Abstract
Metro rail systems (MRS) currently face a serious threat from terrorist attacks – especially through use of explosives. The threat comes at a time when scores of new MRS are under construction or at the planning stage in cities across the world. Designers of these systems need to consider ways to detect explosives without an adverse impact upon passenger comfort and profitability. This paper presents a framework for designers to identify security functions in MRS, understand current methods of threat detection used in MRS and recognise their relationship with other operational requirements. Application of this framework at the planning stage can assist in designing systems where terrorist threats can be better addressed with reduced impact on passenger experience and MRS operations. The application of a framework of analysis inspired by Ekblom’s work to nine functioning MRS yields a concise representation of the major design issues architects and security specialists have to consider for effective integration of security systems in stations.
1. Introduction
1.1. Background
There exist nearly 200 operational metro rail systems (MRS) worldwide. The International Association of Public Transport defines a MRS as an urban electric transport system with high capacity and frequency of service. In addition, a MRS is totally independent from other traffic, road or pedestrian (UITP, Citation2013). According to the World Metro Database (Citation2013), 81 MRS are either at the planning stage or already under construction (Table ). In particular, emerging economies, like China and India, are rapidly building urban metro rail systems in their growing cities to decongest road traffic, and provide more environmentally friendly means of transport to their communities (Litman, Citation2007). A recent study by the Association of the European Rail Industry (Citation2012) found that the global market for metro rail infrastructure and equipment has been growing at a rate of 3.2% per year through the global downturn (2008–2010), and is set to continue its growth at a rate of about 2.7% per year until 2017.
Table 1. MRS projects under construction or proposed.
In the design of a metro system, the emphasis is placed upon facilitating the movement of passengers (Vuchic, Citation2005). Owing to their functionality, metro rail projects were conceived as ‘open architecture’ systems, and little attention was paid to security (Riley, Citation2004, p. 4). Past incidents have shown that MRS provide suitable environments not only to passengers but also to offenders such as pick pockets (Cozens, Neale, Hillier, & Whitaker, Citation2004) and sexual offenders (Kirchhoff et al., Citation2007). Moreover, they are notorious target sites for terrorists (O’Neill, Robinson, & Ingleton, Citation2011) seeking to create mass panic, disrupt daily life of a city, adversely affect transport infrastructure for several days and cause a significant symbolic impact (Wilson, Jackson, Eisman, & Riley, Citation2007). This was evidenced by the recent series of bombings against Madrid’s Cercanias commuter train system in 2004, London Underground in 2007, Mumbai suburban rail network in 2008 and Moscow Metro in 2010.
Among the most prevalent methods of terrorist attack is the use of explosives. Explosive devices have been a weapon of choice for those who aim to strike against passenger rail for two reasons. First, it is easy to smuggle explosives on trains as checking is rare at stations (Wilson et al., Citation2007). Second, detonation of bombs in packed commuter trains can cause mass casualties. Considering a set of terrorist incidents involving trains between 2003 and 2007 (Stavropol, Moscow, Madrid, London, Dewana and Mumbai), the Mineta Transport Institute reported that, on an average, each bomb killed 24 persons (Jenkins, Citation2007). The lethal role explosives have played in attacks against passenger rail is also apparent in RAND’s Database of Worldwide Terrorism Incidents (CitationRDWTI). An analysis of 833 incidents between 1960 and 2010 shows that explosives were used in 70% of cases involving passenger fatalities and 77% of cases involving passenger injuries (Table ).
Table 2. Global statistics of passenger fatalities and injuries between 1960 and 2010.
In a context where terrorism has become a global political component (Kydd & Walter, Citation2006), it is hardly surprising that those in charge of MRS, either existing or in development, are now increasingly concerned with improving the security of their infrastructures worldwide. Responses to a questionnaire by industry stakeholders showed that they considered Improvised Explosive Devices (IEDs) as the most lethal threat to MRS (O’Neill et al., Citation2011).
There is a need to integrate into current and future metro rail networks comprehensive security systems that could be used for the detection and disruption of terrorist activities (Bocchetti, Flammini, Pragliola, & Pappalardo, Citation2009). However, they are hampered by the fact that despite the obvious need for it, there has been little published work on the design of security checkpoints at metro rail stations. There is considerable academic literature in the domain of airport security focusing on diverse issues. Examples of research include framework for selecting the right baggage inspection systems (Blejcharova, Cheu, & Bina, Citation2012), comparison of various leadership models for checkpoints (Wetter, Laube, & Hofer, Citation2009), impact of information on security decisions at airports (Kirschenbaum, Mariani, Gulijk, Rapaport, & Lubazs, Citation2012), influence of weather conditions on security control process (Wetter, Lipphardt, & Hofer, Citation2010) and role played by human factors in detection of threats (Hofer & Wetter, Citation2012).
However, studies show that findings in the domain of airport security are not entirely transferrable to the railway sector (Jenkins, Butterworth, & Gerston, Citation2010) as there are differences between these applications and their contexts. For instance, whilst it is admitted that railway commuters should be able to embark on a train as they arrive at a station, airline passengers are expected to arrive at the airport several hours before their flights to fulfil the requirements of security checks (Government Accountability Office, Citation2010, p. 31).
Planners of urban railways need to understand the challenges that exist in designing secure systems for MRS, and appreciate how the design choices impact on the objectives of multiple stakeholders. As an example, a study of the English rail system identified 27 different stakeholders at a typical railway station who need to be brought together to address the design and operational challenges inherent in dealing with security threats (Gregson-Green, Dainty, & Bosher, Citation2013). Designers have to work under the constraints that the environment of a railway station will impose upon them. These include the spatial configuration of a station and the large number of passengers who must be accommodated during rush hour.
1.2. Aim
This article seeks to contribute to the future design and retrofitting of secure MRS by revealing how the characteristics of security systems impact on the qualitative characteristics of those infrastructures, including, but not limited to, security. It aims at providing an epistemic foundation to support the design of MRS that can host more effective and less disruptive security systems. To reflect the importance that detection technologies and procedures now have in the security strategies of MRS, this article focuses on systems contributing to the detection (including checkpoints) of terrorist threats involving explosives.
2. Method
2.1. Framework of analysis
2.1.1. Introduction
In order to understand the relationships between the design of a security system and the operational qualities of its environment, it is useful to adopt a consistent set of terms that can express the what, why and how of security systems and security practices. As the following example shows, security is underpinned by complicated concepts whose links are not always easy to comprehend, and do not always mix well with existing systems engineering frameworks.
In the recent years, cash-in-transit (CIT) companies have invested in cash degradation systems such as dye bombs (Smith & Louis, Citation2010). Amongst those intelligent banknote neutralisation systems (IBNS) are used to ‘permanently neutralizing banknotes if any unauthorized attempt is made to open [their] container’. (EC, Citation2009, p.15)
Amongst security practitioners, some confusion appears to exist about the meaning of the term function, ranging from what a system does, the immediate environmental change it creates, to the ultimate security impact it supports. The function of an IBNS system is regarded as ‘prevention’ (of attacks) by some, ‘deterrence’ (of offenders) by others, ‘detection’ (of offenders) by a third group, ‘increasing the detectability of stolen bank notes’ by a fourth one and ‘ink-marking them’ for others. Other would regard it as ‘preventing the use of stolen bank notes in society’. Finally, some would consider all the above as the functions of an IBNS.
The inherent difficulty that exists in structuring our knowledge of security procedures, policies, processes and products has led to the construction of epistemic frameworks of varying robustness and complexity. For our purpose, such frameworks can be used to unambiguously and concisely describe the logical principles of different security systems, and accurately translate generic principles into specific mechanisms (and vice versa). Prior to the presentation of the method adopted in this article, it is therefore useful to clearly define the approach and terms adopted in this article.
2.1.2. Approach and terms used
The first two steps of the framework adopted for this piece of work (and presented in the next section) aim at identifying the elements of relevant security systems and their properties. These steps are inspired by Ekblom’s mechanism-based classification of crime prevention (Ekblom, Citation1994) and his more recent framework known as Conjunction of Criminal Opportunity (Ekblom, Citation2011).
In the original article, Ekblom (Citation1994) proposed a classification underpinned by the principles and entities involved in the delivery of a crime reduction effect. The framework was generated to provide a suitable taxonomy for the ‘development of crime prevention as a discipline’. To understand the approach employed, it is necessary to appreciate the distinction between the terms method, causal mechanism and principle.
MethodFootnote1 is an element of preventive action which operates through a particular and indivisible set of causal routes, ending up as influences on one or more components of the proximal circumstances of criminal events’ (Ekblom, Citation1994). ‘[They] are the what of intervention: practical plans and designs for actions intended, through Implementation and Involvement, to realise the principles in particular contexts. […]. (Ekblom, Citation2011)
Causal mechanisms of prevention describe the ways in which the methods actually have their effect. (Ekblom, Citation1994)
Principles are generic causal mechanisms abstracted from their specific context-bound, interactions. They are the how of intervention. […]. (Ekblom, Citation2011)
Principles and mechanisms are the main components used in the following analysis. In addition, we also define the term security system:
‘Security system is a set of components coherently organised and/or selected for the purpose of actualizing one or more security mechanisms’. Security systems can include human operators and existing environmental elements.
In (Meyer & Ekblom, Citation2012), a security function is defined as ‘the properties of a product which, interacting through causal mechanisms with entities, agents and systems within its environment, serve the purpose of reducing the risk of crime and increasing security and community safety’. For our purpose:
Security functionality of a system is its capability to influence the state of the world in a specific way which contributes to one or more security objectives.
Borrowing from Ekblom’s approach, security systems used in transport security can be classified based on their primary functions. In other words, they can be classified based on their main direct contribution to the mechanisms actualised. As an example, a system designed to detect specific chemical agents in the air would be classified as a detection system. On its own, a detection system does not reduce harm. However, the information it provides plays a role in a broader security mechanism that involves the activation of an evacuation procedure.
A given system may be classified in more than one category if it has more than one function, that is, if it can actualise various mechanisms. For example, a security officer can be regarded as a security system able to perform communication, detection, neutralisation functions and can therefore be classified in at least three categories. Moreover, functional categories can be further refined. For example, the neutralisation of an offender may be performed in different ways, which would justify the use of a more specific term.
Finally, security systems can have various (direct or indirect, supporting or hindering) effects on various (physical or psychological) elements involved in a crime. In the case of a direct effect, a system impacts directly on the elements involved in a crime script (Cornish, Citation1994), for example the offender. In the case of an indirect effect, a security system indirectly influences the decisions to initiate certain activities, their initiation, completion and outcome (Borrion, Citation2013) typically through controlling the state of certain environmental factors.
2.1.3. Stages
A five-step framework was devised to reveal the relationships between the characteristics of security systems and the qualities of the transport infrastructures that use them.
Identifying the generic security functions performed in selected MRS.
Identifying the principles, mechanisms and entities.
Identifying the design parameters of the systems of interest, and their possible values or levels.
Identifying the functional and non-functional characteristics of the selected transport systems.
Relating the security systems’ design parameters identified in (3) to the qualities of MRS identified in (4).
Given the lack of documents stating in a clear and accurate fashion how security is implemented, the above framework was designed to ensure that the principles, the mechanisms and their factors could be elicited using the following data collection method.
2.2. Data collection
2.2.1. Overview
This study is part of a larger piece of research focusing on the resilience of MRS. As per the scope of the article, the framework of analysis was applied to analyse those systems contributing to the detection of threats involving explosive devices at MRS.
In order to carry out the analysis reported here diverse methods were used, and several MRS systems in different countries were visited over a period of 18 months (7/2012–12/2013).
To avoid dual use issues, this section only provides an aggregated description of the sources and methods used in this study, and the anonymity of those who accepted to contribute their expertise and infrastructure to the study is voluntarily preserved.
2.2.2. Primary data
The following describes the sources of primary data used in this research:
data collection at security checkpoints over several days;
interviews of security personnel working at checkpoints;
participation in security drills at different MRS in operation and in development;
visits of stations accompanied by representatives of organisations managing MRS;
observation of, and contribution to, meetings organised by planners of new MRS over two years;
interviews with security experts working for MRS management organisations;
observations as passengers.
2.2.3. Secondary data
The following describes the sources of secondary data used in this research:
websites and internal reports of MRS organisations;
online videos of security drill uploaded by passengers;
news reports of heightened alert on MRS;
peer-reviewed articles;
independent reports.
2.2.4. MRS instances
Nine MRS were selected for inclusion in this study. Availability of security related data was a primary criterion for selecting these MRS. It is understandable that details of procedures used to secure MRS is a sensitive issue, difficult for academics to get access to. Therefore, in the interest of credibility of information, the sites were selected from a pool where sufficient details of security procedures were available to the authors.
However, ease of access to data though a primary reason for selecting an MRS, was not the only criterion for its inclusion in this study. Size of the network was also a significant factor, as security from explosives is a concern for busy railway networks. All the MRS discussed in this paper are relatively large networks with a number of stations ranging between 89 stations (Singapore) and 422 stations (New York) and daily ridership ranging from 1.7 million passengers (Delhi) to 8.5 million passengers (Tokyo).
Given the subject of this paper it is understandable that whether security was a matter of concern for stakeholders was another criterion that was considered for the inclusion of certain MRS in this study. New York, Moscow, Beijing, Delhi, London and Tokyo are cities that have experienced a problem with terrorism in recent past, or have witnessed actual terrorist attacks on their MRS in the last two decades. These MRS were believed to be representative of the actual threats stakeholders would typically face.
MRS in Singapore, Taipei and Seoul were selected to make the sample more ecologically representative of future MRS given 50 of the 81 new MRS projects under construction or at a planning stage will be based in Asia (see Table for more details). Finally, the personal experience of the authors with security procedures in place at certain MRS (e.g. Seoul) was an additional factor for their inclusion (Table ).
Table 3. Technical features of ten MRS.
3. Application of the framework to MRS security
3.1. Functions of security systems
Step 1: Identifying the generic security functions performed in selected MRS.
3.1.1. A focus on information
Security at MRS can be achieved through the disruption of sequences of actions leading to crime events, or the reduction of the harm they may cause (Jenkins & Trella, Citation2012). To achieve the sought impacts within acceptable conditions, security systems can be used to perform certain functions, enhancing human capability or reducing the operational costs of security (Peterman, Citation2006).
For effectiveness, security systems are used in a certain way, at a certain time, in certain circumstances or against certain individuals. Moreover, for efficiency, their use is often limited to a prescribed domain of operation, as required by the application. For example, ‘officers at New York’s MRS conduct the inspection for no longer than necessary to ensure that the individual is not carrying an explosive device … a typical inspection lasts for a matter of seconds’ (Jenkins et al., Citation2010, p. 14).
The nature of security measures, therefore, makes their use reliant on the occurrence of certain conditions (i.e. states or events) and the availability of specific information about those. For this reason, the detection of malevolent individuals on MRS premises, the identification of their intent and detailed knowledge about their operational resources can be extremely useful to support security operations including tasking and management of law enforcement personnel.
Owing to the scope of this study, only those functions supporting threat detection are detailed below. However, despite being related to the creation of information (and thus of psychological/analytical nature), the operation of detection systems can be combined with the actualisation of mechanisms affecting physical attributes in order to improve performance.
For this reason, the functions of security systems that support threat detection are described in two parts. The first list includes those functions that are solely related to information generation and management, whilst the second list includes a range of functions related to the physical alteration of elements for the purpose of enhancing detection performance.
3.1.2. Functions contributing to detection in MRS
3.1.2.1. Functions related to information
Functions related to the generation and management of information are critical to the implementation of effective and efficient security systems. In the following, we list a range of functions that contribute to threat detection: to detect, to authenticate, to identify, to image, to inform, to stimulate (using communication means), to prime, to locate, to manage, to profile, to track.
To detect: e.g. determining the presence of certain anomalies, substances, individuals or behaviours (Hardmeier, Hofer, & Schwaninger, Citation2005).
To authenticate: e.g. verifying that an individual is a member of staff, verifying that an individual has the right to access certain parts of the infrastructure (Adey, Citation2003).
To identify: e.g. determining the name of a given chemical substance (Federici et al., Citation2005).
To image: e.g. representing the content of certain items of luggage using X-ray technology (Singh & Singh, Citation2003).
To inform (i.e. communicate): e.g. raising an alarm or calling in armed units in response to a detected threat (Kirschenbaum et al., Citation2012).
To locate: e.g. determining the location of individual passengers considered as potential threats to the infrastructure (Lee, Smeaton, O'Connor, & Murphy, Citation2005).
To manage: e.g. performing resource allocation, tasking and scheduling (Emil, René, & Franziska, Citation2009).
To profile: e.g. classifying passengers who fit the profile of an offender for extra security checks (Sweet, Citation2009).
To track: e.g. following the movement of certain passengers through station premises (McCoy, Bullock, & Brennan, Citation2005).
3.1.2.2. Functions related to the physical alteration of elements
In addition to systems performing information generation and management, other systems can be employed to support those. For example, some security systems are designed to cause a physical alteration of their environment in order to influence the detection of criminal elements. The following list presents some of the functions that those systems typically perform:
To control the use of space (attractiveness, physical and cognitive accessibility, usability): e.g. to design a station in such a way that every passenger can be monitored before they enter a station to increase the chance of detecting behavioural anomalies for example.
To control the use of resources (attractiveness, physical and cognitive accessibility, usability, functionality): e.g. to make certain detection resources more usable to enhance process efficacy.
To stimulate: e.g. challenging suspicious passengers to produce a valid ticket or IDs.
Through the performance of these functions, security measures can enhance the processes by which threat detection occurs by increasing the sensitivity or selectivity of the detection process, or ensuring that the detection process is applied as planned, for example by preventing spoofing or ensuring that no individual is able to evade a screening process.
3.2. Principles, mechanisms and entities used to achieve threat detection
Step 2: Identifying the principles, mechanisms and entities.
3.2.1. Principles used for detection
Detection is generally achieved on the basis of indicators (Heuer & Pherson, Citation2011, p. 132). For example, the National Counter Terrorism Security Office in the UK provides a list of indicators that can be used to identify suspicious behaviours possibly associated with hostile reconnaissance conducted at airports (NaCTSO, Citation2012). In a detection system, a selection of attributes are determined for certain entities and compared with the corresponding indicators.
The attributes of interest vary with the type of threats considered, the context and the availability of instruments that can measure them. The following provides a list of principles that are used to achieve detection. First, detection may occur on the basis of the identity of an entity, e.g. individuals, objects, etc. (Yoo, Citation2009). For this, unique identifiers such as passports or number plates are compared with those in watch lists. Also known as hotlists, these are commonly used at border control checkpoints or road checkpoints (e.g. Haines, Citation2009; Krouse, Citation2010).
However, it is not always practically feasible to obtain the identity of all entities in a given population due to practical, financial or ethical reasons (Monahan, Citation2006), as shown by the decision of the UK Government not to implement an identity card scheme (Beynon-Davies, Citation2011).
In those cases, detection can also be achieved non-cooperative manner based on observations made of an entity’s appearance or behaviour (Frank, Maccario, & Govindraju, Citation2009). For example, the clothes or trajectories of an individual intending to carry out an attack may be anomalous in comparison with those of ‘normal users’. Detection may also be carried out indirectly by considering entities whose appearance or behaviour may be affected by the nearby presence of an offender.
3.2.2. Attributes of observed entities
The following presents some of the entities and attributes that may be considered in a detection process.
Identity: e.g. John Smith
Type
Individual: e.g. male, female
Object: e.g. clothes, containers
Relational
Ownership: e.g. has, belongs to
Mechanical: e.g. carries
Sensorial: e.g. conceals
Location: e.g. is at, is within, is near
Appearance: e.g. wears a bulky jacket
Behaviour: e.g. has been standing in the same place for 10 min
Intent: e.g. intend to enter in a train carriage
Stage within the crime script: e.g. planning, preparation
3.3. System design parameters
Step 3: Identifying the design parameters of the systems of interest, and their possible values or levels.
3.3.1. Security procedure
Meyer and Ekblom (Citation2012) and Meyer (Citation2012) have looked at trajectories followed by offenders who intend to target railways with explosives. For any such offender, one of the early steps in the execution scene of their crime script typically consists of entering the station premises without being detected or challenged. This applies whether they are a suicide bomber or a terrorist who intends to escape after planting a lethal device.
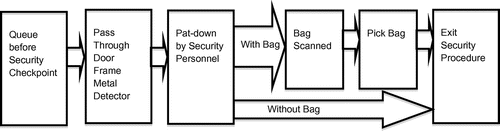
In order to disrupt this script during the first step, security personnel at MRS can rely on different measures (Clarke & Newman, Citation2006). These include asking passengers to walk through a door frame metal detector (DFMD), a physical pat-down of passengers to check if any explosives have been concealed on their person, visual inspection of bags by asking passengers to open them or directing passengers to put their bags through an X-ray scanner (Figure ).
3.3.2. Pat-down
Physical pat-down or frisking of potential offenders has long been in use by police forces across the world (Cook, Citation1971). In the context of a MRS, pat-down of passengers at railway stations would take place before they board their trains. In a typical pat-down, the officer runs a hand-held metal detector over the body of the passenger to detect the presence of metallic objects that would be concealed under their clothing (Government Accountability Office, Citation2010). To this aim, the officer may physically touch the passenger if they suspect a bulky item might be hidden under the clothing. This procedure is primarily used to detect knives, firearms or explosives strapped on their bodies.
3.3.3. Door frame metal detectors
DFMD are ubiquitous in security procedures at MRS. DFMDs work by asking passengers to walk under them, and alert security personnel if the passenger is carrying metallic objects on his person. The sensitivity of DFMDs can be adjusted to raise an alarm only for large metallic objects, and not for small items like keys and coins (Government Accountability Office, Citation2010). DFMDs can assist security personnel in speeding up movement of passengers through checkpoints, as only those passengers that trigger an alarm need to be patted down, while others are allowed to walk through unimpeded.
3.3.4. X-ray scanning
X-ray scanning machines are used to inspect bags carried by passengers. ‘Current X-ray-based baggage scanning techniques are based on measuring the amount of X-ray absorption due to different hidden materials [and work best for distinguishing] metal items from clothes, shoes, etc (O’Flynn et al., Citation2013). There are very few MRS in the world where X-ray scanning machines are used on a regular basis. At the time of writing this article, MRS in Beijing, New Delhi and Moscow were the only three facilities in the above list where all passengers are requested to submit their bags for X-ray scanning. In those places, an operator is tasked to determine if explosives are hidden in passengers’ luggage from images appearing on the scanner’s screen.
3.3.5. Other inspection methods
Apart from pat-downs and baggage screening (which are the primary means of detection for contraband), other security measures are also used to detect explosives. These include visual inspection of the content of a passenger’s bag, generally at the time of pat-down, and random checks by canine units (Peterman, Citation2006) which have been found to be relatively effective in detecting explosives (Furton & Myers, Citation2001).
All the MRS discussed in this paper use CCTV surveillance as a means of monitoring potential offenders. The Seoul MRS is the only network on the list where images from a moving train are relayed in real time to an Operations Control Centre (OCC). This gives authorities an opportunity to detect offenders at an early stage of their crime script implementation. At all MRS on the list, CCTV cameras at stations relay images to a control room where security officials can keep a watch on movement of offenders through the station premises, and coordinate with patrolling units to stop and question them.
Officers in New York have been trained to read suspicious body language (Government Accountability Office, Citation2010) as a means of distinguishing likely offenders from the general population of passengers. It allows them to be more selective in the application of additional screening measures, and therefore minimise disruption to other passengers on the network.
The detection methods discussed in this section have a relationship with the variables listed in Table , and their impact upon the railway environment. The number of security officers, X-ray machines, DFMDs in service has a bearing on how long it will take passengers go through security checks. Service time (the duration of an inspection task) has a direct effect on the time spent by passengers to go through security checks. Finally, the proportion of total passengers subjected to a particular form of inspection also has an impact on the time it takes them to move through security checks.
3.3.6. Impact of security design choices on the railway environment
The choices architects make for the design and configuration of security checkpoints at railway stations have an impact far beyond just the ability of security personnel to detect certain kinds of threat.
Decisions to include or exclude specific features of a security procedure have a direct bearing on the cost of operations of the rail operator. In addition, designers need to understand that given the thoroughness of a security procedure, movement of passengers through station premises is impeded as they have to wait in security queues before they pass through the inspection procedure (Dwyer, Citation2010).
Each inspection task takes a certain amount of time to be completed, which in turn has implications for the amount of time passengers have to wait, crowding on the station premises. Moreover, setting up a security system involves investment in both machinery and trained personnel, which has implications for the cost borne by the railway operator. Security systems can also create ethical and legal issues related to privacy concerns of passengers, legality of certain types of checks (Monahan, Citation2006). All these factors have to work in tandem with detection of threats at railway stations, while ordinary passengers are able to commute with relatively limited discomfort.
The initial hypothesis underpinning this work is that those involved in the planning of MRS are more likely to propose satisfactory security designs (i.e. designs that meet the multiple requirements of the stakeholders) if they have a clear idea of the potential impact specific procedures may have upon the station’s environment.
Towards this end we present a list of security variables in Table and the relationships they have with operational aspects of a working metro rail station. This information was extracted from a range of methods listed in Section 2.
Table 4. Security features of nine MRS in the world.
3.4. Functional and Non-functional characteristics of MRS
Step 4: Identifying the functional and non-functional characteristics of the selected transport systems.
For the purpose of analysing the design of security systems, it is useful to adopt a model representing the objectives of organisations running MRS systems. Arguably these are driven by two elements: the value of their organisation and the satisfactory delivery of a public service. Leaving aside liabilities, the components impacting on the value of an organisation can be regarded as the value of the assets and the profitability of the services it set out to deliver (Vuchic, Citation2005). The value of the assets is directly dependent upon their integrity, and as such any malicious element that has the potential to significantly impact on their physical state would need to be managed accordingly. The profitability of the services depends on the running cost of the infrastructure and the revenues made through selling the services to its users (Hale & Charles, Citation2009). The running cost depends on the efficiency of the infrastructure, whereas the revenues depend on (i) its ability and capacity to deliver the advertised services, as well as (ii) the demand for the services and prices. The former is driven by the legality (of the system and its implementation) and the capacity of the infrastructure (Kraft, Citation1987). Legality depends in part on compliance to regulations including safety related ones. The demand for the service depends on its attractiveness to the targeted population (Li & Wong, Citation1994) which also depends on its acceptability amongst the population of potential users, its affordability, availability, frequency and performance (e.g. speed and coverage) (Lyons & Chatterjee, Citation2008). Finally, the satisfactory delivery of a public service can be estimated using a number of already listed elements that influence the level of satisfaction of the population.
An operational MRS is subjected to operational requirements, among which security of passengers from explosive attacks is just one. On a daily basis, the stakeholders of an MRS have a number of service elements to fulfil. A recent document published by ISO (Citation2011) describes several of these elements as quality requirements (or quality attributes) from a system.
Using this document as a guide, the authors of this paper considered 14 elements expected from MRS: Legality, Affordability, Attractiveness, Acceptability, Availability, Capacity, Efficiency, Frequency, Integrity, Performance, Profitability, Reliability, Safety and Sustainability. Whilst this list is not exhaustive it provides a useful foundation for architects and planners interesting in better understanding how certain security measures may impact on the quality of a transport system.
Taken together, the elements of the list contribute to passengers’ experience of using the MRS, financial returns and operational longevity of the system. Stakeholders will expect from designers of MRS that there is no or limited conflict between these operational and qualitative requirements and demands placed by security systems.
3.5. Relationship between Security systems and MRS characteristics
Step 5: Relating the characteristics of security systems to the qualities of MRS.
Each factor listed in Table has an impact on the above operational characteristics of a MRS. Security decisions taken at railway stations influence the demand for the service by influencing, for example, the comfort of passengers and their customer experience (Dwyer, Citation2010). For example, a decision to increase security checks can add to the feeling of discomfort of passengers if they have to wait for a long time in queues, but it can also instil a sense of safety in them (Peterman, Citation2006). To take another example, security procedures can have a direct impact on revenue earned by a railway operator. Long waiting times for passengers in security checks mean trains on a network run below their capacity as passengers get held up at the station.
Table brings together the factors in Table to show which elements of a security system have a relationship with the operational characteristics of a MRS. Designers can use this framework to visualise the place of security checkpoints within the larger operation of a MRS. This information can be used to plan architecture of security checkpoints, and format of security procedure in a way to maximise revenue for the rail operator, and safety and comfort for passengers without compromising on security officers’ ability to detect offenders (Table ).
Table 5. Design factors and their impact upon the railway environment.
Table 6. Environmental factors and their impact upon the railway environment.
4. Discussion
4.1. The current situation
The MRS studied in this paper follow different security plans with the aim of detecting, and preventing offenders from carrying out their goals. Where explosives are high on the list of concerns, security procedures assume a more visible format (Taylor et al., Citation2005). Therefore, in Beijing, New Delhi and Moscow all bags that are taken on trains go through an X-ray scanner to inspect their contents. Moreover, in Delhi all passengers are patted down before they board their trains (Siemiatycki, Citation2006). Armed units patrol the stations regularly. Three authors of this paper participated in a security drill where a weapon was detected in a passenger’s bag during X-ray scanning. In line with functions related to information management (Section 3.1.3) the X-ray machine operator raised an alarm, relayed the information to the nearest armed response unit, which in turn took possession of the detected weapon and ‘detained’ the passenger concerned.
Checkpoint evolution in response to threats, incidents or events is an essential part of several MRS studied in this paper. In Beijing, on days of public holidays, Communist Party conferences, presence of security officers at checkpoints on MRS is increased. They also proactively challenge potential offenders (Section 3.1.3) by randomly asking passengers for identification papers.
In New York, checkpoint evolution is assisted by use of mobile X-ray machines that can be moved around station premises. Officers then select passengers to submit their bags to scanning. This selection is made on the basis of various inputs such as size of bag, reading body language of potential offenders or an intelligence alert (Government Accountability Office, Citation2010; Peterman, Citation2006).
In New Delhi, passengers are subjected to extra checks during pat-downs, and X-ray scanning on certain important days of the year such as public holidays and religious festivals. This has an impact on other factors of MRS operation, especially the amount of time passengers have to wait in queues at the station (NDTV, Citation2013).
In Seoul, terrorist attack using explosives is not seen as a major threat when compared to New Delhi, Moscow or New York rail systems. Therefore, there are currently no security checkpoints at any of its stations. Other measures used for explosive detection such as canine units, baggage scanning and pat-down of passengers are also generally absent. Establishment of checkpoints is also restrained by the fact that most stations on Seoul MRS do not have enough space to allow passengers to queue for security checks during rush hour.
4.2. Need for improvement
Security systems on MRS across the world can differ according to the local context within which they function. In New Delhi, female passengers are patted down only by female security officials, which can also create some design challenges. Provisions have to be made at stations for separate queues for men and women. Areas have to be earmarked where female passengers are patted down behind screens, and security officials have to ensure that there is always a female guard at every checkpoint. In contrast, there are no such gender considerations for Beijing MRS security.
There is also diversity of local threats that security agencies respond to. On the Beijing MRS, checkpoints feature liquid detectors to prevent passengers from carrying gasoline on trains. In Seoul, following an arson attack on a MRS in Daegu in 2003 special provisions have been made to detect fire using a network of surveillance cameras. On the Tokyo MRS, staff have been intensively trained in evacuation of passengers to prevent mass casualties from a poison gas attack like the one in 1995 (Funato, Citation2005).
To be effective in detecting offenders, security tasks and technology at security checkpoints need to evolve with time (Jacobson, Lee, & Nikolaev, Citation2009). Designers of metro rail stations will benefit from working with a clear framework that lists the tasks security personnel perform under varying at different MRS in the world. This can be used as a blueprint to design intelligent security checkpoints that can increase or decrease their detection capability in response to circumstances. To do so planners need to have a clear understanding of the relationship between security processes that take place on a metro rail station, and the overall operation of the MRS within which they are situated.
4.3. Limitations
The intellectual contribution of this article is limited by several barriers. First, only publically available information was used in the analysis. There is, therefore, a non-negligible risk that the researchers were not made privy to certain detection systems implemented covertly at stations. Second, whilst all the information about Beijing, New Delhi, Seoul and London was confirmed by direct sources working in the MRS, part of the information concerning other stations obtained from public websites may not be absolutely up to date. Third, the list of MRS discussed in this study only represents a sample of the systems operating in the World, and there is also a risk, albeit minor, that some other detection systems exist in MRS not considered above. Fourth, security being a politically sensitive issue, it is difficult to predict how salient security measures will be in MRS in the future. Finally, public acceptability of security measures can vary considerably in the days following a terrorist attack (Davis & Silver, Citation2004). The degree of adoption of sophisticated detection systems across MRS networks will also depend on the occurrence of successful attacks, and the perceived need to act against future ones.
5. Conclusion
Making MRS secure against all forms of crime, including terrorist attacks, requires a delicate balance of several factors. Railway operators realise that guaranteeing secure transit for passengers is important to keep customers satisfied, and in turn generate revenue for the company through increased passenger journeys. Concurrently, maintaining security at stations demands not just a one-time investment in equipment, and infrastructure, but continues to impact upon passenger experience of using the MRS.
Planners can come to the aid of railway operators by designing security checkpoints that harmonise conflicting goals of a railway operation. The first step forward in this direction is to identify the demands of a MRS-related security task, nuances of a comfortable passenger experience and overall goals of a railway operator. This paper presents a vocabulary for planners to articulate these issues, and address them at the design stage of MRS itself, so that secure journeys become an integral part of passengers’ daily commute.
Notes
1. In our work, the term ‘measure’ is used in place of ‘method’.
References
- Adey, P. (2003). Secured and sorted mobilities: Examples from the airport. Surveillance & Society, 1, 500–519.
- Association of the European Rail Industry. (2012). Worldwide rail market study 2012. Retrieved from http://www.unife.org/page.asp?pid=66
- Beynon-Davies, P. (2011). The UK national identity card. Journal of Information Technology Teaching Cases, 1, 12–21.10.1057/jittc.2011.3
- Blejcharova, N., Cheu, R. L., & Bina, L. (2012). Framework for selecting screening technologies for checked baggage inspection systems at airports. Journal of Transportation Security, 5, 239–252.10.1007/s12198-012-0094-7
- Bocchetti, G., Flammini, F., Pragliola, C., & Pappalardo, A. (2009, August). Dependable integrated surveillance systems for the physical security of metro railways. Paper presented at Distributed Smart Cameras, 2009. ICDSC 2009. Third ACM/IEEE International Conference on Digital Object Identifier.
- Borrion, H. (2013). Quality assurance in crime scripting. Crime Science, 2, 6–18. 10.1186/2193-7680-2-6
- Clarke, R. V., & Newman, G. R. (2006). Outsmarting the terrorists. Westport: Praeger Security International.
- Cook, J. G. (1971). The art of frisking. Fordham Law Review, 40, 789–803.
- Cornish, D. B. (1994). The procedural analysis of offending and its relevance for situational prevention. Crime Prevention Studies, 3, 151–196.
- Cozens, P., Neale, R., Hillier, D., & Whitaker, J. (2004). Tackling crime and fear of crime while waiting at Britain’s railway stations. Journal of Public Transport, 7, 23–41.
- Davis, D. W., & Silver, B. D. (2004). Civil liberties vs. security: Public opinion in the context of the terrorist attacks on America. American Journal of Political Science, 48, 28–46.10.1111/ajps.2004.48.issue-1
- Dwyer, A. S. (2010). Intending to travel. Benefit, cost, and active management of terrorism-related risk in the railway environment. British Transport Police. Unpublished.
- Ekblom, P. (1994). Proximal circumstances: A mechanism-based classification system of crime prevention. In R. Clarke (Ed.), Crime prevention studies (Vol. 2, pp. 185–232). Monsey, NY: Criminal Justice Press.
- Ekblom, P. (2011). Crime prevention, security and community safety using the 5Is framework. Basingstoke: Palgrave Macmillan.
- Emil, W. O., René, L., & Franziska, H. (2009, October). A comparison between two leadership models for security checkpoints. In Security Technology, 2009. 43rd Annual 2009 International Carnahan Conference on, 59–67 (IEEE).
- European Commission (EC). (2009). White Paper on professional cross-border transportation of euro-cash by road between Member states in the Euro Area. Retrieved from http://www.europeanpaymentscouncil.eu/knowledge_bank_detail.cfm?documents_id=352
- Federici, J. F., Schulkin, B., Huang, F., Gary, D., Barat, R., Oliveira, F., & Zimdars, D. (2005). THz imaging and sensing for security applications—Explosives, weapons and drugs. Semiconductor Science and Technology, 20, S266.10.1088/0268-1242/20/7/018
- Frank, M. G., Maccario, C. J., & Govindraju, V. (2009). Behaviour and security. In P. Seidenstat, & F. X. Splane (Eds.), Protecting airline passengers in the age of terrorism (pp. 86–106). Santa Barbara, CA: Greenwood.
- Funato, T. (2005, March). Lessons learned from Tokyo subway sarin gas attack and countermeasures against terrorist attacks. Presentation made to Workshop on Implementing Sustainable Urban Travel policies in Japan and other Asia-Pacific Countries, Tokyo.
- Furton, K. G., & Myers, L. J. (2001). The scientific foundation and efficacy of the use of canines as chemical detectors for explosives. Talanta, 54, 487–500.10.1016/S0039-9140(00)00546-4
- Government Accountability Office. (2010). Technology assessment: Explosives detection technology to protect passenger rail. United States Government Accountability Office. Retrieved from http://www.gao.gov/new.items/d10898.pdf
- Gregson-Green, L., Dainty, A., & Bosher, L. (2013). Understanding the impacts of multiple stakeholders on the future security of main English railway stations. Infrastructure Risk and Resilience, 2013, 34–40.
- Haines, A. (2009). The role of automatic number plate recognition surveillance within policing and public reassurance (Doctoral dissertation). University of Huddersfield.
- Hale, C., & Charles, P. (2009, September). Managing peak demand for passenger rail: A literature review. In 32nd Australasian Transport Research Forum (ATRF), Auckland.
- Hardmeier, D., Hofer, F., & Schwaninger, A. (2005, October). The X-ray object recognition test (X-ray ORT)-a reliable and valid instrument for measuring visual abilities needed in X-ray screening. In Security Technology, 2005. CCST’05. 39th Annual 2005 International Carnahan Conference on, 189–192 (IEEE).
- Hofer, F., & Wetter, O. E. (2012). Operational and human factors issues of new airport security technology—Two case studies. Journal of Transportation Security, 5, 277–291.10.1007/s12198-012-0096-5
- Heuer, R. J., & Pherson, R. H. (2011). Structured analytical techniques for intelligence analysis. Washington, DC: CQ Press.
- International Organization for Standardization (ISO). (2011). ISO/IEC/IEEE 29148:2011 – Systems and software engineering — Life cycle processes — Requirements engineering. ISO/IEC/IEEE Switzerland: ISO.
- Jacobson, S. H., Lee, A. J., & Nikolaev, A. G. (2009). Designing for flexibility in aviation security systems. Journal of Transportation Security, 2(1–2), 1–8.
- Jenkins, B. M. (2007). The terrorist threat to surface transport. San Jose, CA: Mineta Transport Institute. Retrieved from http://frequency.transportation.org/sites/security/docs/Jenkins–The%20Terrorist%20Threat%20to%20Surface%20Transportation.pdf
- Jenkins, B. M., Butterworth, B. R., & Gerston, L. N. (2010). Supplement to MTI study on selective passenger screening in the mass transit rail environment. San Jose, CA: Mineta Transportation Institute. Retrieved from http://www.transweb.sjsu.edu/MTIportal/research/publications/documents/Selective%20Screening%20Supplement%20%28with%20Covers%29.pdf
- Jenkins, B. M., & Trella, J. (2012). Carnage Interrupted: An analysis of fifteen terrorist plots against public surface transportation (Report No 11 – 20). San José, CA: Mineta Transportation Institute.
- Kirschenbaum, A. A., Mariani, M., Gulijk, C. V., Rapaport, C., & Lubazs, S. (2012). Airports at risk: The impact of information sources on security decisions. Journal of Transportation Security, 5, 187–197.10.1007/s12198-012-0091-x
- Kirchhoff, G. F., Morosawa, H., Barkhuizen, J., Bussinger, C., Sutseyo, H., & Bey, J. F. (2007). The Asian passengers’ safety study of sexual molestation on trains and buses: The Indonesian pilot study. Acta Criminologica, 20, 1–13.
- Kraft, E. R. (1987). A branch and bound procedure for optimal train dispatching. Journal of the Transportation Research Forum, 28, 263–276.
- Krouse, W. J. (2010). Terrorist watchlist checks and air passenger prescreening. Collingdale, PA: Diane Publishing.
- Kydd, A. H., & Walter, B. F. (2006). The strategies of terrorism. International Security, 31, 49–80.10.1162/isec.2006.31.1.49
- Lee, H., Smeaton, A. F., O’Connor, N., & Murphy, N. (2005). User-interface to a CCTV video search system. IEEE International Symposium on Imaging for Crime Detection and Prevention (ICDP 2005), January, 39–43.
- Li, S. M., & Wong, F. C. (1994). The effectiveness of differential pricing on route choice. Transportation, 21, 307–324.
- Litman, T. (2007). Evaluating rail transit benefits: A comment. Transport Policy, 14, 94–97.10.1016/j.tranpol.2006.09.003
- Lyons, G., & Chatterjee, K. (2008). A human perspective on the daily commute: Costs, benefits and trade‐offs. Transport Reviews, 28, 181–198.10.1080/01441640701559484
- McCoy, T., Bullock, R. J., & Brennan, P. V. (2005). RFID for airport security and efficiency. IEE Seminar on Signal Processing Solutions for Homeland Security, January, 8.
- Meyer, S. (2012). Reducing harm from explosive attacks against railways. Security Journal, 25, 309–325.10.1057/sj.2011.23
- Meyer, S., & Ekblom, P. (2012). Specifying the explosion-resistant railway carriage—A ‘bench’ test of the security function framework. Journal of Transportation Security, 5, 69–85.10.1007/s12198-011-0082-3
- Monahan, T. (Ed.). (2006). Surveillance and security: Technological politics and power in everyday life. Oxford: Routledge.
- National Counter Terrorism Security Office (NaCTSO). (2012). Counter terrorism protective security advice for general aviation v2. London: Association of Chief Police Officers.
- NDTV. (2013, August 12). Increased security at Delhi’s airport and metro ahead of Independence day. Retrieved from http://www.ndtv.com/article/cities/increased-security-at-delhi-s-airport-and-metro-ahead-of-independence-day-404729
- O’Flynn, D., Desai, H., Reid, C. B., Christodoulou, C., Wilson, M. D., Veale, M. C., & Speller, R. D. (2013). Identification of simulants for explosives using pixellated X-ray diffraction. Crime Science, 2(1), 1–6.
- O’Neill, C., Robinson, A. M., & Ingleton, S. (2011). Mitigating the Effects of Firebomb and Blast Attacks on Metro Systems. Procedia – Social and Behavioral Sciences, 1–10. Retrieved from http://www.ncl.ac.uk/newrail/assets/docs/ONeilletal-Mitigatingtheeffectsoffirebomb.pdf
- Peterman, D. R. (2006). Passenger rail security: Overview of issues. Congressional Research Service. Retrieved from http://www.au.af.mil/au/awc/awcgate/crs/rl32625.pdf
- RAND’s Database of Worldwide Terrorist Incidents (RDWTI). Retrieved from http://www.rand.org/nsrd/projects/terrorism-incidents.html
- Riley, J. (2004). Terrorism and rail security. Santa Monica, CA: RAND. Retrieved from http://www.rand.org/pubs/testimonies/2005/RAND_CT224.pdf
- Siemiatycki, S. (2006). Message in a metro: Building urban rail infrastructure and image in Delhi, India. International Journal of Urban and Regional Research, 30, 277–292.10.1111/ijur.2006.30.issue-2
- Singh, S., & Singh, M. (2003). Explosives detection systems (EDS) for aviation security. Signal Processing, 83, 31–55.10.1016/S0165-1684(02)00391-2
- Smith, L., & Louis, E. (2010). Cash in transit armed robbery in Australia. Trends and Issues in Crime and Criminal Justice, 397, 1–6.
- Sweet, K. M. (2009). Aviation and Airport Security. Terrorism and Safety Concerns. Boca Raton, FL: CRC Press.
- Taylor, B., Loukaitou-Sideris, A., Liggett, R., Fink, C., Wachs, M., Cavanagh, E., Cherry, C., & Haas, P. J. (2005). Designing and operating safe and secure transit systems: Assessing current practices in the United States and abroad (Report No. 04-05). Mineta Transportation Institute: San Jose, CA.
- UITP: International Association of Public Transport. (2013). What are metros? Retrieved November 19, 2013, from http://www.uitp.org/Public-Transport/metro/index.cfm
- Vuchic, V. R. (2005). Urban transit: Operations, planning, and economics. Hoboken, NJ: Wiley.
- Wetter, O. E., Laube, R., & Hofer, F. (2009, October). A comparison between two leadership models for security checkpoints: Enhancing processes by optimizing crew performance. Paper presented at Security Technology, 2009. 43rd Annual 2009 International Carnahan Conference.
- Wetter, O. E., Lipphardt, M., & Hofer, F. (2010, October). External and internal influences on the security control process at airports. Paper presented at Security Technology (ICCST), 2010 IEEE International Carnahan Conference.
- Wilson, J. M., Jackson, B. A., Eisman, M., & Riley, K. J. (2007). Securing America’s passenger rail systems. Santa Monica: RAND. Retrieved from http://www.rand.org/pubs/monographs/2007/RAND_MG705.pdf
- World Metro Database. (2013). Retrieved from http://mic-ro.com/metro/table.html
- Yoo, K. E. (2009). Screening on the ground, security in the sky. In P. Seidenstat & F. X. Splane (Eds.), Protecting airline passengers in the age of terrorism (pp. 63–85). Santa Barbara, CA: Greenwood.