Figures & data
Table 1. Results of the uncertainty analysis
Table 2. Results of the NIST
Table 3. Correlation coefficients between original “Lena” image and permutated “Lena” image
Table 4. Correlation results of adjacent pixels
Table 5. Correlation results of different encryption key generated with a very small difference in all system parameters
Figure 6. Results of the proposed encryption algorithm (a) Plain Baboon image (b) Encrypted Baboon image (c) Decrypted Baboon image
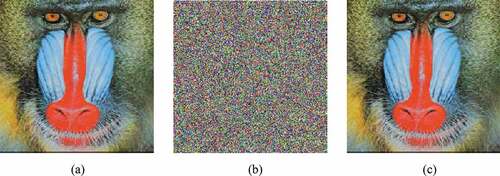
Figure 7. Results of the encryption (a) “Peppers” image (b) “Landscape” image (c) “Airplane” image (d) Cipher “Peppers” image (e) Cipher “Landscape” image (f) Cipher “Airplane” image
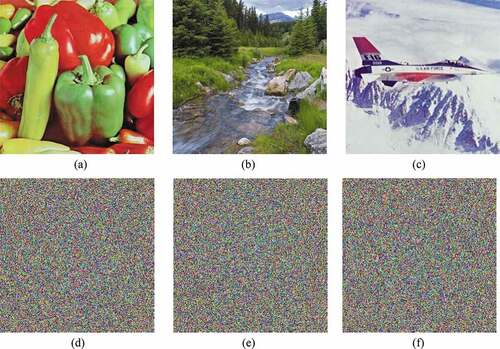
Table 6. Results for key sensitivity analysis-I
Figure 8. Results for key sensitivity analysis-II (a) Encrypted Baboon image with Key-1 (b) Wrong decrypted image with a slightly difference of (c) Wrong decrypted image with a slightly difference of
(d) Wrong decrypted image with a slightly difference of
(e) Wrong decrypted image with a slightly difference of
(f) Correct decrypted image with Key-1.
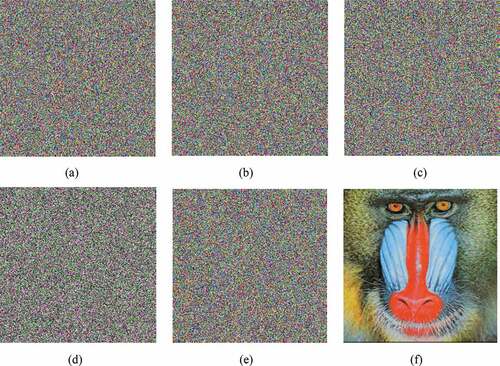
Table 7. Results for MSE and PSNR analyses
Table 8. Results for entropy analysis
Table 9. Entropy comparison between AES and the proposed algorithm
Table 10. Entropy comparison between Reference-C and the proposed algorithm
Table 11. Correlation coefficients analysis
Table 12. Correlation coefficients of adjacent pixels in cipher image
Table 13. NPCR and UACI results for the proposed algorithm
Table 14. NPCR and UACI results for the proposed algorithm
Table 15. NPCR and UACI results for Reference-C
Table 16. NPCR and UACI results for the proposed scheme
Table 17. Speed performance analysis of the proposed scheme