?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
This paper concerns a one-phase inverse Stefan problem in one-dimensional space. The problem is ill-posed in the sense that the solution does not depend continuously on the data. We also consider noisy data for this problem. As such, we first regularize the proposed problem by the discrete mollification method. We apply the integration matrix using Bernstein basis polynomials for the discrete mollification method. Through this method, the execution time was gradually decreased. We then extend the space marching algorithm for solving our problem. Moreover, proofs of stability and convergence of the process are given. Finally, the results of this paper have been illustrated and examined by some numerical examples. Numerical examples confirm the efficiency of the proposed method.
1. Introduction
The term ‘Stefan problem’ is generally used for problems with phase-changes such as from the liquid to the solid. Stefan problem has piqued increasing interest of many researchers for over a century, since these problems are important in many engineering, science and technology applications such as freezing the foodstuffs [Citation1], crystal growth [Citation2,Citation3], solidification and melting of metals [Citation4,Citation5], laser drilling in metals and the cornea [Citation6], the surgical removal of a body part or tissue, such as in atrial fibrillation [Citation7], movement of sea coasts with the ocean depth and a surface flux changing as a power of time [Citation8,Citation9], preservation of human blood, solar energy storage [Citation10] and many others.
The direct Stefan problem consists of determining the temperature in the domain and the position of the moving interface when the initial and boundary conditions, and the thermal properties of the heat conducting body are known [Citation10–15]. One class of inverse Stefan problem requires the reconstruction of the function which describes the boundary conditions when the position of the moving boundary is known [Citation16]. This kind of problem becomes an inverse design problem [Citation17]. Moreover, inverse Stefan problems belong to a very important class of improperly posed problems in control theory which have many engineering applications. For example, in the technology of refining a material by means of recrystallization, one is interested in solving the inverse Stefan problem which consists of finding the temperature and heat flux at the fixed surface guaranteeing the flatness of the crystallization front [Citation18].
The exact or analytic solutions of direct and inverse Stefan problems are restricted to a few simple cases. One often has to apply numerical methods such as the finite difference method [Citation19], the boundary element method (BEM) [Citation20], the method of fundamental solutions [Citation18], the heat balance integral method and the refined integral method [Citation21], the variational iteration method [Citation17], etc. in solving these phase-change problems. Here, we propose a stable and convergent numerical algorithm based on the discrete mollification and space marching methods for solving a one-phase inverse Stefan problem. The mollification method is recognized as a reliable and capable regularization method that has been widely applied to solve many ill-posed problems [Citation22–25]. It uses a convolution of the noisy data and a specific function with a parameter to smooth the noisy data. More recently, it has been proved that the mollification method is a versatile and useful tool when dealing with parabolic partial differential equations [Citation22,Citation25]. Simple implementation, accurate and stable solution in the presence of high level noise is the main characteristic of the mollification method. In this paper, we introduce a new discrete mollification method based on the integration matrix using Bernstein basis polynomials.
The outline of this paper is as follows. In Section 2, we formulate the direct and inverse Stefan problems. Section 3 begins with a brief description of the discrete mollification method followed by a new approach for it based on the integration matrix using Bernstein basis polynomials. In Section 4, we regularize and solve our inverse Stefan problem. Section 5 concerns the stability and convergence proof of the space marching numerical algorithm. Finally, some numerical examples are given in Section 6. The numerical results show that an accurate and computationally low-cost approximation to the inverse Stefan problem can be obtained using the presented method.
2. Mathematical model
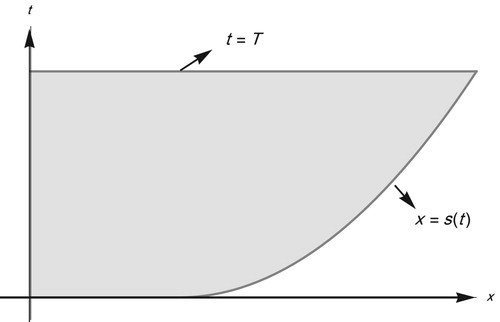
Let be a domain in
(Figure ). For the direct one-phase Stefan problem we seek a solution
which satisfies the following equation
(1)
(1) subject to the initial condition
(2)
(2) the Dirichlet and Neumann boundary conditions on the moving boundary
(3)
(3)
(4)
(4)
and Dirichlet boundary condition on x = 0
(5)
(5) (for more details, see [Citation17]), where α is the thermal diffusivity,
and
, with
, ρ is the density, L is the latent heat and K is the thermal conductivity, T is a given final time,
is a positive nondecreasing function describing the position of the moving boundary,
is given and u, x and t refer to temperature, space and time, respectively. The boundary condition in (Equation5
(5)
(5) ) can be changed to the
(6)
(6)
Existence and uniqueness of a solution, and continuous dependence on the data, i.e. well-posedness, for and
hold for the direct one-phase Stefan problem (Equation1
(1)
(1) )–(Equation5
(5)
(5) ) and (Equation1
(1)
(1) )–(Equation4
(4)
(4) ),(Equation6
(6)
(6) ) [Citation10,Citation26,Citation27]. The inverse Stefan problem that will be considered in this paper consists of finding the temperature
,
and
satisfying (Equation1
(1)
(1) )–(Equation6
(6)
(6) ), when the moving boundary
is known. This inverse problem is highly ill-posed [Citation26]. Now, we assume that functions
and
are not known exactly and we only have approximations of these functions presented as
and
, respectively. In addition, these approximate functions satisfy the following conditions:
where ϵ denotes the maximum level of noise. Due to perturbations in the problem's data and the ill-posedness of the proposed problem, we first regularize the problem through a method called discrete mollification.
In the next section, we introduce a new discrete mollification method based on Bernstein basis polynomials.
3. The method of discrete mollification using Bernstein basis polynomials
Mollification is a filtering procedure, based on convolution, which has proven to be convenient for the regularization of a variety of ill-posed problems [Citation22–25,Citation28,Citation29]. In this section, we first recall the definition of Bernstein polynomials and using these polynomials, we find the integration matrix in this basis. Next, we introduce the basic idea of our new discrete mollification method based on the mentioned integration matrix.
3.1. Bernstein basis polynomials and the integral matrix
A Bernstein polynomial (also called Bézier polynomial) defined over the interval has the form
(7)
(7) This is not a typical scaling of the Bernstein polynomials; however, this scaling makes matrix notations related to this basis slightly easier to write.
We choose Bernstein basis polynomials because when , Bernstein polynomials are appropriate and reasonable approximations to functions involved in the mollification process. Moreover, the integration matrix for Bernstein basis polynomials is well structured and easy to use. This enables us to take the integrals quickly and efficiently which substantially reduces the necessary CPU times (see Tables and ).
Table 1. RMS and CPU time(s) for 
 in Example 6.1.
in Example 6.1.
Table 2. RMS for 
 in Example 6.2.
in Example 6.2.
The Bernstein polynomials are nonnegative in , i.e.
for all
Bernstein polynomials are widely used in computer-aided geometric design [Citation30].
For a function , a polynomial approximation,
, written using Bernstein basis is of the form
(8)
(8) where the
's are sometimes called the Bézier coefficients
and are defined by:
Lemma 3.1
If is given by (Equation8
(8)
(8) ), then
(9)
(9) where
is an undetermined constant row vector of size M + 2 and
is an
matrix that has the following structure:
(10)
(10)
Proof.
A little computation using (Equation7(7)
(7) ) shows that [Citation31]
(11)
(11) where any
with either a negative or larger than M index, j, is set to 0 in (Equation11
(11)
(11) ). Now, we take the antiderivatives of the sides of (Equation11
(11)
(11) ) for
. We can then write the basis functions of degree M of the left-hand side of the resulting equation in terms of those of degree M + 1 (see e.g. [Citation32] for more details) and from there, it is fairly easy to derive (Equation10
(10)
(10) ). For example, for M = 3,
has the following form
(12)
(12)
3.2. A new discrete mollification method
We first assume to be a discrete function defined on
satisfying
In [Citation25], for p>0 and every
, Murio defined discrete mollification of G as follows.
(13)
(13) where
,
,
and
such that
. From now on, the p-dependency on the kernel has been dropped for simplicity of notation.
Now, let be the degree-M Bernstein approximation of
over
. If
, r = 0, 1, we have the following result about the rate of convergence of
[Citation33]:
(14)
(14) where
is modulus of continuity of
and
.
We define the discrete mollification of G through the integration matrix (Equation10(10)
(10) ) in the following form:
(15)
(15)
where
and
are defined in Equations (Equation7
(7)
(7) ) and (Equation10
(10)
(10) ), respectively.
Next, we obtain
(16)
(16) See Examples 6.1 and 6.2 of Section 6 for some numerical examples.
From now on, we refer to Equation (Equation13(13)
(13) ) and (Equation16
(16)
(16) ) as the old and new techniques for discrete mollification, respectively. We usually take p = 3 and the radius of mollification, δ, is selected automatically by generalized cross validation method (GCV) (for more details, see [Citation25]). The new technique for discrete mollification satisfies consistency, stability and convergence estimates as follows.
Theorem 3.2
Let ,
and
be the Lipschitz constants of
and
respectively.
If
and
is the discrete version of g, then there exist positive constants C,
and
such that
Moreover, if
then,
If
is the perturbed discrete version of g satisfying
then
If
and
is the perturbed discrete version of g satisfying
then there exist positive constants C,
and
such that
Moreover, if
then,
Proof.
a. For the first part of (a), we first prove
(17)
(17) We have
From (Equation14
(14)
(14) ), we get
(18)
(18) The triangle inequality yields
Applying Theorem 4.1 in [Citation25] and inequality (Equation17
(17)
(17) ), we have
To prove the second part of (a), we use the triangle inequality again to get
(19)
(19) According to the definition of discrete mollification by Bernstein basis polynomials (Equation15
(15)
(15) ), we obtain
where the last inequality is obtained from Equation (Equation14
(14)
(14) ). We then have
(20)
(20) From (Equation19
(19)
(19) ) and (Equation20
(20)
(20) ) and Theorem 4.1 in [Citation25], we have
and the proof of (a) is complete.
In (a), with , we obtain uniform approximation as
.
b. For proving the first part of (b), it suffices to note that
(21)
(21) we then have
For the second part of (b), we have
(22)
(22) In (b), for each fixed
, we attain uniform approximation.
c. All of the estimates in are based on the results in (a) and (b) and the triangle inequality.
Setting and
, we obtain uniform convergence as
.
Theorem 3.3
Let be the discrete version of g and
be a differentiation operator defined by
where
is the central difference operator, then there exists a positive constant
such that
Proof.
By the definition of differentiation operator and discrete mollification, we have
Applying the Mean Value Theorem gives
where the constant
represents an upper bound, in magnitude, for the first order derivative of
.
Theorem 3.4
Let be the discrete version of g,
and
satisfy
. There exist positive constants C,
and
such that
Proof.
The proof is a simple application of Taylor's theorem with the constant representing an upper bound, in magnitude, for higher order derivatives of
.
In order to compute throughout the domain
, we have to extend our discrete data function g to a bigger interval
or confine this function to
. In this work, the first approach described in [Citation25] is applied. An optimizing process is used to calculate the extension function of g in the intervals of
and
. This process is introduced by Mejia and Murio in [Citation23].
4. The regularized problem and the numerical procedure
The regularized problem is described as
(23)
(23)
(24)
(24)
(25)
(25)
(26)
(26)
where
shows the mollified function with respect to the radius of mollification, δ. Here, we intend to develop a numerical scheme based on the space-marching method to solve the regularized problem (Equation23
(23)
(23) )–(Equation26
(26)
(26) ). To this end, we denote
Table
The space marching algorithm for this problem is as follows.
Space Marching Algorithm
Choose
and
radii of mollification by GCV method.
Set
In this step we can calculate the unknown values of
(shown in Figure ) through the known boundary values
for
.
For n = 0 to
(27)
(27)
(28)
(28)
(29)
(29)
Set
. Do while
If
,
If
, then set
,
else set
,
else set
,
(30)
(30)
(31)
(31)
(32)
(32)
5. Stability and convergence analysis
In this section, we state and prove the stability and convergence properties of the space marching scheme (Equation27(27)
(27) )–(Equation32
(32)
(32) ). In particular, Theorem 5 shows the stability of our numerical method and Theorem 6 guarantees its convergence.
is defined in step 4 of the space marching algorithm.
Theorem 5.1
Stability theorem
The marching scheme (Equation27(27)
(27) )–(Equation32
(32)
(32) ) is stable.
Proof.
Let . From (Equation27
(27)
(27) )–(Equation29
(29)
(29) ), we have
(33)
(33)
(34)
(34)
(35)
(35)
Also Equation (Equation30
(30)
(30) ) and (Equation31
(31)
(31) ) give
(36)
(36)
(37)
(37)
By Theorem 3.3 and Equation (Equation32
(32)
(32) ), we derive
(38)
(38) From (Equation33
(33)
(33) )–(Equation38
(38)
(38) ), we have
where
then we have
(39)
(39) and then
(40)
(40) where
. The proof is complete.
Theorem 5.2
Convergence theorem
The numerical scheme (Equation27(27)
(27) )–(Equation32
(32)
(32) ) converges to the exact solution of the inverse Stefan problem (Equation1
(1)
(1) )–(Equation6
(6)
(6) ).
Proof.
We set ,
,
and
therefore, we have
(41)
(41)
(42)
(42)
(43)
(43)
(44)
(44)
(45)
(45)
and
(46)
(46)
Following (Equation44
(44)
(44) ) and (Equation45
(45)
(45) ), it is obtained that
(47)
(47)
(48)
(48)
Applying Theorem 3.4 and (Equation46
(46)
(46) ), we derive
(49)
(49) Following (Equation41
(41)
(41) ) and (Equation42
(42)
(42) ), we get
(50)
(50)
(51)
(51)
Applying Theorem 3.4 and (Equation43
(43)
(43) ), it is obtained that
(52)
(52) By (Equation47
(47)
(47) )–(Equation49
(49)
(49) ), we derive
(53)
(53)
and
(54)
(54)
by (Equation50
(50)
(50) )–(Equation54
(54)
(54) ) we have
(55)
(55) in a similar way for
and
, we get
(56)
(56)
(57)
(57) Let
Then we have
(58)
(58)
where
. Moreover, from
by choosing
,
and
, we see that when ϵ, h and k tend to zero, the right side of (Equation58
(58)
(58) ) tends to 0, so does the
and proof is complete.
6. Numerical results
This section begins with two examples to show the advantages of the new technique for discrete mollification method over the old one proposed in [Citation25]. Next, in order to compare our numerical results with those obtained by other methods, two benchmark test problem are given.
To measure the efficiency of our method, we define the root mean square error (RMS),
where N + 1 is the total number of testing points in the domain
, and the
are test points, and
and
are the exact and approximate values at the test points. The noisy discrete data functions are generated by adding a random perturbation to the exact data functions, which is defined by:
where the
's are Gaussian random variables with variance
. In these examples, we take final time T = 1. We performed our computations using Mathematica 10.3.1 software on a Core i5 CPU machine with 8Gb of memory.
Example 6.1
In this example, we have the exact data function . The numerical results in Table show the RMS errors and CPU time for the old and new discrete mollification methods. As shown, the new method gives better results.
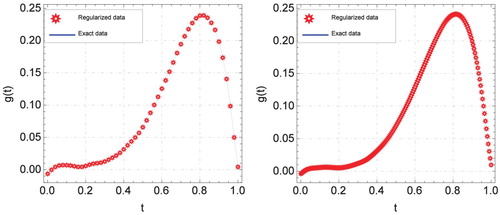
A graphical comparison of the exact data function g and the regularized data function with two noise levels
and
appear in Figures and .
Figure 3. Graphs of exact and regularized data functions for using new discrete mollification method with
, N = 50 (left panel) and
, N = 200 (right panel) for Example 6.1
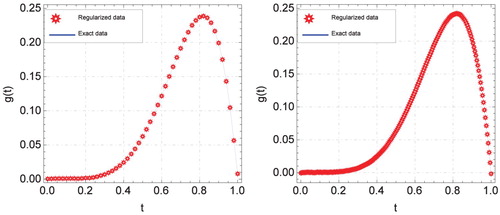
Figure 4. Graphs of exact and regularized data functions for using new discrete mollification with
, N = 50 (left panel), and with
, N = 200 (right panel) for Example 1.
Example 6.2
This example represents an exponential approximation to an instantaneous pulse. The equation for the exact data function is
Example 6.3
This example which is taken to be the same as tested in [Citation18,Citation26,Citation27], concerns a problem with a nonlinear moving interface. In this example, we take ,
,
and the moving interface is given by
The exact solution pair is
and
To assess the accuracy of numerical procedure, we first add random noise
and
to the initial condition (Equation2
(2)
(2) ) and the Neumann boundary condition (Equation4
(4)
(4) ), then we employ the new technique of discrete mollification along with the space marching algorithm presented in Section 4 for this test problem. Figures – illustrate exact and approximate solutions and absolute error for
and
, respectively. From these figures, we conclude that at fixed mesh points, the absolute error of numerical results increases by increasing noise level. The RMS and
errors for this inverse problem with different values of
and N are listed in Table with two noise levels
and
. This Table shows that at a fixed noise level ϵ, as the number of mesh points increases, the accuracy of the algorithm will improve. Finally, Figure illustrates the graph of the absolute error for
. This figure demonstrates the effectiveness of the method presented in this paper. We can compare our numerical results with the results of [Citation18,Citation26,Citation27]. However, results of [Citation18,Citation26] for
demonstrate an oscillatory and unstable behaviour (see Figure 12 of [Citation18] and Figures 15 and 17 of [Citation26]) while Figures and show that our method is free of such unstable oscillations. Obviously, comparing Figures , and with Figures 6, 7 and 9 of [Citation27] shows that our method perform better, especially for high noise levels. We note that in Examples 3-4, we added the random noise levels to the initial and boundary conditions while in [Citation18,Citation26,Citation27] the noise levels only being applied to the boundary input data. However, our results were even betteer than these Refs.
Figure 5. Graphs of noisy data function (left panel) and exact and regularized data functions (right panel) using new discrete mollification with
, N = 128 for Example 2.
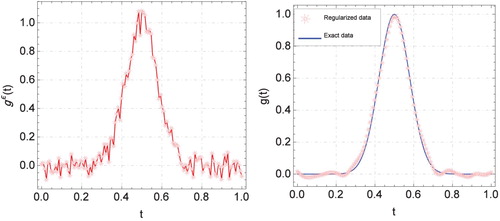
Figure 6. Graphs of exact and computed solutions for with
,
, N = 200 (left panel) and absolute error for
with
,
, N = 200 (right panel) for Example 3.
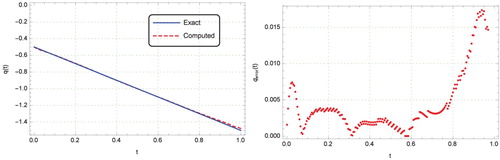
Figure 7. Graphs of exact and computed solutions for with
,
, N = 200 (left panel) and absolute error for
with
,
, N = 200 (right panel) for Example 3.
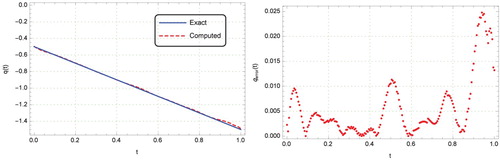
Figure 8. Graphs of exact and computed solutions for with
,
, N = 300 (left panel) and absolute error for
with
,
, N = 350 (right panel) for Example 3.
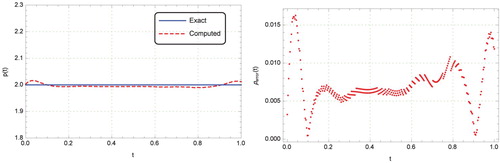
Figure 9. Graphs of exact and computed solutions for with
,
, N = 300 (left panel) and absolute error for
with
,
, N = 350 (right panel) for Example 3.
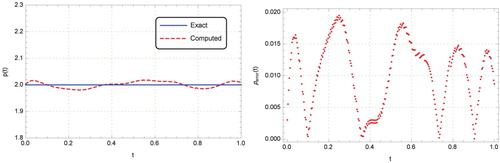
Table 3. RMS and 
 for Example 3.
for Example 3.
Example 6.4
In this example [Citation34], we consider problem (Equation1(1)
(1) )–(Equation6
(6)
(6) ) with
,
,
, and
The exact solution of this test problem is
and
We test the accuracy of the proposed method by solving this problem by the above-mentioned method with several values of
and N and different noise levels. Figures – illustrate exact and approximate solutions and absolute error for
and
, respectively. From these Figures, we conclude that at fixed mesh points, the absolute error of numerical results increases with increasing noise level. The RMS and
errors for this inverse problem with different values of
and N are listed in Table with two noise levels
and
. This Table shows that at a fixed noise level ϵ, as the number of mesh points increases, the accuracy of the algorithm will improve. Finally, Figure illustrates the graph of the absolute error for
. This figure demonstrates the effectiveness of the method presented in this paper. Our method also performs better than the unregularized decomposition method employed in [Citation34], which is valid only for exact data.
Figure 11. Graphs of exact and computed solutions for with
,
, N = 200 (left panel) and absolute error for
with
,
, N = 200 (right panel) for Example 4.
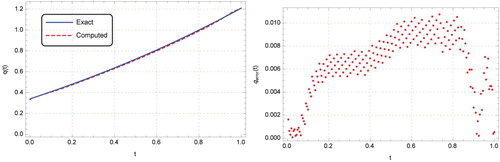
Figure 12. Graphs of exact and computed solutions for with
,
, N = 200 (left panel) and absolute error for
with
,
, N = 200 (right panel) for Example 4.
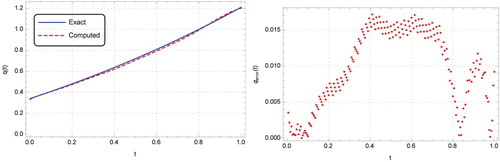
Figure 13. Graphs of exact and computed solutions for with
,
, N = 200 (left panel) and absolute error for
with
,
, N = 200 (right panel) for Example 4.
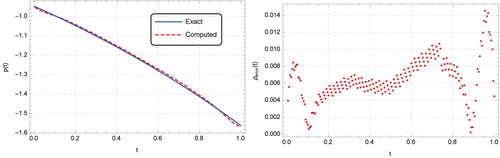
Figure 14. Graphs of exact and computed solutions for with
,
, N = 200 (left panel) and absolute error for
with
,
, N = 200 (right panel) for Example 4.
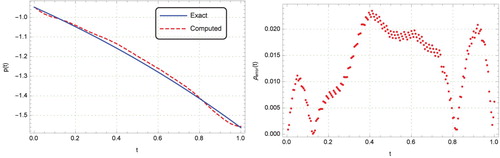
Table 4. RMS and 
 for Example 4.
for Example 4.
7. Conclusions
In this study, a class of inverse one phase Stefan problem with unknown temperature distribution and heat flux at the boundary x = 0 has been investigated. For solving this problem, a regularization procedure using Bernstein basis polynomials combined with explicit space marching scheme is implemented. As shown in Examples 6.1 and 6.2, by the new technique of discrete mollification, RMS error and especially CPU time are reduced. Moreover, a proof of stability and convergence of the aforementioned algorithm is provided. Finally, the results of this paper have been illustrated by some numerical examples. Numerical examples confirm the efficiency of the proposed method.
References
- Bakal A, Timbers G, Hayakawa K. Solution of the characteristic equation involved in the transient heat conduction for foods approximated by an infinite slab. Can Inst Food Technol. 1970;3:76–77. doi: 10.1016/S0008-3860(70)74275-X
- Conti M. Density change effects on crystal growth from the melt. Phys Rev. 2001;E64:051601.
- Libbrecht KG. The physics of snow crystals. Rep Prog Phys. 2005;68:855–895. doi: 10.1088/0034-4885/68/4/R03
- Lin WS. Steady ablation on the surface of a two-layer composite. Int J Heat Mass Transf. 2005;48:5504–5519. doi: 10.1016/j.ijheatmasstransfer.2005.06.040
- Sharifi N, Bergman TL, Allen MJ, et al. Melting and solidification enhancement using a combined heat pipe foil approach. Int J Heat Mas Tran. 2015;78:930–941. doi: 10.1016/j.ijheatmasstransfer.2014.07.054
- Tayler AB. Mathematical models in applied mechanics. Oxford: ClarendonPress; 2001.
- Namenanee K, McKenzie J, Kosa E, et al. A new approach for catheter ablation of atrial fibrillation: mapping of the electrophysiologic substrate. J Am College Cardiol. 2004;43(11):2044–2053. doi: 10.1016/j.jacc.2003.12.054
- Salva NN, Tarzia DA. Explicit solution for a Stefan problem with variable latent heat and constant heat flux boundary conditions. J Math Anal Appl. 2011;379:240–244. doi: 10.1016/j.jmaa.2010.12.039
- Trueba JL, Voller VR. Analytical and numerical solution of a generalized Stefan problem exhibiting two moving boundaries with application to ocean delta formation. J Math Anal Appl. 2010;366:538–549. doi: 10.1016/j.jmaa.2010.01.008
- Gupta SC. The classical Stefan problem, basic concepts, modelling and analysis. Amsterdam: Elsevier; 2003.
- Crank J. Free and moving boundary problems. Oxford: Clarendon Press; 1984.
- Finlayson BA. The method of weighted residuals and variational principles. New York: Academic Press; 1972.
- Meirmanov AM. The Stefan problem. Berlin: Walter de Gruyter; 1992.
- Ozisik MN. Heat conduction. New York: Wiley; 1980.
- Rubinstein LI. The Stefan problem. Providence: AMS; 1971.
- Goldman NL. Inverse Stefan problem. Dordrecht: Kluwer; 1997.
- Slota D. Direct and inverse one-phase Stefan problem solved by the variational iteration method. Comput Math Appl. 2007;54:113–1146. doi: 10.1016/j.camwa.2006.12.061
- Johansson BT, Lesnic D, Reeve T. A method of fundamental solutions for the one-dimensional inverse Stefan problem. Appl Math Model. 2011;35:4367–4378. doi: 10.1016/j.apm.2011.03.005
- Mitchell SL, Vynnycky M. Finite-difference methods with increased accuracy and correct initialization for one-dimensional Stefan problems. Appl Math Comput. 2009;215:1609–1621.
- Wrobel LC. A boundary element solution to Stefan's problem. Southampton: Computational Mechanics Publications and Berlin: Springer-Verlag; 1983. p. 173–182. (Boundary Elements; V).
- Bollati J, Semitiel J, Tarzia DA. Heat balance integral methods applied to the one-phase Stefan problem with a convective boundary condition at the fixed face. Appl Math Comput. 2018;331:1–19. doi: 10.1016/j.cam.2017.09.008
- Acosta CD, Mejia CE. Stabilization of explicit methods for convection diffusion equations by discrete mollification. Comput Math Appl. 2008;55:368–380. doi: 10.1016/j.camwa.2007.04.019
- Mejia CE, Murio DA. Mollified hyperbolic method for coefficient identification problems. Comput Math Appl. 1993;26(5):1–12. doi: 10.1016/0898-1221(93)90067-6
- Mejia CE, Acosta CD, Saleme KI. Numerical identification of a nonlinear diffusion coefficient by discrete mollification. Comput Math Appl. 2001;62:2187–2199. doi: 10.1016/j.camwa.2011.07.004
- Murio DA. Mollification and space marching, In: Woodbury, K ed. Inverse Engineering Handbook, CRC Press;2002.
- Reddy GMM, Vynnycky M, Cuminato JA. On efficient reconstruction of boundary data with optimal placement of the source points in the MFS: application to inverse Stefan problems. Inverse Probl. Sci. Eng. 2018;26:1249–1279. doi: 10.1080/17415977.2017.1391244
- Reddy GMM, Vynnycky M, Cuminato JA. An efficient adaptive boundary algorithm to reconstruct Neumann boundary data in the MFS for the inverse Stefan problem. J Comput Appl Math. 2019;349:21–40. doi: 10.1016/j.cam.2018.09.004
- Coles C, Murio DA. Identification of parameters in the 2-D IHCP. Comput Math Appl. 2000;40:939–956. doi: 10.1016/S0898-1221(00)85005-1
- Mejia CE, Murio DA. Numerical solution of generalized IHCP by discrete mollification. Comput Math Appl. 1996;32(2):33–50. doi: 10.1016/0898-1221(96)00101-0
- Farin G. Curves and surfaces for computer-Aided geometric design. San Diego: Academic Press; 1997.
- Amiraslani A. Differentiation matrices in polynomial bases. Math Sci. 2016;10:47–53. doi: 10.1007/s40096-016-0177-x
- Farouki RT, Rajan VT. Algorithms for polynomials in Bernstein form. Comput Aided Geom Des. 1988;5:1–26. doi: 10.1016/0167-8396(88)90016-7
- Lorentz GG. Bernstein polynomials. 2nd ed. New York: Chelsea Publishing Co; 1986.
- Grzymkowski R, Slota D. One-phase inverse Stefan problem solved by Adomain decomposition method. Comput Math Appl. 2006;51:33–40. doi: 10.1016/j.camwa.2005.08.028

![Figure 2. The unknown UMnn at the (Mn,n)th mesh point calculated in step 3 for n=1,…,N with N = 3 and M0=3, where Mn=[s(tn)/h].](/cms/asset/8107c951-eca6-4eb2-a3f1-8d68671cab9b/gipe_a_1733996_f0002_oc.jpg)