ABSTRACT
The collection of accurate, detailed, and timely intelligence buttresses critical law enforcement decision-making. However, the quality and quantity of the intelligence gathered relies heavily upon the interviewing techniques used to retrieve it. The perceptions of intelligence practitioners are key to developing an understanding of practices concerning intelligence collection. Yet, to date, no research has been undertaken that explores the United Kingdom’s Source Handlers’ perceptions of the interviewing processes employed with informants. The present study interviewed 24 Source Handlers from Counter Terrorism Dedicated Source Units in the United Kingdom. Five themes emerged from the interviews, (i) a comparison between interviewing and debriefing; (ii) the PEACE model in intelligence interviews; (iii) the importance of effective communication; (iv) Source Handlers’ use of cognitive retrieval techniques; and, (v) Source Handler interview training. The perceived commonalities between interviewing and debriefing provided support for the transferability of investigative interviewing research and practices into the collection of Human Intelligence (HUMINT), reiterating themes (ii), (iii), and (iv). Finally, participants highlighted a need for additional training concerning intelligence gathering techniques, as police officers who are responsible for gathering HUMINT could benefit from further professional development based on investigative interviewing research and professional practices.
Introduction
The collection of accurate, detailed and timely intelligence supports law enforcement decision-making. Intelligence generates leads of enquires, which aim to prevent criminal activity at a local, regional, national and international level. Further still, the distinction between intelligence and information is key to what will ultimately be collected, recorded, analysed, and subsequently shared within and across law enforcement and partner agencies (Stanier & Nunan, Citation2018). Hence, ‘intelligence is information designed for action’ (Grieve, Citation2004, p. 25). However, the quality and quantity of the intelligence gathered relies on interviewing techniques. As such, maximising the amount of intelligence appears highly dependent upon a better understanding and application of psychological research on memory and communication.
This study gained unprecedented access to a range of Counter Terrorism Dedicated Source Units (CTDSU) in the United Kingdom (UK). Consequently, 24 Source Handlers were interviewed about their perceptions of the interviewing processes employed during interactions with Covert Human Intelligence Sources (CHIS, hereafter informants), and the applicability of investigative interviewing techniques and models to intelligence collection. UK CTDSUs are responsible for the day-to-day management of counter terrorism and domestic extremist informants, governed primarily by the Regulation of Investigatory Powers Act 2000. The existing literature on Human Intelligence (HUMINT) has for the most part been conducted outside the UK (e.g. Evans, Meissner, Brandon, Russano, & Kleinman, Citation2010; Oleszkiewicz, Granhag, & Kleinman, Citation2017; Russano, Narchet, Kleinman, & Meissner, Citation2014). Whilst research on memory retrieval and cognition applies to informants globally, the present study fills a research gap regarding UK Source Handlers’ perceptions of the interviewing processes employed with informants.
Interviewing for intelligence
Interactions with human sources, and subsequently the collection of HUMINT forms a major role within the intelligence picture in the UK. HUMINT interviewsFootnote1 take place in a number of operational circumstances, with many occurring within a collapsing time frame. For example, conducting an exploratory prisoner debrief within a 45-minute prison visit, during a port stop whereby a passenger arrives into the country, within police custody where suspects are detained for other offences unconnected with the Source Handlers approach, and a cold call pitch (unsolicited contact) in person or via the telephone. Such interviews aim to develop a long-term rapport (see Meehan, Kelly, & McClary, Citation2019) to bring the human source on board as an informant, in order to conduct additional intelligence interviews going forward. Once established, secure meetings can be arranged that allow for a more thorough interview, as time and location is more flexible outside of a formal criminal justice setting.
Authorised informants are legally defined as CHIS and while not a legal requirement, it is embedded practice for all law enforcement agencies to manage their informants within Dedicated Source Units (DSUs). A DSU within England and Wales has the responsibility to identify, assess, recruit and deploy informants. The DSU structure, subject to resourcing, may include a number of different functions; recruitment team, prison team, handling team and an analytical and research desk. In practise, it is not uncommon for the roles to be undertaken by the same Source Handlers. Informants are managed in accordance with the Regulation of Investigatory Powers Act 2000 (RIPA Citation2000) and its Codes of Practice (Home Office, Citation2018). RIPA 2000 and the associated national policing doctrine covers informant authorisations, informant’s security and welfare and general oversight arrangements.
Despite the statutory framework outlined by RIPA Citation2000 and internal policy and practice, the legislation and accompanying codes are silent on the rules around the techniques used within informant interactions. Source Handlers undertake intelligence interviews of informants (i.e. CHIS) which do not fall under the provisions contained within the Police and Criminal Evidence Act 1984 (PACE Citation1984), regarding the detention, treatment and questioning of suspects. Moreover, current Source Handler training in the UK includes little mention of interviewing techniques. Therefore, the authors reiterate that research and training concerning investigative interviewing (e.g. Clarke & Milne, Citation2016; Evans et al., Citation2010; Fisher & Geiselman, Citation2019; Milne & Bull, Citation1999; Shepherd & Griffiths, Citation2013) should be applied to the intelligence context. This is because there are two key similarities between investigative interviewing and intelligence debriefing: they both aim to obtain reliable and detailed information and both concern interviewing witnesses, albeit informants are ‘a special type of witness’ (Billingsley, Nemitz, & Bean, Citation2001, p. 7).
In England and Wales, the PEACE model of interviewing has been established over 25 years (an acronym for the model’s five phases of Planning and Preparation; Engage and Explain; Account; Closure; and Evaluation, College of Policing, Citation2019). This model is built on interviewing techniques such as the Cognitive Interview (CI), which is designed to gather information that is based on scientific principles concerning how memories are stored and accessed. The CI has been found to increase the amount of correct information given by interviewees (Fisher & Geiselman, Citation1992; Memon, Meissner, & Fraser, Citation2010; Milne & Bull, Citation1999). The present study discussed the application of the PEACE model and cognitive retrieval techniques to HUMINT collection, as perceived by Source Handlers themselves.
The PEACE model of interviewing
The introduction of the PEACE modelFootnote2 (Central Planning and Training Unit, Citation1992) provided the police with a flexible model, exemplifying the information gathering approach by highlighting interviewee vulnerability, the frailty of human memory, and the consequences of unethical interviewing. Supported by psychological theory and research (Walsh & Bull, Citation2010), the PEACE model promotes information gathering via rapport building, effective communication, open-mindedness and an understanding of memory which is equally applicable to Source Handler and informant interactions.
First, the Planning and Preparation phase would encourage Source Handlers to research the person of interest before the interview and assist with rapport building (Meehan et al., Citation2019). Second, the Engage and Explain phase involves the Source Handler developing and maintaining rapport in order to create conditions so the informant can talk freely and understand the purpose of the interaction, whilst assessing the informants’ capabilities of providing comprehensive information (and then adapting their interview style to accommodate) (Alison, Alison, Noone, Elntib, & Christiansen, Citation2013; Walsh & Bull, Citation2012). Third, in the Account phase, the informant is given the scope to provide fully the information they know. This phase encourages the use of Conversation Management (CM), the CI, and the relevant cognitive retrieval techniques to collect additional information (Clarke & Milne, Citation2016; Shepherd & Griffiths, Citation2013). Questions are asked to prompt the informant to provide fulsome details and clarification when required. Fourth, the Closure phase provides the informant the chance to add or clarify anything, and for the Source Handler to discuss the next steps and ensure that rapport has been maintained throughout (Alison et al., Citation2013; Walsh & Bull, Citation2012). The final phase involves Evaluation, which urges the Source Handler to reflect on the interview process, understand what information has been collected and take the appropriate actions in response. The PEACE model can provide an informative structure for effective intelligence interviews.
Cognitive retrieval techniques
In the Account phase, a Source Handler should be trained to employ a range of cognitive retrieval techniques to assist information collection (Memon et al., Citation2010). The CI is a flexible technique which was developed to enhance the social interaction and cognitive processes (Fisher & Geiselman, Citation1992; Milne & Bull, Citation1999). The social interaction is enhanced via the employment of rapport-based interviewing (Alison et al., Citation2013). Redlich, Kelly, and Miller (Citation2014) examined U.S. military and federal interrogators’ perceived use various interrogation techniques. Regardless of the intended outcome and context of the interrogation, rapport and relationship building were reported as the most frequently used, and perceived as the most effective, especially when compared to confrontational techniques (Redlich et al., Citation2014).
Rapport-based interviewing should facilitate cognitive processes, which are supported via a range of techniques such as the Mental Reinstatement of Context (MRC) and multiple and varied retrieval avenues. Fisher and Geiselman (Citation2019) advocated for the CI to be utilised in non-criminal contexts, with specific reference to gathering intelligence from human sources. In particular, Leins, Fisher, Pludwinski, Rivard, and Robertson (Citation2014) investigated the recall of multiple events from participants, reporting that the CI yielded considerably more information than a free narrative followed by direct questions. Leins et al.’s (Citation2014) study can extrapolate to such intelligence-gathering sessions where informants attend numerous meetings with organised crime groups (Fisher & Geiselman, Citation2019). Thus, the CI would benefit HUMINT scenarios, which concern interviewing for intelligence (alike investigative interviews; Meissner, Surmon-Böhr, Oleszkiewicz, & Alison, Citation2017).
The original CI components (i.e. report everything; context reinstatement; change order; change perspective) are designed to assist the memory retrieval process (see Fisher & Geiselman, Citation1992). However, interactions with informants are usually constrained by time. Once the security of a Source Handler and informant meeting is in place and the welfare of the informant has been checked, time for the interaction might be limited. In investigative interviews, when faced with such time challenges it has been found that the full set of CI techniques cannot be used and modified version of the CI is often conducted (Dando, Wilcock, & Milne, Citation2009). Hence, research concerning modified CIs, such as those using sketch plans (Dando et al., Citation2009; Eastwood, Snook, & Luther, Citation2019), timeline technique (Hope, Mullis, & Gabbert, Citation2013), and self-generated cues (Leins et al., Citation2014), which are short and are effective at enhancing recall are beneficial to the HUMINT context.
Modified CIs have been found to be invariably effective in gathering detailed information, while reducing the time taken, when compared to the full CI (Dando et al., Citation2009). Two CI techniques in particular; report everything (encourages a recall in as much detail as possible without editing, regardless of perceived importance of the details or how partially remembered) and Mental Reinstatement of Context (MRC; mentally reconstruct both the physical and emotional context of the event to assist recall) have been found effective (Milne & Bull, Citation2002). Furthermore, Dando et al. (Citation2009) examined another memory retrieval technique, the Sketch MRC which encouraged the participant to draw a detailed sketch/plan of the event whilst verbally describing as they draw. Such a technique would enable informants to recall from their own retrieval cues and not be led by the Source Handler. Dando et al. (Citation2009) found that the Sketch MRC was as effective as those interviews where MRC alone was used and faster. They also found that interviews using the Sketch MRC prompted more information than interviews that did not employ the MRC at all (i.e. ‘standard interviews’, where the interviewee was just asked to report everything), while also yielding fewer confabulations (Dando et al., Citation2009).
Cognitive mnemonics such as the timeline technique (Hope et al., Citation2013) and self-generated cues (Wheeler & Gabbert, Citation2017) may also assist in circumstances where an informant is required to recall specific details from a series of events (e.g. attending numerous secret meetings). The timeline technique confirmed that episodic memory is temporally ordered. Hence, the temporal context, which links to the chronological order, plays an important role in assisting with information recall (Hope et al., Citation2013). That study also found that the timeline technique retrieved more correct details than interviews that used free recall techniques.
In turn, self-generated cues would encourage the informant to generate salient details about the to-be-remembered event to facilitate further retrieval (Wheeler & Gabbert, Citation2017). This is a non-leading interview technique as it would have no input from the Source Handler. It has been found that self-generated cues helped participants recall more than twice as many person, conversation, action, and setting details (Leins et al., Citation2014), and that self-generated cues increased reporting with no cost to accuracy compared to other-generated cues or free recall (Wheeler & Gabbert, Citation2017). Recent research has developed the timeline technique to incorporate self-generated cues, finding that more correct details were reported in comparison to both the other-generated cues and no cues conditions (Kontogianni, Hope, Taylor, Vrij, & Gabbert, Citation2018). Such developments would be applicable to informant interviews as the timeline technique and self-generated cues benefit recall.
The present study
The perceptions and experiences of intelligence practitioners are key to developing an understanding of intelligence collection. However, to the authors’ knowledge, no research has been conducted on Source Handlers’ perceptions and experiences of the interviewing processes employed with informants in the UK. The present study attempted to address this gap by conducting interviews with 24 Source Handlers from a range of UK CTDSUs, and discussing the applicability of investigative interviewing research and practice to Source Handlers and informant interactions.
Method
Participants
After receiving ethical clearances from the first author’s university and research funders, 24 Source Handlers from a number of CTDSUs across England were recruited. 96% were male and 4% female. The participants’ experience as a Source Handler ranged from 1–15 years (M = 6.35, SD = 3.72) with their ages ranging from 33–59 years (M = 44.25, SD = 6.48). 50% of participants had received PEACE training, with their most recent training course ranging from 1994 to 2016. The participants in this study are the same sample as those from the authors’ previous work, which examined Source Handlers’ perceptions and experiences of building and maintaining rapport with informants (Nunan, Stanier, Milne, Shawyer, & Walsh, Citation2020).
Materials
A structured interview protocol (N = 32 questions) was employed and was divided into three large topics, (i) rapport (Nunan et al., Citation2020); (ii) interviewing processes (the present study); and (iii) provenance (the focus of further study). The data was divided into three topics due to the large quantity of qualitative data generated from the interviews, and because the research aimed to generate a number of thematic themes on each of the three topics. The present study explored the themes generated from the questions (n = 10; see Appendix 1) of subsection (ii) interviewing processes, which addressed the perceptions and experiences of interviewing processes employed with informants. Interviews were audio recorded and stored on a secure University drive.
Procedure
Access to the police officer sample was provided by the second author, through their contacts within each CTDSU, who acted as designated gatekeepers. The first author used a purposive sampling method, which involved contacting each CTDSU gatekeeper to set up structured interviews with HUMINT police officers who matched the inclusion criteria of regularly gathering intelligence from informants. Due to the operational commitments of the participants, the first author undertook the structured interviews in one of three ways; (i) audio recorded face-to-face interviews (n = 11); (ii) audio recorded telephone interviews (n = 4); or (iii) participants provided written responses via the designated gatekeeper’s email (n = 9), which resulted in a sample of 24. Interviews conducted by methods (i) and (ii) ranged between 19–55 min duration (M = 37.45, SD = 12.12), being later transcribed with the identifiable details redacted by the first and second author for data analysis. As the participants work within covert units, they were provided with the option to provide consent verbally before the audio recorded interview took place. Further, participants were required to read through and approve their own interview transcripts to ensure correct transcription, and to provide participants with the option to redact their transcript, if deemed inappropriate for open publication. Participants who responded via email had any identifiable details or operationally sensitive information redacted by their designated gatekeeper before it was sent to first author’s University email address.
Data analysis
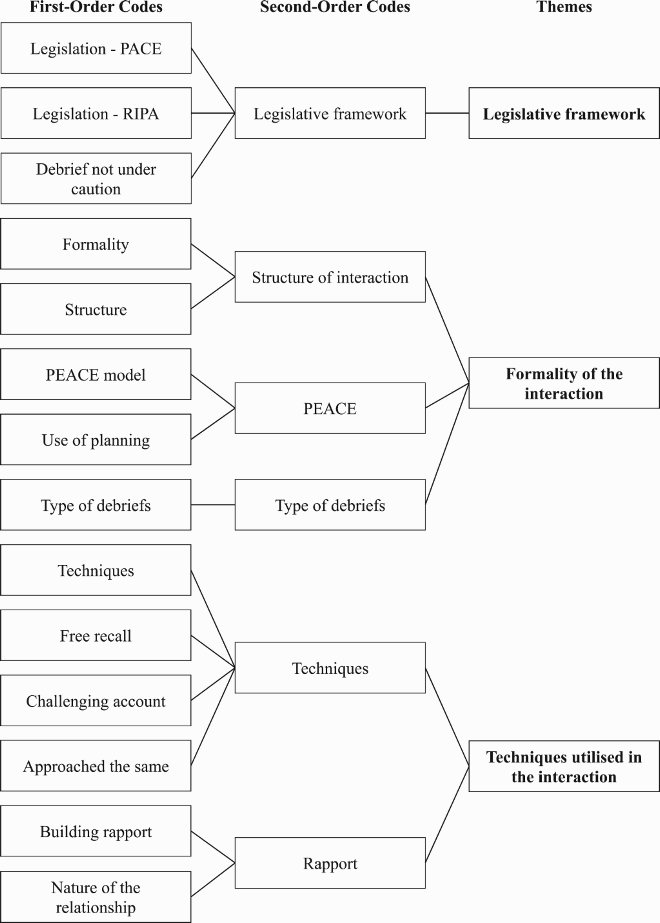
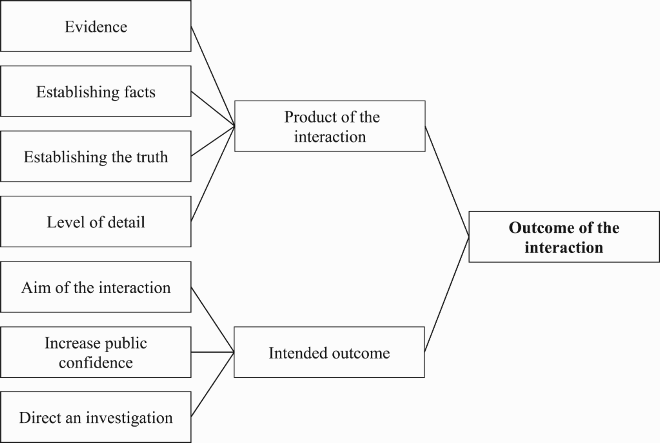
The qualitative responses were thematically analysed based on the guidance by Braun and Clarke (Citation2006), incorporating a deductive and inductive analysis process. The design of the interview protocol was initially deductive in nature, by exploring interviewing procedures, techniques and models. The responses were then analysed inductively, allowing themes to emerge. The data analysis process consisted of the following steps; (i) collating and listing the responses from participants under each question; (ii) the first and second authors thoroughly familiarised themselves with the transcriptions; (iii) a wealth of first-order codes were identified from the responses in an attempt to code every discussion point made by each participant; (iv) the abundance of first order codes were merged to create fewer second-order codes; and (v) second-order codes were combined further to establish five overarching themes which were then discussed and agreed upon with the second author (see Appendix 2 for an example of the thematic analysis process) Inter-rater reliability was undertaken during the coding process. An independent rater coded 10% of the transcripts from the first-order codes through to the final themes. A Cohen’s Kappa 0.87 was revealed between the two sets of scores, showing a strong strength of agreement (Robson & McCartan, Citation2016).
Results
Five themes were identified from the results: (i) a comparison between interviewing and debriefing; (ii) the PEACE model in intelligence interviews; (iii) the importance of effective communication; (iv) Source Handlers’ use of cognitive retrieval techniques; and, (v) Source Handler interview training. Exemplar quotations that best demonstrate the identified themes are discussed with reference to the psychological literature of police interviewing and cognitive retrieval techniques.
(i) A comparison between interviewing and debriefing
Participants were asked whether they believed that a difference exists between an investigative interview and an intelligence debrief with an informant. From the responses, four subthemes emerged; (a) legislative framework; (b) formality of the interaction; (c) techniques utilised in the interaction; and (d) outcome of the interaction.
(a) Legislative framework
In England and Wales, different legislation underpin police investigative interviewing and intelligence debriefs with informants. The former is controlled by the Police and Criminal Evidence Act Citation1984, which governs procedures for detaining and questioning suspects, while the latter falls under RIPA 2000. Participants commonly contrasted suspect interviewing with intelligence debriefs in regard to such legal rules. For example, Participant 2 stated:
There are strict rules about the way the investigative interview is undertaken (PACE 1984, tape recording, access to legal advice etc). Debriefing is usually about securing historical information about an event that has already happened or about people of interest to law enforcement. There is no requirement to adhere to PACE 1984 rules although any subsequent tasking may require consideration of RIPA 2000. (Participant 2)
(b) Formality of the interaction
This theme was reported as a further difference, especially when participants compared a suspect interview with an informant debrief. Participants explained that the points to prove element of an investigative interview (the required pieces of evidence to prove the offence in question has taken place), due to a specific criminal offence or number of offences being investigated, requires a more formal interview, preceded by advice as to the interviewee’s legal rights. In contrast, an informant debrief was perceived as a more informal interaction, which does not have to be conducted before the 24-hour custody clock expires, PACE 1984. For example;
The investigative interview in my view within the police they take part in a particular format, in a particular location, for a particular reason for an evidential gathering purpose to establish a particular fact, whereas a debrief isn’t that, it can be at any location, on any situation, at any given time. (Participant 22)
(c) Techniques utilised in the interaction
With regards to the techniques used during the two forms of interactions, the key difference reported by the participants was the lack of challenging of the account within debriefs in comparison to interviews, where officers are trained to challenge when, for example, inconsistencies in an account remain unresolved after seeking clarifications from a suspect:
The investigative interview, you’re looking at achieving sort of evidence by questioning, you’re looking at challenging discrepancies, whereas in a debrief there’s less of a challenge … it’s very much a recall, a detailed recall, but it’s very much just a, what have you experienced, what have you seen, what have you heard, when have you heard it, it’s more of a witness interview as opposed to a suspect interview. (Participant 15)
(d) Outcome of the interaction
Half of the participants highlighted the differences in outcome of the interactions. While information received from suspects in an investigative interview would be treated as evidence, gathered intelligence was no more than actionable information. Nevertheless, despite such different labels, participants reported that both an investigative interview and an intelligence debrief are essentially one and the same:
Both are there to seek the truth and to try and validate … I think they come from the same skill set, I think the similarities are more than the differences, both are there to try and underpin it and to corroborate that account so I think the term debrief is another word for an investigative interview so having thought about it now I think my view is they are the same but with different labels. (Participant 24)
(ii) The PEACE model in intelligence interviews
Participants highlighted a range of techniques associated with the PEACE model of interviewing. This theme derived from the participants’ discussions concerning the importance of planning, interviewing flexibility, interview/debrief objectives, and the evaluation of the intelligence gathered (i.e. provenance). Participant 24 advocated the PEACE model:
Motivational questions are the two stock and trade, if you’re not using the PEACE plan I don’t think there is a better one that I am aware … you can’t just rock up and hope it all works out for you, but if you plan it, if you sit there and plan your interview, no matter how good an interviewer you are, you’ve got a fine chance if you’ve planned your interview. (Participant 24)
I would say actually planning is under used and then actually thinking about the structure of your interview, I think too many people still think they don’t need a plan, I know what I am doing, go in and talk, and actually when they come out and you say, what did they say about this? Ah I didn’t ask them about that, well why didn’t you because that was part of that plan? So, I think the planning … we will say right ok who’s going to do what? What are we going to do? What’s the aims of this interview? Why are we having this meet today? What do we want to get from it? (Participant 18)
A lot of focus around, how do you know that?, why do you know that?, who else knows that?, and sort of again there is a lot of focus on risk when you’re speaking to people. (Participant 12)
(iii) The importance of effective communication
Effective communication should flow throughout an interaction with an informant, spanning across the Engage and Explain, Account and Closure phases. In particular, the Account phase, underpinned by an uninterrupted account, encourages the use of relevant and varied cognitive retrieval techniques to retrieve additional information (Clarke & Milne, Citation2016; Shepherd & Griffiths, Citation2013). The Account phase is also where questions are asked to prompt the informant to provide clarity and greater detail to the initial account.
Participants referenced active listening as a frequently used skill. This skill links heavily to an uninterrupted free recall phase, allowing the informant to talk freely. Active listening not only allows the Source Handler to absorb the information, but to also demonstrate that they are interested in what the informant has to say.
Giving people that time to answer, not interrupting, so I think that the skills we are taught, good interviewer, good handler will use those. (Participant 24)
Well that open recall, and then the recall probe, after that you’ve had what you’ve got from them, you feel like you’ve got everything from it and then it’s that drilling down on the accuracy of it, just exactly what was it that was said, what exactly was done, and then it’s just seeking that same probing to get the provenance of it. (Participant 16)
Participants also stated that once the Source Handler has exhausted their open questions, the use of probing and recapping topic areas was considered to be a frequently used interviewing technique.
Depends on your sources, you can’t say there is one [memory technique] you use frequently because each person is different, you have to identify what works for your source. (Participant 11)
(iv) Source Handlers’ use of cognitive retrieval techniques
Participants commonly perceived interviewing techniques to incorporate a range of cognitive retrieval techniques and some elements of the CI. Probing an informants’ account was supported by a range of cognitive retrieval techniques to enhance the information obtained.
Debriefing, eliciting of information so it’s more conversational than anything else, but it does come to a particular point when you’re looking at specifics that you then go through that process of actually interviewing, picking up on pertinent points and making those particular notes, revisiting them. (Participant 21)
Open recall more than anything else because it’s a nice easy relaxed way … if you try and force it you either corrupt memory or you get them to forget things, they rush past it because they are trying to get that information out, so just letting them to, again it’s conversational, just allow them to remember it and the little triggers that are important to them. (Participant 21)
The most popular technique would be to ask the source to put themselves back in the place and describe everything about the situation and how they felt. This may involve asking them to close their eyes and relax. (Participant 7)
Rather than them sitting there talking to us and us writing it down basically, so just whatever best helps them communicate, you know it might be better they actually have a bit of pen and paper and draw what they are actually talking about, things like that are probably under used and something we don’t necessarily always think of at the time. (Participant 12)
The cognitive interview is a very effective tool, you know for ABE [a guidance document developed to assist those responsible for interviewing victims and witness] … I’ve interviewed someone for a week before I was involved as a Tier 5 [an interview advisor], we interviewed her for a week and it was just amazing the amount of stuff she came out with … do we get to sit down for a week and do a 2 hour session in the morning and a 2 hour session in the afternoon [with an informant], no, that’s not real life … checking they’re safe and well that’s a standing order, you know the things they are interested in you haven’t forgot about, the kids, the exams, the car broke down, when it actually knuckles down into the core business time, it’s quite tight, it’s tighter than you might think. (Participant 24)
(V) Source Handler interview training
An apparent lack of exposure to psychological research-based techniques was evident from the current participants’ comments. Participants reported that techniques to assist memory recall must exist but there was a lack of training on this topic and ‘refreshers’ through continuous professional development days are needed for Source Handlers to embed such techniques into practice:
In honesty I am sure there are plenty because I don’t think we are necessarily exposed to that many kind of techniques … I don’t think we use them routinely enough at all. (Participant 17)
By some people yes and by others not, because they have not done it [CI training], so they probably don’t know about it, it’s probably a better tool to use in intelligence gathering than it is in some victim based scenarios because actually sometimes what you might take a victim back to might not be the most pleasant thing. (Participant 18)
None of the participants discussed using an entire CI with an informant. This is most likely due to the CI’s lengthy process (Dando et al., Citation2009) and the majority of interactions Source Handlers have with their informant are shorter in comparison to investigative interviews.
I suppose we do free recall, taking them back and yeah we do a bit of that, but sometimes you’ve got to know the individual and you’ve got to that stage through the rapport … down the line then your relationship is so good with them that you can say right I need that, let’s go back … and it can become more of an investigative interview once the relationship is built down the track. (Participant 13)
Everybody’s an individual, everybody’s different so everybody has different aspects of what they want to do, your informants are all different, and you have to assess them to see what works for them … I wouldn’t say one boot fits all. (Participant 11)
Discussion
This study explored police Source Handlers’ perceptions of informant interviewing processes. The findings highlighted an overlap between the underlying psychological principles of intelligence debriefing and investigative interviewing. The sample acknowledged the obvious differences between the two types of interactions, particularly the formality, legislative oversight, and evidence versus intelligence collection. Despite the acknowledged differences, both forms of interaction strive to collect reliable, timely and detailed information from a human source, which can be achieved by using the same cognitive retrieval techniques (Fisher & Geiselman, Citation2019). For example, modified CIs, sketch plans (Dando et al., Citation2009; Eastwood et al., Citation2019), the timeline technique (Hope et al., Citation2013), and self-generated cues (Leins et al., Citation2014). Therefore, there are good grounds for the implementation of cognitive retrieval techniques into HUMINT practices (see Meissner et al., Citation2017), underpinned by the PEACE model approach.
As outlined by the first phase of the PEACE model, and emphasised by previous research (Clarke & Milne, Citation2016; Walsh & Bull, Citation2010; Walsh & Milne, Citation2008), interview Planning and Preparation provides a foundation for a successful interaction. Planning for an upcoming informant interaction may also assist a Source Handler to use research-based techniques during the Account phase. Additionally, the Planning and Preparation phase could be utilised to organise lengthier face-to-face meetings, to provide the Source Handler with ample time to use a range of cognitive retrieval techniques with the informant.
The application of the PEACE model to intelligence gathering should encourage a flexible interviewing structure, which utilises rapport building (Walsh & Bull, Citation2010) to gain a detailed and reliable account (Stanier & Nunan, Citation2018). The promotion of a more detailed recall concerning the information shared by the informant can also support the process of ‘provenancing’ the gathered intelligence, especially when an open to closed questioning approach is utilised, underpinned by effective communication, and cognitive retrieval techniques (Milne & Bull, Citation1999).
Additionally, participants noted Source Handlers are likely to have an individual approach to gathering HUMINT. This may provide further support for implementing the PEACE model into informant interactions, especially as the PEACE model’s ethos incorporates a flexible interviewing approach. Conversely, the different communication approaches to informant interactions the Source Handler’s alluded to may highlight a diverse level of interviewing knowledge and ability across the sample. For example, participants did not commonly perceive interviewing techniques to incorporate a range of cognitive retrieval techniques and a number of interviewing techniques were reported by participants as being underused, and there was some confusion over CM (see Shepherd & Griffiths, Citation2013) elements such as the challenge phase, which was mentioned as a CI technique.
The upskilling of Source Handlers should promote the use of open questioning, highlight the importance of active listening, and provide the Source Handler with an armoury of cognitive retrieval techniques (Kontogianni et al., Citation2018; Leins et al., Citation2014). Participants who stated they do not regularly, or have not used, cognitive retrieval techniques, including elements of the CI, may not be maximising intelligence gathering opportunities. It may also be considered best practice to utilise techniques such as the timeline technique (Hope et al., Citation2013) and self-generated cues (Wheeler & Gabbert, Citation2017) in place of summarising. If those Source Handlers who view investigative interviews and debriefs as entirely separate interactions were to perceive them as underpinned by the same psychological and practical foundations, this may generate a further appreciation for the psychology of information gathering. In turn, this may encourage an ethos of interview planning and promote an evidence-based approach.
It is important to discuss the use of cognitive retrieval techniques with context, as HUMINT practices often take place with short time constraints, whereby statutory safety and welfare concerns take priority. Hence, this article aimed to promote the effectiveness and suitability of existing interviewing practices realistically applicable to HUMINT interactions, by highlighting the need for a toolbelt of cognitive retrieval techniques, deployable within the Engage and Explain and Account phase of a PEACE intelligence interview. Whilst safety and welfare of the informant and Source Handler must take priority, the gathering of intelligence is the raison d’être for informants, so effective interviewing practices should also be considered a vital responsibility for Source Handlers.
Currently, central Source Handler training in the UK includes little mention of interviewing techniques. This tallies with the perceptions of the Source Handler sample. The concerns which have been highlighted are justified, as the training regime does not appear to cater sufficiently to the Source Handler’s specialised role. A training programme specifically focused on intelligence interviewing needs to be developed to complement the existing Source Handler training course. As the benefits of training can fade over time or be applied inaccurately, interview training should be reinforced through continuing professional development and reviews (Griffiths & Walsh, Citation2018). Taken together, the adoption of the PEACE model and a toolbelt of cognitive retrieval techniques for intelligence interviews, all supported by a training programme is the starting point in enhancing and professionalising a specialised area of intelligence practice.
Limitations and future direction
The study acknowledges that a small sample of police officers were interviewed. Though, due to the specialist area of policing (CTDSU), and use of qualitative methodology to understand the sample’s perceptions and experiences, the themes identified provide a new insight into covert intelligence practices. As a result of researching operational covert police officers, a pragmatic approach to data collection was required. Therefore, the different methods of data collection may have impacted upon some responses, especially as email responses were occasionally less detailed than face-to-face and telephone interactions. It must be also noted that this research concerns participants’ perceptions rather than observations and evaluations of their actual behaviour (Robson & McCartan, Citation2016). Perceptions of how often interviewing techniques are used and their effectiveness may differ from their actual practices. Therefore, research should analyse actual audio recorded phone interactions between Source Handlers and informants. Future research should also explore informants’ perceptions and experiences of their interactions with Source Handlers.
The lack of awareness and training from DSU staff regarding research on the gathering of intelligence is concerning and should be addressed by reviewing and redesigning informant-related training packages. This will require additional research-based techniques to be incorporated into the original Source Handler training, continuous professional development, written guidance, and the potential for bolt-on courses on intelligence interviewing. Where security permits, interactions should be peer reviewed either directly or remotely by trained assessors (Griffiths & Walsh, Citation2018). Moreover, academic institutions need to make their research accessible to policing practitioners. Professionalising UK intelligence practices requires a reenergised and prioritised working relationship between academics, intelligence practitioners and operational trainers. The resultant policy and practice should adopt an evidence-based approach to intelligence interviewing.
Acknowledgements
The authors wish to thank all police officers who took the time to participate, as without them this research would not have been possible. This research forms part of the doctoral work of the first author who is in receipt of a doctoral studentship funded by the Centre for Research and Evidence on Security Threats (ESRC Award: ES/N009614/1).
Disclosure statement
No potential conflict of interest was reported by the author(s).
Correction Statement
This article has been republished with minor changes. These changes do not impact the academic content of the article.
Additional information
Funding
Notes
1 For the purposes of this article, the term interviewing is used in its broadest sense to include an intelligence interaction between a police Source Handler (the interviewer) and an informant who may have information of interest (the interviewee).
2 While the PEACE model continues to be the police framework for investigative interviewing (see College of Policing, Citation2019), it is not underpinned by statutory legislation or specific codes, unlike the management of CHIS.
References
- Alison, L. J., Alison, E., Noone, G., Elntib, S., & Christiansen, P. (2013). Why tough tactics fail and rapport gets results: Observing rapport-based Interpersonal techniques (ORBIT) to generate useful information from terrorists. Psychology, Public Policy, and Law, 19(4), 411–431. doi: 10.1037/a0034564
- Billingsley, R., Nemitz, T., & Bean, P. (2001). Informers-Policing, policy and practice. Cullompton: Willan Publishing.
- Braun, V., & Clarke, V. (2006). Using thematic analysis in psychology. Qualitative Research in Psychology, 3(2), 77–101. doi:10.1191/1478088706qp063oa
- Central Planning and Training Unit. (1992). Investigative interviewing: A guide to interviewing. London: Home Office.
- Clarke, C., & Milne, R. (2016). Interviewing suspects in England and Wales: A national Evaluation of PEACE interviewing: One decade later. In D. Walsh, G. Oxburgh, A. Redlich, & T. Mykleburst (Eds.), International developments and practices in investigative interviewing and interrogation, vol 2. Suspects (pp. 101–118). London: Routledge.
- College of Policing. (2019). Investigative Interviewing. Retrieved from https://www.app.college.police.uk/app-content/investigations/investigative-interviewing/
- Dando, C., Wilcock, R., & Milne, R. (2009). The cognitive interview: The efficacy of a modified mental reinstatement of context procedure for frontline police investigators. Applied Cognitive Psychology, 23, 138–147. doi: 10.1002/acp.1451
- Eastwood, J., Snook, B., & Luther, K. (2019). Establishing the most effective Way to Deliver the sketch Procedure to enhance interviewee free recall. Psychology, Crime & Law, 1–26. doi: 10.1080/1068316X.2018.1538416
- Evans, J. R., Meissner, C. A., Brandon, S. E., Russano, M. B., & Kleinman, S. M. (2010). Criminal versus HUMINT interrogations: The importance of psychological science to improving interrogative practice. The Journal of Psychiatry & Law, 38(1–2), 215–249. doi: 10.1177/009318531003800110
- Fisher, R. P., & Geiselman, R. E. (1992). Memory-enhancing techniques for investigative interviewing: The cognitive interview. Springfield: Charles C Thomas Publisher.
- Fisher, R. P., & Geiselman, R. E. (2019). Expanding the cognitive interview to Non-criminal Investigations. In J. J. Dickinson, N. Schreiber Compo, R. Carol, B. L. Schwartz, & M. McCauley (Eds.), Evidenced-Based investigative interviewing: Applying cognitive principles (pp. 1–28). New York: Routledge.
- Grieve, J. G. D. (2004). Developments in UK criminal intelligence. In J. H. Ratcliffe (Ed.), Strategic thinking in criminal intelligence (pp. 25–36). Sydney: The Federation Press.
- Griffiths, A., & Walsh, D. (2018). Qualitative analysis of qualitative evaluation: An exploratory examination of investigative interviewers’ reflections on their performance. Psychology, Crime & Law, 24(4), 433–450. doi: 10.1080/1068316X.2017.1390115
- Home Office. (2018). Covert Human Intelligence Sources, Revised Code of Practice. Retrieved from https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/742042/20180802_CHIS_code_.pdf
- Home Office. (2019). Police and Criminal Evidence Act 1984 (PACE) codes of practice. Retrieved from https://www.gov.uk/guidance/police-and-criminal-evidence-act-1984-pace-codes-of-practice
- Hope, L., Mullis, R., & Gabbert, F. (2013). Who? What? When? Using a timeline technique to facilitate recall of a complex event. Journal of Applied Research in Memory and Cognition, 2(1), 20–24. doi: 10.1016/j.jarmac.2013.01.002
- Kontogianni, F., Hope, L., Taylor, P. J., Vrij, A., & Gabbert, F. (2018). The benefits of a self-generated cue mnemonic for timeline interviewing. Journal of Applied Research in Memory and Cognition, 7(3), 454–461. doi: 10.1016/j.jarmac.2018.03.006
- Leins, D. A., Fisher, R. P., Pludwinski, L., Rivard, J., & Robertson, B. (2014). Interview protocols to facilitate human intelligence sources’ recollections of meetings. Applied Cognitive Psychology, 28(6), 926–935. doi: 10.1002/acp.3041
- Meehan, N., Kelly, C. E., & McClary, M. (2019). The snitching hour: Investigations and interviewing in a county jail. Security Journal, 32(3), 198–217. doi: 10.1057/s41284-018-0157-y
- Meissner, C. A., Surmon-Böhr, F., Oleszkiewicz, S., & Alison, L. J. (2017). Developing an evidence-based perspective on interrogation: A review of the U.S. Government’s high-value detainee interrogation group research program. Psychology, Public Policy, and Law, 23(4), 438–457. doi: 10.1037/law0000136
- Memon, A., Meissner, C. A., & Fraser, J. (2010). The cognitive interview: A meta-analytic review and study space analysis of the past 25 years. Psychology, Public Policy, and Law, 16(4), 340–372. doi: 10.1037/a0020518
- Milne, R., & Bull, R. (1999). Investigative interviewing: Psychology and practice. Chichester, England: Wiley.
- Milne, R., & Bull, R. (2002). Back to basics: A componential analysis of the original cognitive interview mnemonics with three age groups. Applied Cognitive Psychology: The Official Journal of the Society for Applied Research in Memory and Cognition, 16(7), 743–753. doi: 10.1002/acp.825
- Nunan, J., Stanier, I., Milne, R., Shawyer, A., & Walsh, D. (2020). Eliciting human intelligence: Police source handlers’ perceptions and experiences of rapport during covert human intelligence sources (CHIS) interactions. Psychiatry, Psychology and Law, 1–27. doi: 10.1080/13218719.2020.1734978
- Oleszkiewicz, S., Granhag, P. A., & Kleinman, S. M. (2017). Eliciting information from human sources: Training handlers in the Scharff technique. Legal and Criminological Psychology, 22(2), 400–419. doi:10.1111/lcrp.12108
- Police and Criminal Evidence Act. (1984). (EW). http://www.legislation.gov.uk/ukpga/1984/60/contents
- Redlich, A. D., Kelly, C. E., & Miller, J. C. (2014). The who, what, and why of human intelligence gathering: Self-reported measures of interrogation methods. Applied Cognitive Psychology, 28(6), 817–828. doi: 10.1002/acp.3040
- Regulation of Investigatory Powers Act. (2000). (EW). http://www.legislation.gov.uk/ukpga/2000/23/contents
- Robson, C., & McCartan, K. (2016). Real world research. Chichester: John Wiley & Sons.
- Russano, M. B., Narchet, F. M., Kleinman, S. M., & Meissner, C. A. (2014). Structured interviews of experienced HUMINT interrogators. Applied Cognitive Psychology, 28(6), 847–859. doi: 10.1002/acp.3069
- Shepherd, E., & Griffiths, A. (2013). Investigative interviewing: The conversation management approach. Oxford: Oxford University Press.
- Stanier, I. P., & Nunan, J. (2018). Reframing intelligence interviews: The applicability of psychological research to HUMINT Elicitation. In A. Griffiths, & R. Milne (Eds.), The psychology of criminal Investigation: From theory to practice (pp. 226–248). London: Routledge.
- Walsh, D., & Bull, R. (2010). What really is effective in interviews with suspects? A study comparing interviewing skills against interviewing outcomes. Legal and Criminological Psychology, 15(2), 305–321. doi: 10.1348/135532509X463356
- Walsh, D., & Bull, R. (2012). Examining rapport in investigative interviews with suspects: Does its building and maintenance work? Journal of Police and Criminal Psychology, 27(1), 73–84. doi: 10.1007/s11896-011-9087-x
- Walsh, D. W., & Milne, R. (2008). Keeping the PEACE? A study of investigative interviewing practices in the public sector. Legal and Criminological Psychology, 13(1), 39–57. doi: 10.1348/135532506X157179
- Wheeler, R. L., & Gabbert, F. (2017). Using self-generated cues to facilitate recall: A narrative review. Frontiers in Psychology, 8(1830), 1–15. doi: 10.3389/fpsyg.2017.01830
Appendix
Appendix 1: Interview Protocol
1. Do you believe there is a difference between an investigative interview and a de-brief? Please explain in full detail
2. What interview techniques are commonly used during an intelligence gathering interview/debrief?
3. What interview techniques should be used during an intelligence gathering interview/debrief?
4. Are memory techniques used during an intelligence gathering interview/debrief?
5. Are there any memory techniques which are used most frequently during an intelligence gathering interview/debrief?
6. Are there any memory techniques which are used least frequently during an intelligence gathering interview/debrief?
7. Is the Cognitive Interview regularly used during an intelligence gathering interview/debrief?
8. Is there an element of the Cognitive Interview which is used most frequently during an intelligence gathering interview/debrief?
9. Is there an element of the Cognitive Interview which is used least frequently during an intelligence gathering interview/debrief?
10. Are there any techniques which are under used?
Appendix 2: Thematic Analysis example for ‘Interviewing versus Debriefing’