?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
The fractional derivative that is used to compute the solution of the corruption system with Power-Law Kernel, Mittag-Leffler Kernel, and Exponential Decay Kernel. It is important to study and analyse corruption dynamics, because it is an act that has a direct effect on public rights, and because of this the right of the rightful owner, just got destroyed. Using hypothesis theory for differential equation, this work suggests and assesses a nonlinear deterministic model for the dynamics of corruption. Positivity and boundedness are verified for the proposed corruption model to identify the level of resolution of corruption factor in society. Fractional-order corruption model is investigated with different kernels for efficient results. The necessary criteria for the best control of corruption transmission were identified using Pontryagin's maximal concept. The numerical simulation showed that corruption must be resisted by an integrated control strategy. Numerical simulations are used to demonstrate the correctness of the proposed approaches. Finally, simulations are derived for the proposed schemes to check the effectiveness of the results and to analyse the corruption behaviour in society as well as dynamically highlight the propagation of corruption group.
1. Introduction
In order to obtain unlawful power for personal interests and illegal profit, the criminal offence or dishonest performed by a single person or an organization is termed corruption. Corruption may be done over a wide span including fraud, illegal payments, bribery and many other unlawful means. Corruption in the political sector occurs when an office bearer or another public servant performs a legitimate service to his advantage. Corruption is very common in our country.
Corruption and crime are social ills that are commonplace in almost every country around the world in varying degrees and proportions. Every nation designed some structures and allocated resources to eliminate or reduce corruption to a maximum extent. Policies and rules have been defined to deal with it and they fall under the anti-corruption section.
Corruption is basically an unlawful activity for personal gain, through the abuse of power or authority by officials from the public sector (government) or the private sector (corporation) [Citation1]. Cuervo-Cazurra et al. examine worldwide commercial corruption, offering a critical appraisal of the problem and recommendations for future research. Because of its illegal nature, variances in perceptions of illegality, and heterogeneity in the application of anti-bribery laws between countries, I believe that corruption serves as a laboratory for developing international business studies in [Citation2]. The facts and ideas offered by top researchers globally provide a backdrop for supplemental and supplementary probes and theories, according to G Geis et al. [Citation3], widespread corruption, and lawlessness [Citation4]. Corruption may be originated on either the demand or supply side [Citation5]. The rules of democracy, law and human rights are all threatened by corruption and integrity. Economic development is hampered by inequity and social fairness and puts the market economy at risk for its proper functioning and impartiality [Citation2, Citation6]. It is a major concern in every country on the planet, particularly in emerging nations [Citation6]. Although the majority of countries have policies or strategies in place to combat corruption, it is still a public epidemic.
Statistical models with comprehensive and detailed control analysis are some key tools in determining and understanding corruption fluctuations and when it comes to corruption decision-making. In the present study, some research studies on corruption exist. A study by [Citation7] suggested and analysed the determining model of human corruption. They calculated the basic reproduction number (BRN), the non-corruption rating scale, and the inherent balance that point to the results of numerical simulations that indicated that corruption can be managed to some extent but not removed. The authors designed and analysed a model by using mathematical tools of the power of corruption [Citation2]. The basic production number and equity points that are free of corruption and corruption are determined. Lemecha [Citation8] elevated them by considering the statistical model of corruption and also the awareness initiated by anti-corruption and prison counselling. The introduction of the unique points free from corruption and endless equality was analysed, and a fundamental production number was computerized. Research in [Citation9] has introduced triangular models that represent the laws of increasing trend or decreasing trend of corruption. In [Citation6], a mathematical model was developed independently to define the corruption level. The research work [Citation10] considered the Game’s theoretical methodology to deal with corruption. Khan [Citation11] developed the anti-corruption model and presented that it is possible to eliminate corruption if the ratio of the rate of dismissal to the level of corruption is equal to unity. The authors [Citation12] created a SIR model for the power of corruption. In addition, the study has expanded the procedure to analyse complete control with one correct control policy. The term corruption, according to KO Jackob, refers to the practice of abusing a public trust or office for personal gain. When there is no political resolve to tackle corruption, it poses a threat to national development and prosperity. EACC’s anti-corruption tactics include prevention and disengagement activities [Citation13].
Some respectable authors, on the one hand, lauded these beginning conditions for their ability to account for aberrant processes. Caputo, on the other hand, proposed an alternative differential operator based on experimental evidence, which is the convolution of a function’s derivative with a power law. The normal initial condition is obtained by applying the Laplace transform to this variant. Furthermore, the function was assumed to be differentiable, which, some writers thought, was a constraint in theory but was a good differentiation in fact, which was necessary for evaluating modifications [Citation14]. With a non-local and no-singular kernel, we presented a novel fractional derivative. We demonstrated some of the new derivative’s valuable qualities and used them to solve the fractional heat transfer model [Citation15] and they do not meet several typical derivative properties such as the index law. We offer a numerical approach and mathematical analysis for the well-known three-dimensional quadratic autonomous self-govern system, which is chaotic due to the coexistence of multi-scroll attractors, as shown by M Khumalo et al. In the Caputo sense, the scheme is based on the Atangana-Baleanu fractional derivative. The fractional derivatives are introduced to the non-local and non-singular kernel in the formulation of these schemes. After that, the fractional derivative is approximated using the Adams–Bashforth scheme family [Citation16, Citation17]. The study concludes that foreign aid does not result in encouraging and significant changes in overall economic growth in developing economies. By contrast, corruption has a powerful impact on foreign aid effectiveness [Citation19].
Different authors use fractional derivatives to understand the actual behaviour of the different types of dynamics. Accordingly, a relatively novel numerical treatment is introduced to investigate and interpret approximate solutions to telegraph and Cattaneo models of time-fractional derivatives in the Caputo sense [Citation20, Citation21]. The reliability, stability and exactness of the proposed FF-ANN-PSO-IPM are established through comparison with outcomes of the standard numerical procedure with the Adams method for both single and multiple autonomous trials with precision of order 4 to 8 decimal places of accuracy [Citation22]. The authors present the analytical treatment to the bioheat transfer Pennes model by modern fractional derivatives and their related phenomena in [Citation23–26]. Some authors consider an initial-value problem comprising this generalization and analyse the existence and the uniqueness of its solution for different epidemic and non-epidemic phenomena, also see their behaviours in [Citation27–31]. A computational method, based on B-spline polynomials and their operational matrix of Atangana-Baleanu fractional integration, is proposed for the numerical solution of this class of problems [Citation32]. For more details, see [Citation37–42].
In this work, we propose a dynamic of corruption with a fractional operator in the introduction section and preliminaries are given to understand the corruption dynamics and methodology used to analyse, respectively. The qualitative and auantitative analysis of the system was also treated. The stability and uniqueness of the system are also presented by using fixed point theory results. Analysis of the model was made with (i) Mitting Lifter Kernel (ii) Power Law Kernel (iii) Exponential Decay Kernel. In the end, numerical simulations are made with the support of theoretical results.
2. Basic of fractional calculus
2.1. Definition: [18]
Allow f (t) to be a function that isn’t always differentiable. Consider the numbers , where is the fractal dimension and is the fractional order. The following is a definition of a Fractal-Fractional derivative with order 0 and 1 and a Power-Law Kernel:
(1)
(1)
(2)
(2)
2.2. Definition: [18]
The Exponential Decay Kernel for Fractal-Fractional Derivative is defined as
(3)
(3)
2.3. Definition: [18]
The Mittag-Leffler Kernel for the Fractal-Fractional Derivative can be defined as
(4)
(4)
2.4. Definition: [18]
Power law-type kernel within the FFI with order is defined as
(5)
(5)
2.5. Definition: [18]
The decay-type kernel within the FFI with order is defined as
(6)
(6)
2.6. Definition: [18]
The Mittag-Leffler-type kernel within the FFI with order is defined as
(7)
(7)
3. Corruption model
At all times during the study, for all humans, we consider a positive natural death rate. Susceptible persons will be transferred to the exposed class if they have a rate of contact with corrupted people of rate p, with a p per contact likelihood of corruption transmission. Individuals moved at a pace to the contaminated compartment with the remainder travelling to the recovered compartments. Corrupted persons learn about the effect of their actions in prison and move to the recovered subpopulation at a rate of these rescued individuals were transferred at a rate of to the vulnerable groups, with the remaining percentage going to the honesty section. All parameter descriptions are listed in Table . Concerning the above considerations, the model will be controlled by the following system of differential equations:
(8)
(8) with the initial condition
(9)
(9)
Table 1. Description of parameters of the corruption model.
3.1. Positive solutions with non-local operators
This section shows that solutions to a fractional calculus model with non-local operators are positive. With non-local operators, all solutions are positive if all beginning conditions are positive. To begin, we’ll look at the Caputo–Fabrizio case.
(10)
(10)
With the Caputo derivative, we obtain
(11)
(11) We obtain the Atangana-Baleanu derivative
(12)
(12)
Theorem 3.1:
Along the starting circumstances, the solution of the proposed corruption model given in system (8) is unique and bounded in .
Proof:
We’ve obtained
If
, then it is impossible to exit the hyperplane, according to the answer. The domain
is a positively invariant set since the vector field on each hyper-plane around the non-negative orthant likewise points to
which shows a positive and bounded solution for the proposed system.
3.2. Application of corruption dynamic model
In this part, the proposed mathematical corruption dynamic model is subjected to the new differential and integral operators. The conventional differential operator will be replaced with the operator with Power-Law, Exponential Decay, and Mittag-Leffler Kernels. Additionally, the version with variable order will be applied. We start with an exponentially decaying kernel.
(13)
(13) For simplicity, we’ll express the equation as follows:
(14)
(14) where
(15)
(15) The following is the result of using a Fractal-Fractional integral with an Exponential Kernel.
For this model, we can have the following scheme
(16)
(16)
(17)
(17)
(18)
(18)
(19)
(19)
(20)
(20)
We can have the following for the Mittag-Leffler Kernel:
(21)
(21)
The following numerical system can be obtained
(22)
(22)
(23)
(23)
(24)
(24)
(25)
(25)
(26)
(26) We can have the following for the Power-Law Kernel
The following numerical system can be obtained.
(27)
(27)
(28)
(28)
(29)
(29)
(30)
(30)
(31)
(31) where
.
Now, using an exponential kernel, we use the same procedure for the fractal-fractional derivative.
(32)
(32) where the operator has a variable fractal dimension and a fixed fractional dimension. The equation above may be rewritten as follows:
(33)
(33)
(34)
(34)
(35)
(35)
(36)
(36)
(37)
(37)
The following numerical approximation results from using the same method.
(38)
(38)
(39)
(39)
(40)
(40)
(41)
(41)
(42)
(42) For the Mittag-Leffler Kernel,
(43)
(43)
(44)
(44)
(45)
(45)
(46)
(46)
(47)
(47) As a result, we may provide the following technique for solving our equation numerically.
(48)
(48)
(49)
(49)
(50)
(50)
(51)
(51)
(52)
(52) For the Power-Law Kernel,
As a result, for the numerical solution of our equation, we may provide the following approach.
(53)
(53)
(54)
(54)
(55)
(55)
(56)
(56)
(57)
(57)
4. Results and discussion
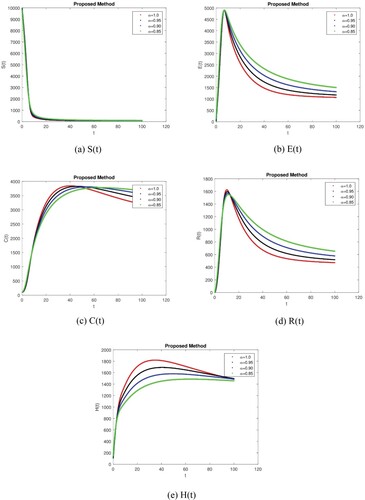
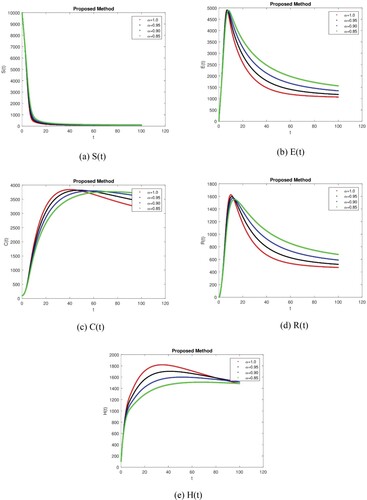
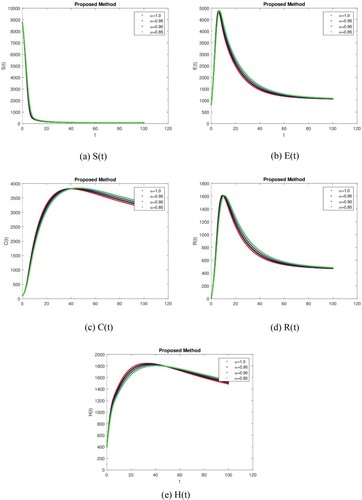
By using the Power-Law, Exponential Law, and Mittag-Leffler kernel techniques, we obtain the numerical simulation, and the graphs act for the numerical simulation results for the different values of = 0.95, 0.90, 0.85, and 1.0. The numerical simulations in this section are used to study the temporal dynamical behaviour associated with the corruption using fractional-order parameters. It is critical to demonstrate the feasibility of the stated work and to test the validity of the analytical work using large-scale numerical simulation. The numerical results of the model for different fractional values are determined according to the steady-state point using different kernels. The model’s dynamics are affected by a change in value, according to these simulations. We can also see that compared to the traditional derivative, the fractional value results are more efficient in all three cases. We obtain the results as shown in Figure (a–e) by executing the Mittag-Lefler Kernel with the specified parameter values. Figure (a) shows that the susceptible individual decreases as fractional values decrease due to an increase in exposed and corrupt individuals. Figure (b,d) shows that the exposed and recovered individual increases and then decreases after a certain time and approaches its stable position as fractional values decrease but this stable position does not show its control position. Figure (c) shows that corrupt individuals increase and after a certain time it comes to a stable position due to campaigning shows that we may first stop to increase the corrupt people. Recovered individuals increase due to an increase in honest individuals and come to a stable position after a certain time, as shown in Figure (d,e). We obtain the results shown in Figure (a–e) by executing the Power-Law kernel with the specified parameter values. Similarly, we get the results shown in Figure (a–e) by executing the Exponential Law kernel with the specified parameter values. Similar behaviour can be seen in Figure (a–e) and in Figure (a–e) as can be seen in Figure (a–e) with minor effects. This shows that it requires more social media campaigns and punishment of corrupt individuals to stop corruption in society in all three cases. The graphical representation shows that over time, susceptible individual decreases due to an increase in corrupt people in all cases with minor effects. It indicates that we need to control corrupt individuals differently and need a strong punishment system to control it.
Figure 1. Simulation of all Compartments of the Corruption Model with the Mittag-Lefler Kernel using different fractional values.
5. Conclusion
We proposed a corruption model in this study to analyse corruption in society to check the dynamical behaviour of the system for constant controls with fractional operators. Positive and bounded solutions for corruption effects are verified. This research shows that the fractional operator approach provides more useful outputs on compartmental population dynamics than the classical model using different kernels. As a result, the Power-Law Kernel, Mittag-Leffler Kernel, and Exponential Decay Kernel can be concluded to be especially helpful for modelling real-world problems to analyse for efficient results. A numerical simulation is used to show the influence of fractional order to analyse its effects on the community using MATLAB. It is clear from the simulation that it affects the individual and corrupts group rises over time and we need a strong punishment process to overcome the effect of corruption. So, in order to overcome this habitual-minded and poverty factor-minded individual, it required anti-corruption campaigning through media and advertisements and putting corrupt people in jails and punishing them to make your society corruption free. To examine the actual action of corruption in the community, we execute the process of hanging.
Disclosure statement
No potential conflict of interest was reported by the author(s).
References
- Bahoo S, Alon I, Paltrinieri A. Corruption in international business: a review and research agenda. Int Bus Rev. 2020;29(4):101660.
- Cuervo-Cazurra A. Corruption in international business. J World Bus. 2016;51(1):35–49.
- Pontell HN, Geis G. International handbook of white-collar and corporate crime. Irvine, CA: Springer; 2007.
- Eguda F, Oguntolu F, Ashezua T. Understanding the dynamics of corruption using mathematical modeling approach. Int J Innov Sci Eng Technol. 2017;4(8):190–197.
- Heimann F, Boswell NZ. The OECD convention: milestone on the road to reform. New perspectives on combating corruption. p. 65–74. Washington: Transparency International; 1998.
- Alemneh HT. Mathematical modeling, analysis, and optimal control of corruption dynamics. J Appl Math. 2020;2020:Article ID 5109841, 1–13.
- Abdulrahman S. Stability analysis of the transmission dynamics and control of corruption. Pac J Sci Technol. 2014;15(1):99–113.
- Lemecha L. Modelling corruption dynamics and its analysis. Ethiop J Sci Sustain Dev. 2018;5(2):13–27.
- Waykar SR. Mathematical modelling: a comparatively mathematical Study model base between corruption and development. IOSR J Math. 2013;6(2):54–62.
- Nikolaev P. Corruption suppression models: the role of inspectors’ moral level. Comput Math Model. 2014;25(1):87–102.
- Khan MAU. The corruption prevention model. J Discrete Math Sci Cryptogr. 2000;3(1-3):173–178.
- Athithan S, Ghosh M, Li X-Z. Mathematical modeling and optimal control of corruption dynamics. Asian-Eur J Math. 2018;11(06):1850090.
- Nathan O, Jackob K. Stability analysis in a mathematical model of corruption in Kenya. Asian Res J Math. 2019;15(4):1–15.
- Caputo M. Linear models of dissipation whose Q is almost frequency independent—II. Geophys J Int. 1967;13(5):529–539.
- Atangana A, Baleanu D. New fractional derivatives with nonlocal and non-singular kernel: theory and application to heat transfer model. arXiv preprint arXiv:1602.03408, 2016.
- Mathale D, Goufo EFD, Khumalo M. Coexistence of multi-scroll chaotic attractors for a three-dimensional quadratic autonomous fractional system with non-local and non-singular kernel. Alexandria Eng J. 2021;60(4):3521–3538.
- Xu C, Farman M, Hasan A, et al. Lyapunov stability and wave analysis of Covid-19 omicron variant of real data with fractional operator. Alexandria Eng J. 2022;61(12):11787–11802.
- Ahmad S, Ullah A, Abdeljawad T, Akgül A, Mlaiki N, Analysis of fractal-fractional model of tumor-immune interaction, Results Phys, 2021;25:104178.
- Yu Y, Lihong H, Mouneer S, Ali H, Munir A. Foreign assistance, sustainable development and commercial law: a comparative analysis of the impact of corruption on developing economies. Front Environ Sci. 2022;10:959563. doi:10.3389/fenvs.2022.959563
- Abu-Gdairi R. Analytical solution of nonlinear fractional gradient-based system using fractional power series method. Int J Anal Appl. 2022;20:51.
- Al-Smadi, M., Arqub, O.A. and Gaith, M., Numerical simulation of telegraph and Cattaneo fractional-type models using adaptive reproducing kernel framework. Math Methods Appl Sci, 10(4), 2020, doi:10.1002/mma.6998
- Umar M, Sabir Z, Raja MAZ, et al. Neuro-swarm intelligent computing paradigm for nonlinear HIV infection model with CD4+ T-cells. Math Comput Simul. 2021;188:241–253.
- Abro KA, Atangana A, Francisco J, et al. An analytic study of bioheat transfer Pennes model via modern non-integers differential techniques. Eur Phys J Plus. 2021;136(11):1–11.
- Abro KA, Atangana A, Gómez Aguilar JF. A comparative analysis of plasma dilution based on fractional integro-differential equation: an application to biological science. Int J Model Simul. 2023;43(1):1–10.
- Li X, Agarwal RP, Gómez Aguilar JF, et al. Threshold dynamics: formulation, stability & sensitivity analysis of co-abuse model of heroin and smoking. Chaos, Solitons Fractals. 2022;161:112373.
- Takasar H, Ullah AA, Abro KA, et al. A passive verses active exposure of mathematical smoking model: a role for optimal and dynamical control. Nonlinear Eng. 2022;11(1):507–521.
- Jajarmi A, Baleanu D, Sajjadi SS, et al. Analysis and some applications of a regularized Hilfer fractional derivative. J Comput Appl Math. 2022;415:114476.
- Baleanu D, Ghassabzade FA, Nieto JJ, et al. On a new and generalized fractional model for a real cholera outbreak. Alexandria Eng J. 2022;61(11):9175–9186.
- Baleanu D, Abadi MH, Jajarmi A, et al. A new comparative study on the general fractional model of COVID-19 with isolation and quarantine effects. Alexandria Eng J. 2022;61(6):4779–4791.
- Jajarmi A, Baleanu D, Vahid KA, et al. A new and general fractional Lagrangian approach: a capacitor microphone case study. Results Phys. 2021;31:104950.
- Erturk VS, Godwe E, Baleanu D, et al. Novel fractional-order Lagrangian to describe motion of beam on nanowire. Acta Phys Pol A. 2021;140(3):265–272.
- Tajadodi H, Khan A, Francisco Gómez-Aguilar J, et al. Optimal control problems with Atangana-Baleanu fractional derivative. Optim Control Appl Methods. 2021;42(1):96–109.
- Khan H, Alam K, Gulzar H, et al. A case study of fractal-fractional tuberculosis model in China: existence and stability theories along with numerical simulations. Math Comput Simul. 2022;198:455–473.
- Begum R, Tunç O, Khan H, et al. A fractional order Zika virus model with Mittag–Leffler kernel. Chaos, Solitons Fractals. 2021;146:110898.
- Khan H, Begum R, Abdeljawad T, et al. A numerical and analytical study of SE (Is)(Ih) AR epidemic fractional order COVID-19 model. Adv Differ Equ. 2021;2021(1):1–31.
- Khan H, Begum R, Abdeljawad T, et al. A numerical and analytical study of SE (Is)(Ih) AR epidemic fractional order COVID-19 model. Adv Differ Equ. 2021;2021(1):1–31.
- Ahmad H, Khan MN, Ahmad I, et al. A meshless method for numerical solutions of linear and nonlinear time-fractional Black-Scholes models. AIMS Math. 2023;8(8):19677–19698.
- Ahmad H, Ozsahin DU, Farooq U, et al. 2023.
- Khaliq S, Ahmad S, Ullah A, et al. New waves solutions of the (2+1)-dimensional generalized Hirota–Satsuma–Ito equation using a novel expansion method. Results Phys. 2023;50:106450.
- Qayyum M, Ahmad E, Tauseef Saeed S, et al. Homotopy perturbation method-based soliton solutions of the time-fractional (2 + 1)-dimensional Wu–Zhang system describing long dispersive gravity water waves in the ocean. Front Phys. 2023;11:1178154.
- Adel M, Khader MM, Ahmad H, et al. Approximate analytical solutions for the blood ethanol concentration system and predator-prey equations by using variational iteration method. AIMS Math. 2023;8(8):19083–19096.
- Ullah I, Ullah A, Ahmad S, et al. A survey of KdV-CDG equations via nonsingular fractional operators. AIMS Math. 2023;8(8):18964–18981.