.2514/1.J051107
- Yang JP, Li PZ, Yang YF, et al. An improved EMD method for modal indentification and a combined static-dynamic method for damage detection. J Sound Vib. 2018;420:242–260. doi: 10.1016/j.jsv.2018.01.036
- Feng DM, Feng MQ. Computer version for SHM of civil infrastructure: from dynamic response measurement to damage detection – a review. Eng Struct. 2018;156:105–117. doi: 10.1016/j.engstruct.2017.11.018
- Zhang WS, Du ZL, Sun G, et al. A level set approach for damage identification of continuum structures based on dynamic responses. J Sound Vib. 2017;386:100–115. doi: 10.1016/j.jsv.2016.06.014
- Wang XJ, Yang HF, Qiu ZP. Interval analysis method for damage identification of structures. AIAA J. 2010;48:1108–1116. doi: 10.2514/1.45325
- Vahedi M, Khoshnoudian F. Sensitivity-based damage identification method for structures exposed to ground excitation. Inverse Probl Sci Eng. 2018;26:1404–1431. doi: 10.1080/17415977.2017.1406487
- Yu L, Zhu JH, Yu LL. Structural damage detection in a truss bridge model using fuzzy clustering and measured FRF date reduced by principle component projection. Adv Struct Eng. 2013;16:207–217. doi: 10.1260/1369-4332.16.1.207
- Guo J, Wang L, Takewaki I. Frequency response-based damage identification in frames by minimum constitutive relation error and sparse regularization. J Sound Vib. 2019;443:270–292. doi: 10.1016/j.jsv.2018.11.020
- Link RJ, Zimmerman DC. Structural damage diagnosis using frequency response functions and orthogonal matching pursuit: theoretical development. Struct Control Health Monit. 2015;22:889–902. doi: 10.1002/stc.1720
- Lin RM, Ng TY. Applications of high-order frequency response functions to the detection and damage assessment of general structural systems with breathing creaks. Int J Mech Sci. 2018;148:652–666. doi: 10.1016/j.ijmecsci.2018.08.027
- Pandey AK, Biswas M, Samman MM. Damage detection from changes in curvature mode shapes. J Sound Vib. 1991;145:321–332. doi: 10.1016/0022-460X(91)90595-B
- Cao MS, Radzienski M, Xu W, et al. Identification of multiple damage in beams based on robust curvature mode shapes. Mech Syst Signal Process. 2014;46:468–480. doi: 10.1016/j.ymssp.2014.01.004
- Yan WJ, Ren WX. Closed-form modal flexibility sensitivity and its application to structural damage detection without modal truncation error. J Vib Control. 2014;20:1816–1830. doi: 10.1177/1077546313476724
- Seyedpoor SM, Montazer M. A damage identification method for truss structures using a flexibility-based damage probability index and differential evolution algorithm. Inverse Probl Sci Eng. 2016;24:1303–1322. doi: 10.1080/17415977.2015.1101761
- Lu ZR, Wang L. An enhanced response sensitivity approach for structural damage identification: convergence and performance. Int J Numer Methods Eng. 2017; 111:1231–1251. doi: 10.1002/nme.5502
- Hadjian Shahri AH, Ghorbani-Tanha AK. Damage detection via closed-form sensitivity matrix of modal kinetic energy change ratio. J Sound Vib. 2017; 401:268–281. doi: 10.1016/j.jsv.2017.04.039
- Hosseinzadeh AZ, Amiri GG, Razzaghi SAS. Model-based identification of damage from sparse sensor measurements using Neumann series expansion. Inverse Probl Sci Eng. 2017;25:239–259. doi: 10.1080/17415977.2016.1160393
- Cui HY, Xu X, Peng WQ, et al. A damage detection method based on strain modes for structures under ambient excitation. Measurement. 2018;125:438–446. doi: 10.1016/j.measurement.2018.05.004
- Bernagozzi G, Mukhopadhyay S, Betti R, et al. Output-only damage detection in buildings using proportional modal flexibility-based deflections in unknown mass scenarios. Eng Struct. 2018;167:549–566. doi: 10.1016/j.engstruct.2018.04.036
- Dahak M, Touat N, Kharoubi M. Damage detection in beam through change in measured frequency and undamaged curvature mode shape. Inverse Probl Sci Eng. 2019;27:89–114. doi: 10.1080/17415977.2018.1442834
- Ghadimi S, Kourehli SS. Multi cracks detection in Euler-Bernoulli beam subjected to a moving mass based on acceleration responses. Inverse Probl Sci Eng. 2018;26:1728–1748. doi: 10.1080/17415977.2018.1430145
- Hosseinzadeh AZ, Razzaghi SAS, Amiri GG. An iterared IRS technique for cross-sectional damage modelling and identification in beams using limited sensors measurement. Inverse Probl Sci Eng. 2019;27:1145–1169. doi: 10.1080/17415977.2018.1503259
- Dinh-Cong D, Vo-Duy T, Ho-Huu V, et al. Damage assessment in plate-like structures using a two-stage method based on modal strain energy change and Jaya algorithm. Inverse Probl Sci Eng. 2019;27:166–189. doi: 10.1080/17415977.2018.1454445
- Fu YZ, Liu JK, Wei ZT, et al. A two-step approach for damage identification in plates. J Vib Control. 2016;22:3018–3031. doi: 10.1177/1077546314557689
- Yang Z-B, Chen X-F, Xie Y, et al. Hybrid two-step method of damage detection for plate-like structures. Struct Control Health Monit. 2016;23:267–285. doi: 10.1002/stc.1769
- Li J, Wu BS, Zeng QC, et al. A generalized flexibility matrix based approach for structural damage detection. J Sound Vib. 2010;329:4583–4587. doi: 10.1016/j.jsv.2010.05.024
- Pandey AK, Biswas M. Damage detection in structures using changes in flexibility. J Sound Vib. 1994;169:3–17. doi: 10.1006/jsvi.1994.1002
- Yang QW, Liu JK. Damage identification by the eigen parameter decomposition of structural flexibility change. Int J Numer Methods Eng. 2009; 78:444–459. doi: 10.1002/nme.2494
- Ashory MR, Masoumi M, Jamshidi E, et al. Using continuous wavelet transform of generalized flexibility matrix in damage identification. J Vibroeng. 2013;15:512–519.
- Masoumi M, Jamshidi E, Bamdad M. Application of generalized flexibility matrix in damage identification using imperialist competitive algorithm. KSCE J Civil Eng. 2015;19:994–1001. doi: 10.1007/s12205-015-0224-4
- Katebi L, Tehranizadeh M, Mohammadgholibeyki N. A generalized flexibility matrix-based model updating method for damage detection of plane truss and frame structures. J Civil Struct Health Monit. 2018;8:301–314. doi: 10.1007/s13349-018-0276-5
- Golub GH, Van Loan CF. Matrix computations. 4th ed. Baltimore: The Johns Hopkins University Press; 2013.
- Horn RA, Johnson CR. Topics in matrix analysis. Cambridge: Cambridge University Press; 1991.
- Calamai PH, More JJ. Projected gradient methods for linearly constrained problems. Math Program. 1987; 39:93–116. doi: 10.1007/BF02592073
- Lawson CL, Hanson RJ. Solving least square problems. Philadelphia (PA): SIAM; 1995.
- Bjorck A. Numerical methods in matrix computation. Heidelberg: Springer; 2015.
- Murty K. Linear complementarity, linear and nonlinear programmming. Berlin: Helderman; 1988.
- Cottle RW, Pang JS, Stone RE. The linear complementarity problem. Boston: Academic Press; 1992.
- Chen XJ, Xiang SH. Perturbation bounds of P-matrix linear complementarity problems. SIAM J Optim. 2008;18:1250–1265. doi: 10.1137/060653019
- Shi ZY, Law SS, Zhang LM, Structural damage detection from modal strain energy change. ASCE J Eng Mech. 2000;126:1216–1223. doi: 10.1061/(ASCE)0733-9399(2000)126:12(1216)
Appendix
Proof
Proof of lemma 4.4
It is easy to verify that the BLS problem (21) is equivalent to following quadratic programming problem:
In Lemma 4.1, let
, the conclusion is achieved.
Proof
Proof of theorem 4.1
By Lemma 4.1, there exit such that
is the solution of LCP
,
. From Lemma 4.3, we have
Proof
Proof of theorem 4.2
For cases without and with noise, from (17), two right hands of our proposed method are related to following two matrices, respectively.
Thus,
where is given in Equation (25).
By Equation (19), two right hands for cases without and with noise are and
, respectively. By the property of vec operation, i.e. Equation (5), we have
By Theorem 4.1, we have