?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Awareness of virus spreading is an important issue for building various defence strategies and protecting personal computers, smart devices, network devices, etc. In this research work, we develop epidemiological models to address this problem and introduce certain modified epidemiological fractional SAIR model, where we consider the fractional derivative in Caputo sense. We utilize the residual power series method to construct approximate solutions for the governing system. To show the efficiency and suitability of the proposed technique, we introduce a comparative between the obtained solutions and those solutions that are constructed using the fourth-order Runge–Kutta method. We derive some numerical results by considering specific values for the parameters in the governing model, and then we depict some of these results into two and three dimensions.
Mathematics Subject Classifications:
1. Introduction
Fractional models are considered as a natural generalization to the classical models with integer order and receive a great attention in the scientific community due to their diverse applications in physics [Citation1], astronomy [Citation2], engineering [Citation3], pharmacology [Citation4] and medicine [Citation5,Citation6]. In literature, many local and non-local fractional operators have been developed and proposed including Caputo–Fabrizio [Citation7], Riesz [Citation8], Palmer [Citation9], Letnikov [Citation10], Grnwald [Citation11], Riemann–Liouville [Citation12], and AtanganaBaleanu operators [Citation13]. This diversity depends on the nature of the real problem used in the applications [Citation14,Citation15].
The computer virus is a form of software that can replicate itself and spread to others from one computer. Viruses target the file system primarily, as worms use system weakness to scan and attack machines. However, computer viruses attacks are the major issues of the computer security and knowing their distribution is an essential component of any defensive strategy.
Since at least in 1988, several disease models discussing computer virus transmissions have been studied. Murray [Citation16] is the first to propose the relationship between computer viruses and epidemiology. Even though Murray did not suggest particular models, he discussed analogies to certain epidemiological protection techniques for public health. A new model involving computer virus propagation on a multi-user device was studied by Gleissner [Citation17], yet no provision was made for the identification and elimination to viruses. At recent days, a group has examined susceptible-infected-susceptible models for computer viruses dissemination at IBM Watson Research Center [Citation18–21].
In recent years, researchers addressing different research questions about computer viruses aims to study computer viruses spreading models, propagation properties, control strategies, tipping point, and epidemic dynamics [Citation22]. Researchers proposed different mathematical models that describe the computer viruses spreading. A number of these models use the general susceptible, infected, recovered (SIR) epidemic model. In Refs. [Citation23,Citation24], the authors applied the residual power series (RPS) method to analyse the SIR epidemic mode. They applied the technique to fractional SIR and compare the output results with the Runge–Kutta method. For computer epidemic, the SIR model is modified to include one more class of computers which are related to non-infected computers with anti-virus, the new model called SAIR. Therefore, computers in SAIR are classified into four classes: susceptible computers, non-infected computers with anti-virus, infected computers, and recovered computers [Citation25]. Freihat et al. [Citation26] used the multi-step homotopy analysis method to describe computer viruses spreading where the technique used is based on the SAIR model.
Furthermore, Lefebvre [Citation27] focuses on the affection of the propagation of computer viruses and studies the time required to clean the infected computers. Furthermore, he divides computers into three categories: susceptible computers, infected computers, and recovered computers. The Lefebvre studies are based on the Kernack–McKendrick model which defines the dynamic of an infectious disease. Moreover, Kumar and Singh [Citation28] proposed a new fractional epidemiological model with the use of Mittag–Lffler law to study the computer viruses spreading. Computer network, as a target of computer viruses, was studied by Upadhyay and Singh [Citation29]. They classified computer nods in a network into two categories: the first category is called attacking class and the second is called targeted class. In each class, they define three types of computers based on the status of each computer: susceptible, infectious, and recovered. On the other side, Tang et al. [Citation30] proposed a new network virus propagation model. The new type is called SLBRS which is based on states' cycle: susceptible, latent, breaking out, recovered, and susceptible. Other applications can be found in Refs. [Citation31–36] and the references therein.
The mathematical model considered in this paper is based on dividing the computer into four groups, where T is the total number of computers. The criteria that have been adopted to classify the computer into groups are the computer status and the existence of the anti-virus. Hence, the four groups of computers are:
Susceptible (S): refers to non-infected computers by viruses but susceptible to be infected. These computers are a subject to be infected at any time according to a communication channel with infected computers.
Anti-virus (A): refers to non-infected computers by viruses but equipped with anti-virus.
Infected (I): refers to infected computers.
Removed (R): refers to removed computers due to an infection or not.
The total number of computers that are subject of this study is: . The following non-linear system of first-order ordinary differential equations describes the SAIR model:
(1)
(1) subject to
Here, α, β, σ, and δ are positive constants. The rate of the susceptible computers S which supposed to be infected depends on creating a communication with infected computers. β is the rate of infections where the susceptible-infected computer communicates with infected ones since it is presented in the product SI. The conversion of the susceptible computers into secured computers (computers with anti-virus) is related to the product SA, as controlled by
, which depends on the foundation of anti-virus defined by computer administrator. On the other side, the use of anti-virus can fix the infected computers and convert them into secured computers with a rate related to AI with rate factor given by
. These computers are subject to be removed with the rate δ as they are being useless. Furthermore, there is a probability with rate σ to restore and convert the removed computer to susceptible computers. These scenarios are considered according to the assumption that the infection is related to known virus.
Based on previous scenarios, the definition of the SAIR model of fractional order can be written in the following form:
(2)
(2) subject to
(3)
(3) where
, and
are the Caputo derivatives of order
, and
for
, and
, respectively, and
To assure the match of the dimension in both sides in the fractional model (2), we consider the coefficient
with aid of the auxiliary parameter γ [Citation33]. The fractional model was considered here, because many physical phenomena have an substantial fractal order description, which makes it necessary to have a fractional system to explain such phenomena. Moreover, the fractional model provides a more accurate model than the ordinary calculus of physical systems [Citation36–42]. We have considered the Caputo derivative in this work because it refers to the memory effect via a convolution between the integer order derivative and a power of time. This paper aims to utilize effective technique, the RPS method, and establish an approximate solution for the fractional SAIR model (1). The proposed method is easy to be performed and computationally attractive to gain the desired numerical solutions for the significant and notable governing model. Despite the importance of this system, it was not given enough attention to devise numerical solutions for it. So, the novelty of this paper lies in using the proposed method to provide such numerical solutions. We will also study the effect of the fractional derivative on the behaviour of the deduced solutions.
2. Preliminaries
The aim of this section is to present some of the fundamental meanings and facts of the fractional calculus and the fractional power series used in subsequent sections of this report.
Definition 2.1
A function is said to be in the space
if it can be written as
for some
where
is continuous in
, and is said to be in the space
if
.
Definition 2.2
The Riemann–Liouville integral operator of order β with is defined as
(4)
(4) The identity operator is
, for
. Hence,
.
Definition 2.3
The Caputo fractional derivative of of order
with
is defined as
(5)
(5)
Definition 2.4
A power series expansion of the form
(6)
(6) is called a fractional power series about
. In particular, at
, the series
is said to be a fractional Maclaurin series. Furthermore, at
, with the understanding that the term corresponding to n = 0 in (Equation9
(9)
(9) ), we consider the convention that
, whereas the fractional power series (Equation9
(9)
(9) ) converges when
.
Theorem 2.5
Let f has a fractional power series (FPS) representation at of the form
It was found that when
, are continuous on
, then
where Γ is the gamma function,
(m-times), and ϱ is the radius of convergence.
3. RPS solution for SAIR of computer viruses
The solution of the non-linear fractional SAIR model is found by implementing the following steps:
Step1: This step has the initial assumption about , and
which have the FPS initial time
as
(7)
(7) where
for some
.
According to this assumption, we use the terms ,
,
, and
to denote the nth truncated series of
and
, respectively, where they can be defined as
(8)
(8) From the initial condition in Equation (Equation3
(3)
(3) ), where n = 0, we have
and
. Thus, we can rewrite the nth truncated series in Equation (Equation8
(8)
(8) ) in the following form:
(9)
(9) Step 2: The definition of the residual functions for the model is given in Equation (Equation2
(2)
(2) ):
(10)
(10) Therefore, the definition of the nth residual functions of
and
are, respectively,
(11)
(11) Obviously,
From the fact that the Caputo derivative of any constant is zero, we can conclude that [Citation37]
The following steps based on this main idea are considered in the core of the RPS method.
Step 3: In this step, the nth truncated series of and
are substituted into Equation (Equation11
(11)
(11) ) to obtain the coefficients
and
, where
. Then, the Caputo fractional derivative operators
,
, and
are applied on
and
, respectively. The following equations are the desired result:
(12)
(12)
4. Implementation and numerical results
For the accuracy of the FRPSM against the known built-in fourth-order Runge–Kutta (RK4), Mathematica procedure will be demonstrated for computer viruses in the case of the integer order derivatives. The FRPSM is coded in Mathematica 10 computer algebra kit. In all calculations performed in this article, Mathematica environment variable digits, which regulate the sum of the significant digits, are set to 20. The fractional SAIR model subject to , and
is
(13)
(13) We refer to the order of the fractional derivative by α where it is in the range
. Using the RPS method's steps, which was discussed in Section 3, leads to the following forms of the first truncated power series approximations
Based on Equation (Equation11
(11)
(11) ), the first residual functions of
,
,
, and
are, respectively, given as follows:
We can compute the value of
,
,
, and
by equating
,
,
, and
by zero. Hence,
For n = 2, the forms for the second truncated power series approximation are
Hence, the second residual functions are
Applying the operator
to
,
,
, and
yields
The value of
,
,
, and
can be computed using the fact
Therefore, we have
Continuing this process, we get the third approximations
Tables – represent a numerical comparison between RK4 solution and RPS solution for
. The results show the accuracy of RPS for approximating the solution of the SAIR model. Furthermore, the absolute error
and relative error
are computed for
as shown in Table , where the
as an absolute error is defined in Equations (Equation14
(14)
(14) ) and (Equation15
(15)
(15) ) and shows the definition of the relative error. Tables – show the absolute value and the relative value of
,
, and
, respectively.
(14)
(14)
(15)
(15) From the observed results in Tables –, we conclude that by using few approximations to obtain a high accuracy via RPS technique. Moreover, from the use of the independent values of the interval [0,1], we observe that the estimated error is more accurate. Finally, the results that show a higher accuracy are achieved as more components of RPS solution are evaluated. Overall, the tables represent that there is a high effectiveness of using the RPS technique.
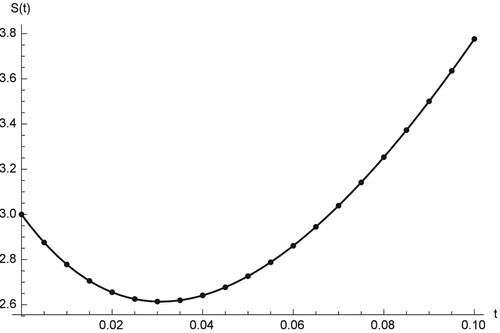
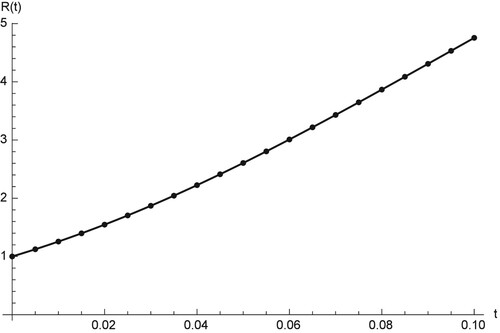
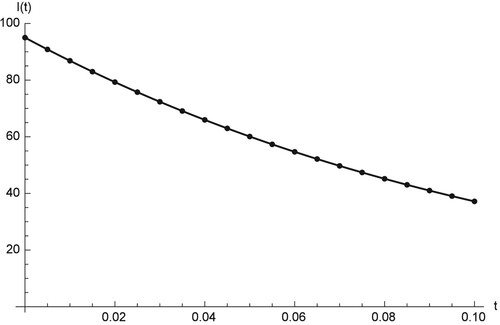
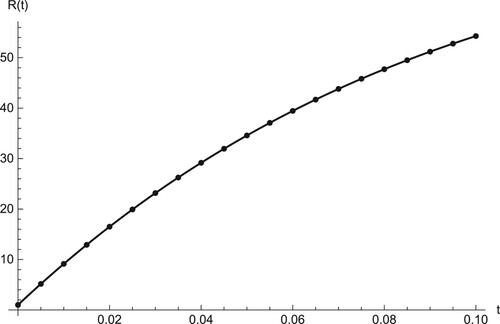
Figures show comparison between the RK and RPS solution of ,
,
, and
for
.
Table 1. Approximate solution of using RK4 and RPS methods.
Table 2. Approximate solution of using RK4 and RPS methods.
Table 3. Approximate solution of using RK4 and RPS methods.
Table 4. Approximate solution of using RK4 and RPS methods.
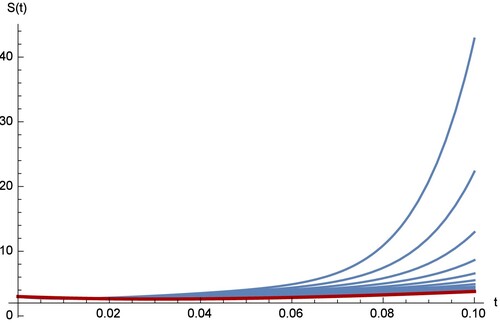
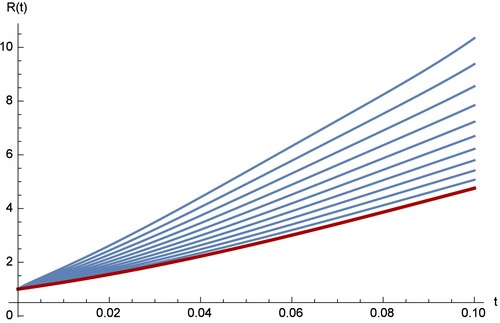
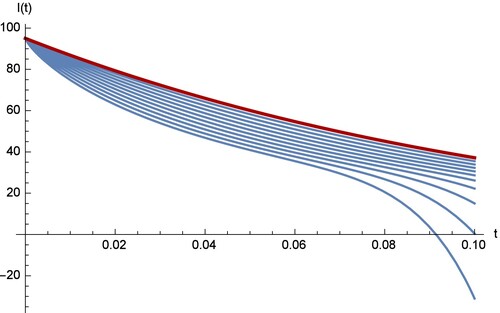
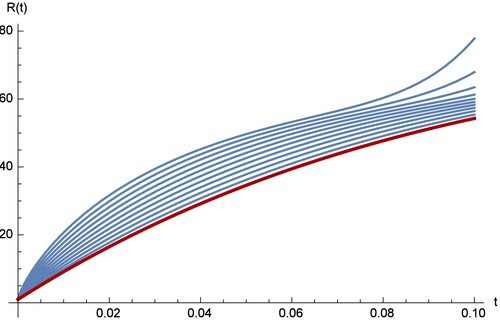
Figures – show the comparison between the RPS and the RK4 solution, where the fractional order is and the sample size is k = 20. From the chart in figures, we see that the approximation which results from using the RPS methods is efficient and can be achieved by implementing similar technique on small samples as in our case is only 20. Figures – show that the two methods can be obtained on
, and
and can predict the behaviour of the four compartments accurately.
Figures show the RPS solution of ,
,
, and
for different value of α. In Figures –, the RPS approximation methods for the four computer categories (susceptible, anti-virus, infected, and recovered) are established for different values of α. The sub-figures show the graphical line for the different values of
, where
with step s = 0.02 over the interval [0,0.1]. In the figures, it is clear that the degree of the freedom for the fractional order derivation is greater than the degree of the integer order derivation. From the four curves of
, and
, we can observe that the four curves of the fractional SAIR model are close to the classical SAIR model as the fractional order close to the integer order.
5. Conclusion
In this paper, we deal with significant model in computer science, SAIR model, which provides a perception of the problem of viruses in the computer field. The fractional version of the SAIR model was considered in this paper. We utilize the power full tool, RPS method, to construct an approximate solution to the governing model. Some of the obtained results have been depicted in two and three dimensions to illustrate the physical properties of it at the selected values for the considered parameters. Moreover, we compare the developed approximate solutions using Runge–Kutta method. The analytical approach solutions of the model are shown to be accurate and have a long time validity. It should be noted that there are very few works in the literature that provide approximate solutions to the governing system in this paper. Therefore, the novelty of this paper lies in presenting approximate solutions to this fractional system using new simple and easy-to-apply method to discuss and study the governing system. The RPSM's power and the capacity are also provided as an easy tool for computing non-linear problem solutions that appear as models in some fields including certain models in science and engineering topics.
Acknowledgments
This research has received funding support from the National Science, Research and Innovation Fund (NSRF), Thailand.
Disclosure statement
No potential conflict of interest was reported by the authors.
Additional information
Funding
References
- Kumar S. A new fractional modeling arising in engineering sciences and its analytical approximate solution. Alex Eng J. 2013;52(4):813–819.
- Kilbas A, Srivastava H, Trujillo J. Theory and applications of fractional differential equations. Amsterdam: Elsevier; 2006.
- Al-Smadi M, Djeddi N, Momani S, et al. An attractive numerical algorithm for solving nonlinear Caputo–Fabrizio fractional Abel differential equation in a Hilbert space. Adv Differ Equ. 2021;2021(1):271.
- Al-Smadi M, Abu Arqub O, Zeidan D. Fuzzy fractional differential equations under the Mittag–Leffler kernel differential operator of the ABC approach: theorems and applications. Chaos Solitons Fractals. 2021;146:Article ID 110891.
- Al-Smadi M. Simplified iterative reproducing kernel method for handling time-fractional BVPs with error estimation. Ain Shams Eng J. 2018;9(4):2517–2525.
- Hasan S, Al-Smadi M, El-Ajou A, et al. Numerical approach in the Hilbert space to solve a fuzzy Atangana–Baleanu fractional hybrid system. Chaos Solitons Fractals. 2021;143:Article ID 110506.
- Abuteen E, Freihat A, Al-Smadi M, et al. Approximate series solution of nonlinear, fractional Klein–Gordon equations using fractional reduced differential transform method. J Math Stat. 2016;12(1):23–33.
- Al-Smadi M, Freihat A, Khalil H, et al. Numerical multistep approach for solving fractional partial differential equations. Int J Comput Methods. 2021;14(3):Article ID 1750029.
- Moaddy K, Freihat A, Al-Smadi M, et al. Numerical investigation for handling fractional-order Rabinovich–Fabrikant model using the multistep approach. Soft Comput. 2018;22(3):773–782.
- Al-Smadi M, Abu Arqub O. Computational algorithm for solving Fredholm time-fractional partial integrodifferential equations of Dirichlet functions type with error estimates. Appl Math Comput. 2019;342:280–294.
- Al-Smadi M, Freihat A, Abu Hammad M, et al. Analytical approximations of partial differential equations of fractional order with multistep approach. J Comput Theor Nanosci. 2016;13(11):7793–7801.
- Alabedalhadi M, Al-Smadi M, Al-Omari S, et al. Structure of optical soliton solution for nonlinear resonant space–time Schrdinger equation in conformable sense with full nonlinearity term. Phys Scr. 2020;95(10):Article ID 105215.
- Al-Smadi M, Dutta H, Hasan S, et al. On numerical approximation of Atangana–Baleanu–Caputo fractional integro-differential equations under uncertainty in Hilbert space. Math Model Nat Phenom. 2021;16:41.
- Al-Smadi M, Abu Arqub O, Hadid S. An attractive analytical technique for coupled system of fractional partial differential equations in shallow water waves with conformable derivative. Commun Theor Phys. 2020;72(8):Article ID 085001.
- Al-Smadi M, Abu Arqub O, Hadid S. Approximate solutions of nonlinear fractional Kundu–Eckhaus and coupled fractional massive Thirring equations emerging in quantum field theory using conformable residual power series method. Phys Scr. 2020;95(10):Article ID 105205.
- Murray W. The application of epidemiology to computer viruses. Comput Secur. 1988;7(2):139–145.
- Gleissner W. A mathematical theory for the spread of computer viruses. Comput Secur. 1989;8(1):35–41.
- Kephart JO, White SR. Directed-graph epidemiological models of computer viruses. In: Proceedings of the IEEE symposium on security and privacy, USA; 1991. p. 343–359.
- Kephart JO, White SR. Measuring and modelling computer virus prevalence. In: Proceedings of the IEEE symposium on security and privacy; 1993. p. 2–15.
- Kephart JO, White SR, Chess DM. Computers and epidemiology. J Mag. 1993;5:20–26.
- Kephart JO, Sorkin GB, Chess DM, et al. Fighting computer viruses. Sci Am. 1997;277:88–93.
- Huang CY, Lee CL, Wen TH, et al. A computer virus spreading model based on resource limitations and interaction costs. J Syst Softw. 2013;86(3):801–808.
- Hasan S, Al-Zoubi A, Freihet A, et al. Solution of fractional SIR epidemic model using residual power series method. Appl Math Inf Sci. 2019;13(2):153–161.
- Freihat AA, Handam AH. Solution of the SIR models of epidemics using MSGDTM. Appl Appl Math. 2014;9(2):622–636.
- Piqueira JRC, Araujo VO. A modified epidemiological model for computer viruses. Appl Math Comput. 2009;213(2):355–360.
- Freihat A, Zurigat M, Handam A. The multi-step homotopy analysis method for modified epidemiological model for computer viruses. Afr Mat. 2015;26(3–4):585–596.
- Lefebvre M. A stochastic model for computer virus propagation. J Dyn Games. 2020;7(2):163.
- Kumar D, Singh J. New aspects of fractional epidemiological model for computer viruses with Mittag–Leffler law. Math Model Health Soc Appl Sci. 2020;39:283–301.
- Upadhyay RK, Singh P. Modeling and control of computer virus attack on a targeted network. Phys A: Stat Mech Appl. 2020;538:Article ID 122617.
- Tang W, Liu Y-J, Chen Y-L, et al. SLBRS: network virus propagation model based on safety entropy. Appl Soft Comput. 2020;97:Article ID 106784.
- Al-Smadi M, Abu Arqub O, Momani S. A computational method for two-point boundary value problems of fourth-order mixed integrodifferential equations. Math Probl Eng. 2013;2013:Article ID 832074.
- Han X, Tan Q. Dynamical behavior of computer virus on internet. Appl Math Comput. 2010;217(6):2520–2526.
- Baleanu D, Abadi M, Jajarmi A, et al. A new comparative study on the general fractional model of COVID-19 with isolation and quarantine effects. Alex Eng J. 2022;61(6):4779–4791.
- Baleanu D, Ghassabzade F, Nieto J, et al. On a new and generalized fractional model for a real cholera outbreak. Alex Eng J. 2022;61(11):9175–9186.
- Erturk V, Godwe E, Baleanu D, et al. Novel fractional-order Lagrangian to describe motion of beam on nanowire. Acta Phys Pol. 2022;140(3):265–272.
- Agarwal P, Nieto J, Ruzhansky M, et al. Analysis of infectious disease problems (Covid-19) and their global impact. Singapore: Springer; 2021.
- El-Ajou A, Abu Arqub O, Al-Smadi M. A general form of the generalized Taylors formula with some applications. Appl Math Comput. 2015;256:851–859.
- Kumar S, Ahmadian A, Kumar R, et al. An efficient numerical method for fractional SIR epidemic model of infectious disease by using Bernstein wavelets. Mathematics. 2020;8(4):558.
- Farman M, Ahmad A, Akgl A, et al. Epidemiological analysis of the coronavirus disease outbreak with random effects. Comput Mater Contin. 2021;67(3):3215–3227.
- Komashynska I, Al-Smadi M, Abu Arqub O, et al. An efficient analytical method for solving singular initial value problems of nonlinear systems. Appl Math Inf Sci. 2016;10(2):647–656.
- Al-Smadi M, Abu Arqub O, El-Ajou A. A numerical iterative method for solving systems of first-order periodic boundary value problems. J Appl Math. 2014;2014:Article ID 135465.
- Chen J, Hu M-B, Li M. Traffic-driven epidemic spreading in multiplex networks. Phys Rev E. 2020;101:Article ID 012301.
- Al-Jarrah A, Massa'deh MO, Baareh AEK, et al. A study on r-edge regular intuitionistic fuzzy graphs. J Math Comput Sci. 2021;23(4):279–288.