?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
This study deals with the problem of the state estimation for discrete-time memristive neural networks with time-varying delays, where the output is subject to randomly occurring denial-of-service attacks. The average dwell time is used to describe the attack rules, which makes the randomly occurring denial-of-service attack more universal. The main purpose of the addressed issue is to contribute with a state estimation method, so that the dynamics of the error system is exponentially mean-square stable and satisfies a prescribed
disturbance attenuation level. Sufficient conditions for the solvability of such a problem are established by employing the Lyapunov function and stochastic analysis techniques. Estimator gain is described explicitly in terms of certain linear matrix inequalities. Finally, the effectiveness of the proposed state estimation scheme is proved by a numerical example.
1. Introduction
As we all know, with the rapid development of automation and information technology in today's society, artificial intelligence (AI) has become a research hot-spot in various fields, and artificial neural networks (ANNs), as the one of the most important part of artificial intelligence, have also been widely concerned (Fu & Chai, Citation2007; Rego & Araújo, Citation2021; Song et al., Citation2007). ANNs are inspired by biological nervous system, which provides a new solution for modelling, control and optimization of nonlinear systems. However, considering that the research objects are more and more complex and the calculation scale is more and more large, the traditional resistors can no longer meet the practical needs because of their inherent physical constraints. Therefore, a device with smaller physical size and higher integration is urgently needed.
In 1971, the existence of a two-port component is described in Chua (Citation1971) and named memristor. In 2008, HP Lab completed the physical realization of memristor for the first time. Since then, memristor has attracted the attention of many scholars because of its memory function, extremely low power consumption, nano-scale size and many other advantages. The memory characteristics and learning function of memristors make the neural networks (NNs), composed of memristors, more similar to human brain, which brings new dawn for the development of NNs. Recurrent neural networks (RNNs) using memristors instead of resistors can achieve higher integration, the so-called memristive neural networks (MNNs) are widely valued in information processing, pattern recognition, brain-like research and other fields, and a number of numerous research on MNNs have emerged (Cao et al., Citation2020; Guo et al., Citation2015; Liu et al., Citation2018; Strukov et al., Citation2008; Wang et al., Citation2017; Yang et al., Citation2015; Zhang & Shen, Citation2013). However, it should be pointed out that a large amount of existing literatures are about continuous-time MNNs (CMNNs). Although the study of discrete-time MNNs (DMNNs) has more practical significance in engineering practice, DMNNs are still in a relatively neglected state compared with the CMNNs because of the failure to find a appropriate method to deal with state-related parameters.
The research of memristor neural network mainly includes two aspects: finding more economical materials and analysing the dynamics of systems. At present, there have been a large number of research on the dynamic behaviour analysis of CMNNs, but the related results with discrete-time are much less (Lv et al., Citation2021; Rakkiyappan et al., Citation2015; Xiao & Zeng, Citation2018; Xin et al., Citation2019; Zhu et al., Citation2018). It is worth mentioning that the problem of state estimation has always been a hot topic in the study of complex networks. In practice, it is impossible or even unrealistic to know the state of neurons in the system directly. Therefore, how to estimate the state of internal neurons effectively based on the available measurement information has important research significance. And there have been many achievements on the state estimation of NNs (Huang et al., Citation2008; Ji et al., Citation2018; Liu et al., Citation2020; Rakkiyappan et al., Citation2015; Shen et al., Citation2011; Wang & Xue, Citation2018; Wang et al., Citation2005; Wang et al., Citation2012; Zou et al., Citation2015). Wang et al. (Citation2005) Studied the state estimation problem of neural networks with time-varying delays. The robust state estimation problem for a class of uncertain NNs with time-varying delay is studied in Huang et al. (Citation2008). The state estimation problem of a class of DMNNs under random mixed delay and fading measurements is studied in Liu et al. (Citation2020).
Nowadays, with the development of network communication technology, the activities and communication of the whole society depend on electronic technology. It is well known that many parts of communication network (such as sensors, controllers, etc.) are connected through shared media (Chen et al., Citation2013; Clark et al., Citation2012; Guan et al., Citation2016). However, due to the existence of public parts, attackers can enter the network through these vulnerable units to maliciously destroy the transmission data, resulting in the interruption of system stability. With the advance of communication technology, the ability of attackers to launch network attacks is also improving, and the forms of attacks are more complex and serious. In the past few years, the network security of complex networks has become a research focus. In the network without security protection device, attackers will maliciously intercept, tamper with and destroy the communication data in the transmission process, so as to destroy the stability of plants or move plants along the targets of the attackers (Ding et al., Citation2017; Ge et al., Citation2019; Liu et al., Citation2021; Yu & Yuan, Citation2020; Zhan et al., Citation2013; Zhao et al., Citation2020; Zhang et al., Citation2020). Generally, cyber-attacks are divided into three types (Ding et al., Citation2018): denial of service (DoS) attacks (Cao et al., Citation2021; Zhang et al., Citation2019), deception attacks (Teixeira et al., Citation2015; Yuan et al., Citation2021) and replay attacks (Huang et al., Citation2020; Zhu & Martinez, Citation2014).
DoS attacks are one of the most common and threatening attack types. For the networks with high real-time requirements, DoS attacks hinder the timeliness of data transmission, which not only reduces system performance, but even damages the stability of the entire system. There have been a lot of research work on DoS attacks. In Befekadu et al. (Citation2015), the author uses Markov model to control random DoS attacks, while in Amin et al. (Citation2009), the author uses Bernoulli distribution to describe them. In DoS attacks, an attacker can temporarily interrupt the connection between the systems and the internet, affecting the transmission of data packets. In addition to being described using Bernoulli or Markov models, such attacks have appropriate frequency and duration (Ding et al., Citation2021; Song et al., Citation2020). The duration and frequency of DoS attacks are clearly described in Persis and Tesi (Citation2015), and the stability of closed-loop system is studied on this basis.
Based on the above considerations, this paper aims to study the state estimation problem of DMMNs with time delay under DoS attack. And Bernoulli model is established to describe the randomness of DoS attacks. In addition, considering the duration and frequency of attacks, the switching between attacks and non-attacks is described by the switching theory. By using stochastic analysis technique and linear matrix inequalities, the sufficient conditions satisfying
performance are obtained, and the explicit expression of estimator gain is given. The main contributions of this paper as follows: (1) The
state estimation problem of DMNNs with time-varying delays and randomly occurring DoS attacks is studied; (2) According to the theory of switched systems, depending on the frequency and duration of DoS attacks, the sufficient conditions that the error system can satisfy the exponentially mean-square stability and
performance are obtained; (3) The estimator gain is obtained through a set of linear matrix inequalities. Finally, a simulation example is given to illustrate the effectiveness of the proposed estimator mechanism.
The remainder of this article is organized as follows, with the problem description and related preparation described in Section 2. The main content is in Section 3, including the sufficient conditions for the error system to satisfy the mean square exponential stability, the sufficient conditions for the error system to satisfy the performance index and the expression of the estimator gain. A simulation example is given in Section 4 to prove the effectiveness of the proposed method. Finally, the final conclusion is given in Section 5.
Notation: Unless otherwise specified, the notation used is fairly standard. and
denote the n-dimensional Euclidean space and the set of all
real matrices, respectively.
is the space of square-summable n-dimensional vector functions over
. The notation
(respectively, X>Y) where X and Y are symmetric matrices, means that X−Y is positive semi-definite (respectively, positive definite). I is used to represent the identity matrix with matching dimensions. The notation P>0 means that P is positive definite matrix.
represents the transpose of A.
stands for a block-diagonal matrix.
represents the expectation. The symbol * indicates the symmetric term of a matrix.
2. Problem formulation
Consider DMNNs with time-varying delays in following form:
(1)
(1) where
and
donate the neuron state and the measurement output, respectively;
is the network output;
represents the self-feedback matrix;
and
are the connection weight matrix, the delay-dependent connection weight matrix, respectively;
is the external disturbance input belonging to
; L is the known disturbance intensity matrices with appropriate dimensions; C, G and M are known real matrices with appropriate dimensions;
and
are the nonlinear functions of the neuron activation function, which are not delay-dependent and delay-dependent, respectively;
is the time-varying transmission delays and satisfies
(2)
(2) where
and
are the upper and lower bounds of the time-varying delays, respectively,and they are the positive integers. The initial condition of (Equation1
(1)
(1) ) has the form
for
.
According to the similar analysis (Liu et al., Citation2018), the state can be rewritten as:
(3)
(3) where
,
,
,
,
,
, here
,
,
are known scalars, H,
,
and
are known real constant matrices,
satisfies that
.
Furthermore, the data may be attacked during transmission, and the attack model can be describe as follows:
(4)
(4) where
is the information received by the estimator actually. The stochastic variable
is a stochastic variable and satisfying Bernoulli distribute white sequence, the form as follows:
(5)
(5) where
are known constants.
Remark 2.1
Cyber-attacks are generally divided into the DoS attacks, the deception attacks and reply attacks. The adversary prevents the estimation from receiving sensor information to carry out DoS attacks. In this paper, the randomly occurring behaviours of the DoS attacks are described by Bernoulli distribute white sequences with known conditional probability, and the estimator receives the normal measurements when . In this article, we consider that the state of the system is switched between the occurrence of an DoS attacks and the occurrence of no DoS attacks. Denote the time instant, at which DoS attacks are launched by malicious adversaries, as
.
Based on the actually received signal , the following state estimator is proposed to estimate the neuron state
:
(6)
(6) where
is the estimate of the state
,
represents the estimate of the output
, and K is the estimator gain to be designed.
The estimation error can be described as:
(7)
(7) where
,
,
,
and
is the output estimation error. And based on setting
, we have the following function:
(8)
(8) where
Here, we first introduce the following assumption and definition, and then go further.
Assumption 2.1
The neuron activation functions and
satisfy
and
(9)
(9)
(10)
(10) where
,
,
and
are constant matrices.
Assumption 2.2
Denote the number of on/off DoS attacks occurring on the interval as
, there exist the chatter bound
and average dwell-time
satisfy:
(11)
(11)
Remark 2.2
In this article, the system is considered as a switching system involving that the attack is active or silent. In order to make sure stability, the frequency and average dwell time of DoS attack are constrained as shown in Assumption 2.2. Denote the time instant, at which DoS attacks are launched by malicious adversaries, as . A basic problem is to determine a minimum
so that the system can meet the prescribed performance index.
Our main idea in this article is to design an appropriate estimator (Equation6(6)
(6) ) such as:
System (Equation8
(8)
(8) ) with
is exponentially mean-square stable.
Under zero initial conditions, for given disturbance attention level
and all nonzero
(12)
(12)
3. Main results
In this section, the state estimation of the augmented system (Equation8
(8)
(8) ) is addressed by utilizing the Lyapunov stability analysis approach. To start with, we give the following useful lemmas that will be needed for the subsequent derivation in this paper.
Lemma 3.1
Schur complement
Given constant matrices where
and
, then
if and only if
Lemma 3.2
S-procedure
Let and E be real matrices with appropriate dimensions, and
. Then, the inequality
holds if and only if there exists a scalar
such that
or, equivalently,
Lemma 3.3
Given scalars , if exists a Lyapunov function
such that the following
hold, where
,
. Then for any switching signal, the system (Equation8
(8)
(8) ) is exponentially mean-square stable with the average dwell-time
Sufficient conditions for the augmented system (Equation8(8)
(8) ) to satisfy
performance constraint (Equation12
(12)
(12) ) are established in the following results.
Theorem 3.1
Let state estimation gain K be given. The system (Equation8(8)
(8) ) with
is exponentially mean-square stable if there exist matrices
, Q>0, and scalars
,
,
such that:
(13)
(13) and the average dwell-time
satisfy
(14)
(14) where
Proof.
Select the following Lyapunov functional candidate:
(15)
(15) where
(16)
(16)
(17)
(17)
(18)
(18) For the convenience of analysis,
is used to represent the switching time sequence of switching signals
for
. Then, under
, letting
, along the trajectory of system (Equation8
(8)
(8) ), we have
(19)
(19) Similarly, it follows that
(20)
(20) and
(21)
(21) Subsequently, according to (Equation15
(15)
(15) ), (Equation19
(19)
(19) )–(Equation21
(21)
(21) ), we can easily access to that
(22)
(22) where
Next, we deduce from Assumption 2.1 that the nonlinear functions
and
satisfy
(23)
(23) It is evident from (Equation22
(22)
(22) ) and (Equation23
(23)
(23) ) that
(24)
(24)
can obviously be obtained, which corresponds to Lemma 3.3. Therefore, it can be concluded that the system (Equation8
(8)
(8) ) with
is exponentially mean-square stable, which ends the proof of Theorem 3.1.
Theorem 3.2
Let K and disturbance attention level be given. Under the zero initial condition, the system (Equation8
(8)
(8) ) is exponentially mean-square stable with
and satisfies
performance constraint (Equation12
(12)
(12) ) for all nonzero
if there exist matrices
, Q>0, and scalars
,
,
such that:
(25)
(25)
(26)
(26) and the average dwell-time
satisfy
(27)
(27) where
and other parameters are defined as Theorem 3.1.
Proof.
Next, the performance of system (Equation8
(8)
(8) ) is investigated. Consider the same Lyapunov functional as (Equation15
(15)
(15) ) is chosen and (Equation25
(25)
(25) ), we have
(28)
(28) where
In what follows, let us investigate the impact of switches induced by DoS attacks. On the interval
, the switching instants are donated as
. Since there are only two states of the system, namely, normal transmission state and DoS attacked, the following proof is discussed in two cases: (1) donating intervals without switches as
; (2) an existing switch
.
Case (1): Intervals without switches, it follows directly from (Equation28
(28)
(28) ) that
(29)
(29) Case (2): Suppose there is a switch from instant
to
, we have
(30)
(30) where
represents the number of on/off DoS attacks occurring on the interval
. And then
(31)
(31) Invoking (Equation27
(27)
(27) ) and the definition of the average dwell-time,
(32)
(32) which implies that
Under zero initial condition and
, then we have
(33)
(33) the proof of Theorem 3.2 is completed.
Based on the above theorems, the desired estimator is designed as follow.
Theorem 3.3
Let the disturbance attention level be given. Under the zero initial condition, the system (Equation8
(8)
(8) ) is exponentially mean-square stable and satisfies
performance constraint (Equation12
(12)
(12) ) for all nonzero
if there exist matrices
, Q>0, Y >0 and positive scalars
,
,
, ϑ such that
(34)
(34)
(35)
(35) where
and other parameters are defined as Theorem 3.1. If the foregoing conditions hold, a desired estimator gain is given by
(36)
(36)
Proof.
Donate
According to (Equation36
(36)
(36) ), we have that from (Equation34
(34)
(34) )
(37)
(37) where
Then, by using S-procedure, the (Equation37
(37)
(37) ) can be described as follow
(38)
(38) where
. Rearrange (Equation38
(38)
(38) )
(39)
(39) Pre-multiplying and poet-multiplying (Equation39
(39)
(39) ) by
and its transpose, one can find that condition (Equation34
(34)
(34) ) guarantees the (Equation25
(25)
(25) ) by Lemma 3.1. the augmented system (Equation8
(8)
(8) ) is exponentially mean-square stable and satisfies
performance constraint, and the appropriate estimator gain can be obtained.
Remark 3.1
This article aims to study the state estimation problem of discrete-time delayed MNNs subject to DoS attacks. For DMNNs with time-varying delays, considering the DoS attack with a certain success probability, the frequency of DoS is described according to the switching system theory. In a word, a new unified framework is established to account for the
state estimation of the DMNNs with time-varying delays and randomly occurring DoS attacks.
4. Illustrative example
In this section, a numerical example is given to illustrate the effectiveness of the proposed method. Consider DMNNs (Equation1(1)
(1) ) with parameters as
and other paraments are given as
The activation functions
and
are chosen as
which satisfy the Assumption 2.1 with
In the example, the parament of DoS attacks are taken as
, the disturbance attenuation level
. The discrete delays are set as
, then we have
and
.
Solving the Theorem 3.3, we can obtain the feasible solution:
Case (a):
, there is no DoS attack
Case (b):
, there exist DoS attack
In the simulation, the exogenous disturbances are chosen as . The initial values of the neuron state are random values and obey the uniform distribution on
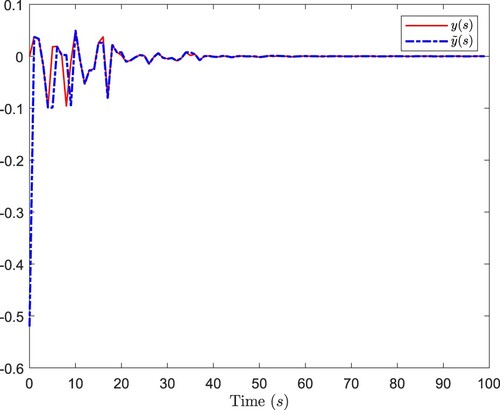
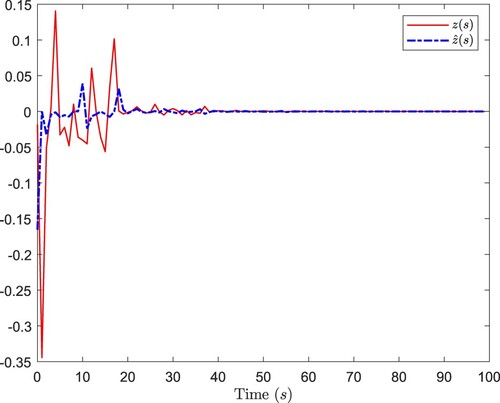
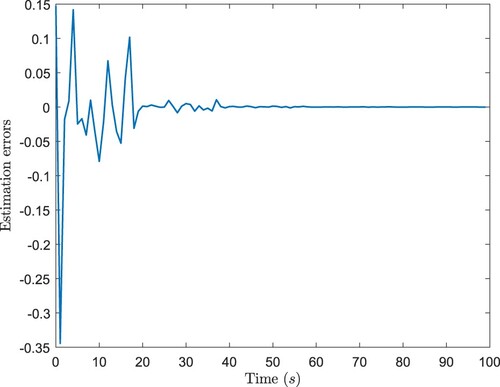
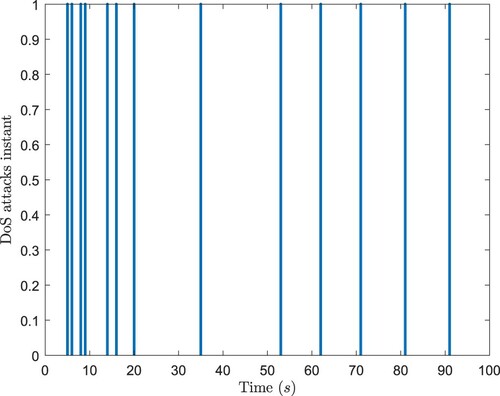
. Figures show simulation results. Figure plots the ideal measurements output and the received signals of the estimator. Figure describes
and its estimation
. Figure depicts the estimation errors. And Figure shows the instants of the DoS attacks. It can be indicated that, the proposed estimator could provide satisfactory state estimations for DMNNs under the DoS attacks.
5. Conclusions
In this paper, the state estimation problem of a class of DMNNs with time-varying delay subject to DoS attacks is studied. Using the attacks' frequency and durations to describe DoS attacks, the modelled network can be essentially described as a switched system that handles between DoS attacks and no DoS attacks. By using Lyapunov stability theorem, the system satisfies the mean-square exponential stability and
performance index, and a set of linear matrix inequalities are used to express the sufficient conditions for the system to satisfy the target performance. Finally, a simulation example is given to verify the effectiveness of the results. In the future other types of cyber-attacks can be considered instead of DoS attacks. What needs to be made clear is that how to consider cyber-attacks and network security issues in complex networks and reduce the impact of attacks deserves further study.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
References
- Amin, S., Cárdenas, A. A., & Sastry, S. S. (2009). Safe and secure networked control systems under denial-of-service attacks. In Hybrid systems: Computation and control, 12th international conference (Vol. 5469, pp. 31–45). Springer.
- Befekadu, G. K., Gupta, V., & Antsaklis, P. J. (2015, December). Risk-sensitive control under markov modulated denial-of-service (DoS) attack strategies. IEEE Transactions on Automatic Control, 60(12), 3299–3304. https://doi.org/10.1109/TAC.2015.2416926
- Cao, E., Zhang, B., Cai, Z., Han, Q., & Wang, B. (2021). Observer-based state feedback H∞ control for offshore steel jacket structures under denial-of-service attacks. ISA Transactions, 115(8), 46–60. https://doi.org/10.1016/j.isatra.2021.01.006
- Cao, Y., Sun, B., Guo, Z., Huang, T., Yan, Z., & Wen, S. (2020). Global stabilization of memristive neural networks with leakage and time-varying delays via quantized sliding-mode controller. Neural Processing Letters, 52(3), 2451–2468. https://doi.org/10.1007/s11063-020-10356-y
- Chen, J., Li, J., & Lai, T. H. (2013, September). Energy-efficient intrusion detection with a barrier of probabilistic sensors: Global and local. IEEE Transactions Wireless Communications, 12(9), 4742–4755. https://doi.org/10.1109/TW.2013.072313.122083
- Chua, L. (1971, September). Memristor-the missing circuit element. IEEE Transactions on Circuit Theory, 18(5), 507–519. https://doi.org/10.1109/TCT.1971.1083337
- Clark, A., Bushnell, L., & Poovendran, R. (2012). A passivity-based framework for composing attacks on networked control systems. 2012 50th Annual Allerton conference on communication, control, and computing (Allerton), Monticello, IL, USA (pp. 1814–1821). IEEE.
- Ding, D., Han, Q., Ge, X., & Wang, J. (2021, January). Secure state estimation and control of cyber-physical systems: A survey. IEEE Transactions on Systems, Man, and Cybernetics-Systems, 51(1), 176–190. https://doi.org/10.1109/TSMC.6221021
- Ding, D., Han, Q., Xiang, Y., Ge, X., & Zhang, X. (2018). A survey on security control and attack detection for industrial cyber-physical systems. Neurocomputing, 275(1), 1674–1683. https://doi.org/10.1016/j.neucom.2017.10.009
- Ding, D., Wang, Z., Ho, D. W. C., & Wei, G. (2017). Distributed recursive filtering for stochastic systems under uniform quantizations and deception attacks through sensor networks. Automatica, 78(1), 231–240. https://doi.org/10.1016/j.automatica.2016.12.026
- Fu, Y., & Chai, T. (2007, May). Neural-network-based nonlinear adaptive dynamical decoupling control. IEEE Transactions on Neural Networks, 18(3), 921–925. https://doi.org/10.1109/TNN.2007.891588
- Ge, X., Han, Q., Zhong, M., & Zhang, X. (2019). Distributed Krein space-based attack detection over sensor networks under deception attacks. Automatica, 109(7), 108557. https://doi.org/10.1016/j.automatica.2019.108557
- Guan, X., Yang, B., Chen, C., Dai, W., & Wang, Y. (2016, January). A comprehensive overview of cyber-physical systems: From perspective of feedback system. IEEE/CAA Journal of Automatica Sinica, 3(1), 1–14. https://doi.org/10.1109/JAS.2016.7373757
- Guo, Z., Yang, S., & Wang, J. (2015, June). Global exponential synchronization of multiple memristive neural networks with time delay via nonlinear coupling. IEEE Transactions on Neural Networks and Learning Systems, 26(6), 1300–1311. https://doi.org/10.1109/TNNLS.2014.2354432
- Huang, H., Feng, G., & Cao, J. (2008, August). Robust state estimation for uncertain neural networks with time-varying delay. IEEE Transactions on Neural Networks, 19(8), 1329–1339. https://doi.org/10.1109/TNN.2008.2000206
- Huang, J., Zhao, L., & Wang, Q. (2020). Adaptive control of a class of strict feedback nonlinear systems under replay attacks. ISA Transactions, 107(11), 134–142. https://doi.org/10.1016/j.isatra.2020.08.001
- Ji, H., Zhang, H., Li, C., Senping, T., Lu, J., & Wei, Y. (2018). H∞ control for time-delay systems with randomly occurring nonlinearities subject to sensor saturations, missing measurements and channel fadings. ISA Transactions, 75(5), 38–51. https://doi.org/10.1016/j.isatra.2018.02.015
- Liu, H., Wang, Z., Shen, B., & Dong, H. (2020, February). Delay-distribution-dependent H∞ state estimation for discrete-time memristive neural networks with mixed time-delays and fading measurements. IEEE Transactions on Cybernetics, 50(2), 440–451. https://doi.org/10.1109/TCYB.6221036
- Liu, H., Wang, Z., Shen, B., & Liu, X. (2018, August). Event-triggered H∞ state estimation for delayed stochastic memristive neural networks with missing measurements: The discrete time case. IEEE Transactions on Neural Networks and Learning Systems, 29(8), 3726–3737. https://doi.org/10.1109/TNNLS.2017.2728639
- Liu, R., Hao, F., & Yu, H. (2021, December). Optimal SINR-based DoS attack scheduling for remote state estimation via adaptive dynamic programming approach. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 51(12), 7622–7632. https://doi.org/10.1109/TSMC.2020.2981478
- Lv, X., Cao, J., & Rutkowski, L. (2021). Dynamical and static multisynchronization analysis for coupled multistable memristive neural networks with hybrid control. Neural Networks, 143(1), 515–524. https://doi.org/10.1016/j.neunet.2021.07.004
- Persis, C. D., & Tesi, P. (2015, November). Input-to-state stabilizing control under denial-of-service. IEEE Transactions on Automatic Control, 60(11), 2930–2944. https://doi.org/10.1109/TAC.2015.2416924
- Rakkiyappan, R., Chandrasekar, A., & Cao, J. (2015, September). Passivity and passification of memristor-based recurrent neural networks with additive time-varying delays. IEEE Transactions on Neural Networks and Learning Systems, 26(9), 2043–2057. https://doi.org/10.1109/TNNLS.2014.2365059
- Rego, R. C. B., & Araújo, F. M. U. (2021, August). Nonlinear control system with reinforcement learning and neural networks based lyapunov functions. IEEE Latin America Transactions, 19(8), 1253–1260. https://doi.org/10.1109/TLA.2021.9475855
- Shen, B., Wang, Z., & Liu, X. (2011, January). Bounded H∞ synchronization and state estimation for discrete time-varying stochastic complex networks over a finite horizon. IEEE Transactions on Neural Networks, 22(1), 145–157. https://doi.org/10.1109/TNN.2010.2090669
- Song, J., Ding, D., Liu, H., & Wang, X. (2020). Non-fragile distributed state estimation over sensor networks subject to DoS attacks: The almost sure stability. International Journal of Systems Science, 51(6), 1119–1132. https://doi.org/10.1080/00207721.2020.1752843.
- Song, Y., Chen, Z., & Yuan, Z. (2007, March). New chaotic PSO-based neural network predictive control for nonlinear process. IEEE Transactions on Neural Networks, 18(2), 595–601. https://doi.org/10.1109/TNN.2006.890809
- Strukov, D. B., Snider, G. S., Stewart, D. R., & Williams, R. S. (2008). The missing memristor found. Nature, 453(7191), 80–83. https://doi.org/10.1038/nature06932
- Teixeira, A., Shames, I., Sandberg, H., & Johansson, K. H. (2015). A secure control framework for resource-limited adversaries. Automatica, 51(6), 135–148. https://doi.org/10.1016/j.automatica.2014.10.067
- Wang, H., Duan, S., Huang, T., Wang, L., & Li, C. (2017, March). Exponential stability of complex-valued memristive recurrent neural networks. IEEE Transactions on Neural Networks and Learning Systems, 28(3), 766–771. https://doi.org/10.1109/TNNLS.2015.2513001
- Wang, H., & Xue, A. (2018). Adaptive event-triggered H∞ filtering for discrete-time delayed neural networks with randomly occurring missing measurements. Signal Processing, 153(6), 221–230. https://doi.org/10.1016/j.sigpro.2018.07.027
- Wang, Z., Ho, D. W. C., & Liu, X. (2005, January). State estimation for delayed neural networks. IEEE Transactions on Neural Networks, 16(1), 279–284. https://doi.org/10.1109/TNN.2004.841813
- Wang, Z., Shen, B., & Liu, X. (2012). H∞ filtering with randomly occurring sensor saturations and missing measurements. Automatica, 48(3), 556–562. https://doi.org/10.1016/j.automatica.2012.01.008
- Xiao, Q., & Zeng, Z. (2018, June). Lagrange stability for T–S fuzzy memristive neural networks with time-varying delays on time scales. IEEE Transactions on Fuzzy Systems, 26(3), 1091–1103. https://doi.org/10.1109/TFUZZ.91
- Xin, Y., Li, Y., Huang, X., & Cheng, Z. (2019, February). Quasi-synchronization of delayed chaotic memristive neural networks. IEEE Transactions on Cybernetics, 49(2), 712–718. https://doi.org/10.1109/TCYB.2017.2765343
- Yang, S., Guo, Z., & Wang, J. (2015, July). Robust synchronization of multiple memristive neural networks with uncertain parameters via nonlinear coupling. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 45(7), 1077–1086. https://doi.org/10.1109/TSMC.2014.2388199
- Yu, Y., & Yuan, Y. (2020). Event-triggered active disturbance rejection control for nonlinear network control systems subject to DoS and physical attacks. ISA Transactions, 104(16), 73–83. https://doi.org/10.1016/j.isatra.2019.05.004
- Yuan, H., Guo, Y., & Xia, Y. (2021). Event-based distributed filtering against deception attacks for sensor networks with quantization effect. ISA Transactions. https://doi.org/10.1016/j.isatra.2021.08.009 .
- Zhan, Z., Xu, M., & Xu, S. (2013, November). Characterizing honeypot-captured cyber attacks: Statistical framework and case study. IEEE Transactions on Information Forensics and Security, 8(11), 1775–1789. https://doi.org/10.1109/TIFS.2013.2279800
- Zhang, D., Liu, L., & Feng, G. (2019, April). Consensus of heterogeneous linear multiagent systems subject to aperiodic sampled-data and dos attack. IEEE Transactions on Cyberetics, 49(4), 1501–1511. https://doi.org/10.1109/TCYB.6221036
- Zhang, G., & Shen, Y. (2013, October). New algebraic criteria for synchronization stability of chaotic memristive neural networks with time-varying delays. IEEE Transactions on Neural Networks and Learning Systems, 24(10), 1701–1707. https://doi.org/10.1109/TNNLS.5962385
- Zhang, X., Han, Q., Ge, X., & Ding, L. (2020, August). Resilient control design based on a sampled-data model for a class of networked control systems under denial-of-service attacks. IEEE Transactions on Cybernetics, 50(8), 3616–3626. https://doi.org/10.1109/TCYB.6221036
- Zhao, X., Liu, C., & Tian, E. (2020). Finite-horizon tracking control for a class of stochastic systems subject to input constraints and hybrid cyber attacks. ISA Transactions, 104(2), 93–100. https://doi.org/10.1016/j.isatra.2019.02.025
- Zhu, M., & Martinez, S. (2014, March). On the performance analysis of resilient networked control systems under replay attacks. IEEE Transactions on Automatic Control, 59(3), 804–808. https://doi.org/10.1109/TAC.2013.2279896
- Zhu, W., Wang, D., Liu, L., & Feng, G. (2018, August). Event-based impulsive control of continuous-time dynamic systems and its application to synchronization of memristive neural networks. IEEE Transactions on Neural Networks and Learning Systems, 29(8), 3599–3609. https://doi.org/10.1109/TNNLS.2017.2731865
- Zou, L., Wang, Z., Gao, H., & Liu, X. (2015, December). Event-triggered state estimation for complex networks with mixed time delays via sampled data information: The continuous-time case. IEEE Transactions on Cybernetics, 45(12), 2804–2815. https://doi.org/10.1109/TCYB.2014.2386781