Abstract
How did ARPANET or Advanced Research Projects Agency networks, arguably the most expensive invention in history, become the Internet? The US tax-funded ARPANET was tested before being commercialized. Testing included neutralizing civilians in an anti-Communist counterinsurgency with minimal evidence and plausible deniability. Max Weber’s ideal type and social order concepts help describe how occupational status groups (OSGs) tested ever-changing ARPANET derived networks for illegal, unconstitutional spying, while presidential orders dictated ARPANET’s development. After testing, ARPANET was transferred to Defense Communications Agency, cloned in smaller versions and distributed in low-intensity warfare and military base building abroad. As the US telephone system was broken up, Americans sought affordable telephone services from new networked and wireless communication systems. The government did not want to manage growing databanks and ordered ARPANET backbone be commercialized. Merit, IBM, and MCI commercialized the ARPANET’s backbone in a way similar to what Weber described in his first dissertation. Conclusions include 1) ARPANET was convenient for the military since it hid evidence and was non-evident; 2) causes for commercializing the ARPANET differ from other researchers’ findings since ARPANET testing history is acknowledged; and 3) Weber’s theories help frame a plausible account of ARPANET commercialization.
PUBLIC INTEREST STATEMENT
This article describes the ordered steps of the Advanced Research Project Agency networks or ARPANET’s testing, distribution, and privatization into the Internet, framed by Max Weber’s concepts. This article condenses the major elements of my University of Auckland, PhD thesis entitled, Exploiting and Neutralising the “Communist Threat” for the Privatised Internet, supervised by professors Neal Curtis and Luke Goode. The thesis broke new ground in media history by using Max Weber’s social order concept to frame a prehistory that sketched how the world’s most expensive invention, the forerunner to the Internet, the ARPANET, was tested in anti-Communist, counterinsurgency warfare, distributed in the largest US military base-building campaign in history, and commercialized in legislated steps, under orders from the president. This article is illustrated with chronologies that chart the ARPANET into Internet history. Because much of the research was fragmented, the chronologies became a methodological tool to hold the data. Since the chronologies were not included in the thesis, they are used here to illustrate the article.
1. Introduction
Authors present different origin stories for the Internet, likely the world’s most expensive invention that we all depend on, which claims no owner and facilitates the market while having no price tag of its own. Many accounts relate how the Internet’s forerunner, the Advanced Research Projects Agency networks (hereafter ARPANET) or ARPANET backbone as it is often called, was built by the Defense Advanced Research Projects Agency.Footnote1 The milestones of ARPANET’s technical development are already well reported.Footnote2 Before the ARPANET could be put in mission service with the Pentagon, it had to be tested (Packard, Citation2020b). Here, I frame ARPANET's history with Max Weber’s social order and ideal type theories along with his insights into commercial partnerships to posit an analysis for ARPANET’s testing, distribution, and privatization. MacKie-Mason and Varian (Citation1994) described ARPANET’s function: “In the late 1960s, The Advanced Research Projects Administration (ARPA), a division of the U.S. Defense Department, developed the ARPANET to link universities with high-tech defense contractors” (p. 1). Defense contractors included RAND, Michigan Educational Information Research Triad Inc. (MERIT), International Business Machines (IBM), Microwave Communications Inc. (MCI), General Electric (GE) which all contributed to the building, testing, distribution, and commercialization of the ARPANET into the Internet. In his article entitled, The Origin and Nature of the US “Military-Industrial Complex” John Alic (Citation2014) wrote that the US government “channeled money to industry” after WWII when the “US military could no longer expect to control weapons design and development” (p. 66). Channeling trillions of dollars’ worth of tax revenue into military contracts required informational infrastructure like the ARPANET to channell government records and monitor the budgets, as Charles Hitch (Citation1966) a former RAND employee, former comptroller for Secretary of State McNamara, wrote about when he was Treasurer of the University of California system in his book Decision-making for defense. The ARPANET itself acquired a reputation for being the most expensive invention in history, although it is unknown how much taxpayer and private money was invested into it over the decades. Since “no single agency” could afford to pay for all the R&D it became an ongoing project financed by multiple government appropriations and supplemented with private funds (Simpson, Citation1995, p. 465). The term “formally privatized” is used to differentiate the ARPANET backbone, which was developed and privatized in legislative steps, from the ARPANET R&D, which was continuously spun off to private companies throughout ARPANET’s early development and testing phase (1960–1975). ARPANET R&D was always a privatization-project in process and the government did not patent the R&D. However, the government did privatize the ARPANET backbone in legislated steps with deadlines. The US taxpayers paid for the R&D for interactive computers and networks and the government received the first computers made by companies and afterwards, bought computers. Companies commercialized government R&D without the government “recovering” funds from the companies or patenting the technology (US. Congress. Senate. 1970, pp. 736–7). Since ARPANET R&D was paid for with US taxes, it had to pass military tests before it could be put into mission service with the Defense Communications Agency (DCA) or be sold or turned over to a commercial business.Footnote3 Testing included neutralizing civilians suspected of being Communist or having subversive tendencies. ARPANET R&D was not a classified operation, and published research about the academic workforce that pioneered ARPANET R&D was plentiful as acknowledged above, however accounts of ARPANET's history that focus on the milestones of ARPANET technical development in US universities present only part of ARPANET's history. Writing about the intelligence community as a workforce that tested ARPANET in counterinsurgency to neutralize civilians was unconventional, even though the research showed that the intelligence community “really wanted” interactive computers and state-of-the-art networks like ARPANET as part of their technical collection (Nordberg & Asprey 1988). Literature about how the ARPANET invention was tested in anti-Communist counterinsurgency, is fragmented, censored, hidden, scattered, and reported on in different ways by different authors—which is why I used Max Weber’s theories to frame research findings about ARPANET testing, distribution, and formal privatization history. I incorporated contributions from authors like those cited above, with other findings, into a theoretical framework based on Max Weber’s social order and ideal type concepts and his research into commercial partnerships of the Middle Ages. In the “Justification for the approach: answering research questions necessitated using Max Weber’s theories” section below, I discuss how research for answering the research questions convinced me that the findings needed to be couched in Weber’s social order, ideal typology, and commercial partnership concepts. The fragmented literature motivated me to use Weber’s concepts to make the history more cohesive. I interpret Weber’s social order, ideal type concepts, and his insights about commercial partnerships and apply them to the research findings in the “Results: Weber’s Concepts applied to findings to answer research questions.” Appendix A offers an illustration of Max Weber’s Social order as I understand it. Appendix B shows chronologies that hold fragmented research findings from an array of literature. The chronologies follow ARPANET development over time and across geographical areas. They are a reference to show legislative steps that dictated ARPANET’s testing, distribution, and privatization/commercialization into the Internet. At the top of the chronologies are names of major actors. Michigan State University or anything pertaining to Michigan, such as Merit, Ford Motor Company, or Michigan State University Group (MSUG) has its own column as does Microwave Communication Inc. (MCI) , IBM , and the intelligence community (CIA, FBI, NSA, Military intelligence, and many other such agencies).Footnote4 The realms that appear in Weber’s Social Order (Power, Market, and Social honor) correspond to the actors in the chronology. On the left side of the chronologies is a timeline that shows the decades and the presidential administrations. They begin with the 1920–1930 (or the interwar years), 1930–1940 (the Great Depression) and 1940–1950 all. These decades saw the establishment of the National Security Act of 1947 and the change in tax laws (taxes collected from employers or “source” in advance, rather than from taxpayers) that provided the government an assured funding source for multi-year complex military budgets. In the 1950s the chronology shows the president secretly established the National Security Agency and established the Defense Advanced Research Projects Agency (DARPA). In 1959, the Department of Defense (DOD) authorized Directive 5129.33 which ordered DARPA to build a communication system for the Complex (the ARPANET). Even before the Directive was signed, the MSUG had been in South Vietnam, Laos, and Thailand brokering and building microwave networks for public safety operations. By the 1960s there was funding for building the ARPANET. At the same time an eastern counterpart MICHNET (Michigan networks) was being built after Michigan State University Technical Group (or MSUG) returned to Michigan from Vietnam in 1962 (see chronology 1960s-1970). The “Transition phase” chronology (1970–1980) shows ARPANET transferred to DCA (in the mid-1970s) and the many government investigations of intelligence agencies. The “Distribution phase” (1980–1990) shows the DCAnet (ARPANET backbone and DCA networks) expanding into cloned stay-behind nets abroad in LIW. The formal privatization of the ARPANET backbone, NSF-networks, and non-NSF networks into the commercial Internet (by executive orders) is shown in 1990–2000 chronology. The “Personhood phase” of the commercial Internet is noted in the 1900–2000s chronology. The Literature Review discusses the difficulty of researching the literature from this “anything goes” Cold War, counterinsurgency era, when ARPANET was tested, distributed, and privatized.Footnote5 I assembled history from an array of literature by social scientists, lawyers, journalists, and government investigators who (unlike the military) did not have the advantage of large budgets, computers, technical collection, and advanced communication systems to aid their research. Their research was hindered by government secrecy; lack of the kind of networked communications that the military used; government spying; telephone wiretapping, and smearing and censorship of their publications, and with the advent of the commercial Internet, a reduction in the publishing companies that had published these and many other authors’ works. In the “Results: Weber’s Concepts applied to findings to answer research questions” section Weber’s concepts are applied to the findings and the chronologies help to illustrate the analysis. Weber’s social order concept helps interpret how and why the intelligence community workforce (or what Weber called the social honor realm) tested the ARPANET. Weber’s ideal typology helps to describe the growing, changing, and distributed ARPANET or the machine side of the ARPANET invention. Weber’s insights about commercial partnerships help describe how social realm contractors such as Merit, IBM, and MCI formally privatized the ARPANET into the Internet under orders and in legislated steps.
2. Justification for the approach: answering research questions necessitated using Max Weber’s theories
In their article entitled, The Privatization of the Internet’s Backbone Network, Rajiv Shah and Jay Kesan (2007) wrote about why more scrutiny of ARPANET history was needed, citing issues about how the privatization happened, the cost of the Internet, and regulating the commercial Internet. They cited an article by MacKie-Mason and Varian, entitled “The economics of the Internet” which appeared in Dr. Dobb’s Journal (1994, 19 (14): 6–16). Shah and Kesan wrote that ARPANET backbone privatization history:
has not been scrutinized by either academics or the press. The privatization is significant for communication scholars [..]. First, it represents the transfer of an important communication technology to the private sector. The U.S. government spent approximately $160 million in direct subsidies over an 8-year period to fund the backbone network. However, the government likely spent 10 times this amount in developing the Internet through other public funds from state governments, state-supported universities, and the national government (MacKie-Mason & Varian, Citation1994) [.] the government transitioned the backbone network to private control. Unlike other communication technologies, the privatization of the backbone left few regulatory requirements. [.] this has implications for concentration in the backbone industry as well as the government’s ability to regulate the Internet (Shah & Kesan, Citation2007, pp. 93–94).
A year after the Dr. Dobb’s article was published, American University communications professor Christopher Simpson (Citation1995) published National Security Directives of the Reagan and Bush administrations: the declassified history of US political and military policy, 1981–1991. One National Security Decision Directive (NSDD) was about funding for telecommunications security programs in the mid-1980s, during the largest military base-building program in history, as David Vine (Citation2015) wrote about in Base nation: how U.S. military bases abroad harm America and the world. At this time, the ARPANET backbone had been transferred to DCA and was in service to DCAnet. The directive indicated that the cost for securing the military’s telecommunications systems was in the tens of billions of dollars and although the NSA wanted authority over the program “no single agency” could carry the costs to implement it (1995, p. 465). Since no one company or agency funded all the ARPANET expenses, there is no estimate for its value, nor a price tag for the sale of the network, since the backbone was legally transferred from the National Science Foundation (NSF) to Advanced Networks and Services Inc. (a commercial partnership of IBM, Merit, and MCI).
Since ARPANET has a reputation for being the most expensive invention in history, how was the funding justified? During the Cold War, anti-Communism was used to justify funding for counterinsurgency in the US and abroad. US taxes for ARPANET R&D were justified for ongoing anti-Communist, counterinsurgency operations against civilians—not soldiers. Whereas conventional wars were waged by and against trained soldiers, in counterinsurgency, networked and technical communications replaced soldiers and were used to monitor and neutralize civilians in the name of anti-Communism and national security.Footnote6 Targeting alleged and real Communists required surveillance, political intelligence, computers to process the intelligence and networks to transmit the intelligence between advisors in remote locations and commanding officers in the Pentagon, Whitehouse, or elsewhere.
An example of counterinsurgency was the Phoenix program in the Vietnam War described in Douglas Valentine’s (2000) The Phoenix Program. Phoenix was designed to “[.] replace the bludgeon with a scalpel. The key to the operation is precise targeting […] Theoretically, Phoenix’s main tools were good intelligence and good files. The objective of the program was to find out who among the Vietnamese population were Vietcong cadres, and arrest or kill them” (US. Congress. Senate 1973a, p. 56). In funding and furthering the capabilities of this new kind of warfare against political, and then other kinds of activists, both in the US and abroad, the intelligence community was a workforce that collected, processed, stored, and transmitted political intelligence through the new growing and interactive computer networks that were pioneered in the Cold War years.
Since no one company or agency could or would pay for all the R&D, US taxpayers (in what Weber termed the “market” realm) initially paid for it over decades. The military budgets that paid for ARPANET R&D were not well regulated since the intelligence community agents (in what Weber termed the “social honor” realm) were self-styled, self-enforced, self-regulated, and worked on their honor, for the nation’s and their own job, security. The Church Committee reported that government and private funds spent on national security operations were secret and unregulated (US. Senate 1976a). When the NSF turned the ARPANET backbone over to Merit, IBM, and MCI there was no bill of sale or final price tag for this invention; although no estimation of its cost is certain, I argue the cost is higher when the lives that were neutralized for testing this invention are added.
Each research question led to another. In 1975, ARPANET had passed military tests, so why was the ARPANET backbone not commercialized then? Instead, it was transferred into mission service with the DCA and commercialized a decade later. Since the ARPANET turned DCAnet supplied intelligence to combat missions, what happened in that decade? It appears the ARPANET backbone/DCA net was cloned and distributed in low-intensity warfare (LIW) and the largest US military base-building program in history.Footnote7 The 1980s saw the distribution of what Vietnam veteran Jeffery Stein called “stay behind nets” abroad, while microwave networks were built up in the US (Stein & Klare, Citation1973). After that, the government ordered the formal privatization of the ARPANET backbone and allowed Merit, IBM and MCI to commercialize the ARPANET backbone, the National Science Foundation (NSF) and non-NSF networks. Then, the question became: Why did the government allow Merit, IBM, and MCI to privatize the ARPANET backbone and not some other companies?
In seeking answers to these questions, it became clear that information about how the ARPANET R&D was tested in counterinsurgency, distributed in base building, and commercialized through commercial partnership law, was fragmented. The ARPANET Completion Report that was written to summarize ARPANET’s history before it was transferred to DCA net was silent about events that ARPANET had been well positioned to transmit data about in its testing phase. Expenditures on ARPANET were not well documented. The workforce that collected intelligence for testing ARPANET was hard to identify. Authors who researched this transitional network history were at a disadvantage since the government withheld information either by censoring reports (like the Pike report) or through the Freedom of Information Act process or FOIA. The FOIA Act of 1966 restricted public access to government records the same year that the FBI’s COINTELPRO and the CIA’s CHAOS programs began running together.Footnote8 Thus, intelligence collection of taxpayers’ personal information increased, while the citizens’ ability to see the documents collected was restricted. An example of how fragmentation hindered a comprehensive understanding of the ARPANET history emerged from research at the pivotal juncture where ARPANET was transferred to DCA. The ARPANET would have been instrumental in trafficking data about the 1976 Operation Condor car bombing of Chilean economist and former Ambassador to the US Orlando Letelier and his American assistant Ronni Moffitt in Washington, DC. The bombing happened when ARPANET was transferring to the Pentagon. The ARPANET’s ability to track a terrorist attack on US soil, allegedly authorized from Chile, would have been keenly observed by the new head of the CIA, G.H.W. Bush. The Report says nothing about this important terrorist attack in the nation’s capital at the time when ARPANET was on the verge of being put into mission service with DCA or was already in service. The terrorist attack would have been a good test for ARPANET's mission service with the Pentagon since the FBI did not intercept this terrorist attack, leaving ARPANET conveniently available for processing the data shared between Washington and Chile about the bombing. Why did not the FBI intercept the attack and why did not the ARPANET Completion Report discuss the role the ARPANET played in protecting national security from a terrorist attack in the heart of the nation’s capital? Questions like these arose from the research which I could not answer. It became necessary to apply Weber’s social order concept to help hold fragmented history together in spite of missing information and unanswered questions. To represent groups of unknown, unnamed scientists, intelligence agents, and other professionals contracted for national security programs, such as the National Security Agency, I framed the findings with Weber’s social order concepts. Weber’s ideas about occupational status groups (hereafter OSGs) within the social order, differentiated social honor groups (like the intelligence community) from other groups, such as New Deal civil servants like the FCC, who were not backed with the same federal national security “validity” (Galtung) or “legitimate order” (as Weber termed it) that backed Cold War intelligence and military contractors or occupational status groups (OSGs). Intelligence, police, and military OSGs along with OR scientists and economists in private labs, universities, and think tanks usurped the status of New Deal-oriented civilian OSGs. Weber’s concepts helped describe how this happened and the rationale behind it.
Since Weber’s theories were popular in Cold War America, where military R&D was conducted, it was convenient to apply Weber’s theories to the ARPANET history. In the chronologies, one column lists some of Weber’s works as they were translated and published. Weber’s social order and ideal type concepts are discussed in the following sections, along with his insights into historical commercial partnerships. I apply those concepts to the testing, distribution, and formal commercialization history of the ARPANET in the “Results: Weber’s Concepts applied to findings to answer research questions” section. Two of Weber’s theories are discussed below. The social order concept addresses the human workforce who tested, distributed, and formally privatized the ARPANET for national security. The ideal type theory addresses the continuous communication systems hardware and software that the workforce was always improving, testing, and changing. The ARPANET was a machine that was always changing because the workforce tasked with improving the machine both idealized it and were never satisfied with it. Using Weber’s social order and ideal typology together provides a flexible theoretical lens to interpret ARPANET’s phased history.
2.1. Weber’s social order
Weber’s social order concept helped to conceptualize the human side of this continuous communication system or ARPANET based on Weber’s essay “Class, Status, Party” in From Max Weber: essays in sociology (Citation1958, pp. 180–196) and the re-published version of the essay in the two volume, Economy and society: an outline of interpretive sociology (Weber, Citation1978, pp. 1, 305–307, 2, 932–939) edited by Guenther Roth and Claus Wittich. Both sources were widely read in Cold War America.
Appendix A features an illustration of Weber’s social order as I interrupt it. It shows how the social order concept divides society into three realms—the political or power realm, the market, or economic classes realm and the social or social honor realm. Some people circulate through these realms and/or occupy more than one realm at a time. Each realm has a special power and function. The power realm is occupied by the political party and top military leadership, and they have power over political decision-making, military force, corporal punishment, and taxes. Their function is to issue orders. Since Weber saw the world as disenchanted, he thought that human conduct was no longer dictated by customs, religion, or tradition, but rather by orders from political leaders based on ideas about legitimacy or validity, which is what “order” in “social order” refers to. For example, the Department of Defense issued Directive 5129.33 (see chronology 1950–1960). It ordered DARPA to build a continuous communication system for “the exchange of information and advice […] with the military departments, other DOD agencies and appropriate research and development agencies outside the Department of Defense, including private business entities, educational or research institutions or other agencies of Government” (DOD, 1959, p. 2). This order initiated ARPANET R&D. Another example is shown in the illustration when the CIA under “pressure” from the White House initiated the domestic CIA spy operation called CHAOS (1967–1974) at the same time the FBI was running COINTELPRO (1956–1971) (US Senate, 1976b, p. 99). At the same time, the Vietnam War was a staging ground for tests that could not be done in the US, such as the Phoenix Program.
According to the social order concept, working classes and capitalists controlled the commercial market and mass production for mass consumption. The working classes did not have a lot of social standing or education nor much control over how they did their work. The power realm did not trust them. The working classes produced goods for the market, profits for the capitalists, tax revenue for the power realm, and they reproduce themselves. In all this production activity, this realm transparently showed the inequality it produced with a few rich capitalists and many poor people. It generated the tax revenue for the original ARPANET R&D. Here, the focus is mostly on the intelligence or national security workforce or what Weber called the social honor realm actors. These actors were sometimes contractors to the government from market realm companies like IBM, Merit, or MCI. They were tasked with keeping the ARPANET back bone out of the commercial market and using it for their own national security operations, until the President ordered ARPANET backbone to be privatized.
The social honor realm included the intelligentsia or the middle classes. Weber called them “self-styled professionals” or occupational status groups (OSGs); (Weber, Citation1978, p. 1: 305–307, 2:932–939; Packard, Citation2023). The social honor realm had power over lifestyle, community (such as the intelligence community) and hindering the market. They often had family pedigrees, better educational opportunities, were professionals, doctors, scientists, experts, Nobel laureates, and celebrities. Some had degrees, awards, and high security clearances. They set conventions for lifestyle (such as the single head of a household family and a suburban home) and they were a community that shared conventions, like political party membership, attending similar schools, churches, and social functions. Unlike the market realm actors, social realm actors had the power to hinder the market. This power was based on a relationship between the social realm actors and the political party leadership and one of the functions of the social realm—to usurp, conserve, and consume “special goods,” to keep them out of the hands of the perceived enemy or Communist Threat and/or the market (Weber, Citation1978, pp. 2, 937). This entailed either usurping these goods from the enemy or neutralizing the enemies’ ability to use special goods by excluding them from the market and using them for national security. Political leaders trusted social honor realm actors and did not regulate their national security work. They gave them tax revenue and trusted them to use it for national security without regulating how it was spent (US Senate, 1976a, p. 469). They trusted the social realm to keep special goods (like the ARPANET) out of the hands of the Communist threat and out of the market realm, for national security. Weber identified a special good as something like a special fund or a third object that was held jointly in commercial partnerships. In his first dissertation about commercial partnerships in the Middle Ages, he tried to trace the origins of this special fund in the history of maritime general and commercial partnerships but found it difficult since the documents were often unavailable. He got around the research void by examining the available documents in different historic cities and comparing the findings over time. The results were a methodology for Weber’s most famous concept, the ideal type. By looking at samples of available commercial partnership documents over time and across countries, Weber drew conclusions about how the modern firm with its special fund, special goods, or third objects, had emerged from new, legal and contractual forms of commercial partnerships. In a US, Cold War context, many things could be considered a third object or part of a special fund: spy intelligence product; missile systems; high-tech weapons; or the ARPANET invention. Entire university systems were like a special fund because the government funded huge contracts for basic R&D from universities that helped to build ARPANET R&D and adjoining inventions like interactive computers, bilingual computers, protocols, IMPs, software, data processing, and so on. All these special goods went into building ARPANET, a continuous communication system, a technical collection system, or a World Wide Web.
When social realm actors tested rare goods like the ARPANET or withheld it from the market (from commercialization) or usurped special goods from the enemy, they often engaged in dishonorable conduct, counterinsurgency, and neutralizing people and therefore they had to have control over their lifestyle, since they had to appear socially honorable when their profession entailed covert activity, in the name of national security. Unlike the economic classes, self-regulating social realm professionals had the freedom to perform their national security jobs in self-styled ways; however, to maintain their social honor image and status, they had to keep the political party leaders trusting them and funding them, without their covers being blown. Ex-CIA agent Vincent Marchetti described this dichotomy in The Rope Dancer (1974) about the lifestyle of a CIA agent in Cold War suburbia USA.
The social order model applies to the ARPANET in the following ways: The political party ordered the ARPANET be built; social honor realm actors built and tested it and used it for their own purposes—keeping it out of the market and out of enemy hands. Political party leaders ordered that the ARPANET be privatized. The NSF followed orders and turned the ARPANET backbone and NSF networks over to trusted and experienced, social realm contractors (including those who had built Michnet) to commercialize the ARPANET backbone into a privatized and commercialized network that traversed Michnet. These legislative steps that dictated ARPANET’s transition into the Internet are discussed in the Results section below and illustrated in the Chronologies in Appendix B.
Social realm contractors Merit and partners IBM and MCI moved the ARPANET backbone into the market realm and set up new telecommunications companies that were profit making and ongoing. These social realm actors, with permission from the political party and their government employer, transitioned to market realm capitalists and inequality increased in the market realm. As inequality rose, the power realm no longer had to spend so much tax revenue on this expensive invention, but the tax revenue was not spent on social needs to reduce inequality. Party leadership expected the new Internet would be a job creator that would lead the US out of recession, instead military budgets grew along with inequality.
2.2. Weber’s ideal typology
Weber’s (Citation1949) famous, ideal type theory, drawn from his essay “‘Objectivity’ in Social Science and Social Policy” is used to describe the ARPANET or the machine side of this informational infrastructure. Weber’s ideal typology helps to conceptualize the machine side of this continuous communication system, always being improved, cloned, and turned into a distributed system, yet ideally, it retained the properties of the original ARPANET, which was tested in counterinsurgency. “Objectivity” in Social Science and Social Policy was published in The methodology of the social sciences (Weber, Citation1949) and translated by Edward A. Shils and Henry A. Finch.Footnote9 The essay made Weber’s ideal type concept widely available to American readers in the Cold War years. Weber’s ideal type concept acknowledges that things change over time and yet human understanding of those things also changes, yet still can identify something in the same way that it originally began. Thus, we call a university, government, or an auto plant that is over a hundred years old, a university, government, or auto plant, even though the kinds of activity that go on in them, or the cars made in them, may be very different from the activity that went on in, or cars made in, them a hundred years ago.Footnote10 The ARPANET began as a tool of counterinsurgency and as it grew and changed its original capabilities were not discarded as improvements were added to the growing machine and its networks. No matter what combination of equipment, of protocols or time sharing or packet switching or networks were linked to networks—all these technical details distract from the fact that this growing machine was just another type of ARPANET grown large and able to do more of what the ARPANET was designed to do—spy, process data, store data, share and transmit data, and aid intelligence agents in neutralizing civilians—an activity that Jeff Halper (Citation2015) bluntly calls “war against the people”.
Regarding the issue of classified and unclassified documents, I did not differentiate them since both were trafficked in ARPANET in its testing years. Instead, I follow what Weber and later, Frank Donner observed. Weber argued that the social realm withheld special goods (such as a special fund, databanks inventions, tabulating machines, codes) from the market and from enemy hands, for the political leadership. Donner (Citation1980/Citation1981) writing in Cold War America, confirmed Weber’s argument when he observed that the political party leadership did not use the intelligence product that the intelligence community produced—the intelligence community used it (Donner, Citation1981, p. 9). Using Weber’s and Donner’s approach frees the analysis from having to differentiate or identify which networks or computers were used for classified or unclassified documents - something that cannot be verified by third parties anyway.
2.3. Weber on commercial partnerships
To describe the formal privatization of the ARPANET I enlisted Weber’s (2003) insights regarding commercial partnerships as he reported them in 1889 in his first dissertation The history of commercial partnerships in the Middle Ages translated by Lutz Kaelber. Weber’s first dissertation research regarding commercial partnerships of the Middle Ages frames discussion about the formal privatization phase of the ARPANET backbone. Weber wanted to know if Imperial German commercial partnership law was rooted in earlier European, Romanist, or German versions of commercial partnership and how a “special fund” emerged within partnerships (Weber, Citation2003). The special fund was a legal instrument or a third object that gave large firms advantages. Commercial partnerships were contractual, arraignments that tied OSG members of the social honor realm to members of the political party or market realm for marketing goods. Weber thought modern firms that shared a joint name, a special fund, and conditions regarding liability had emerged from earlier general partnerships.
A modern limited partnership was a “participatory relationship” or a joint partnership where the partners contributed money into the firm to cover debts (Weber, Citation2003, p. 181). “Participation” distinguished the modern, limited, joint commercial partnership (2003, p. 181). A partner who contributed more money could recover or retain more assets if the firm suffered losses. This was advantageous for participants who had money to invest in a firm since they did not have to pay creditors in the event of loss, because they had contributed money in advance for debts (which protected the partner’s private accounts). In his book review of Kaelber’s translation, Rutger’s University professor Paul McLean described Weber’s insights:
Partnership is not simply a cooperative effort of self-interested individuals, but a binding and durable form of such cooperation. [.] it involves three acts: (1) the creation of a separate capital fund to which contributions are made by the various partners as stipulated by a founding contract; (2) the establishment of a joint name under which the partnership conducts business; and (3) a decision about the nature of partners’ liability toward creditors. In the case of the general partnership, born in Florence, this liability is “joint and several”; in the case of the limited partnership, with a lineage through Genoa and Pisa, some partners enjoy more restricted liability, based usually on their contribution of capital but not labor or managerial time. It took an extraordinary amount of time, imagination, and jurisprudential effort to conceive of the continuously operating commercial partnership as an autonomous legal entity, a corpus (the Latin word for the start- up capital of the firm; p. 176) endowed with “a kind of personality” of its own (p. 56; McLean, Citation2004, p. 253).
Weber defined the special fund as “the object of all legal functions” concerning partnership’s assets. Wealth was a “complex of rights” that differentiated major commercial firms from other enterprises (Weber, Citation2003, p. 56). Weber explained,
Insofar one can call “wealth” a complex of rights that serve a certain purpose and are circumscribed by special rules […] If the characteristics of an “asset” are legally present in an object then the idea of an asset or something functionally similar, suggests itself as a way of making the term more precise as a bearer of rights. One way to achieve this is through the use of the term “firm.” Basically, the firm [.] functions only to encapsulate the relations of property in regard to the partnership. From the perspective of commerce, the firm takes on a kind of personality by this very fact. […] Even if the company did not truly take on a legal personality, the law allowed that the “firm” the “business,” the “partnership” fulfils individual and important functions of a bearer of law (Weber, Citation2003, p. 56).Footnote11
Even when firms had special funds, Weber found it difficult to research them because of secrecy or a “lack of documents” (the document trail often disappeared) (Weber, Citation2003, p. 147). Regulations often excluded from liability things that had not “obtained a price” (had not been sold or registered or were priceless; “(Weber, Citation2003, p. 77).Footnote12 Weber researched how maritime trade was superseded by land and community-based limited or joint partnerships with special funds to protect participants from full liability. As the trader’s function became more complicated the trader participated more and more in forming a joint, limited, commercial partnership for an ongoing firm. Trading partners or contractors negotiated for more freedom from their employers to put the investor’s capital to work abroad, “[wherever he might go]” into commercial operations (Weber, Citation2003, p. 74). For example, Weber wrote,
difficulties arose especially in regard to the controversial question of how far the tractator had to follow the instructions of the investor or the socius stans, respectively, during travel, to what extant he was allowed to deviate, without being endangered, from the intended route or travel, and naturally about the consequences of his death in foreign country, and similar problems. The tractator’s lack of independence is the rule, whereas the opposite is usually stipulated by the clause that he should take the societas quocunque iverit [wherever he might go]. […] (Weber, Citation2003, p. 74).
Instead of being a contractor who sold the goods on a temporary basis, contractors created positions for themselves by usurping the position of the investors, first by negotiating greater independence in contracts and later by negotiating a limited, joint partnership contract to form their own firm. Commercial partnerships protected the partners, as McLean describes here:
This form imposed obligations on partners with respect to each other: to delineate spheres of decision-making, to accept the consequences of each other’s actions taken in the name of the firm, to limit each other’s opportunistic pursuit of business outside the company’s purview, and to decide how profits would be shared. It also imposed duties with respect to third parties: creditors of the firm had to be privileged over partners, who would otherwise seek to pay themselves first. This development was critical for maintaining firms’ (and partners’) reputations. At the same time, the partnership form provided critical protection to the partners, and the separation of the firm’s business from personal accounts meant that partners’ investments were protected from each other’s private improprieties. In essence, the law created a firewall between persons and firms that made risky ventures and large-scale capital accumulation more feasible. (McLean, Citation2004, p. 254)
These protections worked well for commercial partnerships in the Cold War, national security Complex environment, where OSG operations were kept secret and plausibly deniable to protect the partners whose missions and budgets were unknown to other members, Congress, and taxpayers. Weber used his ideal typology methodology to answer his research questions and get around research problems caused by state secrecy, lack of documents, or what today is called plausibly denied.
To sum up, Weber’s social order concept helps describe the human workforce side of the ARPANET informational infrastructure. The ideal type concept helps describe the machine side of the informational infrastructure. The informational infrastructure is always growing and changing and yet always retains the qualities of the original ARPANET, whether it is in mission service to DCA, to NSF, or to the commercial Internet. This growing changing network is always a mixture of the old, original qualities of the ARPANET and the new improvements that emerge from it. The government contractors who helped build this growing informational infrastructure transitioned into commercial owners/managers in the market realm to become capitalists and were no longer bound to conserve the special good or ARPANET backbone and its associated NSF networks/non-NSF-networks, according to the investor’s regulations, but rather, to capitalize off them. The next section reviews literature regarding ARPANET testing history, which demonstrated the necessity for Weber’s theoretical framing.
3. Literature review regarding ARPANET testing led to the theoretical framing
I unpacked history from a wide range of literature, much of it published before the advent of the commercial Internet to investigate how the intelligence community helped test ARPANET, distribute DCAnet, and formally privatize the ARPANET backbone unto the Internet. I did not use many on-line resources; nor did I research technical literature about ARPANET R&D; nor did I tap the rich troves of the National Security Archives, or Project Censored series from Sonoma State University, because I wanted to read the kinds of literature that the intelligence community, academics, and the public were reading in the Cold War years, that was widely read, accessible, and set the tone for how people were thinking. I wanted to read the material the way people in the Cold War era had read it (in books, journals, and reports) rather than reading it in still more fragmented, secondary, and special digest form declassified and retrospective accounts, which most people did not read. I used this research approach intentionally because I wanted to see the landscape the way the pre-Internet workforce that I was writing about popularly saw it, through long books, dissertations, journal articles, TV, radio and newspaper coverage, meeting proceedings, and interviews.
I also wanted to share the research experience with the reader, so I used a lot of block quotes. Ultimately, I relied on many secondary sources and hopefully more researchers will examine primary documents, given the time and resources to locate them. My research techniques are what I was educated to use in the pre-Internet years; researching largely from print media, which entailed a sustained attention span, critical thinking, and personal reflection.
Multi-volume government reports, and long books written by Michael Klare and Michael McClintock helped me understand how the US military, police, and intelligence community meshed itself with civilian society using state-of-the-art, continuous communication technology (such as non-visible wireless networks) for anti-Communist, paramilitary, and police counterinsurgency in the US and abroad. The world’s most expensive invention, ARPANET, helped foster new kinds of counterinsurgency and low-intensity warfare (LIW). At the peak of the Vietnam War there were networked surveillance systems being built in the US and in Vietnam. There were intelligence operations that meshed with these networks, COINTELPRO and CHAOS in the US and Phoenix in Vietnam. Later, Frank Donner’s (Citation1981; Citation1990) Age of Surveillance and Protectors of Privilege and Douglas Valentine’s (2000) The Phoenix Program chronicled these parallel developments. Spy activity in the US was at an all-time high when the FBI and CIA ran domestic spy programs together (1966–1971) to collect information on Americans and search for foreign (Communist) anti-war agitators. At the same time, the US military was conducting surveys to detail the lives of South Vietnamese living in hamlets. California Senator Tunney (1969) wrote a report about the Hamlet Evaluation System (HES) or Grievance Census reports. Later, Valentine (Citation2000), Lt. Col. John L. Cook (Citation1997), and Joy Rohde (Citation2011) also wrote about the South Vietnam Hamlet Evaluation System (HES). Valentine quotes former CIA Director and Saigon Station Chief, William Colby, explaining how the data was used:
We were getting all those statistics, and if you could get them on the computer, you could play them back and forth a little better and see things you couldn’t see otherwise. It was really quite interesting. I never really believed the numbers as absolute, but they helped you think about the problems. We would use it for control of how local people were doing,” he explained, “how if one province reported they had captured a lot of category Cs, but no As, and another province said it captured 15 category As, first you’d check if there were any truth to the second story, and if it is true, you know the second province is doing better than the first one. You don’t believe the numbers off-hand, you use them as a basis for questions. (Valentine Citation2000, p. 275)
Huge amounts of survey data were being generated, processed, and banked regarding both South Vietnamese and US civilians. In 1969, a Committee on Foreign Affairs published a report entitled, Measuring Hamlet Security in Vietnam which cast doubt on the hamlet survey data being collected in Vietnam (U.S. Congress 1969). This report triggered a reduction of advisors and increased quotas for targeted assassinations and drove up demand for better remote communication systems that could service the fewer and more remote advisors. That same year, back in the US, Columbia University professor Jerry Rosenberg (1969) published The Death of Privacy. Rosenberg’s book addressed the issue of a proposed US national data bank. The US public had been surveyed to find out, among other things, what people thought about having their personal data recorded in a national computer bank. Americans filled out long and invasive surveys with hundreds of questions as Vance V. Packard (Citation1964) reported on in The Naked Society. At the same time, South Vietnamese were filing monthly Grievance Census reports. The first line of Rosenberg’s preface warned that Hitler had used a confidential European Census to “weed out some of his potential antagonists.” These events transpired while ARPANET's general computer was tested for its ability to make remote communications easier, more shared and convenient.
By 1975–76 the ARPANET had passed military tests and was transferred to the DCA for mission service with the Pentagon; a decade later ARPANET backbone was privatized into the commercial Internet we use today. After ARPANET became DCAnet in 1976 it was cloned and smaller versions of it were distributed in the largest US military base-building program in history. As part of ARPANET’s transition to DCA, a report by DARPA Program Manager, Stephen Walker, was authored in January 1978, entitled, ARPANET Completion Report. The title page of Report No. 4799 reads, “A History of the ARPANET the First Decade, April 1981.” For this report to have been written, ARPANET must have passed “feasibility demonstrations” to allow it to be assigned to mission service with DCA (US Congress. Senate, 1972, p. 729, Packard, Citation2020b, p. 38). Although the report did not explicitly define what military tests the ARPANET had performed, it stated that the ARPANET had made itself more “convenient” for “social” and academic purposes. The way that ARPANET had demonstrated feasibility was explained this way:
Somewhat expectedly, the network has facilitated a social change in the United States computer research community. It has become more convenient for geographically separated groups to perform collaborative research and development. The ability to easily send files of text between geographically remote groups, the ability to communicate via messages quickly and easily, and the ability to collaboratively use powerful editing and document production facilities has changed significantly the “feel” of collaborative research with remote groups. Just as other major improvements in human communication in the past have resulted in a change in the rate of progress, this social effect of the ARPANET may finally be the largest single impact of the ARPANET development. (US DARPA, Citation1978, Chapter III, p. 110).
The shared communications aspect of the new computer R&D made remote communications more convenient for scientists like J.C.R. Licklider (or Lick), the famous two-time Director of the Information Processing Techniques Office (IPTO) at ARPA. But as Levine (Citation2018) pointed out in Surveillance Valley, Lick said he intentionally distanced IPTO from scientists using similar R&D in remote Vietnam (p. 52).Footnote13 The ARPANET was being developed for remote applications or “stay behind nets” that were left in Vietnam and other countries in bases, airfields, embassies, and other locations (Valentine, Citation2000, p. 405; Stein & Klare, Citation1973, p. 159). Duplicating, cloning, and standardizing computers to take orders remotely and replicating them for distribution in remote locations, enabled LIW in Latin America that followed the US withdrawal from the Vietnam War. The Report stated that:
There has been good success in transferring the ARPANET technology to other parts of the Department of Defense. The Defense Communications Agency procured two small networks, essentially identical to the ARPANET in function, for the purpose of gaining experience with the ARPANET technology [.] Two other networks essentially identical to the ARPANET but smaller, have also been procured by other parts of DOD. (US DARPA Citation1978, Chapter III, p. 101). Footnote14
After the US had withdrawn from the Vietnam War and before ARPANET was transferred to DCA and put under the management of the newly appointed CIA Chief, G.H.W. Bush, ARPANET was introduced to the US public in 1975 by NBC Nightly News correspondent Ford Rowan (Citation1978) author of Technospies. Special reports by Rowan were aired each night for a week in June of 1975 regarding new massive government surveillance programs, enabled by powerful computers and by ARPANET. California Senator Tunney chaired an investigation regarding Ford Rowan’s newscasts in 1975.Footnote15 Testifying was David Cooke, the Deputy Assistant Secretary of Defense. Cooke had served under ARPA founder and Secretary of the Department of Defense (DOD), Neil McElroy. Cooke testified that the DOD did not have “Army civil disturbance files, which were ordered destroyed in 1970 and 1971” and said there was “no evidence that they were transferred via an existing computer net from Fort Holabird to NSA and on to MIT” (US. Congress. Senate. 1975, p. 20). Cooke’s statement stressed that there was no evidence (of the electronically transmitted) files. Unlike testimony in other investigations by the Church and Pike committees, Cooke’s testimony left out discussion about how the intelligence community and police departments had been wiretapping telephone lines across the US for decades or how the new ARPANET had helped create a more convenient way to do eavesdropping, which was essentially invisible (one could not see how the spying was done) and did not leave wiretap evidence. The ARPANET and its growing affiliated networks (DCAnet, NSF net, etc.) made spying easier since the military could say it left “no evidence” when intelligence, presidential orders, or black lists were sent electronically to remote locations.Footnote16 Those who were spied on in remote locations in countries that Bevins (Citation2020) wrote about or in the US as Donner wrote about could not see how the collection happened, had no legal recourse, no evidence, and could not confront the protected spies—in keeping with the FBI’s modus operandi.
Non-evident, wireless, and technical collection systems (microwave, optic fiber, and satellite) that the ARPANET interacted with afforded the intelligence community the advantage of transmitting intelligence without evidence (since electronic files were hidden) or human spies (who might become whistleblowers) and without the taxpayers or legislators (who might stop tax collection from the source) able to see or know how the surveillance happened. Nor were those spied on able to confront the spies or obtain evidence. When Senator Tunney suspected illegal intelligence collection was happening, the intelligence community could say there was “no evidence” of the surveillance as Cooke’s testimony demonstrated (US Congress. Senate. 1975, p. 20). The Army did not have the evidence Tunney was asking about, because it had been duplicated electronically and stored in data banks, while it was unclear whether the originals were “destroyed” (French, 1975). While civilians were spied on, they had no evidence to use in court to protect themselves with, even though the intelligence data banks were filled with civilian data for future reference. This was how ARPANET demonstrated feasibility for evidence-free, government military and intelligence spying, operational research (OR), and orders from the highest levels in government. This was a technical advancement upon the handwritten card indexing systems that the Nazis had used to track German workers via their mandatory workbooks or the tabulating card index system that tracked tattooed forced labor distributed to the concentration camps that destroyed the human evidence (Aly & Roth, Citation2004, pp. 44–47; Black, Citation2001b).
In 1978, Ford Rowen published his book Techno Spies, which explained in detail how massive and growing government data banks had become problematic for the government after interactive computers and military surveillance of civilians had made privacy rights a public concern. With the advent of interactive computers, government databanks, which had once been managed and kept separate, were vulnerable to hacking and theft, or being filled with military spy intelligence that frequently entailed aggressive and illegal spying, in violation of Constitutional rights. Rowan’s book capped a decade of similar findings, made by dozens of government investigations into intelligence agency abuses. During the 1970s investigations into intelligence agencies were made by both the Congress and the Senate, as well as individual legislators like Nelson Rockefeller and Sam Ervin and numerous committees and subcommittees. The investigations were prompted by a variety of events, such as ex-military intelligence Captain Christopher Pyle’s (Citation1970) The Washington Monthly whistleblower account about military surveillance of US citizens entitled, “CONUS Intelligence: The army watches civilian politics.” Pyle explained that the military was collecting intelligence on law-abiding citizens without consent and for future reference. He warned this activity would damage democratic government since the surveillance could be used to neutralize moderate factions of society, causing a polarization of society into political extremes and prompting the rise of authoritarian government, which would rely on more surveillance. He also warned that it would make governments and the databanks and networked informational infrastructures they increasingly depend upon prone to coups; after all, the informational infrastructure was a link to taxpayer revenue, corporations, military contracts, and so on.
Pyle’s article prompted a three-year investigation into military spying, by the Committee on the Judiciary’s subcommittee on Constitutional Rights, which produced, Military surveillance of civilian politics: A report (1973). The report confirmed “self-enforced” military agents were filling “a myriad of Army intelligence computers” with illegally and unconstitutionally collected data about citizens (US. Congress. Senate. 1973b, pp. 7, 117). It confirmed that military leaders ordered the spying to be stopped, but agents continued the spying and third-party investigations were not allowed. In the middle of the three-year investigation, in 1972, Senators Adlai E. Stevenson, Sam Ervin, Edward Muskie, and George McGovern agreed that they were being spied on by the military and assembled the Democratic National Committee (DNC) to investigate. Editor Richard Blum (Citation1972) chronicled this meeting of political and policy experts chaired by Stevenson. Blum’s report (Citation1972) recorded the results of this investigation. It endorsed less technical spy agency information; fewer secret government documents; less covert intelligence activity; regulating the intelligence community and reducing Presidential privilege to use the intelligence community without Congressional approval. The committee's goals were viewed as a threat to the intelligence community. A couple of years later, the Democratic National Committee offices in the Watergate building were bugged under orders from President Nixon, who resigned in 1974 because of the scandal. This event sent a message to the Democrats that they were still under surveillance and a message to party leadership that bugging, and wiretapping was a risk even to Presidents—now leadership saw advantages in wireless communication and computer enhanced ways of doing surveillance that did not leave risky evidence that might lead to hard bargaining or impeachment. By the time the Internet was commercialized the recommendations that the DNC had endorsed in their 1972 report had been reversed.
In spite of the DNC and Military surveillance of civilian politics reports, public outrage and military orders to cease collecting intelligence, the “self-enforced” agents did not stop aggressive spy operations; they followed presidential concerns, or orders, which had more validity for national and job security (US Congress. Senate. 1973b). A year after the Judiciary’s subcommittee on Constitutional Rights published its report, Frank Donner (Citation1974), a constitutional lawyer, authored an article in The Nation entitled “Hoover’s Legacy.” Donner reported on how political intelligence was usurping the place of policing in the US and posed a conflict of interest, since the police were in effect, lawlessly painting law-abiding citizens as communists and subversives and using the false picture to justify more federal funding for national and their job security. There was hope that once Hoover died, this trend might end, but instead the trend continued under new FBI leadership. Donner had been monitoring this trend since the House on Un-American Affairs (HUAC) had been censored in 1956 and Hoover secretly continued HUAC’s work in the covert form of COINTELPRO’s aggressive spy operations, as Morton Halperin et al. reported in Citation1976 in The Lawless State.
Presidential orders to collect intelligence, superseded military orders to cease collection of data. The intelligence community disregarded military orders to stop collecting intelligence or to destroy files, since they had a higher validity to abide by presidential orders in the name of national security as Computer World reporter Nancy French (1975) investigated . As Pyle (Citation1974) described in his Columbia University dissertation, each intelligence agency wanted its own databanks and did not want to share its data, for, among other things, career advancement (and besides, the data might have revealed something libelous about agency operations and intelligence collections). The result was that demand for databanks, networks, and computers grew as each agency wanted its own databanks (Pyle, Citation1974). The government could neither stop the spying nor protect and manage the expanding data in the growing array of interactive computers, data banks, and networks that connected them. At this juncture, ARPANET was transferred to DCA, where spying and network building expanded during a distribution phase that transplanted networks abroad through military base building and LIW throughout the 1980s.
In addition to government reports and newscasts, there were books that reported on the growing computer and network enhancements and the political intelligence industry both in the US and abroad. Constitutional lawyer Frank Donner chronicled the rise of a computer and network enhanced US political intelligence system rooted in anti-Communist ideology that pre-dated WWI. Donner’s three books The UnAmericans (1961), The Age of Surveillance (1980/1981) and Protectors of Privilege (1990) described how new forms of technical collection that grew from ARPANET R&D enabled a division of labor between policing and intelligence operations. While policing was supposed to protect civilians, political intelligence operations collected information, for future reference, about civilians deemed threats to the status quo, based on anti-Communist ideology. Donner observed that the collected intelligence product commodity was not used by the government (which paid for the operations) but rather by the intelligence agencies themselves for “future reference” in the name of national and job security.Footnote17 While Donner chronicled computer and networked enhanced political intelligence growing in the US, historian Michael McClintock chronicled similar developments in Latin America. Writing in the 1985, in the midst of the largest US military base-building campaign in history, Michael McClintock foresaw the emergence of what he called “todays intelligence system” tied to computer and networked enhanced military operations abroad such as ORDEN (order in Spanish) in El Salvador.Footnote18 In The American Connection McClintock wrote, “Development of today’s intelligence system and setting up ORDEN were part of a single process” (1985, p. 204). McClintock expanded his analysis of counterinsurgency in Instruments of Statecraft: U.S. Guerrilla warfare, Counterinsurgency, Counterterrorism 194–1990. While books like these make counterinsurgency more understandable, history of the ARPANET must be read between their lines since ARPANET and its affiliated networks were essentially invisible to most authors. Only years later, after the Internet was commercialized, did the public comprehend how new “wireless” and regional networks were in fact global, thanks to the equally invisible World Wide Web
In 1990, Valentine published The Phoenix program, the same year Donner published Protectors of privilege: red squads and police repression in urban America. Reading back to back these books show how American anti-Communist, red squad intelligence operations were exported to South Vietnam for public safety programs that entailed building networked communication systems and meshing them with paramilitary operations to neutralize the Vietcong infrastructure (VCI). In Surveillance Valley, Yasha Levine (Citation2018) acknowledged that ARPANET R&D was part of Cold and Vietnam War counterinsurgency operations such as Agile and Phoenix and that other accounts of ARPANET history underestimate this. Following Levine in 2019, one of the most recent and critically acclaimed studies of the Internet, Shoshana Zuboff’sCitation2019) The Age of Surveillance Capitalism does not account for the testing of the Internet, which I argue weakens her theory (Packard, Citation2020c , Citation2023). Levine had hindsight and looked back at ARPANET from the post-Internet years, while McClintock (writing in the pre-Internet years) had foresight from examining networked societies in Cold War era Latin America. I second Levine and McClintock’s analysis since privatization of the ARPANET into the Internet was contingent upon ARPANET passing military tests in counterinsurgency in the US, Vietnam, Latin America, and arguably other countries that Bevins (Citation2020) and McClintock (Citation1992) wrote about.
Writing about the role of the intelligence community in testing the ARPANET was difficult since the work of intelligence agencies was secret to protect national security.Footnote19 For example, the NSA is not supposed to exist. During ARPANET ‘s Cold War history, a division of labor emerged in the intelligence community. Writing in the 1970s Marchetti & Marks reported how the CIA became an agency that specialized in covert operations, while NSA advanced in “technical collection” which they described:
Technical collection, once a relatively minor activity in which gentlemen really did read other gentlemen’s mail, blossomed into a wide range of activities including COMINT (communications intelligence), SIGINT (signal intelligence), PHOTINT (photographic intelligence), ELINT (electronic intelligence), and RADINT (radar intelligence). Data was obtained by highly sophisticated equipment on planes, ships, submarines, orbiting and stationary space satellites, radio and electronic intercept stations, and radars—some the size of three football fields strung together. The sensors, or devices, used for collection consisted of high-resolution and wide-angle cameras, infra-red cameras, receivers for intercepting micro-wave transmissions and telemetry signals, side-looking and over-the-horizon radars, and other even more exotic contrivances […] and it has created a new class of technocrats who conceive, develop and supervise the operations of systems so secret that only a few thousand (sometimes only a couple of hundred) people have high enough security clearances to see the finished intelligence product (Marchetti & Marks, Citation1980, p. 82).
At the same time, the CIA had jurisdiction over intelligence operations throughout the Americas, while the FBI had authorization to install FBI offices “in more than twenty-five foreign capitals” during ARPANET’s testing and general computer years (1969–1976; Donner, Citation1974, p. 689). Government investigations revealed to the public that the US was becoming a surveillance state staffed by agencies and agents who claimed a greater national security legitimacy than other governmental agencies, as the CIA headed by G.H.W. Bush was “utterly responsive to the instructions of the President and the Assistant to the President for National Security Affairs,” as the Village Voice leaked from the Pike Committee report findings (Latham, Citation1976, p. 71). The US Congress and president trusted these agencies to protect national security and appropriated “more than 50 percent” of US government income or tax revenue to them (US Congress. Senate, 1961, p. 124). Military intelligence agents collected intelligence data that was trafficked, processed, stored, and hidden in the new computer data banks. It appeared that the intelligence community played a role in testing the ARPANET and since the intelligence community was both secret and vast it was easier to describe it using Weber’s social order to theoretically frame it.
To sum up, the literature researched was mostly in the public domain rather than from archives or even online. This had the advantage of showing the readers what the ARPANET workforce was reading and thinking about and what the government chose to inform the public about. In the section above, I discussed Weber’s social order concept and ideal typology and how I applied it to the workforce that tested the ARPANET. In the Results section below, I apply Weber’s concepts to the ARPANET history along with Weber’s observations about commercial partnerships, to describe how the intelligence community workforce helped test networks that commercial contractors such as Merit, IBM, and MCI helped build and how political leadership formally commercialized the ARPANET backbone, NSF net, and non-NSF networks.
4. Results: Weber’s Concepts applied to findings to answer the research questions
In this section I use Weber’s concepts to help interpret answers to the research questions. The chronologies in Appendix B are an illustrative reference. To reiterate the questions: How was the ARPANET tested so that it qualified to be transferred to DCA in 1975–6, rather than commercialized? Since ARPANET's backbone was formally privatized a decade after it was transferred to DCA, what happened during that decade? How was formal privatization of the ARPANET backbone authorized and why were certain companies, namely Merit, IBM, and MCI, contracted to commercialize the ARPANET backbone? These questions are addressed in the sections below entitled, 1960–1976 ARPANET Testing Phase; 1976–1987 DCAnet and ARPANET Backbone Distribution Phase; and 1987–2000s Formal Privatization of ARPANET Backbone Phase.
4.1. ARPANET Testing Phase
Military testing was required before the ARPANET backbone could be put into mission service or commercialized because US tax dollars had paid for the R&D (U.S. Congress. Senate. 1972 pp. 725–830; Packard Citation2020b). As discussed above, successful testing entailed creating a continuous communication system that could transmit, process, and store electronic communications for the Complex and between countries or remote locations, easily, without evidence of the transmission, to maintain plausible deniability for national security and counterinsurgency warfare. Operations that could not be done in the US, like Phoenix or operations in Latin America and the other countries that Bevins (Citation2020) wrote about, were also testing grounds for ARPANET's general computer. For example, Latin American countries with mutual defense agreements had “blacklists” with names of people to be neutralized or killed by paramilitary forces which were transmitted through state-of-the art networks that necessarily left no evidence of the transmission, to protect the US and corporate interests (Bevins, Citation2020, p. 161). This was in keeping with Weber’s description of the self-styled workforce of the social honor realm, which was tasked with conserving special goods, like the ARPANET or arguably blacklists, from the market realm taxpayers and from the enemy, for its own operations in the name of national and job security.
For example, in Appendix B, the testing phase decade of ARPANET is outlined in the 1960–1970 chronology. The 1947 National Security Act (see 1940–1950 chronology) was in full effect. The tax revenue for military funding was being tapped at the source thanks in part to the efforts of Milton Friedman (Friedman & Friedman, Citation1998, pp. 120–124). In 1952, President Truman established the National Security Agency by secret decree (see 1950–1960 chronology). The NSA soon became an “independent agency” which by 1976 the Pike Committee feared was taking the intelligence community into the “realm of economics” (US Congress, 1975–76b, p. 2079; Packard, Citation2023). In 1958, the Defense Advanced Research Projects Agency (DARPA) was established, and a 1959 DOD Directive 5129.33 ordered that ARPANET be built (see chronology 1950–1960). By then MSUG was already in South Vietnam, where it helped establish a strategic hamlet program that collected monthly hamlet survey data shared with Washington, DC. The MSUG included CIA advisors and “former state troopers or big city-detectives” who had professional roots in the “pacesetter” Detroit, anti-Communist, red squads, and their FBI and corporate affiliates like “Ford Motor Company and Citibank,” as described by (Black, Citation2009); Valentine (Citation2000, p. 32); Donner (Citation1990, p.p. 291–298); Majka, (Citation1981); Bevins (Citation2020, p. 215). The Detroit red squad model (noted in the 1940–1950 chronology) was transplanted to South Vietnam when the US government paid MSUG $15 million dollars to broker the building of microwave communications systems in Vietnam, Laos, and Thailand in affiliation with public safety programs as reported by the United States Operations Mission to Vietnam Annual Report for Fiscal Year 1959 …; Valentine (Citation2000) and Ernst (Citation1995, Citation1998). When MSUG left South Vietnam in 1962 the groundwork was laid for the Phoenix, AGILE, and IGLOO White operations in South Vietnam, which Paul Edwards (Citation1996) wrote about in The closed world: computers and the politics of discourse in Cold War America.
In 1961 three AT&T microwave towers in Utah and Nevada were bombed by men calling themselves the American Republican Army. Called the Wendover Blast, it gave the military a reason to build a resistant, invisible microwave network that would be hard for bombers to see or target and invisible to taxpayers who were spied on. In 1962, when MSUG returned to Michigan, Com-Share Inc. of Ann Arbor Michigan published “Economic Need for Common Carrier Microwave Communications” (see chronology 1960–1970). This report helped boost demand for microwave system construction and launch Microwave Communication Inc. as Cantelon, wrote about in The History of MCI: 1968–1988: The early Years. As Michnet was being constructed, it linked the Michigan State University system with the same infrastructure that had been built up in Michigan for use by the anti-Communist red squads for spying on and neutralizing unionists and strikes, during the 1930s-1950s, namely the state legislators, police, automotive corporation service departments, and the FBI (see chronologies 1920–1930, 1930–1940, 1940–1950 chronologies). While Michnet was built up, President Kennedy appointed the president of Ford Motor Company, Robert Strange McNamara to be Secretary of the US DOD and by 1962 had signed Memorandum No. 124 Establishment of the Special Group (Counter-Insurgency) which authorized development of a lab in South Vietnam to advance counterinsurgency warfare (see chronology 1960–1970).
From 1962 to 1964, the RAND Corporation authored a series of reports proposing a decentralized network of computer nodes that could survive damage from nuclear war. What had begun as civilian defense red squad operations in US cities in the Cold War were transplanted to Vietnam and elsewhere, through programs like the Agency for International Development (AID) and Public Safety and then returned to the US with enhanced continuous communications features, to emerge as Michnet or ARPANET and other networks. Cross-pollination of network R&D between remote and domestic technology was enabled through US police, university expertise, and complex corporations. For example, Colonel Jack A. Crichton, a Legion of Merit award winner, anti-communist, oilman, and a political ally of G.H.W. Bush, was famous for building an underground, command post located under the Dallas Health and Science Museum patio. By 1962 it was “fully equipped with communications equipment” to prevent communist infiltration and keep “continuity of government” (Baker, Citation2009, pp. 117–122). Colonel Crichton’s underground, Dallas command center (which was left out of the 1963 JFK assassination investigation) represented a type of network node similar to what US military advisors helped build in Vietnam and Latin American countries, such as El Salvador’s ORDEN.
During the ARPANET testing phase in the 1960s the military invested heavily in trying to identify who the Communists were. IBM was making smaller, more productive computers, while IPTO pioneered interactive computing. Social scientists helped collect data on populations abroad for special operations as Joy Rohde’s (Citation2013) Armed with expertise: the militarization of American social research during the Cold War reports. Operations like Phoenix, COINTELPRO, and CHAOS increased demand for experimental computers, nodes, and networks that could process massive amounts of spy data. During the 1960s MCI forged ahead with building regional microwave networks, Michnet grew as the ARPANET nodes on the west coast emerged and IBM computers were becoming interactive, smaller and easier to transport to remote locations with help from CIA air proprietaries. Everything seemed to be successful except for Project Camelot. Camelot was going to collect data on populations abroad for predicting and controlling social movements in developing countries. Its cover was blown by a scandal that exposed the project to bad press. It was terminated, causing much debate and grief for social scientists speculating on the expensive program, as described in a volume of essays edited by Irving Horowitz (1998) entitled The Rise and Fall of Project Camelot. Camelot, however, was soon supplanted by a US-based project called Cambridge and many other projects, which smoothed the technology pathway toward civilian data collection drawn from the source (directly through personal computing) rather than collected through cumbersome, leaky, third parties that might draw bad press (which OSGs loathed).
Herman (Citation1998) explained how Project Camelot grew out of WWII psychological warfare, which became increasingly meshed with the military as funding increased for counterinsurgency warfare. Camelot was a DOD sponsored plan that enlisted “psyops” and social scientists in the venture of predicting and controlling development and revolution abroad in smaller countries. Camelot would have been the most expensive behavior research in US military history, Herman noted: “With a $4–6 million contract over a period of three years, it was considered a veritable Manhattan Project for the behavioral sciences …” (p. 103). The organization that fostered Camelot, Special Operations Research Office (SORO) changed into the Center for Research in Social System (CRESS). These organizations embodied the fusion of social science with military, police, intelligence, and computer science to win hearts and minds for the Cold War effort as it shifted warfare from the battlefield into civil society. Herman wrote,
The boundaries between military and civilian targets, between wartime and peacetime conflicts, already beginning to blur during World War II when examined through the lens of psychological warfare, took on an eerie permanence during the Cold War. Military psychological operations experts were only stating what many Americans already felt […]. Since peace and war were no longer entirely distinguishable, the services provided by experts became a permanent military asset (Herman Citation1998, p. 99-100).
Counterinsurgency warfare required OSGs collecting information from civilians, at least until personal computing, AI, and networked society could automate the information collection from the source, through an unregulated, commercialized Internet. Political scientist Ithiel Pool, along with IPTO director Licklider, supported Camelot, however other scientists thought Camelot could be used for destabilizing a country and this caused sensational press coverage, as Rohde (Citation2013) reported. The Camelot program was terminated in 1965, and a new Foreign Area Research Council was formed in the State Department Bureau of Intelligence and Research (see chronology 1960–1970, in third column). The Council was going to review R&D projects of national security agencies such as the Pentagon, AID, and the CIA. Such a review process presented “access” problems for many social scientists and was debated by US scholars like Lucian Pye (Wallerstein, Citation1997, pp. 224–225).
The outcome of these developments was twofold. First, ARPANET research was excluded from the Foreign Area Research Council review process based on the premise that it was done only in the US. ARPANET scientists were freed from having to submit their research to State Department review. Importantly, research funded by NSF or privately funded R&D was exempted from review, if R&D was based in the US. Thus, ARPANET R&D was free from government oversight as the ARPANET backbone was transferred out of DCA and into NSF in the 1980s and was improved with private funding. If past be guide, the intelligence agencies saw the Foreign Area Research Council as an obstruction to their national security operation missions to be overcome, or as a test for sharing electronic data and R&D between countries without evidence of the transmission. Thus, R&D from a lab in Vietnam transmitted without evidence to labs in the US was a test for ARPANET and a way to get around the government regulations without evidence. Arguably R&D from abroad was shared with US military computer scientists in the US without evidence of the transmission, making R&D from abroad appear to be US-based R&D, when in fact it was from foreign sources (where it could be tested in ways not possible in the US) or vice versa and free of any Foreign Area Research Council review.Footnote20 In this scenario, the military would have been able to transfer blacklists without evidence and with plausible deniability (under the pretext that such transmissions could not happen since there were government regulations against it).
The second outcome was a new domestic, IPTO supported, Project Cambridge (Project CAM) that replaced CAMELOT with spy data collection based in the US. Levine (Citation2018) described Project CAM as “counterinsurgency technology” (pp. 64–71). Leslie’s (Citation1993) The Cold War and American science: The military-industrial-academic complex at MIT and Stanford discusses uprisings on US campuses around CAM. The protestors would have been good targets for intelligence watchlists, which were being built up as the FBI’s COINTELPRO and the CIA’s CHAOS programs began running together from 1966 to 1971. Project CAM would provide data processing for operations like these, with ARPANET's general computer available for testing until 1975. This twofold outcome from CAMELOT’s supposed failure showed the successful dual nature of ARPANET development and testing as R&D in Vietnam (processing hamlet survey data to help neutralize Vietcong) went on side-by-side, with US-based operations to neutralize anti-war activists in the US.
In Appendix B in the 1960–1970 chronology, it is noted that IPTO Director Robert Taylor (1966–1969) went to Vietnam, after the 1967 Tet Offensive, to program a computer at Tan Son Nhut Air Force Base outside of Saigon. In a 1989 interview Taylor explained that intelligence from the Air Force, Navy, and the Army was being consolidated into a single report by Washington officials (Aspray, Citation1989, pp. 12–13; Hafner & Lyons, Citation1996, pp. 151–152; Newman, Citation1998, p. 153). The computer and its networks were being used by self-styled professionals of the social realm intelligence community, while ARPANET was a general-purpose computer. In 1969, South Vietnamese hamlets were mandated to neutralize a certain quota of Viet Cong each month, while advisors were being cut back. Increased kill quotas with fewer advisors in the field drove up demand for more state-of-the art communications as advisors became more remote (Cook, Citation1997, pp. 300–301). Taylor’s communications between Vietnam and IPTO tested ARPANET's non-evident, remote capabilities for “stay-behind” nets left in Vietnam, after the US withdrew in 1975 as Stein & Klare reported in Citation1973.
As noted above, the CIA opened CHAOS under “White House pressure” (US Senate 1976b, pp. 99–102). CHAOS (1966–1971) and COINTELPRO (1956–1971) ran with many other military intelligence spy programs that Pyle (Citation1974) described. Together, they generated domestic spy data that filled “a myriad of Army intelligence computers” with illegally and unconstitutionally data about citizens collected by “self-enforced” agents (US. Congress. Senate. 1973b, pp. 7, 117). The growing amount of data had to be processed in new ways by universities with military R&D contracts (Packard, Citation2020a Citation2020b). As CHAOS and COINTELPRO ran together, the 1966 Freedom of Information Act was passed restricting public access to previously public records and a new consortium of Michigan State Universities called Michigan Educational Research Information Triad, Inc. (Merit) was established. The new Michnet provided a microwave communication system for the universities, the police, automotive industries, state government, and the FBI. Earlier MSUG had brokered contracts for the microwave systems built in Vietnam, Laos, and Thailand in the 1950s, paving the way for the stay-behind nets in the 1970s, which new computers were added to as the networks expanded.
Merit helped manage Michnet which merged universities with civilian society, government, police, private industry, and the intelligence community—all enhanced with network communications that did not leave evidence. This expertise qualified Merit to be the contractor that NSF would trust to formally privatize the ARPANET backbone and commercialize the NSF and non-NSF networks into the Internet, about twenty years later. At the same time, demand for faster, smaller, computers increased, and IBM launched System/360, which increased computer productivity at a lower cost. In 1969, the FCC (now more of a friend to the telecommunications industry rather than a regulator of it) allowed MCI permits to build microwave systems between Chicago and St. Louis.Footnote21 Private companies could finally build the microwave networks that GE and IBM had tried to build in the 1940s before the New Deal FCC had stopped them (see chronology 1940–1950).Footnote22
The 1970–1980 chronology shows how the US government, under pressure from an outraged public, investigated the self-enforced, self-styled social honor realm or intelligence communities’ unlawful and massive surveillance programs. The decade began with the Watergate wiretapping scandal that unseated President Nixon which demonstrated how wiretapping evidence was a risk to the President. It sent a strong message to political leaders that wireless networked communication systems that did not leave evidence, had advantages. The Church and Pike Committee investigations were the best-known of at least 80 government investigations into intelligence community abuses as Donner, reported in Age of Surveillance (Citation1981 pp. 528–532). Whistle-blowers like Christopher Pyle and Daniel Ellsberg and Vietnam veterans like the Winter soldiers, stoked anti-war sentiment in the US and provided a sort of honey pot to attract activists that the intelligence agencies wanted to create files on for future reference. The government investigations and bad press angered the intelligence community and military OSGs who rallied and voted for conservative leaders like Ronald Reagan and G.H.W. Bush. In turn, Reagan and Bush rewarded their supporters with more government funding to conduct surveillance of civilians not just in the US (for the War on Drugs) but in other countries through low-intensity warfare (LIW) and military base building and in outer space for the Strategic Defense Initiative or Star Wars program.
While the US public was distracted by sensational news coverage about Watergate, the Pentagon Papers, government investigations into intelligence agencies and the US withdrawal from Vietnam, the companies that would formally privatize the ARPANET into the Internet were making great strides. In 1968, McNamara had become the head of the World Bank and remained there until Reagan became President in 1981. As noted in the 1970–1980 chronology, during the 1970s IBM produced a Customer Information Control System (CICS) for automating economic transactions and banking. By 1972, Merit was running an inter-university packet switching data network that would be a model for the commercialized Internet when Merit was selected to privatize the ARPANET. MCI had formed a partnership with Lockheed Missiles & Space Corporation. MCI and Lockheed added Communication Satellite Corporation (COMSTAT). IBM, MCI, and COMSAT later added Aetna (the largest insurance company in the US) to create Satellite Business Systems (SBS) and MCI bought out COMSTAT. Communication satellites made it easier to transfer vast amounts of data electronically across the world, whether for private insurance companies, the military, IBM, the intelligence community, US companies abroad, or presidential orders. Valentine describes how these trends manifest in South Vietnam in the form of the “Big Mack” computer that processed the growing numbers of “identified and unidentified” Vietcong killed, captured, and rallied after Phoenix transitioned to CORDS and the US prepared to “stop pursuing the war and start reporting” about it instead with stay-behind nets (Valentine Citation2000, p. 288–289).
New developments in software technology enabled data searches that could track and trace individuals for assassinations in Vietnam, neutralizations in Latin America and for almost anything. While MCI’s regional networks were growing across the US and IBM and MCI satellite communication systems were transmitting personal data about entire populations across the world, a new software called Prosecutors Management Information Systems or PROMIS, was able to search through the data for specific targets. William Hamilton is credited with pioneering PROMIS in the US in a R&D “unit of the” NSA (Ben Menashe, Citation2015, p. 130). PROMIS may have been tested in Vietnam for the VCI Neutralization Information System as Valentine (Citation2000) described:
In January 1970 the VCI Neutralization Information System was inaugurated to record all anti-VCI operations. The National Police Criminal Information System (NPCIS) was implemented in April 1970 to track VCI who were held beyond “statutory limitations.” Designed to “interface” with Chieu Hoi “tracking system,” which aided province security committees in the “post-apprehension monitoring of released VCI,” NPCIS was also compatible with the VCI Neutralization and Identification Information System, which stored in its classified files, “a history of the VCI member from time of his identification to his neutralization” (Valentine, Citation2000, p. 289).
PHMIS may have been the template for DOJ MIS and PROMIS, which offered a non-evident way to help get around cumbersome judicial, court and trial by jury protocol and protect national security operatives from being subjected to judicial proceedings for crimes against humanity. The saga of PROMIS is long, unfinished, and riddled with many mysterious murders and censorship that invites more study (Packard, Citation2023). Big Mack, PROMIS, and the ARPANET general computer became part of a growing foundational network for building a World Wide Web and there were no government regulations overseeing these world changing events.
Around the time the ARPANET was transferred to DCA, Chilean economist and former ambassador to the US, Orlando Letelier and his US assistant Ronni Moffitt were murdered in a car bombing in Washington D.C. in September 1976. This bombing in the nation’s capital was allegedly authorized by Chile, but was CIA assisted (Bevin 2020, p. 215). It happened 3 years after the coup toppled Letelier’s former employer, President Allende, replaced by General Pinochet. Pinochet orchestrated operation CONDOR, a multi-country operation to specifically track and neutralize political activists, particularly those traveling across borders, as Francesca Lessa (2022) examined in The Condor Trails: Transnational Repression and Human Rights in South America.
In The Condor years John Dinges wrote that when General Pinochet visited Kissinger, he expressed concerns about Letelier lobbying Congress to defund the military dictatorship in Chile. Nixon had made Henry Kissinger Director of Central Intelligence (DCI). Marchetti and Marks (Citation1980) wrote that “Kissinger with his control now asserted over virtually all national security community’s key committees had clearly emerged as the most powerful man in U.S. intelligence” (p. 91). It seemed Pinochet was asking for orders to neutralize Letelier; such orders would have been sent via ARPANET since state-of-the-art networks did not leave evidence of blacklists. At the time, ARPANET was well positioned to be tested for transmitting communications about the September 1976 car bombing in Washington DC that neutralized Letelier and his American assistant Ronnie Moffit. At the same time, G.H.W. Bush was taking charge of the CIA with more administrative power than any other DIC and with more informational infrastructure power too, namely the ARPANET or alternatively DCAnet. ARPANET’s ability to track a terrorist attack on US soil would have been a test closely watched by the new head of the CIA.
A few months after the bombing Milton Friedman was awarded a Nobel Prize in Economics. The political leadership liked Friedman’s Capitalism and freedom neoliberal economics and the social honor realm neoliberal OSGs like those Karin Fischer (Citation2015) wrote about in the context of pre-coup Chile. In contrast, the sensational news coverage about Letelier’s Citation1976 murder associated him, his American assistant Ronnie Moffitt, and his September 1976 article in The Nation entitled, ‘Freedom’s Awful Toll: The “Chicago Boys” in Chile’, with America’s symbol for terrorists—bombs and blood. By 1976, ARPANET had demonstrated feasibility for making communications more convenient for the Complex and was transferred to DCA (see 1970–1980 chronology). Although the transfer is often cited as happening in 1975, Salus (Citation1995) noted “DCA actually” managed the ARPANET in 1976 (p. 83).
The American public was relieved that the twenty-year Vietnam War had ended and did not want the US to engage in more wars so it elected Jimmy Carter to be President in 1977 in hopes he would keep the US out of further wars. No sooner had the US withdrawn from Vietnam, the US public was informed that the same kind of electronic surveillance, tracking, and data banking that had helped wage war on the Vietcong were being employed by the US government to monitor US citizens. NBC correspondent Ford Rowan presented a week-long series of reports on prime-time television in June 1975 to inform the public that the intelligence community was collecting personal information about Americans, cross-referencing it with data from different sources, and data-banking it for future reference. What he described was similar to how Big Mack and the VCI Neutralization Information System operated.
With the arrival of Carter, G.H.W. Bush left the CIA, but he had been there long enough to see the ARPANET transition to DCAnet. During the Carter administration, US engagement in wars slowed but then skyrocketed. Military historian Michael Klare’s (Citation1972) book War without end: American planning for the next Vietnams had warned that the wars would not stop; 48 years later Vine’s Citation2015 book The United States of War confirmed this. The complex had multi-year military contracts and tax revenue from “the source” to automatically subsidize complex companies through new, state of the art, computer enhanced, electronic distribution, and banking systems (Packard, Citation2023). The Institute for Policy Studies tried to find out how many computers the US military was distributing for its wars in Latin America by filing a FOIA, but the government refused to provide the information (Klare & Arnson et al., Citation1981). The computer companies feared public exposure, bad press, and disruption of their trade. The social honor realm contractors were withholding special goods (like computers) and information about them from the open market and using them for their own national security purposes and for more LIW.
Unable to stop the wars and in reaction to the findings of the Church and Pike Committee, President Jimmy Carter enacted the Foreign Intelligence Surveillance Act of 1978 (FISA) to stop the NSA’s warrantless domestic spying (see 1970–1980 chronology). Congress created the FISA court, a US federal court to manage requests from the NSA for surveillance warrants against foreign agents in the US. In 1978, the new FISA court appeared to have reigned-in the problem of domestic NSA spying, however, a loophole in the Act, Section 702, authorized the controversial PRISM program that allowed surveillance of online activity. Later, the Bush-Cheney (2001–2009) administration allowed the NSA to engage in spying operations that violated the FISA court for the War on Terror (see chronology 2000s). Edward Snowden leaked information about this activity and was punished by being stranded in Russia. In contrast, James Risen (Citation2006), a New York Times reporter on national security, was awarded a Pulitzer Prize for his coverage of these post 9/11 events in State of War . In 2014 Glen Greenwald also an award-winning journalist, wrote about them in No Place to Hide;Edward Snowden The NSA, and the U.S. surveillance state .
4.2. DCAnet and ARPANET Backbone Distribution Phase
The intelligence community and the police favored G.H.W. Bush and Ronald Reagan and helped elect them to the White House for two terms during the 1980s. ARPANET was in mission service with the DCA and government investigations of the intelligence community ended. McNamara left the World Bank in the midst of a growing recession. IBM began marketing personal computers in 1981, generating a growing demand for fast computer memory chips, and large data storage. In 1982, AT&T lost its anti-trust court case against the Department of Justice and agreed to give up 22 companies that provided most of the telephone service to the American public. Also broken up was the rate averaging system that had kept telephone services affordable for low-income customers, by charging high-income customers more. In the worst recession since WWII, Americans saw their telephone service bills rising. Public concern over military spying and R&D changed to concern over “stagflation” (inflation with slow job growth) and rising costs of living. On 9 January 1982, the “$80 Billion Divesture” of AT&T was announced in an article by Holsenolph in the New York Times (Holsendolph, Citation1982). Another article by Feder (1981) announced the “end of action” of the more than a decade old, government anti-trust lawsuit against IBM, just when IBM was launching the personal computer Citation1982 (see 1980–1990 chronology). A third story was titled, “New layoffs push U.S. jobless rate from 8.9% from 8.4%.” The question “Could business failures of the 1980s have been caused by covert hacking, enabled by new, powerful, non-evident interactive computers and DOJ MIS software, in the hidden and exclusive hands of intelligence or other operatives?” is not unreasonable and invites further study.
In 1983, the DoD officially split DCA net into MILNET for military purposes and ARPANET for civilian purposes, however national security operations would presumably have had access to both, thus blurring the distinction between personal data and data collected for national security; since there were no strong privacy protections for civilians, there was little incentive to reduce the blurriness. In the aftermath of the Bell system breakup, the intelligence community had superior ways to spy via networks, which unlike landline telephone systems showed little evidence of taps nor required human informants. In 1974, the movie, The conversation, showed Americans the potential of wiretapping without visible, evident, or libelous “taps.” As the recession worsened and telephone service rates rose the AT&T Bell Telephone system was broken up into seven “baby bells” that could not compete with the onslaught of new microwave telecommunications regional networks that MCI was overlying onto the AT&T telephone line infrastructure.
The Reagan-Bush administration increased the wars in Latin America, fostered a domestic War on Drugs, and launched Reagan’s favorite program, the Strategic Defense Initiative or Star Wars Program, in space. The military decided it could not identify specific targets as it had aimed to do in Vietnam. Now the US military called the wars abroad “low intensity conflict” or “low intensity war” (LIC of LIW) a different name for counterinsurgency, “where the scale and character of the hostilities are kept just below the threshold where the world would recognize it as overt military aggression” (US Congress. Senate, 1962, p. 20). Low-intensity warfare did not use draftees and bombs, but it did use intelligence data, networked communication systems (like DCA net and the ARPANET backbone), stay-behind nets and promoted development of private military corporations.
By the mid-1980s DCA cloned, stay-behind-nets, linked to the ARPANET backbone, like the ones tested in Vietnam, were being distributed across the world, laying a foundation for the World Wide Web. The Reagan-Bush administration generously funded the wars abroad, the domestic War on Drugs and the Star Wars program, which made the Reagan-Bush administration popular with the military, the police, the intelligence communities, as well as the companies that sold computers and surveillance equipment to the police. MILNET was incorporated into Defense Data Network or Defense Integrated Systems Network. In a 1994 artcle in Communications of the ACM Internet pioneer Robert Kahn explained, “TCP/IP protocol would still allow computers on the MILNET to talk to computers on the new ARPANET, but the MILNET network nodes would be protected by virtue of locating them in protected sites, rather than […] labs and on university campuses” (Citation1994p. 16). By the early-1980s the ARPANET informational infrastructure had created “a viable technology for wider use in defense” (1994, p. 16). Smaller computers and networks cloned from DCAnet and in communication with it were distributed in the largest military base-building campaign, a history described in David Vine’s Citation2015 Base Nation. Bases that Congress would not approve for funding were built with private funds. For example, a base in Honduras that could accommodate “approximately 3,000 U.S. troops” was built and equipped with “radar facilities” under the guise of training exercises listed in Operations & Management military budgets (US Congressional Record, 1984, p. II 6820; Packard, Citation2023).
Under the Reagan-Bush administrations, the contractors building networks abroad, in space and in the US enjoyed greater and greater freedom “[wherever he might go]” (as Weber termed it) to put the government R&D to work in ongoing ways (,2003 , p. 74). Contractors wanted to put the government’s R&D to work in ways that would allow them to run ongoing firms free from yearly government contracts, cumbersome budgeting, appropriation hearings, consumer and environmental protections, and investigations. This was in keeping with how Weber’s first dissertation had described the historical trends in commercial partnerships changing in the maritime industries of the Middle Ages. Contractors negotiated with their employers for more freedom to put the employer’s goods to work in remote locations and establish firms that were ongoing. The Reagan-Bush administration favored these trends; in keeping with Weber’s social order concepts about the power realm, the political leaders issued orders to privatize ARPANET backbone, the NSF and non-NSF networks.
5. Formal Privatization of ARPANET Backbone Phase
Reagan signed an Executive Order 12591 Facilitating Access to Science and Technology in 1987. It initiated the Federal Technology Transfer Act of 1986 which amended the Stevenson-Wydler Technology Innovation Act of 1980 (see 1980–1990 chronology). The Order mandated that the government transfer federally owned or originated technology to state and local governments and to the private sector. The Order reinforced the Federal Technology Transfer Act of 1986 which established a legal foundation for privatizing the ARPANET backbone and included guidelines for transferring government funded R&D to the private sector such as the following:
SEC. 4. International Science and Technology. In order to ensure that the United States benefits from and fully exploits scientific research and technology developed abroad, [… .] (c) The Secretaries of State and Commerce and the Director of the National Science Foundation shall develop a central mechanism for the prompt and efficient dissemination of science and technology information developed abroad to users in Federal laboratories, academic institutions, and the private sector on a fee-for-service basis.
SEC. 5. Technology Transfer from the Department of Defense. Within 6 months of the date of this Order [10 April 1987], the Secretary of Defense shall identify a list of funded technologies that would be potentially useful to United States industries and universities (p. 9).Footnote23
Following orders, the NSF solicited proposals for managing, upgrading, and expanding the ARPANET backbone and the NSF and non-NSF networks. NSF specified that it wanted a “three-level hierarchy” architecture for the network consisting of a transcontinental “backbone” connected to a; “second level” of independently administrated networks that connected with upward of 30 university, industrial, government, or campus networks (US. Congress, 1992, p. 37). Merit submitted a proposal along with its partners MCI and IBM, which also brought along the Michigan Strategic Fund as a private funding source or special fund (third object). MCI had established “regional microwave networks” throughout the US as Cantelon reported.,(Citation1993). IBM had a long, “quasi-governmental” contractual relationship, with the US government as Black reported in IBM and The Holocaust (Citation2001a, p. 120). As noted above, Merit was a consortium of nine universities from the same university system that had sent MSUGroup to Vietnam to build networks and manage the 15-million-dollar government contract. MSUGroup had historic roots in the Detroit Red Squad, Ford Service Department, FBI, and the Michigan State government inter-war and Cold War history that Donner (Citation1990, pp. 291–298), Ernst (Citation1995, Citation1998), and Majka (Citation1981) wrote about (see 1920–1930; 1930–1940; 1940–1950 chronologies). It had helped build Michnet, which enhanced earlier Michigan red squad/FBI and MSU academic networks. NSF trusted Michnet as a model for commercializing its NSF/non-NSF networks. President Nixon appointed MSU President, John Hannah to head the Agency for International Development (AID). Given the government’s relationship with MSU and IBM, and IBM’s business ties with MCI (through SBS) the NSF trusted the partners to manage the commercialization of the ARPANET backbone, NSF/non-NSF networks. Merit met NSF’s demands with a proposal for a faster network and lower cost. IBM contributed software and MCI provided connectivity. The State of Michigan Strategic Fund contributed funding. The agreement was signed by the deadline specified in Section 5 of the Executive Order 12591. On 19 November 1987, NSF awarded Merit, IBM, and MCI a five-year “Cooperative Agreement” that allowed for a lot of self-regulation. Merit could change and improve the networks and the NSF could modify the agreement, adding more funding and sub-contractors (MERIT Network Inc. Citation1987). The contractors negotiated for more freedom to put the ARPANET backbone and the NSF and non-NSF networks to work in an ongoing and distributed way. Without going over budget, the partners refurbished the ARPANET backbone by July of 1988, while backbone traffic compounded every month. The growing demand required ongoing improvements to the ARPANET backbone and the partners increased their contributions and participation in the venture.
In 1989, the G.H.W. Bush-Quayle administration replaced the Reagan-Bush administration. As CIA head G.H.W. Bush had overseen the transfer of ARPANET backbone to DCA, now President G.H.W. Bush would oversee ARPANET’s transition to a commercial Internet. NSF worked with Merit to create regional networks from university system networks, nationwide. In 1991, ARPANET’s military service officially ended and Congress passed the High-Performance Computing Act authored by Senator Al Gore (also known as the Gore Act). It established a new name for the emerging commercialized ARPANET backbone, rising from the ashes of the old backbone, namely “the Internet.” Importantly the act stipulated the US be the leader in high-performance computing, thus requiring Merit and its partners to contribute money to keep the Internet in a leadership position in computing and network technology. Now Merit and its partners wanted commercial clients to help pay for ongoing upgrades to the commercial Internet.
In a 1992 Congressional hearing Merit spokesman Van Houweling noted that “NSF’s additional funding commitment was augmented by major cost sharing by IBM and MCI” (US. Congress. 1992, p. 38). In doing this the partners and the government changed their legal relationship on 17 September of 1990. Merit subcontracted with a new company called Advanced Network & Services, Inc. (ANS). This new commercial partnership allowed ANS to provide network management and operations “for the” NSFNET (MERIT Inc., 1990, p. 1). Now, Merit, through ANS, brokered contracts for improving and expanding the NSF and non-NSF networks, instead of NSF. IBM, MCI, and the Merit Strategic Fund also signed on as part of the commercial partnership of ANS. The NSF approved the agreement and inverted its position with the former contractors, making NSF a customer to ANS, while still being an employer (see chronology 1990–2000).
A subcontract between Merit and ANS stated that ANS accepted Merit’s obligations to the NSF and to the Merit Strategic Fund (MSF) Agreement. ANS would “perform the duties and responsibilities that Merit was obligated to perform pursuant to the NSF and MSF Agreements” (MERIT Network, Inc., 17 September 1990, p. 1). Through ANS, Merit made decisions for the NSF, while ANS met the demands of the original cooperative agreement and the Gore Act.Footnote24 Through ANS, Merit could broker services and make improvements to the networks with more freedom than the federal government’s NSF could. The ANS joint commercial partnership was called the “Parties” or individually a “Party.” The ANS assumed from Merit “all future funding for Services” as well as the “Grant Agreement between Michigan Strategic Fund and MERIT” (MSF Agreement, dated 19 November 1987) as “compensation for services to be provided” (1990, p. 1). The subcontract stated IBM and MCI “shall have made their required initial contribution to the ANS pursuant to the terms of the Formation and Funding Agreement.” A “Dispute Resolution” clause on the third page stipulated that parties settle disputes among themselves to avoid litigation. When litigation became necessary, the prevailing party could recover reasonable expenses incurred (including attorney fees). A 17 September 1990, “Operating Agreement Between Advanced Network & Services, Inc. and Michigan Educational Research Information Triad, Inc.” explained that ANS had a subcontract with MERIT to operate NSFNSET expansion with NSF approval and MERIT would advise the ANS. An “Article VII Information Transfers 7.03” in the operating agreement, mandated NSF would not share Confidential Information received from the parties without “written authorization except as may be required by law” (MERIT Network, Inc., Citation1990, p. 6). Here all the elements that Weber had identified as part of a commercial partnership are represented—a name for the firm (ANS), a special fund (Merit Strategic Fund), agreements for dealing with losses and avoiding hard bargaining, secrecy, and a legal inversion of the former contractors becoming managers and then owners of ongoing capitalist enterprises that moved them out of the social honor realm (with permission from the government employer) and into the market realm.
The ANS certificate of incorporation (approved by the NSF) stressed that ANS was expanding the exchange of information among academic, government, and private industry users, which were the same users the ARPANET had serviced according to the 1959, DOD Directive No. 5129.33. Forming the ANS firm gave the parties more freedom to expand and improve the NSFNET and non-NSF networks in ways that the government might not have been allowed to do. ANS was a private, 501C, non-profit corporation, and did not pay taxes. Through ANS, the parties usurped the government’s non-profit NSF networks and non-NSF networks. As Weber had described in his dissertation about commercial partnerships, contractors sought more and more freedom to invert their position with their employers, allowing them to establish ongoing firms as new members of the market realm. ANS could put the US government’s special goods to work in an unregulated, ongoing commercial enterprise rather than working on a contract-to-contract basis. However, it was necessary that ANS keep the US at the forefront of high-performance computing, as mandated by the Gore Act, which incentivized ANS to charge Internet users to subsidize a fund for Internet maintenance.
The ARPANET backbone, now an ANS asset, was no longer owned by the US government nor was there a price tag for it because in the social realm special goods had no price tag or were priceless while in service to national security, as Hitch & McKean (Citation1960/Citation1965) had argued in their book The economics of defense in the nuclear age. Weber argued that hard bargaining in the marketplace over the sale of a good was avoided by members of the social realm (Packard, Citation2023). ANS could rightly assert that “network hardware itself is owned by ANS and communications facilities are leased by ANS from MCI and others” since ANS had, under authorization of presidential orders, usurped NSF’s management of the networks in accordance with Ex. Ord. No. 12,591 and with permission from the NSF (US, 1992, p. 39). The ANS began collecting a bundle of rights to take on a “personality” as Weber (Citation2003) wrote about (p. 56).
Next, ANS formed a for-profit ANS CO+RE Systems, Inc. to subscribe prospective commercial customers who wanted to lease Internet access (see 1990–2000 chronology). The goal was to bring academic networks into a commercial relationship through the Internet. The for-profit subsidiary ANS CO+RE Systems Inc. was established on 30 May 1991, to interface with commercial customers like AT&T. Importantly, Kesan and Shah (Citation2001) noted that NSF “agreed to allow ANS to solicit commercial users for almost a year before alerting the public” (p. 122). Kesan and Shah’s (2001) documentation of this history is noteworthy since the Office of Inspector General found “lack of documentation” regarding NSF’s decision to allow commercial access to the NSFNET (or ANSnet) without either peer review or review from the Supervisory of National Science Board (p. 122). However, after the ANS was formally privatized, peer review was unnecessary.
ANS CO+RE Systems Inc. sold customer connectivity to ANS for a fee. Fees for connectivity to ARPANET/ANS net were paid by the customer, and taxes and operating expenses were deducted; the remainder was “returned to ANS for reinvestment in the network infrastructure” (US Congress. 1992, p. 40). The money returned to ANS (from customers’ fees) went into a fund to pay for improving the Internet, thus allowing the US government to begin withdrawing its funding for the Internet. Over time, the collected monies would offset what Merit, IBM and MCI had initially contributed. The fund grew as customers rented access to the Internet and populated a new kind of territory called cyberspace.Footnote25
The Director of the Division of Networking and Communications Research and Infrastructure and the consultant NSF hired to work with ANS was Stephen Wolff. Lickleider’s biographer M.M. Waldrop (Citation2018) quoted Wolff explaining how NSF “forced the regionals to become general-purpose network providers” adding that there were “all these young but extremely vigorous commercial operators who had no commitment to academia. They would just sell Internet access to business, industry, individuals, whoever would buy it” (p. 439).
As a subsidiary of ANS, ANS CO+RE System Inc., met the NSF’s transfer and commercialization goals. It was a for-profit-legal arrangement mirroring the non-profit ANS. NSF and Merit, the non-profit ANS and for-profit ANS CO+RE Systems Inc. commercialized the Internet in a planned (not a free market) way. Kesan and Shah (Citation2001) described this process, as did Mitchell Kapor of The Electronic Frontier Foundation and William Schrader of Performance Systems International Inc., to name only a few (US. Congress. 1992). Kapor said that the ANS approach to commercialization was not competitive, but individually selective. A company that wanted commercialized access to the Internet had to go through ANS CO+RE Systems Inc. and pay to become a commercial network. The ANS insisted that anyone could have commercial access by signing up for it through regional networks that used the “ANS-run backbone service” (US. Congress. 1992, p. 117). However, companies wanting free network services through NSF networks (owned by ANS) had to use the on-line service only for academic and research purposes not commercial services. A few companies were selected and paid for commercial service (like Sprint, AT&T, and a few others), while others were hindered from participating in the new and emerging digital market system causing bottlenecks. Kapor complained that Wolff withheld the ANS backbone access from the open market, but Wolff acted in accordance with the most important aspect of the social honor realm mission, the “hindrance of the free development of the market” (Weber, Citation1978, pp. 2:937).
The bottleneck problem or the planned installation of the ARPANET into the market realm was resolved when NSF subsidized the regional networks, so they could buy commercial network services through ANS CO+RE System Inc. Access to the ANS backbone networks for commercial use was not obtained through free market competition but through planning and government funding. The ANS network was commercialized without disrupting the original three-tiered infrastructure with a national backbone, trans-continental services, the regional layer, and the local area networks, in a way that could “maintain the connectivity to the research and education” (US. Congress. 1992, p. 118). However, it also maintained the intelligence community’s surveillance of the academic community that the ANS network afforded. Electronic monitoring of academics continued seamlessly since the military feared academics might turn Communist, as some had during “the Great Depression”—even worse, they might socialize the Internet or commercialize it by themselves (US. Congress. Senate. 1976c, p. 524). This was a concern to the intelligence community, the police, and the Complex because they needed an unregulated Internet for their own operations and to service money management for multi-year, military contract budgeting.
Weber observed that as contractors contributed more and more into commercial ventures, the contracts changed, allowing the contractors more freedom to commercialize the employer’s product. As the contractor’s role changed into a commercial vendor’s role, the new businessmen (the former contractor) were able to offer shares of the firm to the investor or invite the investor to be part of a limited partnership. This was demonstrated in 1992, when Al Gore and the Democratic National Committee received thousands of dollars, including “a $50,000 contribution from MCI” from companies like Sprint, U.S. West, and NYNEX, all newly connected to the commercial Internet as Kesan and Shah (Citation2001, p. 119) described.
In 1992, Merit and ANS signed the Strategic Partnership Plan, which included establishing a headquarters in Ann Arbor, Michigan, and stipulations that all ANS internet traffic would transverse Michnet.Footnote26 In Spies for Hire Shorrock (reported on important administrative developments that shaped the young telecommunications industry:
… the number of government agencies that were privatized during the Clinton administration is astounding. One of the first government services to be sold to private interests was the vast computer network known as the Internet […]. In 1993, the Clinton administration turned over the registration of domain names—the addresses that are used for e-mail and Web sites—to a private company called Network Solutions (perhaps this is what Gore meant in 2000 when he claimed to be the “inventor” of the Internet). A few years later, when the company’s government-sanctioned monopoly became controversial, management of the Web was handed over to an international consortium called the Internet Corporation for Assigned Names and Numbers of ICANN (Shorrock Citation2008, pp. 87–88)
The World Wide Web opened to the public in 1995 (see 1990–2000 chronology). Political leaders hoped the commercialized Internet would drive job growth. That same year, Congress passed the Telecommunications Deregulation Bill, eliminating most regulations of the US communications industry. Communications industry concentration increased rapidly after Clinton signed the Telecommunications Act of 1996. The world’s largest sale of public utility communications property and the four largest corporate mergers of communications companies in history followed after, which former Project Censored, Director Carl Jensen’s (Citation1997) book 20 years of Censored News addressed (pp. 320–321, 324–5) and Robert McChesney (Citation1996) and others like Ralph Nader, wrote about.
By 1996, the formal privatization of the ARPANET into the Internet was achieved when ANS (Merit, IBM, and MCI) inverted its position with NSF (the government/investor) and established a capital fund (to pay for Internet improvements) and a joint name (see chronology 1990–2000). The new telecommunications companies that contracted with ANS were in a position to acquire a legal personality or bundle of rights, as Weber described in his History of Commercial Partnerships.... While the public transitioned away from land-line telephone service to new kinds of electronic communication devices, the CIA had been experimenting with “ghost detainees” prisons, and the NSA was exposed in international spying (Echelon) (see chronology 1990–2000). The CIA renditions involved skirting FISA and Echelon showed what networked enhanced NSA spying in Europe might do in a US setting.
The attack on the twin towers in New York on 9/11 gave president G.W. Bush Jr. a reason to issue secret orders that pressured the new telecommunications companies to help wage the War on Terror—essentially by spying on their customers (see chronology 2000s). The presidential orders freed the companies and the intelligence community from FISA regulations. By searching for terrorists who might have caused the attack, the new telecommunications companies followed in the footsteps of the telephone companies that had helped wiretap landline telephones for the FBI. The new telecommunications companies that cooperated with the government were rewarded for having acted in “good faith” and the administration granted them retroactive immunity (The Harvard Law Review Electronic Surveillance, 2009). The telecommunications companies had acquired a bundle of rights that protected them from civil lawsuits over privacy violations. This also protected the government from potentially risky court testimony and press coverage.
The next year the Citizen’s United Act was passed. It granted corporations free speech rights the way Americans have constitutionally protected free speech. This allowed corporations to give unlimited campaign finance to political parties, as an extension of the corporations’ constitutionally protected speech. Political parties need campaign finance to promote their policies since politics entails a lot of publicity and elections. Weber had argued that once firms were established, they could return shares to former employers. The Citizen’s United ruling allowed the telecommunications companies to return some of their profits to government leaders in the form of campaign finance (see chronology 1990–2000). Preserving free speech was necessary for agency intelligence gathering functions (for future reference) and for legally backing the Citizen’s United Act, which gave the telecommunications companies a way to share their profits with politicians. Even telecommunication company customers have unlimited and protected speech on their devices, since it is stored for future reference. No longer hindered from the market, the formally privatized Internet now had its personhood with a triangulated, legal bundle of rights and protections, a special fund, and a name and had transitioned into the market realm.
6. Conclusion and topics that invite further study
As described above, ARPANET was decades in the making, riddled with secrets and the history fragmented or scattered. When information was missing or secret Weber’s social order and ideal type concepts helped generate a coherent, meaningful history for the ARPANET. ARPANET development history draws on some technical development histories cited in the introduction and ARPANET’s counterinsurgency testing history, which traversed countries and continents. Changes in types of counterinsurgency warfare relied on those technical developments. When history was assembled from scattered sources, new questions arose. To organize the findings, get around unanswered questions and make a meaningful, coherent history of the testing, distribution, and commercialization of the ARPANET backbone, Weber’s theoretical frameworks helped to interpret the history of this arguably most expensive invention in history.
To answer the research questions like: How was the ARPANET tested? Once ARPANET passed military tests in anti-Communist counterinsurgency, why was it not commercialized then, instead of being put into mission service with the Pentagon and commercialized a decade later? meant following the discourse across borders and over decades, within and outside of the Cold War years. By the 1980s each sector of US society had different reasons to demand a commercial Internet. The public wanted to fill the void of government regulated civilian telephone services that were going away; the government wanted to free itself of managing risky interactive intelligence databanks, and the intelligence community wanted to upgrade their wiretapping technology after the FBI had used telephone company employees and police departments across the US for decades to wiretap countless numbers of US citizens land-line telephones (how many is unknown). Wiretapping was an institutionalized practice for the FBI and law enforcement purposes. It was labor intensive and left physical evidence on telephone lines and was hard to keep secret. Thus, the intelligence community anticipated computers and wireless networks that were essentially invisible to civilians and taxpayers, less costly to spy with and did not require informants who might testify in court or in investigations. If customers could see how the wiretapping happened, find evidence and use it for court cases that revealed government illegal, unconstitutional spying, the intelligence agencies could have been exposed to what Weber (Citation1978) termed hard bargaining (court cases or bad press) that would have put social realm actor’s jobs at risk (p. 2:937).
Who built these new types of evidence-free, technical collection systems? Answering this question entailed distinguishing a largely hidden, contacted, OSG workforce and sketching the histories of their market realm or quasi-governmental employers. Weber’s social order concept helped to illustrate this information (see Appendix A, Max Weber’s Social Order). The social order model distinguished the workforce that produced for the market, from the workforce that hindered the market, and tested and used special goods against the Communist threat. Weber’s social order helped to make ARPANET more evident by distinguishing the special good or third object (the ARPANET backbone and its databanks and adjoining networks) from the human workforce or OSGs who built and tested it. The concept helped show how national security OSGs withheld special goods, like the ARPANET, from enemy hands and from the commercial market until the political party ordered the ARPANET be formally privatized and commercialized. In their capacity as social realm contractors for ARPANET R&D, Merit, IBM, and MCI helped create demand for the new and wireless networks that government funds had helped build. They were well positioned to formally privatize the ARPANET backbone and NSF net and non-NSF networks in legislated steps, with help and permission from the NSF, funding from private and government sources and through forming two commercial partnerships, nonprofit ANS Inc. and for-profit ANS CO+RE Systems Inc. Like the contractors Weber wrote about in his first dissertation, IBM, Merit, and MCI inverted their position with their employer. The federal government employer became a customer of the new telecommunications companies as they ushered the commercial Internet into the market realm.
Showing some of the history or the legal personality, of the companies that privatized the ARPANET backbone meant gathering and chronicling some history about Merit, IBM, and MCI. Chronologies are shown in Appendix B to hold the data and illustrate the phased history of the ARPANET backbone decade by decade. The chronologies sketch events pertaining to Merit, IBM, and MCI in regards to ARPANET development; testing; distribution; formal privatization; and legal personhood.
IBM has a long “quasi-governmental” history with the US government that Edwin Black (Citation2001a) among others has chronicled. Merit’s history is tied into Michigan’s interwar history and aligned with 1950s Michigan State University Group (MSUG) history and 1960s Michnet (Michigan network) history (see chronologies 1920–1950). As a technical collection system that was pioneered abroad in Vietnam, Michnet greatly advanced upon the human networks forged in the interwar and WWII years, designed to break up labor unions, spy on Ford employees, manipulate political elections, neutralize strikes, and purge activists as described by Majka (Citation1981) in,Organizational linkages, networks, and social change in Detroit. MCI grew into a major corporation after a 1966 study showed an “economic need” for common carrier microwave regional networks (what the economic need was, invites further study). IBM, Merit, and MCI built microwave, fiber optic, and satellite communication systems that could facilitate a merger of the commercialized Internet once the ARPANET backbone was under orders from the president to be privatized in legislative steps (see chronology 1980–1990, Citation1990–2000). Weber’s description of contractors seeking more freedom from employers to establish their own firms aptly describes the formation of ANS Inc.
The chronologies help show how Michigan state legislators, automotive industries and industrialists, the police, the Detroit Red Squad and the FBI worked together to monitor and purge citizens considered threats to state and corporate interests. With the advent of the Internet, these historical, human, networks became meshed into the ARPANET backbone, the NSF and non-NSF networks, Michnet and its adjoining MSU statistical science and processing facilities. Michnet meshed with the Internet (or ANS net) made it more convenient for new types of OSGs to process telecommunications data and share it among the long-established, human-based, networks of state legislators, police, industrialists, and the FBI, or “organizations that attempted to prevent the social functioning of more liberally-oriented groups” as Majka (Citation1981) expressed it.
6.1 Topics that invite further study
Arguably all ARPANET history invites further study in print, online and through archival research at the National Security Archives. There are many topics that invite further study, but too many to list here. Topics like, why was not Michnet part of ARPANET? Or what Environmental Impact Reports were made for the ANS networks? need more research. Questions like: What if taxes were not collected at the source? Or, what constitutes a national security special good? need more research. For example, classified information or government secrets are a special good that loses its value when leaked. Is classified information sometimes leaked to the public when it is expedient for military interests—perhaps for withdrawing from a war? How much freedom and the kind of lifestyle a whistleblower enjoys in the market realm (or suffers in prison) might be a reflection of how a military employer has or has not authorized the special good to be leaked? Did self-enforced agents act with a higher validity (in service to the president and national security) than Edward Snowden (a spy turned whistleblower for the public good) did, when Snowden leaked information about operations that Glenn Greenwald (Citation2014) published? At the other end of this spectrum, too much classified information may destabilize an Empire. In Lords of secrecy: the national security elite and America’s stealth warfare Scott Horton argued decisions about war are made by self-directed and unaccountable national security elites, which are kept secret from the public and can destroy democracy. This is similar to what Simpson (Citation1995) observed, that security directives “often contain elements paradoxically intended for publicity within elites’ national security circles yet secrecy from the public at large” (1995, p. 7). Social realm OSGs show off what they covertly do, to elite leaders, while keeping this secret from the taxpayers, from Congress-people who might change tax laws to stop collecting taxes at the source, or neutralized people who might bring lawsuits. Horton (Citation2015) acknowledged Max Weber’s preoccupation with state secrecy, writing, “So, reflected Weber, why did Germany lose World War I? […] Weber focused on identifying Germany’s structural weaknesses, and he became convinced that Germany was hurt by its obsession with state secrets.” (pp. 54–55). State secrets are a special good, like the ARPANET, that the social honor realm can release or retain according to its own expedient needs and this invites further research.
Correction
This article has been corrected with minor changes. These changes do not impact the academic content of the article.
Acknowledgements
Thank you to Dr. Neal Curtis, Associate Professor of Media, film, and Television at the University of Auckland and Associate Dean of Post Graduate Research, who supervised my thesis entitled, Exploiting and Neutralising the ‘Communist Threat’ for the Privatised Internet, which this article draws on. Thank you to the Faculty of Arts of the University of Auckland for a $4000NZD 2020 Covid Initiative award to promote publishing some of my PhD thesis research. This article and another work-in-progress entitled, “Changing Information Infrastructures from Imperial Germany to Cold War USA: A Prehistory of the ARPANET” share this award. Thank you to professors James Galbraith, Economics, University of Texas, Austin, Mike Lloyd, Sociology professor atof Victoria University of Wellington, and Emeritus professor Dean Dorn, Sociology, California State University, Sacramento, for reading article drafts. Milan Law helped with the graphics. Thank you to Spot It Proofing and UPS . Thank you to Editor Dr. Guangchao Charles Feng , Bavadharani Lakshmipathy and the Production Team at Cogent Social Science: Media & Communication Studies. This article is dedicated to Douglas Valentine, Michael McClintock and Christopher Simpson whose books have been valuable for this research.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
Notes on contributors
Noel Packard
Noel Packard is an interdisciplinary and multidisciplinary, theorist who applies classical theories of Karl Marx, Max Weber, and other classical theorists to contemporary issues of individual, collective, and electronic memory. I test how classical theories that predate the Internet can help to interpret todays Internet issues and understand the history of the Internet. She has a PhD in Media, Film, and Television from University of Auckland, a BA Honors in Sociology from Victoria University of Wellington, NZ, an MA in Sociology from the New School in NYC, an MA in Public Administration from California State University, East Bay, and a BA in Economics from California State University of Fresno, CA.
Notes
1. ARPANET was originally built by the Defense Advanced Research Projects Agency (DARPA) which was established in 1958. DARPA changed it’s name to Advanced Research Projects Agency (ARPA), then returned to using DARPA (from 1970–1993), then it changed back to ARPA; later it changed back to DARPA. Both names appear here. ARPANET was a network of networks that communicated with interactive computers which were in the control of political officials, the military and private companies. It was a network that other networks grew from. It was called both “ARPANET backbone” and a “general computer” since it transmitted classified and unclassified documents from 1969 to 1975. ARPANET is thought to be the most expensive invention in history and presidential orders would have been sent on such a state-of-the-art communication system because it left no evidence of the transmission. ARPANET and the computers and networks derived from it were invisible or non-evident to the public and Congress to protect government and corporate interests that used the networks for national security operations in the years before ARPANET backbone was formally privatized and commercialized into the Internet.
2. ARPANET R&D generated many inventions such as: time sharing; the interface message processor (IMP) which allowed different computers to talk to each other; interactive computers; TCP/IP or transmission control protocol/Internet protocol; packet switching; and the World wide Web. Authors who have written about these technical milestones include Jeffrey MacKie-Mason & Hal Varian (1994), Peter Salus (1995)), Arthur Norberg & Judy O’Neill (1996), Katie Hafner & Matthew Lyon (1996), Janet Abbate (2000), Manuel Castells (2001), John Naughton (2001), Nathan Newman (1998, 2002), Milton Mueller 2002 and Yasha Levine) among others.
3. ARPANET backbone was transferred to mission service with the Defense Communications Agency (DCA) in 1975–6. DCA is a US Department of Defense (DOD) combat support agency and is linked to White House Communications Agency. It was established in 1960 in Fort Mead, Maryland. In 1991 DCA changed its name to Defense Information Systems Agency. After a decade of DCA service, the ARPANET backbone was transferred to National Science Foundation (NSF), which commercialized it under orders and in planned steps.
4. The intelligence community consists of dozens of secretive government agencies and the most well know ones are: the Federal Bureau of Investigation (FBI) established by J. Edgar Hoover; the Central Intelligence Agency (CIA) established through the National Security Act of 1947; the National Security Agency (NSA) established by secret executive order in 1952. The NSA intercepted communications from US “enemies and friends” to secure US codes from being intercepted by others. Marchetti and Marks (1980) wrote: “The NSA though placed under the control of the Defense Department, soon established an independent bureaucratic identity of its own” including hundreds of listening posts all over the world operated by other U.S. agencies such as Army Security Agency, the Navy Security Service, and the Air Force Security Agency, all under the NSA’s policy coordination “ … the messages they intercept are sent back to NSA headquarters at Fort Mead, MD, near Washington” (pp. 167–168).
5. The Cold War (1945–1990) was a period of hostility between the US and the Soviet bloc countries that was not “hot” (active warfare) but “cold” because it entailed counterinsurgency warfare that relied on spying, surveillance, and computer-enhanced operations. The US was promoting the buildup of North American Treaty Organization (NATO) countries abroad and fostering anti-communism at home. The spy operations were generously funded and unregulated; intelligence agents had legal immunity and were “self-enforced” (US. Congress. Senate. 1973b, pp. 7, 117). As such, the Cold War era acquired the reputation of being an “anything goes” time (McClintock, 1985, pp. 30, 1992, 137, 341). The government took a hands-off approach to counterinsurgency, the intelligence community, and the ARPANET R&D. When the US public demanded the government regulate the intelligence community, the government’s response was to enact laws that limited the public’s ability to access government records and increased spending on wars, spying, and policing.
6. Neutralization first meant that political activists were monitored, tracked, and rendered inactive; a practice used in the US as Johnson 1990 and Rorabaugh (1989, pp. 104–5) described. It grew to include assassination and a range of abuses of alleged and real Communists and those the military considered subversive. In other countries, it became more aggressive; stalking and targeting people considered to be enemies, for targeted assassination, as described in Vincent Bevin’s (2020) book The Jakarta Method, Michael McClintock’s (1985) The American Connection and Lt. Col. John L. Cook’s (1997) The Advisor: The Phoenix Program in Vietnam. These counterinsurgency operations used political intelligence, electronic monitoring, computer data banks, and early forms of software to track people as targets and neutralize them. It turned warfare into a “battle of man against man” to use Weber’s terminology (1978, pp.1: 92–93) or to use Cook’s (1997) terminology, a “personalized” type of warfare (pp. 120–121). Valentine (2000) examined the changing meanings of (and the changing targets of) neutralization from the “Phoenix concept of ‘explicit terrorism’ disguised as antiterrorism” to the concept that only assassinations of heads of state qualified as assassinations (p. 427). Counterinsurgency operations against the Native American Indian Movement (AIM) and Black Panther Movement are detailed in Ward Churchill and Vander Wall’s (1990) Agents of repression. Donner (1961, 1981, 1990), Keller (1989) 1989), Wilford (2008), Zwerling et al. (2011) and Rosenfeld (2013) report on how these programs impacted the academic communities and New Left. Jeff Halper (2015) and G.H.W. Bush used the term “pacification” for neutralization (Baker, 2009, p. 131).
7. Low intensity warfare (LIW) or low intensity conflict (LIC) was what the US military called counterinsurgency after President Reagan signed NSDD 277 authorizing the Complex “to develop and implement a unified national strategy” for LIW as Klare & Kornbluh reported in in 1988 in Low Intensity Warfare 1988, (p. 6) and Simpson reported in National Security Directives, (1995, p. 742) (see chronology 1980–1900). LIW had roots in counterinsurgency and was developed for Latin American countries “after the 1959 Cuban revolution and for South Vietnam in the early 1960s.” (1988, p. 6) It was a coordinated program of political intelligence and surveillance coupled with psychological operations and security measures. Thus, the US military did not appear to be provoking conventional war and maintained plausible deniability. Plausible deniability became a priority when the CIA formed the Office of Special Projects for covert operations (such as NSC 10/2 against foreign threats) because the operations were done in ways that “would always afford” the government was not accountable (Stone & Kuznick, 2013, p. 213). In Surprise, Kill Vanish Anne Jacobsin wrote that plausible deniability was made into an “official construct” to protect the president (2019, (p. 36).
8. COINTELPRO (1956–1971) is a code name for FBI operations that spied on people suspected of Communist or subversive tendencies across a wide range of society from far-right extremist groups to what the FBI called the New Left (Senate 1976c pp. 86–96) In 1976 in The Lawless State, Morton Halperin et al. 1976), wrote that after HUAC was censored in 1956, FBI Director J. Edgar Hoover set up COINTELPRO on his own, without government oversight or approval. In 1965 a government publication entitled, “The Anti-Vietnam and teach-in-movement … ” raised fears that Communist agitators were stoking anti-war sentiment (US Congress Senate, 1965). President Johnson urged the intelligence community to find anti-Vietnam War agitators and the CIA ran CHAOS (as indicated in the illustration in Appendix A). The FBI and CIA both agreed to ran domestic operations while ARPANET was in testing phase and a general use computer (1969–1975) transmitting both classified and unclassified electronic communications among the Complex. ARPANET was being tested by these spy programs and Phoenix, while IBM was building smaller, more powerful and interactive computers, Merit was building Michnet and MCI was developing a nationwide microwave system (see 1960–1970 Testing Phase chronology in Appendix B). Donner (1971, 1981) and Zwerling et.al. (2011) reported on how CIA and FBI spies infiltrated student movements.
9. Edward Shils had served in the Office of Special Services, which became the CIA after 1947. Although he did not complete a PhD, Shils taught sociology at the London School of Economics (where Friedrich A. Von Hayek taught) and at the University of Chicago (where Milton Friedman taught) and was a participant in Hayek’s Mont Pelerin Society. Hans Gerth and C. Wright Mills plagiarized Shils translation of Weber’s “Class, Status, Party” essay and published it in their book Max Weber: Essays in Sociology. Oakes and Vidich (1999) wrote about this scandal, which caused a professional rift between C. Wright Mills and the established, neoliberal, Weber translators (Parsons, Knight, Shils). Shils (1956) went on to publish Torment of secrecy: The background and consequences American security policies which advocated that Americans respect national security elites and trust them, since ordinary citizens were not informed enough to participate in government decision making about national security budgets or policies. In 1960 Mills (1960) published “Letter to the New Left” in the New Left Review, and the FBI adopted the term “New Left” for people targeted for COINTELPRO. Mills was on the FBI watchlist and knew it; he died of a heart attack in 1962. Mills’ daughters, Kathryn and Pamela (2000) wrote about how they remembered their father’s death. This history demonstrates how neoliberal OSGs tried to control the consumption of Weber’s translated works in the US.
10. In 1895 upon taking a Chair at University of Freiburg, Weber made an inaugural address, “The Nation State and Economic Policy”. He argued there were many neutral statistical facts and advanced scientific products, but people still viewed them according to their “value judgements” (Weber,1994 1994 p. 18). Weber was saying that human bias and “old general types of human ideals” overshadowed or colored whatever neutral science, idea, or product was produced. He urged Germans to cultivate “conscious self-scrutiny” about this (p. 19). In Weber’s lifetime, Ford Motor Company mass produced the first commercial car. No matter how many models or types of car were produced, or whether cars were used for civilian or military purposes, the car retained the original four wheels and a motor. Shortly after Weber died, Ford promoted the anti-semitic newspaper “The Dearborn Independent” along with its cars, demonstrating how the neutral, scientifically, systematically, produced car product could also be a vehicle for old, general types of Nazi ideology (Black, 2009, pp. 2–16). Weber understood that people’s ideas colored their sense of reality and played an important, trackmen, role in how things did or did not change. Weber was doubtful about how much science could predict human behavior and his theories are not systematic.
11. This might remind Americans of the Citizens United Act, which ruled corporations are essentially individuals with free speech rights that allow them to make unlimited campaign contributions.
12. Hitch and McKean (1960/1965) discussed the impossibility of ascribing prices or price caps to national security expenditures; justifying an endless flow of tax revenue spent on endless wars at the expense of unmet social needs. Weber argued that the market can not meet social needs when money is diverted to more “urgent” needs such as war and leads to “a battle of man against man” (Packard, 2023).
13. Licklider said in a 1988 interview that he “stayed out” of what another scientist named Godel was doing in Vietnam. However, Lick knew the Army Research Office would be “happy to join ARPA and make a team”. He said he feared Godel was trying to “get control over” his research (Aspray & Norberg, 1988, pp. 28, 34). I maintain ARPANET general computer serviced the Vietnam War and the Phoenix Program, although the general public and Congress were uninformed about this new communication technology hidden from them in the same way the Nazi’s had kept tabulating machines hidden from the Germans. Edwin Black (2001) wrote that many Jews did not know how the Nazi’s selected them for the concentration camps until the Holocaust Museum opened in Washington, D.C. and displayed the source of the tracking data—the Hollerith tabulating machine. Tabulating machines, like the IBM computers that followed after them, were inaccessible to the general public, kept in secured places, and used exclusively. This made spying easier since civilians could not see how the monitoring was done, nor could they confront the spies, nor could they obtain evidence to prove that the spying was happening; thus, legal recourse for civilians was denied, while spies were protected. This was in keeping with the FBI’s modus operandi, stemming from Hoover’s 1950s “Responsibilities Program” and enhanced with networks, interactive computers, and the ARPANET (Rosenfeld, 2013, p. 35).
14. Around the time J. Edgar Hoover died in 1972, ARPA’s Information Processing and Technology Office (IOTO) contracted with Bolt, Beranek, and Newman to clone two upgraded networks, modelled on the ARPANET: The Community Online Intelligence Program (COINS) network and Platform Network. Abbate (2000) noted that COINS provided the National Security Agency (NSA) and the Pentagon “operational data communications” via ARPANET “for many years” (pp. 134, 234 n19).
15. Transcripts of the newscasts and a description of ARPANET were published in the proceedings of Surveillance technology joint hearings before the Subcommittee on Constitutional Rights of the Committee on the Judiciary and the Special Subcommittee on Science, Technology, and Commerce of the Committee on Commerce (US Congress Senate, 1975, pp. 3–6).
16. Congress held a Hearing of the Select Committee on Intelligence chaired by Congressman Pike of New York. The committee heard testimony about pervasive police wiretapping as “the most effective law enforcement tool” and the NSA operating as an “independent agency” (US Congress. Senate 1975–76a; US Congress. Senate 1975–76b). Congress terminated the Pike Committee, and President Ford suppressed the findings and assigned G.W.H. Bush to head the CIA in 1975–1976; when ARPANET was transferred to DCA. Many other committees investigated the intelligence agencies. Upwards of 80 investigations were reported on in the 1970s with the most famous one being the “Senate Select Committee to Study Governmental Operations, with respect to Intelligence Activities” (commonly called the “Church Committee Report”). It was a Senate sponsored study of the abuses of the intelligence community chaired by Senator Frank Church. The report filled six volumes and was about 4,000 pages (U.S. Congress. Senate. 1976a,b,c).
17. Donner often uses the term “future reference” as an ambiguous expression for what I would term future neutralization. As I understand it, Donner thought the political intelligence community monitored civilians who they did not think were American enough and then planned how to set them up in ways that helped the intelligence community further its operations for national and job security. Today, computer data banks and AI make this process easier or more convenient.
18. Established in 1961, in El Salvador, ORDEN (1961–1979) was known as Organización Democrática Nacionalista (National Democratic Organization). As Michael McClintock (1985) reported, it began as a civil defense or reserve army of civilians that grew into an intelligence-gathering infrastructure for the Salvadoran armed forces that meshed with computer-assisted, counterinsurgency and paramilitary operations for special operations and military recruitment. I argue this network proceeded and was built up at the same time that ARPANET and Michnet were built in the US and may foretell how networked societies function over long periods of time. Today El Salvador’s government has a prison system that may be the largest in the Americas and a militarized police force that protects civilian areas from militarized gangs, thus polarizing society into the (police protected) free citizens and the unfree citizens (in prison); ideal type comparisons might be drawn to other highly networked countries such as Israel and Palestine.
19. When Congress approved the National Security Act of 1947 it officially created the CIA and Air Force and established a premise for developing weapons to fight the Communist Threat. Anti-Communist counterinsurgency became a “third kind” of warfare, exemplified by operations like NSC 10/2 or clandestine military operations performed with “plausible deniability” (Stone & Kuznick, 2013, pp. 213, U.S. Congress. 1962, 20). These operations enlisted Nazi and Eastern European informants hired by the National Security Commission (NSC). Soon after, Americans’ negative attitudes towards Germans changed to anti-Communism and promoted NATO (Simpson, 1988). Out of these events, ARPA was established, tasked with building high-risk, high-cost, and secret weapons to counter Communism, including the most expensive invention, the ARPANET.
20. PHMIS, DOJ MIS and Prosecutors Management Information Systems or PROMIS were software that retrieved electronic data and made it possible to track individual people or data before the commercial Internet (Valentine 2000). The long saga of PROMIS is reported on by Ben- Menashe (2015); Fricker (1993, 2013); Linsalata (1991); Packard (2020a, 2023, p. 87); Thomas & Keith (1996); the US Congress (1990)(1990) among others. Such software made the tracking of any kind of electronic data possible and enabled tracking civilians across borders and neutralizing them as Ben-Menashe reported. This kind of software was necessary for tracking electronic banking transactions for legitimate transcations or for electronic fraud and bankrupting as Thomas interviewed William Hamilton, the inventor of PROMIS, about. The Reagan administration distributed versions of PROMIS and those who used it, such as Wakenhut (with its private collection of files on Americans), anticipated, I surmise, an unregulated or free Internet to implement their software needs on.
21. Cantelon (1993) wrote that before the end of WWII, IBM, GE, Philco Corporation, Western Union, and AT&T had built microwave networks between US cities in the early 1940s (pp. 508–524). The FCC stopped the microwave expansion. This set GE and IBM against the FCC and against government regulation. The FCC “long blocked” FBI wiretapping so the FBI joined with the corporations (McConahay, 2018, p. 199) Cantelon (1993) chronicled how MCI fought the FCC and built regional microwave networks across the US.
22. Susan Brinson (2004) described how the anti-Communist Dies Committee mobilized with the television companies, politicians, and the FBI to launch aggressive investigations into whether FCC staffers were Communists. Brinson (2004) wrote, “Between 1940 and 1960 FCC commissioners made appearances in a minimum of 80 House investigations and 96 Senate investigations, with peak attendance during the 77th Congress (1940–1941) and the 84th through the 86th Congresses (1955–1960)” (p. 15). FCC Chairman Fly resigned under the strain of on-going investigations and the FCC became more of a protector of the media market, rather than an industry regulator.
23. This extract of Exc. Ord. 12591 is from a summary of USC 3710: Utilization of Federal Technology under Title 15/Chapter 635/§3710. http://uscode.house.gov/view.xhtml?req=(title:15%20section:3710%20edition:prelim)
24. In 1991 Congress passed the High-Performance Computing Act authored by Senator Al Gore. Often called the Gore Act it mandated that the US be the leader in high-performance computing and required MCI, IBM, and MERIT to contribute to the Internet in on-going ways to keep US computing in a world leadership position and the Internet upgraded. It also established funding for the National Research and Education Network (NREN) and helped coin the name Internet. This bill spurred ANS Inc. to seek commercial clients to help pay for the required upgrades.
25. I would argue that the arraignment operated somewhat like the “Transfer Agreement” (Black 2001/1984). Zionists and Nazis made a pact whereby Jews could liquidate their wealth and leave Nazi Germany to settle in Palestine to establish their own homeland (Israel). A Zionists Liquidation Bank sold Jewish assets to the Nazis and the first thousand pounds, “minus a small percent for administration” was returned to the Jew. The remaining proceeds went into a fund for buying German products for Israel (2001/1984, p. 136). Jewish wealth went to the Third Reich, while Jews became occupants of a usurped homeland with trade ties to Germany and subsidies from the US. Halper (2015) and Loewenstein (2023) discussed how these developments impacted the Palestinians as Israel developed its own ways to pacify Palestinians and usurp their homeland without providing them with a Transfer Agreement.
26. To reiterate, Michnet was a university system network rooted in MSUG expertise that supplanted long-established human organizational linkages between universities, private companies, state government, police red squads, and the FBI dating back to the 1930s and even earlier. These anti-Communist networks were examined in Majka’s “Organizational Linkages, Networks and Social Change in Detroit” (1981). This dissertation examined “organizations that attempted to prevent the social functioning of more liberally-oriented groups” in Detroit. Majka justified the research because it provided “data which have been difficult to obtain” (1981, p. 5). Although Michnet was not part of the ARPANET, after ANS privatized the Internet, ANS usurped communications from the former ARPANET and filtered them through Michnet. Michigan state universities are world famous for their advanced statistical science capabilities and training programs. Data flowing from ANS networks through Michnet flowed through a statistical industrial center in the heart of a state with powerful automotive industries, organized red squads, conservative political networks with longstanding ties to the FBI and Ford Motor Company and to historic, anti-Communist, vigilante groups which Black (2009) Donner (1990) and Majka (1981) wrote about.
References
- Abbate, J. (2000). Inventing the Internet. The MIT Press.
- Alic, J. A. (2014). The origin and nature of the US “Military-industrial complex. Vulcan, 2(1), 63–47. https://doi.org/10.1163/22134603-00201003
- Aly, G., & Roth, K. H. (2004). The Nazi census: Identification and control in the Third Reich. Intro. by E. Black. Temple University Press.
- Aspray, W., & Norberg, A. (1988, 28 October). An Interview with J.C.R. Licklider Conducted by William Aspray and Arthur Norberg. Charles Babbage Institute). https://conservancy.umn.edu/bitstream/handle/11299/107436/oh150jcl.pdf
- Aspray, W., & Norberg, A. (1989, February 28). An interview with Robert Taylor Conducted by William Aspray. Charles Babbage Institute). Carroll & Graf Publishers, Inc. Retrieved 14/09/21 from. https://hdl.handle.net/11299/107666
- Baker, R. (2009). Family of Secrets: The Bush dynasty, the powerful forces that put it in the White House and what Their influence means to America. Bloomsbury Press.
- Bevins, V. (2020). The Jakarta method: Washington’s anticommunist crusade and the mass murder program that shaped our world. Public Affairs.
- Ben-Menashe, A. (2015). Profits of war: Inside the secret U.S.-Israeli Arms network. TrineDay.
- Black, E. (2001a). IBM and the Holocaust. Crown Publishers.
- Black, E. (2001b). The Transfer Agreement: The untold story of the secret agreement between the Third Reich and Jewish Palestine Carroll & Graf Publishers, Inc. Original publication 1984.
- Black, E. (2009). Nazi Nexus: America’s corporate connections to Hitler’s Holocaust. Dialog Press.
- Blum, R. H. (Ed.). (1972). Surveillance and espionage in a free society: A report by the planning group on intelligence and security to the policy council of the democratic national committee. Praeger Publishers.
- Brinson, S. (2004). The Red Scare, politics, and the Federal Communications. PRAEGER. Commission, 1941-1960.
- Cantelon, P. (1993). The history of MCI: 1968-1988: The early Years. Heritage Press.
- Castells, M. (2001). The Internet galaxy: Reflections on the Internet, business, and society. Oxford University Press.
- Churchill, W., & Vander Wall, J. (1990). Agents of repression: The FBI’s secret wars against the black panther party and the American Indian movement. South End Press.
- Cook, C. L. (1997). The Advisor: The Phoenix program in Vietnam. Schiffer Publishing Ltd.
- Dinges, J. (2004). The Condor years: How Pinochet and his allies brought terrorism to three continents. The New Press.
- Donner, F. (1961). The Un Americans. Ballantine Books.
- Donner, F. (1971). Spies on Campus in Concern the Playboy college reader (pp. 157–172). Harcourt Brace Jovanovich, Inc.
- Donner, F. (1974, June 1). Hoover’s Legacy. The Nation, 678–690.
- Donner, F. (1981). The age of surveillance: The aims and methods of America’s political intelligence system (with Introduction to the Vintage Edition). Vintage Books, Original publication 1980
- Donner, F. (1990). Protectors of privilege: Red squads and police repression in urban America. University of California Press.
- Edwards, P. N. (1996). The closed world: Computers and the politics of discourse in Cold War America. The MIT Press.
- Electronic Surveillance- Congress Grants Telecommunications Companies Retroactive Immunity from Civil Suits for Complying with NSA Terrorist Surveillance Program. FISA Amendments Act of 2008. Pub. L. No. 110-261, 122 Stat. 2436. Harvard Law Review, Feb. 2009, Vol. 122, No. 4 (Feb. 2009), pp. 1271-1278. https://www.jstor.org/stable/40379748
- Ernst, J. (1995). Forging a fateful alliance: The role of Michigan State University in the development of America’s Vietnam policy. Diss. University of Kentucky.
- Ernst, J. (1998). Forging a fateful alliance: The role of Michigan State University and the Vietnam War. Michigan State University Press.
- Feder, B. J. (9 January 1982). End of Action on I.B.M. Follows Erosion of its Dominant Position. The New York Times.
- Fischer, K.(2015). The influence of neoliberals in Chile before, during and after Pinochet. In P. Mirowski & D. Plehwe Eds., The road from Mont Pèlerin: The making of the neoliberal thought collective Harvard University Press. 305–346. Original publication 2009
- French, N. (1975, June 11). Army files on citizens still not destroyed. ComputerWorld, 9 (24). https://ia800802.us.archive.org/19/items/computerworld924unse/computerworld924unse.pdf
- Fricker, R. L. (1993, January). The INSLAW Octopus: Software piracy, conspiracy, cover-up, stonewalling, covert action: Just another decade at the Department of Justice. Wired, 1–36. Conde Nast. https://www.wired.com/1993/01/inslaw/
- Fricker, R. L. (2013). PRISM’s controversial forerunner. Consortium News, 25(319), 1–4 https://consortiumnews.com/2014/0915/prisms-controversial-forerunner-2/.
- Friedman, M. (2002). Capitalism and freedom, Fortieth anniversary edition. The University of Chicago Press.
- Friedman, M., & Friedman, R. (1998). Two lucky people. The University of Chicago Press.
- Greenwald, G. (2014). No place to hide: Edward Snowden, The NSA, and the U.S. surveillance state. Metropolitan Books.
- Hafner, K., & Lyons, M. (1996). Where Wizards stay up late: The origins of the Internet. Simon and Schuster.
- Halper, J. 2015. War against the people: Israel, the Palestinians and global pacification. Pluto Press. 2015 https://doi.org/10.2307/j.ctt183pct7
- Halperin, M. H., Berman, J. J., Borosage, R. L., & Marwick, C. M. (1976). The lawless state: The crimes of the U.S. intelligence agencies. Penguin Books.
- Herman, E. (1998). Project Camelot and the career of cold war psychology. In C. Simpson (Ed.), Universities and empire: Money and politics in the social sciences during the cold war (pp. 97–134). The New Press.
- Hitch, C. (1966). Decision-making for defense. University of California Press.
- Hitch, C. J., & McKean, R. N. (1965). The economics of defense in the nuclear age Athenaeum. Original publication 1960.
- Holsendolph, E. (January 9, 1982). Court hearing set: $80 Billion divestiture is required – rises in local rates seen. New York Times, A1, 34.
- Horton, S. (2015). Lords of Secrecy: The national security elite and America’s stealth warfare (pp. 54–55). Nation Books.
- Jacobsen, A. (2019). Surprise, kill vanish: The secret history of CIA paramilitary armies, operators, and assassins. Little, Brown and Company.
- Jensen, C. (ed.). (1997). 20 Years of censored news. Seven Stories Press.
- Johnson, L. K. (1990, May). Review of the book The liberals and J. Edgar Hoover: Rise and fall of domestic intelligence state, by W. W. Keller. The Journal of Politics, 52(2), 651–654. https://doi.org/10.2307/2131914
- Kahn, R. E. (1994, August). Viewpoint: The role of government in the evolution of the internet. Communications of the ACM, 37(8), 15–19. https://doi.org/10.1145/179606.179729
- Keller, W. W. (1989). The liberals and J. Edgar Hoover: Rise and fall of a domestic intelligence state. Princeton University Press.
- Kesan, J. P., & Shah, R. C. (2001). Fool us once shame on you—Fool us twice shame on us: What we can learn from the privatizations of the Internet backbone network and the domain name system. Washington University Law Review, 78(1). https://openscholarship.wustl.edu/law_lawreview/vol79/iss1/2
- Klare, M. (1972). War without end: American planning for the next Vietnams. Alfred A. Knopf.
- Klare, M., Arnson, C., Miller, D., & Volman, D. (1981). Supplying Repression: U.S. Support for Authoritarian Regimes Abroad. Original work published 1977. Forward by R. Falk. Institute for Policy Studies, Transnational Institute.
- Klare, M. T., & Kornbluh, P. (Eds.). (1988). Low Intensity Warfare: Counterinsurgency, Proinsurgency and Antiterrorism in the Eighties. Pantheon Book.
- Latham, A. (1976, February 16). The Pike papers: An introduction. The Village Voice. Latham. https://www.villagevoice.com/1976/02/16/the-cia-report-the-president-doesnt-want-you-to-read/
- Lessa, F. (2022). The Condor trials: Transnational repression and human rights in South America. Yale University Press.
- Leslie, S. W. (1993). The Cold War and American science: The military-industrial-academic complex at MIT and Stanford. Columbia University Press.
- Letelier, O. (1976, August 28). Economic ‘freedom’s’ awful toll: The ‘Chicago Boys’ in Chile. The Nation, 137–142.
- Levine, Y. (2018). Surveillance Valley: The secret military history of the Internet. Public Affairs.
- Linsalata, P. (1991, NovemberDecember). The Octopus file. Columbia Journalism Review. 30(4)
- Loewenstein, A. (2023). The Palestine laboratory: How Israel: Exports the technology of occupation around the world. Verso.
- MacKie-Mason, J. K., & Varian, H 1994 . “The economics of the Internet”, Dr. Dobbs Journal 6. 19(14).
- Majka, L. (1981) Organizational linkages, networks, and social change in Detroit [doctoral dissertation]. (Wayne State University, Detroit, MI)
- Marchetti, V., & Marks, J. D. (1980). The CIA and the cult of intelligence. Bantam Doubleday Dell Publishing Group, Inc. Originally published in 1974.
- McChesney, R. W. 1996, July/August. The global struggle for democratic communication. Monthly Review 48:3 1–20. ProQuest https://doi.org/10.14452/MR-048-03-1996-07_1
- McClintock, M. (1985). The American connection, Volume One. State terror and popular resistance in El Salvador. Zed Books.
- McClintock, M. (1992). Instruments of statecraft U.S. guerrilla warfare counter-insurgency, and counter terrorism, 1940-1990. U.S.: Pantheon Books.
- McConahay, M. (2018). The Tango war: The struggle for the hearts, minds and the riches of Latin America During World War II. St. Martin’s Press.
- McLean, P. 2004. Review of the history of commercial partnerships in the middle ages, by M. Weber & L. Kaelber. Contemporary Sociology 33: 253–254. Retrieved 13/02/22 from http://www.Jstor.org/stable/3593738 2
- MERIT Network, Inc. (1987). Cooperative agreement. In MERIT Network, Inc. records 1966-2002. Atlas Systems, Inc. Mixed Material, Box 28. Bentley Historical Library, University of Michigan.
- MERIT Network, Inc. (1990). Amendment 12: Subcontract to ANS and change to general terms and conditions. In MERIT Network, Inc. records 1966-2002. Atlas Systems, Inc. Mixed material, Box 29. Bentley Historical Library, University of Michigan.
- MERIT Network, Inc. (1991). Connectivity agreement. In MERIT Network, Inc. records 1966-2002. Atlas Systems, Inc. Mixed Material, Box 38. Bentley Historical Library, University of Michigan.
- Mills, C. W. (1960). Sept.–Oct.). letter to the new left. New Left Review, 5.
- Mills, K., & Mills, P. (Eds.). (2000). C. Wright Mills: Letters and Autobiographical Writings Eds. Mills, Kathryn, Mills, Pamela. Intro. by Wakefield, Dan. University of California Press.
- Mueller, M. L. (2002). Ruling the root: Internet governance and the taming of Cyberspace. The MIT Press.
- Naughton, J. (2001). A brief history of the future: The origins of the Internet. Naughton.
- Newman, N. (1998). Net Loss: Government, technology and the political economy of community in the age of the Internet. Diss. University of California.
- Newman, N. (2002). Net loss: Internet prophets, private profits and the costs to community. Pennsylvania State University press.
- Norberg, A. L., & O’Neill, J. E. (1996). Transforming computer technology information processing for the Pentagon, 1962–1986. John Hopkins University Press.
- Oakes, G., & Vidich, A. J. (1999). Collaboration, reputation and ethics in American academic life: Hans H. Gerth and C. Wright Mills. University of Illinois Press.
- Packard, N. (2020a, March 23). Three kinds of demand pull for the ARPANET into the INTERNET. Cogent Social Science Media and Communication Studies, Cogent Social Sciences, 6(1). https://doi.org/10.1080/23311886.2020.1720565
- Packard, N. (2020b, April 24). The ARPANET into the Internet: A tale of two networks. Studies in Media and Communication, Retrieved from. 8(1), 37. https://doi.org/10.11114/smc.v8i1.4783
- Packard, N. (2020cJune25). Overlooked history in the Age of Surveillance Capitalism [Book Review of: The Age of Surveillance Capitalism: The Fight for a Human Future at the New Frontier of Power by S. Zuboff]. The Journal of Media Economics. 31(1–2), 68–74. Retrieved 9/2/22 from.
- Packard, N. (2023). Exploiting and neutralising the ‘Communist Threat’ for the Privatised Internet. [ Doctoral dissertation, University of Auckland]. ResearchSpace https://hdl.handle.net/2292/64456
- Packard, V. (1964). The naked society. Longmans.
- Pyle, C. H. (1970, January). CONUS Intelligence: The Army watches civilian politics. The Washington Monthly. 4–16.
- Pyle, C. H. (1974). Military surveillance of civilian politics, 1967-1970 ( Unpublished doctoral dissertation). Columbia University.
- Risen, J. 2006 State of War: the secret history of of the CIA and the Bush administration . (Free Press)
- Rohde, J. (2011). The last stand of the psychocultural cold warriors: Military contract research in Vietnam. Journal of the History of the Behavioral Sciences, 47(3), 232–250. https://doi.org/10.1002/jhbs.20509
- Rohde, J. (2013). Armed with expertise: The militarization of American social research during the cold war. Cornell University Press.
- Rorabaugh, W. J. (1989). Berkeley at war: The 1960s. Oxford University Press.
- Rosenfeld, S. (2013). Subversives: The FBI’s war on student radicals and Reagan’s rise to power. Farrar, Straus, and Giroux.
- Rowan, F. (1978). Techno spies. G.P. Putnam’s Sons.
- Salus, P. H. (1995). Casting the beyond Net: From ARPANET to INTERNET and beyond. Addison-Wesley Publishing Company.
- Shah, R. C., & Kesan, J. P. (2007). The privatization of the internet’s backbone network. Journal of Broadcasting and Electronic Media, 51(1), 93–109. https://doi.org/10.1080/08838150701308077
- Shils, E. A. (1956). The torment of secrecy: The background and consequences of American security policies. William Heinemann Ltd.
- Shorrock, T. (2008). Spies for hire: The secret world of intelligence outsourcing. Simon and Schuster.
- Simpson, C. (1988). Blowback: The first full account of America’s recruitment of Nazi’s and its disastrous effect on our domestic and foreign policy. Weidenfeld and Nicolson.
- Simpson, C. (1995). National security directives of the Reagan and Bush administrations the declassified history of U.S. political and military policy, 1981-1991. Westview Press.
- Snowden, E. (2019). Permanent record. Macmillan.
- Stein, J., & Klare, M. T. (1973, April 20). From the Ashes, Phoenix. Commonweal, 154–159.
- Stone, O., & Kuznick, P. (2013). The untold history of the United States. EBURY Press.
- Thomas, K., & Keith, J. (1996). The Octopus: Secret government and the death of Danny Casolaro. Feral House.
- Valentine, D. (2000). The Phoenix program. Open Road Media, Original work published 1990
- Vine, D. (2015). Base Nation: How U.S. Military Bases Abroad Harm America and the World. Metropolitan Books.
- Vine, D. (2020). The United States of war: A global history of America’s endless conflicts, from Columbus to the Islamic State. University of California Press.
- Waldrop, M. M. (2018). The Dream Machine: J.C.R. Licklider and the Revolution That Made Computing Personal. Viking Penguin.
- Wallerstein, I. (1997). The Unintended Consequences of Cold War Area Studies. In The Cold War & the university: Toward an intellectual history of the postwar years.W.W. Norton & Co.
- Weber, M. (1949). Objectivity” in Social Science and Social Policy. In E. A. Shils & H. A. Finch (Eds.), The methodology of the social sciences (pp. 50–113). The Free Press.
- Weber, M. (1958). From Max Weber: Essays in sociology (H. Gerth & C. W. Mills, Eds.). Oxford University Press. Original publication 1946.
- Weber, M. (1958). Class, Status, Party. In H. Gerth & C. W. Mills (Eds.), From Max Weber: Essays in Sociology (pp. 180–196). Oxford University Press.
- Weber, M. (1978). Economy and society. G. Roth & C. Wittich. Eds., (E. Fischoff, H. Gerth, A. M. Henderson, F. Kolegar, C. Wright Mills, T. Parsons, M. Rheinstein, G. Roth, E. Shils, and C. Wittich, Trans.). University of California Press. (Original work published 1968.
- Weber, M. (1994). Weber: Political writings (P. Lassman & R. Speirs, Ed.). Cambridge University Press.
- Weber, M., (2003). In: The History of Commercial Partnerships in the Middle Ages, L. Kaelber. Rowman and Littlefield Publishers, Inc.
- Zuboff, S. (2019). The Age of Surveillance Capitalism: The Fight for a Human Future at the New Frontier of Power. Profile Books.
- Zwerling, P. (Ed.). (2011). The CIA on Campus: Essays on Academic Freedom and the National Security State. McFarland & Company, Inc.
- Public Documents
- United States. Congress. Senate. (1961). Department of Defense appropriations for fiscal year 1962: Hearings before the subcommittee. Eighty-seventh Congress, first session. United States. Washington: U.S. GPO. Retrieved 24 February 2020 from https://hdl.handle.net/2027/uc1.b3795656
- United States. Congress. Senate. (1962) Department of Defense appropriations for 1963: Hearings before the subcommittee of the Committee on Appropriations, United States Senate, Eighty-seventh Congress, second session on H.R. 11289, making appropriations for the Department of Defense for the fiscal year ending June 30, 1963, and for other purposes United States. Washington, D.C.: U.S. GPO. Retrieved 05 November 2020 from https://hdl.handle.net/2027/uc1.a0000415497
- United States. Congress. Senate. (1965). Committee on the Judiciary. Subcommittee to Investigate the Administration of the Internal Security Act and Other Internal Security Laws. The anti-Vietnam agitation and the teach-in-movement: the problem of Communist infiltration and exploitation; a staff study. Washington: U.S. GPO. Retrieved 06 June 2020 from https://hdl.handle.net/2027/hvd.32044053349361
- United States. Congress. House. Committee on Foreign Affairs. (1969). Measuring hamlet security in Vietnam. Report of a special study mission … of the Committee on Foreign Affairs, Tunney, J. V. United States. Congress. House. Committee on Foreign Affairs. (1969). Measuring hamlet security in Vietnam. Report of a special study mission … of the Committee on Foreign Affairs, House of Representatives. Pursuant to the provisions of H. Res. 179, 90th Congress: A resolution authorizing the Committee on Foreign Affairs to conduct through studies and investigations of all matters coming within the jurisdiction of such Committee. Washington: U.S. GPO. https://hdl.handle.net/2027/uiug.30112068389920 ( accessed on 02 August 2021)
- United States. Congress. Senate. Committee on Appropriations. (1970). Department of Defense appropriations for fiscal year 1971: hearings before the Subcommittee of the Committee on Appropriations for fiscal year 1071: hearings before the Subcommitte of the Committe on Appropriations, United States Senate, Ninety-first Congress, second session, on H.R. [19590, making appropriations for Department of Defense for the fiscal year ending June 30, 1971, and for other purposes . Part 1. ‘Nonrecovery of R. & D. Costs by Government’ (pp. 736-7). U.S. GPO. https://hdl.handle.net/2027/umn.31951p01213044g
- United States. Congress. Senate. (1972). Department of Defense. Appropriations for Fiscal Year 1973. Part I. Hearings before a Subcommittee of the Committee on Appropriations. United States Senate. 92nd Congress, Second Session. (February 25.28, March 14, 16, 22-24, 1972); Department of Defense, Advanced Research Projects Agency, Statement of Dr. Stephen J. Lukasik, Director, p.p. 725-830, Washington, DC: U.S. GPO. Retrieved 28 February 2020 from https://babel.hathitrust.org/cgi/pt?id=uc1.31210017813393andview=1upandseq=729
- United States. Congress. Senate. Committee on Armed Services. (1973a). Nomination of William E. Colby: Hearing, Ninety-Third Congress, first session, on nomination of William E. Colby to be Director of Central Intelligence, July 2, 20, and 25, 1973. Washington: U.S. GPO. Retrieved 06 July 2021 from https://hdl.handle.net/2027/mdp.39015074749253
- United States. Congress. Senate. (1973b). Committee on the Judiciary. Subcommittee on Constitutional Rights. Military surveillance of civilian politics: A report. 93rd Congress, 1st session. Washington, D.C.: U.S. GPO. Retrieved 03 August 2020 from https://hdl.handle.net/2027/uc1.a0000636795
- United States. Senate. (1975) Surveillance technology joint hearings before the Subcommittee on Constitutional Rights of the Committee on the Judiciary and the Special Subcommittee on Science, Technology, and Commerce of the Committee on Commerce, United States Senate, Ninety-fourth Congress, first session … June 23, September 9 and 10, 1975. United States. Washington: U.S. GPO, 1975. Retrieved 09 October 2021 from https://hdl.handle.net/2027/mdp.39015078638619
- United States. Congress. Senate. (1975-76a). Intelligence agencies and activities: Domestic Intelligence Programs. Hearings of the Select Committee on Intelligence, U.S. House of Representatives, Ninety-fourth Congress. First Session. Part 3. “Electronic Surveillance—Relationship of Federal Agencies to Local and State Police.” October 9, 1975. Pp. 939-973. United States. Washington: U.S. GPO. 1975-Retrieved 08/03/21 from https://hdl.handle.net/2027/uiug.30112119391693
- United States. Congress. Senate. (1975-76b). Intelligence agencies and activities: Domestic Intelligence Programs. Hearings of the Select Committee on Intelligence, U.S. House of Representatives, Ninety-fourth Congress. Second Session. Part 6, NSA as an Independent Agency.” January, 27, 1976. Pp. 2078–2082 United States. Washington: U.S. GPO 1975- Retrieved 08 March 2021 from https://hdl.handle.net/2027/uiug.30112119391693
- United States. Senate. (1976a). Select Committee to Study Governmental Operations, with respect to Intelligence Activities. Final Report. 94th Congress, 2nd Session, Book I, Foreign and Military Intelligence.: U.S. GPO. https://babel.hathitrust.org/cgi/pt?id=mdp.39015070725273andview=1upandseq=3
- United States. Congress. Senate. (1976b). Select committee to study governmental operations with respect to intelligence activities. Final report. 94th Cong., 2nd sess. Book II, Intelligence activities and rights of Americans. US GPO.
- United States. Senate. (1976c). Supplementary Detailed Staff Reports on Foreign Military Intelligence. Final report. 94th Cong., 2nd sess. Book III, Supplementary detailed staff reports on the intelligence activities and rights of Americans. US GPO.
- United States. Defense Advanced Research Projects Agency (DARPA). (1978, January 4). ARPANET Completion Report. “ Report No. 4799 A History of the ARPANET the First Decade, April 1981” Information Processing Techniques Office, United States. Advanced Research Projects Agency (ARPA). https://walden-family.com/bbn/arpanet-completion-report.pd
- United States, Congress. House. Committe on the Judiciary., Subcommitte on Economic and Commercial Law., (1990) The Attorney General's refusal to provide congressional access to ”priviledged' INSLAW documents: Hearing before the Subcommittee on Economic and Commercial Law of the Committee on the Judiciary, House of representatives, One Hundred First Congress, second session, December 5, 1990. Washington: (GPO)Retrieved 25 8 23 https://do.handle.net/2027/pst.000017591348
- United States. Congress. House. Management of NSFNET. United States. Congress. House. Management of NSFNET. Hearing Before the Subcommittee on Science of the Committee on Science, Space, and Technology U.S. House of Representatives. One Hundred First Congress, Second Session. March 12, 1992. Washington: U.S. GPO. Retrieved August 15, 2021 from https://hdl.handle.net/2027/pst.000019985411
- United States. Congressional Record–House. (June 25, 1984) Reagan’s ‘Training Exercises’ A Cover for Militarizing Honduras. US GPO II6818-II 6820.
- Department of Defense Advanced Research Project Agency. (1959, December 30). Department of Defense Directive, No. 5129.33. The Army Library, Washington D.C.
- United States Operations Mission to Vietnam. (1959). Annual Report for Fiscal Year 1959, July 1, 1958, to June 30, 1959. MSU Vietnam Group Archive. Vietnamproject.archives.msu.edu
APPENDIX A
Weber’s Social Order
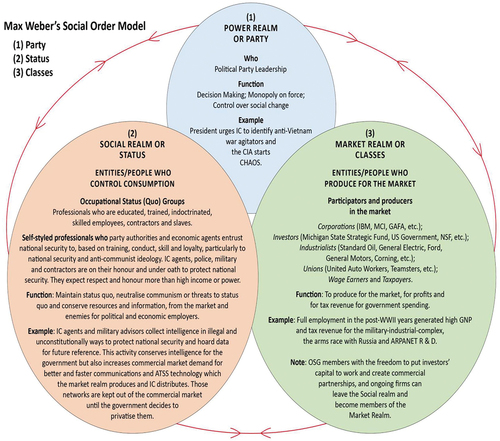
APPENDIX B
Chronologies
