Abstract
Ostracism, the act of ignoring and excluding, is a universally applied tactic of social control. Individuals who detect ostracism often change their behaviors to be readmitted into the group, even if it means becoming excessively socially susceptible to influence. We tested whether ostracized individuals are more socially susceptible to a subsequent influence attempt. In this study, 65 undergraduates were randomly assigned to a 2 (Inclusion or Ostracism)×3 (Compliance tactic: foot‐in‐the door, target request only, door‐in‐the‐face) between‐participants design. The participants played Cyberball and were either included or ostracized, and then they were approached with a request to donate money. Despite no differences between the three tactics, ostracism increased compliance across all request types. Our discussion focuses on the implications for ostracism‐induced social susceptibility.
This material is based on work supported by the National Science Foundation under Grant No. 0519209 awarded to the third author. We would like to thank Janice Kelly for her comments, and Jessica Bartman, Katherine Lang, Patrick O'Brien, Vista Ritchie, and Kirsten Zeiser for their excellent acting skills as confederates.
Social scientists have become increasingly interested in the impact of ostracism, social exclusion, and rejection (Williams, Citation2001, Citation2007; Williams, Forgas, & von Hippel, Citation2005). Ostracism, defined here as being excluded and ignored, has a powerful immediate effect on individuals. Within even a brief episode of a minimal ostracism experience, individuals report distress, anger, sadness, and lower levels of belonging, self‐esteem, control, and meaningful existence (Williams, Cheung, & Choi, Citation2000b; Zadro, Williams, & Richardson, Citation2004). In a neuroimaging study, it was found that ostracized individuals showed significant increased activation of the dorsal anterior cingulate (dACC), the same region that is activated when experiencing physical pain (Eisenberger, Lieberman, & Williams, Citation2003). This activation occurred even when participants initially expected not to be included, and their self‐reported levels of distress were highly correlated with their dACC activation.
This immediate reaction appears to be reflexive; that is, it does not seem to be moderated by cognitive intervention. Thus, studies have demonstrated that the distress is just as devastating when the ostracism is attributed to the computer than to other humans (Zadro et al., Citation2004), when it is not known if the others are interacting with each other (Smith & Williams, Citation2004), if ostracized by ingroup, outgroup, or even despised outgroup members (Gonsalkorale & Williams, Citation2007; Williams, Bernieri, Faulkner, Grahe, & Gada‐Jain, 2000a), or if, by being ostracized, one is monetarily better off than if one had been included (van Beest & Williams, Citation2006).
Our research question focuses on the next stage of reactions; how the ostracized individual copes with his or her distress and threatened needs. According to Williams (Citation2001; Williams & Zadro, Citation2005), the next stage occurs after the ostracized individual has time to reflect on, and appraise, the ostracism experience. At this point, presumably, ostracism by a computer, a despised outgroup, or when the others were unable to include the individual will result in a relatively quicker recovery than when, say, ingroup members ostracize intentionally. Williams posits that the primary aim of coping responses is to fortify the need or needs that are thwarted by the ostracism experience. For instance, individuals who seek control or a desire to be recognized as a result of ostracism can exert control over other individuals, or force others to notice perhaps even by being anti‐social or aggressive (Twenge, Baumeister, Tice, & Stucke, Citation2001; Williams et al., Citation2000a). For example, the “Bind, Torture, Kill” serial killer (BTK) (King, Citation2005) wrote to the press, regarding his unresolved killing spree, “How many do I have to kill, before I get my name in the paper or some national attention?” This quote from the BTK killer exemplifies an extreme desire for control and recognition, without regard for positive regard.
A desire for more belonging and/or self‐esteem are best fortified by behaving in ways that are more appealing to others, such as working hard on a collective task (Williams & Sommer, Citation1997), attending carefully to information about others in your group (Pickett, Gardner, & Knowles, Citation2004), mimicking others' behaviors (Lakin & Chartrand, Citation2005; Ouwerkerk, Kerr, Galucci, & van Lange, Citation2005), or conforming to an incorrect but unanimous majority (Williams et al., 2000b). Our concern, however, is that these appeasing responses may not be entirely beneficial to ostracized individuals, and instead might render them easy prey for compliance professionals, such as telemarketers and salespeople. Even worse, ostracized individuals may be more susceptible to con‐artists, sexual predators, and cult recruiters. As a first step toward exploring this idea, in the present study we ask whether ostracized individuals are more likely to comply with a stranger's request to donate money.
The goal of this research is to determine if individuals who are ostracized are more socially susceptible to influence attempts. Are ostracized individuals, in the service of trying to be more attractive to others, more likely to fall prey to direct requests, as well as to compliance tactics, such as foot‐in–the‐door technique (Freedman & Fraser, Citation1966) or the door‐in‐the‐face technique (also called reciprocal concession; Cialdini et al., Citation1975). The foot‐in‐the‐door requires only that an initial small request is made and granted, and is then followed by a larger request (the target request, for which compliance would be the actual goal of the tactic). The door‐in‐the‐face technique is basically the opposite approach: start with a very large request that will not be granted, and then ask for the smaller (target) request (Cialdini, Citation2001). We chose these compliance tactics because they are well‐known, oft‐cited compliance strategies that ironically use opposing procedures, thus allowing us to test for the robustness of our ostracism → compliance predictions. We considered that to the extent increased susceptibility was primarily the result of an extrinsic motivation to be liked by another person, perhaps the door‐in‐the‐face technique might produce larger effects, as it operates under a desire to fulfill an implied social contract of reciprocity. To the extent that the foot‐in‐the‐door technique results from a desire to be consistent (a more intrinsic motivation), then perhaps the compliance increase would be less pronounced. However, our main focus was on whether, following ostracism, there is general increase in compliance.
Our aim was to determine if ostracism increased social susceptibility in the form of compliance, and also to test the generalizability of the effect, if it did occur, across a variety of compliance tactics. Thus in this study we tested post‐ostracism susceptibility to (1) a direct request, (2) the foot‐in‐the‐door technique, and (3) the door‐in‐the‐face technique. Based on previous research findings we expect a main effect of ostracism, such that any request for donations, regardless of the tactic employed, would result in increased compliance. This should occur because the impact of ostracism quite often overpowers the impact of other crosscutting factors and because, in all cases, the participant can regain a sense of belonging, control, self‐esteem, and meaningful existence by complying with the confederate's request.
The paradigm used to manipulate ostracism was Cyberball, a virtual ball‐toss game conducted over a computer (Williams et al., 2000b; Williams & Jarvis, Citation2006). Cyberball has been used in several published studies (Eisenberger et al., Citation2003; Gonsalkorale & Williams, Citation2007; Williams et al., 2000; van Beest & Williams, Citation2006b; Zadro, Boland, & Richardson, Citation2006; Zadro et al., Citation2004). In the first phase of the study participants play a virtual ball‐toss game on the computer with two other players (who are actually computer generated and controlled). Included participants receive the ball as many times as the other participants; ostracized participants only get the ball thrown to them a few times at the beginning, and never again. After they have finished playing Cyberball, participants are led to a new laboratory room and are seated next to another participant (a confederate) who is also waiting. Participants are told that this other participant had not played in their Cyberball game. The confederate uses one of three randomized and scripted compliance tactics to solicit donations for the University Marching Band. We tested whether ostracized individuals donated more money to the University Marching Band than did included individuals.
METHOD
Participants and design
As partial fulfillment of their introductory psychology requirements, 65 Purdue University undergraduates participated in a study advertised as examining the effects of mental visualization. Because of a computer‐programming oversight, a portion of the demographic information, specifying sex, age, and race, was not collected. From the retrieved demographic data, the participant pool was representative of the university's student population, 12 men and 13 women, M age 19.80, 84% Caucasian/White. The participants were randomly assigned to a 2 (Cyberball experience: inclusion or ostracism)×3 (Type of request: foot‐in‐the‐door, target request only, door‐in‐the‐face) between‐participants design. The students received partial course credit in exchange for their participation. Five participants indicated vague levels of suspicion, but were retained because they did not guess the hypothesis and their exclusion did not affect the results.
Procedure
Each participant was taken to the lab and seated at a computer. The experimenter explained that she was interested in the effects of mental visualization on a subsequent task. To begin, participants completed assessment questions using Medialab software (Jarvis, Citation2002). In the next phase of the experiment the participants were told that, to warm up their mental visualization abilities, they would be playing a computer game with other participants. The computer game, Cyberball, instructed them to not worry about the actual game itself, but to use it as a means to engage their mental visualization abilities. They were asked to imagine what the other players looked like, to imagine the setting, the weather, etc. These are the standard instruction for Cyberball, and the mental visualization cover story is emphasized so that it cannot be viewed as a task at which one can succeed or fail (Williams et al., 2000b; Williams & Jarvis, Citation2006).
The Cyberball game depicted three players on a computer screen, of which two were positioned to the left and right of an animated hand that represented the participant, placed in the 6 o'clock position. Although the participant was led to believe that there were two other actual players, in fact the other two players were computer generated and pre‐programmed. The game was programmed for 30 total throws and lasted approximately 5 minutes. When participants received the ball they were instructed to choose, by clicking one of the other players with their mouse, the player to whom they wished to throw the ball, and the game continued in this fashion until the designated number of throws was completed.
Cyberball experience
Included participants received the ball on approximately one‐third of the throws. Ostracized participants received two throws at the beginning of the game, after which the two other players threw the ball exclusively between themselves.
Self‐reports following Cyberball
After the Cyberball game ended, participants were asked a series of questions on the computer. Using a 5‐point scale (from 1 = not at all, to 5 = extremely) adapted from the questions used by Zadro et al. (Citation2004), the questions asked about the participant's feelings of belonging, self‐esteem, control, and meaningful existence they experienced during the game. They were asked three questions that assessed the success of the inclusion/ostracism manipulation: their feelings of exclusion, being ignored, and their guess of the percentage of throws that they received. In addition, participants were asked several questions on their mood, including items such as happy, sad, angry, and pleasant.
Compliance request
For the second phase of the experiment, participants were led to a waiting room. Already seated in the waiting area was a confederate who was ostensibly waiting to begin another study. Once the participant was seated, the researcher left the waiting area and stated that she would return shortly. The confederate wore a Purdue University Marching Band t‐shirt and recited a memorized script, saying that he/she was in the Purdue Marching Band, and proceeded to employ (based on random assignment) one of the three requests.
For the target‐request only condition, the confederate said, “I'm getting pledges from students for donations. Would you be willing to fill out this pledge card and donate something to the band?”
For the foot‐in‐the‐door condition, the confederate made a small request first, followed by the target question. All participants agreed to the small initial request. Specifically, the confederate said, “Hi, I'm in the band, and I'm getting pledges from students for donations. Can I ask you a few short questions? [yes]. Have you ever heard the band play? [yes/no] Do you know anybody who is in the band? [yes/no].” Then the confederate asked the same target request as in the first condition.
For the door‐in‐the‐face condition, the confederate made a large request first, followed by the target question. None of the participants agreed to the large request. In this condition the confederate said, “Hi, I'm in the band, and I'm getting pledges from students for donations. Would you be willing to donate $100 to the band? [yes/no].” Then the confederate asked the same target request as in the first condition. “Okay, well would you be willing to fill out this pledge card and donate something to the band?”
For all three conditions, once the donation request was made, the confederate offered the participant a pledge card and pointed to the line on the pledge card with a dollar sign ($) followed by a blank line on which the participant was to make his or her pledge (including, the confederate said, writing “$0” to indicate no pledge).
After 5 minutes had passed, the researcher returned to the waiting room and asked the confederate to follow her out of the room. As the confederate was leaving the waiting area, the researcher handed the participant a post‐experimental questionnaire, paper, and pen, and asked that it be completed. The post‐experimental questionnaire was administered to collect responses of suspicion (e.g., “What do you think this experiment is about?”) and manipulation checks for the donation request (they were to check one of four descriptions that best represented what occurred). When the researcher returned to the waiting room the post‐experimental questionnaire was collected and then the participants were fully debriefed and dismissed.
RESULTS
Manipulation checks
Inclusion/ostracism manipulation
The first two manipulation check questions on ostracism were highly correlated (r = .96, p<.0001), and were thus combined to indicate the extent to which participants felt ignored and excluded. Ostracized participants reported feeling more ignored and excluded (M = 4.67, SD = .57) than did included participants (M = 1.72, SD = 1.07), t(63) = 13.86, p<.0001, d = 3.43. Also, included participants reported receiving a higher percentage of ball tosses (M = 34.56, SD = 9.83) than did ostracized participants (M = 9.40, SD = 4.88), t(63) = 13.14, p<.0001, d = 3.24.
Compliance condition manipulation
Our attempt to assess the compliance condition manipulation was less clear. We tried to ask questions that would indicate whether participants were asked simply for a donation (target request only), or only after a small initial request (foot‐in‐the‐door), or only after a large initial request (door‐in‐the‐face). However, the ability of participants to realize that answering a few small questions constituted our definition of small request seems, in retrospect, doubtful. Therefore, only 66% of the participants correctly identified the donation request condition. The other 34% were all in either foot‐in‐the‐door or the door‐in‐the‐face condition, but most simply said they were asked to donate money (our check for target request only). Analyses with and without the correct choice had no effect on the pattern of results, so we kept all participants in the analysis and interpreted these data as the result of a vaguely worded manipulation check.
Social needs and mood following Cyberball
Because the questions related to the four needs were highly intercorrelated (α = .93), we combined participants' responses to these questions to form a need–threat index. We reversed the score so that higher scores indicate more threat. Ostracized participants (M = 3.91, SD = .58) reported more threat than did included participants (M = 2.30, SD = .53), t(63) = 12.20, p<.0001, d = 3.04. Also, ostracized participants reported less positive mood (M = 2.92, SD = .48) than did included participants (M = 3.55, SD = .35), t(63) = 6.07, p<.0001, d = −1.50. Thus we replicated earlier studies that showed Cyberball‐induced ostracism threatened the four needs and increased negative affect.
Donations
The amount of money participants were willing to donate
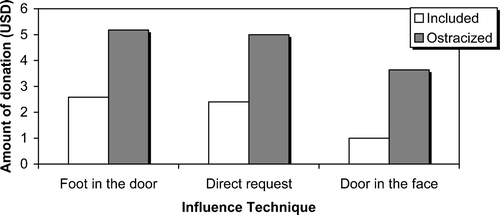
The amount of money participants were willing to donate was examined with a 2 (Cyberball experience)×3 (type of request) between‐participant ANOVA. As shown in Figure , there was a main effect for Cyberball experience such that ostracized participants were willing to donate more money than included participants, F(1, 59) = 6.50, p = .013, η 2 = .097. There was no effect for type of request, nor was there an interaction between the two factors.
Number of participants willing to donate any money
We conducted a logistic regression analysis to examine whether condition affected whether participants donated something (n = 30) or nothing (n = 35). Although not reaching standard levels for significance, there was a trend for more ostracized (58%) participants to give some money compared to included (32%) participants, B = 2.02, Wald statistic = 2.75, p<.10. The main effect of the type of request was not significant; nor was the interaction.
DISCUSSION
This study tested how ostracism might affect people's susceptibility to a persuasive attempt and whether these effects could be generalized to different techniques. We found that people became more susceptible to a persuasive attempt after being ostracized compared with after being included. This is consistent with early findings that following ostracism individuals would behave in ways that are more appealing to others to fortify their threatened social needs (Pickett et al., 2004; Lakin & Chartrand, Citation2005; William & Sommer, Citation1997). The major difference between this study and earlier studies is that the appealing response (to donate money) in this study has obvious cost to ostracized individuals. This suggests that following ostracism people would be more willing to comply with the persuasive attempts by compliance professionals, from the innocuous telemarketer to the unscrupulous con‐artist.
In this study we also found that the effect of ostracism on people's susceptibility to persuasive attempts could be generalized to other persuasive techniques. Participants became more persuaded by the foot‐in‐the‐door and the door‐in‐the‐face techniques after being ostracized compared to after being included. Further, neither the door‐in‐the‐face nor the foot‐in‐the‐door technique was more effective than the request‐only condition. Although surprising, a meta‐analysis showed that 21% of studies (out of 28) examining FITD found no effect or an opposite effect, and 25% (out of 18) studies investigating DITF found no effect or an opposite effect (Dillard, Hunter, & Burgoon, Citation1984). Perhaps the DITF technique led to slightly smaller donations because the first request for a $100 donation was considered extreme by the participants. According to Cialdini (Citation2001) the DITF tactic backfires if the first request is deemed unreasonable. Nevertheless, our primary aim was to determine whether compliance increased after ostracism, which it did, regardless of the compliance technique used.
Many studies have demonstrated anti‐social reactions to ostracism and social exclusion and these responses seem to occur mostly when re‐inclusion in the group (or another group) is impossible or improbable (Maner, DeWall, Baumeister, & Schaller, Citation2007; Williams, Citation2007). When there is an opportunity for re‐inclusion, or when inclusion in other groups seems likely, then it appears that ostracized individuals attempt to perceive, think, or behave in ways that facilitate their re‐inclusion. We refer to responses with this aim as socially appeasing. Social appeasement includes social attentiveness, higher levels of collective effort, more cooperation and less free‐riding, conformity, and mimicry (for a review, see Williams, Citation2007; Williams & Zadro, Citation2005). Many of these social appeasement behaviors, however, are not necessarily safe or functional. In the case of being excessively socially susceptible, it could mean forgoing one's internal guidelines and beliefs, and becoming more pliable and less principled. Future research might investigate whether individuals who are ostracized are more socially susceptible to different types of compliance tactics that involve other psychological processes. For instance, to fortify the need of control, ostracized individuals may be more responsive to scarcity compliance techniques that appear to restrict their control. Moreover, to fortify belonging, ostracized individuals may be more responsive to compliance techniques that involve a desire to be liked (e.g., similarity ploys, etc.).
This study represents an initial investigation into how ostracism can cause increased social susceptibility, in this case in the form of compliance, Additional research is needed to determine the boundary conditions for ostracism‐induced social susceptibility, and to what extent extreme examples of susceptibility, like joining cults or terrorist groups, can be attributed to need fortification following a sense of being ostracized by close others, or even by society in general.
Notes
This material is based on work supported by the National Science Foundation under Grant No. 0519209 awarded to the third author. We would like to thank Janice Kelly for her comments, and Jessica Bartman, Katherine Lang, Patrick O'Brien, Vista Ritchie, and Kirsten Zeiser for their excellent acting skills as confederates.
REFERENCES
- Cialdini , R. B. 2001 . Influence: Science and practice (4th ed.) , Boston : Allyn & Bacon .
- Cialdini , R. B. , Vincent , J. E. , Lewis , S. K. , Catalan , J. , Wheeler , D. and Darby , B. L. 1975 . Reciprocal concessions procedure for inducing compliance: The door‐in‐the‐face technique. . Journal of Personality and Social Psychology , 31 : 206 – 215 .
- Dillard , J. P. , Hunter , J. E. and Burgoon , M. 1984 . Sequential‐request persuasive strategies: Meta‐analysis of foot‐in‐the‐door and door‐in‐the‐face. . Human Communication Research , 10 : 461 – 488 .
- Eisenberger , N. I. , Lieberman , M. D. and Williams , K. D. 2003 . Does rejection hurt? An fMRI study of social exclusion. . Science , 302 : 290 – 292 .
- Freedman , J. L. and Fraser , S. C. 1966 . Compliance without pressure: The foot‐in‐the door technique. . Journal of Personality and Social Psychology , 4 : 195 – 203 .
- Gonsalkorale , K. and Williams , K. D. 2007 . The KKK won't let me play: Ostracism even by a despised outgroup hurts. . European Journal of Social Psychology , 37 : 1176 – 1186 .
- Jarvis , W. B. G. 2002 . Medialab (Version 2002) [computer software] , New York : Empirisoft .
- Kenny , D. A. and Nasby , W. 1980 . Splitting the reciprocity correlation. . Journal of Personality and Social Psychology , 38 : 249 – 256 .
- King , L. 2005, February 18 . Analysis of BTK killer developments. CNN Larry King Live Transcripts Retrieved August 28, 2006, from http://transcripts.cnn.com/TRANSCRIPTS/0502/18/lkl.01.html
- Lakin , J. L. and Chartrand , T. L. 2005 . “ Exclusion and nonconscious behavioral mimicry. ” . In The social outcast: Ostracism, social exclusion, rejection, and bullying , Edited by: Williams , Forgas , J. P and von Hippel , W . 279 – 295 . Hillsdale, NJ : Psychology Press .
- Maner , J. K. , DeWall , C. N. , Baumeister , R. F. and Schaller , M. 2007 . Does social exclusion motivate interpersonal reconnection? Resolving the “Porcupine Problem.” . Journal of Personality and Social Psychology , 92 : 42 – 55 .
- Ouwerkerk , J. W. , Kerr , N. L. , Gallucci , M. and Van Lange , P. A. M. 2005 . “ Avoiding the social death penalty: Ostracism and cooperation in social dilemmas. ” . In The social outcast: Ostracism, social exclusion, rejection, and bullying , Edited by: Williams , K. D , Forgas , J. P and von Hippel , W . 322 – 332 . Hillsdale, NJ : Psychology Press .
- Pickett , C. L. , Gardner , W. L. and Knowles , M. 2004 . Getting a cue: The need to belong and enhanced sensitivity to social cues. . Personality and Social Psychological Bulletin , 30 : 1095 – 1107 .
- Smith , A. and Williams , K. D. 2004 . R U there? Effects of ostracism by cell phone messages. . Group Dynamics: Theory, Research, and Practice , 8 : 291 – 301 .
- Twenge , J. M. , Baumeister , R. F. , Tice , D. M. and Stucke , T. S. 2001 . If you can't join them, beat them: Effects of social exclusion on aggressive behavior. . Journal of Personality and Social Psychology , 81 : 1058 – 1069 .
- van Beest , I. and Williams , K. D. 2006 . When inclusion costs and ostracism pays, ostracism still hurts. . Journal of Personality and Social Psychology , 91 : 918 – 928 .
- Williams , K. D. 2001 . Ostracism: The power of silence , New York : Guilford Press .
- Williams , K. D. 2007 . Ostracism. . Annual Review of Psychology , 58 : 425 – 452 .
- Williams , K. D. , Bernieri , F. , Faulkner , S. , Grahe , J. and Gada‐Jain , N. 2000a . The Scarlet Letter study: Five days of social ostracism. . Journal of Personal and Interpersonal Loss , 5 : 19 – 63 .
- Williams , K. D. , Cheung , C. K. T. and Choi , W. 2000b . CyberOstracism: Effects of being ignored over the Internet. . Journal of Personality and Social Psychology , 79 : 748 – 762 .
- Williams , K. D. , Forgas , J. P. and von Hippel , W. 2005 . The social outcast: Ostracism, social exclusion, rejection, and bullying , Hillsdale, NJ : Psychology Press .
- Williams , K. D. and Jarvis , B. 2006 . Cyberball: A program for use in research on ostracism and interpersonal acceptance. . Behavior Research Methods, Instruments and Computers , 38 : 174 – 180 .
- Williams , K. D. and Sommer , K. 1997 . Social ostracism by one's coworkers: Does rejection lead to loafing or compensation. . Personality and Social Psychology Bulletin , 23 : 693 – 706 .
- Williams , K. D. and Zadro , L. 2005 . “ Ostracism: The indiscriminate early detection system. ” . In The social outcast: Ostracism, social exclusion, rejection, and bullying , Edited by: Williams , J. P , Forgas , J. P and von Hippel , W . 19 – 35 . New York : Psychology Press .
- Zadro , L. , Boland , C. and Richardson , R. 2006 . How long does it last? The persistence of the effects of ostracism in the social anxious. . Journal of Experimental Social Psychology , 42 : 692 – 697 .
- Zadro , L. , Williams , K. D. and Richardson , R. 2004 . How low can you go? Ostracism by a computer lowers belonging, control, self‐esteem, and meaningful existence. . Journal of Experimental Social Psychology , 40 : 560 – 567 .