?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Matrix Multiplication is a basic engineering and scientific problem, which has application in various domains. There exists many cryptographic solutions for secure computation of matrix multiplication, but cryptographic preamble makes them infeasible for outsourcing with large input size to the cloud server. In this paper, we propose a privacy-preserving, verifiable and efficient algorithm for matrix multiplication in outsourcing paradigm illustrated by the following scenario: the client is having a large data-set and needs to perform matrix multiplication, but unable to process due to the lack of computing resources. Therefore, the client outsources the computation to the cloud server. We evaluate the algorithm on security, efficiency and verifiability parameters and discuss the implementation details. The result analysis shows that the algorithm is highly efficient and endorses the practical usability of the algorithm. Using this algorithm, we can mostly replace the costly cryptographic operations and securely solve matrix multiplication on a large data-set.
Public Interest Statement
Outsourcing is a common practice widely used as a cost-effective strategy in the business world. It is very often clients take help from some external vendor to accomplish their work. The reason for outsourcing could be many, a client want to access some specialized service or someone offering a service more economical than producing in-house. With the advent of cloud computing a variety of client looking for its services since cloud offers convenient on-demand network access to infrastructure services (CPU, Storage, Network), platform services (programming environment, language, library, services and tool) and software services (application such as web-based email service) in pay-as-per-use manner on a very economical cost. However, despite the tremendous benefit outsourcing data and computation to cloud server generates various privacy and security concerns, which must be handled before using it for real life problems.
1. Introduction
The growing number of smart devices and their increasing desire to execute computationally intensive task makes the outsourcing of computation to the cloud server a promising solution. The outsourcing paradigm enables a resource-constrained client to execute large computation task by offloading their computation load to the massive cloud servers. The availability of cloud servers empowers the clients to execute large computations. Now they are no longer restricted to their limited CPU, storage, and bandwidth (Shiraz, Gani, Khokhar, & Buyya, Citation2013). Despite the tremendous advantage, this promising paradigm brings many security and privacy concerns such as confidently of data (input and output) and the integrity of result, which makes the client reluctant to outsource its computation on the cloud server. In particular, the client data carries sensitive information such as personal health records, financial records, trends of stock, scientific research records, just list a few. Therefore, these types of confidential data needs to be encrypted to maintain the confidentiality and the integrity, before outsourcing to the cloud server. One such approach to address such security concerns is apply some encryption scheme. However, the traditional encryption scheme would not work here. Because the traditional encryption scheme changes the input data into cipher and performing meaningful computation on cipher is very difficult. The second concern is the correctness of the result since the cloud server is not a trusted party. Therefore, it may return a wrong result due to a flaw, bug in the logic or some time intentionally deviates from the algorithmic instructions (in case of malicious cloud). This means there is no guaranty on the integrity of the result. Therefore, an outsourcing algorithm must be proficient in providing privacy to the confidential data (input and output) and verifying the correctness of the result. Further, efficiency is also an important challenge in the process of algorithm design. In outsourcing framework, the client perform some operations such as transformation, verification, and retransformation. Therefore, the execution time needed to perform client operations (transformation, verification, and retransformation) must be substantially lesser than executing the original outsourced ploblem else the outsourcing has no meaning (Chen, Xiang, & Yang, Citation2014; Lin & Chen, Citation2010; Mohassel, Citation2011).
The particular problem that we address in this paper is matrix multiplication. The matrix multiplication is an elementary operation and useful in many domains such as statistics, finance, oil and gas explorations, machine learning, sensor network, agriculture, predicting rainfall, image encryption, watermarking, telemedicine and others. There are various algorithms available for secure outsourcing of various core problems of linear algebra including matrix multiplication (Atallah & Frikken, Citation2010; Atallah, Frikken, & Wang, Citation2012; Fiore & Gennaro, Citation2012; Mohassel, Citation2011; Zhang & Blanton, Citation2014). Many of these algorithms were not initially designed for cloud environment. Therefore, these algorithms do not consider the computational asymmetry of the cloud server and the client. Further, these algorithms were developed using complex cryptographic preambles to encrypt the data-set (input and output), which makes them unsuitable for the computation on the cloud with large dats-et. Furthermore, these algorithms does not consider the result verification as an essential requirement. However, for the secure outsourcing in the malicious cloud environment, result verification is a vital part of the algorithm design. These gaps in the present state-of-the-art motivate us to design a secure and efficient outsourcing algorithm for matrix multiplication.
The proposed secure outsourcing algorithm for Matrix Multiplication (MM) on various inputs x1, x2 … xn is securely executes the computation on the cloud server, while maintaining the privacy of input/output, correctness, result verification and computational efficiency.
The main contribution of paper includes following:
| (a) | In this paper, we are introducing orthogonal matrix to protect the privacy of the data-set. The algorithm is capable of multiplying any valid dimension of (M1 & M2). | ||||
| (b) | The proposed algorithm required an optimal one round of communication. The client in the proposed algorithm verifies the encrypted result obtained from the cloud server with modest overhead and high probability. | ||||
| (c) | The analytical analysis shows that the algorithm is successfully meeting the challenges of correctness, security, verifiability, and efficiency. | ||||
| (d) | The experimental evaluation validates the proposed algorithm. The result analysis shows that the algorithm is highly efficient and endorses the practical usability of the algorithm. All the experimental results can be reproduced. | ||||
The rest of the paper is organized as follows: Section 2 discusses the related work done in the area of secure computation. Section 3 provides the detail discussion on the matrix multiplication outsourcing problem, its mathematical elements, and system model to solve them. Section 4 formulates the proposed matrix multiplication outsourcing algorithm and provide detail discussion on the design of the outsourcing algorithm. Section 5 presents analytical analysis of the proposed outsourcing algorithm on correctness, security, verifiability and efficiency parameter. Section 6 presents the experimental analysis of the proposed outsourcing algorithm. Finally, concluding remark and future direction incorporated in Section 7.
2. Related work
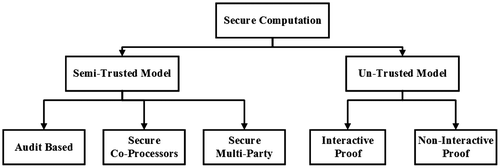
In literature, there are various algorithms available for secure outsourcing of various core problems of linear algebra. Moreover, secure outsourcing is divided into two parts i.e. semi-trusted computing model and untrusted computing model. A detail classification of secure outsourcing algorithms are shown in Figure . In the semi-trusted computing model, the cloud server follows the algorithm instructions and produces the correct result, but the cloud server secretly records the accessible data, and attempt to retrieve meaningful information. In the semi-trusted model, the first one is audit based (Belenkiy et al., Citation2008; Monrose, Wyckoff, & Rubin, Citation1999; Seshadri et al., Citation2005), the client or the trusted workers in audit-based approach re-computes some part of computation performed by the untrusted workers. This approach is unfeasible for a computationally weak client because if the client is capable of performing the computation, then there is no need to outsource the computation to the cloud server. This method also required that some workers must be honest or at least non-colluding in nature. The second one is secure-co-processors (Bajikar, Citation2002; Smith & Weingart, Citation1999; Yee, Citation1994), or Trusted Platform Modules (TPMs) method, which required to deploy trusted hardware on the server to provide an isolated execution environment. This model is also impractical, since it is not possible to install TPM on third party cloud server. The last one is secure multiparty computation, the computation is divide among two or more workers without allowing any participated worker to view another individual’s secret data. The resultant of computation is the union of the output of all workers (Dreier & Kerschbaum, Citation2011; Du, Chen, & Han, Citation2004; Lindell & Pinkas, Citation2009; López-Alt, Tromer, & Vaikuntanathan, Citation2012). This model is not feasible in cloud environment since this model required that the participating workers must have comparable computing capability. However, client transfers the entire computation load to the massive cloud servers in the outsourcing paradigm in cloud environment.
In untrusted computing model, the server can deviate from the algorithmic instructions and behave arbitrarily. The solution of this problem applies some encryption techniques to perform secure computation and handle the result verification to verify the correctness of the result. There exists two types of verifiable outsourcing i.e. interactive proof and non-interactive proof. In interactive proof, a weak verifier actively challenges a server (prover). The prover replies a probabilistic proof to the client (verifier) to convince him (verifier) about the truth of the statement that he is unable to compute (Fortnow & Lund, Citation1993; Goldwasser, Kalai, & Rothblum, Citation2008; Goldwasser, Micali, & Rackoff, Citation1989). The second one is the non-interactive proof, where a weak client outsources the computation to a powerful server, the server returns the result along with the proof of verification (Chen, Chang, Hsieh, & Chen, Citation2014; Chen et al., Citation2015; Chen, Li, & Ma, Citation2014; Gennaro, Gentry, & Parno, Citation2010; Hong, Vaidya, & Lu, Citation2012; Hu & Tang, Citation2015; Laud & Pankova, Citation2015; Lei, Liao, Huang, Li, & Chunqiang, Citation2013; Lei, Liao, Member, Huang, & Li, Citation2015; Wang, Ren, Wang, & Urs, Citation2011; Wang, Ren, Wang, & Wang, Citation2013; Zhou, Li, & Member, Citation2016).
Our solution applies non-interactive proof to provide verifiability of computation. Therefore, the attention is more on non-interactive verifiable algorithms. Gentry’s provides a novel Fully Homomorphic Encryption (FHE) scheme (Gentry, Citation2009). This scheme allows the server to perform arbitrary computation on encrypted input, but the solution suffers from the complexity of FHE that makes it far from practical use for outsourcing (Gennaro et al., Citation2010; Gentry, Citation2010; Mohassel, Citation2011; van Dijk, Gentry, Halevi, & Vaikuntanathan, Citation2010). Moreover, FHE does not guarantees that the server performs correct computation. Gennaro et al. (Citation2010) has proposed a non-interactive solution for the secure outsourcing of polynomial function. First, they model the polynomial function into Yao’s grabbled circuit (Yao, Citation1982, 1986). Then homomorphically (Gentry, Citation2009) encrypt the circuit and send to the server for the execution of the polynomial function. The cloud server performs the execution & returns a computationally sound non-interactive proof that can verify in O(m) time. Another elegant solution is proposed by Chung, Kalai, and Vadhan (Citation2010). The client performs pre-processing and create hundreds of problem instances mostly of same type. Then apply homomorphic encryption for privacy on problem instances. The server computes these functions without knowing the actual inputs. Finally, the client verifies the solution of the same type of problem for ensuring their correctness. The main drawback of these two algorithms that they are incurring huge computation load on both client and server due to the complex homomorphic encryption. These algorithms are also require modeling of problem into circuit, which needed to dealing with large amount of parameters. However, one main advantage of these methods that they took constant time for verification.
Furthermore, there are many algorithms available, which address some specific type of problems. Atallah, Pantazopoulos, Rice, and Spafford (Citation2002) have carried out an investigation for many problems such as matrix multiplication, quadrature, a solution of the differential equation, the system of linear equations. Their solution explicitly leaking private information. Besides, the proposed work do not handle the result verification. Further, Benjamin and Atallah (Citation2008) gave an outsourcing algorithm for matrix multiplication. The algorithm developed on the assumption of two non-colluding servers that the servers will not share secret information between them. However, this method is vulnerable to colluding attack. Later on Atallah and Frikken (Citation2010) proposed a secure matrix multiplication outsourcing algorithm based on the theory of secret sharing. This algorithm is an improvement of their previous work in Benjamin and Atallah (Citation2008), regarding single server and computational efficiency. However, this algorithm also suffers from computational overhead due to Shamir’s secret sharing technique. The scalar multiplication complexity expands up to polynomial time. Blanton, Zhang, and Frikken (Citation2013) addressed the large scale computation of biometric computation. The implementation leverages individual structures of distance computation and random sampling. The result verification method can verify the result with modest overhead and high probability. Lei et al. (Citation2013) presented matrix inversion outsourcing algorithm. They uses monomial matrix for the privacy of input/output matrix. The algorithm efficiently outsources the matrix inversion to the cloud server, while maintaining the correctness, privacy of the input-output, and verifies the result efficiently. Next, an algorithm addresses linear programming (LP) in Wang, Ren, and Wang (Citation2011). This method split the LP solver into two parts; those are the LP solver on cloud and the LP parameters on client-side. The client transforms the input data using a transformation technique and outsources to the LP solver on a cloud server. Then cloud server solves the linear programming problem with the help of LP solver and returns the result. The client verifies the result using the fundamental theorem of duality. Further, another algorithm is presented for LP problem, which reduces the computation and communication time significantly (Hong et al., Citation2012). There are many algorithms published recently for the “system of linear equation” (Chen et al., Citation2015; Chen, Xiang, et al., Citation2014; Wang, Ren, Wang, & Urs, Citation2011). The algorithm proposed by Wang, Ren, Wang, and Urs Citation(2011) requires (n) round of communication between the client and cloud before the client get the convergent solution. The algorithm encrypts the input in O(n2) in setup phase and verify the output in O(n2). The n round of communication between the client and the cloud is the main drawback of this method which increses the communication overhead and also add security vulnerability. Next, an algorithm in Chen, Xiang, et al. Citation(2014) identified a new solution for the linear equation, which employs some special linear transformations using diagonal matrices. This algorithm requires one round of communication between the client and the cloud. Further, an algorithm (Chen et al., Citation2015) utilizes the sparse matrix to propose a new secure outsourcing algorithm of large-scale linear equations in the fully malicious model. The algorithm requires only O(1) round of communication between the client and cloud server.
3. Details of secure outsourcing algorithm
3.1. Outsourcing algorithm
A secure and verifiable outsourcing algorithm has five steps in the following order: KeyGen, ProbTrans, Compute, Verify, and Retransform.
| (a) |
| ||||
| (b) |
| ||||
| (c) |
| ||||
| (d) |
| ||||
| (e) |
| ||||
3.2. System model
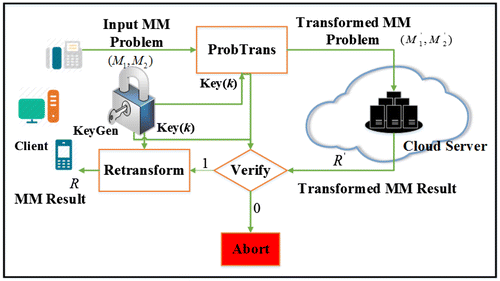
The proposed system model for secure outsourcing of matrix multiplication algorithm is shown in Figure . The resource-constrained client wants to execute a matrix multiplication problem, but due to lack of computing resources, the client unable to perform such expensive computation. Thus, the client outsources the problem to the massive cloud servers. The client first applies a transformation operation on the input problem and produces
. Now, this transformed problem
is outsourced to the cloud server. Further, the cloud server computes the matrix multiplication for the transformed input
and produces the result R′. The client receives the result R′ from the cloud server. The client first verifies the encrypted result (R′) with the help of secret keys and the transformed input
. If the result passes the verification test successfully, then only the client re-transforms/decrypts the result to obtain the result R of the problem
otherwise the algorithm is aborted.
3.3. Threat model
The security threat in outsourcing system model originated from the suspicious behavior of the cloud server. The previous work for the secure outsourcing computation defines three threat model that are “Trusted Model”, “Semi-Trusted Model”, and “Untrusted Model” (Chen et al., Citation2015; Lei et al., Citation2013; Lei, Liao, Huang, & Heriniaina, Citation2014).
3.3.1. Trusted model
The cloud server follows the algorithm instructions correctly and it does not attempt to unauthorized access to the client information. Therefore, no need of encryption and verification.
3.3.2. Semi-trusted model
In this model, the cloud behaves as “honest but curious” or “lazy but honest” or even both. Goldreich, Micali, Goldreich, Micali, and Wigderson (Citation1987) first introduces the honest but curious model. The server follows the algorithm instructions and produces the correct result, but the cloud server tries to secretly record the accessible data and attempt to retrieve meaningful information. However, the proposed algorithm has been design to handle such threat model. The cloud server is not able to extract the original information from the transformed input or the result. The lazy but honest model behaves honestly; it does not record any such information or computation but behave lazily, that the cloud server might not perform on the agreed service level. It might send some invalid result to save computing resources. To, share the remaining resources with other clients to increase the financial gain. The proposed system model for matrix multiplication successfully addresses this security threat. The client can detect the correctness of result with an optimal probability.
3.3.3. Un-trusted model
The third threat model comes from the malicious behavior of cloud server, which is the strongest adversarial model. In this model, the server could be “lazy”, “curious”, and “dishonest”. The cloud server deviates from the algorithm instructions and performs arbitrary. The cloud server may return random indistinguishable result and try to escape and not being detected by the client. The proposed algorithm can detect any such malicious adversary. For this purpose, an effective and efficient result verification technique has been introduced, which verify the correctness of the result.
3.4. Basic idea of matrix multiplication outsourcing
The matrix multiplication operation is represented as:(1)
(1)
where M1 is an m * n matrix in , M2 is an n * p matrix in
, and the resultant R is an m * p matrix in
. The basic idea of matrix multiplication outsourcing algorithm is as follow: Let the resource-constrained client has a matrix multiplication problem of large input size, but due to lack of computing resources, the client outsources this problem to the cloud server. The MM problem is denoted as
and its solution as R. Further, the client applies a transformation operation on input data to preserve the privacy of data. Then, this transformed data is outsourced to the cloud server. Thus, from the viewpoint of the cloud server, this transformed problem is same as any other matrix multiplication problem. However, the cloud server could read this input, but unable to recover the original client information. In this way, the algorithm protects the privacy of the input. Then, the cloud server executes the matrix multiplication on the transformed input and produces the encrypted result
. Then, the client verifies the integrity of result
, once the result passes the verification step, then client retransform/decrypts and accepts the result.
4. Privacy preserving proposed transformation technique for matrix multiplication
In this section, we present the development of linear transformation method to protect the privacy of client’s data. For a matrix multiplication problem , the privacy of
called the input privacy and the privacy of (R) called the output privacy. The client applies an efficient and secure transformation operation on the data
to transformed MM problem
, the transformation operation maintain the confidentiality of data (input and output).
| (a) | The equation R = M1 * M2 provides us direction to transform the input ( | ||||
(2)
(2)
where AT is the transpose of matrix A and I is identity matrix. Now, A is an orthogonal matrix, if M′1 = (M1 * A) and M′2 = (AT * M2), then the transformed solution R′ = (M1A * ATM2). However, an issue has been rise, that this method is unable to provide privacy to the output result. The cloud server could easily read the output result since R = R′.
| (b) | We further explore the method to find a better solution, which provide privacy to the both input and output. In the pursuit of solution, if we transform the input matrix M′1 = (D1 * M1 * A) and M′2 = (AT * M2 * D2), and putting these transformed value to the Equation (1), the output result | ||||
(3)
(3)
| (c) | The proposed method discussed in section (b) is analyzed to see whether its efficiency can be further improved. We look into the matrix property for better results. It has found if we restrict the key matrices A, D1 & D2 to diagonal matrix. The efficiency of the proposed algorithm will be improved. Thus, the client will achieve more performance gain. When the orthogonal matrix A restrict to be diagonal, the orthogonal property required to be relaxed to some extent, that means the entries of diagonal elements of matrix A are either r or - r, where r is a real number. Thus, the diagonal matrix A is such that, ATA = r2I. Now apply the new values of key matrices to transform the matrix multiplication problem. The transformed problem | ||||
(4)
(4)
The output result in both the Equations (3) and (4) are not leaking information to the cloud server. Moreover, the method discussed in section (c) improves the efficiency of the algorithm, but lagging in the security than the method in section (b). Therefore, there is a trade-off between security and efficiency of the proposed algorithm. Based on the requirement of security and efficiency the client either use method (b) or method (c). Further, it is worth noting that at the place of diagonal matrix D1 & D2, permutation matrix can be utilized. However, the permutation matrix takes more time for computation than the diagonal matrix but provides greater security. Thus, for the application, which requires more security can choose either one of the combinations as per their requirement.
4.1. Details of matrix multiplication algorithm construction
There are five sub-algorithms in the proposed matrix multiplication outsourcing algorithm that are ,
,
,
, and
. Since the proposed algorithm has developed for malicious cloud environment, the key generation algorithm run each time for a new problem submission. This effective mechanism (new keys for a new problem) diminishes the chance of known-plain-text and chosen-pain-text attack.
4.1.1. 

The client invokes this algorithm with an input security parameter , this algorithm first generates an identity matrix. These matrices are masked with the non-zero random numbers
which produces two diagonal matrices (D1, D2) and then the orthogonal matrices (A). The orthogonal matrix A has been generated using Gram-Schmidt algorithm (Björck, Citation1994; Estep & Higham, Citation2004). In this way the key matrices are generated, which are {k = A, D1, D2}.
Table
Table
4.1.2. 

For every new input, the sub-algorithm invokes and transforms the input in order to preserve the privacy. This algorithm transforms the input into
. This operation dominates the client side computation cost, but still efficient than computing a general matrix multiplication. The one-time cost of
is O (mn + np), after that the MM outsourcing algorithm runs very efficiently.
Table
4.1.3. 

This sub-algorithm performs the computation on the cloud server. The operation computes matrix multiplication as
.
Table
4.1.4. 

The cloud server sends the computed result to client. The client computes , where x is the column matrix x ∊ {1, 0}. This algorithm introduces an extra term x to minimize the complexity of computation. Since the matrix-vector multiplication only cost O (n2). If the cloud server has correctly executed the
correctly, the relation (D = 0) should be hold true
Table
4.1.5. 

If the matrix multiplication passes the verification step successfully then only this step will execute to find the original values of the matrix multiplication
else this step is simply omitted.
Table
5. Analysis of proposed matrix multiplication algorithm
The proposed MM outsourcing algorithm is simultaneously meeting all the four challenges of an outsourcing algorithm that are correctness, security, verifiability, and efficiency. The analytical analysis of the algorithm follows the previous work in (Chen, Chang et al., Citation2014). Further, we present an analytical analysis of proposed algorithm in a malicious cloud environment.
5.1. Correctness analysis
The matrix multiplication outsourcing algorithm will perform correctly, only if the client and the cloud server follow the algorithm instructions properly and produces correct result. Further, we are providing a mathematical explanation, which verifies our claim.
Theorem 1
The proposed algorithm is correct if both the client and cloud follows the algorithm instructions properly.
Proof
The client first transforms the input () into
, and M′2 = (ATM2D2), then the cloud server will compute R′,
(a) Correctness Analysis, when the key matrix A is orthogonal and are diagonal matrices.
From the Equation (3),
Then in the procedure of matrix multiplication re-transformation, the client will compute result R where,(5)
(5)
(b) Correctness Analysis, when the key matrix A is a orthogonal diagonal matrix and D1, D2 are diagonal matrices.
From the Equation (4),
The client computes the result R where,(6)
(6)
Thus, the client will get the correct result in both the cases, which implies the proposed algorithm is correct.
5.2. Security analysis
In the malicious cloud environment, the cloud server behaves as curious cloud. Therefore, the server may record all the client information (input and output) and then tries to retrieve the original information from the recorded information. However, the cloud server never succeeded to recover the original information. Further, a security analysis is presented, which justify our claim. The security analysis follows the previous work on secure outsourcing on cloud computing (Chen, Chang et al., Citation2014; Wang et al., Citation2013).
Theorem 2
In a malicious cloud model the proposed matrix multiplication outsourcing algorithm able to protect the privacy of client’s input (M1, M2) and the processed output R.
Proof
The proposed algorithm able to provide privacy to the input and output data-set of the matrix multiplication. We have provided mathematical proof to justify out claim.
First, the input privacy
The client first transforms the original input matrix to
where
and
. The cloud server has only access to the transformed problem
and have no information about
and the security keys (A, D1, D2). The matrices M′1, M′2 are not leaking information to the cloud server about the original matrices (M1 and M2). The matrices (A, D1, D2) are in
respectively.
| (a) | Security analysis, when the key matrix A is orthogonal and | ||||
Let each entry in the orthogonal matrix A is l bit long integer. The matrix A is a n * n matrix in so, there are approximately
bit of information, that means there are
possible choices of key matrix A. Similarly, D1 & D2 are diagonal matrices, they have
bit of information. Further, the key matrices (A, D1, D2) combined have
possibilities, which is a large value in term of m, n, and p. The estimated time of brute-force attack on the key space to recover the original matrix (M1 and M2) is
, which is a exponential bound quantity in terms of (m, n, p). Further, the client generates a new key for every new problem submission to cloud server. Thus, the cloud server cloud never recovers meaning full information about the input data.
| (b) | Security analysis, when the key matrix A is an orthogonal diagonal matrix and D1, D2 are diagonal matrices. | ||||
The key matrix A is a diagonal matrix and its entries are set to either r or - r, where the r is a random real number of l bit long. There are 2n+l possibility of A, whereas for diagonal matrix D1 & D2 there are 2ml+pl possibilities. In this case the client has 2ml+pl+n+l possible choices for the key matrices, which is still an exponential time bound quantity in terms of (m, n, p). Therefore, in this case also the cloud server could not recover any meaningful information.
Second, the output privacy
Similarly, the output result is also protected in the same way as the input data is protected. The resultant matrix is also not leaking any information to the cloud. Thus, a malicious cloud server even if record the input and the output information, but never able to recover the original input and output information. Besides, the client generates a pair of new securities keys (A, D1, D2) for every new problem submission to the cloud server. Thus, our encryption system is similar to one-time-pad encryption system. Therefore, there is also no chance of known-plain-text attack or chosen-plain-text attack.
5.3. Verifiability analysis
In the malicious threat model, the cloud server may deviate from the actual instruction of the matrix multiplication outsourcing algorithm and return a random arbitrary result. Thus, the matrix multiplication outsourcing algorithm must be equipped with the result verification process, which is able to verify the correctness of the result.
Theorem 3
A wrong/invalid result never passes the result verification step.
Proof
If the cloud server performs computation correctly, a wrong result R′ never passes the verification test.
Therefore,(7)
(7)
If the cloud produces a wrong result, it never passes the verification step. Further, we provide proof to justify the claim. If cloud produces a wrong result, then , then their exist at least a row D which is not equals to zero.
(8)
(8)
Let the row di ≠ 0(9)
(9)
So, there exist at least one element in this row which is not equal to zero, let Di,k ≠ 0,(10)
(10)
Applying total probability theorem,(11)
(11)
, substituting these values to Equation (11).
(12)
(12)
, substituting this value to Equation (12)
(13)
(13)
The verification process run k times, the value of k is a tradeoff between efficiency versus verifiability.(14)
(14)
The proof reveals that even if the cloud produces the wrong result, it never passes the verification test. The probability to pass the erroneous result is a negligible quantity. Thus, the client able to catch the erroneous result produced by cloud server. In this article, we have performed the experiments by taking k = 20, while 20 bit is acceptable, because 1/220 is itself a big quantity , means the verification process fails to detect a wrong result once in million.
5.4. Efficiency analysis
The outsourcing algorithm is divided into two parts that are the client-side and the cloud-side computation. The client performs the following sub-operations the Key Generation , problem transformation
, Result Verification
and the Result re-transformation
, while the cloud server computes the computationally expensive matrix multiplication algorithm. Table
Table 1. Theoretical performance analysis of MM outsourcing algorithm
Theorem 4
The secure outsourcing algorithm is efficient implementation of matrix multiplication
Proof
In order to perform secure outsourcing of matrix multiplication to cloud server, the client needs to perform some matrix multiplication in procedure of ,
, and
. However, due to special arrangement of key matrices ((A, D1, D2) that is only one element is present in each row and column. The multiplication at client-side only cost quadratic times, since the cost of addition is omitted. Thus, the multiplication cost for M′1 = (D1M1A) and M′2 = (ATM2D2) only cost O (mn + np). For the result verification the client performs the following operation
. The asymptotic complexity of this operation is only O (mp). Once the result R′ computed by cloud server passes the result verification algorithm. The client retransform the result R′ execution following operation
. The time complexity required to execute this operation is only O (mp). Thus, the asymptotic time complexity of client-side computation is only O (mn + np + mp), while the cloud server takes O (mnp). Thus the proposed outsourcing algorithm is
times efficient than the general matrix multiplication algorithm.
The client got a clear performance gain due to time complexity gap between client and cloud. As the size of m, n, & p increases the client will got sufficient performance gain. Therefore, this outsourcing algorithm is efficient and a feasible solution from resource constrained client.
5.5. Comparison analysis
In this section, we provide a comparison of the proposed algorithm with the published work (Atallah & Frikken, Citation2010; Benjamin & Atallah, Citation2008). The algorithm in (Benjamin & Atallah, Citation2008) is working on the assumption of two non-colluding servers. Thus, if the servers are colluding they can pass secret information between them that makes this approach vulnerable for colluding attack. Besides, this algorithm works in a semi-trusted model, which makes the algorithm ill-suited for the untrusted behavior of cloud. The algorithm in Atallah and Frikken (Citation2010) is an improvement over the previous algorithm in Benjamin and Atallah (Citation2008). It achieves provable security on the Shamir secret sharing scheme. This algorithm is work over finite field and suffers from large communication overhead of secret sharing. Therefore, do not meeting the requirements of outsourcing of large computation. A comparative analysis of proposed algorithm with these state-of-the-art algorithms are presented in Table .
Table 2. Comparison with other MM outsourcing algorithm
6. Experimental analysis
The implementation of the proposed algorithm is based on the mathematical and theoretical analysis discussed in the previous sections. The algorithm is implemented using Matlab language version 2014a on a system simulating both the client and server. The system configuration is “CPU Intel® Core™ I3 (CPUs)~1.8 GHZ 4 GB Ram”. The client and cloud server having the same computing resources, which reflects the actual running time of the algorithm. If the algorithm is executed on two different systems, the algorithm performance would be case specific. Although, in reality, the cloud servers always have more computing resources that will further reduce the execution time of the problem. The evaluation of the proposed algorithm mainly focused on the client-side execution time and cloud-side execution time. In addition, for the proposed algorithm, the execution cost dominates and the communication cost is significantly small. Therefore, we ignore the communication cost in the performance analysis.
To measure the performance of the algorithm, we are using three standard parameters efficiency, performance-gain and the relative extra cost.(15)
(15)
Ideally, the efficiency of the algorithm should be close to one. If the efficiency is nearby one, it indicates that the execution time of original problem and the encrypted problem is almost same.
The second parameter is performance gain for the client “It represents the actual speed-up the client has gained from outsourcing the problem”.(16)
(16)
Theoretically, the performance gain of the client should always be greater than one.
REC: The relative extra cost is defined as the amount of extra work done by the client and cloud server in outsourcing paradigm as compared to direct method. REC is also known as overhead of the outsourcing algorithm. Ideally, REC should be near to zero, which indicates that the outsourcing paradigm incur minimum burden on the client and the cloud server.(17)
(17)
Further, the terms use in the experimental analysis presented in Table .
Table 3. Terms and description
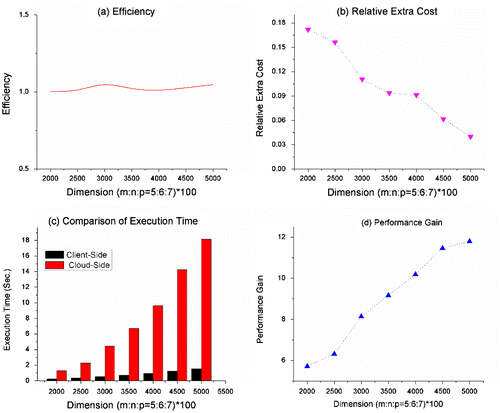
We execute the MM outsourcing algorithm multiple times for each problem instance to get a stable system performance. The experimental performance analysis of the proposed algorithm is shown in Table and Figure . We can see in Figure (a) and Table , that the efficiency parameter remains close to one, which means the outsourcing paradigm adds minimum overhead on the cloud server for executing an encrypted problem. Further, it is shown in Table that the REC parameter stays 0.36896 for (500 * 600 * 700) problem size and 0.03984 for (5000 * 6000 * 7000) problem size, a decrease of 89.20% in REC parameter as the problem size increases from (500*600*700) to (5000 * 6000 * 7000). The values of REC indicate that the extra work done by the cloud and client reduces as the problem size increases, for larger size problem the overhead reduces to great extent. Figure (b) shows that the REC is monotonically decreasing. Further, Figure (c) demonstrates the comparison of execution the times of matrix multiplication using direct method and proposed outsourcing algorithm. The time to execute a problem of size (5000 * 6000 * 7000) is 18.15 s, but when the computation is outsourced to the cloud server using the proposed algorithm, it takes only 1.539 s. This happen because the client in our algorithm work only O (mn + np + mp) for matrix multiplication rather the computation burden of O (mnp).
Table 4. Performance analysis of MM outsourcing algorithm
Therefore, a computational saving of for the client and as the size of problem (m, n, p) increases the client got substantial computational saving. Furthermore, the performance-gain parameter is in double-digit for the larger size problem and able to attain more than 11.79 times, which is a very motivating factor to use MM outsourcing algorithm in real-world scenarios. Note that the graphical performance analysis presented in Figure is stared from matrix of size 2000. Below that size refer to the Table . Finally, the theoretical and experimental analysis of matrix multiplication outsourcing algorithm proves, that the resource-constrained client can execute large matrix multiplication by offloading their computation load to massive cloud servers using matrix multiplication outsourcing algorithm. The proposed work is very efficient and able to maintain the privacy of data under the malicious cloud environment. Due to the rising demand of outsourcing, the proposed solution would be very helpful for the research community to carry out further research work.
It is worth noting that the experimental performance depends on problem dimension, the underlying execution platform, and algorithm for solving matrix multiplication (Lei et al., Citation2013). If the cloud exploits other faster matrix operation algorithms, then client speedup will decrease to some extent. However, as long as the size of the input goes sufficiently large, the client get a significant performance-gain due to the apparent computation gap between the client-side computation and server-side computation.
7. Conclusion
In this paper, we formulated and implemented a new outsourcing algorithm for the matrix multiplication problem. The proposed algorithm is entirely different from the previous algorithms, which were based on the complex cryptographic preambles, that makes them ill-suited for the computation outsourcing with large input size to the cloud computing. Remarkably, the proposed computation outsourcing algorithm has not uses any such complex cryptography techniques and developed by utilizing linear transformation method using the concepts of linear algebra. The algorithm is able to meet the challenges of input/output privacy, correctness, verifiability, and efficiency, which is well demonstrated in the analytical analysis of the algorithm. The proposed algorithm needed a onetime setup cost of O (mn + np + mp) on the client system, while executes the matrix multiplication with O (mnp) on the cloud server. That makes the proposed algorithm times efficient implementation of matrix multiplication. In future, it would be remarkable to see novel algorithms, which reduces the overhead cost incur by the verification process and develop newer algorithms both with constant verification time and with greater efficiency. However, finding newer computationally expensive mathematical, scientific and engineering problem and designing outsourcing solution for them, would always be noticeable.
Acknowledgement
The authors would like to thank NIT Raipur for providing infrastructure & facilities to carry out this research work.
Additional information
Funding
Notes on contributors
Malay Kumar
Malay Kumar has received MTech degree in Computer Engineering from National Institute of Technology, Kurukshetra, Haryana, India, in 2012. He is currently working towards his PhD degree in Computer Science and Engineering from National Institute of Technology, Raipur, Chhattisgarh, India. His current research interest includes secure outsourcing of mathematical and scientific application, encryption schemes, scheduling, distributed systems and cloud computing.
References
- Atallah, M. J., & Frikken, K. B. (2010). Securely outsourcing linear algebra computations. Proceedings of the 5th ACM Symposium on Information, Computer and Communications Security - ASIACCS '10 (p. 48). New York, NY: ACM Press.10.1145/1755688
- Atallah, M. J., Frikken, K. B., & Wang, S. (2012). Private outsourcing of matrix multiplication over closed semi-rings. SECRYPT, 136–144.
- Atallah, M. J., Pantazopoulos, K. N., Rice, J. R., & Spafford, E. E. (2002). Secure outsourcing of scientific computations. Advances in Computers, 54, 215–272.10.1016/S0065-2458(01)80019-X
- Bajikar, S. (2002). Trusted platform module (tpm) based security on notebook pcs-white paper. Mobile Platforms Group Intel Corporation 1–20.
- Belenkiy, M., Chase, M., Erway, C. C., Jannotti, J., Küpçü, A., & Lysyanskaya, A. (2008). Incentivizing outsourced computation. Proceedings of the 3rd international workshop on Economics of networked systems (pp. 85–90). New York, NY: ACM Press.10.1145/1403027
- Benjamin, D., & Atallah, M. J. (2008). Private and cheating-free outsourcing of algebraic computations. 2008 Sixth Annual Conference on Privacy, Security and Trust (PST) (pp. 240–245). New York, NY: IEEE.10.1109/PST.2008.12
- Björck, Å. (1994). Numerics of Gram-Schmidt orthogonalization. Linear Algebra and its Applications, 197-198197, 297–316.10.1016/0024-3795(94)90493-6
- Blanton, M., Zhang, Y., & Frikken, K. B. (2013). Secure and verifiable outsourcing of large-scale biometric computations. ACM Transactions on Information and System Security, 16(3), 1–33.10.1145/2555946
- Chen, C-A., Chang, G-Y., Hsieh, S-Y., & Chen, J. (2014). Conditional (t, k)-diagnosis in graphs by using the comparison diagnosis model. IEEE Transactions on Computers, PP, 1–1.10.1109/TC.2014.2345407
- Chen, F., Xiang, T., & Yang, Y. (2014). Privacy-preserving and verifiable protocols for scientific computation outsourcing to the cloud. Journal of Parallel and Distributed Computing, 74, 2141–2151.10.1016/j.jpdc.2013.11.007
- Chen, X., Huang, X., Li, J., Ma, J., Lou, W., & Wong, D. S. (2015). New algorithms for secure outsourcing of large –scale systems of linear equations. IEEE Transactions on Information Forensics and Security, 10, 69–78.
- Chen, X., Li, J., & Ma, J. (2014). New algorithms for secure outsourcing of modular exponentiations. Parallel Distributed, 541–556.
- Chung, K. M., Kalai, Y., & Vadhan, S. (2010). Improved delegation of computation using fully homomorphic encryption. Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), 6223, 483–501.
- Dreier, J., & Kerschbaum, F. (2011). Practical secure and efficient multiparty linear programming based on problem transformation (Doctoral dissertation). IACR Cryptology ePrint Archive.
- Du, W., Chen, S., & Han, Y. S. (2004). Privacy-preserving multivariate statistical analysis: Linear regression and classification. Proceedings of the 2004 SIAM International Conference on Data Mining (pp. 222–233). Philadelphia, PA: Society for Industrial and Applied Mathematics.
- Estep, D., & Higham, N. J. (2004). Accuracy and stability of numerical algorithms. SIAM Review, 46(4). Retrieved from http://www.jstor.org/stable/20453564
- Fiore, D., & Gennaro, R. (2012, October). Publicly verifiable delegation of large polynomials and matrix computations, with applications. In Proceedings of the 2012 ACM conference on Computer and communications security (pp. 501–512). ACM.
- Fortnow, L., & Lund, C. (1993). Interactive proof systems and alternating time—space complexity. Theoretical Computer Science, 113, 55–73.10.1016/0304-3975(93)90210-K
- Gennaro, R., Gentry, C., & Parno, B. (2010). Non-interactive verifiable computing: Outsourcing computation to untrusted workers. Lect. Notes Comput. Sci. (including Subser. Lect. Notes Artif. Intell. Lect. Notes Bioinformatics), 6223, 465–482.
- Gentry, C. (2009). A fully homomorphic encryption scheme (Doctoral dissertation). Stanford University.
- Gentry, C. (2010). Computing arbitrary functions of encrypted data. Communications of the ACM, 53, 97–105.10.1145/1666420
- Goldreich, W. A., Micali S., Goldreich, O., Micali, S., & Wigderson, A. (1987). How to play any mental game, or a completeness theorem for protocols with honest majority. Proceedings of 19th Annual ACM Symposium on Theory of Computing (pp. 218–229). New York, NY: ACM Press.
- Goldwasser, S., Micali, S., & Rackoff, C. (1989). The knowledge complexity of interactive proof systems. SIAM Journal on Computing, 18, 186–208.10.1137/0218012
- Goldwasser, S., Kalai, Y. T., & Rothblum, G. N. (2008). Delegating computation: Interactive proofs for muggles. Stoc, 62, 113–122.
- Hong, Y., Vaidya, J., & Lu, H. (2012). Secure and efficient distributed linear programming. Journal of Computer Security, 20, 583–634.10.3233/JCS-2012-0452
- Hu, X., & Tang, C. (2015). Secure outsourced computation of the characteristic polynomial and eigenvalues of matrix. Journal of Cloud Computing, 4, 4–9.
- Laud, P., & Pankova, A. (2015). Transformation-based outsourcing of linear equation systems over real numbers. IACR Cryptology ePrint Archive, 2015, 322.
- Lei, X., Liao, X., Huang, T., Li, H., & Chunqiang, H. (2013). Outsourcing large matrix inversion computation to a public cloud. IEEE Transactions on Cloud Computing, 1(1), 1–1.
- Lei, X., Liao, X., Huang, T., & Heriniaina, F. (2014). Achieving security, robust cheating resistance, and high-efficiency for outsourcing large matrix multiplication computation to a malicious cloud. Information Sciences, 280, 205–217.10.1016/j.ins.2014.05.014
- Lei, X., Liao, X., Member, S., Huang, T., & Li, H. (2015). Cloud computing service: The case of large matrix determinant computation. IEEE Transactions on Services Computing. 8, 688–700.
- Lin, K., & Chen, M. S. (2010). Privacy-preserving outsourcing support vector machines with random transformation. Proceedings of the 16th ACM SIGKDD international conference on Knowledge discovery and data mining (pp. 363–372). New York, NY: ACM Press.10.1145/1835804
- Lindell, Y., & Pinkas, B. (2009). Secure multiparty computation for privacy-preserving data mining. Journal of Privacy and Confidentiality, 1, 59–98.
- López-Alt, A., Tromer, E., & Vaikuntanathan, V. (2012). On-the-fly multiparty computation on the cloud via multikey fully homomorphic encryption. Proceedings of the 44th symposium on Theory of Computing - STOC '12 (p. 1219). New York, NY: ACM Press.10.1145/2213977
- Mohassel, P. (2011). Efficient and Secure Delegation of Linear Algebra. IACR Cryptology ePrint Archive, 2011, 605.
- Monrose, F., Wyckoff, P., & Rubin, A. D. (1999, February). Distributed execution with remote audit. In Ndss (Vol. 99, pp. 3–5).
- Seshadri, A., Luk, M., Shi, E., Perrig, A., Van Doorn, L., & Khosla, P. (2005, October). Pioneer: Verifying integrity and guaranteeing execution of code on legacy platforms. In Proceedings of ACM Symposium on Operating Systems Principles (SOSP) (Vol. 173).
- Shiraz, M., Gani, A., Khokhar, R. H., & Buyya, R. (2013). A review on distributed application processing frameworks in smart mobile devices for mobile cloud computing. IEEE Communications Surveys & Tutorials, 15, 1294–1313.10.1109/SURV.2012.111412.00045
- Smith, S. W., & Weingart, S. (1999). Building a high-performance, programmable secure coprocessor. Computer Networks, 31, 831–860.10.1016/S1389-1286(98)00019-X
- van Dijk, M., Gentry, C., Halevi, S., & Vaikuntanathan, V. (2010). Fully homomorphic encryption over the integers. Adv. Cryptology– EUROCRYPT ‘10, 6110, 24–43.10.1007/978-3-642-13190-5
- Wang, C., Ren, K., Wang, J., & Urs, K. M. (2011). Harnessing the cloud for securely solving large-scale systems of linear equations. ICDCS '11 Proceedings of the 2011 31st International Conference on Distributed Computing System, 24, 549–558.
- Wang, C., Ren, K., & Wang, J. (2011). Secure and practical outsourcing of linear programming in cloud computing. Proc. -IEEE INFOCOM (pp. 820–828). New York, NY: IEEE.
- Wang, C., Ren, K., Wang, J., & Wang, Q. (2013). Harnessing the cloud for securely outsourcing large-scale systems of linear equations. IEEE Transactions on Parallel and Distributed Systems, 24, 1172–1181.10.1109/TPDS.2012.206
- Yao, A. C. (1982). Protocols for secure computations. SFCS '82 Proceedings of the 23rd Annual Symposium on Foundations of Computer Science (pp. 1–5). New York, NY: ACM Press.
- Yao, A. C. C. (1986, October). How to generate and exchange secrets. In Foundations of Computer Science, 1986, 27th Annual Symposium on (pp. 162–167). IEEE.
- Yee, B. (1994). Using secure coprocessors (Doctoral dissertation). IBM.
- Zhang, Y., & Blanton, M. (2014, October). Efficient secure and verifiable outsourcing of matrix multiplications. International Conference on Information Security (pp. 158–178). Springer International Publishing.
- Zhou, L., Li, C., & Member, S. (2016). Outsourcing eigen-decomposition and singular value decomposition of large matrix to a public cloud. IEEE Access, 4, 869–879.