Abstract
The study explores the intellectual structure, development, and evolution of national security research through bibliometric analysis of research articles on national security from 2000 to 2017. The analysis incorporates 54,572 references cited by 5,827 authors from 817 journals in which national security appeared. The results of the study present the most cited articles, authors, countries, institutions, and keywords in the knowledge domain of national security. The study categorizes the major research areas in national security research. The study ends with a discussion on results and concludes findings and implications by describing emerging trends and neglected areas in national security research.
PUBLIC INTEREST STATEMENT
The concept of national security has always been comprehend in its traditional way “military security”. The researchers have given a lot of attention to change the comprehension from traditional to non-traditional security elements which includes a wide range of socio-political and economic factors. The national security literature is evolving and the present study gathers all the debates in this knowledge domain as it enters in 21st century. The study gives a detailed view of national security research with dominant articles which really influence the course of this concept and are shaping the future trends. The study provides the different clusters within the national security knowledge domain to make it more convenient for readers to comprehend the evolution of these categories. The study also highlights the authors, institutions, and countries which are contributing significantly in national security research to make it more sound more security policies at national and international level.
1. Introduction
National security remains a site for many scholars to contest and express their ideas about who, what, and where is to be secured. This comprehension of national security reflects the policy directions through which national issues are perceived and answered (Anwar & Rafique, Citation2012). The concept of national security appears to be ambiguous and as one analyze it more deeply gets more confused due to the unavailability of specifications (Wolfer, Citation1952). The concept of security in third world countries needs to be addressed more than military security. This includes nation building to enhance internal security, securing food, better health system, and economic security (Azar & Moon, Citation1988). Security in Third World countries has been analyzed through US or USSR regional interests rather than their vulnerabilities of national structures, institutions, and regimes (Ayoob, Citation1991). The realist representation of security as a derivative of power has reduced the complexity of this concept (Stone, Citation2009).
When another nation is presented as a threat, inner emotional difficulties are treated with the projection of self-attributes with the nation in focus. This increases the need for love by redefining the symbols of the nation as more protective, indulgent, powerful, and wise (Lasswell, Citation1936). The prominence of national security in foreign policy and international politics by academicians and politician has appeared after world war II. Since then it has been misused and abused especially by politicians (Baldwin, Citation1997). The concept of national security renders its political and scientific application. The value states place on security varies greatly as some states are more interested to acquire more values by overestimating or underestimating the security as “the absence of threats to acquired values”. States might overestimate or underestimate the perceived damages for their acquisition (Wolfer, 1952). National security concept remains underdeveloped due to definitional difficulty, overlapping with power concept and less attention from scholars to its conceptual development. Comprehensive National security should incorporate political, economic, environmental, and societal approaches along with its traditional military approach (Buzan, Citation1991). The truth in a society is based on material factors such as influence. This truth is socially constructed interpretation of reality. The concept of security in a broader sense is contextual by defining the nature of the act in the securitization framework as designated threats to security (Mcdonald, Citation2008).
The end of the cold war brought a major shift in the concept of security. The refocus was on non-military aspects of security which include a broad range of domestic security issues ranging from economic to ecological. This leads the securitization to comprehend various dynamics between state and individuals (Wæver, Citation1993). Security is now being built with society as its core element. Security through collective projects, public initiatives, and international political actions change the narratives of responsible actors in communicating security themes (Smith, Citation1999). National security should be developed by choosing the right model at right time for the right place. By implementing the wrong model at the wrong time can result in more violence or prolong violence (Morris, Citation2012). National security is a prevention of values and standards from the threat in the present and future. Threats include human and non-human both and narrow policy options which can affect the quality of life for its nationals (Romm, Citation1993). National security is meant to prevent war and if imposed it guarantees the victory of the nation (Lippmann, Citation1943). The concept of security can be expressed as a measurable level of capabilities of a nation at any specific time (Paleri, Citation2008).
The vast literature does not provide clear dimension from the debates on the idea of national security and even the direction of its expansion. The study found no research which could summarize the research fronts and intellectual base in the development of national security concept except a few on human security and collaborative leadership. The study explores the evolution of the concept of national security to get a clear dimension of an idea through scienometric analysis of 54,572 references made by 5,827 authors in 817 journals from Web of Science from 2000 to 2017. It identifies the influential research areas in national security both in past and present and indicates some future directions in this domain.
2. Methodology
In the field of information science and management, the Bibliometric analysis can be classified as the mathematical and statistical method to gauge the magnitude of trends and patterns in the existing knowledge set, i.e. the author’s contributions, the performance of the institutions, to understand the geographic and logical integrations in the form of clusters within literature (Budd, Citation1988; Erar, Citation2002; Fairthrone, Citation1969). Conceptually, the bibliometric analysis in the form of quantitative and the qualitative findings uses Bradford’s dispersion law to analyze literature (Budd, Citation1988), Zipf’s law to understand data intelligently (Piantadosi, Citation2014), and the author’s, countries’, and the institution-level contribution by the help of Lotka’s law (Pao, Citation1985). The successful trend pattern in the research areas can be driven.
Citespace is the well-structured software package designed by the Drexel University, which helps to construct information visualization, and bibliometric analysis in a quantitative manner. The functional attributes like co-citation analysis for authors, references and journals, and the co-occurrence of keywords encourages the scientists to identify the emerging trends in the keyword domain area while focusing on the specified time frame. In the academic pool of literature, it is obvious to be observed that enormous scientific studies have preferred to use “Citespace” for analyzing the evolving knowledge space. For example: in the field of environmental sciences (Chen, Citation2016) analyzed “energy” and highlighted the development in the primary theoretical concerns and the environmental sustainability are the future hotspots in scientific studies. GU et al (Citation2017) analyzed the discipline of “medical informatics” in a structural manner and uncover the highly trending area of big-data as a future direction and Li et al. (Citation2016) reviewed the health risks related to the research stream of “toxicity” and “PFOA” by using Citespace.
This bibliometric research in the area of national security was aimed at scratching the intellectual structure, and to list and analyze articles, authors, and institutions in this knowledge area as well as highlighted the future research directions. During the first step to compiling a database that is suitable for the national security-related studies, the study selected reputable journals in the relevant knowledge area as refereed journal articles are reliable sources of knowledge and the quality of journals usually implies the quality of articles. Only the “Social Science Citation Indexed” (SSCI) based results from the “Web of Science” (WoS) were consider for the further studies, as the WoS provides inter-disciplinary citation indexing, ability to provide pattern recognition in the literature, and the results which can be graphically representable (Web of Science, Citation2016). In terms of bibliometric studies, WoS provides deep insight as compared to other available service provides, i.e. Scopus (Bettencourt & Kaur, Citation2011) and preferred in the existing bibliometric studies (Shiau, Citation2015; Topalli & Ivanaj, Citation2016; Wang, Lai, Zuo, Chen, & Du, Citation2016). Although the keywords are holding technical terms and nature, so the purpose of using SSCI was to understand the on-going academic developments in the field of political science, public administration, area studies, security studies, and other disciplines, i.e. socio-economic and environmental sciences. These keywords were then reviewed and refined by existing academic literature in Web of Science for scholarly articles on national security. The resultant values were cross-checked by using other scholarly search engines such as “Emerald”, “EBSCO”, “Springer”, “Sage”, and “Wiley”. After the keyword search, findings were further scrutinized to identify whether they were relevant to national security studies. Further, to create valued results, the content as the value of call for papers, introduction to special issues, volume indexes, books, book reviews, commentaries, conference proceedings, doctoral theses, focus on national security were excluded. The above screening procedures were aimed at ensuring that the focus of the study was mainly on scholarly articles on national security. Moreover, after reducing the irrelevant results manually and eliminating the duplication in the search results, the findings from the WoS analyzed to reveal the emerging trends and dimensions in literature.
3. Results
This section represents the discussion on the findings of a quantitative analysis of 54,572 references made by 5,827 authors in 817 journals in the past two decades. The results contain co-citation analysis, keywords analysis, analysis of journals, and analysis of institutions that influence the national security as a field of study. Co-citation analysis helps to show the intellectual relationships between scholars and their works for an available time. It exposes the most influential work that has been important to reshape the intellectual structure of national security Article and furthermore it helps to identify future research areas through burst detection analysis. It enhances the comprehension of the structure of any discipline both at the micro and macro level (Liu, Yin, Liu, & Dunford, Citation2015).
3.1. Highly cited articles in national security research
3.1.1. Article co-citation analysis
The analysis of co-cited articles explores the links between co-cited references. This network can be used to show the primary intellectual structure of a given field of study. Co-citation analysis specifically identifies the uniformity of concepts and references in terms of their association with national security (Chen & Ibekwe-Sanjuan, Citation2010). Highly co-cited articles are good indicators of advanced ideas and developments in the field of national security. This co-citation network in national security covers 5827 articles published between 2000 to 2017 with 2514 nodes and 5862 links. Each node in co-citation analysis demonstrates single cited article, journal, or author. The node size represents cumulative co-citation frequency of specific scholarly article and its ring’s thickness indicates the total number of co-citations across the given time series (Chen, Hu, Liu, & Tseng, Citation2012).
CiteSpace deploys color codes to nodes and edges to distinguish joint networks and each year is represented by a different color. The links connecting different nodes indicates co-citation links among different articles, co-citation frequency depends on the thickness of these links (Seyedghorban, Matanda, & LaPlaca, Citation2016).
The figure shows the co-citation analysis results. The article with largest citation ring is by Seligman, Laraia, and Kushel (Citation2009) titled “Food insecurity is associated with chronic disease among low-income NHANES participants” indicating that it is most frequently cited article in the national security research area with 28 total citations. Using data from 5094 poor adults studies the relationship between food insecurity and adverse health outcomes. They found an association between food insecurity and chronic diseases especially cardiovascular. The second largest co-cited article is by Foucault, (Citation2007) titled “security, territory and population” with a total citation of 26. It’s an edited compilation of Foucault’s lectures at College de France. Foucault explores the biopower and techniques of security to control and regulate population with institutions in the sphere of the nation-state. The transformation of government into governmentality (Table ).
Table 1. Top10 Article co-citation analysis of the knowledge domain of “National Security” during the year 2000–2017
The third most frequent co-cited article with total citation of 23 is by Seligman el at, (Citation2007) titled “Food Insecurity is Associated with Diabetes Mellitus: Results from the National Health Examination and Nutrition Examination Survey (NHANES) 1999–2002”. With a cross-sectional analysis of the National Health and Nutrition Examination Survey from 1999 to 2002, they find that 16% of severely food insecure participants have diabetes. Food insecurity acts as a factor for diabetes as inexpensive food is high in calories but low in nutrition value. Fourth highest co-citation of the article is by Godfray et al. (Citation2010) titled “Food Security: The Challenge of Feeding 9 Billion People” with 22 citations, explores the complex relationship between population growth and demand for food consumption. The ongoing continuity in population and consumption growth will lead to food demand for the next 40 years. Calls for a global strategy to protect the bioecology and environment from the effects of the food system (Figure ).
Figure 1. Article co-citation analysis of the knowledge domain of “National Security” during the year 2000–2017
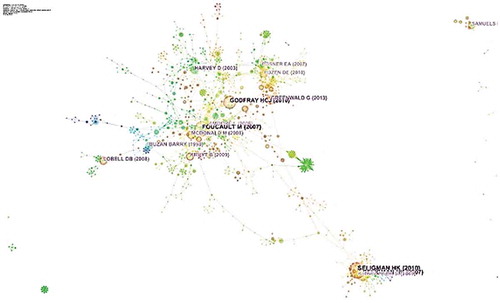
The fifth highest cited work is by Greenwald (Citation2013) with a frequency of 16 citations in the covered period. Greenwald G at that time was a columnist in guardian and wrote vigorously on civil liberties and US national security. In 2013, he wrote a number of columns in guardian covering different topics on NSA, UK, and US government and privacy & freedom. The most impactful writing was on Xkeyscore an NSA tool through which any official can collect almost everything an Internet user does on the Internet without any authority’s approval. This ignites debate on surveillance and internet user privacy.
Mcdonald, (Citation2008) comes sixth with a citation frequency of 15 for an article titled “securitization and the construction of security”. Criticizing the framework of securitization, he presents the idea of the broader framework with two characteristics namely “analytical values” and “progressive normative implications”. As “securitization framework problematically narrow” when it comes to defining the form of the act, the context of act and nature of the act. Harvey, (Citation2003) with his book titled “the new imperialism” shares the same position with a citation frequency of 15. Explores the domestic politics of US and its military adventure abroad, war and oil in Iraq and the role of the economy in foreign militarism. He exposes the primary factors which operate these significant shifts in US politics and its policies. Lobell et al. (Citation2008) shares this position with Macdonald (2008) and Harvey (Citation2003) with citation frequency of 15 for his scholarly work titled “Prioritizing Climate Change Adaptation Needs for Food Security in 2030”. The investments to improve “agricultural adaptation to climate” do not favor regions evenly. They analyze climate risk to crops in 12 food insecure areas by deploying “statistical crop model” and “climate projection” for 2030 and find that Africa and South Asia regions as insufficient adaptation measures.
Next position is shared by four authors with citation frequency of 14, (i) Kruyt, van Vuuren, de Vries, and Groenenberg (Citation2009) titled “indicators for energy security” discuss availability, accessibility, affordability, and acceptability of energy; (ii) Kirkpatrick & Tarasuk, Citation2008) titled “Food insecurity is associated with nutrient inadequacies among Canadian adults and adolescents” call policy attention toward household food insecurity due to inadequate nutrition intake; (iii) Amoore, (Citation2006) titled “Biometric borders: Governing mobilities in the war on terror” proposes biometric borders by deploying “scientific technologies and managerial expertise” for border management along with exercise of bio-power; and (iv) Buzan, Wæver, and Wilde (Citation1998) book titled “security: a new framework for analysis” representing a synthesis for traditional and widening concepts on security by incorporating constructive approach into a single framework.
3.1.2. Burst detection in article co-citation
CiteSpace has another algorithm function “burst detection” which helps to identify current topics and emerging trends in a given field of interest. Burst detection identifies key research areas with articles actively getting attention in a field of study in a specific time (Chen, Citation2006). The table represents the results for burst detection and shows the top five most significant publication with the highest citation bursts in national security research in past 20 years. The articles in burst detection analysis can indicate previous trends, emerging trends, and their impact on possible future research trends in the domain of national security (Table ).
Table 2. Burst detection in article co-citation analysis of the knowledge domain of “National Security” during the year 2000–2017
This also presents an interesting twist as one finds that the articles with highest citation frequency may or may not have the highest burst. Burst detection analysis for national security for this specific time period stands valid. The article with the highest detected burst is by Barry. Buzan et al. (Citation1998) not listed in the top 10 highest cited research work as discussed in the previous section. This book is considered as an outline of ideas of Copenhagen school about security. This widening concept of security presents political, social, economic, and environmental as key factors for security analysis along with traditional military security, initiated a new debate to extend the securitization agenda.
The second highest burst is detected for Katzenstein (Citation1996) for his book titled “the culture of national security: Norms and identity in world politics” and again it has low citation frequency of 11. It presents a sociological perspective of national security politics by analyzing the dramatic changes in world politics during 1980 and 1990. “Security interests are defined by actors who respond to cultural factors”. This perspective has been developed by incorporating cultural and institutional framework of policy and constructed identity of the state. Next comes Greenwald (Citation2013) with third highest burst detection with his columns on civil liberties and US national security. Harvey, D. C. N.-E. H. Citation2003 320. 9730905. M. C. L. E. H. 2003 (2003) work “The new imperialism” is detected to have forth highest burst in an attempt to expose the underlying factors of US domestic politics and its foreign military adventures. The fifth highest burst represents the most interesting finding of this analysis with Seligman et al. (Citation2009) scholarly work “Food insecurity is associated with chronic disease among low-income NHANES participants” having highest citation frequency in last 12 years.
3.2. Keyword co-ward analysis
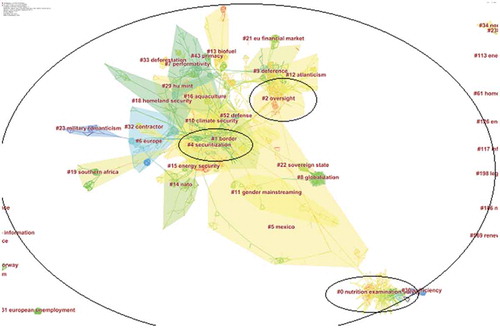
“Keyword co-word analysis” is applied to detect changes in a particular research area which can be helpful to indicate the ongoing research in a certain knowledge domain (Liu et al., Citation2015). Keyword co-word analysis enables one to extract important concepts under study and helps to identify significant conceptual foundation of the study area. The keyword co-word analysis for national security indicates 547 nodes and 3555 links. Security, policy, food security, politics, united states, national security, war, climate change, and China are the most frequently cited keywords. The keyword analysis reveals “policy” keyword as most important research avenue within the national security studies with 276 citations followed by food security (275), politics (249), USA (224), and war (189). It is justified as all the debates in this domain constructed around the concept of security from various aspects like the military, social, political, economic, environmental, health, food, and human (Table ).
Table 3. Top 10 keywords in terms of frequency and centrality
Yang and Li (Citation2000) titled “Cultivated Land and Food Supply in China” investigates the cultivated land changes in China by incorporating state and provincial data in terms of food supply and indicate that under current land management system China will compromise her long-term food security, and Shiau, Samaras, Hauffe, and Michalek (Citation2009) titled “Impact of battery weight and charging patterns on the economic and environmental benefits of plug-in hybrid vehicles” develop “Plug-in hybrid electric vehicle” PHEV simulation models with additional batteries to explain its effect on fuel consumption, its cost and emission of greenhouse gases by measuring distance travel between charges and propose the adoption of small capacity plug-in hybrid electric vehicles for urban users, are most frequently cited articles by keyword policy.
Chen (Citation2007) titled “Rapid urbanization in China: A real challenge to soil protection and food security” analyzes the accelerated urbanization and its impact on cultivated land in China to indicate an immediate policy response toward national food security goal and to mitigate the soil pollution as a result of this urbanization, and Rudel et al. (Citation2009) titled “Agricultural intensification and changes in cultivated areas, 1970–2005” incorporate national data of “United Nations Food and Agricultural Organization” data for cropland between 1970 and 2005 to find the relationship of intensified agriculture and decline in cultivated land and find no such relation with available data, are highly cited article by keyword food policy.
Hansen (Citation2000) titled “The Little Mermaid’s Silent Security Dilemma and the Absence of Gender in the Copenhagen School” analyzes the honor killing in Pakistan as a matter of survival which encompasses individual security as construct of collective security and proposes the inclusion of gender in the security agenda, and Elbe (Citation2006) titled “Should HIV/AIDS Be Securitized? The Ethical Dilemmas of Linking HIV/AIDS and Security” formulate the global response on HIV/AIDS by using securitization theory and conclude that the theory is unable to resolve the complex agenda, have highest citation frequency, are highly cited articles by keyword politics (Figure ).
Figure 2. Keyword co-word analysis of the knowledge domain of “National Security” during the year 2000–2017
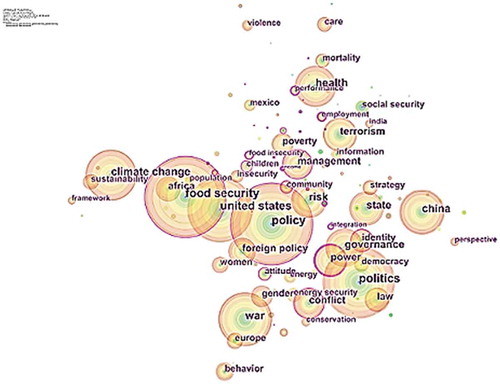
Alaimo, Olson, and Frongillo (Citation2001) titled “Food insufficiency and American school-aged children’s cognitive, academic, and psychosocial development” uses the Third National Health and Nutrition Examination Survey (NHANES III) to show the relationship between negative academics and family level food insufficiency, and Perls et al. (Citation2002) titled “Life-long sustained mortality advantage of siblings of centenarians” present hypothesis that living to extreme old age encompasses a significant familial tendency of longevity by analyzing “pedigrees” of 444 centenarian families in the US by comparing 2,092 centenarians siblings with 1900 “birth cohort survival data” from the US social security administration, are highly cited articles by keyword USA.
Turner (Citation2001) titled “The erosion of citizenship” argues that withdrawn of national citizenship have been enlarged by global rights like environmental, aboriginal, and cultural rights replacing social security with ontological security, and Pantazis and Pemberton (Citation2009) titled “From the ‘Old’ to the ‘New’ Suspect Community: Examining the Impacts of Recent UK Counter-Terrorist Legislation” uses Hillyard’s (Citation1993) “suspect community” notion to analyze the effects of identifying Muslims as “suspect community” in counter-terrorism legislation and indicates that it will hamper national security, are highly cited articles by keyword war.
3.3. Cluster analysis
CiteSpace can perform another quantitative function which is called cluster analysis. It helps to classify co-citation networks by key clusters of references which associate closely with each other and loosely with other clusters of co-cited (Chen & Ibekwe-Sanjuan, Citation2010). This association within the cluster and with other clusters helps to indicate active research areas and the areas which need more attention in the field of national security. The results of this analysis for national security reveals that most of the scholars have consumed the intellectual energies to analyzing national security through nutrition examination survey broadly under adult mortality making it the largest cluster with 142 members. The highest frequently co-cited articles in this cluster are Seligman et al. (Citation2007) titled “Food insecurity is associated with chronic disease among low-income NHANES participants”, Seligman et al. (Citation2007) titled “Food Insecurity is Associated with Diabetes Mellitus: Results from the National Health Examination and Nutrition Examination Survey (NHANES) 1999–2002” and Kirkpatrick and Tarasuk (Citation2008) titled “Food insecurity is associated with nutrient inadequacies among Canadian adults and adolescents”. The second largest cluster analyzes national security in the light of border and biopolitics with 139 members. The most co-cited articles are Sparke (Citation2006) titled “A neoliberal nexus: Economy, security and the biopolitics of citizenship on the border” exploring the development of advanced border crossing program (NEXUS) and how it changes the political geography in North America. Amoore, (Citation2006) titled “Biometric borders: governing mobilities in the war on terror proposes scientific technologies and managerial expertise” for border management along with exercise of bio-power and Fearon and Laitin (Citation2001) titled “Ethnicity, insurgency and civil war” challenges the traditional understanding that accounts the end of cold war for proliferating civil wars and presents conditions like poverty, slow economic growth, weak state institutions and large population that favor insurgency for political agenda (Figure ).
The third largest cluster in national security is detected with term homeland security under log likely hood of secrecy with 121 members. Waxman (Citation2012) titled “National security federalism in the age of terror” presents a federalism frame by focusing on vertical intergovernmental arrangements for promotion of policy values of accountability and efficiency for long-term cooperation in boosting national security, Frost (Citation2007) titled “The state secret privilege and separation of powers” challenges the state secret privileges against executive conducts in war on terror by Bush administration as a secret subject to defend national security has repeatedly invoked the state secrets privilege in cases challenging executive conduct in the war on terror, arguing that the very subject matter of these cases must be kept secret to protect national security and suggests courts not to dismiss these cases until assured by Congress for executive oversight, and Pozen (Citation2005) titled “The Mosaic Theory, National Security, and the Freedom of Information Act” presents the evolution of mosaic theory to control the information to restrict freedom of Information act in the aftermath of 9/11.
The fourth largest cluster in national security focuses on securitization and refers to Copenhagen school with 85 members. The highly frequent cited works are by Mcdonald, (2008) titled “Securitization and construct of security” presents the securitization agenda as a narrowly defined concept by just focusing on moment of intervention, Stritzel (Citation2007) titled “Towards a theory of securitization: Copenhagen and beyond” proposes an alternative framework for future research on securitization by criticizing the construct of this theory, and the book by Barry Buzan and Hansen (Citation2009) titled “The evolution of international security studies” and present the historical intellectual base of development of international security studies by comprising all authoritative debates on subject matter.
Last in the top five co-cited reference cluster comes the climate frontiers with 85 members. The most frequent co-cited articles in this cluster are by Godfray et al. (Citation2012) titled “Food Security: The Challenge of Feeding 9 Billion People” explore the complex relationship between population growth and demand for food consumption. The ongoing continuity in population and consumption growth will lead to food demand for the next 40 years, the report by (SecurityAndClimate) CNA corporation titled “National security and the threat of climate change”, and Schmidhuber and Tubiello (Citation2007) titled “Global food security under climate change” exploring the possible impact of climate change on food security by examining the availability, stability, utilization, and access elements of food security.
The national security debate turns to be divergent with 711 clusters and without any certain association between these clusters as the result of analysis indicates a high level of uncertainty. This makes it impossible to explain any linkage between the ongoing research in this field. Most of the clusters are observed to be far away from the center and even in the center, the distribution seems to be deviating indicating the widening understanding of national security concept making it more complex to explain any clear relationship among researchers.
3.4. Author co-citation analysis
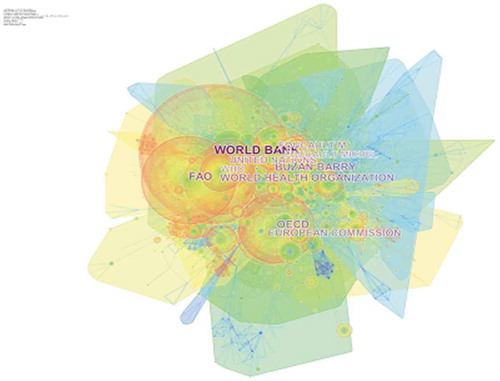
White and Griffith (Citation1981) presented author co-citation analysis for the first time as a convenient tool to identify “invisible college networks” by indicating the co-occurrence of individual work by other authors. The study applied this tool to identify interrelationship among different researchers and scholars within the study area of national security. The author co-citation analysis for national security, when running through CiteSpace, appears to have 224 nodes and 112 co-citation links. The size of the nodes represents the number of citations, the higher the number bigger the node. No author has found to create deep influence in the development of national security concept. The inner red circles present an increased citation of the author at a specific time. More interestingly the highly frequent co-cited authors appear to be international institutions reports. World Bank., (2002) development report on building institutions for markets, Barry Buzan and Wæver (Citation2003), and Food and Agriculture Organization., (Citation2002) “the state of food insecurity in the world” are most co-cited authors in national security (Figure ).
3.5. Journal co-citation analysis
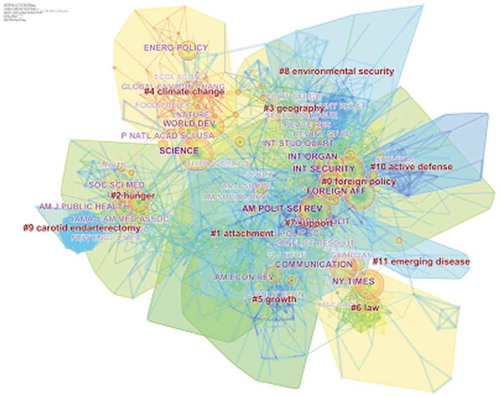
“Journal co-citation network analysis” reveals macrostructure of the given study field by identifying highly frequently cited journals. The analysis also provides the contribution of journals in the conceptual development of a given field of study (Li, Ma, & Qu, Citation2017). Journal co-citation analysis is an important quantitative tool to find similarities for examination of the development of the subject. The analysis for national security contains 817 nodes and 3489 links. The results show that American political science review, Science, International Security, Foreign affairs magazine, and International organization as top five journals with the highest frequency above 400. The top five journals cover areas on political science, ecology and climate, international and national security, international relations and international affairs, respectively. Among all journals, the Foreign affair is an American magazine but it has a great influence on its foreign policy and first-hand source of Samuel P. Huntington’ article “clash of civilizations” (Figure ).
3.6. Countries and institutions
Bibliometric analysis is incomplete until it indicates those countries and institutions that are influential and contributed to the evolution of the concept of national security. This analysis reveals top five co-cited authors from USA (2092), England (684), Australia (319), Canada (280), and Germany (172). US researchers, scholars, and writers are the most co-cited authors in the area of national security.
In USA, Ross (Citation2001) titled “Does Oil Hinder Democracy?” uses time-series 1971–1997 cross-national data of 113 states to show the relation between oil exporting countries have strong association with authoritarian rule, Bethell et al. (Citation2002) titled “Identifying children with special healthcare needs: Development and evaluation of a short screening instrument” develops an effective and flexible value based screening instrument which indicates children with special healthcare needs (CSHCN) across populations to show proportionate rate with other studies of CSHCN (Figure ).
Figure 6. Country co-citation analysis of the knowledge domain of “National Security” during the year 2000–2017
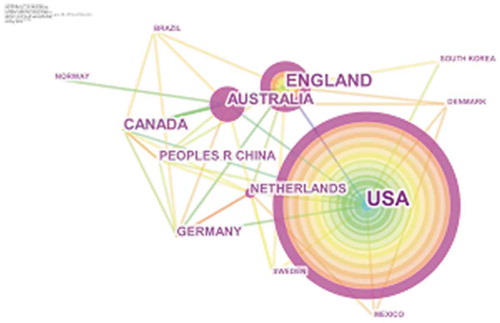
In England authors Turner (Citation2001) titled “The erosion of citizenship” argues that withdrawn of national citizenship have been enlarged by global rights like environmental, aboriginal, and cultural rights replacing social security with ontological security, Overland et al. (Citation2006) titled “A population-based cohort study of the effect of common mental disorders on disability pension awards” presents mental illness as the least recognized healthcare domain as a key factor in underestimating for social security awards.
In Australia, authors Andrews & Shabani, Citation2012) titled “Re-envisioning the role of hydrogen in a sustainable energy economy” suggests that hydrogen economy time has terminated with inclusion of electric batteries but it still has crucial role to play for range comparability to traditional fuels in every aspect of its usage, Mcculloch and Pickering (Citation2009) titled “Pre-crime and counter-terrorism: Imagining Future Crime in the ‘War on Terror’” presents pre-crime context of counter-terrorism by identifying the trials and breaks in criminology with a shift from post crime criminal justice to pre-crime national security.
In Canada, authors Lipp, (Citation2007) titled “Lessons for effective renewable electricity policy from Denmark, Germany and the United Kingdom” suggests effectiveness and policy design as key elements in renewable electricity development by using feed-in tariff (FIT) and the renewable portfolio standard (RPS), Stolle, Soroka, and Johnston (Citation2008) titled “When Does Diversity Erode Trust? Neighborhood Diversity, Interpersonal Trust and the Mediating Effect of Social Interactions” uses Citizenship, Involvement, Democracy’ (CID) survey in the US and the “Equality, Security and Community Survey” (ESCS) in Canada to show the effects of ethnic diversity on social cohesion.
In Germany, authors Bazilian et al. (Citation2011) titled “Considering the energy, water and food nexus: Towards an integrated modelling approach” describe energy, water, and food policy to have frequent intertwined anxieties like services access, environmental impacts, and price volatility, Khoury et al. (Citation2014) titled “Increasing homogeneity in global food supplies and the implications for food security” indicates changes in the indifferent national crops in food supply with their relevant importance around the globe in past 50 years.
Harvard University (88), University of California, Berkeley (52), Australian National University (49), Kings College London (41), and University of Toronto (40) appears to be the top five institutions in developing the conceptual construct of national security.
Harvard University has the strongest burst and present a turning point with highly co-cited articles by Perls et al. (Citation2002) titled “Life-long sustained mortality advantage of siblings of centenarians” present hypothesis that living to extreme old age encompasses a significant familial tendency of longevity by analyzing “pedigrees” of 444 centenarian families in the US by comparing 2092 centenarians siblings with 1900 “birth cohort survival data” from the US social security administration, Safran et al. (Citation2007) titled “Toward a National Framework for the Secondary Use of Health Data: An American Medical Informatics Association White Paper” provides a framework to protect healthcare data for legitimate secondary use as it implies personal healthcare information, not for healthcare delivery (Figure ).
Figure 7. Institution co-citation analysis of the knowledge domain of “National Security” during the year 2000–2017
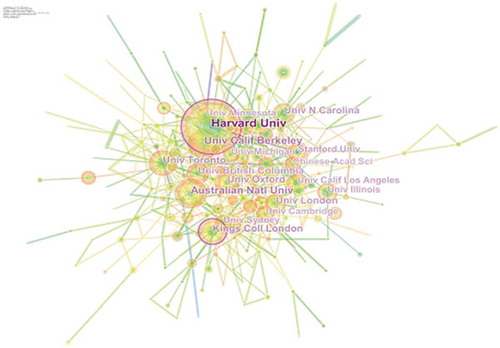
The other institution with the highest burst and turning point is Kings college London with highly co-cited articles Coid et al. (Citation2009) titled “Psychopathy among prisoners in England and Wales” analyzes a national representative sample of prisoners to measure the “prevalence of psychopathy” and the “distribution and correlates of psychopathic traits” and find that it is most prevalent in male prisoners, Meltzer et al. (Citation2010) titled “Job insecurity, socio-economic circumstances and depression” shows a strong relationship between job insecurity and depression even after controlling for biographic characteristics, economic factors, and job characteristics.
4. Discussion
The knowledge mapping through bibliometric analysis by using CiteSpace enables research to construct a clearer picture of intellectual development which goes beyond traditional citation count methodology. Results reveal that national security is still a developing concept as no conclusion appears in scholarly work. The findings suggest that some of the national security aspects like nutrition examination survey, food insecurity, borders, biopolitics, homeland security, and secrecy have received the greater attention of researchers and scholars than the other aspects, pointing out the dominance of non-traditional concepts of national security both in theoretical and methodological approaches.
The analysis suggests research on national security has mostly adopted the insight from widening agenda of securitization by focusing more on the human aspect of national security rather than militarization. Still unable to define national security context as pouring more knowledge domains and expanding it to an extent where it swallows more than it can digest. The article co-citation analysis in this study identified the intellectual construct and advanced ideas within the national security domain and indicated Seligman et al (Citation2007), Foucault (Citation2007), and Seligman et al. (Citation2007) as the most frequently co-cited scholarly works based on non-traditional security agenda. The need to refer non-traditional security concept here is meant to explain the construct of national security by incorporating political, economic, social, environmental, food, and cultural concepts.
The above results are consistent with the findings of cluster analysis which has suggested food insecurity, nutrition survey, borders, and biopolitics as the top areas which have received great attention from researchers in the field of national security. The bibliometric analysis did not find any intellectual turning point articles in co-citation. The intellectual turning point is important to unfold the intellectual structure and to indicate the transition in the concept of national security by detecting the paradigm shifts with the identification of channels which connect the ongoing research in different time periods.
Burst detection analysis is an alternative tool to diagnose the potential intellectual turning points. The articles with their burst terminated have seen the active contribution of scholars to diffuse their idea in the domain of national security in a specific time period. Barry Buzan et al. (Citation1998) with their scholarly work “Security: a new framework for analysis” has the burst in the years covered by this study in the field of national security. They have presented a constructive operational method to differentiate between politicization and securitization to comprehend who needs to securitize what under what conditions. The study accommodates the wider security agenda of economic, societal, and environmental security with traditional military and political security agenda. The sectors as an analytical method and securitization to make security issues as security issues. The multi-sectoral approach allows the propagation of securitization but constructive method provides ways to question and politicize the particular case. The conceptual development focuses on actors rather than features of threat. Whereas the Seligman et al. (2010) with his work on food insecurity and chronic diseases in adults still has an ongoing burst, indicating a potential paradigm shift and transition in the intellectual development of national security concept from other perspectives to this particular perspective of security.
5. Conclusion
The scienometric analysis helps to identify the evolution of national security concept in the new millennium. The cited references indicate the research fronts and direction of research by incorporating the available intellectual base of the subject. Still unable to identify clear linkages between clusters with available information on Science of the web, the study indicates various complexities in the concept of national security. The current findings are enough to say that the national security debates now focus on food insecurity, health, climate, and sustainability as main concerns. The study finds information security, cybersecurity, and security of networks as an area that is not attended by national security researches though important in any country’s security policy. The concept of national security as a political and policy agenda remains undefined if not distinguish clearly with sectoral, territorial, and institutional settings.
Additional information
Funding
Notes on contributors
Muhammad Azfar Anwar
Muhammad Azfar Anwar is the PhD Candidate at University of Science and Technology of China, having the Master’s degree in “Government and Public Policy”. His research evolves around the knowledge sphere of “National Security”. During his doctoral studies, he is emphasizing the “Food Security” and “Climate Change” as the major research area.
Zhou Rongting
Zhou Rongting is the Director of “Department of Science Communication & Popularization” in University of Science and Technology of China, and Executive Director of the Lifelong Learning Laboratory. His research work has been published in several internationally well recognize journals.
Wang Dong
Wang Dong is the PhD Candidate at University of Science and Technology of China, having the specialization in scientific visualization, bibliometrics, and scientometrics, and the sociology of science. Currently focusing the “Philosophy of Science and Technology” as major research area.
Fahad Asmi
Fahad Asmi is post-doctoral researcher at University of Science and Technology of China. His research area evolves around “Innovation, Science, and Society” for the sustainable eco-system.
References
- Alaimo, K., Olson, C. M., & Frongillo, E. A. (2001). Food insufficiency and american school-aged children’s cognitive, academic, and psychosocial development. Pediatrics, 108, 1.
- Amoore, L. (2006). Biometric borders: Governing mobilities in the war on terror. Political Geography, 25(3), 336–351. doi:10.1016/j.polgeo.2006.02.001
- Andrews, J., & Shabani, B. (2012). Re-envisioning the role of hydrogen in a sustainable energy economy. International Journal of Hydrogen Energy, 37(2), 1184–1203. doi:10.1016/j.ijhydene.2011.09.137
- Anwar, M. A., & Rafique, Z. (2012). Defense spending and national security of Pakistan: A policy perspective. Democracy and Security, 8(4), 374–399. doi:10.1080/17419166.2012.739551
- Ayoob, M. (1991). The Security Problematic of the Third World. World Politics, 43(2), 257–283. doi:10.2307/2010473
- Azar, E. E., & Moon, C. (1988). National security in the third world : The management of internal and external threats. Aldershot: Edward Elgar.
- Baldwin, D. A., & Baldwin, D. A. (1997). The concept of security *. Review of international studies, 19(1993), 5–26.
- Bazilian, M., Rogner, H., Howells, M., Hermann, S., Arent, D., Gielen, D., … Yumkella, K. K. (2011). Considering the energy, water and food nexus : Towards an integrated modelling approach. Energy Policy, 39(12), 7896–7906. doi:10.1016/j.enpol.2011.09.039
- Bethell, C. D., Read, D., Stein, R. E. K., Blumberg, S. J., Wells, N., & Newacheck, P. W. (2002). Identifying children with special health care needs: Development and evaluation of a short screening instrument. Ambulatory Pediatrics, 2(1), 38–48.
- Bettencourt, L. M. A., & Kaur, J. (2011). Evolution and structure of sustainability science. Proceedings of the National Academy of Sciences of the United States of America, 108(49), 19540–19545. doi:10.1073/pnas.1102712108
- Budd, J. M. (1988). A bibliometric analysis of higher education literature. Research in Higher Education, 28(2), 180–190.
- Buzan, B. (1991). New Patterns of Global Security in the twenty-frst century. International Affairs, 67(3), 431–451. doi:10.2307/2621945
- Buzan, B., & Hansen, L. (2009). The evolution of international security studies. Political science. doi:10.1017/CBO9780511817762
- Buzan, B., & Wæver, O. (2003). Regions and powers: The structure of international security. United States of America by Cambridge University Press, 190. doi:10.1017/CBO9781107415324.004
- Buzan, B., Wæver, O., & Wilde, J. D. (1998). Security : A new framework for analysis. Boulder, Colo: Lynne Rienner Pub.
- Chen, C. (2006). CiteSpace II : Detecting and visualizing emerging trends. Journal of the American Society for information Science and Technology, 57(3), 359–377. doi:10.1002/asi
- Chen, C., Hu, Z., Liu, S., & Tseng, H. (2012). Emerging trends in regenerative medicine: A scientometric analysis in CiteSpace. Expert Opinion on Biological Therapy, 12(5), 593–608. doi:10.1517/14712598.2012.674507
- Chen, C., & Ibekwe-Sanjuan, F. (2010). The structure and dynamics of cocitation clusters : A multiple-perspective cocitation analysis. Journal of the American Society for information Science and Technology, 61(7), 1386–1409. doi:10.1002/asi
- Chen, D., Liu, Z., Luo, Z., Webber, M., & Chen, J. (2016). Bibliometric and visualized analysis of emergy research. Ecological Engineering, 90, 285–293.
- Chen, J. (2007). Rapid urbanization in China: A real challenge to soil protection and food security. Catena, 69(1), 1–15. doi:10.1016/j.catena.2006.04.019
- Coid, J., Yang, M., Ullrich, S., Roberts, A., Moran, P., Bebbington, P., … Hare, R. (2009). International journal of law and psychiatry psychopathy among prisoners in England and Wales ☆. International Journal of Law and Psychiatry, 32(3), 134–141. doi:10.1016/j.ijlp.2009.02.008
- Elbe, S. (2006). Should HIV/AIDS be securitized? The ethical dilemmas of linking HIV/AIDS and security. International Studies Quaterly, 50(1), 119–144. doi:10.1111/j.1468-2478.2006.00395.x
- Erar, A. (2002). Bibliometrics or informetrics: Displaying regularity in scientific patterns by using statistical distributions. Hacettepe Journal of Mathematics and Statistics, 31, 113–125.
- Fairthrone, R. A. (1969). Empirical hyperbolic distributions (Bradford-Zipf-Mandelbrot) for bibliometric description and prediction. Journal of Documentation, 2(4), 319–343. doi:10.1108/eb026404
- Fearon, J. D., & Laitin, D. D. (2001). Ethnicity, insurgency, and civil war ∗. American political science review, (April 2000), 75–89. doi:10.1017/S0003055403000534
- Food and Agriculture Organization. (2002). The state of food insecurity in the world 2002 : Food insecurity : When people must live with hunger and fear starvation. Rome : Food and Agriculture Organization of the United Nations.
- Foucault, M. (2007). Security, territory, population : Lectures at the Collège de France, 1977-78. (Arnold I. Davidson & G. Burchell, Eds.). Palgrave Macmillan.
- Frost, A. (2007). The state secrets privilege and separation of powers. Fordham L. Rev., 75, 4.
- Godfray, H. C. J., Beddington, J. R., Crute, I. R., Haddad, L., Lawrence, D., Muir, J. F., & Toulmin, C. (2010). Food security: The challenge of feeding 9 billion people. Science, 327(5967), 812–818. Retreived from https://doi.org/10.1126/science.1185383
- Godfray, H. C. J., Beddington, J. R., Crute, I. R., Haddad, L., Lawrence, D., Muir, J. F., & Toulmin, C. (2010). Food security: The challenge of feeding 9 billion people. Science, 327(5967), 812–818.
- Godfray, H. C. J., Beddington, J. R., Crute, I. R., Haddad, L., Lawrence, D., Muir, J. F., … Toulmin, C. (2012). The challenge of food security. Science, 327(February), 812. doi:10.4337/9780857939388
- Greenwald, G. (2013). XKeyscore: NSA tool collects “nearly everything a user does on the internet” US news | The Guardian. Retrieved from https://www.theguardian.com/world/2013/jul/31/nsa-top-secret-program-online-data
- Gu, D., Li, J., Li, X., & Liang, C. (2017). Visualizing the knowledge structure and evolution of big data research in healthcare informatics. International Journal of Medical Informatics, 98, 22–32. Retreived from https://doi.org/10.1016/j.ijmedinf.2016.11.006
- Hansen, L. (2000). The little mermaid’s silent security dilemma and the absence of gender in the copenhagen school. Millennium - Journal of International Studies, 29(2), 285–306. doi:10.1177/03058298000290020501
- Harvey, D. (2005).The new imperialism. Oxford: Oxford University Press.
- Hillyard, P. (1993). Suspect community : People’s experience of the prevention of terrorism acts in Britain. Pluto Press.
- Katzenstein, P. J. (1996). The culture of national security: Norms and identity in world politics. Columbia University Press.
- Khoury, C. K., Bjorkman, A. D., Dempewolf, H., Ramirez-Villegas, J., Guarino, L., Jarvis, A., … Struik, P. C. (2014). Increasing homogeneity in global food supplies and the implications for food security. Proceedings of the National Academy of Sciences, 111(11), 4001–4006. doi:10.1073/pnas.1313490111
- Kirkpatrick, S. I., & Tarasuk, V. (2008). Food insecurity is associated with nutrient inadequacies among canadian adults and adolescents. The Journal of Nutrition, 138(3), 604–612.
- Kruyt, B., van Vuuren, D. P., de Vries, H. J. M., & Groenenberg, H. (2009). Indicators for energy security. Energy Policy, 37(6), 2166–2181. doi:10.1016/j.enpol.2009.02.006
- Lasswell, H. D. (1936). Politics who gets what, when, how. McGraw Hill. Retrieved from http://www.policysciences.org/classics/politics.pdf
- Li, K., Gao, P., Xiang, P., Zhang, X., Cui, X., & Ma, L. Q. (2016). Molecular mechanisms of PFOA-induced toxicity in animals and humans: Implications for health risks. Environment International. Retreived from https://doi.org/10.1016/j.envint.2016.11.014
- Li, X., Ma, E., & Qu, H. (2017). Knowledge mapping of hospitality research ? A visual analysis using CiteSpace. International Journal of Hospitality Management, 60, 77–93. doi:10.1016/j.ijhm.2016.10.006
- Lipp, J. (2007). Lessons for effective renewable electricity policy from denmark, germany and the united kingdom. Energy Policy, 35(11), 5481–5495. doi:10.1016/J.ENPOL.2007.05.015
- Lippmann, W. (1943). U.S. foreign policy: Shield of the republic. Walter Lippmann: Amazon.com: Books. Little, Brown & Company.
- Liu, Z., Yin, Y., Liu, W., & Dunford, M. (2015). Visualizing the intellectual structure and evolution of innovation systems research: A bibliometric analysis. Scientometrics, 103(1), 135–158. doi:10.1007/s11192-014-1517-y
- Lobell, D. B., Burke, M. B., Tebaldi, C., Mastrandrea, M. D., Falcon, W. P., & Naylor, R. L. (2008). Prioritizing climate change adaptation needs for food security in 2030. Science (New York, N.Y.), 319(5863), 607–610. doi:10.1126/science.1152339
- Mcculloch, J., & Pickering, S. (2009). Pre-crime and counter-terrorism imagining future crime in the “ War on terror. The British Journal of Criminology, (May), 628–645. doi:10.1093/bjc/azp023
- Mcdonald, M. (2008). Securitization and the construction of security. European journal of international relations, 14(4), 563–587. doi:10.1177/1354066108097553
- Meltzer, H., Bebbington, P., Brugha, T., Jenkins, R., Mcmanus, S., & Stansfeld, S. (2010). Job insecurity. Socio-Economic Circumstances and Depression, 1401–1407. doi:10.1017/S0033291709991802
- Morris, T., & Morris, T. (2012). Police practice and research : An achieving national security : Comparing four state security models Achieving national security : Comparing four state security models. Police Practice and Research, (December 2014), 37–41. doi:10.1080/15614263.2011.596689
- Overland, S., Dahl, A. A., Ph, D., Krokstad, S., Ph, D., Bjerkeset, O., … Psych, M. R. C. (2006). A population-based cohort study of the effect of common mental disorders on disability pension awards. American journal of Psychiatry, (August), 1412–1418.
- Paleri, P. (2008). National security : Imperatives and challenges. New Delhi: Tata McGraw-Hill Pub. Co.
- Pantazis, C., & Pemberton, S. (2009). From the “ old ” to the “ new ” suspect community examining the impacts of recent UK counter-terrorist legislation. British Journal of Criminology, 646–666. doi:10.1093/bjc/azp031
- Pao, M. L. (1985). Lotka’s law: A testing procedure. Information Processing and Management, 21(4), 305–320. doi:10.1016/0306-4573(85)90055-X
- Perls, T. T., Wilmoth, J., Levenson, R., Drinkwater, M., Cohen, M., Bogan, H., … Puca, A. (2002). Life-long sustained mortality advantage of siblings of centenarians, (Track II).
- Piantadosi, S. T. (2014). Zipf’s word frequency law in natural language: A critical review and future directions. Psychonomic Bulletin\& Review, 21(5), 1112–1130. doi:10.3758/s13423-014-0585-6
- Pozen, D. E. (2005). The Mosaic theory, national security, and the freedom of information act. Yale Law Journal, 628–679.
- Romm, J. J. (1993). Defining national security : The nonmilitary aspects. Council on Foreign Relations Press.
- Ross, M. L. (2001). Does oil hinder democracy? World politics, 53(3), 325–361. doi:10.1353/wp.2001.0011
- Rudel, T. K., Schneider, L., Uriarte, M., Turner, B. L., Defries, R. S., Lawrence, D., … Grau, R. (2009). Agricultural intensification and changes in cultivated areas, 1970-2005. Proceedings of the National Academy of Sciences of the United States of America, 106(49), 20675–20680. doi:10.1073/pnas.0812540106
- Safran, C., Bloomrosen, M., Hammond, W. E., Labkoff, S., Markel-Fox, S., & Tang, P. C. (2007). Toward a national framework for the secondary use of health data: An American Medical Informatics Association White Paper. Journal of the American Medical Informatics Association : JAMIA, 14(1),1–9. Retreived from https://doi.org/10.1197/jamia.M2273
- Schmidhuber, J., & Tubiello, F. N. (2007). Global food security under climate change. Proceedings of the National Academy of Sciences of the United States of America, 104(50), 19703–19708. doi:10.1073/pnas.0701976104
- Seligman, H. K., Bindman, A. B., Vittinghoff, E., Kanaya, A. M., & Kushel, M. B. (2007). Food insecurity is associated with diabetes mellitus: Results from the National Health Examination and Nutrition Examination Survey (NHANES) 1999-2002. Journal of General Internal Medicine, 22(7), 1018–1023. doi:10.1007/s11606-007-0192-6
- Seligman, H. K., Bindman, A. B., Vittinghoff, E., Kanaya, A. M., & Kushel, M. B. (2007). Food insecurity is associated with diabetes mellitus: Results from the national health examination and nutrition examination survey (nhanes) 1999-2002. Journal of General Internal Medicine, 22(7), 1018–23. doi:10.1007/s11606-007-0192-6
- Seligman, H. K., Laraia, B. A., & Kushel, M. B. (2009). Food insecurity is associated with chronic disease among low-income. The Journal of Nutrition\, 140, 304–310. doi:10.3945/jn.109.112573.number
- Seyedghorban, Z., Matanda, M. J., & LaPlaca, P. (2016). Advancing theory and knowledge in the business-to-business branding literature. Journal of Business Research, 69(8), 2664–2677. doi:10.1016/j.jbusres.2015.11.002
- Shiau, C. S. N., Samaras, C., Hauffe, R., & Michalek, J. J. (2009). Impact of battery weight and charging patterns on the economic and environmental benefits of plug-in hybrid vehicles. Energy Policy, 37(7), 2653–2663. doi:10.1016/j.enpol.2009.02.040
- Shiau, W.-L. (2015). The intellectual core of enterprise information systems: A co-citation analysis. Enterprise Information Systems, 7575(March), 1–30. doi:10.1080/17517575.2015.1019570
- Smith, S. (1999). The increasing insecurity of security studies: Conceptualizing security in the last twenty years. Contemporary Security Policy, 20(3), 72–101.
- Sparke, M. B. (2006). A neoliberal nexus: Economy, security and the biopolitics of citizenship on the border. Political Geography, 25(2), 151–180. doi:10.1016/j.polgeo.2005.10.002
- Stolle, D., Soroka, S., & Johnston, R. (2008). When does diversity erode trust? Neighborhood diversity, interpersonal trust and the mediating effect of social interactions. Political Studies, 56(1), 57–75. doi:10.1111/j.1467-9248.2007.00717.x
- Stone, M. (2009). Security according to Buzan: A comprehensive security analysis. Security Discussion Papers. Series 1 edn. Grouped’ Etudesetd’ Expertise “Sécuritéet Technologies” GEEST-2009. New York
- Stritzel, H. (2007). Towards a theory of securitization: Copenhagen and Beyond. European Journal of International Relations, 13(3), 357–383. doi:10.1177/1354066107080128
- Topalli, M., & Ivanaj, S. (2016). Mapping the evolution of the impact of economic transition on Central and Eastern European enterprises: A co-word analysis. Journal of World Business, 51(5), 744–759. doi:10.1016/j.jwb.2016.06.003
- Turner, B. S. (2001). The erosion of citizenship. British Journal of Sociology, 2(52), 189–209. doi:10.1080/00071310120044944
- Wæver, O. (1993). Securitization and desecuritization. Copenhagen: Centre for Peace and Conflict Research.
- Wang, Y., Lai, N., Zuo, J., Chen, G., & Du, H. (2016). Characteristics and trends of research on waste-to-energy incineration: A bibliometric analysis, 1999–2015. Renewable and Sustainable Energy Reviews, 66, 95–104. doi:10.1016/j.rser.2016.07.006
- Waxman, M. C. (2012). National security federalism in the age of terror | stanford law review. Stanford Law Review, 64, 2.
- Web of Science. (2016). The citaton connection - real facts - ip & science - thomson reuters.United Kingdom : Clarivate Analytics
- White, H. D., & Griffith, B. C. (1981). Author cocitation: A literature measure of intellectual structure. Journal of the American Society for Information Science, 32(3), 163–171. doi:10.1002/asi.4630320302
- Wolfers, A. (1952). National security as an ambiguous symbol. Political Science Quarterly, 67(4), 481.
- Yang, H., & Li, X. (2000). Cultivated land and food supply in China. Land Use Policy, 17(2), 73–88. doi:10.1016/S0264-8377(00)00008-9