?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
This paper presents a novel approach for encrypting images using a Sudoku as its encryption key. This algorithm uses both symmetric and asymmetric key cryptography. It works with any type of data, Sudoku size, and keyspace. The image undergoes the process of modified thresholding, using a pseudo-random number generated from a Sudoku as the threshold. This image is then padded with zeros or the average pixel values to ensure the dimensions are multiples of the Sudoku's size and the image rows are shuffled randomly. For each iteration, the image rows are shuffled, followed by the columns, and finally, the image is rotated clockwise by 90 degrees. The resultant image is highly encrypted and resilient to brute-forcing methods. The algorithm requires roughly 25 milliseconds per iteration for a colored square image of dimensions and has an NPCR value of 99.60% and a UACI value of 35.65%. The gargantuan keyspace offered by the Sudoku keys ensures obedience of Kirchoff's principle and Shannon's maxim.
1. Introduction
In 2022, more than 3.5 quintillion bytes of data were generated globally every day (Earthweb, Citation2023). This amount is growing exponentially as the use of smart devices increases. Almost every little piece of data (Mune & Bhura, Citation2020) is being stored somewhere forever in this internet era. In such a scenario, data encryption assumes prime importance. It is needed to maintain privacy, as there always are dishonourable elements of society trying to gain disallowed access to someone's private data (Mhatre et al., Citation2022). Often, the goal of such attackers is to leak this private data to cause colossal losses to individuals and organizations. In other cases, it is to use this private data for blackmail or ransom or is sometimes done just to cause trouble for the victim (K. Mehta, Dhingra, et al., Citation2022; Sawant et al., Citation2022).
One way to avoid these issues is data encryption. The sender of this data should encrypt it so that it is stored safely and can be decrypted by the intended receiver when required. The main goal of an encryption algorithm should be that encryption and decryption processes be extremely fast and yet withstand any attacks that can crack them. Various techniques of encipherment, such as the RSA Encryption Algorithm, Advanced Encryption Standard (AES) algorithm, Hill Cipher (Rajvir et al., Citation2020), Shift Cipher, Affine Cipher, Vernam Cipher, etc. have been developed in the past. There, however, is a need for the creation of new encryption techniques as aggressors all over the world ceaselessly endeavour to crack these algorithms. No algorithm remains foolproof over time as ingenuity lies not only with the creator of an encryption algorithm but also with the attacker, who is guaranteed to find a solution sooner or later. Hence, an algorithm creator should always bear in mind that the attacker might be aware of the system, that is, the working of the algorithm, and hence the algorithm's security relies on the keys, according to Kirchoff's principle and Shannon's maxim (Jajodia & van Tilborg, Citation2011).
A classic Sudoku is a Japanese puzzle (Felgenhauer & Jarvis, Citation2006) which contains nine rows of nine columns each where each row contains the first nine positive integers shuffled in a manner in which the numbers appear only once in the individual rows or the grids formed by these rows.
It has been observed that a structured, mathematical entity in which a pattern exists, such as a Sudoku, is an outstanding producer of complex, hard-to-decipher, and sizeable keyspaces. Taking into account the requisites of a high-quality encryption algorithm described above and using the unique capability of a Sudoku to provide a massive keyspace as described in Section 5.1, which allows obedience of Kirchoff's principle and Shannon's maxim, this paper deferentially attempts to contribute to the world of cryptography, a new symmetric-key block cipher encryption technique based on the patterns found in a traditional Sudoku puzzle. The algorithm is later extended to Sudokus of other sizes. This algorithm encrypts an image in several iterations at a blazing pace using a Sudoku as the key for each iteration of this process which scrambles the data in ‘blocks’.
This paper has been written for an image file (Kumar et al., Citation2014) as the data to be encrypted. The same principles can, however, be applied to any form of data that can be divided into smaller blocks and processed individually. Several randomly generated Sudokus are used as the keys for each round of encryption. The encryption algorithm works on blocks of sudoku-sized data units at a time. To ensure a higher level of encryption, the technique uses multiple rounds of encryption done using a transposition cipher so that the actual data cannot be easily retrieved from the encrypted data without using the keys. This algorithm is highly flexible, works with custom keyspaces and different Sudoku sizes, and takes the keys as input.
2. Related works
In the ‘Plain Text Encryption Using Sudoku Cipher’ by Dey et al. (Citation2019), the authors use the Sudoku Cipher for encrypting plain text data based on a fixed grid of a Sudoku. The added benefit of this is during transmission, in case any modifications are done to the encrypted message, they can easily be detected, as they may violate the uniqueness limitations in each row, column, or mini-grid of the Sudoku puzzle.
The ‘Speech signal compression and encryption based on Sudoku, fuzzy C-means, and threefish cipher’ by Abduljaleel and Khaleel (Citation2021) makes use of the Sudoku in an intermediate step as a scrambling technique along with the Fuzzy C algorithm to achieve encryption on audio files before passing the data to threefish algorithm for further encryption and compression.
In ‘A simplified data encryption standard algorithm’ by Schaefer (Citation1996), a new and simplified version of the data encryption algorithm is presented where all the parameters are reduced as much as possible, which makes the inner workings of the algorithm accessible to undergraduates with the intention that the knowledge of the working can be extrapolated to the non-simplified version of the data encryption algorithm.
In ‘An empirical study to compare the performance of some symmetric and asymmetric ciphers’ by Kofahi (Citation2013), Elliptic Curve Cryptosystem (ECC) asymmetric encryption algorithm is compared with symmetric block cipher algorithms, namely Triple-Data Encryption Standard (T-DES) (Coppersmith et al., Citation1996), Advanced Encryption Standard (AES), and Blowfish. The evaluation is based on key generation, encryption, and decryption to determine the key size, security strength, and speed. The result of this evaluation was that ECC proved to be better than others in terms of security strength and is also scalable for future requirements.
‘A new image encryption algorithm for grey and color medical images’ by Kamal et al. (Citation2021) introduces a new image splitting technique based on image blocks. These image blocks are then encrypted by scrambling them in a zigzag pattern with rotation and random permutations. A chaotic logistic map is then used to generate a key to decrypt the medical image. This algorithm proved to be more efficient than any other medical image encryption algorithm (Choi et al., Citation2020; Jeong et al., Citation2018).
In ‘A Combination of Block-Based Chaos with Dynamic Iteration Pattern and Stream Cipher for Color Image Encryption’ by Budiman and Setiadi (Citation2020), a new encryption method is proposed which is based on using a combination of chaotic methods (Y. Li et al., Citation2021), streams, and hash functions (Applebaum et al., Citation2017). The hash algorithm used is SHA-1 and the image is divided into blocks which are encrypted by a dynamic key pattern based on chaotic keys.
In ‘A New Algorithm For Digital Image Encryption Based On Chaos Theory’ by Pourasad et al. (Citation2021), the feasibility of Chaotic methods-based digital image encryption is checked as this technique makes use of random chaos sequences for encryption of the image, and it is a quick and highly-secured method but has limited accuracy. The analysis was done on various performance metrics such as the Unified Average Changing Intensity (UACI), Correlation coefficient, Peak Signal to Noise Ratio (PSNR), and Number of Pixels Change Rate (NPCR). The result of this analysis as shown by the simulation, is that this technique is effective and can be used to encrypt images.
In ‘Image Encryption using the Sudoku Matrix’ by Y. Wu et al. (Citation2010), the authors have proposed a lossless method of encrypting an image using a Sudoku as a reference matrix to create a chaotic sequence using a logistic map to change pixel intensities as the first step and then using the reference matrix again to scramble the image by changing the position of the pixels. Only one Sudoku puzzle is used for the entire algorithm. The authors have manipulated the images such that high diffusion is achieved making the encrypted image completely unrecognizable.
In ‘Image Encryption with Variable Length Key’ by Guanghui et al. (Citation2016), the authors have proposed a new encryption scheme for images with a variable length running key created from a modified tent map (C. Li et al., Citation2017). It can create a uniformly distributed sequence of pseudo-random numbers. This encryption technique is resilient to the known/chosen plaintext attack.
In ‘A Combined Sudoku and Synthetic Colour Image Techniques for Cryptographic Key Generation’ by Manikandan et al. (Citation2021) the authors have proposed an algorithm for key generation which involves generating Sudoku values generated from random sessions wherein after solving these Sudoku puzzles using the recursive as well as backtracking techniques Sudoku matrices are obtained from which bits of pixels of a synthetic color image are extracted to form a key.
In ‘An Efficient Three Layer Image Security Scheme using 3D Arnold Cat Map and Sudoku Matrix’ by Meenakshi and Manivannan (Citation2015), the authors have proposed three-layer encryption for greyscale images. After exposing the greyscale image to the 3D ACM cipher layer, the image is first shuffled according to the Sudoku matrix permutation and then ex-ored with this matrix.
In ‘Image Encryption Algorithm Based on a New Five Dimensional Hyperchaotic System and Sudoku Matrix’ by Mehdi and Kadhim (Citation2019) the authors have attempted to create a chaotic sequence using a Sudoku matrix for key generation. The chaotic sequence is used to shuffle the image, then carry out an ex-or operation between the shuffled image and the Sudoku matrix, shuffle the image again, and then carry out another ex-or operation between this image and the chaotic key.
In ‘Image encryption based on permutation-substitution using chaotic map and Latin Square Image Cipher’ by Panduranga and Naveen Kumar (Citation2014) the authors have demonstrated an encryption scheme for images based on permutations using chaotic maps and Latin square image cipher. The demonstrated technique comprises permutation and substitution steps. In the permutation step, the permutation of the target image is done according to a chaotic sequence generated using a chaotic map. In the substitution step, a 256 bits secret key is used to generates a Latin Square Image Cipher (LSIC) which is used as the key image to perform an XOR operation between the permuted image and the key image. This method can be used for any image of any desired dimensions.
In ‘A Novel Color Image Encryption Algorithm Based on Hyper-chaotic System and Permutation-Diffusion Architecture’ by Wang et al. (Citation2012), the authors have proposed an encryption technique for colored images based on hyper-chaotic systems and the permutation-diffusion architecture. This algorithm makes use of a permutation block generated by mixing the red, green and blue components of a pixel. Using this algorithm, high diffusion is achieved and two entirely different encrypted images are obtained despite change of the last pixel only. Tests reveal that this algorithm is resistant to statistical and differential attacks.
In ‘A novel image encryption algorithm based on chaotic shuffling method’ by Wang et al. (Citation2017), an encryption technique to encrypt color images based on a chaotic shuffling-diffusion method has been proposed. The algorithm involves the generation of a chaotic sequence by a logistic map (Kocarev & Jakimoski, Citation2001), which is used to label the row coordinates of pixels of the shuffled image. Next, another logistic map is used for labeling the column coordinates of pixels of the shuffled image. Then, using the proposed pixel exchange model, the image is shuffled to change the position of pixels. After this, a matrix that is of the same size as the original image is generated by a third logistic map to enlarge the key space employing the MOD and the XOR operations. This algorithm is resistant to statistical, differential, plaintext, and the chosen-plaintext attack.
S-boxes short for substitution boxes are non-linear components used to achieve the confusion in block ciphers. In ‘S-box design method based on improved one-dimensional discrete chaotic map’ by Lambié (Citation2018), the author has proposed a new method for generating s-boxes using one-dimensional discrete chaotic maps, recording a forty-three percentage increase in creation speed and a gain of thirty-two percentage in space utilization. This approach is useful in fields where complete digitization is required and in lightweight devices with compact memories.
Dang et al. (Citation2021) describes a way of sharing data in a secure and encrypted manner on a peer-to-peer network (P2P) by making use of blockchain technology. Data is encrypted by making use of an attribute-based encryption algorithm to share keys amongst a group of authorized users, while the blockchain network ensures proper distribution of the keys. By having multiple copies of the data in the blockchain nodes, the proposed system is immune to the possibility of data unavailability due to the crashing of peer nodes. The authors have compared different types of attribute-based encryption algorithm and have used ciphertext-policy attribute-based encryption (CP-ABE) in their implementation. Although this system is vulnerable to quantum computing attacks, the authors predict quantum computers to be years away and expect a quantum-proof implementation by that time.
3. Methodology
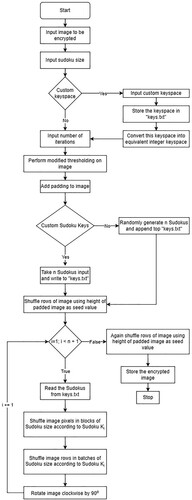
This section describes the encryption pattern, encryption algorithms and the working of our Sudoku-based encryption algorithm.
3.1. Encryption pattern
The algorithm follows a symmetric-key block as well as a transposition encipherment pattern which makes use of n + 4 keys, where n is the number of rounds that the algorithm iterates over:
The Sudoku size: The size of the Sudoku can be modified to enhance security. For example -- the algorithm can make use of a
Sudoku puzzle as the key instead of the standard
The first key: an integral number -- the height of the original image to be encrypted.
The second key: an integral number -- the width of the original image to be encrypted.
The third key: an integral number -- the number of rounds of encryption that the Sudoku undergoes, which can be as low as one or as high as a thousand, depending on the encrypter's satisfaction.
‘n’ more keys follow, depending on the value of n in the first key. These keys are the randomly generated Sudokus, which encrypt the data in blocks of the Sudoku size. A standard Sudoku contains 9 blocks of 9 digits each, ranging from 1 through 9.
The
th key: a seed value generated from a list of numbers ranging from 0 to the height of the padded image (first value inclusive, second value exclusive).
Since the data is processed in blocks of Sudoku size, and each element in the block is scrambled to form permutations generated to the tune of each sub-block of the Sudoku keys, this technique can be classified as a block transposition cipher. More accurately, the algorithm can also be called a multi-level block transposition technique, as for a standard Sudoku, the data is being permuted in 9 sub-blocks of 9 such rows corresponding to each row in the Sudoku. This shuffles the data in blocks of 9, per row of the key, but in blocks of 81 per round of encryption.
To make the algorithm more secure, the sender can choose to encrypt the keys themselves by using any asymmetric key encryption technique (Srivastava et al., Citation2022). The sender encrypts each of the n + 4 keys (n is the number of rounds of encryption in the algorithm) and sends the keys encrypted with the asymmetric key encipherment technique along with the data encrypted using the original n + 4 keys (Mune & Bhura, Citation2022). The receiver can then decrypt these keys using their private key.
As an optional feature, the input custom keyspace can also be stored in ‘keys.txt’. These keys are variable in length and characters governed by the desired input from the user. This can further enhance the security as the custom keyspace complicates the decryption of the keyspace first, followed by further encryption. As an example, a user might want the number ‘3’ to be represented as number ‘5’, the number ‘9’ to be represented as number ‘2’ and so on. This keyspace can be completely devoid of logic as it is governed by user choice, and may be difficult to crack.
3.2. Algorithms
The pseudo-code of the encryption and decryption algorithms is shown in this section. The encryption process has four parts. First, the algorithm generates all keys necessary for the encryption process followed by the generation of a pseudo-random number. This random number is used for the process of ‘thresholding’ in the image. The third step describes the creation of padding around the image followed by the actual encryption algorithm.
The decryption process used to reverse the effects of encryption is described in the next three steps. First, the decryption algorithm inverts the effects of the row and column shuffling followed by the step to remove the padding around the image. The final step in decryption is the restoration of the original image by the removal of the effects of thresholding.
Algorithm 1 Read Image, Store Keys
Algorithm 2 Generate Pseudo Random & Perform Thresholding
Algorithm 3 Image Padding
Algorithm 4 Sudoku Based Encryption
Algorithm 5 Sudoku Based Decryption of Encrypted Image
Algorithm 6 Remove Image Padding
Algorithm 7 Restore original image by reversing thresholding
3.3. Implementation
This section describes the encryption and decryption techniques of the algorithm in detail.
3.3.1. Encryption
The encryption technique has been described in this section. The first step of the algorithm involves reading the image in a particular format. The picture is read as a two-dimensional array, with the first dimension being the height of the image and the second dimension being the width. Every element of the inner array is either a pixel value if the image is gray-scale or a tuple in the RGB (Red-Blue-Green) format if the image is a color image. This particular format is critical for the shuffling process in the iterative phase of the algorithm. The height and width of the image are stored as the first two keys of the algorithm in ‘keys.txt’ which contains all the keys.
The second step requires user input for the Sudoku size the user wishes to use in the encryption process. A larger Sudoku size would ensure a higher level of encryption but also require more time. Then if the user wishes to use a custom keyspace, they can enter that stored in the keys.txt file and convert it into the equivalent integer keyspace for the encryption process.
The third step calls for user input of the fourth key, which is the number of rounds of encryption. The n subsequent keys, the Sudokus, are generated or manually entered by the user. The algorithm will only accept as many Sudokus as the rounds of encryption of the user's first inputs. The user can always return and re-encrypt the image if he feels that the encryption obtained is insufficient. The first key is then saved to a text file where the subsequent n + 1 keys shall be stored.
Step four involves the generation of random Sudokus by the machine. Users also have the option to enter their Sudoku puzzles as keys manually. These subsequently generated or manually entered Sudoku puzzles are saved to a text file for storage or transmission, with each key being written on a new line.
The fifth step of the algorithm is the thresholding process, modified for this algorithm as follows. A pseudo-random number, considered a threshold for this algorithm, is obtained by adding the elements along the diagonal from the top left of the image to the bottom right. If, on adding this number to the pixel in the case of gray-scale images or to its red, green, or blue value in the case of color images, the number obtained is smaller than 255, which is the highest permissible value of a pixel, the pixel value is set to this number; otherwise, the pixel value is set to this value subtracted from 255. This provides an image with a color scheme that contrasts the original image within the limits of the random number generated. The word “thresholding” has been used, keeping in mind that the pixel value is modified based on the pseudo-random number.
Since the dimensions of the input image are variable, the sixth step of the algorithm has two parts, the first is adding padding around the entire image to make the height and width of the image a multiple of the Sudoku size. As an example, if the Sudoku to be used for the image is of size , the padding shall ensure that the dimensions of the image are a multiple of 81 since a Sudoku of this size gives a square with 81 values transposed on the image as it horizontally reflects on it. For a Sudoku of size
, the padding would make the image's dimensions a multiple of 256. The padding can be calculated after reading the image, converting it into arrays of pixels with an equal number of padding pixels at the top and bottom as well as on the right and the left. The padding on the sides may or may not be equal to the padding on the bottom and top, depending on the figure's dimensions. The padding added to the image is usually the most common pixel value found in that image. There are several other methods of generating the padding, as well. One can create the pixel padding using the red, blue, and green values obtained by averaging all the values found in the image. The height of this padded image is stored in the file ‘keys.txt’ as the final key of the process.
The second part of sixth seven is shuffling the image according to the final key. This scrambling (Y. Li et al., Citation2016) has been done to introduce randomness into the algorithm. Once the image has been scrambled and padded, it is ready to enter the actual encryption rounds, which involve using the n Sudoku keys. It can be noted that the padded image is encrypted; hence, the encrypted image contains extra padding when the sender communicates it to the receiver. An attempt at removing the padding shall result in data loss as the padded borders are also involved in the encryption process.
The image next enters the iterative phase. The user has decided the number of iterations stored in the first key. If the user is unsatisfied with the result of the encryption, they can always try the algorithm with a higher number of iterations. First, the Sudoku puzzles are read from the key file. The image, having entered this iterative phase, undergoes the following transformations. Every array in the picture is divided into smaller arrays of length equal to the Sudoku length. Next, the smaller arrays are shuffled according to the combination in which each array in the Sudoku is obtained. This shuffling process is used in the iterative phase, part two of the fourth step, and the final stage of the algorithm takes inspiration from the Simplified Data Encryption Standard (S-DES) algorithm, where the given binary string is permuted according to the sequences provided. Note that the standard Sudoku is an array containing nine arrays containing nine elements.
Next, the rows are shuffled in batches of Sudoku size according to the Sudoku of the appropriate round. This ensures that the individual pixels and the entire rows of pixels are reorganized. This improves the diffusion property of the algorithm, as shuffling only the rows or the pixels in the rows is insufficient. For every iteration, the final sub-step involves rotating the image 90 degrees clockwise.
After the iterative phase is complete, the final step involves another random shuffle of the entire image in the order defined in the second key. This gives us an encrypted image ready for transmission from the sender to the receiver.
describes the entire encryption process as a flow chart.
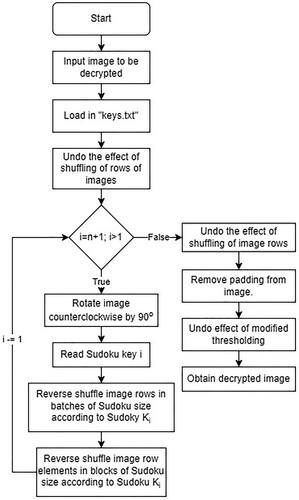
3.3.2. Decryption
The decryption technique has been described in this section. This process reverses the effects of encryption obtained from the technique described in the previous section. It involves three steps: the reversal of the iterative phase, the removal of padding, and the reversal of the effect of the modified thresholding.
The first step is the inversion of the random shuffling of the columns based on the seed value stored in the ‘keys.txt’ file. The next step is the iterative phase wherein firstly, the image is rotated counterclockwise by 90 followed by the inversion of the row and column shufflings of the image based on the Sudoku keys in the reverse order of their storage. The row decryption is obtained by dividing every single image array into rows of the size of the length of the Sudoku puzzle and then performing the reversal operation on each smaller array. The last key of ‘keys.txt’ is again used to remove the effect of randomization of the arrays that constitute the columns of the image. This proffers a decrypted image that still possesses the padding and the thresholding.
The padding is removed based on the height and width stored in the keys. The padding length equals the actual height and width of the image subtracted from the total height and width of the padded image and is subtracted evenly from the top, right, bottom and left of the image.
The thresholding of the image is reversed by subtracting the pseudo-random number from each pixel value in the case of gray-scale images or the red, green, and blue values that constitute a pixel in color images and obtaining the original pixel value greater than or equal to 0, or adding 255 to the obtained pixel value if a negative integer is obtained.
shows the entire decryption process as a flow chart.
4. Results and discussions
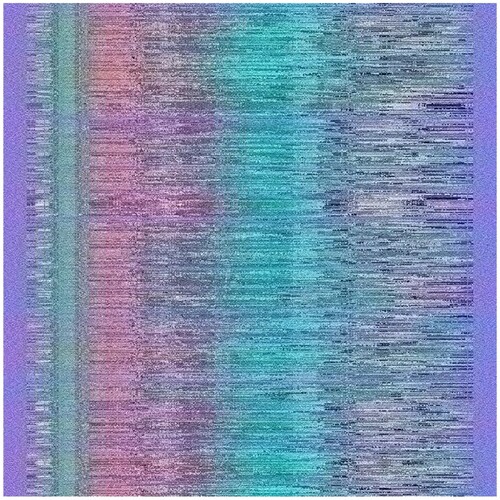
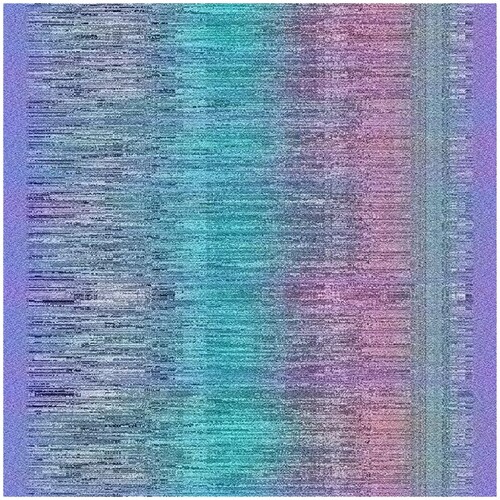
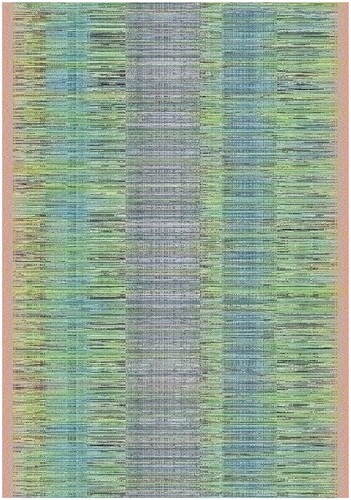
For the tests, the standard image of ‘Lena’ of size pixels originally in the ‘.tif’ format was used. The image transformations after modified thresholding and 50, 75, and 100 iterations were observed. The rotation of the image and the shuffling of the pixels using the keys make the images chaotic and unrecognizable. The essence of the algorithm lies in the strength of key generation and not in the actual shuffling of the pixels where very little diffusion occurs. This is because the algorithm relies more on the fact that the key space is beyond the computation power of any normal computer or even the more advanced supercomputers for which tougher variations of this algorithm -- which were described previously - can be used.
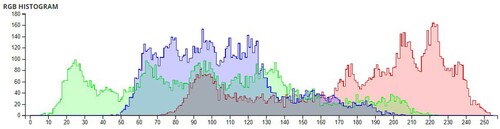
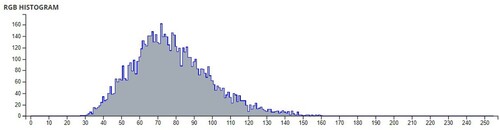
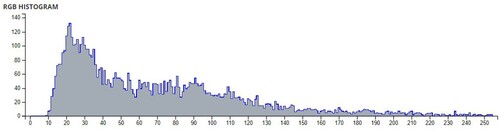
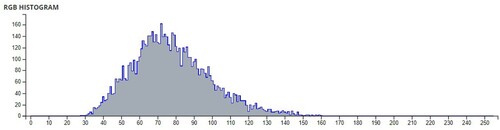
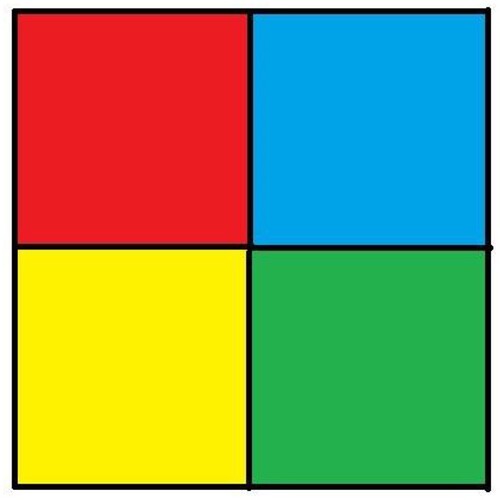
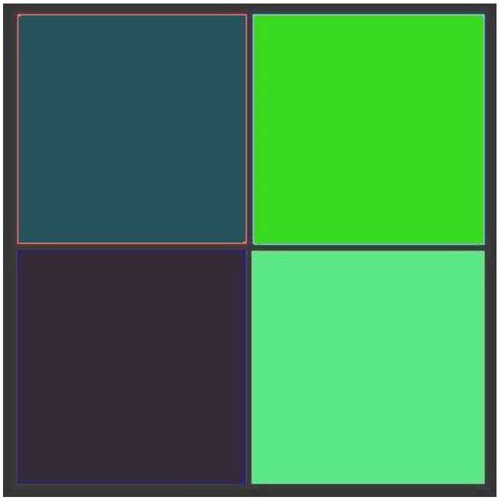
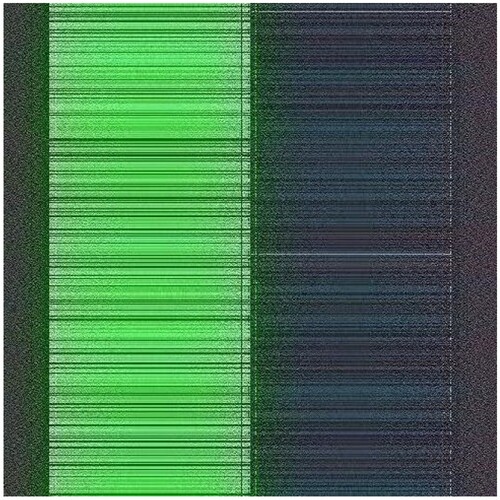
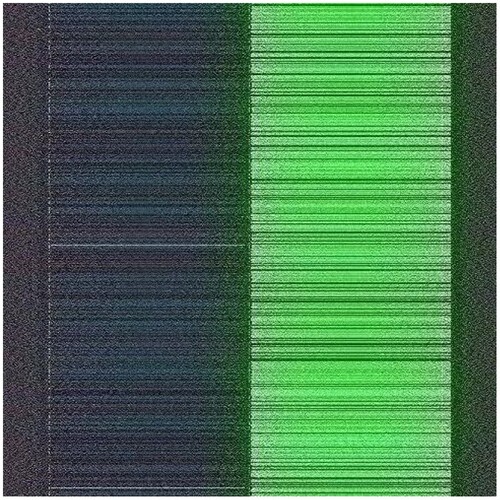
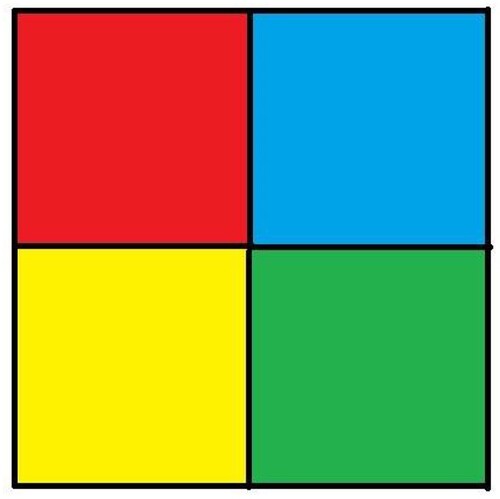
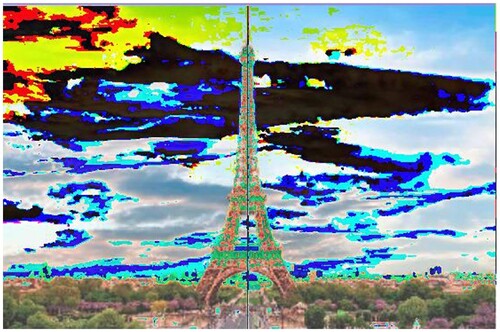
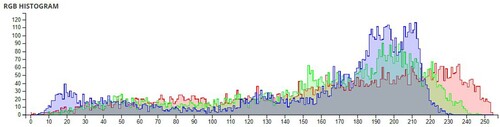
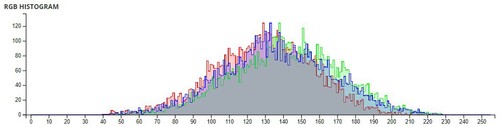
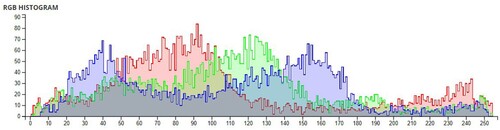
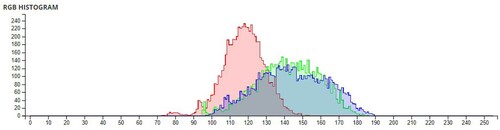
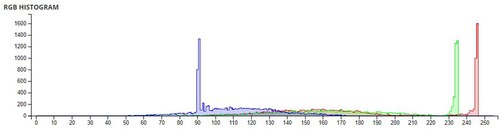
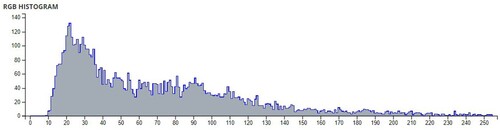
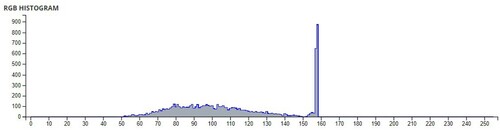
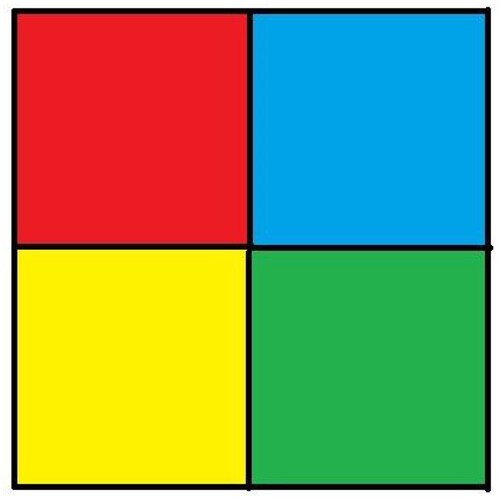
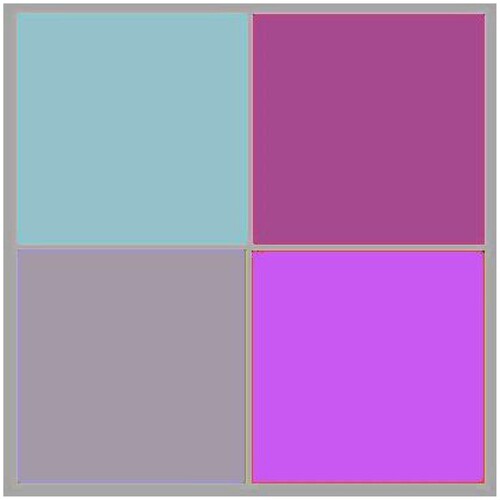
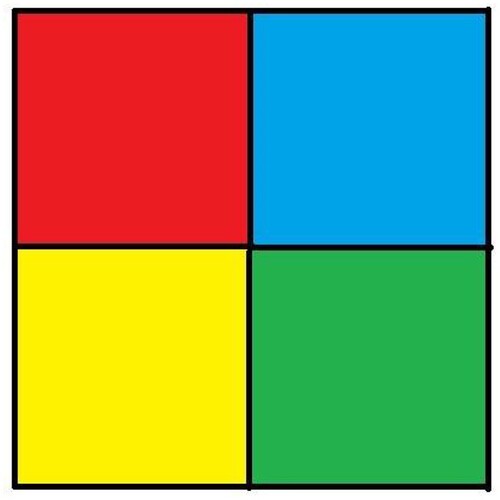
Additional tests are on different types of images. The second image that is encrypted is a black-and-white image of a forest. The third image is of multi-colored quadrants of a square to show how diffusion is taking place in the algorithm. The fourth image is a symmetric image of the Eiffel tower. The fifth image is the image of an Orca, and the final image is a mirror image of towers. A histogram of the image before and after encryption is also displayed to show the confusion and diffusion of the image due to encryption.
The images were tested using Sudokus and
Sudokus to show the changes in the output image and the time changes reflected in the encryption process. The results are visualized as follows:
4.1. Results obtained using 
 Sudoku
Sudoku
to show the cipher-text image at various iterations of encryption, using a Sudoku as the key, and the changes reflected in their color histograms before and after the encryption. The authors have used 6 images of various types to demonstrate the working of the encryption algorithm.
4.1.1. Image 1
4.1.2. Image 2
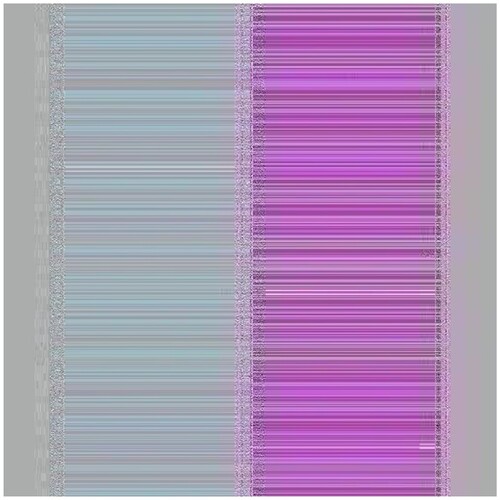
4.1.3. Image 3
4.1.4. Image 4
4.1.5. Image 5
4.1.6. Image 6
4.2. Results obtained using 
 Sudoku
Sudoku
to shows the ciphertext image at various iteratios of encryptions, using the 16x16 Sudoku as the key, and the changes reflected in their color histograms before and after the encryption. The authors have used 6 images of various types to demonstrate how the working of the encryption algorithm.
4.2.1. Image 1
4.2.2. Image 2
4.2.3. Image 3
4.2.4. Image 4
4.2.5. Image 5
4.2.6. Image 6
5. Analysis of results
This section analyses the algorithm using different metrics. Firstly, the key space analysis gives an insight into the various combinations of the keys that can be created with the suggested technique to reduce the key size that is stored or transmitted. Secondly, the security analysis is a description of the vulnerability of the algorithm to various types of attacks.
Thirdly, the time complexity analysis is a demonstration of the real world running time of the algorithm. Fourthly, the average pixel intensity value analysis shows the changes in the average RGB pixel values of the images before and after the encryption process is done. Finally, the key sensitivity analysis describes the diffusion pattern of the algorithm.
5.1. Key space analysis
The only restriction on the user input value n is that is needs to be lesser than the maximum number of possible solvable Sudoku grids combinations which are 6 sextillion, 670 quintillion, 903 quadrillion, 752 trillion, 21 billion, 72 million, 936 thousand, 960.
For the transposition combination after the Sudoku-based scrambling encryption, we randomly shuffle an array of the same size and store the value. The number of possible randomly shuffling combinations is equal to the height of the image that is to be encrypted. Combining this with the Sudoku possibilities, the total number of possible key combinations increases drastically and is in the power of a septillion.
If still a larger key space is needed then a Sudoku of larger grid size can be considered as it will have more possible combinations. For instance, a
Sudoku can be has 1,903,816,047,972,624,930,994,913,280,000 possible combinations.
With such a large key space, brute-forcing the algorithm will take up a lot of time even with a fast computer, which is the requirement of a good encryption technique (Phan, Citation2004). As of July 2022, the world's fastest supercomputer is the Hewlett Packard Enterprise Frontier with a processing speed of 1.102 exaflops per second. For an image of pixels with n = 100 encryption rounds, the total possible combinations of the keys would be
combinations. Dividing the number of possible combinations by the processing speed, we get
seconds which is approximately equal to
years.
So, even with the world's fastest supercomputer, it is impossible to try all possible combinations rendering this algorithm immune to brute-force attacks.
5.1.1. Reducing key size
Instead of sending the entire Sudokus as the key to the encryption algorithm, one way could be using python libraries like py-sudoku that can generate custom-sized Sudokus from a seed value. This seed value can either be a user input or randomly generated by the computer. This seed value can be easily cracked using public key cryptography. However, using symmetric key cryptography by deciding an arbitrary seed value, we can avoid any compromise on security.
As a result, key size per Sudoku can be drastically reduced from a array in the case of the Standard Sudoku to a single integer number. This does not compromise the algorithm's security as even though a Sudoku can be seeded from the library, there are still 6,670,903,752,021,072,936,960 possibilities for a single
Sudoku key.
5.2. Security analysis
The security of an algorithm is directly proportional to its key size. In this scenario, the total key size would bits. where n is the number of encryption rounds and h is the height of the image that is to be encrypted. With such a large key size, it is almost impossible to guess the key and as proven in the key space analysis, the brute force technique is also not the easiest way of cracking the encrypted data.
One vulnerable point can be when the key itself needs to somehow be transmitted to the receiver. For this, we can make use of asymmetric key encryption algorithms such as RSA or Diffie Hellman which will ensure the authenticity of the key for both sender and receiver.
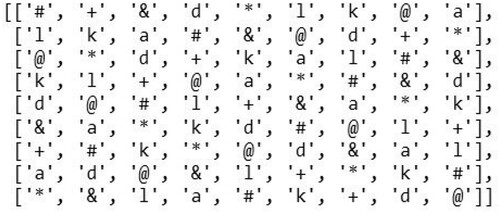
Another method of making the key more secure would be to define an arbitrary key space which would involve the use of different symbols substituting the numbers in the Sudoku keys. For example, for a sample Sudoku () as defined in the image below, with a key space where the numbers are represented by arbitrary symbols as: 1: ‘’, 2: ‘
’, 3: ‘a’, 4: ‘d’, 5: ‘k’, 6: ‘
’, 7: ‘
’, 8: ‘l’, 9: ‘+’, the arbitrarily created Sudoku () would appear as it does in the adjacent image.
The security of this algorithm can be further enhanced when unsolved Sudoku puzzles are stored and transmitted as keys. This gives an added advantage to the security as solving a Sudoku is computationally NP-complete. Further, a Sudoku ceases to be unique if there are less than 17 clues in it, and thus transmitting several such Sudokus would make it impossible to crack them if the creator keeps track of the clues which are not stored in the key itself. A simple solution would be to encrypt the number in these clues as well as their position inside of the Sudoku matrix using a different encryption technique.
5.3. Time complexity analysis
For the running time tests, a Windows 10 laptop computer with a Random Access Memory of 16 gigabytes running on a processor of the configurations: Intel(R) Core(TM) i9-9880H CPU @ 2.30GHz was used. The algorithm was tested on several iterations -- 25, 50, 75, 100. A sample set of 10 Sudoku puzzles generated as the keys were:
Key 2: [[4, 7, 1, 9, 8, 5, 3, 6, 2], [8, 9, 2, 7, 3, 6, 1, 5, 4], [5, 6, 3, 1, 2, 4, 8, 7, 9], [1, 5, 6, 8, 9, 2, 4, 3, 7], [2, 3, 8, 4, 1, 7, 5, 9, 6], [9, 4, 7, 6, 5, 3, 2, 1, 8], [6, 1, 9, 3, 4, 8, 7, 2, 5], [7, 8, 5, 2, 6, 1, 9, 4, 3], [3, 2, 4, 5, 7, 9, 6, 8, 1]]
Key 3: [[9, 7, 6, 1, 4, 8, 5, 3, 2], [5, 3, 8, 2, 6, 9, 7, 1, 4], [4, 2, 1, 5, 3, 7, 8, 9, 6], [8, 6, 5, 4, 9, 2, 3, 7, 1], [3, 9, 4, 6, 7, 1, 2, 5, 8], [7, 1, 2, 8, 5, 3, 6, 4, 9], [6, 4, 3, 9, 2, 5, 1, 8, 7], [1, 5, 9, 7, 8, 6, 4, 2, 3], [2, 8, 7, 3, 1, 4, 9, 6, 5]]
Key 4: [[2, 5, 7, 1, 6, 4, 3, 9, 8], [4, 8, 3, 5, 9, 7, 6, 2, 1], [6, 9, 1, 8, 2, 3, 7, 5, 4], [5, 3, 6, 4, 1, 9, 8, 7, 2], [7, 1, 8, 3, 5, 2, 9, 4, 6], [9, 2, 4, 7, 8, 6, 1, 3, 5], [8, 6, 9, 2, 3, 5, 4, 1, 7], [3, 7, 2, 6, 4, 1, 5, 8, 9], [1, 4, 5, 9, 7, 8, 2, 6, 3]]
Key 5: [[7, 2, 5, 8, 6, 9, 4, 3, 1], [4, 6, 1, 5, 3, 7, 8, 2, 9], [3, 8, 9, 1, 4, 2, 5, 7, 6], [1, 7, 8, 3, 2, 4, 6, 9, 5], [6, 4, 2, 9, 1, 5, 7, 8, 3], [5, 9, 3, 6, 7, 8, 1, 4, 2], [2, 3, 7, 4, 5, 1, 9, 6, 8], [9, 5, 6, 7, 8, 3, 2, 1, 4], [8, 1, 4, 2, 9, 6, 3, 5, 7]]
Key 6: [[3, 9, 6, 1, 4, 7, 2, 8, 5], [5, 1, 2, 8, 6, 9, 4, 7, 3], [7, 8, 4, 5, 2, 3, 1, 9, 6], [6, 2, 8, 4, 7, 1, 3, 5, 9], [9, 5, 7, 2, 3, 8, 6, 4, 1], [4, 3, 1, 9, 5, 6, 8, 2, 7], [8, 4, 3, 6, 9, 5, 7, 1, 2], [2, 7, 5, 3, 1, 4, 9, 6, 8], [1, 6, 9, 7, 8, 2, 5, 3, 4]]
Key 7: [[3, 6, 9, 4, 8, 1, 2, 5, 7], [7, 5, 4, 9, 2, 3, 8, 1, 6], [2, 1, 8, 5, 6, 7, 9, 4, 3], [8, 9, 1, 7, 5, 6, 3, 2, 4], [6, 3, 2, 1, 9, 4, 5, 7, 8], [4, 7, 5, 2, 3, 8, 1, 6, 9], [1, 8, 3, 6, 7, 2, 4, 9, 5], [5, 4, 6, 8, 1, 9, 7, 3, 2], [9, 2, 7, 3, 4, 5, 6, 8, 1]]
Key 8: [[7, 1, 8, 2, 9, 6, 5, 4, 3], [4, 5, 6, 8, 3, 1, 2, 7, 9], [9, 3, 2, 4, 7, 5, 1, 6, 8], [5, 8, 9, 6, 1, 4, 3, 2, 7], [6, 7, 3, 9, 2, 8, 4, 5, 1], [2, 4, 1, 7, 5, 3, 9, 8, 6], [3, 2, 4, 1, 8, 7, 6, 9, 5], [8, 6, 5, 3, 4, 9, 7, 1, 2], [1, 9, 7, 5, 6, 2, 8, 3, 4]]
Key 9: [[8, 1, 3, 4, 6, 7, 2, 9, 5], [9, 4, 6, 3, 2, 5, 1, 8, 7], [5, 2, 7, 9, 8, 1, 6, 3, 4], [4, 6, 9, 7, 3, 8, 5, 1, 2], [2, 7, 5, 6, 1, 9, 8, 4, 3], [3, 8, 1, 5, 4, 2, 7, 6, 9], [1, 5, 8, 2, 9, 3, 4, 7, 6], [6, 3, 2, 1, 7, 4, 9, 5, 8], [7, 9, 4, 8, 5, 6, 3, 2, 1]]
Key 10: [[7, 8, 9, 3, 4, 1, 6, 2, 5], [1, 5, 2, 8, 6, 9, 3, 7, 4], [4, 3, 6, 2, 7, 5, 8, 1, 9], [2, 1, 8, 5, 9, 3, 7, 4, 6], [3, 7, 4, 6, 1, 2, 9, 5, 8], [9, 6, 5, 4, 8, 7, 2, 3, 1], [6, 2, 3, 9, 5, 4, 1, 8, 7], [8, 4, 7, 1, 2, 6, 5, 9, 3], [5, 9, 1, 7, 3, 8, 4, 6, 2]]
Key 11: [[1, 3, 9, 4, 8, 5, 7, 2, 6], [2, 7, 5, 3, 6, 1, 8, 4, 9], [4, 6, 8, 2, 9, 7, 3, 5, 1], [9, 8, 3, 1, 5, 6, 2, 7, 4], [7, 1, 4, 9, 2, 8, 6, 3, 5], [5, 2, 6, 7, 3, 4, 9, 1, 8], [3, 4, 1, 8, 7, 9, 5, 6, 2], [6, 9, 7, 5, 4, 2, 1, 8, 3], [8, 5, 2, 6, 1, 3, 4, 9, 7]]
The numbering of the keys starts from 4 and not 1 as the first two keys are the height and width of original image, and the third key is the number of iterations, that is 10. The following results were obtained:
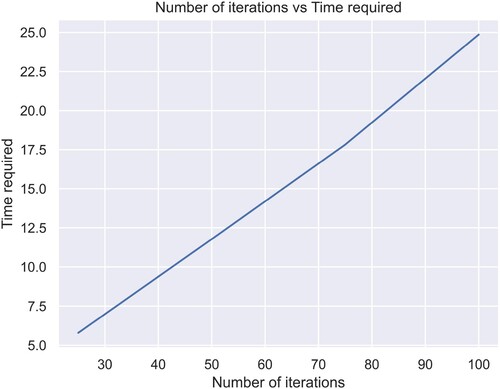
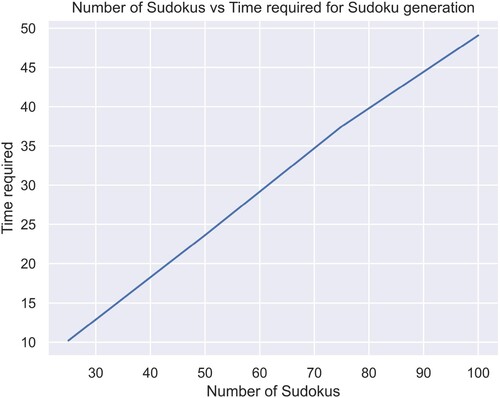
It can be observed ( & ) that the algorithm takes only 25 seconds to complete 100 iterations, which shows its computational efficiency. This analysis does not include the time required to actually generate the keys. To generate 25, 50, 75, 100 keys the time required is shown in and
.Table 1. Comparison of iterations for Lena.
Table 2. Time required for key generation.
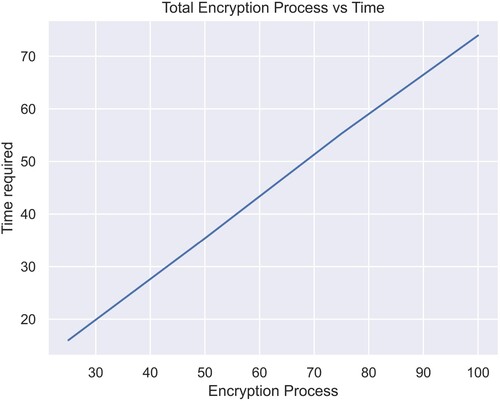
Hence, the total time required for the Sudoku key generation and the time required for iterations give us the total running time of the algorithm (). 100 iterations of the algorithm require roughly a minute and a quarter to execute for the image named Lena. A lighter version of this algorithm involves the usage of just one Sudoku for all iterations. This would shrink the total time required to roughly, the time required for encryption only as the time required to generate
keys is omitted. This also reduces the necessity for the third key and the algorithm ends up using only 3 keys, the first being the height of the unpadded image, the second being the width of the image, the third being the Sudoku used and the fourth being the random array generated from the height of the image. Note here that the first iteration involves the generation of the key and the random shuffling of the image according to this key which is the last key in the set of keys generated. Hence the approximate running time of the algorithms on different images is shown in and .
Table 3. Total time per set of iterations for Lena for a Sudoku of size in seconds.
Table 4. Total time required for 100 iterations of all images using Sudoku and
Sudoku.
The time required for 100 iterations of the images encrypted in this paper for as well as
Sudokus is given in the table below:
5.4. Average pixel intensities analysis
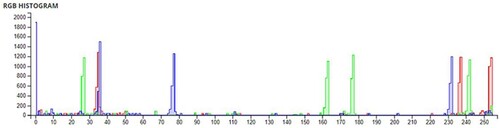
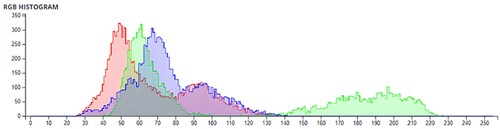
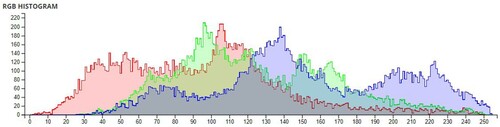
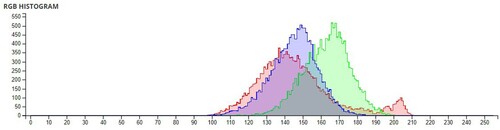
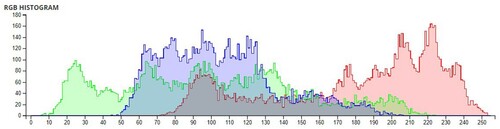
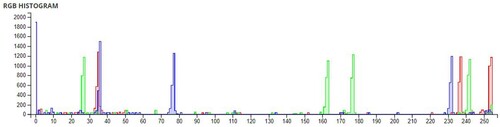
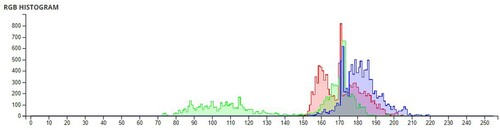
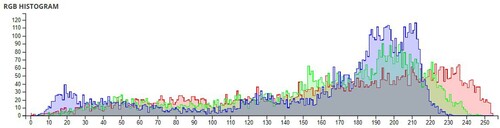
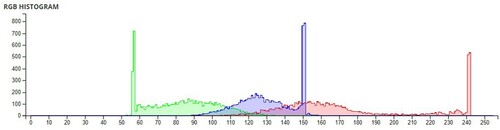
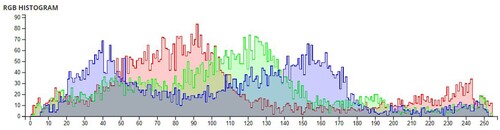
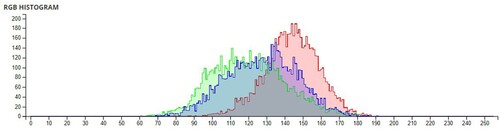
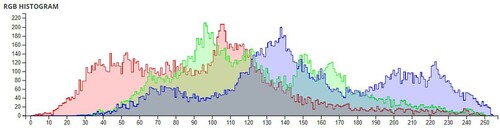
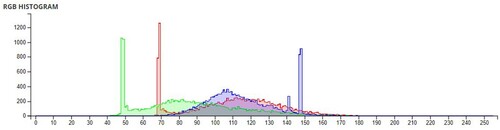
The pixel values of any image are usually described in the form of a histogram. The more different the histogram values of the encrypted image are from the original image, the better the encryption, as it reduces the possibilities of statistical attacks on the image.
In , a comparison of the average pixel intensities is shown between the original images and the encrypted images using Sudokus and 16x16 Sudokus. It is seen that there is a significant change in the average pixel values after the encryption showing the confusion element of the encryption.
Table 5. Average pixel intensities of Images before and after encryption using Sudoku and
Sudoku.
5.5. Information entropy analysis
Entropy, in general, refers to randomness. For cryptographic use cases, the higher the entropy values, the higher the security is considered, as it increases the difficulty in finding the randomly generated value since the formula reversal method is no longer available.
Shannon entropy is a common way of finding out the information available in every pixel. It works by quantifying the absolute amount of storage and transmission needed to capture information stored in a variable based on the frequency of data values.
(1)
(1) The above equation is the Shannon Entropy equation where ‘H(X)’ is the information entropy for the image, ‘Pi’ is the probability of the variable ‘Xi’ and ‘N’ stands for the total number of variable values available which is 256 in the case of greyscale images. According to Hamza and Titouna (Citation2016), the highest possible Shannon Entropy value is 8 and any value even close to 8 is considered to have good entropy.
In , Shannon Entropies of the original and encrypted images are compared. We can confidently say that the encryption process increases the Shannon entropy of the images and brings it much closer to the highest possible value i.e. 8.
Table 6. Comparison of Shannon entropies of original images and encrypted Images.
In , the Information Entropy of the proposed algorithm is compared with other algorithms using Lena as the base value. We can thus conclude that our proposed algorithm has a better information entropy than most algorithms but still falls behind some (Roy et al., Citation2021) by a slight margin.
Table 7. Information Entropies comparison for different algorithms on Lena.
5.6. Key sensitivity analysis
The encryption algorithm is based on multiple randomly generated Sudokus as the keys. Changing just one Sudoku does not drastically affect the encrypted image, as the diffusion ability of this algorithm is low because only 81-pixel tuples are shuffled per Sudoku. The algorithm is also not acutely affected in a single iteration for the same reasons. If, however, all the Sudoku keys are different, then the final encrypted image would be entirely different. Iterations also make the image more chaotic, proving their importance in this algorithm.
5.7. Analysis of differential attacks effects
NPCR (Number of Pixels Changed Rate) and UACI (Unified Average Changing Intensity) are metrics used in differential attacks on encryption systems to evaluate the strength of encryption algorithms. These attacks exploit the fact that small changes in the plain text will result in small changes in the cipher text, known as differential characteristics.
NPCR measures the proportion of pixels in an image that is changed after encryption, while UACI measures the average intensity of the changes.
A higher NPCR or UACI value indicates that a larger number or proportion of pixels change after encryption, making the encryption more secure against differential attacks. Conversely, a lower NPCR or UACI value indicates that the encryption is more vulnerable to differential attacks.
Suppose C1 represents the plain-text image and C2 represents the cipher-text image, and the pixel values at grid are represented by C1
and C2
respectively. D(i,j) is a bipolar array as described in Equation (Equation2
(2)
(2) ).
(2)
(2)
(3)
(3)
(4)
(4)
The range of NCPR values and UACI values is from 0% to 100%. shows the NCPR and UACI values for different images and different Sudoku's used. From this table, we can conclude that using a bigger Sudoku increases the NPCR value in all cases and the UACI value in majority of the cases making the encrypted images more resilient to differential attacks.
Table 8. Obtained NPCR and UACI values for encrypted images using different Sudokus.
compares the NCPR and UACI values of the proposed algorithm and other available encryption algorithms using Lena as the standard image. From this table, we can conclude the proposed algorithm is very close to current industry standards and even surpasses some of them in some cases.
Table 9. Comparison of NPCR and UACI values between different algorithms on Lena.
6. Applications
The complexity of this algorithm makes it suitable for image encryption and transmission in applications with abundant storage and processing power (Balani et al., Citation2022; Pampattiwar & Chavan, Citation2021). This can be done to encrypt movies and videos, which are a sequence of images, to reduce piracy and theft of data.
Journalists can make use of this algorithm to securely transfer images so that they do not get leaked before being published. Using fixed locations of Sudoku for example The Times Of India daily Sudoku can even remove the process of sending the key and therefore eliminate a possible loose end in the overall security of the data.
Another application of this algorithm would be in text cryptography, where a user possesses texts in different languages using various symbols that can be defined in custom keyspaces, shuffled using the Sudoku keys, and transmitted. Including timestamps with the image would assist in reinforcing image integrity.
7. Conclusion and future scope
This document demonstrated a new image encryption algorithm based on the Japanese puzzle Sudoku. This encipherment technique followed the block cipher approach and involved shuffling data and its values using multiple Sudokus as keys on several different images. Results exemplified a resistance to various attacks, especially the brute-force attack. They proved that as the image underwent more iterations, the obscurity of the original image increased, exhibiting greater diffusion, and the pixel value changes based on sudoku values introduced confusion in the final encrypted image.
A wide range of analyses was done on the algorithm to gauge its effectiveness, such as key space analysis, security analysis, time complexity analysis, average pixel intensities analysis, information entropy analysis, key sensitivity analysis, histogram analysis, and differential attack effects analysis. From these analysis, we can conclude that this algorithm is quite secure and performs better than the majority of the other encryption algorithms it is compared to. In some cases, where other algorithms perform better, they do by a very slight margin.
Although this paper covered image encryption, but the algorithm can encrypt practically any form of data, including but not limited to multimedia data such as audio, video, and plain text, as well as various discrete signals available in multiple dimensions. The only requirement is that the data be capable of fragmentation which is essential for the modification, transposition and shuffling of the data.
The future scope would involve implementing this algorithm on not only different images but also images of different file formats and observing the variations in the time and space complexities of the outputs obtained. This algorithm is flexible and provides limitless combinations when paired with different encryption algorithms to encrypt the Sudokus. A recursive approach of the algorithm can be implemented on the Sudokus themselves, encrypting these Sudoku keys using this algorithm depending on security requirements. Another area of improvement in this algorithm is the differential attacks analysis, where the algorithm got slightly lower NPCR values than its competitors. The next possible area of improvement would be to improve this algorithm's encryption and decryption speeds by implementing it in a significantly faster processing language like Java or C++. Doing so can make it possible to use this algorithm for instant communication.
An essential parameter to determine an algorithm's usability is its time and space complexity and its resistance to different attacks. Future scopes would also involve testing this algorithm using the various uncommon attacks available in an attacker's arsenal and make this algorithm resilient to quantum computing attacks.
Disclosure statement
There is no financial or non-financial interest in publishing this work.
Additional information
Notes on contributors
Kanaad Deshpande
Kanaad Deshpande is a final-year computer engineering student at Dwarkadas Jivanlal Sanghvi College of Engineering, which is affiliated with the University of Mumbai. His major research interests include cryptography and cybersecurity, blockchain technologies, and machine learning.
Junaid Girkar
Junaid Girkar is a final-year computer engineering student at Dwarkadas Jivanlal Sanghvi College of Engineering, which is affiliated with the University of Mumbai. He is fascinated by on-going research in the fields of cybersecurity, blockchain, machine learning, data mining, and Internet of Things.
Ramchandra Mangrulkar
Dr. Ramchandra Mangrulkar, being a postgraduate from National Institute of Technology, Rourkela, received his PhD in Computer Science and Engineering from SGB Amravati University, Amravati in 2016. At present, he is working as an Associate Professor in the Department of Computer Engineering at SVKM's Dwarkadas J. Sanghvi College of Engineering, Mumbai. Dr. Ramchandra Mangrulkar has published 55 papers and 24 book chapters with Taylor and Francis, Springer and IGI Global. He has 15 publications in Web of Science Core Collection, 7 ESCI and Scopus and 37 Scopus only with H-index around 7. He has also edited 5 books with CRC Press, Taylor and Francis Series. He is in the panel of Reviewers in many international journals and has reviewed many book proposals submitted to publishers of international repo. He has also shown keen interest in conducting and organizing workshops on Artificial Intelligence BoT in Education, Network Simulator 2, Innovative tools for Research and LaTeX & Overleaf. He is also working as internal thesis advisor at NMIMS's MPSTE Mumbai and DY Patil's RAIT, Navi Mumbai. He also worked as external referee for PhD thesis evaluation at SGB Amravati University and RTM Nagpur University. He is an active member of the Board of Studies in various universities and autonomous institutes in India.
References
- Abduljaleel, I. Q., & Khaleel, A. H. (2021). Speech signal compression and encryption based on Sudoku, fuzzy C-means and threefish cipher. International Journal of Electrical and Computer Engineering (IJECE), 11(6), 5049–5059. http://doi.org/10.11591/ijece.v11i6.pp5049-5059
- Applebaum, B., Haramaty-Krasne, N., Ishai, Y., Kushilevitz, E., & Vaikuntananthan, V. (2017). Low-complexity cryptographic hash functions. 8th Innovations in Theoretical Computer Science Conference (ITCS 2017), 67, 7:1–7:31. https://doi.org/10.4230/LIPIcs.ITCS.2017.7
- Arpaci, B., Kurt, E., & Çelik, K. (2020). A new algorithm for the colored image encryption via the modified Chua's circuit. Engineering Science and Technology, an International Journal, 23(3), 595–604. https://doi.org/10.1016/j.jestch.2019.09.001
- Balani, N., Chavan, P., & Ghonghe, M. (2022). Design of high-speed blockchain-based sidechaining peer to peer communication protocol over 5G networks. Multimedia Tools and Applications, 81(25), 36699–36713. https://doi.org/10.1007/s11042-021-11604-6
- Budiman, F., & Setiadi, D. R. I. M. (2020). A combination of block-based chaos with dynamic iteration pattern and stream cipher for color image encryption. International Journal of Intelligent Engineering and Systems, 13(6), 132–141. http://doi.org/10.22266/ijies2020.1231.12
- Choi, U. S., Cho, S. J., Kim, J. G., Kang, S. W., & Kim, H. D. (2020). Color image encryption based on programmable complemented maximum length cellular automata and generalized 3-D chaotic cat map. Multimedia Tools and Applications, 79(31), 22825–22842. https://doi.org/10.1007/s11042-020-09033-y
- Coppersmith, D., Johnson, D. B., & Matyas, S. M. (1996). A proposed mode for triple-DES encryption. IBM Journal of Research and Development, 40(2), 253–262. https://doi.org/10.1147/rd.402.0253
- Dang, N. T., Tran, H. M., Nguyen, S. V., Maleszka, M., & Le, H. D. (2021). Sharing secured data on peer-to-peer applications using attribute-based encryption. Journal of Information and Telecommunication, 5(4), 440–459. https://doi.org/10.1080/24751839.2021.1941574
- Dey, K. N., Golui, S., Dutta, N., Maji, A. K., & Pal, R. K. (2019). Plain text encryption using Sudoku cipher. ICICC 2019. Advances in Intelligent Systems and Computing, 1034. https://doi.org/10.1007/978-981-15-1084-7_3
- Earthweb (2023). Retrieved February 1, 2023, from https://earthweb.com/how-much-data-is-created-every-day/
- Felgenhauer, B., & Jarvis, F. (2006). Mathematics of Sudoku I. Mathematical Spectrum, 39(1), 15–22. https://citeseerx.ist.psu.edu/document?repid=rep1&type=pdf&doi=d2b0eb07e7fa8bc5e7bb2cc24877e26db19fb2c2
- Guanghui, C., Xing, Z., & Yanjun, L. (2016). Image encryption with variable length key. IETE Technical Review, 33(3), 297–309. https://doi.org/10.1080/02564602.2015.1088412
- Hamza, R., & Titouna, F. (2016). A novel sensitive image encryption algorithm based on the Zaslavsky chaotic map. Information Security Journal: A Global Perspective, 25(4–6), 162–179. https://doi.org/10.1080/19393555.2016.1212954
- Hanchinamani, G., & Kulakarni, L. (2014). Image encryption based on 2-D zaslavskii chaotic map and pseudo hadmard transform. International Journal of Hybrid Information Technology, 7, 185–200. http://dx.doi.org/10.14257/ijhit.2014.7.4.16
- Jajodia, S., & van Tilborg, H. C. (2011). Shannon’s maxim. Encyclopedia of Cryptography and Security. https://doi.org/10.1007/978-1-4419-5906-5_1167
- Jeong, H. S., Park, K. C., Cho, S. J., & Kim, S. T. (2018). Color medical image encryption using two-dimensional chaotic map and C-MLCA. 2018 Tenth International Conference on Ubiquitous and Future Networks (ICUFN), 501–504. https://doi.org/10.1109/ICUFN.2018.8437025
- Kamal, S. T., Hosny, K. M., Elgindy, T. M., Darwish, M. M., & Fouda, M. M. (2021). A new image encryption algorithm for grey and color medical images. IEEE Access, 9, 37855–37865. https://doi.org/10.1109/ACCESS.2021.3063237
- Kocarev, L., & Jakimoski, G. (2001). Logistic map as a block encryption algorithm. Physics Letters A, 289(4–5), 199–206. https://doi.org/10.1109/ACCESS.2021.3063237
- Kofahi, N. A. (2013). An empirical study to compare the performance of some symmetric and asymmetric ciphers. International Journal of Security and Its Applications, 7(5), 1–16. https://doi.org/10.14257/ijsia.2013.7.5.01
- Kumar, M., Aggarwal, A., & Garg, A. (2014). A review on various digital image encryption techniques and security criteria. International Journal of Computer Applications, 96(13), 19–26. https://doi.org/10.5120/16854-6720
- Lambié, D. (2018). S-box design method based on improved one-dimensional discrete chaotic map. Journal of Information and Telecommunication, 2(2), 181–191. https://doi.org/10.1080/24751839.2018.1434723
- Li, C., Luo, G., Qin, K., & Li, C. (2017). An image encryption scheme based on chaotic tent map. Nonlinear Dynamics, 87(1), 127–133. https://doi.org/10.1007/s11071-016-3030-8
- Li, Y., Song, B., Cao, R., Zhang, Y., & Qin, H. (2016). Image encryption based on compressive sensing and scrambled index for secure multimedia transmission. ACM Transactions on Multimedia Computing, Communications, and Applications (TOMM), 12(4s), 1–22. https://doi.org/10.1007/s11071-016-3030-8
- Li, Y., Yu, H., Song, B., & Chen, J. (2021). Image encryption based on a single-round dictionary and chaotic sequences in cloud computing. Concurrency and Computation: Practice and Experience, 33(7), 1–1. https://doi.org/10.1002/cpe.5182
- Manikandan, C., Satwik, K. S. S., Smarani, T. M., & Umamaheshwari, P. (2021). A combined Sudoku and synthetic colour image techniques for cryptographic key generation. Journal of Physics: Conference Series, (1), 012050. http://dx.doi.org/10.1088/1742-6596/1767/1/012050
- Meenakshi, P., & Manivannan, D. (2015). An efficient three layer image security scheme using 3D arnold cat map and Sudoku matrix. Indian Journal of Science and Technology, 8(16), 1–6. https://dx.doi.org/10.17485/ijst/2015/v8i16/63545
- Mehdi, S. A., & Kadhim, A. A. (2019). Image encryption algorithm based on a new five dimensional Hyperchaotic system and Sudoku matrix. 2019 International Engineering Conference (IEC), IEEE, 188–193. https://doi.org/10.1109/IEC47844.2019.8950560
- Mehta, D., Jha, M., Suhagiya, H., & Mangrulkar, R. (2022). DieRoll: A unique key generation and encryption technique. Journal of Applied Security Research, 1–28. https://doi.org/10.1080/19361610.2022.2124589
- Mehta, K., Dhingra, G., & Mangrulkar, R. (2022). Enhancing multimedia security using shortest weight first algorithm and symmetric cryptography. Journal of Applied Security Research, 1–24. https://doi.org/10.1080/19361610.2022.2157193
- Mhatre, M., Kashid, H., Jain, T., & Chavan, P. (2022). BCPIS: Blockchain-based counterfeit product identification system. Journal of Applied Security Research, 1–26. https://doi.org/10.1080/19361610.2022.2086784
- Mune, A. R., & Bhura, S. A. (2020). An analysis of heterogeneous data with extreme learning via unsupervised multiple kernels. 2nd International Conference on Data, Engineering and Applications (IDEA), IEEE, 1–7. https://doi.org/10.1109/IDEA49133.2020.9170688
- Mune, A. R., & Bhura, S. A. (2022). Three-stage heterogeneous data clustering using unsupervised multiple kernel and extreme learning machine. Data, Engineering and Applications: Select Proceedings of IDEA 2021, Springer Nature Singapore, 531–540.
- Norouzi, B., Seyedzadeh, S. M., Mirzakuchaki, S., & Mosavi, M. R. (2014). A novel image encryption based on hash function with only two-round diffusion process. Multimedia Systems, 20(1), 45–64. https://doi.org/10.1007/s00530-013-0314-4
- Pampattiwar, K. N., & Chavan, P. (2021). Challenges, opportunities, and applications of 5G network. In Future Trends in 5G and 6G (pp. 81–94). https://doi.org/10.1201/9781003175155
- Panduranga, H. T., & Naveen Kumar, S. K. (2014). Image encryption based on permutation-substitution using chaotic map and Latin Square Image Cipher. The European Physical Journal Special Topics, 223(8), 1663–1677. https://doi.org/10.1140/epjst/e2014-02119-9
- Phan, R. C. W. (2004). Impossible differential cryptanalysis of 7-round advanced encryption standard (AES). Information Processing Letters, 91(1), 33–38. https://doi.org/10.1016/j.ipl.2004.02.018
- Pourasad, Y., Ranjbarzadeh, R., & Mardani, A. (2021). A new algorithm for digital image encryption based on chaos theory. Entropy, 23(3), 341. https://doi.org/10.3390/e23030341
- Rajvir, C., Satapathy, S., Rajkumar, S., & Ramanathan, L. (2020). Image encryption using modified elliptic curve cryptography and Hill cipher. Smart Intelligent Computing and Applications: Proceedings of the Third International Conference on Smart Computing and Informatics, 1, 675–683. https://doi.org/10.1007/978-981-13-9282-5_64
- Roy, M., Chakraborty, S., & Mali, K. (2021). The MSK: A simple and robust image encryption method. Multimedia Tools and Applications, 80, 21261–21291. https://doi.org/10.1007/s11042-021-10761-y
- Sawant, V., Solkar, A., & Mangrulkar, R. (2022). Modified symmetric image encryption approach based on mixed column and substitution box. Journal of Applied Security Research, 1–34. https://www.tandfonline.com/doi/full/10.1080/19361610.2022.2150498
- Schaefer, E. F. (1996). A simplified data encryption standard algorithm. Cryptologia, 20(1), 77–84. https://doi.org/10.1080/0161-119691884799
- Seyedzadeh, S. M., & Mirzakuchaki, S. (2012). A fast color image encryption algorithm based on coupled two-dimensional piecewise chaotic map. Signal Processing, 92(5), 1202–1215. https://doi.org/10.1016/j.sigpro.2011.11.004.
- Srivastava, S., Tiwari, A., & Srivastava, P. K. (2022). Review on quantum safe algorithms based on symmetric key and asymmetric key encryption methods. 2nd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), IEEE, 905–908. https://doi.org/10.1109/ICACITE53722.2022.9823437
- Wang, X., Teng, L., & Qin, X. (2012). A novel colour image encryption algorithm based on chaos. Signal Processing, 92(4), 1101–1108. https://doi.org/10.1016/j.sigpro.2011.10.023
- Wang, X., Wang, S., Zhang, Y., & Guo, K. (2017). A novel image encryption algorithm based on chaotic shuffling method. Information Security Journal: A Global Perspective, 26(1), 7–16. https://doi.org/10.1080/19393555.2016.1272725
- Wu, X., Wang, K., Wang, X., Kan, H., & Kurths, J. (2018). Color image DNA encryption using NCA map-based CML and one-time keys. Signal Processing, 148, 272–287. https://doi.org/10.1016/j.sigpro.2018.02.028
- Wu, Y., Zhou, Y., Noonan, J. P., Panetta, K., & Agaian, S. (2010). Image encryption using the Sudoku matrix. Mobile Multimedia/Image Processing, Security, and Applications 2010, 7708, 222–233. https://doi.org/10.1117/12.853197
- Zhang, G., & Liu, Q. (2011). A novel image encryption method based on total shuffling scheme. Optics Communications, 284(12), 2775–2780. https://doi.org/10.1016/j.optcom.2011.02.039