?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
In this article, for a degenerate parabolic equation we study an inverse problem for restoration of source temperature from the information of final temperature profile. The uniqueness of this inverse problem is first established by taking an integral transform and using Liouville's theorem (complex analysis). With aids of an integral identity, a Lipschitz stability for the inverse problem is further constructed. Finally, several numerical experiments are presented to show the accuracy and efficiency of the algorithm.
1. Introduction and main results
Throughout this paper, assuming T is a given positive number and ρ is known as a -function, we study a one-dimensional parabolic equation degenerating at the boundary of the space domain, namely
(1)
(1) with suitable boundary condition which will be given later. We suppose that the degenerate coefficient
satisfies the following conditions:
(2)
(2) The study of such degenerate parabolic equation was initially motivated by some physical and financial mathematics models. For example, in the heat transfer, the thermal conductivity coefficient
is usually related to the structure of the material, density and other factors. The lower the value of
, the stronger its heat resistance. So if the value of
on the boundary x = 0 is so small, then the model (Equation1
(1)
(1) ) can be regarded as an approximation of this case, which indicates the ability to resist heat transfer. We refer to e.g. Buchot and Raymond [Citation1], Martinez et al. [Citation14], Oleinik and Samokhin [Citation15] for motivating examples of a Crocco-type equation coming from the study of the velocity field of a laminar flow on a flat plate. The well known Black–Scholes equation is such the case where the degenerate parabolic boundary degeneracy occurs at the boundary (see e.g. Egger and Engl [Citation8] and Jiang and Tao [Citation12]).
In Equation (Equation1(1)
(1) ), the term
is called the source term and it is crucial to know or determine the coefficient f. However, usually this term cannot be directly measured due to the mixing of the effects of several factors, which requires one to use inverse problems to identify these quantities by involving additional information that can be observed or measured practically. In this paper, our main concern is:
Problem 1.1
Consider the degenerate parabolic equation (Equation1(1)
(1) ) with the following initial condition
(3)
(3) and boundary condition
(4)
(4) Determine the unknown source f from the final state observation
,
.
Problems of this type have important applications in several fields of applied science and engineering. For example, f usually describes the medium properties of generating heat source or heat sink in thermology. For recovering the source term, sometimes we have to measure the final state of the solution u since it is difficult to obtain the information of the solution at the early stage of the diffusion processes.
As is known, inverse source problems for classical parabolic equations are well studied in the literature. Here we do not intend to give a complete list of references, and one can consult Choulli and Yamamoto [Citation5], Hasanov and Slodika [Citation10], Isakov [Citation11] and Rundell and Colton [Citation16] for example. However, to the best of the authors' knowledge, the works concerned with inverse degenerate problems are quite few in contrast with the non-degenerate case. In Cannarsa et al. [Citation4], the Carleman estimate with singular weight function was established for (Equation1
(1)
(1) ) with
, from which an inverse source problem with addition boundary data was discussed. Similarly, we refer to Tort [Citation18] where the Lipschitz stability results in inverse source problems for the degenerate parabolic equations was established by the global Carleman estimates. We refer to Deng et al. [Citation6] and Rao et al. [Citation20] for theoretical and numerical treatments on determining the source term in (Equation1
(1)
(1) ). [Citation6] reconstructed the source by a numerical algorithm on the basis of the conjugate gradient method. In [Citation20], an iteration scheme of the Landweber type is applied to handle the numerical solution of the inverse problem. We also refer to Deng and Yang [Citation7] and Tort and Vancostenoble [Citation19] for the coefficient inverse problems, and refer to Yang and Deng [Citation21] for the backward problem for the degenerate parabolic equation. For other topics of degenerate parabolic equations, e.g. the null controllability, we may refer the reader to Cannarsa et al. [Citation2,Citation3] and the references therein.
In this paper, for the degenerate parabolic equation (Equation1(1)
(1) ), we show that in the case where ρ is only t-dependent and smooth enough, the spatial component can be uniquely determined from the final overdetermination. We have
Theorem 1.1
Assume is positive for any
. Let
and suppose u solves Equation (Equation1
(1)
(1) ) with initial-boundary conditions (Equation3
(3)
(3) ) and (Equation4
(4)
(4) ). Then
in
implies
in
.
By the above theorem, we can further see that when the data have some perturbations, the source term must have corresponding changes.
Theorem 1.2
Under the same assumptions in Theorem 1.1, we suppose that , i = 1, 2 are two pairs of solutions of our inverse source problem correspondingly to data
i = 1, 2. Then
Here the norm will be given in Section 3.
For proving Theorem 1.1, several technical lemmas for this degenerate parabolic equation are needed, so we collect them in Sections 2.1 and 2.2. Preparing all necessities, say, Lemmas 2.2 and 2.3, by Liouville's theorem (complex analysis) we will finish the proof of Theorem 1.1 in Section 2. In the following Section 3, an integral identity is to be put forward with which the stability in Theorem 1.2 can be constructed via a suitable topology. In Section 4, an iteration thresholding method based on the Tikhonov regularization is designed to obtain the numerical solution for our inverse source problem, and some typical numerical experiments are tested to be verified the validity of the iteration scheme. Finally, concluding remarks are given in Section 5.
2. Proof of Theorem 1.1
In this section, we will set up notations and terminologies, review some of standard facts on the functional analysis and give the proof of Theorem 1.1.
2.1. Weighted Sobolev spaces and Hardy inequality
In this part, we introduce a weighted Sobolev spaces and a Hardy-type inequality which play an important role in the proof of our inverse source problem as well as the regularity estimates for the solution to Equation (Equation1(1)
(1) ) with the initial-boundary conditions (Equation3
(3)
(3) ) and (Equation4
(4)
(4) ).
In addition to (Equation2(2)
(2) ), we suppose that the degenerate coefficient
satisfies the following conditions:
such that
for every
.
If
, there exist m>0 and
such that for every
, we have
For example, satisfies the above conditions. Under these assumptions on the degenerate coefficient
, the boundary condition (Equation4
(4)
(4) ) can be rephrased as follows:
(5)
(5)
Remark 2.1
We point out that the functional framework in which the problem is well posed depends on whether or
. We distinguish the two following cases: I.
, the weakly degenerate case at 0; II.
, the strongly degenerate case at 0.
We introduce the following weighted Sobolev space related to the degenerate coefficient :
which is a Hilbert space with the scalar product
We define the unbounded operator A :
by
where
will be given later.
Definition 2.1
Weak degeneracy
For , we define
(6)
(6) and we let
(7)
(7)
Definition 2.2
Strong degeneracy
For , we let
(8)
(8) We define
as follows
(9)
(9)
Thus, in the case of , if
, then u satisfies the Dirichlet boundary condition
and in the case
, every
satisfies the Neumann boundary condition
and the Dirichlet boundary condition
. Moreover, the operator A is the infinitesimal generator of a strongly continuous semigroup
on
. Consequently, we have the following well-posedness result (see, e.g. Futouhi and Salimi [Citation9, Theorem 14]).
Proposition 2.1
Let ρ be given in and
. For all
Equation (Equation1
(1)
(1) ) with the initial-boundary conditions (Equation3
(3)
(3) ) and (Equation5
(5)
(5) ) has a unique solution
.
Moreover, we have the following Hardy-type inequality of the solution in the framework of weighted Sobolev spaces .
Lemma 2.1
Hardy-type inequality, e.g. [Citation9, Remark 20]
Let we have
where the constant C>0 depending only on
and α.
2.2. Estimates under frequency domain
In this part, we will show several useful lemmas which are mainly concerned with the estimates of the solution of Equation (Equation1(1)
(1) ) with initial-boundary conditions (Equation3
(3)
(3) ) and (Equation5
(5)
(5) ) under frequency domain. For this, we multiply both sides of Equation in (Equation1
(1)
(1) ) by
with
, and integrate from 0 to T to derive
Noting that
, from integration by parts, we find
(10)
(10) where
(11)
(11)
Lemma 2.2
Let and
be a sufficiently small and fixed constants. Assuming the function
is positive in
. Then there exists a positive constant
such that the following inequality
is valid for any
.
Proof.
We will prove the above inequality holds true in either of the following two cases.
Case 1 .
Case 2 .
In Case 1, by integration by parts we represent as follows
For
, by a direct calculation, we find
The choice of s, say,
implies that
(12)
(12) which can be further used to derive that
Let us turn to evaluating
. For this, a direct calculation derives
hence that
finally that
Moreover, by the inequality
,
, we see that
Combining all the above estimates, we find
Now for sufficiently large
, then
is also sufficiently large in view of (Equation12
(12)
(12) ). Consequently there exists a constant
such the estimate
provided that
with K>0 is a sufficiently large constant.
Finally, in Case 1, that is, with sufficiently large K>0, we have
Moreover, noting that
implies
, we further see that
which derives that
Next, we evaluate
in Case 2, that is, the case when s lies in
. By taking δ small enough, we are led to
We first rewrite
as follows
hence that
where
. Finally, we obtain
where the constant
is only dependent on
. Moreover, for
, one can easily check that
therefore, we have
Collecting all the above estimates we finish the proof of the lemma.
Lemma 2.3
Assume is positive for any
. Let
and suppose u solves Equation (Equation1
(1)
(1) ) with initial-boundary conditions (Equation3
(3)
(3) ) and (Equation4
(4)
(4) ). Then the function
which is defined in (Equation11
(11)
(11) ) can be estimated as follows
(13)
(13)
Proof.
We denote as the conjugate of the complex valued function
. Then multiplying
on both sides of Equation (Equation10
(10)
(10) ), and taking integral on
lead to
Here we omitted the x in
and
when no confusion can arise. Integration by parts yields
where
The real part of
can be represented as follows:
(14)
(14) while the imaginary part is
(15)
(15) Now in the case of
, where
will be chosen later, we find from (Equation14
(14)
(14) ) that
which combined with Lemma 2.1 yields
By the Hölder inequality, we have
therefore
that is,
Now we choose ϵ being small enough so that
, then
Let us turn to the case of
, from the definition of
, it follows that
Then Lemma 2.2 derives
It remains to consider the case of
, where
is sufficiently small. In view of (Equation15
(15)
(15) ), we see that
Then
2.3. Proof of Theorem 1.1
As a direct application of the estimates in the above subsection, we will give a proof of Theorem 1.1.
Proof
Proof of Theorem 1.1
Since and
are analytic in
, and hence
is a holomorphic function in
removing the zero points of
, where
is arbitrarily fixed. However, from hyperthesis
, Lemma 2.3 and Riemann's theorem (see, e.g. [Citation17]) guarantee that all the singularities of the function
are removable, and then this function can be regarded as an analytic function in
and is bounded on
. Thus the Liouville theorem (see, e.g. [Citation17]) implies that the analytic function
must be independent of s, that is, there exists a constant
depending on ϕ such that
,
.
Now we take the parameter s be real number and we claim that must be zero by letting
in
. Indeed, by integration by parts, we find that
We estimate the part
, s>0, as follows
Here
will be chosen in the following. From Proposition 2.1, we see that for any
, there exists
such that
for any
. Therefore,
It remains to evaluate
. By noting
, a direct calculation yields
Collecting all the above estimates, we finally obtain
which implies
We must have
since
can be arbitrarily small.
Since is independent of s, these two estimates for
and
imply that the constant
is zero, which further implies
,
by noting
can be arbitrarily chosen. Consequently
where
if
and
vanishes outside of
, which implies
in
due to the uniqueness of the Laplace transform, and hence
in
. We complete the proof of the theorem.
Remark 2.2
Here we should mention that this kind of inverse source problem in the non-degenerate cases has been well studied thanks to the eigensystem of the elliptic operator. We do not know if the Fourier expansion can also perform well in dealing with our case. In fact, the traditional eigenfunction expansion argument requires the symmetry of the equation, and also the nonsingular coefficients are needed. However, our method based on the integral transform has no special requirements for the structure of the equation, except that the coefficient must be time independent.
3. Proof of Theorem 1.2
In this section, following the arguments used in Li and Yamamoto [Citation13], a Lipschitz stability for determining the source magnitude will be established.
3.1. An integral identity
For proving the second main result, we will give an integral identity with aid of an adjoint problem, which reflects a corresponding relation of varied of the unknown source functions with changes of the initial-boundary values and additional observations.
Lemma 3.1
Consider
the solution of (Equation1
(1)
(1) ) with initial and boundary conditions given by (Equation3
(3)
(3) ) and (Equation4
(4)
(4) ), and
. Then it follows that
(16)
(16) where
denotes a solution of a suitable adjoint problem with input data
.
Proof.
Denote , and note that
and
both satisfying Equation (Equation1
(1)
(1) ), initial-boundary value (Equation3
(3)
(3) ) and (Equation4
(4)
(4) ), we have
(17)
(17) with initial and boundary conditions (Equation3
(3)
(3) ) and (Equation4
(4)
(4) ).
By smooth test function multiplying two sides of Equation (Equation17
(17)
(17) ), and integrating on
, we obtain
Integration by parts yields
Substituting into the boundary conditions (Equation3
(3)
(3) ) and (Equation4
(4)
(4) ), and choosing
as a solution of the following adjoint problem:
(18)
(18) with boundary value (Equation4
(4)
(4) ) and controllable inputs
, we can complete the proof of the lemma.
3.2. Construction of stability
By the above established identity (Equation16(16)
(16) ), we will construct a stability with a suitable topology. For this purpose, noting to the identity (Equation16
(16)
(16) ), we first define a bilinear form
in terms of ρ by
(19)
(19)
We then define a functional via:
(20)
(20) where
is the solution to the adjoint system (Equation18
(18)
(18) ) with (Equation4
(4)
(4) ) and
. It is not difficult to check that the functional
is a semi-norm on
. Indeed, from the bilinearity of
, it follows that
and the triangle inequality
From Theorem 1.1 and the integral identity (Equation16
(16)
(16) ), we conclude that
implies f = 0. We then see that
is a norm on
. Then by the integral identity (Equation16
(16)
(16) ) and applying Schwartz inequality, we can easily prove Theorem 1.2.
Proof
Proof of Theorem 1.2
By the integral identity (Equation16(16)
(16) ), applying the Schwartz inequality, we see that
We finish the proof of the theorem.
4. Numerical simulation
In this section, we are devoted to developing an effective numerical method for the numerical reconstruction of the unknown source in the domain from the addition data u in
.
4.1. Iterative thresholding algorithm
We discuss Equation (Equation1(1)
(1) ) with initial and boundary values (Equation3
(3)
(3) ) and (Equation4
(4)
(4) ) and we write its solution of problem (Equation1
(1)
(1) ) as
in order to emphasize the dependency on the unknown function f. Here and henceforth, we set
as the true solution to our inverse source problem (1.1), and by using noise contaminated observation data
in
, we carry out numerical reconstruction. Here
satisfies
with the noise level δ.
In the framework of the Tikhonov regularization technique, we propose the following output least squares functional related to our inverse source problem
(21)
(21) where
is the regularization parameter.
Now we intend to calculate the Fréchet derivative of the objective functional
for finding a minimizer. For an arbitrarily fixed direction
, a direct calculation implies
where
denotes the Fréchet derivative of
in the direction g, and the linearity of (Equation1
(1)
(1) ) immediately yields
from which we further derive
(22)
(22)
Remark 4.1
It is not applicable to find the minimizer of the functional Φ directly in terms of the above formula of the Fréchet derivative of . Indeed, in the computation for
, one should solve system (Equation1
(1)
(1) ) for
with g varying in
, which is undoubtedly quite hard and computationally expensive.
We introduce the adjoint system of (Equation1(1)
(1) ) to reduce the computational costs for the Fréchet derivatives, that is, the following system for a backward differential equation
(23)
(23) We write the solution of (Equation23
(23)
(23) ) as
, and similar to the argument used in the above section, we further treat the first term on the right-hand side of (Equation22
(22)
(22) ) as
implying
This suggests a characterization of the solution to the minimization problem (Equation21
(21)
(21) ).
Lemma 4.1
The function is a minimizer of the functional
in (Equation21
(21)
(21) ) only if it satisfies the variational equation
(24)
(24) where
solves the backward problem (Equation23
(23)
(23) ) with the control input
.
We can obtain the iterative thresholding algorithm by adding to both sides of (Equation24
(24)
(24) ) and rearranging the equation (Equation24
(24)
(24) ) as follows
(25)
(25) where M>0 is a tuning parameter for the convergence, it suffices to choose
(26)
(26) where
denotes the operator norm of an operator under consideration and the operator A is defined as follows.
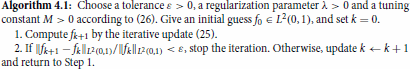
Based on the above discussion, now we propose the following iterative thresholding algorithm for the reconstruction of the unknown source term.
Remark 4.2
As can be seen from (Equation25(25)
(25) ), for computing
at each iteration step, one only needs to solve the forward problem (Equation1
(1)
(1) ) once for
and the backward problem (Equation23
(23)
(23) ) once. Therefore, the numerical implementation of Algorithm 4.1 is easy and computationally cheap.
4.2. Numerical experiments
In this part, we set T = 1 and ,
, and apply the iterative thresholding algorithm established in the previous subsection to numerically recovery the unknown source term. We carry out several test numerical experiments to check the performance of the reconstruction method.
We divide the space-time region into
equidistant meshes. First we set the tolerance parameter
, M = 1,
, initial guess
and test the performance of the algorithm with the following examples.
Example 4.1
In the first numerical experiment, we take
| (A) |
| ||||
| (B) |
| ||||
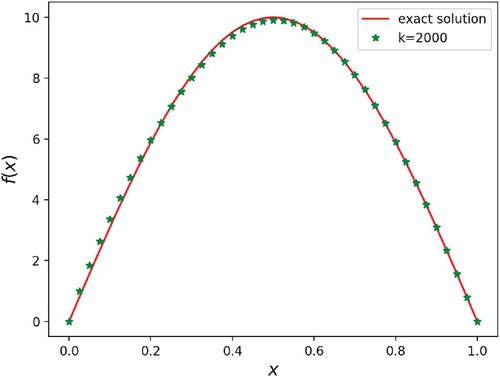
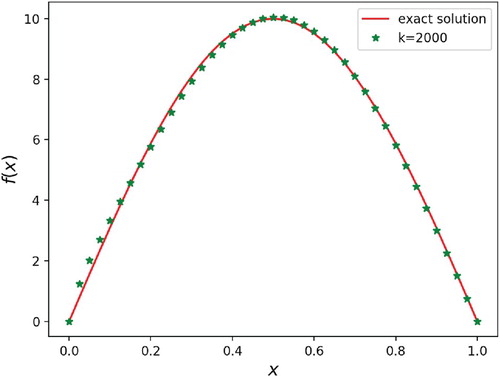
Figures and show the reconstruction results with diffusion coefficients and
. It can be easily seen that the source term can be recovered very well after 2000 iterations. The relative error between the reconstructed source and the true source is less than
.
In the following examples, we consider the noisy data generated in the form
where rand
denotes the uniformly distributed random number in
and the noisy levels are
and
.
Example 4.2
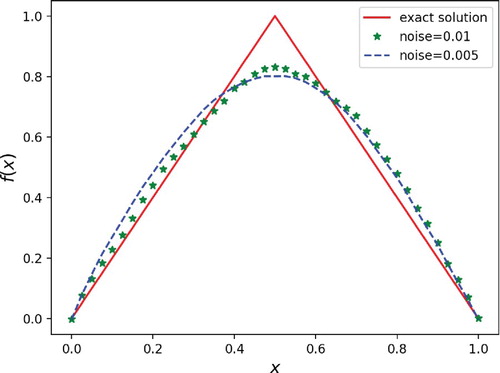
We consider numerical experiment with noise contaminated observation data.
| (A) |
| ||||
| (B) |
| ||||
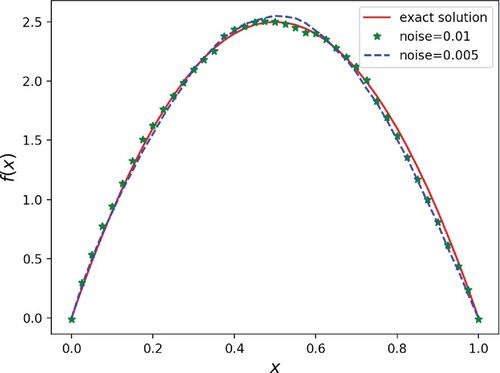
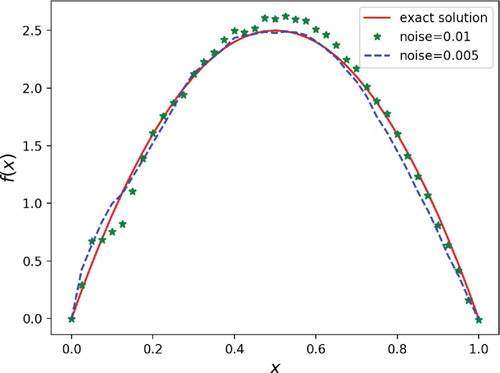
In Figure , the source term is obtained after k = 1073 iteration steps, and the relative error of the reconstructed solution of the inverse source problem is less than . In Figure , the iteration steps k = 2000 and the relative error is less than
. Moreover, we can also see that the degeneracy on boundary may produce a relatively large impact on the reconstruction results. It is not difficult to find that the recovered curve for the case
is better than that of the case
, particularly near the boundaries. It is not hard to understand because the diffusion coefficient
has much more degeneracy than
at the boundary x = 0.
Similarly, the reconstruction of from the noisy data
is also performed.
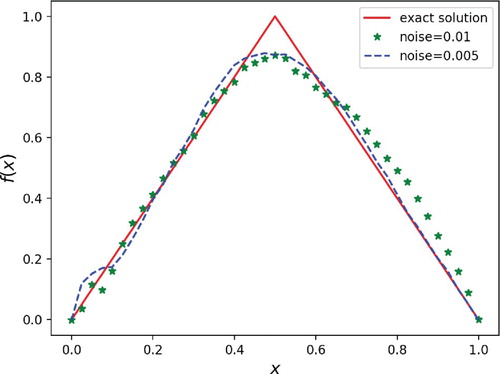
Example 4.3
We consider numerical experiment with non-differentiable source.
| (A) |
| ||||
| (B) |
| ||||
The results are shown in Figures and , where the noisy levels and
. In Figures and , after the iteration steps k = 3000, the source is recovered with the relative error less than
and
respectively.
Remark 4.3
Figures – and the relative errors indicate the efficiency and accuracy of the proposed Algorithm 4.1 for reconstructing the unknown source term. However, it should be mentioned here that owing to the poor regularity of the target function, the reconstruction results are not as well as those of the smooth case in the previous examples.
5. Concluding remarks
In this paper, we considered the inverse problem in reconstructing the source term for the degenerate parabolic equations from the final observation. We first introduced the Hardy type inequality in the framework of weighted Sobolev spaces. We transferred the degenerate equation into a degenerate elliptic one by using finite Laplace transform. As a direct application of the Hardy inequality, we showed that the source term can be uniquely determined from the final state of the solution by the Liouville theorem. By using the integral identity, we further verified the Lipschitz continuous dependency of the source with respect to the final data of the solution with given topology. We should mention that compared with classical parabolic equations, the main difficulty for degenerate equations lies in the degeneracy of the principle coefficients which may lead to the corresponding solution has no sufficient regularity, even if the initial value and the coefficients are sufficiently smooth functions. There will be a challenge if the degenerate equation has flux. Moreover, in the proofs of our results, we need the assumption that all the coefficients are only x-dependent. It will be more interesting and challenging to consider what happens with the properties of the solutions in the case where the coefficients are both t- and x -dependent. It will be also interesting to consider the stability of the inverse source problem if in
is not valid. For example,
.
In the numerical aspect, we reformulated the inverse source problem as an optimization problem with Tikhonov regularization. After the derivation of the corresponding variational equation, we characterized the minimizer by employing the associated backward degenerate parabolic equation, which results in the iterative method. Then several numerical experiments for the reconstructions were implemented to show the efficiency and accuracy of the proposed Algorithm 4.1. Here we should mention that formula (Equation24(24)
(24) ) for finding the minimizer of problem (Equation21
(21)
(21) ) is not suitable for f which is not vanished on the boundary. Indeed, for deriving Algorithm 4.1, the homogeneous boundary condition of the solution v to the backward problem was assumed. It will be interesting to derive the iteration scheme without assuming this homogeneous boundary condition on f. The algorithm for the general case remains open.
Acknowledgments
The second author thanks National Natural Science Foundation of China 11801326.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
References
- Buchot JM, Raymond JP. A linearized model for boundary layer equations. Optimal control of complex structures (Oberwolfach, 2000). Basel: BirkhNauser; 2002; p. 3–42. (Internat. Ser. Numer. Math.; 139).
- Cannarsa P, Martinez P, Vancostenoble J. Null controllability of degenerate heat equations. Adv Differ Equ. 2005;10:153–190.
- Cannarsa P, Martinez P, Vancostenoble J. Carleman estimates for a class of degenerate parabolic operators. SIAM J Control Optim. 2008;47:1–19. doi: 10.1137/04062062X
- Cannarsa P, Tort J, Yamamoto M. Determination of source terms in a degenerate parabolic equation. Inverse Probl. 2010;26:105003. (20pp) doi: 10.1088/0266-5611/26/10/105003
- Choulli M, Yamamoto M. Generic well-posedness of a linear inverse parabolic problem with diffusion parameters. J Inverse and Ill-Posed Prob. 1999;7(3):241–254.
- Deng ZC, Qian K, Rao XB, et al. An inverse problem of identifying the source coefficient in a degenerate heat equation. Inverse Probl Sci Eng. 2015;23(3):498–517. doi: 10.1080/17415977.2014.922079
- Deng ZC, Yang L. An inverse problem of identifying the coefficient of first-order in a degenerate parabolic equation. J Comput Appl Math. 2011;235(15):4404–4417. doi: 10.1016/j.cam.2011.04.006
- Egger H, Engl HW. Tikhonov regularization applied to the inverse problem of option pricing: convergence analysis and rates. Inverse Problems. 2005;21:1027–1045. doi: 10.1088/0266-5611/21/3/014
- Fotouhi M, Salimi L. Null controllability of degenerate/singular parabolic equations. J Dyn Control Syst. 2012;18(4):573–602. doi: 10.1007/s10883-012-9160-5
- Hasanov A, Slodička M. An analysis of inverse source problems with final time measured output data for the heat conduction equation: A semigroup approach. Appl Math Lett. 2013;26(2):207–214. doi: 10.1016/j.aml.2012.08.013
- Isakov V. Inverse parabolic problems with the final overdetermination. Commun Pure Appl Math. 1991;44(2):185–209. doi: 10.1002/cpa.3160440203
- Jiang LS, Tao YS. Identifying the volatility of underlying assets from option prices. Inverse Probl. 2001;17:137–155. doi: 10.1088/0266-5611/17/1/311
- Li G, Yamamoto M. Stability analysis for determining a source term in a 1-D advection-dispersion equation. J. Inv. Ill-posed Problems. 200614(2):147–155. doi: 10.1515/156939406777571067
- Martinez P, Raymond JP, Vancostenoble J. Regional null controllability of a linearized Crocco-type equation. SIAM J Control Optim. 2003;42:709–728. doi: 10.1137/S0363012902403547
- Oleinik AO, Samokhin VN. Mathematical models in boundary layer theory. Chapman and Hall/CRC; 1999.
- Rundell W, Colton DL. Determination of an unknown non-homogeneous term in a linear partial differential equation, from overspecified boundary data. Applicable Anal. 1980;10(3):231–242. doi: 10.1080/00036818008839304
- Rudin W. Real and complex analysis. Singapore: Tata McGraw-Hill Education; 1987.
- Tort J. Determination of source terms in a degenerate parabolic equation from a locally distributed observation. C R Acad Sci Paris, Ser I. 2010;348:1287–1291. doi: 10.1016/j.crma.2010.10.031
- Tort J, Vancostenoble J. Determination of the insolation function in the nonlinear sellers climate model. Ann I H Poincare-AN. 2012;29:683–713. doi: 10.1016/j.anihpc.2012.03.003
- Rao XB, Wang YX, Qian K. Numerical simulation for an inverse source problem in a degenerate parabolic equation. Appl Math Modelling. 2015;39:23–24. S0307904X15001687. doi: 10.1016/j.apm.2015.03.016
- Yang L, Deng ZC. An inverse backward problem for degenerate parabolic equations. Numer Meth for Partial Differ Equ. 2017;33:1900–1923. doi: 10.1002/num.22165