ABSTRACT
Using a crime script analysis, this research aims to document how smugglers operate when they traffic arms from the US to foreign countries. Our study is based on an analysis of 66 cases that have been judged by US courts (2008–2017). The criminal activities involved are detailed in a series of distinct scenes, according to Cornish’s theory. Five scripts have been developed, based on the means of transport used by the traffickers: road transport, commercial airlines, postal services, freight transport and crossing the border on foot. Results suggest that most criminals prefer to operate according to an established modus operandi. This commonality suggests that the potential exists for the professionalisation of this criminal activity. Indeed, offenders are likely to maintain it to reduce effort and risk. Complementary sources of information would help to enrich the approach proposed in this study and to address the challenges posed by complex cases.
1. Introduction
Weapons trafficking occurs worldwide and is a major international issue, because such weapons end up being used by criminal organisations and in acts of war, terrorism, crime, smuggling and suicideFootnote1. Weapons trafficking refers to all forms of the illicit transfer of firearms, ammunition, explosive weapons and associated materialsFootnote2. The trafficking of weapons has been described as a four-step process: the possession (with or without previous acquisition), transportation, storage and sale of the productFootnote3.
This article aims at analysing and formalising the trafficking process through the use of crime scripts. The concept of scripts came from cognitive science and was then developed in criminology by Cornish in 1994. In his study, Cornish argued that crime scripts are analytical tools to look at behavioural routines, by considering the offenders as rational individuals. Crime scripting is modelling modus operandi by capturing step by step the actions followed by the offendersFootnote4. Scripts may also be used to decompose a criminal activity into a sequence of events that describe actions before, during and after the commission of a crimeFootnote5. According to Borrion, there are three types of scripts and four levels of abstractionFootnote6. The three types of scripts are ‘potential script’ based on hypothetical sequences of actions, ‘planned scripts’ based on sequences of actions potentially encountered and ‘performed script’ which is based on empirical data. Regarding levels of abstractions, from the lowest to the highest levels, Borrion argues there are respectively ‘tracks’, ‘scripts’, ‘protoscripts’ and ‘metascripts’Footnote7. A script at track level is developed from a case study. ‘Scripts’ are less specific than ‘tracks’, but they provide general characteristics that can be shared by several tracks. At the next level, a protoscript further generalises, clustering several scripts in a specific time or region. Metascript provides a description that, ideally, fits to any script of the offence under analysis.
Scripts can be developed to focus on particular aspects, for example, classifying a crime as a success, an attempt or a failureFootnote8. A breakdown of the steps followed by smugglers could result in intelligence that could assist investigators and forensic scientists by pointing them towards sites where physical and digital traces of criminal activity could be found. Such a process increases the chances of disrupting illegal activity by providing a better understanding of the crime commission processFootnote9.
This study analyses the process of weaponsFootnote10 trafficking using a crime script analysis that draws upon judicial reports produced in the US and on press releases. The objective is to identify the specificities of and similarities between international weapons trafficking cases that originated in the US according to the means of transport selected be the offenders. While crime scripting can be used to analyse the rationale behind crime commission, this explanatory study focuses on the description of the steps taken, without analysing the triggers, facilitators or motivations behind them. In addition, this research focuses on analysing the illegal international sales process that emanates from the US; it does not consider the internal, domestic US market.
2. Literature review
2.1. Weapons trafficking as part of international illicit trade
Illicit trade, of which weapons trafficking is one example, is a complex and multidimensional phenomenon. The demand for weapons emanates from both legal and black markets and from a range of sources. Such sources include terrorist groups, criminal syndicates and individual citizensFootnote11. Illegally procured arms are used for a range of purposes, such as fighting a war, issuing threats or providing protection.
Most of the weapons that are sold illicitly fall into the category of small arms and light weapons (SALW). SchroederFootnote12 has observed that handguns represented 77% of the firearms seized from criminals, drug traffickers and gang members in eight American cities from 2007 to 2012 inclusive. The acquisition of light weapons has been described as a relatively straightforward process, facilitated by the fact that such small arms are available, convenient in terms of transport and cheaper than large-calibre equipmentFootnote13. A study by the UNODCFootnote14 found that pistols in 2016–2017 represented more than 50% of firearms seized in the US. In Europe, pistols, rifles and shotguns are equally seized. In Africa and Asia, the most common seized firearms were shotguns, while rifles were the most confiscated weapons in Oceania.
The trade and use of illegally acquired weapons pose many challenges: They threaten the security of communities and countries, escalate violence and tension into deadly conflicts, and represent a major governance issueFootnote15. McEvoy and HidegFootnote16 have estimated that in 2016 about 210,000 firearms-related violent deaths occurred worldwide. Of these fatalities, 81% were intentional homicides. Firearm-related suicide was excluded in this studyFootnote17. In 2016, 44% of all recorded homicides were perpetrated with firearmsFootnote18. StohlFootnote19 has also stated that weapons trafficking is only one part of a much wider, global shadow economy. In this economy, weapons are used to threaten competitors or as a means of payment for other illicit goods, such as diamonds, drugs and timber, to sellers who wish to acquire weapons.
Small arms are commonly traded and used by traffickers and criminal organisations because of their durability, ease of use, lethality and ease of maintenance. In addition, the small size of such weapons makes them easy to store and hideFootnote20.
The UNODCFootnote21 have identified three arms trafficking methods: trafficking by land, by sea or involving many actors that carry small amounts of arms. The latter method is referred to as ‘ant trafficking’. Ant trafficking is particularly difficult to intercept, because it is multiple, small, discreet and consequently barely detectable. The UNODCFootnote22 has evidence that this technique is being used to traffic arms between the US and Mexico.
Some weapons trafficked from the US are initially legally acquired from gun shops but are then trafficked by a ‘straw man’Footnote23. In fact, Faltas and Chrobok argue that acquiring weapons legally in the US is a relatively easy process, even given the administrative conditionsFootnote24. They also added that the first administrative step is that weapons retailers are subjected to a strict process before being granted marketing authorisationFootnote25. According to Gildea and Pierce, the broker must provide information to obtain an export licence such as the end use, the end user, the commodity, the consignee, the ultimate consignee and the freight forwarder. The type, calibre, quantity, value, brand, model, serial number and user of the weapon(s) are also documentedFootnote26. However, Braga and al commented that such controls do not apply to private transactions between individuals, which might occur at gun shows or other secondary marketsFootnote27. The shortcoming might explain the extent of the weapons trafficking from the US to Mexico, for instance. With no background checks being performed, Ford argues that it is relatively easy for traffickers to acquire weapons on secondary marketsFootnote28. In the Small Arms Survey report, SchroederFootnote29 found that at least 46 countries had been affected by the illegal import of firearms from the US.
Even though it is possible to buy weapons legally in the US, most traffickers opt not to acquire weapons in this way. The preferred manner of illegally transferring arms involve three main forms of subterfuge: legal acquisition followed by illegal retransfer; illegal acquisition through legal channels (including using fake IDs or declaring fictitious written statements) and illegal acquisition through illegal channels (such as theft)Footnote30. Holtom, Pavesi and RigualFootnote31 provided an example of illegal retransfer: When weapons are retransferred from authorised end users to an individual living in a different country or to an unauthorised person, this is a form of ‘illegitimate misappropriation’. This technique is used by traffickers to illegally export weapons worldwideFootnote32. In the 2016 Small Arms SurveyFootnote33, the analysis of 159 US police reports highlighted the modus operandi used by smugglers, from weapons acquisition to routing and transporting weapons to foreign locations. Their results revealed at least two methods of material acquisition (legal or illegal): either in gun shops or on the internet. These results were in part confirmed by Rhumorbarbe et alFootnote34. when they stated that online material acquisition occurred on both the clear web and the dark web. Globally, firearm acquisition seems to rely on ‘a diverse set of illegal pathways, including corrupt licenced dealers, unlicensed sellers, straw purchasers, residential theft, and theft from licenced dealers, common carriers, and firearm manufacturers. Organized, large-scale trafficking exists, but it is not predominant’Footnote35.
There is a lack of knowledge about the mechanics of trafficking from the US. While the global picture of arms trafficking (either worldwide or from the US) is helpful, it mainly relies on national reporting of seizures. For instance, the UNODCsFootnote36 relies on data provided by 81 different countries and they have to work on the assumption that each country is free to share all or part of the available data. However, global reports fail to capture the detailed mechanics of trafficking, including the procedures involved before and after the actual illicit transfer. This lack of knowledge is also due to the complexity of collecting data on weapons traffickingFootnote37. Moreover, the inherent complexity of the international dimension of trafficking also contributes to this shortcomingFootnote38. For example, Gildea and PierceFootnote39 have stated that even when U.S. Customs and Border Protection has the resources to carry out controls, it is possible to examine only about 1% of the merchandise that crosses the borders of the US. Furthermore, weapons smuggling is only one of the illegal activities requiring control by the U.S. Customs and Border Protection.
2.2. The use of crime scripting in European studies
While the amount of research using crime scripts has increase over the last yearsFootnote40, only few studies from Europe have used a crime script approach to analyse small arms trafficking.
De VriesFootnote41 relied on crime scripting to describe ammunition trafficking in the Netherlands. Using information from both the National Collection of Bullets and Cartridge Cases of the Netherlands Forensic Institute (NFI) and 10 interviews with experts, the author created a crime script consisting of five scenes.
The first scene corresponds to ammunition production, the second to ammunition procurement, the third to the transportation, the fourth to the sale and, finally, the fifth scene corresponds to the possession and use of ammunition. In another study, De VriesFootnote42 relied on crime scripting to describe the trade in and the use of converted firearms in the Netherlands. In her study, she used three different sources of information: two completed police investigation, semi-structured interviews with firearms experts of Dutch police forces, and a quantitative analysis on two databases, Firearms Data System and National Collection Bullets and Cartridges. The author created a script consisting of five scenes: Purchase, Conversion, Transportation, Sales & delivery, and Possession & use. Both of De Vries’ scripts are quite similar, except when looking at the second scene.
WilliamsonFootnote43 is one of the few researchers who is authoring projects that rely on crime script analysis to study firearms trafficking from a sociological perspective, which assumes that individuals who take part in firearms trafficking are rational and see the market as an opportunity. Through the analysis of the British National Ballistics Intelligence Service (NABIS) database, open-source data and subcultural case studies, Williamson explored firearms trafficking and the role of ‘criminal armourers’ in particular in England and Wales by using crime scripts. Williamson described armourer as an ‘individual who has either been convicted of a firearm supply offence or who has stored or collected weapons that could potentially be used by criminal individuals’Footnote44. The operating aspects of firearms trafficking in England and Wales (e.g. activities, motivations and modus operandi), the key factors leading a person to start using or trafficking weapons, and the armourer profiles (novice, innocent, potential, professional, ideological, commercial and ‘home’) were described. Trafficking roles (e.g. purchaser, facilitator, courier and custodian) have also been identified. In a subsequent studyFootnote45, these roles and the armourer types were integrated with a global sale/rental network model. Williamson has described a firearm trafficking network as typically requiring an armourer, a custodian, a middleman/purchaser, a facilitator and a courier to deliver weapon(s) to the customer.
The Small Arms Survey study conducted by SchroederFootnote46 described the means of transport used by smugglers and divided them into three categories: land, sea and air. When smuggling by land, traffickers generally use vehicles to cross borders and mostly crossing the border from Mexico into the US. Weapons – or parts of them – as well as ammunition are usually concealed in vehicles (e.g. under the seats or within the structure). Using the U.S. Postal Service and crossing the border on foot are also categorised as transport by land, even if those methods are not as common as crossing borders in vehicles. In fact, traffickers cross the Mexican border on foot in only 2.5% of the cases. Transport by sea requires containers being carried on cargo ships and filled with legal articles to conceal the weapons. Finally, when transporting arms by air, traffickers usually hide the weapons in their luggageFootnote47. This manuscript provides a deconstruction of the main methods of transportation involved in arms trafficking.
3. Methodology
3.1. Data description
This study relies on a dataset provided by Small Arms Survey (SAS)Footnote48. The SAS dataset is based on US court judgements from 2008 to 2017. It includes 162 trafficking cases that have been disrupted by US police officers. These cases were identified following a three-step methodology. First, a SAS researcher reviewed the press release listings on the Office of the US Attorney’s websites to identify trafficking cases. Secondly, for each case, s/he searched for case information on the regional US Attorney Offices’ websites using keyword searches for .justice.gov in Google. No specific filters were applied. Case information originates mostly from judiciary documents (e.g. complaints, indictments and pleas) and press releases, coming from US Attorney’s Offices in 94 federal districts. Finally, s/he excluded cases containing solely domestic trafficking or cases in which the trafficked items were not shipped from or through the United States.
All documents were titled by the defendant’s name and were in PDF format. Complaints typically contain a global description of the case (i.e. name of the defendant, date of the criminal complaint, case number, date of the criminal action, violated Title of the U.S. Code, name and signature of the judge in charge of a case) and an affidavit in support of the arrest warrant. Indictments also contain the name of the defendant, the criminal number, dates of the indictment, dates of the facts, as well as the details of the counts (i.e. the charges against the defendant).
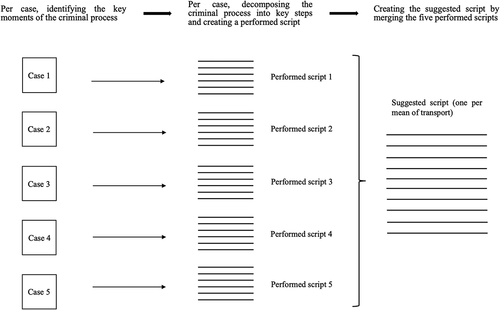
Of the 162 cases, 66 contained a sufficient level of detail for a crime script (see, ). Overall, 176 documents were read, classified according to five means of transport used by traffickers (by road transport, crossing the border on foot, using commercial airlines, using postal services to deliver a package and using freight transports) and analysed. In the first three means of transport (by road transport, crossing the border on foot, using commercial airlines), traffickers transported the material themselves, while for the last two (i.e. using postal services to deliver a package and using freight transports) traffickers required the service of a third-party company. To obtain more information about the cases, additional open-source research (media reports) was conducted online, using a combination of the keywords ‘arms trafficking’ associated with the name of the defendant.
Table 1. Number of cases, classified by categories, used for each mean of transport.
In the 66 cases considered, 188 people were involved, 20 of which were women (10.7%). Background and/or personal information were not analysed because the quantity and the quality of information provided by the documents were not sufficient.
In 42 cases (63.6%) perpetrators had been smuggling weapons for years while in 24 cases (36.4%), documents did not mention any other trafficking attempt. In 34 cases (51.5%), documents described the context of the arrests. In 23 cases (34.8%), authorities arrested traffickers when conducting random searches. The documents studied contained seven (10.6%) investigations that had been conducted by undercover agents. When undercover agents had worked on cases, the level of detail in court documents increased. In 17 cases (25.8%), traffickers were arrested after intelligence had been provided by confidential informants or other institutions (e.g. INTERPOL or EUROPOL). In one case, a transporter was arrested after his ammunitions exploded in a building where police officers were present.
3.2. Crime script analysis
Based on empirical data (performed scripts), this study develops case scripts (tracks). Then, it increases its level of abstraction proposing five planned scripts by means of transportFootnote49: by road (‘Road’), crossing the border on foot (‘Ped’), using commercial airlines (‘Air’), using postal services to deliver a package (‘Post’), using freight transport (‘Freight’).
Crime scripts were used to describe modus operandi for investigators and researchers and to classify data. Crime scripts allowed researchers to identify patterns within some arms trafficking cases. In fact, different traffickers shared the use of similar steps (e.g. the use of the same concealment techniques) even if traffickers were acting independently.
Per mean of transport, we randomly selected five cases from our dataset (see ‘Number of cases used to create a suggested script (one per mean of transport)’, ). Considering the quality of the documents analysed, five cases were informative enough to create one ‘suggested’ script, specific to the identified means of transport. For the ‘Ped’ script, all four cases were analysed. To construct the scripts, each case was carefully read and analysed to identify the main steps of the trafficking process. One step represents one action conducted by, at least, one individual. Then, per case, and according to a specific mean of transport, each step of the criminal process was chronologically decomposed. All steps were described given the information detailed in the documents, creating a performed script at track level. The five performed scripts have been compared between each other in order to identify similarities and differences. As the five performed scripts showed similarities, they were subsequently merged to produce a ‘suggested’ script (see, ). This method has been applied for the five means of transport.
After the creation of the five ‘suggested’ scripts, the other cases (n = 42, see ‘Number of cases used to appreciate the script inclusiveness’, ) were used as a benchmark for considering their inclusiveness. For each of the 42 cases, we decomposed the case by steps and compared them to the steps reported in the suggested scripts following the same methodology as the one described for the creation of the tracks. When the suggested scripts did not encompass some scenes, scripts were adjusted by adding complementary steps. Finally, tables were compiled to summarise the scripts’ scenes and facets.
All scripts were formalised using the same process, whether the case has been carried out by undercover agents or disrupted when authorities conducted random searches. Each case was decomposed into separate scripts, detailing the process of the acquisition, the exportation and the sale of weapons. Each phase of individual script includes different scenes also referred to as steps. For example, scenes could encompass the use of concealment techniques and the concealment of the material within a vehicle.
Then, each scene was classified in subcategories, which described the different facets of the sceneFootnote50. For example, facets could describe the means of transport used by traffickers with – when relevant – the vehicle characteristics such as the brand, category, type of vehicle (e.g. rental vehicle versus personal vehicle), the category of trafficked material (e.g. ammunition, military goggles or small arms), the means of payments and the presence/absence of accomplice and, if relevant, their numbers. Regarding facets encountered in the scripts, we decided to present only the one detected in the dataset.
Then, all these steps were classified based on four of the stages of criminal activity: preparation, pre-activity, activity and post activity. As scripts are a sequence of scenes occurring before, during and after the main crime event, we decided to use respectively the ‘precrime phase’, the ‘crime phase’ and the ‘post-crime phase’. The ‘precrime phase’ regroups both the preparation and the pre-activity stages. It corresponds to all the scenes occurring before the transfer from the US to a foreign country (including e.g. Canada, China, Colombia, Mexico, Philippines, Russia, and Thailand). The actual passage to these destinations – by going through the border – is the ‘crime phase’ (i.e. the scene ‘activity’). The ‘post-crime phase’ is all the scenes that occur after the arrival of the product outside of the US, ranging from the transfer of the arms to re-transfer by the recipient to other persons, to the payment of accomplices (i.e. post-activity scene).
6 report also how often each scene occurs in the 66 analysed cases by percentage. These were calculated with an equal number of cases (within a given script). Some scenes were not encountered in each case, because the offender might have been caught before that scene, or the scene is optional. For example, while some traffickers use concealment methods to hide the weapon in a car or trucks (i.e. within the ‘Road’ script), others do not.
Table 2. Trafficking by road transport (‘Road’) script (n = 18 cases).
Table 3. Trafficking using commercial airlines (‘Air’) script (n = 9 cases).
Table 4. Trafficking by road transport (‘Ped’) script (n = 4 cases).
Table 5. Trafficking using postal services (‘Post’) script (n = 16 cases).
We checked our script’s quality according to six criteria: typology, consistency, context, completeness, precision and uncertaintyFootnote51. These criteria were considered during the scripts construction, which resulted in slight modifications (regarding script consistency and completeness).
4. Results
4.1. Trafficking by road transport (‘Road’)
Two variants of the global script were identified for this mean of transport: ‘self-transport’ and ‘courier’. While both scripts followed the same logic (see, ), the first was characterised by the fact that the transporter was the material buyer, whereas in the ‘courier’ option, accomplices were recruited to cross the border. Eight cases followed the ‘self-transport’ script, and in 10 cases a courier was present. The global crime script corresponded to the integration of both scripts by merging all actors as a ‘transporter’. The distinction is represented by the multifaceted ‘drive to the border’ scene.
Overall, more than 300 weapons were exported, but also tens of thousands of ammunition rounds (ranging from 300 to 65,000 rounds) and handgun bullet magazines (from two to 652 magazines). One to twelve people were involved in trafficking by road. Most cases involved two to three people; however, in three cases seven to twelve people were active. The number of accomplices did not appear to be linked with the extent of the trafficking.
The precrime phase corresponds to scenes 1 to 9 (from the acquisition of a vehicle to traffickers driving to the border). When trafficking by road transport, traffickers acquire the material (scene 3) either online or physically. Often, traffickers buy weapons through typical distribution channels, such as gun shows, gun store or storefront retailers. The acquisition can be either legal or illegal. Detail is lacking on how traffickers paid for the weapons. Among the cases studied, at least three groups paid for weapons in cash.
The storage scene (5) occurs less often in weapons trafficking by car or by truck. This scene is more frequent when accomplices are used. In half of the cases, the trafficked material was concealed (e.g. using foils and tape) while in more than 94.4% of the cases the merchandise was concealed inside the vehicle (e.g. under seats).
Regarding the concealment methods (scenes 7 and 8), even if this scene occurred in half of the cases, traffickers used at least seven different approaches. The material was either wrapped using plastic, foil and tape, or placed inside bags or boxes. Some traffickers obliterated the serial numbers of the weapons. Several parts of the vehicles were used to conceal the material, including engine compartments, the front quarter panels, undercarriage of a vehicle, or the gas tank. Often, personal vehicles were used, including family vehicles, trucks or SUVs. The ‘courier’ script was initially composed of five sub-steps: ‘9a – Transfer the material to the courier’, ‘9b – Deliver the material to courier’, ‘9c – Conceal the material in a new vehicle’, ‘9d – Transfer of the material to a second courier’ and ‘9e – Conceal the material in a new vehicle’. In six cases, arrests were made following Custom and Border Protection controls. In other cases, undercover agents or confidential sources informed investigators of the trafficking.
The crime phase corresponds to scene 10. In this scene, the driver goes through Custom and Border Protection to cross the border. The final phase corresponds to scenes 11 to 15, which starts when the material reaches the foreign country and is delivered to the final recipient.
4.2. Trafficking by crossing the border on foot (‘Ped’)
Crossing the border on foot was encountered in only four cases, thus no percentages were calculated for each scene (). As we decided to present only facets detected in the dataset, this table does not have many entries.
This process resembled the ‘Road’ process, except that the individual would carry the merchandise across the border. Weapons that are small in size, such as grenades (over 30), ammunition (from 300 to 3,500 rounds) and one firearm, were transported on foot. One to four people were involved, with an average of two.
The precrime phase corresponds to scenes 1 to 9. It starts with the recruitment of accomplices and ends with the material transportation through the border. The crime phase corresponds to scene 10, when the transporter crosses the border. The final phase corresponds to scenes 11 to 13, which start when the material is in the foreign country and delivered to the final recipient. The concealment methods used by traffickers are quite simple. They use bags or a cardboard box or they hide the material (ammunition) directly on their body, underneath their clothing.
4.3. Trafficking using commercial airlines (‘Air’)
The use of airplanes to cross borders involved commercial airlines (). One to four people were involved, but mostly one or two. In one case, a conspirator was a police officer. In another case, the conspirator was a pilot. They used their position to go through customs control, avoiding the passenger screening area.
The precrime phase corresponds to scenes 1 to 9 and starts with the recruitment of accomplices and ends with the concealment of the material within containers suitable for airport transit. Traffickers acquire the material through either physical or online environments. Often, traffickers buy weapons through storefront retailers or relatives. The acquisition can be either legal or illegal. In our dataset, payment is made either by cash, credit card or even wire transfers.
The crime phase are scenes 10 to 14, when the trafficker(s) – either purchaser(s) or accomplice(s) – reaches the airport and boards the plane. Dedicated concealment methods are frequently used, and the material is always hidden inside a container (mainly bags/suitcases). Traffickers used at least nine different ways to conceal the merchandise. Moreover, in some cases, they wrapped the weapons in zip-lock bag, foil, tape, cellophane or clothes. Methods of concealment included hiding the weapons inside checked luggage, bags, in the lining of a leather bag or in the lining of a suitcase. Some traffickers obliterated the serial numbers of weapons or disassembled the material. In most cases, customs officers discovered the material during airport security checks. In one case, an arrest was made during a stopover after the suitcase exploded. The final phase, scenes 15 to 17, occur when the transporter collects the container(s) and receives payment.
4.4. Trafficking using postal services (‘Post’)
This modus operandi involves the use of postal services or private shipping companies to send the products to destinations outside the US (). Traffickers transported up to 200 weapons, 6,500 rounds of ammunition, 100 night-vision goggles, bullet magazines (from a few to 5,000, trafficked on multiple occasions), and thermal-imaging equipment. One to 10 people were involved. In three of the 16 cases, more than eight people were involved. In the majority of cases, between one to five people were working together.
In this script, the precrime phase corresponds to scenes 1 to 10. It starts with the recruitment of accomplices and ends with the sale of the material to the final recipient. The crime phase corresponds to scenes 10 to 13, when traffickers require the services of a shipping company and ending when the parcel is sent outside the US. Traffickers acquire the material through either physical or online environments (legally or not). They use storefront retailers and manufacturers, but also online platforms such as Amazon, eBay or dedicated online US shops. In one case the sale occurred on the dark web. Payment was made either by cash, stolen credit or debit cards, PayPal, or cryptocurrencies like Bitcoin, Monero, Zcash or Ethereum. Traffickers used at least five concealment techniques, including the obliteration of serial numbers and disassembling the merchandise. Weapons were concealed in cases or in household items. The final phase corresponds to scenes 14 to 16, starting when the material is collected in a foreign country ().
4.5. Trafficking using freight transport (‘Freight’)
Using freight forwarding services (), traffickers transported up to 204 weapons, 10,500 rounds of ammunition, two handgun bullet magazines and two body armours. The number of discovered weapons was relatively low (from one to 12 in 10 cases). In three cases, the number of weapons being trafficked was larger (from 65 to 204). In one case, around 100 rounds of ammunition were smuggled, but in the majority of cases, around 7,500 to 10,000 rounds were concealed and sent using freight forwarding. One to 10 people were involved, with an average of two people. Only one case involved 10 people, and most of the other cases involved one to four people. The 10-person case is the only case in this study in which a murder (of one accomplice) occurred. Regardless of the modus operandi used, no other cases involved direct violence.
Table 6. Trafficking using freight transport (‘Freight’) script (n = 19 cases).
The precrime phase corresponds to scenes 1 to 10. It starts with the recruitment of accomplices and ends with the material having been packed. As was observed throughout this study, scenes concerning the acquisition of the merchandise (scenes 4 and 5) are mostly taken by the people in charge of the trafficking. Traffickers acquire the material either in the physical or online environments. The physical environment was mostly represented by gun shows, gun stores, storefront retailers, theft, face-to-face discussion, or telephonic texts or calls. Otherwise, traffickers bought their material via online sales platforms such as eBay or Amazon. Traffickers used cash, international wire transfers, credit card or the PayPal system. Regarding concealment methods, traffickers used at least 13 ways to conceal the material (see, for details). Some traffickers obliterated the serial numbers of the weapons, disassembled the material, painted them or co-mingled them. In some cases, they wrapped the material in plastic wrap, foil, tape, foam or clothes. The merchandise was found in boxes, garbage bags, several containers, barrels, wooden crates, household goods, and in the compartments of vehicles.
The crime phase corresponds to scenes 11 to 14, starting with the traffickers requiring the services if a shipping company and ending when the parcel is sent. The final phase corresponds to scenes 15 to 19, starting when the material is retrieved in the foreign country and ending when payment is made. To retrieve the container from the shipping addresses, some traffickers travelled by plane from the US. The stage ‘17 – Additional steps’ (5.26%) is similar to scenes 12 to 15 detailing the phases of sending the package. This scene can encompass a wide range of possible actions. Finally, the packages were retrieved in less than 50% of cases and the payment (scene 19) in less than a third of cases (31.6%).
5. Discussion
SchroederFootnote52 found that most weapons trafficking cases from the US to other countries involved transport by car. This finding might be the result of stronger border controls at points where cars cross, especially between the US and Mexico. In addition, the concealment methods employed by arms transporters using cars were quite simple. It is therefore not surprising that traffickers using cars were being caught by customs or law enforcement officials. These results are in line with those presented in Leuprecht and Aulthouse’s studyFootnote53 in which six cases of arms trafficking from the US to Canada were analysed. They show that some traffickers (in at least 3 out the 6 cases) used cars to cross the borders. In two cases, traffickers did not conceal their firearms in a very sophisticated way, while for the last one, traffickers used a hidden compartment in the gas tank of the vehicle.
Our study found that traffickers also commonly used postal services or freight transport. Freight shipments involve large volumes of goods, providing more opportunities to conceal illegal merchandise. In this context, concealment methods were also more sophisticated, for example, weapons were concealed inside televisions or in CD containers.
The primary objective was to create a single about weapons trafficking from the US (protoscript level). The researchers finally decided not to generalise all five scripts into a single script. We realised that this would have altered the level of detail, rendering the final script less informative. For example, the ‘concealment techniques’ scenes, an element of every script, have their own particularities depending on the means of transport used by traffickers.
While some cases involved a large group of criminals (up to 12 people), others were driven by a single individual. Our deduction is that small groups of people are more flexible and less likely to attract the attention of law enforcement. The number of people involved is not correlated to the extent of the trafficking. For example, in one case involving postal services, two traffickers handled more than 5,000 rounds of ammunition, night-vision goggles and 5,000 assault rifle magazines. Similarly, one individual, who used a vehicle to cross a border, transported more than 10,000 rounds of ammunition, at least 60 weapons, a number of high-capacity pistols and rifle bullet magazines. Using the same modus operandi, two and three people respectively trafficked more than 650 AK-type bullet magazines and over 65,000 rounds of ammunition. These cases exemplify how small groups can be prolific.
In 62 out of 66 cases (93.9%), smugglers, sometimes repeatedly, followed a single modus operandi. In these four remaining cases (6.1%), two groups of traffickers used both the ‘Post’ and the ‘Freight’ means of transport. These findings suggest that diversification is rare in the context of weapons trafficking from the US. This observation could be confirmed by a criminal trajectory analysis. Interviewing traffickers might also help researchers to understand more precisely why they favour the repetition of a particular modus operandi. Our observation regarding the repetition of a favoured modus operandi is in line with the rational choice theory of Clarke and CornishFootnote54. In this theory, criminals are considered as rational, evaluating their choice of actions regarding both potential risks (e.g. getting caught) and benefices (e.g. financial). Indeed, traffickers might not consider varying the modus operandi because it would imply major practical changes and increased effort, including a need to reach out to additional possible conspirators to perform certain new roles, which could increase the visibility of their illegal activity and consequently the risk of being caught. Finally, a modus operandi that has proved efficient is likely to be repeated to maximise the chances of success.
Every case examined in this study has been handled by a US court. The sources were mostly judicial reports (e.g. indictments, plea agreements, complaints). These documents are considered as reliable and contain valid information. In fact, since they emanate from a judicial system, they are reviewed and approved by different parties. They also contain a precise description of the facts that were presented before the court. Concerning the defendant (i.e. age, nationality) and the criminal activities, the information provided has certain limitations. For example, sometimes judicial reports provide only an inventory of the criminal actions. Contrary to police reports, they do not necessarily include details that allow for a reconstruction of the entire criminal process. For this reason, including police reports would complement the research and enrich the findings.
Furthermore, aspects of the criminal activity involved in the trafficking of weapons might not be known to law enforcement. Only a modus operandi that has been detected can be reconstructed. One might argue that some offenders use techniques and approaches that have yet to be detected. Analysing narratives on online forums of buyers and sellers might be considered to fill this knowledge gap partially.
As Lemieux and Bruschi argued in their studyFootnote55, the quality of scripts is difficult to assess. Similarly, extracting and classifying relevant aspects across cases in this study posed significant challenges when analysing 66 cases, all containing different levels of detail. Specific protocols are required to ensure consistent coding among different actors. In the present study, the coding activities were managed by a unique researcher and for a limited number of cases, ensuring a certain consistency for this part of the work. Moreover, all scripts have been reconstructed from a limited number of cases. While at least 16 cases were used to produce three of the scripts, the ‘Ped’ and ‘Air’ scripts are based on 4 and 9 cases. Our generalisation should therefore be considered with caution. However, this study provides a first formalisation of crime scripts for firearms trafficking, with a particular focus on the means of transport.
6. Conclusion
This study focuses on the means of transport used when trafficking weapons from the US to foreign countries. Using judicial documents, 66 cases through were analysed through the lens of the crime script perspective. Findings suggest five scripts in US cross-border weapon trafficking: by road transport (‘Road’), using commercial airlines (‘Air’), using postal services to deliver a package (‘Post’), using freight transport (‘Freight’) or crossing the border on foot (‘Ped’). The research indicates that road, postal and freight means of transports are particularly common, while commercial airlines and crossing the border on foot were more rarely encountered. Further, when considering criminal groups, our study also suggests that the number of people involved is not correlated to the extent of the trafficking. Indeed, both singles and group of criminals may traffic large quantity of material (i.e. over 200 weapons, 100 night-vision goggles, 650 AK-type bullet magazines, over 65,000 rounds for instance). The analysis of the trafficking crime scripts and their facets confirms that concealment methods vary according to means of transportation. Methods are simpler when cross border trafficking is done by car, while concealment is more complex when traffickers transport materials by freight. Eventually, our results corroborate the assumption of a modus operandi specialisation. When a modus operandi proved to be successful, offenders are likely to stick to it in order to reduce the efforts and the risks associated with testing new strategies. In general, traffickers specialise in a single mean of transportation, with only a few using two (postal and freight). This study relied on secondary sources which provide scarce information on offenders’ motivation and decision-making. In the future, other research may fill the gap using primary sources (i.e. police officer interviews and trafficker interviews) and ethnographic methods.
Acknowledgments
The authors thank Matt Schroeder of the Small Arms Survey for sharing his dataset of court cases and for his helpful inputs at the initial stages of this research.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Notes on contributors
Fiona Langlois
Fiona Langlois is a PhD candidate at the School of Criminal Justice (University of Lausanne) and works as teaching and research assistant. She completed her studies in forensic sciences at University of Lausanne, obtained her bachelor’s degree in 2016 and continued with a master in crime analysis. Her research interest focuses on the investigative methods used by public and private bodies on match fixing issues in football. More broadly, her work focuses on the analysis of complex crimes and modus operandi (such as in sport, organized crimes or arms trafficking).
Damien Rhumorbarbe
Damien Rhumorbarbe is a PhD candidate at the Ecole des science criminelles of the University of Lausanne, where he worked for several years as teaching and research assistant in forensic science. His work is mostly focused on the monitoring of new psychoactive substances and illicit drugs markets, although his research interests also include firearms related topics within the perspective of criminal sciences.
Denis Werner
Denis Werner is a PhD candidate at the Ecole des science criminelles of the University of Lausanne, where he worked for several years as teaching and research assistant in forensic science. He contributed to various courses on firearms and gunshot residues for Bachelor, Master and continuing education programs, while participating in several research projects in these fields. He also did forensic casework across different fields at the Ecole des science criminelles. He is currently lecturer in forensic science at the University of Derby (UK).
Nicolas Florquin
Nicolas Florquin is a senior researcher at the Small Arms Survey, which is an associated programme of the Graduate Institute of International and Development Studies in Geneva. His research interests include armed actors’ self-governance mechanisms and illicit flows of arms and ammunition. He previously worked for Geneva Call, an organization specializing in engaging with non-state armed groups on humanitarian issues, and for the UN Group of Experts on Liberia. He received his Ph.D. in applied social science from the University of Brighton.
Stefano Caneppele
Stefano Caneppele (PhD) is Professor in criminology and Deputy Director of the School of Criminal Justice, University of Lausanne (Switzerland). Previously he was an Associate Professor at the Faculty of Political and Social Sciences, Università Cattolica del Sacro Cuore of Milan. He also worked at Transcrime on several international and national research projects (www.transcrime.it) (2002-2015). His research interests focus on the analysis and comprehension of complex crimes, such as economic crime, organized crime and terrorism, the exploitation of illicit markets and the manipulation of licit ones, as well as the role of regulation and law enforcement to prevent their expansion.
Quentin Rossy
Quentin Rossy, associate professor at the School of Criminal Justice in Lausanne, is in charge of the Master program in Crime Data Analysis and Traceology, a program shared with the School of Criminology at the University of Montreal. Anchored in forensic intelligence, his research interests focus on methods of crime analysis, the effects of digital transformations on investigative and criminal intelligence practices, and the analysis of Internet crime, in particular frauds and illicit markets.
Notes
1 UNODC – United Nations Office on Drugs and Crime, ‘Annual Report 2018’; Chainey and Guererro, ‘Developing Crime Analysis in Mexico’; Arsovska and Kostakos, ‘Illicit Arms Trafficking and the Limits of Rational Choice Theory’.
2 Greene, ‘Examining International Responses to Illicit Arms Trafficking’.
3 Chainey and Guererro, ‘Developing Crime Analysis in Mexico’.
4 Tompson and Chainey, ‘Profiling Illegal Waste Activity: Using Crime Scripts as a Data Collection and Analytical Strategy’.
5 Cornish, ‘The Procedural Analysis of Offending and Its Relevance for Situational Prevention’; Cornish, ‘Crime as Scripts’; Morselli and Roy, ‘Brokerage Qualifications in Ringing Operations’; Leclerc and Reynald, ‘When Scripts and Guardianship Unite’.
6 Borrion, ‘Quality Assurance in crime scripting’.
7 Ibid.
8 Cornish, ‘The Procedural Analysis of Offending and Its Relevance for Situational Prevention’.
9 Cornish, ‘The Procedural Analysis of Offending and Its Relevance for Situational Prevention’; Dehghanniri and Borrion, ‘Toward a More Structured Crime Scripting Method’; Leclerc, ‘Script Analysis for Crime Controllers’; Leclerc, Boosting Crime Scene Investigations Capabilities through Crime Script Analysis; Ribaux, Walsh, and Margot, ‘The Contribution of Forensic Science to Crime Analysis and Investigation’; Ribaux et al., ‘Intelligence-Led Crime Scene Processing. Part II’.
10 In this article, the terms ‘weapons’, ‘small arms and light weapons’ (SALW) and ‘firearms’ are used interchangeably. SALW cover both military-style small arms and light weapons, and commercial firearms (handguns and long guns) (see UNGA 1997). Small arms specifically include revolvers and self-loading pistols, rifles and carbines, sub-machine guns, assault rifles, and light machine guns. Light weapons include heavy machine guns, grenade launchers, portable anti-tank and anti-aircraft guns, recoilless rifles, portable anti-tank missile and rocket launchers, portable anti-aircraft missile launchers, and mortars of less than 100 mm calibre. Firearms include revolvers and self-loading pistols, rifles and carbines, shotguns, sub-machine guns, and light and heavy machine guns – in other words, it includes all small arms and certain (but not all) categories of light weapons (see Jenzen-Jones and Schroeder 2018 pp. 27–29).
11 UNODC – United Nations Office on Drugs and Crime, ‘Global Study on Firearms 2020’.
12 Schroeder, ‘On the Record; Illicit Weapons in the United States’.
13 Klare, ‘The New Arms Race’; SaferWorld, ‘Module 3: Impact of Small Arms and Light Weapons on Conflict, Security and Human Development’.
14 UNODC – United Nations Office on Drugs and Crime, ‘Global Study on Firearms 2020’.
15 SaferWorld, ‘Module 3: Impact of Small Arms and Light Weapons on Conflict, Security and Human Development’.
16 Mc Evoy and Hideg, ‘Global Violent Deaths 2017: Time to Decide’.
17 Ibid.
18 Ibid.
19 Stohl, ‘The Tangled Web of Illicit Arms Trafficking’.
20 Greene, ‘Examining International Responses to Illicit Arms Trafficking’; Stohl, ‘The Tangled Web of Illicit Arms Trafficking’; Schroeder, ‘Captured and Counted’; Schroeder, ‘On the Record; Illicit Weapons in the United States’.
21 UNODC – United Nations Office on Drugs and Crime, ‘Global Study on Firearms 2020’.
22 Ibid.
23 Braga et al., ‘Interpreting the Empirical Evidence on Illegal Gun Market Dynamics’.
24 Faltas and Chrobok, ‘Disposal of Surplus Small Arms: A Survey of Policies and Practices in OSCE Countries’; Ford, Firearms Trafficking; McDougal et al., ‘The Way of the Gun’.
25 Faltas and Chrobok, ‘Disposal of Surplus Small Arms: A Survey of Policies and Practices in OSCE Countries’; Gildea and Pierce, ‘Small Arms and Light Weapons Trafficking’; Ford, Firearms Trafficking; Miller, Hepburn, and Azrael, ‘Firearm Acquisition without Background Checks’; US Government, ‘Electronic Code of Federal Regulations (ECFR)’.
26 Gildea and Pierce, ‘Small Arms and Light Weapons Trafficking’.
27 Braga et al., ‘Interpreting the Empirical Evidence on Illegal Gun Market Dynamics’.
28 Ford, Firearms Trafficking.
29 Schroeder, ‘Dribs and Drabs: The Mechanics of Small Arms Trafficking from the United States’.
30 UNODC – United Nations Office on Drugs and Crime, ‘The illicit market in firearms’
31 Holtom, Pavesi, and Rigual, ‘Trade Update. Transfers, Retransfers and the ATT’.
32 Ibid
33 Schroeder, ‘Dribs and Drabs: The Mechanics of Small Arms Trafficking from the United States’.
34 Rhumorbarbe et al., ‘Characterising the Online Weapons Trafficking on Cryptomarkets’.
35 Braga et al., ‘Interpreting the Empirical Evidence on Illegal Gun Market Dynamics’, 791.
36 UNODC – United Nations Office on Drugs and Crime, ‘Global Study on Firearms 2020’.
37 Gildea and Pierce, ‘Small Arms and Light Weapons Trafficking’; Schroeder, ‘On the Record; Illicit Weapons in the United States’.
38 Beauregard and Leclerc, ‘An Application of the Rational Choice Approach to the Offending Process of Sex Offenders’.
39 Gildea and Pierce, ‘Small Arms and Light Weapons Trafficking’.
40 Dehghanniri and Borrion, ‘Crime scripting: A systematic review’.
41 De Vries, ‘From the Instrument of Delivery to the Actual Agent of Harm’.
42 De Vries, ‘Converted Firearms: A Transnational Problem with Local Harm’.
43 Williamson, ‘Criminal Armourers and Illegal Firearm Supply in England and Wales’.
44 Ibid.
45 Williamson, Disrupting Illegal Firearm Supply Through Crime Script Analysis.
46 Schroeder, ‘Dribs and Drabs: The Mechanics of Small Arms Trafficking from the United States’.
47 Ibid.
48 In this article, the term ‘script’ is used regardless its type (planned script, performed script) and its level of abstraction.
49 Ibid.
50 Cornish, ‘The Procedural Analysis of Offending and Its Relevance for Situational Prevention’.
51 Borrion, ‘Quality Assurance in crime scripting’.
52 Schroeder, ‘Dribs and Drabs: The Mechanics of Small Arms Trafficking from the United States’.
53 Leuprecht and Aulthouse, ‘Guns for Hire’.
54 Cornish and Clarke, The Reasoning Criminal.
55 Lemieux and Bruschi, ‘The production of jaguar paste in Suriname: a product-based crime script’.
Bibliography
- Arsovska, J., and P. A. Kostakos. (2008). Illicit Arms Trafficking and the Limits of Rational Choice Theory: The Case of the Balkans. Trends in Organized Crime, 11(4), 352–378. https://doi.org/10.1007/s12117-008-9052-y
- Beauregard, E., and B. Leclerc. (2007). An Application of the Rational Choice Approach to the Offending Process of Sex Offenders: A Closer Look at the Decision-Making. Sexual Abuse, 19(2), 115–133. https://doi.org/10.1177/107906320701900204
- Borrion, H. (2013). Quality Assurance in Crime Scripting. Crime Science, 2(1), 1–12. https://doi.org/10.1186/2193-7680-2-6
- Braga, A. A., G. J. Wintemute, G. L. Pierce, P. J. Cook, and G. Ridgeway. (2012). Interpreting the Empirical Evidence on Illegal Gun Market Dynamics. Journal of Urban Health, 89(5), 779–793. https://doi.org/10.1007/s11524-012-9681-y
- Chainey, S., and N. Guererro. (2019). Developing Crime Analysis in Mexico: Case Studies of Cargo Robbery on Highways, Illegal Weapons Trafficking. Robbery of Convenience Stores and Poppy Cultivation’. https://discovery.ucl.ac.uk/id/eprint/10067263/8/Chainey_UCL%20CNS%20Technical%20note%20on%20Mexico%20CNS%20crime%20analysis%20FINAL.pdf
- Cornish, D. B. (1994). Crime as Scripts. In D. Zahm and P. Cromwell (edited by), Proceeding of the International Seminar on Environmental Criminology and Crime Analysis (pp. 30–45). University of Miami, Coral Gables.
- Cornish, D. B. (1994). The Procedural Analysis of Offending and Its Relevance for Situational Prevention. Crime Prevention Studies, 3(1), 151–196. https://popcenter.asu.edu/sites/default/files/Library/CrimePrevention/Volume_03/06_cornish.pdf
- Cornish, D. B., and R. V. Clarke. (1986). The Reasoning Criminal: Rational Choice Perspectives on Offending. New York : Springer-Verla. 270 . https://doi.org/10.4324/9781315134482
- De Vries, M. (2012). From the Instrument of Delivery to the Actual Agent of Harm: Fighting the Criminal Purchase of Ammunition. European Journal on Criminal Policy and Research, 19, 1-14. https://doi.org/10.1007/s10610-012-9173-3
- Dehghanniri, H., and H. Borrion. ‘Toward a More Structured Crime Scripting Method’. In 2016 IEEE 24th international requirements engineering conference workshops (REW), 94–97. IEEE, 2016.
- Faltas, S., and V. Chrobok. (2004). Disposal of Surplus Small Arms: A Survey of Policies in OSCE Countries. Small Arms Survey. https://www.bicc.de/uploads/tx_bicctools/small_arms_report.pdf
- Ford, J. T. (2009). Firearms Trafficking: US Efforts to Combat Arms Trafficking to Mexico Face Planing and Coordination Challenges. DIANE Publishing.
- Gildea, T., and G. Pierce. (2007). Small Arms and Light Weapons Trafficking: Creating an Assessment Framework from the US Experience. Nonproliferation Review, 14(1), 1–31. https://doi.org/10.1080/10736700601178432
- Greene, O. (2000). Examining International Responses to Illicit Arms Trafficking. Crime, Law and Social Change, 33(1), 151–190. https://doi.org/10.1023/A:1008398420612
- Holtom, P., I. Pavesi, and C. Rigual (2014) Trade Update. Transfers, Retransfers and the ATT. In Small Arms Survey 2014: Women and Guns (Cambridge: Cambridge University Press), 108–143. https://www.smallarmssurvey.org/sites/default/files/resources/Small-Arms-Survey-2014-Chapter-4-EN.pdf
- Klare, M. T. (1997). The New Arms Race: Light Weapons and International Security. Current History, 96(609), 173.
- Leclerc, B. (2013). Script Analysis for Crime Controllers: Extending the Reach of Situational Prevention. Organized Crime, Corruption and Crime Prevention: Essays in Honor of Ernesto U. Savona. https://doi.org/10.1007/978-3-319-01839-3_2
- Leclerc, B. (2017). Boosting Crime Scene Investigations Capabilities through Crime Script Analysis. The Routledge International Handbook of Forensic Intelligence and CriminologyRoutledgehttps://doi.org/10.4324/9781315541945-9
- Leclerc, B., and D. Reynald. (2017). When Scripts and Guardianship Unite: A Script Model to Facilitate Intervention of Capable Guardians in Public Settings. Security Journal, 30(3), 793–806. https://doi.org/10.1057/sj.2015.8
- Leuprecht, C., and A. Aulthouse. (2014). Guns for Hire: North America’s Intra-Continental Gun Trafficking Networks. Criminology, Criminal Justice, Law & Society, 15(3), 57–74. https://www.semanticscholar.org/paper/Guns-for-Hire%3A-North-America’s-intra-continental-Leuprecht-Aulthouse/a5260e14887c4637c198404bb0e1c0606c8fd100.
- Mc Evoy, C., and G. Hideg. (2017). Global Violent Deaths 2017: Time to Decide. Small Arms Survey.
- McDougal, T. L., D. A. Shirk, R. Muggah, and J. H. Patterson. (2015). The Way of the Gun: Estimating Firearms Trafficking across the US–Mexico Border. Journal of Economic Geography, 15(2), 297–327. https://doi.org/10.1093/jeg/lbu021
- Miller, M., L. Hepburn, and D. Azrael. (2017). Firearm Acquisition without Background Checks: Results of a National Survey. Annals of Internal Medicine, 166(4), 233–239. https://doi.org/10.7326/M16-1590
- Morselli, C., and J. Roy. (2008). Brokerage Qualifications in Ringing Operations. Criminology, 46(1), 71–98. https://doi.org/10.1111/j.1745-9125.2008.00103.x
- Rhumorbarbe, D., D. Werner, Q. Gilliéron, L. Staehli, J. Broséus, and Q. Rossy. (2018). Characterising the Online Weapons Trafficking on Cryptomarkets. Forensic Science International, 283, 16–20. https://doi.org/10.1016/j.forsciint.2017.12.008
- Ribaux, O., A. Baylon, E. Lock, O. Delémont, C. Roux, C. Zingg, and P. Margot. (2010). Intelligence-Led Crime Scene Processing. Part II: Intelligence and Crime Scene Examination. Forensic Science International, 199(1–3), 63–71. https://doi.org/10.1016/j.forsciint.2010.03.011
- Ribaux, O., S. J. Walsh, and P. Margot. (2006). The Contribution of Forensic Science to Crime Analysis and Investigation: Forensic Intelligence. Forensic Science International, 156(2–3), 171–181. https://doi.org/10.1016/j.forsciint.2004.12.028
- SaferWorld ‘Module 3: Impact of Small Arms and Light Weapons on Conflict, Security and Human Development’. Small Arms and Light Weapons Control: A Training Manual, 2012. https://www.saferworld.org.uk/resources/publications/713-small-arms-and-light-weapons-control
- Schroeder, M. (2013). Captured and Counted: Illicit Weapons in Mexico and the Philippines. In Small Arms Survey. Small Arms Survey 2013: Everyday Dangers. Small Arms Survey (pp. 282–317). Cambridge: Cambridge University Press. https://doi.org/10.1017/CBO9781107323612.021.
- Schroeder, M. (2014). On the Record; Illicit Weapons in the United States. In Small Arms Survey. Small Arms Survey 2014: Women and Guns. (Cambridge: Cambridge University Press). 244–273
- Schroeder, M. (2016). Dribs and Drabs: The Mechanics of Small Arms Trafficking from the United States. Small Arms Survey: Issue Brief, (17), 1–16. https://www.smallarmssurvey.org/resource/dribs-and-drabs-mechanics-small-arms-trafficking-united-states-issue-brief-17
- Stohl, R. (2004). The Tangled Web of Illicit Arms Trafficking. 21–26. http://www.pogoarchives.org/straus/cdi_archive/terrorinshadows-stohl-2004.pdf.
- UNODC - United Nations Office on Drugs and Crime. ‘Annual Report 2018’, 2018. https://www.unodc.org/documents/AnnualReport/Annual-Report_2018.pdf.
- UNODC - United Nations Office on Drugs and Crime. ‘Global Study on Firearms 2020’, 2020. http://www.unodc.org/unodc/en/firearms-protocol/firearms-study.html
- US Government. ‘Electronic Code of Federal Regulations (ECFR)’, 2020. https://www.ecfr.gov/
- Williamson, H. (2015). Criminal Armourers and Illegal Firearm Supply in England and Wales. British Society of Criminology. https://doi.org/10.13140/RG.2.1.4362.1524
- Williamson, H. (2016). Disrupting Illegal Firearm Supply Through Crime Script Analysis. Modern Crime Prevention. https://doi.org/10.13140/RG.2.1.2265.0002