?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
This paper approaches a bi-connectivity preservation problem for networked multi-robot systems in a distributed control fashion. Since a bi-connected network topology is robust against single node removal, networked multi-robot systems are required to preserve bi-connectedness in cases robots may fail. By employing a perturbed graph Laplacian to find if the network is disconnected after a node is removed, we analyse a sufficient condition that the network is bi-connected. Then we design a distributed control law to preserve the bi-connectedness from the sufficient condition. Moreover, considering cases a robot fails, we propose a control law to let a uni-connected network be bi-connected forcibly. A condition to restore the bi-connectedness by the proposed control is theoretically proved. The effectiveness of the proposed control laws is demonstrated by numerical simulations.
1. Introduction
Multi-robot systems are the systems in which each robot individually makes each decision by communicating with each other. One of the control strategies for such multi-robot systems is a coverage [Citation1] of which the control objective is to cover a given area by the range of sensors equipped by the robots. The coverage control methods are applied for target searching and consisting a mobile ad-hoc network.
To achieve the team objectives through communication or information exchange, it is important that a network modelling the communication topology is connected. The task accomplishment will be hard once the connectedness is lost since the network topology will be divided into two or more components. For this challenge, some autonomous distributed control laws to preserve the connectedness have been proposed [Citation2,Citation3]. Since it is known that the connectedness is equivalent to the second smallest eigenvalue of the graph Laplacian matrix is positive, a lot of the control laws for the connectedness preservation employ the gradient of the second smallest eigenvalue to decide the direction of the robot motion. The second smallest eigenvalue of the graph Laplacian is called algebraic connectivity.
The network connectedness will be violated by the failure of the robots. Bi-connectedness is required to preserve the network connected against a single robot failure and therefore distributed control laws to preserve bi-connectedness have been proposed [Citation4,Citation5]. The work [Citation4] clarified the theoretical fact that the network is bi-connected if and only if the third smallest eigenvalue of the modified Laplacian matrix is positive, and the control method to preserve the third smallest eigenvalue is proposed. However, calculating only the third smallest eigenvalue in a distributed fashion is difficult. Calculating all the eigenvalues is assumed to get the third one, but it requires a lot of computation and communication costs. Apart from connectivity control using the Laplacian eigenvalue, a control algorithm with vertex connectivity of a subgraph is proposed in [Citation5] for connectivity maintenance. A cost function of the vertex connectivity which is calculated in a distributed fashion is designed in that work, but the control algorithm using the cost function does not theoretically guarantee the vertex connectivity under the existence of the task input.
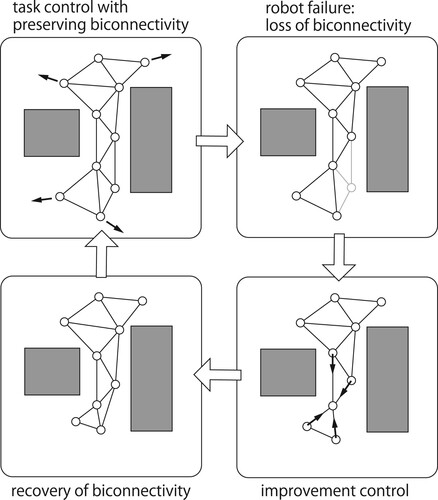
We have proposed a hybrid control method for the bi-connectivity of the multi-robot network using the second smallest eigenvalue of the perturbed Laplacian matrix in the study [Citation6]. Since the second smallest eigenvalue of the Laplacian is efficiently computed by a distributed algorithm [Citation7] unlike the third smallest eigenvalue, overall computation of our control method is accomplished in a distributed fashion. The proposed hybrid control switches two control modes: an improvement control and a preservation control for the bi-connectedness (see Figure ). The improvement control works when the bi-connectedness is violated by a robot failure, and the preservation control enables the multi-robot system to accomplish a team task with preserving the bi-connectedness. The theoretical correctness of the control laws are proved using results of our previous studies [Citation8,Citation9] where we analysed that the second smallest eigenvalue of a perturbed Laplacian is related to the connected components of the network after single robot failure. Additionally, we had claimed that our improvement control method may not resume the bi-connectedness under some conditions.
This paper proposes a refined version of the control method for the multi-robot network bi-connectedness. We try to overcome the bi-connectivity improvement difficulty claimed in the study [Citation6] by stopping the preservation control temporarily. The detailed scheme of the control method and results of the numerical simulation are presented here.
The rest of this paper is organized as follows: Section 2 defines a networked multi-robot system we discuss in this work and formulate a bi-connectivity control problem that is designed to robustify the multi-robot network topology against robotic failures. We propose control methods to solve the bi-connectivity problem in Section 3. Perturbed algebraic connectivity is introduced from our previous studies, and control laws are constructed by employing perturbed algebraic connectivity. In Section 4, results of numerical simulations are demonstrated to represent the effectiveness of the proposed method. Section 5 concludes this paper.
2. Problem formulation
In this section, we define a multi-robot system we consider in this study, and the control problem we try to solve. We assume the multi-robot system consisting of autonomous mobile robots, and define the index set of the robots by
.
The motion dynamics of each robot is formulated as
(1)
(1) where
denotes continuous time,
denotes position of robot
,
denotes a control input of the improvement/preservation for the bi-connectedness,
denotes a task control input such like coverage or target searching.
and
are control gains, and
is a dimension of the configuration space. We assume the task control
is repulsive from neighbour robots as a coverage control, so that the task control act as a disturbance of bi-connectedness.
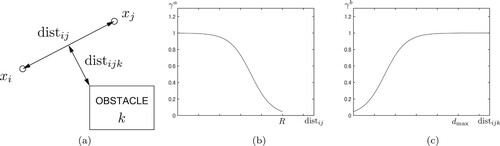
Two robots i and j have a communication link when the distance is less than the communication radius R and there are no obstacles on the line segment from the point
to the point
(hereafter we represent this line segment as
). The network topology
is represented by the weighted adjacency matrix
, such that
where
denotes the ijth entry of the adjacency matrix A. We employ definitions of the ijth entry
from a previous study [Citation10], as
(2)
(2) where
denotes the distance from the obstacle
to the line segment
.
denotes the indexes set of the obstacles to which the distance from the segment
are less than
, that is,
. The functions
and
are defined by
(3)
(3) if
, otherwise
, and
(4)
(4) if
, otherwise
, where
denote positive coefficients. The value
reflects the proximity between the robots compared to the communication radius R, and the value
reflects the farness from the obstacle which impedes the line-of-sight between the robot. From the definition Equation (Equation2
(2)
(2) ), the element
gets closet to 1 only when the distance
is sufficiently small and the distances
are sufficiently large. Figure shows an example of Equations (Equation2
(2)
(2) )–(Equation4
(4)
(4) ) if
,
, and
. By ensuring a line of sight between two robots using the link weight function Equation (Equation2
(2)
(2) ), we try to mitigate troubles ascribed to wireless communication (e.g. interference and fading).
Figure 2. Illustrated description of link weight functions Equations (Equation2(2)
(2) )–(Equation4
(4)
(4) ). (a) Definition of
and
. (b)
with respect to
and (c)
with respect to
.
Using the adjacency matrix A defined above, we define a Laplacian matrix L = D−A where D denotes the degree matrix of which the iith entry is . The second smallest eigenvalue
of the Laplacian matrix L is called the algebraic connectivity, and it is well known that the fact the graph
is connected if and only if
.
We call the graph is bi-connected if a graph
stands connected for all
. When the graph
is disconnected, the node i is called an articulation node. Clearly, we can see a bi-connected graph has no articulation node.
In this paper, we tackle two problems;
find a control input
and control gains
to preserve the graph
is bi-connected for all time
if the initial graph
is bi-connected,
and find a control input
and control gains
to resume the graph
to be bi-connected in finite time
if the initial graph
is not bi-connected but uni-connected.
The first one relates to a subject before a single robot fails and the second one relates to a subject after the failure. The failure in this study means that the robot can not communicate with its neighbours whether temporarily or permanently. Later sections describe the control law to solve these problems.
3. Proposed method
We propose distributed control laws to solve the problems defined in Section 2. First, we introduce a concept of perturbed algebraic connectivity which reflects the importance of a node for the connectivity. The detailed definition and theoretical properties are written in our previous study [Citation9]. We design the control laws using the perturbed algebraic connectivity in this study.
3.1. Perturbed algebraic connectivity
To represent the network topology after the robot i fails, using a sufficiently small positive parameter , we introduce a perturbed adjacency matrix
of which the mnth element is defined by
(5)
(5) Clearly, the perturbed adjacency matrix
represents the graph topology such that the links
incident to the node i are removed from the graph
. The perturbed Laplacian matrix
and the second smallest eigenvalue
of the matrix
are defined in a similar way, but note the perturbed Laplacian is normalized by the weighted degree
. Assuming the graph
is connected, we can see
for all
, and
since the graph which all links incident to the node i is removed is disconnected. Recalling the definition of the second smallest eigenvalue
of the Laplacian matrix
,
(6)
(6) we can see the corresponding eigenvector
has a characteristic property; for arbitrary nodes p and q, the pth element
of the eigenvector is equal to the qth element
if the nodes p and q are connected in the graph
. This property is directly proved from
. From the eigenvalue definition
, we get
(7)
(7) where
denotes the jth element of the eigenvector
.
Assuming the graph is composed of M>0 connected components, we discuss the gradient of the eigenvalue
at
, defined by
(8)
(8) The node i is not an articulation when M = 1 and it is an articulation when M>1. So here we analyse the value
as a function of the component number M. First, from the relations of the eigenvalue like Equation (Equation7
(7)
(7) ), we get equations
(9a)
(9a)
(9b)
(9b) where
denotes the summation of the value
of which node j belongs to mth connected component, and
denotes the number of nodes in the mth component.
denotes the ith element of the eigenvector
, and
denotes an element of the eigenvector with respect to the mth component. As we discussed in the above paragraph, the elements
and
are the same if both nodes p and q are in the same connected component. Note that
since it is equal to the number of nodes in the graph
, and
since the elements of the perturbed Laplacian matrix are normalized. From the relations Equation (Equation9a
(9a)
(9a) ), we get an algebraic equation of the value
, as
(10)
(10) with assuming
. If
and there exists a connected component m such that
, obviously
from Equation (Equation9b
(9b)
(9b) ). The case
for all
does not occur, since
and
. The value
is dependent on the component sizes
and weights
, so we call it the perturbed algebraic connectivity. The perturbed algebraic connectivity
is monotonically non-decreasing with respect to the link weight
, since the algebraic connectivity
is also monotonically non-decreasing.
To analyse a condition if the node i is not an articulation one, we find the maximum value of the perturbed algebraic connectivity when the node i is an articulation.
Theorem 3.1
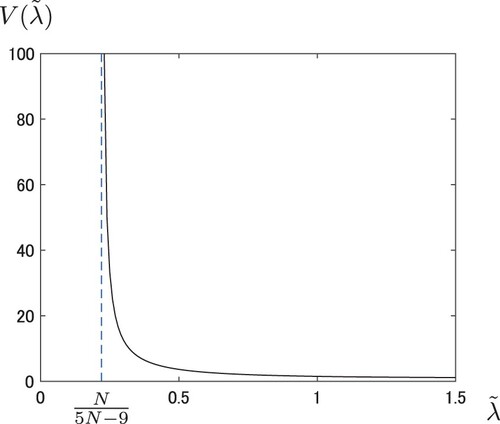
Corollary of [Citation9]
Assume a graph is connected, and the node i has 2 or more communication links. If the perturbed algebraic connectivity
satisfies
(11)
(11) then the node i is not an articulation node.
Proof.
See Appendix.
From the above theorem, our objectives will be achieved by satisfying the condition (Equation11(11)
(11) ), if the perturbed algebraic connectivities are estimated in a distributed fashion. Since the algorithm proposed in the reference [Citation7] can estimate the second smallest eigenvalue of the Laplacian matrix in a distributed fashion using, the eigenvalue
is also able to be estimated if
. Thus, a value
is employed as the approximation of the perturbed algebraic connectivity
in this study. Note the approximated value is smaller than the strict value, that is,
(12)
(12) for all
. This means
is a sufficient condition for the node i not to be an articulation node.
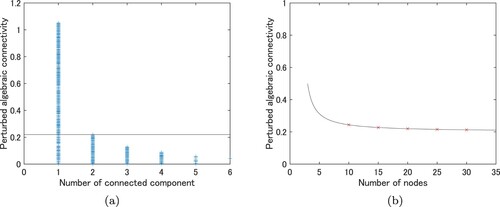
Here we demonstrate numerical examples of the condition Equation (Equation11(11)
(11) ). Figure (a) shows the perturbed algebraic connectivity
of randomly generated graph with N = 20. The random graphs are generated by Erd
s–Rényi model [Citation11] with link probability 0.15, and link weights
are randomly chosen in the interval
. From Figure (a), we confirm that the computed perturbed algebraic connectivity
(shown by the blue + marker) does not exceed
(black line) if the node i is an articulation node. Additionally, we can see the inequality Equation (Equation11
(11)
(11) ) is the sufficient condition, not a necessary condition for non-articulation nodes. Figure (b) shows numerical maximum of the perturbed algebraic connectivity
when the node i is an articulation node. The red x markers indicate the numerical maximums and the black solid line shows the theoretical maximum
. In each case, the theoretical maximum is approximately identical to the numerical maximum.
Figure 3. Numerical demonstration of sufficient condition Equation (Equation11(11)
(11) ). (a)
v.s. # of connected component in
and (b) Numerical maximum of
.
The control method we detail below switches two control modes: bi-connectivity preservation and bi-connectivity restoration. The preservation launches if all the perturbed algebraic connectivity satisfies the condition Equation (Equation11
(11)
(11) ), and the restoration launches if one of the perturbed algebraic connectivity does not satisfy that condition. Note that the system does not detect whether a robot has failed but checks the perturbed algebraic connectivity of the non-failed robots. The bi-connectivity restoration could start even if the network is bi-connected since the inequality Equation (Equation11
(11)
(11) ) is a sufficient condition. The restoration also could start if communication stops temporarily due to radio wave attenuation (e.g. fading). We can say that the system takes a safer policy.
3.2. Bi-connectivity preservation
Since the bi-connectedness is equivalent to the state that all the robot i are not articulation nodes, our control objective will be accomplished if we satisfy the condition Equation (Equation11(11)
(11) ) for all
. Here we propose two control methods: the robots preserve the condition Equation (Equation11
(11)
(11) ) for all time if the condition is initially satisfied.
Inspired by a connectivity preserving control law proposed in the study [Citation3], we define an artificial potential function by
(13)
(13) where
denotes the hyperbolic cotangent function (see Figure ). Then we can ensure the condition Equation (Equation11
(11)
(11) ) if the robots move in the gradient-decreasing direction.
Theorem 3.2
Corollary of [Citation3]
Assume the initial network consist of the initial robot positions
is bi-connected. If the bi-connectivity input
is given by
(14)
(14)
,
, and the task input is bounded
, then the network
is bi-connected for all time t>0.
Proof.
This theorem is proved by showing the energy function is bounded for all time t, where x denotes the positions of all robots
. First, the time derivative of the energy function E is given by
(15)
(15) where
denotes the task input,
denotes the corresponding gain, and
. Then, the energy E may increase only when the inequality holds:
(16)
(16) Here, the gradient
is given by
(17)
(17) where
denotes the hyperbolic cosecant function,
, and
(18)
(18) from
. Note that
. From above, there exists a positive value c such that
(19)
(19) when
, and clearly this is also hold when
. Thus
for all node j and for all time t.
Using the expression Equation (Equation18(18)
(18) ), the control input Equation (Equation14
(14)
(14) ) is rewritten by
(20)
(20) where
(21)
(21) The control input Equation (Equation20
(20)
(20) ) requires the local information
and
, the perturbed eigenpair
and
which is estimated by the distributed algorithm [Citation7], and the degree
for the normalization. Although the degree
is not the local information, all the robots j can modify the elements of the perturbed Laplacian matrix
to be
in a distributed manner.
3.3. Bi-connectivity restoration
Similarly, the robots will resume the condition Equation (Equation11(11)
(11) ) by moving in the gradient increasing direction if the condition is not satisfied initially. We analysed a condition to resume the network bi-connected.
Theorem 3.3
Assume the initial network consist of the initial robot positions
is uni-connected, all distances
from obstacles
to segments
are greater than
, and the convex hull
consist of the initial robot positions
does not contain any obstacles
. If the bi-connectivity input
is given by
(22)
(22) where
, and gains are
,
,
, then the network
becomes bi-connected in finite time
.
Proof.
Under the assumption, the robotic system Equation (Equation1(1)
(1) ) can be rewritten as
(23)
(23) where
denotes the ith element of the eigenvector
w.r.t. the eigenvalue
, and
(24)
(24)
(25)
(25) Here we can see
(26)
(26) Next, the gradient
is expressed by
(27)
(27) from the definition Equation (Equation3
(3)
(3) ). Thus we can rewrite Equation (Equation23
(23)
(23) ) as
(28)
(28) by defining an appropriate strictly positive variable
. Note this dynamics is a consensus algorithm [Citation12]. Therefore, we can see all the points
are in the convex hull
and move towards the consensus set
. Figure illustrates this behaviour. The system state
approaches to the consensus set
and the bi-connectedness is resumed at finite time
.
The above theorem ensures the achievement of the bi-connectivity restoration only under some initial configurations of the robots. Unfortunately in cases that the convex hull contains some obstacles, the multi-robot system falls into a local optimum and the bi-connectedness may not be restored. For instance, the robots which move from the initial positions described in Figure cannot resume the bi-conectedness of the network while preserving all other non-articulation nodes. The local optimum set to be avoided for the bi-connectivity restoration is expressed by
(29)
(29) In other words, the restoration control Equation (Equation22
(22)
(22) ) will make the network bi-connected if the system state
is not in the local optimum set
for all time t.
3.3.1. Avoiding local optimum
To avoid such local minima and to encourage resuming the bi-connectivity, we propose a heuristic technique that temporally stops the preserving control (second term of Equation (Equation22(22)
(22) )) considering that the preservation term disturbs the bi-connectivity restoration. The restoration control input Equation (Equation22
(22)
(22) ) is modified as
(30)
(30) where
denotes the time threshold to preserve non-articulation nodes and
denotes the preserving time count. The parameter
changes as below:
(31)
(31) where
denotes a small margin not to let
be too large. The time threshold
is set to be sufficiently large so that
becomes larger than
only when the system state x is close to the local optimum set
.
A rough outline of this control law Equation (Equation30(30)
(30) ) is given as below. The non-articulation preserving mode (the first line of Equation (Equation30
(30)
(30) )) is stopped when the state x is trapped by the local optima
, and the local optima avoiding mode (the second line of Equation (Equation30
(30)
(30) )) will be executed until the node becomes non-articulation. Since it is difficult to observe that the state x is close to the local optimal set
in a distributed fashion, instead we employ the length of time the bi-connectivity has not been restored. By stopping the non-articulation node preservation condition (Equation11
(11)
(11) ), we try to force the state x to escape from the set
.
The state trajectory of the system Equation (Equation1
(1)
(1) ) with the control law Equation (Equation30
(30)
(30) ) and
does not converge any closed cycles, under the assumption:
(32)
(32) This fact is confirmed by showing that the summation of the perturbed algebraic connectivity
does not decrease over time t. Defining the energy function
, the non-articulation preservation mode does not reduce the energy
, that is,
for all t>0. From a simple deformation:
(33)
(33) we get
for all t>0. Thus, the system trajectory
results in either achievement of the bi-connectivity restoration or convergence towards the alternative local optimum set
(34)
(34) to be avoided. We may be able to avoid this local optimal set
by switching the control mode if
. Further analysis and improving the control law remain future works.
4. Numerical simulations
In this section, numerical simulations are demonstrated to describe the usefulness of the proposed method. The task control input is given by
(35)
(35) considering a coverage control. The perturbation parameter ε is
, and the control gains are
and
. The control input
is saturated as
if
. The number of robotic-nodes is N = 20. The parameters of the link weight
are defined in Equations (Equation3
(3)
(3) ) and (Equation4
(4)
(4) ) are set by
and
.
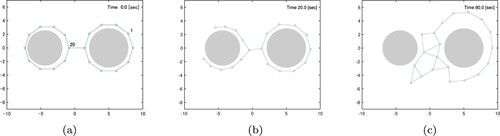
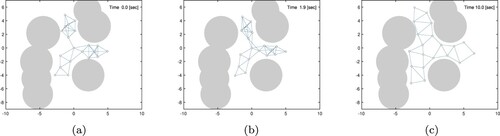
We show a simulation result of the restoration control Equation (Equation22(22)
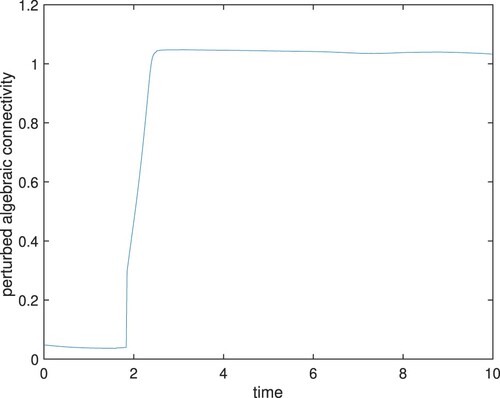
(22) ). Figure represents snapshots of the initial configuration t = 0 (Figure (a)), at time t = 1.9 when the bi-connectivity is restored (Figure (b)), and at time t = 10 when the multi-robot system converges a stable state (Figure (c)). Figure represents the approximated perturbed algebraic connectivity
where the node 20 is initially an articulation one (
on Figure (a)). We can confirm that the algebraic connectivity
increases and is greater than
after t = 1.9. This indicates the proposed control law Equation (Equation22
(22)
(22) ) restores the bi-connectivity of the network and Equation (Equation14
(14)
(14) ) preserves it.
Figure 7. Snapshots of simulation 1. (a) Initial configuration (t = 0). (b) Node 20 is restored at t = 1.9 and (c) Final configuration at t = 10.
Next, we examine the effects of the modified restoration algorithm Equation (Equation30(30)
(30) ). The time threshold
is set as
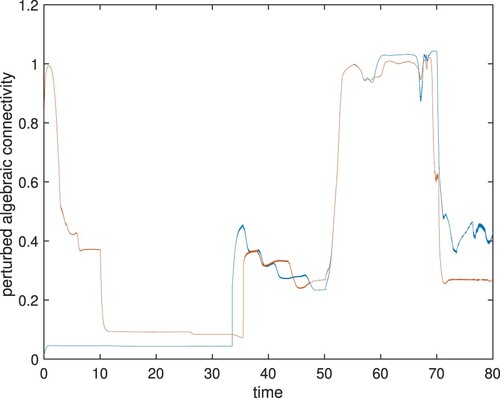
. Figure represents snapshots of the initial configuration t = 0 (Figure (a)), at time t = 20 when the robots move to restore the bi-connectivity (Figure (b)), and at time t = 80 when the bi-connectivity is restored (Figure (c)). Figure represents the approximated perturbed algebraic connectivity
and
, where node 20 is an articulation and node 1 is not an articulation initially. We can confirm that the algebraic connectivity
increases and greater than
after t = 30. The algebraic connectivity
once becomes less than
at t = 10 and becomes greater than
after t = 30. It indicates that node 1 becomes an articulation node once to robustify the network structure around node 20, and it resumes itself after node 20 becomes a non-articulation one.
5. Conclusion
In this paper, we proposed control methods to preserve and restore the bi-connectivity of the multi-robot network, in preparation for a failure of the robot. We introduced the concept of perturbed algebraic connectivity which reflects the connectivity of the graph after a node is removed, and we considered an artificial potential control to preserve the bi-connectivity holding the sufficient condition we derived. To restore the bi-connectivity when the network becomes uni-connected, heuristic control methods were proposed and possibilities and limitations of the methods were discussed. Results of numerical simulations illustrated the effectiveness of the proposed control method.
Future works are as follows. A sufficient condition to achieve the bi-connectivity restoration has not been analysed yet. Theoretical analysis and improvements for the bi-connectivity restoration control remain as future works. Wireless communication quality has not been discussed in this study, in spite of the fact that network connectedness is threatened by poor signal quality due to interference and fading. Evaluations of signal quality via experiments or electromagnetic simulations will be helpful to demonstrate and improve the effectiveness of the proposed control method.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
Notes on contributors
T. Murayama
T. Murayama received the Ph.D. degree in engineering from Kobe University in 2012. In 2023, he joined National Institute of Technology, Wakayama College as an assistant professor. Since 2016, he is an associate professor. From 2019 to 2020, he was a visiting researcher at Department of Sciences and Methods for Engineering, University of Modena and Reggio Emilia. He is a member of IEEE and SICE.
References
- Cortes J, Martinez S, Karatas T, et al. Coverage control for mobile sensing networks. IEEE Trans Rob Autom. 2004;20(2):243–255.
- Zavlanos M, Pappas G. Distributed connectivity control of mobile networks. IEEE Trans Rob. 2008;24(6):1416–1428.
- Sabattini L, Chopra N, Secchi C. Decentralized connectivity maintenance for cooperative control of mobile robotic systems. Int J Rob Res. 2013;32(12):1411–1423.
- Zareh M, Sabattini L, Secchi C. Decentralized biconnectivity conditions in multi-robot systems. In: 2016 IEEE 55th Conference on Decision and Control; Las Vegas (NV); 2016. p. 99–104.
- Kata H, Ueno S. Connectivity maintenance with application to target search. SICE JCMSI. 2021;14(2):22–29.
- Murayama T. Bi-connectivity improvement and preservation for multi-robot network using perturbed algebraic connectivity. In: SICE Annual Conference (SICE2021); 2021. p. 394–399.
- Yang P, Freeman R, Gordon G, et al. Decentralized estimation and control of graph connectivity in mobile sensor networks. In: American Control Conference; Seattle; 2008. p. 2678–2683.
- Murayama T, Sabattini L. Robustness of multi-robot systems controlling the size of the connected component after robot failure. In: Proceeding on 21st IFAC World Congress; Online; 2020. p. 3199–3205.
- Murayama T, Sabattini L. Preservation of giant component size after robot failure for robustness of multi-robot network. In: The 15th International Symposium on Distributed Autonomous Robotic Systems (DARS); 2021.
- Giordano PR, Franchi A, Secchi C, et al. A passivity-based decentralized strategy for generalized connectivity maintenance. Int J Robot Res. 2013;32(3):299–323.
- Bollobás B. Random graphs. 2nd ed. Cambridge: Cambridge University Press; 2001.
- Moreau L. Stability of continuous-time distributed consensus algorithms. In: 2004 43rd IEEE Conference on Decision and Control, Paradise Island, Bahamas; 2004. p. 3998–4003.
Appendix. Proof of Theorem 3.1
For simplicity, we assume the number of the connected components M = 2 from the monotonicity of the perturbed algebraic connectivity, and we write the perturbed algebraic connectivity as since it is obvious that we discuss the articulation node i in this proof. Defining
and
where
and
, we get
(A1)
(A1) if
, from Equation (Equation10
(10)
(10) ). Note the parameter β is in the finite set:
(A2)
(A2) since
should be an integer. The perturbed algebraic connectivity
is in the interval
(A3)
(A3) with assuming
, since
is the minimum solution of the algebraic Equation (EquationA1
(A1)
(A1) ). Note that the function
which denotes the left side of Equation (EquationA1
(A1)
(A1) ) is monotonically increasing in the interval Equation (EquationA3
(A3)
(A3) ).
To find the maximum of the perturbed algebraic connectivity as a function of the valuables α and β, we analyse the gradients
and
. Considering the implicit function theorem, we get
(A4)
(A4) With some calculations substituting the function
, we get
and
(A5a)
(A5a)
(A5b)
(A5b)
Thus, the stationary points satisfy the relations, as
(A6a)
(A6a)
(A6b)
(A6b)
Here, the candidates of the stationary points imply
(A7)
(A7) this shows the fact that
(A8)
(A8) Next, we discuss the stationary set
is whether the extremum or the saddle with respect to the function
. If the set
is the maximum, then the maximum perturbed algebraic connectivity is
from Equation (EquationA6a
(A6a)
(A6a) ). If the set
is the minimum, then the maximum perturbed algebraic connectivity is
with
. This conflicts with the fact that
implies the corresponding connected component is disconnected from the node i. If the set
is the saddle, then the maximum perturbed algebraic connectivity is
with
and
. Substituting
into the second condition of Equation (EquationA6a
(A6a)
(A6a) ), we get
(A9)
(A9) and substituting this into Equation (EquationA1
(A1)
(A1) ), we get
(A10)
(A10) Since
is greater than
for all
, Equation (EquationA10
(A10)
(A10) ) is the maximum perturbed algebraic connectivity when the node i is not an articulation.