Abstract
Although human trafficking for sexual exploitation is a frequently discussed area in current research, especially on the way that human traffickers control their victims, a recurrent problem is the lack of empirical basis. The present study examines control methods (or conditions) used against 137 victims of human trafficking for sexual exploitation. A multidimensional scaling analysis (smallest space analysis (SSA-I)) of 23 control methods (and conditions) derived from a content analysis of police files from the Netherlands revealed three distinct forms of control. These could be interpreted in terms of Canter’s Victim Role model that has been the basis for differentiating offending styles in other violent interpersonal offences. Further analysis showed a relationship between these control styles and different types of prostitution. The three Victim as Object, Victim as Vehicle and Victim as Person modes are consistent with different control methods identified in previous research.
Nearly 11,000 human beings were forced to work in the prostitution industry in the Netherlands in 2010 (10.917)Footnote1, a figure that can only be regarded as an approximation, as it is estimated that the Dutch police are only aware of 7.3% of the possible victims of human trafficking for sexual exploitation.Footnote2 Problems with estimating the actual numbers derive from the fact that not every crime is reported to the police, actually only 50% of the victims report this crime,Footnote3 and therefore, a considerable number of crimes remain undetected. Definitional problems only add to this as there has been considerable debate concerning the term ‘human trafficking’, since it is often confused with human smuggling.Footnote4 Human trafficking is, according to article 3 of the United Nations Protocol of Trafficking (2000):
The recruitment, transportation, transfer, harbouring or receipt of persons, by means of the threat or use of force or other forms of coercion, of abduction, of fraud, of deception, of the abuse of power or of a position of vulnerability or of the giving or receiving of payments or benefits to achieve the consent of a person having control over another person, for the purpose of exploitation. Exploitation shall include, at a minimum, the exploitation of the prostitution of others or other forms of sexual exploitation, forced labour or services, slavery or practices similar to slavery, servitude or the removal of organs.
KleemansFootnote7 further proposes that human trafficking can be divided into three distinctive stages: recruitment (source country), transportation (transit countries) and exploitation (country of destination). In general, the Netherlands can be regarded as a country of destination, the main reason being that prostitution has been legalised in this country.Footnote8 Since October 2000, the brothel ban is also lifted in the Netherlands, which means that prostitutes can be legally exploited in privately held places as long as the owner has a local license, the person is not forced to work as a prostitute and the prostitute has reached the age of majority.Footnote9 As the focus in the present research is solely on the Netherlands, only the exploitation stage is considered. The methods of control employed by the human traffickers in this last stage are, however, dependent on the applied recruitment and transportation methods.Footnote10 To what extent these stages influence each other and if a relationship among them can be found is unclear and warrants research. The different control methods used in the exploitation stages are, however, frequently discussed in previous research.
Control methods of victims of human trafficking for sexual exploitation
In the last decade, several researchersFootnote11 have looked into control methods used by human traffickers against sexual exploitation victims. HughesFootnote12 describes four different control methods: the confiscation of travel documents, the use of violence, the threat to harm family members and a financial dependency upon the human trafficker. KellyFootnote13 expands this view in two different ways. Firstly, through a specification of the isolation method into constant surveillance or confinement and the method of threat against left behind family members, but also the recognition, reinforced by traffickers, of their illegal status, secondly, via an addition of two control methods: shame and humiliation and a cultural-related psychological coercion. These methods are generalised by Smit and BootFootnote14 into violence, threat of violence, extortion, fraud and deception. Logan et al.Footnote15 demonstrated that the control methods could be distinguished into four different themes. Firstly, fear which includes fear of physical and sexual violence, fear of deportation, fear of legal problems, lack of trust in the legal system and a general fear. Secondly, the lack of knowledge about alternatives in where victims are unaware of the available services in the destination country do not know their own rights, do not see themselves as victims or do not have any other alternative. Thirdly, the isolation of the victims which includes a lack of social support, absence of transportation methods, a language barrier and a non-awareness of culturally appropriate services. Finally, the use of physical or psychological confinement. The physical form assigns the holding in captivity of the victim and the physiological way is through the feelings of shame.
The main problems that arise from the above studies are, however, the lack of empirical basis as the findings are frequently reinforced by ideological and political influenced sources.Footnote16 A more research-oriented study, based upon empirical data from different police files, is one conducted by the national police in the Netherlands.Footnote17 They distinguish four different forms of psychological bounding of the victim, i.e. deception (e.g. working circumstances), abuse of the vulnerable position of the victim and having ascendency over the victim (e.g. living regulated by pimp), other direct coercive methods (e.g. religious coercion) and other indirect coercive methods (e.g. shameFootnote18). Although there is a big step taken by using empirical data for research into these methods, the operational application is not directly discussed and the gap between research and practice is therefore still existent.Footnote19 Besides, the methods are analysed individually, whereas these cannot be seen in isolation of other behaviour or contexts.Footnote20
Distinct control styles
Within this Victim Role model for differentiating offending, CanterFootnote21 suggests that offending behaviour is fundamentally an interpersonal activity. The meaning and significance of the offender’s actions is derived from the interaction with the victim. Canter’s Victim Role model of offending styleFootnote22 emphasises ideas about the central control and empathy-deficit components of this interpersonal transaction. According to CanterFootnote23 different forms of control tendency and empathy-deficit combine to produce different interpersonal styles in which three distinct roles are assigned to the victim: Victim as Object, Victim as Vehicle and Victim as Person.
The Victim as Object role draws together the direct possession and subjugation form of control with an empathy deficit that takes the form of the objectification of the victimFootnote24. In the Victim as Object role, the offender sees the victim as having very little, if any, human significance or emotions and relies on physical forms of control.
The Victim as Vehicle role integrates an abusive form of control with an exploitative approach to the victim that is based on a lack of empathy for his/her suffering.Footnote25 In the Victim as Vehicle role, the victim is a vehicle for the expression of the offender’s desires and/or anger and the control is mainly emotional or psychological.
The Victim as Person roleFootnote26 is one in which there is recognition that the victim is human, a person. This role draws together the coercive approach to control with a form of empathy deficit based upon a general undervaluing of the individual.Footnote27 This combination is integrated by a narrative in which the victim, although recognised as completely human, remains a person to be handled and the control is achieved through manipulation.
Canter and YoungsFootnote28 have shown that the Victim Role model distinguishes offending style variants with a number of different violent interpersonal offences, from rape, to stalking and even sexual homicide. This general framework has also been recently replicated by Youngs and IoannouFootnote29 in their study of client-related violence against female street sex workers. It is therefore expected that this framework may also be appropriate in differentiating the different control methods used by human traffickers, as these are a victim-offender interaction that appears to be reinforced with psychological and sociological features.Footnote30
Type of prostitution
Victims of human trafficking for sexual exploitation in the Netherlands appear, according to the most recent estimates,Footnote31 to be mainly active in the window prostitution, followed by escort, hotel escort, club and private houses and least operative in the Chinese beauty branch. Window prostitution is a legalised form of prostitution in the Netherlands in where the prostitute rents a room next to a public street and recruits customers from behind a window. Escort is a type of prostitution in where the prostitute visits customers in places other than hotels, whereas hotel escort only encapsulates prostitution that takes place in a hotel. If a prostitute works in a club or private house the customers can visit them at that place and if they work in the Chinese beauty branch the place is commonly known as a massage parlour, hairdresser or beauty salon, but there is also the (illegal) opportunity to purchase sex in these places.Footnote32
Victims of human trafficking in these types of prostitution are subjected to different forms of control and manipulation. It seems that victims in the hotel and window prostitution have more debts than victims in the escort. The window prostitution appears to deviate from the other types of prostitution in the number of victims that have a love relationship with the human trafficker and the frequency of use or threat of violence. In both methods of control, the frequency is higher for window prostitution than for the other types of prostitution.Footnote33
Present study
As mentioned previously, the Victim Role model has been examined and found to be effective in providing a framework of offending styles across a number of different interpersonal crimes such as rape, stalking and serial murderFootnote34 and most recently violent attacks against female sex workers.Footnote35 The present study therefore explores the potential of this framework for distinguishing control methods (or conditions) of victims of human traffickers for sexual exploitation. The focus is on human trafficking for sexual exploitation only, as this is the most common form of human trafficking.Footnote36 In addition, the relationship between the control methods (or conditions) and the type of prostitution is also explored.
Method
Sample
The sample consisted of 137 victims (120 females and 17 males) of human trafficking originating from various countries [Romania (n = 60), Hungary (n = 32), Czech Republic (n = 9), Slovakia (n = 7), Brazil (n = 5), The Netherlands (n = 5), Latvia (n = 4), Poland (n = 4), Thailand (n = 4), Bulgaria (n = 2), Columbia (n = 1), Cuba (n = 1), Croatia (n = 1), Ukraine (n = 1), Russia (n = 1)]. The mean age was M = 23.7 years (SD = 4.4; range = 17–39 years). The victims were exploited in the following types of prostitution: window prostitution (49.6%), escort (35%), club or private houses (13.9%) and hotels (1.5%).
Procedure
Data originated from a data file of 37 completed criminal investigations of 13 different police regions in the Netherlands that took place between 2007 and 2011. These data were originally gathered for the ‘Criminaliteitsbeeldanalyse’ 2012 (Crime picture analysisFootnote37), which is a nationwide report that is published to describe organised crime (e.g. drugs trafficking, human trafficking) in the Netherlands every other year. The first step was to identify which actions could be used to differentiate the manners in which a victim was kept under control. Using the content analysis approach adopted in numerous previous studies,Footnote38 23 control methods (or conditions) were identified and coded in terms of the presence or absence of each variable.
Previous research has demonstrated that content analysis any more refined than presence/absence dichotomies is likely to be unreliable.Footnote39 Police files are namely not collected for research purposes, but recorded for police and court use.Footnote40 Full variable descriptions are given in Appendix.
Analysis
The data were analysed using smallest space analysis (SSA-I).Footnote41 SSA allows a test of hypotheses concerning the co-occurrence of every variable with every other variable. In essence, the null hypothesis is that the variables have no clear interpretable relationship with each other. SSA is a non-metric multidimensional scaling procedure based upon the assumption that the underlying structure, or system of behaviour, will most readily be appreciated if the relationship between every variable and every other variable is examined.
SSA represents the co-occurrence of variables, in our present study control methods (or conditions), as distances in a geometrical space. The SSA program computes association coefficients between all variables. It is these coefficients that are used to form a spatial representation of items with points representing variables. Each point in the space represents a distinct characteristic of the events under study, such as whether the victim was physically abused. The closer any two points are to each other on the spatial configuration, the higher their associations with each other. Similarly, the farther away from each other any two points are, the lower their association with each other.
A number of studies of criminal actions have found such MDS models to be productive.Footnote42 The particular power of SSA-I comes from its representation of the rank order of co-occurrence as rank orders of the distances in the geometric space (the use of ranks leads to it being considered non-metric MDS).
The measure of co-occurrence used in the present study was Jaccard’s coefficient. Jaccard’s coefficient calculates the proportion of co-occurrences between any two variables as a proportion of all occurrences of both variables. This has now become the standard coefficient used with this type of data since the initial study by Canter and HeritageFootnote43. Its great advantage is that it only calculates co-occurrence across recorded events. Any absence of activity is not used in the calculation. This means it only draws upon what was known to have happened and does not take account of what was not recorded to have happened. With this sort of data, such lack of recording can be in error, whereas noting that something occurred is less likely to be inaccurate.
To test hypotheses, an SSA configuration is visually examined to determine the patterns of relationships between variables and identify thematic structures. Control methods (or conditions) with similar underlying themes are hypothesised to be more likely to co-occur than those that imply different themes. These similarly themed control methods (or conditions) are therefore hypothesised to be found in contiguous locations, i.e. the same region of the plot. The hypothesis can therefore be tested by visually examining the SSA configuration. The coefficient of alienationFootnote44 indicates how well the spatial representation fits the co-occurrences represented in the matrix. The smaller the coefficient of alienation the better is the fit, i.e. the fit of the plot to the original matrix. However, as Borg and Lingoes Footnote45 emphasise, there is no simple answer to the question of how ‘good’ or ‘bad’ the fit is. This will depend upon a combination of the number of variables, the amount of error in the data and the logical strength of the interpretation framework.
In summary, the SSA was used to explore the co-occurrences of these control methods (or conditions) and allowed for the testing of the hypothesis that they can be differentiated into themes.
Results
Control methods (or conditions) in the present study
The most frequent control method used against victims of human trafficking for sexual exploitation in the present study was the victim living at a place owned or rented by a member of the criminal group which occurred in 86.1% of the sample. The isolation of the victims was also apparent in limited social contacts (13.9%) and language barriers as many of them did not speak the commonly spoken languages in the Netherlands; over three-quarters of the victims (78.1%) did not speak Dutch, almost half of the victims did not speak any German (45.3%) and a quarter did not speak English (26.3%). Threat of physical violence or actual physical violence was reported in about half of the sample, 44.5% and 43.8%, respectively. Almost 32% of the victims had their travel documents confiscated and many of them were financially dependent on their trafficker as either their earnings were taken (34.3%) or they had an outstanding debt with a member of the criminal group (18.2%). Constant surveillance was apparent in the sample with 56.9% accompanied to work and 24.1% accompanied when leaving work. Lack of knowledge of alternatives was another control method/condition utilised as 23.4% of the sample did not have any knowledge of her/his own rights. Psychological control was evident via psychological abuse (16.1%), witnessing of physical abuse (9.5%) and threats to family members (6.6%). Shame and humiliation via threatening either to place pictures of the victim with explicit material on the Internet or tell others what job she/he was doing only occurred in 8.8% and 3.6% of the sample. Nine (6.6%) of the victims were sexually abused or threatened with sexual abuse by a member of the criminal group and, interestingly, more than one-fifth of the victims (21.9%) had an intimate relationship with a member of the group. All frequencies are presented in .
Table 1. Frequencies of variables.
Smallest space analysis (SSA) of control methods (or conditions)
shows the distribution of the 23 control methods (or conditions) for the 137 cases on the two-dimensional SSA. The coefficient of alienation of 0.24 indicates a reasonable fit of the spatial representation of the co-occurrences of the behaviours. The regional hypothesis states that items that have a common theme will be found in the same region of the SSA space. To test the hypothesised framework of control methods (or conditions) against victims of human trafficking for sexual exploitation, it was therefore necessary to examine the SSA configuration to establish whether different themes of offender–victim interaction could be identified.
Figure 1. Two-dimensional smallest space analysis (SSA) plot of control methods (or conditions) with regional interpretation (coefficient of alienation = 0.24).
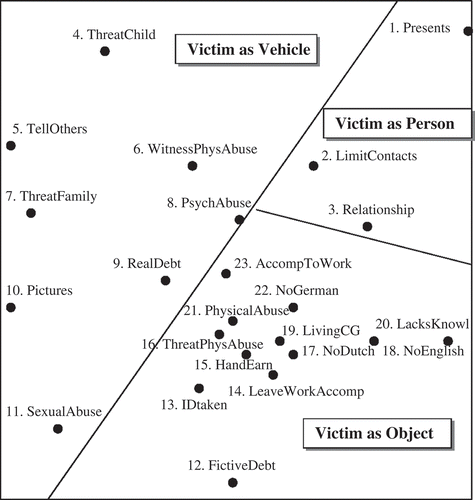
As can be seen in , visual examination of the SSA plot confirmed that it can be partitioned into three distinct regions or themes, according to the role the offender assigns to the victim (Victim as Object, Victim as Vehicle and Victim as Person) identified previously for other types of offences.Footnote46
The victim as object role
As it can be seen from , there is a region that contains a number of control methods (or conditions) concerned with physical control either through use or threat of violence, confinement, surveillance or isolation. Twelve control methods (or conditions) characterise the victim as object offending style: victim having a fictive debt (12), victim’s travel documents are confiscated (13), victim is accompanied by a member of the criminal group when leaving work (14), victim’s earnings are controlled (15), victim is threatened with physical abuse (16), the victim does not speak Dutch (17), the victim does not speak English (18), the victim is staying at a place owned or rented by a member of the criminal group (19), the victim is not aware of her/his rights (20), the victim is subjected to physical violence (21), the victim does not speak German (22) and the victim is accompanied to the workplace (23).
It is apparent from these behaviours that the control is expressed as the direct possession and subjugation of the victim.Footnote47 The offender has a complete lack of empathy for the victim, a lack of awareness of their humanity that produces objectification of the victim. He fails to understand him/her as a human being and makes every effort to control and restrain his victim, treating her/him in an impersonal manner as an object. He attempts to impose the control directly and will inflict physical harm to force this.Footnote48
Further analysis revealed that there was a significant difference between those victims involved/not involved in window prostitution and their scores in the victim as object theme, t(135) = –4.80, p < .001, with those victims involved in window prostitution scoring higher in the Victim as Object theme (M = 6.04, SD = 2.23) than those not involved in window prostitution (M = 4.26, SD = 2.10). On the contrary, victims involved in escort scored lower in the Victim as Object Theme (M = 4.10, SD = 2.23) than those not involved in escort (M = 5.71, SD = 2.21) and this difference was significant, t(135) = 4.03, p < .001.
The Victim as Vehicle Role
In the top left side of the SSA plot, eight variables together form a second control style: a member of the criminal group threatens the child of the victim (4), the victim is threatened that they will tell others what kind of work he/she does (5), the victim has been a witness of physical abuse of other victims (6), a member of the criminal group threatens family members of the victim (7), the victim is psychologically abused (8), the victim has an outstanding debt with a member of the criminal group (9), the victim is threatened that they will place pictures on the Internet revealing that the victim is a prostitute (10) and the victim is sexually abused or threatened with sexual assault by a member of the criminal group (11).
This emotional or psychological control apparent in this region can be explained in terms of Canter’sFootnote49 ‘Victim as Vehicle’ role. There is a lack of concern or compassion for the suffering of the victim that manifests in some form of exploitation.Footnote50 The offender is simply using the victim to express his own desires and/or anger. The sexual activity or the threat of sexual activity is exploitative and demeaning in line with Canter’s general assertion of an exploitative approach to relating to others within the Vehicle role.Footnote51
When assessing the relationship of this theme and types of prostitution, a significant difference was found t(135) = 2.25, p < .05, with those victims not involved in escort scoring higher (M = .88, SD = 1.28) than those victims involved in escort (M = .46, SD = .87) in this theme. In addition, the scores in this theme were higher both for those victims involved in hotel and window prostitution in relation to those who were not involved in this theme, but the differences did not reach statistical significance.
The Victim as Person Role
In the top right-hand section of the plot, three variables form a distinct control style. The victim receives presents from a member of the criminal group (1), the victim is limited or monitored in his/her social contacts (2) and the victim has an intimate/personal relationship with a member of the criminal group (3).
Here the control is achieved through manipulation. The victim is undervalued as an individual, apparent in a preparedness to take advantage of them as people.Footnote52 This style emerges out of a distorted approach to interpersonal relations in which the offender recognises the human feelings of his victim, he realises that he is dealing with a real individual, but his normal human interactions are typically abusive and coercive in nature.Footnote53 These behaviours are a distorted attempt to reduce the interpersonal distance with the victim corresponding to the victim as person role within Canter’sFootnote54 Victim Role Framework.Footnote55
Interestingly, a significant difference was found, t(135) = –11.47, p < .001, with those victims involved in club/private house prostitution scoring higher (M = 1.00, SD = .00) in this theme than those not involved in club/private house prostitution (M = .39, SD = .63). In addition, victims involved in both escort and window prostitution scored lower in this theme, but the differences did not reach statistical significance.
Testing the framework/distribution of cases across Victim Role Themes
Each of the 137 cases in the data set was individually examined to ascertain whether it could be assigned to a Victim Role control style on the basis of the variables which occurred during each case. Every case was given a percentage score for each of the three major roles, reflecting the proportion of Victim as Object, Victim as Vehicle and Victim as Person variables that occurred during the attack. The criterion for assigning a case to a particular theme was that the dominant theme had a greater number of violent behaviours/variables present than the sum of the other two themes. The percentage of intratheme occurrences was used rather than the actual number of occurrences, because the actual total number of control methods (or conditions) in each theme varied.
A case was considered to be a hybrid between two themes if it contained the same proportion of variables for each of those themes. A case was not classified as either pure type or hybrid if it contained less than a third of the variables in any theme or if it contained equal numbers of variables from more than two themes or simply when there was no predominant theme.
Using this system (see ), a total of 85.4% (117 out of 137 cases) could be classified as pure types either exhibiting a dominantly Victim as Object, Victim as Vehicle, or Victim as Person control style. Breaking these 117 cases down, it could be seen that 102 (74.4%) followed a Victim as Object style, 12 (8.8%) a Victim as Person style and only three (2.2%) a Victim as Vehicle style. Eight cases (5.8%) were hybrids, which were a combination of Victim as Object and Victim as Person styles. Finally, only 12 cases (8.8%) could not be classified. These results would seem to suggest that the themes as revealed by the SSA (see ) are a very good representation of different styles in control methods (or conditions) of victims of human trafficking for sexual exploitation.
Table 2. Distribution of cases across Victim Role model control/offending styles.
Discussion
The present study identified distinct control methods of victims of human trafficking for sexual exploitation that parallel the styles of offending identified across a range of other offences including rape, stalking, serial killingFootnote56 and violent attacks against female street sex workers.Footnote57 These control/offending styles were distinguished on the basis of the different forms of interpersonal transaction with the victim identified within Canter’sFootnote58 Victim Role model. Furthermore, different types of prostitution were found to be related to different Victim Roles.
Most of the cases fell clearly within either the Victim as Object, the Victim as Vehicle or the Victim as Person modeFootnote59, highlighting the importance of differentiation among control methods and allowing the integration of a number of previously identified control methods in the literature.
The most dominant form of control methods (or conditions), occurring in almost three-quarters of the cases, was one in which the victim was assigned the role of an Object which interestingly was also the dominant role assigned by violent clients to female street sex workers in a previous study.Footnote60 The Victim as Object mode draws together the direct possession and subjugation form of control with an empathy deficit that takes the form of the objectification of the victim.Footnote61 In the Victim as Object role, the offender sees the victim as having very little, if any, human significance or emotions. The Victim as Object role relies on physical forms of control. In the context of control methods of victims of human trafficking for sexual exploitation, this was revealed in the use or threat of physical violence, confinement, surveillance and isolation of the victim. Victims had their travel documents confiscated, were deceived into believing that they had a debt with one of the traffickers, were not aware of their rights, were always accompanied by a trafficker from and to work, their earnings were controlled, were staying at a place owned by a trafficker and did not have any means of communications, with most experiencing language barriers.
The control methods of confiscation of travel documents,Footnote62 the use of violence,Footnote63 financial dependency upon the trafficker,Footnote64 constant surveillance,Footnote65 confinementFootnote66, threat of violenceFootnote67, deception,Footnote68 lack of knowledge about alternatives,Footnote69 language barriers,Footnote70 abuse of the vulnerable position of the victim and having ascendency over the victim (e.g. living regulated by pimpFootnote71) have all been identified by previous research and clearly are methods associated with the Victim as Object mode. The control methods (or conditions) in this region were found to be associated with window prostitution but not escort, club and private house or hotel prostitution. They were only associated with escort prostitution but in a negative manner, i.e. victims who did not work as escorts scored higher on this theme in relation to victims who did work as escorts. This accords with previous findings that show that the frequency of violence or the threat of violence is associated with window prostitutionFootnote72 emphasised by the fact that many see women involved in window prostitution as objects.
The Victim as Vehicle control style was one in which the focus was on emotional and psychological control. There is a lack of concern or compassion for the suffering of the victim that manifests in some form of exploitation.Footnote73 These control methods (or conditions) are readily understood as the expression of the offender’s symbolically targeted anger and desires, which define the Vehicle role for Canter.Footnote74 The sexual activity or the threat of sexual activity is exploitative and demeaning. In the context of control methods of victims of human trafficking for sexual exploitation, the victim’s family was threatened, the victim was threatened with exposure either by telling others what job she/he did or by placing explicit images on the Internet, psychologically abused, witnessed physical abuse of other victims and had suffered or threatened with sexual abuse and had an outstanding debt with one of the traffickers. The threat to harm family members,Footnote75 shame and humiliationFootnote76 and psychological abuseFootnote77 have all been identified by previous research and clearly are methods associated with the Victim as Vehicle mode.
The only statistically significant relationship found here was a negative relationship between escort prostitution and the Victim as Vehicle style meaning that victims who did not work as escorts scored higher on this theme in relation to victims who did work as escorts. ResearchFootnote78 has shown that victims in hotel and window prostitution have more debts than escort victims. This was also identified in the present study as the scores in the Victim as Vehicle theme were higher for both victims involved in hotel and window presentation compared to those who were not involved in this theme. The differences did not reach statistical significance though.
Finally, the Victim as Person style is one where the control is achieved via manipulation. The Victim as Person role draws together a coercive rather than physical force approach to control with a form of empathy deficit based upon a general undervaluing of the individual.Footnote79 The victim, although recognised as completely human, remains a person to be handled and manipulated. In the context of control methods of victims of human trafficking for sexual exploitation, the victim received presents from a trafficker, was limited in his/her social contacts and was in an intimate/personal relationship with one of the traffickers. This ‘love relationship’ has previously been identified by Bottenberg et al.Footnote80 Interestingly, this style was found to be associated with club/private house prostitution and, contrary to previous researchFootnote81 that showed that those victims that have a love relationship with a human trafficker work in window prostitution, in the current sample, this was not the case; both escort and window prostitution scored lower in this theme, but the differences did not reach statistical significance.
To the authors’ knowledge, this is the first attempt to empirically differentiate control methods (or conditions) of victims of human trafficking for sexual exploitation in the exploitation stage and examine how these relate to different types of prostitution. These findings have both significant theoretical implications in our understanding of the control methods (or conditions) used by traffickers and the crime in general and has the potential of an improvement of the responses towards it with more effective trafficking investigationsFootnote82 but also enhance the understanding of legal professionals and their reactions to this form of crime with more appropriate punishment of the offender. Moreover, determining the best treatment plan for victims can be another area of potential application. The selection of after-care appears to be crucial, as the physical and psychological consequences of these circumstances can be significant (e.g. tiredness, loss of weight, STD, depression, drugs and alcohol addiction, PTSDFootnote83). Finally, in terms of prevention strategies, an empirically substantiated image of a trafficked person in terms of combined control methods could be used in government televised and other campaigns warning potential victims. Relating control methods to victim background characteristics would further strengthen these strategies.
Although the present study identified a framework for differentiating control methods of victims of human trafficking for sexual exploitation, a number of limitations should be noted. The findings are based upon police files, which encapsulate only the human beings that are categorised as victims by the police. It is, however, less likely that the women and men in the most serious forms of slavery and sexual exploitation are reached.Footnote84 The results are therefore only a conceptualisation of the data that are available to the police. Furthermore, the study did not take into consideration the offender, whereby it is unclear whether the control methods used against the victim are typical for one offender or are the result of a criminal group in total. The sample at the present study was predominantly females with males accounting for 12% of the sample. While this is representation of the number of males in comparison with females in human trafficking for sexual exploitation in the Netherlands (9.8% in Bottenberg et al.Footnote85), the study did not look into gender differences and how this may or not have impacted the findings. Lastly, the results of the present research are only applicable to the sexual exploitation of human trafficking victims in the Netherlands. Other forms of human trafficking and other countries are not described in this study. Further research needs to establish its relevance to a more diverse sample.
Future studies would benefit from using data from other sources as well as conducting interviews with offenders of human trafficking to understand the perpetrator’s point of view, not only to determine whether certain offenders use certain methods of control, but also to provide a better understanding of the motive or drive behind the methods used.
The present study is only the first step in the development of the current model notably through the identification of the variations that exist in the control methods (or conditions) of victims of human trafficking for sexual exploitation. The results of this study contribute to the fight of human trafficking in an indirect manner enhancing our understanding of these control methods (or conditions). While it does not address prevention methods directly, it does provide a good framework for them.
Notes
1. Bottenberg, et al., Seksuele Uitbuiting. Criminaliteitsbeeldanalyse Citation2012.
2. See note 1 above.
3. E-Quality, Mensenhandel. Een Genderscan Op De B9-Regeling.
4. Experts Group on Trafficking in Human Beings, Report of the Experts Group; Kelly, Journeys of Jeopardy; and Lee, Human Trafficking.
5. Experts Group on Trafficking in Human Beings, Report of the Experts Group.
6. Kleemans, “Human Smuggling and Human Trafficking.”
7. Kleemans, “Expanding the Domain.”
8. UNODC, Global Report on Trafficking in Persons.
9. Barnett et al., Prostitution; and Daalder, Het Bordeelverbod Opgeheven.
10. Kelly, Journeys of Jeopardy.
11. Hughes, “The ‘Natasha’ Trade”; Kelly, Journeys of Jeopardy; Smit and Boot, “Het Begrip Mensenhandel in De Nederlandse Context”; and Bottenberg et al., Seksuele Uitbuiting. Criminaliteitsbeeldanalyse Citation2012.
12. Hughes, “‘Natasha’ Trade.”
13. See note 10 above.
14. Smit and Boot, “Het Begrip Mensenhandel in De Nederlandse Context.”
15. Logan, “Understanding Human Trafficking.”
16. Weitzer, “Social Construction of Sex Trafficking”; and Zhang, “Beyond the ‘Natasha Story’.”
17. See note 1 above.
18. See note 1 above.
19. Canter, “Tale of Two Cultures.”
20. Salfati and Canter, “Nature of Expressiveness and Instrumentality.”
21. Canter, Criminal Shadows.
22. Canter, Criminal Shadows; and Canter and Youngs, “Sexual and Violent Offenders’ Victim Role Assignments.”
23. See note 21 above.
24. Canter and Youngs, “Sexual and Violent Offenders’ Victim Role Assignments.”
25. See note 24 above.
26. See note 21 above.
27. See note 24 above.
28. See note 24 above.
29. Youngs and Ioannou, “Multivariate Model of Stalking Behaviours.”
30. Hughes, Best Practices to Address the Demand Side.
31. See note 1 above.
32. See note 1 above.
33. See note 1 above.
34. See note 21 above.
35. See note 29 above.
36. See note 8 above.
37. See note 1 above.
38. see Canter and Youngs, Investigative Psychology.
39. Canter and Heritage, “Multivariate Model of Sexual Behaviour”; and Canter and Ioannou, “Multivariate Model of Stalking Behaviours.”
40. Salfati and Dupont, “Canadian Homicide.”
41. Lingoes, “Guttman-Lingoes Non-Metric Program Series.”
42. e.g., Canter and Fritzon, “Differentiating Arsonists”; and Canter and Heritage, “Multivariate Model of Sexual Behaviour”; and Salfati, “Nature of Expressiveness and Instrumentality.”
43. Canter and Heritage, “Multivariate Model of Sexual Behaviour.”
44. Borg and Lingoes, Facet Theory.
45. See note 44 above.
46. See note 21 above.
47. See note 24 above.
48. See note 29 above.
49. See note 21 above.
50. See note 24 above.
51. Canter and Youngs, “Sexual and Violent Offenders’ Victim Role Assignments”; and Youngs and Ioannou, “Multivariate Model of Stalking Behaviours.”
52. See note 24 above.
53. See note 29 above.
54. See note 21 above.
55. See note 24 above.
56. See note 24 above.
57. See note 29 above.
58. Canter, Criminal Shadows; and Canter and Youngs, Investigative Psychology.
59. Canter, Criminal Shadows; Canter and Youngs, Investigative Psychology; and Canter and Youngs, “Sexual and Violent Offenders’ Victim Role Assignments”.
60. See note 29 above.
61. See note 24 above.
62. See note 12 above.
63. Hughes, “‘Natasha’ Trade.”; and Smit and Boot, “Het Begrip Mensenhandel in De Nederlandse Context.”
64. See note 12 above.
65. See note 10 above.
66. Kelly, Journeys of Jeopardy; and Logan, et al., “Understanding Human Trafficking.”
67. Logan, et al., “Understanding Human Trafficking”; and Smit and Boot, Het “Begrip Mensenhandel in De Nederlandse Context.”
68. Bottenberg et al., Seksuele Uitbuiting. Criminaliteitsbeeldanalyse Citation2012; Smit and Boot, “Het Begrip Mensenhandel in De Nederlandse Context.”
69. See note 15 above.
70. See note 15 above.
71. See note 1 above.
72. See note 1 above.
73. See note 24 above.
74. See note 21 above.
75. See note 12 above.
76. Bottenberg et al., Seksuele Uitbuiting. Criminaliteitsbeeldanalyse Citation2012; Kelly, Journeys of Jeopardy; and Logan, et al., “Understanding Human Trafficking.”
77. See note 10 above.
78. See note 1 above.
79. See note 24 above.
80. See note 1 above.
81. See note 1 above.
82. Kelly and Regan, Stopping Traffic; and Parmentier, “Epilogue.”
83. Hughes, “‘Natasha’ Trade”; and Zimmerman et al., Stolen Smiles.
84. Tyldum and Brunovskis, “Describing the Unobserved.”
85. See note 1 above.
Bibliography
- Barnett, L., L. Casavant, and J. Nicol. Prostitution: A Review of Legislation in Selected Countries. Ottawa, CA: Library of Parliament, 2011.
- Borg, I., and J. C. Lingoes. Facet Theory: Form and Content. New York: Springer, 1987.
- Bottenberg, M., J. Valk, M. Kuipers, and L. de Weerd. Seksuele Uitbuiting. Criminaliteitsbeeldanalyse 2012 [Sexual exploitation. Crime picture analysis 2012]. Driebergen: Korps landelijke politiediensten, 2012.
- Canter, D., and R. Heritage. “A Multivariate Model of Sexual Behaviour: Developments in ‘Offender Profiling’ I.” Journal of Forensic Psychiatry 1 (1990): 185–212. doi:10.1080/09585189008408469.
- Canter, D., and D. Youngs. “Sexual and Violent Offenders’ Victim Role Assignments: A General Model of Offending Style.” Journal of Forensic Psychiatry and Psychology 23, no. 3 (2012): 297–326. doi:10.1080/14789949.2012.690102.
- Canter, D. V. Criminal Shadows. London: Harper Collins, 1994.
- Canter, D. V. “A Tale of Two Cultures: A Comparison of the Cultures of the Police and Academia.” In Policing a Safe, Just and Tolerant Society: An International Model, edited by R. Adlam and P. Villiers, 109–121. Winchester: Waterside Press, 2004.
- Canter, D. V., and K. Fritzon. “Differentiating Arsonists: A Model of Firesetting Actions and Characteristics.” Legal and Criminological Psychology 3, no. 1 (1998): 73–96. doi:10.1111/j.2044-8333.1998.tb00352.x.
- Canter, D. V., and M. Ioannou. “A Multivariate Model of Stalking Behaviours.” Behaviormetrika 31, no. 2 (2004): 113–130. doi:10.2333/bhmk.31.113.
- Canter, D. V., and D. Youngs. Investigative Psychology: Offender Profiling and the Analysis of Criminal Action. Chichester: John Wiley and Sons, 2009.
- Daalder, A. Het bordeelverbod opgeheven [The brothel ban lifted]. The Hague: Wetenschappelijk Onderzoek- en Documentatiecentrum, 2002.
- E-Quality. Mensenhandel. Een genderscan op de B9-regeling [Human Trafficking. A Genderscan on the B9-regulation]. The Hague: E-Quality, 2011.
- Experts Group on Trafficking in Human Beings. Report of the Experts Group on Trafficking in Human Beings. Brussels: European Commission Directorate-General Justice, Freedom and Security, 2004.
- Hughes, D. M. “The ‘Natasha’ Trade: The Transnational Shadow Market of Trafficking in Woman.” Journal of International Affairs 53, no. 2 (2000): 1–18.
- Hughes, D. M. Best Practices to Address the Demand Side of Sex Trafficking. Washington, DC: Department of State, 2004.
- Kelly, E. Journeys of Jeopardy: A Review of Research on Trafficking in Woman and Children in Europe. Geneva: International Organization of Migration, 2002.
- Kelly, L., and L. Regan. Stopping Traffic: Exploring the Extent Of, and Responses To, Trafficking in Women for Sexual Exploitation in the UK. London: Great Britain Home Office, Policing and Reducing Crime Unit Research, 2000.
- Kleemans, E. R. “Human Smuggling and Human Trafficking.” In Oxford Handbook on Crime and Public Policy, edited by M. Tony, 409–427. Oxford: Oxford University Press, 2009.
- Kleemans, E. R. “Expanding the Domain of Human Trafficking Research: Introduction to the Special Issue on Human Trafficking.” Trends in Organized Crime 14, no. 2–3 (2011): 95–99. doi:10.1007/s12117-011-9139-8.
- Lee, M. Human Trafficking. Cullompton: Willan Publishing, 2007.
- Lingoes, J. (1973). “The Guttman-Lingoes Non-Metric Program Series.” MA thesis., University of Michigan.
- Logan, T. K., R. Walker, and G. Hunt. “Understanding Human Trafficking in the United States.” Trauma, Violence & Abuse 10 (2009): 3–30. doi:10.1177/1524838008327262.
- Parmentier, S. “Epilogue: Human Trafficking Seen from the Future.” European Journal of Criminology 7, no. 1 (2010): 95–100. doi:10.1177/1477370809347947.
- Salfati, C. G. “The Nature of Expressiveness and Instrumentality in Homicide: Implications for Offender Profiling.” Homicide Studies 4, no. 3 (2000): 265–293. doi:10.1177/1088767900004003004.
- Salfati, C. G., and D. Canter. “Differentiating Stranger Murders: Profiling Offender Characteristics from Behavioural Styles.” Behavioural Sciences and the Law 17, no. 3 (1999): 391–406. doi:10.1002/(SICI)1099-0798(199907/09)17:33.0.CO;2-Z.
- Salfati, C. G., and F. Dupont. “Canadian Homicide. An Investigation of Crime-Scene Actions.” Homicide Studies 10, no. 2 (2006): 118–139. doi:10.1177/1088767906288449.
- Smit, M., and M. Boot. “Het Begrip Mensenhandel in De Nederlandse Context; Achtergronden En Reikwijdte.” Justitiële Verkenningen 7 (2007): 10.
- Tyldum, G., and A. Brunovskis. “Describing the Unobserved: Methodological Challenges in Empirical Studies on Human Trafficking.” In Data and Research on Human Trafficking: A Global Survey, edited by F. Laczko and E. Gozdziak, 17–34. Geneva: International Organization for Migration, 2005.
- UNODC. Global Report on Trafficking in Persons. Vienna: UN.GIFT, 2009.
- Weitzer, R. “The Social Construction of Sex Trafficking: Ideology and Institutionalization of a Moral Crusade.” Politics & Society 35 (2007): 447–475. doi:10.1177/0032329207304319.
- Youngs, D. E., and M. Ioannou. “A Model of Client-Related Violence against Female Street Sex Workers.” Journal of Forensic Social Work 3 (2013): 244–260. doi:10.1080/1936928X.2013.859028.
- Zhang, S. X. “Beyond the ‘Natasha Story’ – a Review and Critique of Current Research on Sex Trafficking.” Global Crime 10, no. 3 (2009): 178–195. doi:10.1080/17440570903079899.
- Zimmerman, C., M. Hossain, K. Yun, B. Roche, L. Morison, and C. Watts. Stolen Smiles: A Summary Report on the Physical and Psychological Health Consequences of Women and Adolescent Trafficked in Europe. London: London School of Tropical Hygiene and Medicine, 2006.
Appendix
Variable Content Dictionary
Presents – The victim received presents from a member of the criminal group.
LimitContacts – The victim is limited or monitored in his/her social contacts by a member of the criminal group.
Relationship – The victim has an intimate relationship with a member of the criminal group.
ThreatChild – A member of the criminal group threatens directly the child of the victim
TellOthers – The victim is threatened by a member of the criminal group that he/she will tell others what kind of work he or she does to others
WitnessPhysAbuse – The victim has been a witness of physical abuse of other victims by a member of the criminal group.
ThreatFamily – A member of the criminal groups threatens directly family members of the victim
PsychAbuse – The victim is psychologically abused by a member of the criminal group.
RealDebt – The victim has an outstanding debt with a member of the criminal group due to payment of e.g. journey, accommodation or food.
Pictures – The victim is threatened by a member of the criminal group that he/she will place pictures on the Internet revealing that the victim is a prostitute
SexualAbuse – The victim is threatened to be assaulted or raped and/or assaulted or raped by a member of the criminal group.
FictiveDebt – The victim is having a fictive outstanding debt with a member of the criminal group due to payment of e.g. journey, accommodation or food.
IDtaken – The victim does not own its own travel documents (i.e. passport or ID card), as it is confiscated by a member of the criminal group.
LeaveWorkAccomp – The victim is accompanied by a member of the criminal group when leaving the work place.
HandEarn – The victim’s earnings are controlled by a member of the criminal group.
ThreatPhysAbuse – Victim is threatened with physical abuse by a member of the criminal group.
NoDutch – The victim does not speak Dutch.
NoEnglish – The victim does not speak English.
LivingCG – The victim is staying at a place that is rented or owned by a member of the criminal group.
LacksKnowl – The victim lacks knowledge of her rights/is not aware of her own status, i.e. being a victim
PhysicalAbuse – The victim is brought in a state of unconsciousness or powerlessness due to the use of force by a member of the criminal group.
NoGerman – The victim does not speak German.
AccompToWork – The victim is accompanied to the workplace by someone of the criminal group.
