?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
In this paper, the observer-based PID control problem is studied for linear discrete-time systems subject to hybrid cyber attacks. Two sets of Bernoulli distributed stochastic variables are utilized to characterize the random nature of the false data injection attack and the replay attack. A sector-like bounded condition is exploited to constrain the malicious signal in the false data injection attack which reflects the certain tolerable bound on the difference between the attack signal and the true signal. Sufficient conditions for the existence of the expected observer-based
PID controller are given to ensure the exponential mean-square stability and the
performance. Then, the controller parameters are calculated by solving a matrix inequality. Finally, a simulation example is employed to demonstrate the effectiveness of the proposed control algorithm.
1. Introduction
In the past decades, the proportional-integral-derivative (PID) control has played a ruling role in practical engineering due to the advantages like ease of hardware implementation (Ang et al., Citation2005, july; Åström et al., Citation1993; Zhao et al., Citation2018; Zhuang & Atherton, Citation1993). In the PID control, there are three parameters which need to be adjusted, that is, the proportional parameter, the integral parameter and the derivative parameter. The parameter tuning of the PID control affects the system performance such as robustness and stability. Therefore, the issue of parameter tuning has been an active discussion topic and plenty of research results have been obtained, see e.g. Rosinová and Veselý (Citation2007), Silva et al. (Citation2002), Takahashi et al. (Citation1997), Ying (Citation2000) and the references therein.
In most of the studies concerning the PID control problem, there is an implicit assumption that the state of the controlled system is directly available. Nevertheless, such an assumption is not always true in reality. In the circumstances, it is inevitable to construct the state once again by using the available measurement output. Recently, various kinds of algorithms for state observers have been put forward and applied in system observation (Basin, Ramírez, et al., Citation2018), closed-loop feedback controller design (Basin, Yu, et al., Citation2018; Lien, Citation2004), robust adaptive unknown input observer (Soleymani et al., Citation2020), observer-based consensus control (Ding et al., Citation2017b) and so on. On the other hand, in the traditional PID control algorithm, the impact of the external disturbance has always been ignored, which results in poor robustness to the external disturbance. To improve the robustness of the PID control scheme, considerable research results have been obtained (Zhao et al., Citation2018; Zhao, Wang, Ding, et al., Citation2020; Zhao, Wang, Wei, et al., Citation2020).
In another research frontier, the networked control system (NCS), with the improvement of the wireless communication technology, has been comprehensively studied in the past decades (Cetinkaya et al., Citation2017; Chen et al., Citation2018; Huang et al., Citation2012; Y. Li et al., Citation2015; Mousavinejad et al., Citation2018; Peng et al., Citation2018; Zhu & Martínez, Citation2014). In the NCS, when the communication network is not protected by the security protections, the signals transmitted through the communication network are vulnerable to the network threats. Among various network threats to the NCS, the cyber attacks aim to spitefully destroy the normal operation of the system by intercepting, falsifying or deleting some crucial data. In recent years, there is an increase of interest on the research of control problem subject to cyber attacks, see Zhao, Wang, Wei, et al. (Citation2020), Ding et al. (Citation2017b), An and Yang (Citation2018, january), Bai et al. (Citation2017), and M. Zhang and Lin (Citation2020).
In this paper, we mainly focus on two types of cyber attacks, namely, the false data-injection (FDI) attack and the replay attack. The FDI attack is known as one of the most dangerous attacks, where the attacker replaces the transmitted information in order to tamper the completeness of data (Yuan & Xia, Citation2018). Recently, the control problem for networked systems under FDI attack has received interest from researchers. For example, in Jin et al. (Citation2017) and Zhao and Yang (Citation2020), adaptive secure control schemes under the FDI attack have been designed. In Bai et al. (Citation2017) and Ding et al. (Citation2018), the control problems under the randomly occurring FDI attack have been studied. As for the replay attack, the attacker records the past transmitted information and injects the recorded information into the system, which leads to extra difficulty in detecting the attack. Up to now, the control problem for systems under the replay attack has also received attention from researchers. For example, a recording-horizon control scheme has been designed to tackle the replay attack in Zhu and Martínez (Citation2014). In Mo et al. (Citation2014), in order to detect whether the system is under replay attack, additional Gaussian signals have been injected into the system. It is worth mentioning that, in most of the existing literature concerning control problems under cyber attacks, only one type of cyber attack has been considered. Nevertheless, in real world, the system may be subject to more than one type of cyber attacks. As such, it is of practical significance to investigate control problem for systems under hybrid cyber attacks.
Motivated by the above discussion, the purpose of this paper is to study the observer-based PID control problem for linear discrete-time systems under hybrid cyber attacks. Three important problems that need to be answered are listed as follows: (1) how to set up an appropriate mathematical model to characterize the FDI attack and the replay attack simultaneously? (2) how to reduce the influence of the hybrid attacks on the performance for the discrete-time system? (3) how to select a suitable and engineering-oriented constraint to characterize the malicious signal considered in this paper? Thus, effort is made to conduct the specific research and solve these problems in this paper.
The main contributions of this paper are underlined as follows: (1) both the FDI attack and the replay attack are considered which caters for the real practice; (2) a novel mathematic model is designed to characterize the FDI attack and the replay attack; and (3) by using the Lyapunov stability theory, an observer-based PID controller is designed which guarantees the desired performance.
The remainder of this paper is outlined as follows. In Section 2, the linear discrete-time system under the hybrid cyber attacks is formulated. In Section 3, the observer-based PID control scheme is carried out. Asimulation example is conducted in Section 4 and the conclusion is given in Section 5.
Notation
The notation utilized in this paper is fairly normative except where otherwise declared. For a matrix W, and
denote the transpose and the orthogonal basis of the null space, respectively. The space of square summable sequences is depicted by
. The symbol ⊗ represents the Kronecker product. In a symmetric matrix, an asterisk * describes a term induced by symmetry. I and 0 show, respectively, the identity matrix and zero matrix with appropriate dimensions.
stands for the expectation of stochastic variable x. For symmetric matrices X and Y,
means that X−Y is non-negative definite, and X>Y means that X−Y is positive definite.
2. Problem formulation
Consider a discrete-time linear system described by:
(1)
(1) where
is the system state,
is the control input,
is the external disturbance,
is the measurement output,
is the control output, and A, B, C, D, E, F are known real constant matrices with appropriate dimensions.
2.1. Observer-based PID controller
In this paper, an observer-based PID controller is designed as follows:
(2)
(2) where
is the estimate of
and
is the output of the controller.
,
,
are the controller gains to be designed and L is the observer gain to be designed. q is a known positive constant which is determined according to practical engineering.
Remark 2.1
In this paper, an observer-based PID controller is constructed whose input is the state estimate and the output is the sum of three parts, among which are the P (proportional term), the I (integral term) and the D (differential term). To be precise, the main procedure of designing the desired PID controller is first to estimate the immeasurable system state, and then utilize the state estimate signal to perform the state-feedback control. Moreover, a time-window with limited length is applied in the integral term for the sake of reducing computation burden.
2.2. The cyber attack model
During the transmission from the controller to the actuator, the control signal is subject to random hybrid cyber attacks. The real control input is modelled as
(3)
(3) where
is the control input received by the actuator,
is the hybrid attack signal which is defined later, and
is a Bernoulli distributed random variable that satisfies
The hybrid attack
contains the FDI attack and the replay attack and is modelled as follows:
(4)
(4) where
is the FDI attack signal satisfying the following condition:
(5)
(5) with G being a known real matrix and
being a known real constant.
stands for the replay attack signal with
where
and
are non-negative integers.
is a Bernoulli distributed random variable that satisfies
Remark 2.2
In this paper, hybrid cyber attacks are injected into the transmission from the controller to the actuator by the adversary. The hybrid attack contains the FDI attack and the replay attack. From the defenders' perspective, the attacks could occur in an intermittent or random manner. To reflect such a practical situation, we utilize two Bernoulli sequences with known statistical information to characterize the random occurrence of the FDI attack and the replay attack. On the other hand, in practice, the adversary generally does not have infinite energy and launch unbounded attack arbitrarily. Then, as for the adversary, it makes practical sense to assume simultaneously that the injected false signal
is sector-like bounded and the time of the recorded past signal
is within a certain range.
Denoting
−
as the estimation error, we have
(6)
(6) Under the controller (Equation2
(2)
(2) ), the augmented system is shown as follows:
(7)
(7)
where
The aim of this paper is to design an
PID controller for the linear discrete-time systems under hybrid cyber attacks such that:
the zero-solution of the closed-loop system (Equation7
(7)
(7) ) with
is exponentially mean-square stable;
under zero initial condition, for all nonzero
, the control output
satisfies the
performance constraint:
(8)
(8) where
is a given scalar standing for the disturbance attenuation level.
3. Main results
3.1. Stability and 
 performance analysis
performance analysis
In this section, an observer-based PID controller (Equation2
(2)
(2) ) is designed for the system (Equation1
(1)
(1) ) under the hybrid cyber attacks (Equation3
(3)
(3) ). Sufficient conditions are given in Theorems 3.1–3.2 to guarantee the exponential mean-square stability and the
performance, respectively. Then, the desired PID controller parameters are derived in Theorem 3.3.
Theorem 3.1
Let ,
,
and L be given. The zero-solution of the system (Equation7
(7)
(7) ) is exponentially mean-square stable with
if there exist positive definite matrices P,
, R and U such that
(9)
(9) where
Proof.
Choosing the following Lyapunov functional:
(10)
(10) where
Calculating the difference of
with
, one has
(11)
(11)
(12)
(12)
(13)
(13)
and
(14)
(14) According to (Equation11
(11)
(11) )–(Equation14
(14)
(14) ), we have
(15)
(15) From the constraint (Equation5
(5)
(5) ), we know that there exists a real number
such that
(16)
(16) In terms of (Equation16
(16)
(16) ), we further obtain
(17)
(17) where
With the help of the Schur Complement Lemma, it is known that
can be ensured by (Equation9
(9)
(9) ). Then, there exists a positive scalar
such that
(18)
(18) By following the similar analysis in Wang et al. (Citation2017), the system (Equation7
(7)
(7) ) is exponentially mean-square stable. The proof is complete.
In Theorem 3.1, the exponential mean-square stability of the system (Equation7(7)
(7) ) is analyzed. In the following theorem, the
performance of the system (Equation7
(7)
(7) ) will be considered.
Theorem 3.2
Let the disturbance attenuation level and the controller gain matrices be given. The system (Equation7
(7)
(7) ) is exponentially mean-square stable and satisfies the
constraint (Equation8
(8)
(8) ) if there exist positive definite matrices P,
, R and U such that
(19)
(19) where
Proof.
It is obvious that (Equation19(19)
(19) ) implies (Equation9
(9)
(9) ), then the system (Equation7
(7)
(7) ) is exponentially mean-square stable. Now, let us prove that the system (Equation7
(7)
(7) ) satisfies the
constraint under the zero-initial condition.
Choosing the Lyapunov functional as (Equation10(10)
(10) ), we have
where
By applying the Schur Complement Lemma, one can see from (Equation19
(19)
(19) ) that
, which implies
(20)
(20) Summing up (Equation20
(20)
(20) ) from 0 to ∞ with respect to k, one has
(21)
(21) which completes the proof.
3.2. PID controller design
In this subsection, the solution to the observer-based PID control problem is presented for linear discrete-time systems subject to hybrid cyber attacks.
Theorem 3.3
Let the disturbance attenuation level be given. The system (Equation7
(7)
(7) ) is said to be exponentially mean-square stable and satisfies the
performance condition (Equation8
(8)
(8) ) with
if there exist positive definite matrices
,
, R, U and matrices
,
,
,
,
,
,
as such:
(22)
(22) where
Moreover, the gain matrices of the controller (Equation2
(2)
(2) ) can be calculated by
(23)
(23)
Proof.
First, we denote
Pre- and post- multiplying inequality
in (Equation19
(19)
(19) ) by diag
and its transposition, one has
(24)
(24) where
Noting that
(25)
(25) the inequality (Equation24
(24)
(24) ) holds if and only if
(26)
(26) Make the following expressions:
(27)
(27) Therefore, taking (Equation26
(26)
(26) ) into consideration, it follows that (Equation19
(19)
(19) ) holds if (Equation22
(22)
(22) ) is true. The proof is now complete.
Remark 3.1
For a kind of discrete-time linear systems subject to hybrid attacks, the designed observer-based PID controller can guarantee that the closed-loop system satisfies both the exponential mean-square stability and the
performance. Furthermore, the gain matrices of the PID controller could be computed conveniently via solving the LMI (Equation22
(22)
(22) ).
Remark 3.2
In this paper, an observer-based PID controller has been designed for discrete-time systems under hybrid cyber attacks. The novelties of this paper are displayed as follows: (1) both the FDI attack and the replay attack have been taken into consideration; and (2) the malicious signal in FDI attack is characterized by the bounded condition which caters for the practical engineering.
4. An illustrative example
In this section, a numerical example is given to show the effectiveness of the developed observer-based PID control scheme.
Consider a system (Equation1(1)
(1) ) whose parameters are given as follow:
The disturbance attenuation level γ is set as 0.97. The occurring probability of the hybrid attacks is set to be
and
is chosen as
which means that the probability of the FDI attack is 0.6. The malicious signal
is chosen as
which satisfies the bounded constraint (Equation5
(5)
(5) ) with G = 1 and
. The integral length q is 3. Meanwhile, the external disturbance is set as
.
Using the YALMIP toolbox in Matlab to solve the matrix inequality (Equation22(22)
(22) ), the parameters of the controller are obtained as follows:
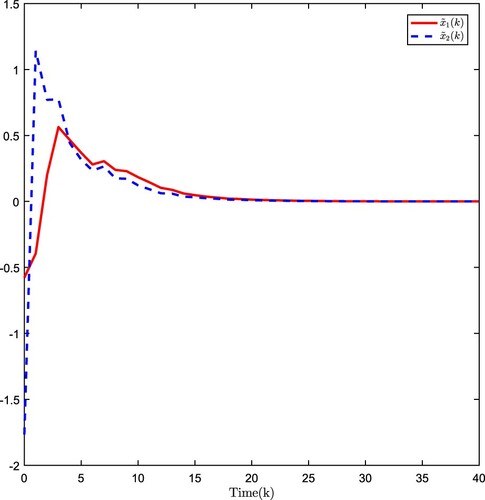
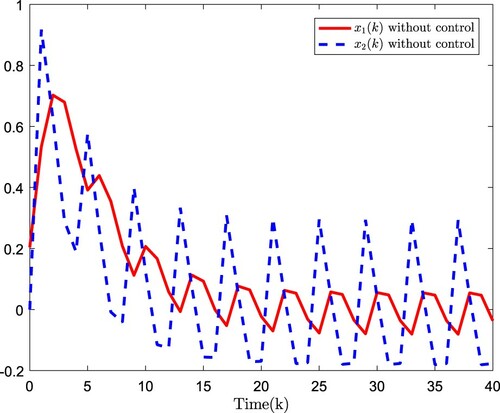
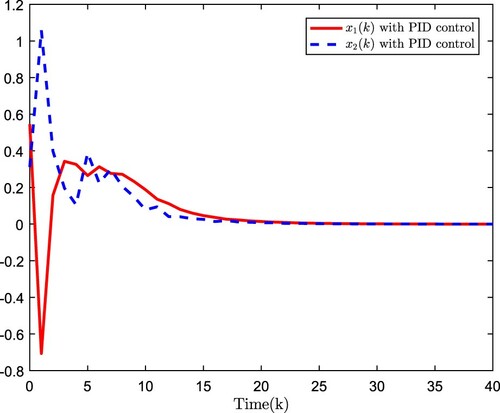
The simulation results are plotted in Figures . Figure plots the estimation error, Figure shows the open-loop system state, and Figure presents the closed-loop system state. The simulation results verify that the developed observer-based
PID control scheme is effectiveness.
5. Conclusions
In this paper, the observer-based PID control problem has been studied for linear discrete-time systems under hybrid cyber attacks. Sufficient conditions have been established to ensure that the closed-loop system is exponentially mean-square stable and satisfied the
performance. Then, the controller gains have been characterized by solving a matrix inequality. Finally, a simulation example has been conducted to demonstrate the effectiveness of the proposed control scheme. For subsequent research directions, we focus on coping with the PID control for systems with uncertainties (Liang et al., Citation2011), nonlinearities (Cui et al., Citation2018; Dong et al., Citation2011; Wang et al., Citation2017), incomplete measurements (Ding et al., Citation2017a; D. Zhang et al., Citation2017), protocols (Ding et al., Citation2019; X. Li et al., Citation2020; Zou et al., Citation2019), multi-rate measurements (Zou, Wang, Dong, et al., Citation2020), dynamic event-triggered mechanism (Zou, Wang, & Zhou, Citation2020, october), time-delays (J. Li et al., Citation2019), respectively.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
References
- An, L., & Yang, G.-H. (2018, January). Decentralized adaptive fuzzy secure control for nonlinear uncertain interconnected systems against intermittent DoS attacks. IEEE Transactions on Cybernetics, 49(3), 827–838. doi:https://doi.org/10.1109/TCYB.2017.2787740
- Ang, K. H., Chong, G., & Li, Y. (2005, July). PID control system analysis, design, and technology. IEEE Transactions on Control Systems Technology, 3(4), 559–576. doi: https://doi.org/10.1109/tcst.2005.847331
- Åström, K. J., Hägglund, T., Hang, C. C., & Ho, W. K. (1993, August). Automatic tuning and adaptation for PID controllers-a survey. Control Engineering Practice, 1(4), 699–714. https://doi.org/https://doi.org/10.1016/0967-0661(93)91394-C
- Bai, C.-Z., Pasqualetti, F., & Gupta, V. (2017, April). Data-injection attacks in stochastic control systems: Detectability and performance tradeoffs. Automatica, 82, 251–260. https://doi.org/https://doi.org/10.1016/j.automatica.2017.04.047
- Basin, M. V., Ramírez, P. C. R., & Guerra-Avellaneda, F. (2018, February). Continuous fixed-time controller design for mechatronic systems with incomplete measurements. IEEE-ASME Transactions on Mechatronics, 23(1), 57–67. https://doi.org/https://doi.org/10.1109/TMECH.2017.2700459
- Basin, M. V., Yu, P., & Shtessel, Y. B. (2018, January). Hypersonic missile adaptive sliding mode control using finite- and fixed-time observers. IEEE Transactions on Industrial Electronics, 65(1), 930–941. https://doi.org/https://doi.org/10.1109/TIE.41
- Cetinkaya, A., Ishii, H., & Hayakawa, T. (2017, May). Networked control under random and malicious packet losses. IEEE Transactions on Automatic Control, 62(5), 2434–2449. https://doi.org/https://doi.org/10.1109/TAC.2016.2612818
- Chen, B., Ho, D. W. C., Hu, G., & Yu, L. (2018, June). Secure fusion estimation for bandwidth constrained cyber-physical systems under replay attacks. IEEE Transactions on Cybernetics, 48(6), 1862–1876. https://doi.org/https://doi.org/10.1109/TCYB.2017.2716115
- Cui, Y., Liu, Y., Zhang, W., & Alsaadi, F. E. (2018, November). Sampled-based consensus for nonlinear multiagent systems with deception attacks: The decoupled method. IEEE Transactions on Systems, Man, and Cybernetics: Systems. https://doi.org/https://doi.org/10.1109/TSMC.2018.2876497
- Ding, D., Wang, Z., Han, Q.-L., & Wei, G. (2018, May). Security control for discrete-time stochastic nonlinear systems subject to deception attacks. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 48(5), 779–789. https://doi.org/https://doi.org/10.1109/TSMC.2016.2616544
- Ding, D., Wang, Z., Han, Q.-L., & Wei, G. (2019, June). Neural-network-based output-feedback control under Round-Robin scheduling protocols. IEEE Transactions on Cybernetics, 49(6), 2372–2384. https://doi.org/https://doi.org/10.1109/TCYB.2018.2827037
- Ding, D., Wang, Z., Ho, D. W. C., & Wei, G. (2017a, April). Distributed recursive filtering for stochastic systems under uniform quantizations and deception attacks through sensor networks. Automatica, 78, 231–240. https://doi.org/https://doi.org/10.1016/j.automatica.2016.12.026
- Ding, D., Wang, Z., Ho, D. W. C., & Wei, G. (2017b, August). Observer-based event-triggering consensus control for multiagent systems with lossy sensors and cyber-attacks. IEEE Transactions on Cybernetics, 47(8), 1936–1947. https://doi.org/https://doi.org/10.1109/TCYB.2016.2582802
- Dong, H., Lam, J., & Gao, H. (2011, January). Distributed H∞ filtering for repeated scalar nonlinear systems with random packet losses in sensor networks. International Journal of Systems Science, 42(9), 1507–1519. https://doi.org/https://doi.org/10.1080/00207721.2010.550403
- Huang, C., Ho, D. W. C., & Lu, J. (2012, April). Partial-information-based distributed filtering in two-targets tracking sensor network. IEEE Transactions on Circuits and Systems I: Regular Papers, 59, 820–832. https://doi.org/https://doi.org/10.1109/TCSI.2011.2169912
- Jin, X., Haddad, W. M., & Yucelen, T. (2017, November). An adaptive control architecture for mitigating sensor and actuator attacks in cyber-physical systems. IEEE Transactions on Automatic Control, 62(11), 6058–6064. https://doi.org/https://doi.org/10.1109/TAC.2017.2652127
- Li, J., Dong, H., Wang, Z., Hou, N., & Alsaadi, F. E. (2019). On passivity and robust passivity for discrete-time stochastic neural networks with randomly occurring mixed time delays. Neural Computing and Applications, 31(1), 65–78. https://doi.org/https://doi.org/10.1007/s00521-017-2980-1
- Li, X., Han, F., Hou, N., Dong, H., & Liu, H. (2020, May). Set-membership filtering for piecewise linear systems with censored measurements under Round-Robin protocol. International Journal of Systems Science, 51(9), 1578–1588. https://doi.org/https://doi.org/10.1080/00207721.2020.1768453
- Li, Y., Shi, L., Cheng, P., Chen, J., & Quevedo, D. E. (2015, October). Jamming attacks on remote state estimation in cyber-physical systems: A game-theoretic approach. IEEE Transactions on Automatic Control, 60(10), 2831–2836. https://doi.org/https://doi.org/10.1109/TAC.2015.2461851
- Liang, J., Shen, B., Dong, H., & Lam, J. (2011, January). Robust distributed state estimation for sensor networks with multiple stochastic communication delays. International Journal of Systems Science, 42(9), 1459–1471. https://doi.org/https://doi.org/10.1080/00207721.2010.550402
- Lien, C. H. (2004, August). Robust observer-based control of systems with state perturbations via LMI approach. IEEE Transactions on Automatic Control, 49(8), 1365–1370. https://doi.org/https://doi.org/10.1109/TAC.2004.832660
- Mo, Y., Chabukswar, R., & Sinopoli, B. (2014, July). Detecting integrity attacks on SCADA systems. IEEE Transactions on Control Systems Technology, 22(4), 1396–1407. https://doi.org/https://doi.org/10.1109/TCST.2013.2280899
- Mousavinejad, E., Yang, F., Han, Q.-L., & Vlacic, L. (2018, November). A novel cyber attack detection method in networked control systems. IEEE Transactions on Cybernetics, 48(11), 3254–3264. https://doi.org/https://doi.org/10.1109/TCYB.2018.2843358
- Peng, L., Shi, L., Cao, X., & Sun, C. (2018, July). Optimal attack energy allocation against remote state estimation. IEEE Transactions on Automatic Control, 63(7), 2199–2205. https://doi.org/https://doi.org/10.1109/TAC.9
- Rosinová, D., & Veselý, V. (2007). Robust PID decentralized controller design using LMI. International Journal of Computers Communications & Control, 2(2), 195–204. https://doi.org/https://doi.org/10.15837/ijccc.2007.2
- Silva, G. J., Datta, A., & Bhattacharyya, S. P. (2002, February). New results on the synthesis of PID controllers. IEEE Transactions on Automatic Control, 47(2), 241–252. https://doi.org/https://doi.org/10.1109/9.983352
- Soleymani, R., Nekoui, M. A., & Moarefianpour, A. (2020, January). Robust adaptive unknown input observer design for a class of disturbed systems. Systems Science and Control Engineering, 8(1), 249–257. https://doi.org/https://doi.org/10.1080/21642583.2020.1739578
- Takahashi, R. H. C., Peres, P. L. D., & Ferreira, P. A. V. (1997, October). Multiobjective H2/ H∞ guaranteed cost PID design. IEEE Control Systems Magazine, 17(5), 37–47. https://doi.org/https://doi.org/10.1109/37.621468
- Wang, D., Mu, C., He, H., & Liu, D. (2017, July). Event-driven adaptive robust control of nonlinear systems with uncertainties through NDP strategy. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 47(7), 1358–1370. https://doi.org/https://doi.org/10.1109/TSMC.2016.2592682
- Ying, H. (2000, April). Theory and application of a novel fuzzy PID controller using a simplified Takagi-Sugeno rule scheme. Information Sciences, 123(3), 281–293. https://doi.org/https://doi.org/10.1016/S0020-0255(99)00133-4
- Yuan, H., & Xia, Y. (2018). Secure filtering for stochastic non-linear systems under multiple missing measurements and deception attacks. IET Control Theory & Applications, 12(4), 515–523. https://doi.org/https://doi.org/10.1049/cth2.v12.4
- Zhang, M., & Lin, C. (2020). Secure state estimation for cyber physical systems with state delay and sparse sensor attacks. Systems Science and Control Engineering. https://doi.org/https://doi.org/10.1080/21642583.2020.1834465
- Zhang, D., Song, H., & Yu, L. (2017, August). Robust fuzzy-model-based filtering for nonlinear cyber-physical systems with multiple stochastic incomplete measurements. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 47(8), 1826–1838. https://doi.org/https://doi.org/10.1109/TSMC.2016.2551200
- Zhao, D., Wang, Z., Ding, D., Wei, G., & Alsaadi, F. E. (2018, April). PID output-feedback control under event-triggered protocol. International Journal of General Systems, 47(5), 432–445. https://doi.org/https://doi.org/10.1080/03081079.2018.1459596
- Zhao, D., Wang, Z., Ding, D., & Wei, G. (2020, June). H∞ PID control with fading measurements: The output-feedback case. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 50(6), 2170–2180. https://doi.org/https://doi.org/10.1109/TSMC.6221021
- Zhao, D., Wang, Z., Wei, G., & Han, Q.-L. (2020, October). A dynamic event-triggered approach to observer-based PID security control subject to deception attacks. Automatica, 120, Article No. 109128, 13 pages. https://doi.org/https://doi.org/10.1016/j.automatica.2020.109128
- Zhao, L., & Yang, G.-H. (2020). Cooperative adaptive fault-tolerant control for multi-agent systems with deception attacks. Journal of the Franklin Institute, 357(6), 3419–3433. https://doi.org/https://doi.org/10.1016/j.jfranklin.2019.12.032
- Zhu, M., & Martínez, S. (2014, March). On the performance analysis of resilient networked control systems under replay attacks. IEEE Transactions on Automatic Control, 59(3), 804–808. https://doi.org/https://doi.org/10.1109/TAC.2013.2279896
- Zhuang, M., & Atherton, D. P. (1993, May). Automatic tuning of optimum PID controllers. IEE Proceedings D-Control Theory and Applications, 140(3), 216–224. https://doi.org/https://doi.org/10.1049/ip-d.1993.0030
- Zou, L., Wang, Z., Dong, H., & Han, Q.-L. (2020, November). Moving horizon estimation with multi-rate measurements and correlated noises. International Journal of Robust and Nonlinear Control, 30(17), 7429–7445. https://doi.org/https://doi.org/10.1002/rnc.v30.17
- Zou, L., Wang, Z., Han, Q.-L., & Zhou, D. (2019, December). Moving horizon estimation for networked time-delay systems under Round-Robin protocol. IEEE Transactions on Automatic Control, 64(12), 5191–5198. https://doi.org/https://doi.org/10.1109/TAC.9
- Zou, L., Wang, Z., & Zhou, D. (2020, October). Moving horizon estimation with non-uniform sampling under component-based dynamic event-triggered transmission. Automatica, 120. https://doi.org/https://doi.org/10.1109/TAC.2019.2910167