?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
Victims of sex trafficking are often forced to participate in a variety of legal and illegal activities, including selling commercial sex, drug trafficking, committing theft, and committing fraud. We build an operational model of a sex trafficking network whose victims are forced to participate in multiple revenue-generating activities that are criminalized. This model was built based on the knowledge of experts who have lived experience or work closely with those with lived experience. This expertise helps to verify modeling assumptions and provides preliminary data to populate the model. We then extend the modeling approach to understand how disruptions to the sex trafficking network, such as those that disrupt different criminal activities, may affect the revenues of the trafficker. This extension not only helps to understand the importance of disrupting the commercial sex market, but it also helps to understand how a trafficker may react after such a disruption and how they may force victims to commit other criminal activity. For sex trafficking networks operating primarily in the nickel and dime commercial sex market and whose victims have substance use disorders, our analysis demonstrates that there could be a significant rise in theft to compensate for lost revenue due to disruptions of trafficking operations in the commercial sex market.
Sustainable Development Goals:
Introduction
People victimized for sexual exploitation (hereafter “sex trafficking”) may be required to participate in a variety of legal and illegal activities as part of their trafficking experience. While the primary activity of most victims is to sell sex, many are also forced to participate in other illegal activities such as receiving, transporting, or selling illegal drugs, committing theft or shoplifting, and committing fraud (Jacobs & Richard, Citation2016; Martin et al., Citation2018; Roe-Sepowitz, Citation2020). Forced criminality poses significant challenges to understanding how a sex trafficker may react to interdiction or disruption of any of these illegal activities. Further, little is known about whether (or how) this may shift activities victims are forced to participate in to generate revenue for the trafficker. This paper presents an operational model of a sex trafficking network whose victims also participate in multiple illegal revenue-generating activities and captures how disruptions affect the revenues of the trafficker.
The idea for this inquiry arose from our five-member survivor-centered advisory group that is part of our core research team. The members bring a combined expertise of more than 90 years of experience as survivor-leaders and/or working with survivors exiting trafficking networks. Members of the advisory group (AG) are coauthors on this paper and were involved in all stages of this research study from conceptualization to write-up. During many meetings, the group highlighted the important and often overlooked experiences of forced criminality as part of the sex trafficking experiences of victims. The model and parameters presented here are based on insights from this group and were cross-referenced with the minimal published literature that is available on forced criminality in sex trafficking, as well as literature on trafficker motivations.
This is a new area of focus in the literature, with many aspects unexplored. We want to be clear about exactly what types of trafficking situations the model does and does not cover. The model itself is a network optimization problem, which falls into the broad field of operations research (OR). We model the revenues generated by victims in a sex trafficking network, in which the trafficker controls the actions of each of the victims and seeks to maximize profits. We chose this focus based on the input and expertise of the survivor-centered advisory group; however, not all trafficking operations have such a clearly defined axis of control. We then consider how to best implement interventions to disrupt the profits of the trafficker operating such a network. This so-called network interdiction problem (Smith & Song, Citation2020) helps to explore interventions that go beyond arresting traffickers or removing victims from their trafficking environment and seeks to disrupt the profitably of such activities.
The OR modeling process involves abstracting the real world by making modeling choices and assumptions. Any OR model of sex trafficking must necessarily abstract traumatic experiences in a way that cannot possibly capture all the complexities of a victim’s or survivor’s lived experience. Abstraction requires making many assumptions that limit the types of trafficking situations that are captured by our OR model. We recognize the axiom attributed to George Box that “all models are wrong, some are useful” (see, for example, Box, Citation1979, p. 202) as being critical in our process. We augment the axiom with the insight that our particular model is useful only in certain contexts. Yet, a properly created OR model can yield important insights into sex trafficking that could aid disruption of the trafficking system.
Terminology is difficult in this problem domain and the literature uses many terms such as trafficker, pimp and facilitator to describe those who force or coerce others’ involvement in commercial sex (Barrick et al., Citation2023). We generally use the term trafficker, unless referring to a published source in which case we use their term.
Background
Operations Research Modeling of Sex Trafficking
The use of OR modeling and other data analytic approaches for examining sex trafficking networks is an emerging area and necessitates careful examination of potential unintended consequences resulting from such approaches (Caulkins et al., Citation2019). A systematic review by Dimas et al. (Citation2022) found that only 1.4% of OR and analytical papers on human trafficking from 2010 through 2021 used primary data to study sex trafficking and that “almost all studies on sex trafficking use data pulled from escort websites (or other online sites hosting illicit advertisements)” (p. 8). For example, data analytical approaches, such as machine learning and other clustering methods, have been applied to scraped web data on both commercial sex ads and massage businesses (e.g., Coxen et al., Citation2023; Dubrawski et al., Citation2015; Keskin et al., Citation2021; Tobey et al., Citation2022; White et al., Citation2021). This line of research does not typically present analysis on prices or revenues associated with the ads. Even if they did analyze prices, online advertisements for sex are marketing tools may not represent actual people, costs, or services.
Social network analysis has been applied to human trafficking networks, typically obtained through the coding of law enforcement data (e.g., Cockbain, Citation2018). Mayorga et al. (Citation2019) and Xie and Aros‐Vera (Citation2022) focused on network interdiction problems where victims are modeled as flow in a network that traffickers move to meet demand. Kosmas et al. (Citation2023, Citation2022) provide an approach that models control as flow within a network and, therefore, help to capture this important dynamic between traffickers and victims.
Some have used publicly available law enforcement case file analysis as data as well, including Xie and Aros‐Vera (Citation2022). It is often easier to access this type of secondary data, thus making it easier to construct OR models and analytics that can use it as input and for testing purposes. However, the limitations of such data also extend to the analysis conducted by the analytical methods. Yet, there is a significant opportunity for the OR and analytical field to build models and data based on primary data sources. We contribute to the literature by creating one such model and gathering data to populate it for one type of trafficking network.
Konrad et al. (Citation2023) suggest that the OR community will need to “grasp subtle yet distinctive nuances” (p. 320) associated with human trafficking in order to contribute to this area. They further argue that the OR community needs to be guided by domain expertise and should incorporate individual agency and survivor-informed approaches into modeling efforts. The latter is quite important since survivor-informed approaches will assure that OR models properly reflect the nuances of lived experiences and help to identify unrealistic assumptions.
Forced Criminality in Sex Trafficking
There is a small but revealing literature on noncommercial sex-based forced criminality among sex trafficking victims. The issue of forced criminality, outside of the commercial sex market, affecting victims of sex trafficking helps to provide a fuller context of their experiences while trafficked. The problem of forced criminality is documented in recent writings on vacatur and expungement that seek to ameliorate the collateral consequences of arrest and conviction for forced criminality outside of commercial sex (e.g., Barnard, Citation2014; Devaney, Citation2022; Martin et al., Citation2018; Mullins, Citation2019; Walton, Citation2020). However, these sources do not provide detailed information about the nature and prevalence of these experiences.
Use of illegal substances by sex trafficking victims is well-documented in the literature and often results in arrest on drug charges, but this is not the only crime done during a victim’s trafficking experience. Jacobs and Richard (Citation2016) led a survey within the National Survivor Network and reported that 40% of survey respondents were arrested on drug possession charges, 18.7% on drug sales charges, and 60% for noncommercial sex-related crimes. Mullins (Citation2019) found that some sex trafficking victims use illegal drugs or steal basic necessities as part of their trafficking situations. Roe-Sepowitz et al. (Citation2020) explored the concept of “trick rolls,” where sex trafficking victims rob sex buyers. They provide a characterization of 467 cases of trick rolls that occurred and were reported to police in Las Vegas, Nevada from October 1, 2017 – October 1, 2018. There were 14 different types of crimes committed across these cases ranging from theft to grand theft auto and robbery with a deadly weapon. Roe-Sepowitz (Citation2019) also reports findings from a survivor roundtable that involved eight child sex trafficking survivors. The roundtable identified forced criminal activities including “transporting drugs, selling drugs, trafficking other victims, stealing from sex buyers, picking pockets on the streets, and shoplifting” (p. 10). Rodríguez-López (Citation2020) provides an analysis of labor trafficking for criminal activities (outside of commercial sex), with many similarities to the criminal activities victims of sex trafficking are forced to commit (e.g., Roe-Sepowitz, Citation2019).
Given the dearth of published literature on forced labor outside of commercial sex, we provide information gathered from our survivor-centered advisory group based on their expertise. provides an overview of the types of activities that the advisory group knew victims to be forced to do. When asked who decides which type of non-sexual work or labor a victim does, members of the advisory group provided the following responses. “Generally, the trafficker tells them or it gets told to the bottom who tells them” and “it is mainly decided by the trafficker with the consideration of information gathered … [the trafficker] looks at potential activities that the victim may be good at.” By controlling the actions of victims, traffickers force them to participate in criminal activities and thus likely react to revenue-generating opportunities within specific markets including commercial sex and criminal activity markets. Given our focus on revenues and forced criminality, we do not consider the other forced labor activities in but recognize they also impact the experiences of victims. Further, it may be that a victim chooses to engage in another criminal activity in order to make money for the trafficker. As stated by a member of our advisory group:
Sometimes we would do non-sexual things without telling our perpetrator. As long as we made bank for that day, they usually didn’t care. But part of the power and control tactics involve us feeling like shit. That happens more often with the sex component.
Table 1. Summary of Forced Activities from the Expertise of Our Advisory Group.
Literature on Revenues in Sex Trafficking Networks
The revenues of sex traffickers and the economics of commercial sex is an important area related to understanding sex trafficking operations and our modeling approaches. Dank et al. (Citation2014) estimated the size of commercial sex markets and reported findings on the average weekly revenues of sex trafficking cases across eight major United States cities. The average weekly revenues found post-2005 in Atlanta and Denver was around $32,000, which is similar to data reported by Horning et al. (Citation2020) obtained through interviews with “pimps” in Harlem, New York. After removing an outlier above $100,000, Horning et al. (Citation2020) reported that the range of weekly revenues had an upper end of $31,500. Horning et al. (Citation2020) also found that pimps had an average of six victims at a time, which informs the number of victims included in our analysis.
Background and Motivation Summary
In summary, our research is motivated by the gap in the literature on OR modeling of sex trafficking networks with forced criminality. Forced criminality poses significant challenges to understanding how a sex trafficker may react to interdiction or disruption of any of these illegal activities, especially in the context of ensuring that appropriate revenues continue to be generated by the operation. Throughout the OR model-building process, the practical expertise of our AG helped to ensure that our operational models were grounded in the lived experiences of those that encountered forced criminality in sex trafficking.
Methods
The methods for this study involved a specific approach to modeling. The research team included three categories: OR experts, qualitative researchers/domain expertise, and the advisory group subject matter experts made up of people who interact closely with survivors and survivor-leaders. Closely following the principles of participatory action research, we view all team members as having equally important and valued knowledge and we worked to build trust and common purpose across all members of the project (Bradbury, Citation2015; Brush et al., Citation2020; Gerassi et al., Citation2017). We were also cognizant of power differentials and sought to explore and balance this (Wallerstein et al., Citation2019). For example, all members of the advisory group were paid the maximum federal allowable rate for consultants to show value for their time as experts. This team spent more than three years building trust and learning each other’s language(s) (Martin et al., Citation2022). We refer to the OR and qualitative researchers as the “academic team” and experts on the survivor-centered advisory group as the “advisory group.”
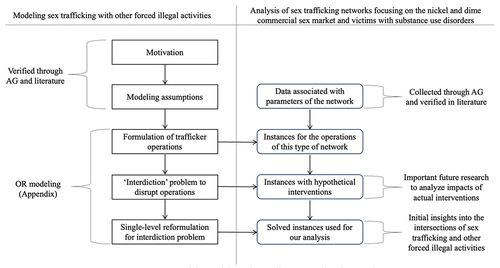
OR modeling typically involves seven steps. According to Sharkey et al. (Citation2021), the knowledge of domain and lived experience experts should ideally be integrated into five of these steps. , from Sharkey et al. (Citation2021), provides an overview.
Figure 1. Or modeling approach and areas where help is needed from trafficking experts. From Sharkey et al. (Citation2021).
Our specific approach in creating the OR model brought participatory research methods into each of the five “domain expert steps” of Sharkey et al. (Citation2021). Specifically, we developed a process, rooted in trust building and respect, which opened space for the advisory group to identify key issues (e.g., forced criminality) and share pertinent knowledge from which to build model parameters and assumptions (Martin et al., Citation2018). Below we describe the specific steps taken for each of the five steps displayed in .
Identifying Important Contexts (1)
During advisory group meetings with the academic team, we discussed the current state of knowledge on trafficking operations and what was missing. The AG emphasized that forced criminality is an important area of work, especially given how criminal records inhibit survivors in their day-to-day life and can prevent recovery. Therefore, we decided to build a model of trafficking networks that could help understand how victims are forced or controlled into different criminal activities, outside of commercial sex.
Domain Expertise on Modeling Choices and Assumptions (2)
The OR team brainstormed assumptions for this model based on transcriptions of advisory group meetings and the literature. Through an iterative process, these assumptions were vetted first by the qualitative research domain experts and then reviewed deeply by the experts on the advisory group. Many of the initial assumptions did not sufficiently capture the lived experience perspectives necessary for us to abstract them into a model. In other words, they were incorrect or incomplete. For example, the academic team had initially assumed that there would be a capacity on the number of hours worked by a victim. The advisory group said that this was partially true in their experience, but that if a trafficker needed something done, they had to do it, no matter how many hours the victim had previously worked in a day. This required a modification of our model where we introduced the concept of “required activities” outside of the initial capacity. Similarly, the initial model parameters aggregated the weekly activities of victims within the trafficking network. AG members said that the amount of variation in day-to-day activities was significant enough that the model should include this.
Realistic Data (3 & 4)
Running a computational model requires data. For this model, we needed data about the revenue-generating criminal activities that may be performed, the hourly revenue received for performing such activities, the number of hours per day a victim is forced to work, and the number of hours of demand within criminal activity markets. There is very limited literature with this type of information. Kosmas et al. (Citation2023) describes the types of data available on trafficking and the difficulties in obtaining realistic data.
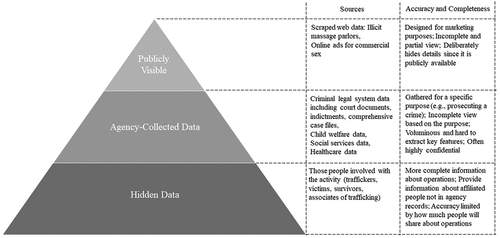
The most accessible data are publicly visible and agency-collected data. However, these sources do not contain accurate information about revenues and work in illegal activities. Our modeling approach and data represents the deepest level of the data pyramid of Kosmas et al. (Citation2023) (see ) because it focuses on the lived experiences of those involved in trafficking networks.
Figure 2. The human trafficking data pyramid. From Kosmas et al. (Citation2023).
To compensate for this data challenge, the academic team identified two sources of published data (Dank et al., Citation2014; Horning et al., Citation2020) and supplemented and extended this with insights from the AG. The AG provided input on the set of revenue-generating criminal activities and the hourly revenue ranges for different commercial sex markets based on their expertise. The kind of data needed for modeling is generally not the way people with lived expertise think about trafficking. Therefore, we needed to work together to figure out how to answer these questions. We gathered initial thoughts through online surveys of the AG, which were then refined through discussion. The surveys gave each AG member the opportunity to think and reflect on their own experiences; while discussions allowed for consensus building.
Initial surveys to understand the types of activities victims may be forced to perform include questions such as: (1) In our past meetings you have described the following examples of non-sexual work or labor that people are commonly expected, forced, or compelled to do as part of their trafficking situation? Please check all that you have seen or heard about (note: the list of examples came from past open discussions on the issue and included housework for the trafficker, taking care of kids for the trafficker or their family, stealing or theft, selling drugs, transporting drugs, driving people around, doing hair, nails or make-up, check fraud, and working in a legal job and giving pay to the trafficker); (2) What do you think is the MOST common kind of non-sexual work or labor that victims of sex trafficking are expected to do as part of their trafficking situation?; and (3) What did we miss in these questions about the non-sexual work or labor that sex trafficking victims are expected to do?. After scoping the model to focus on illegal revenue-generating activities, we asked survey questions such as: (1) How many days per week would a victim participate in [insert a particular activity’s name]?; (2) What was the range in terms of the number of hours per day a victim would participate in [insert a particular activity’s name]?; (3) What was the range in terms of money made per hour in [insert a particular activity’s name]?.
Interpretation (5)
The results of the analysis were discussed as a team and aligned with lived experience. The motivation for many traffickers is money and therefore disruptions that impact the most profitable parts of operations (such as commercial sex) would make trafficking less desirable. The amount of other illegal activities done by victims, based on the outputs of the models, also helps highlight the potential for victims to have a criminal record because of their time in the trafficking operation. This interpretation emphasizes the need to continue to advocate for vacatur and expungement.
Results
The Model
In this section, we provide an overview of the OR modeling efforts. The detailed mathematical formulation of these modeling efforts is described in the Appendix. We do, however, provide a guide to this formulation throughout our discussion below.
We propose to model a sex trafficking operation as a network. A network is a mathematical construct with a set of nodes, N, and a set of arcs, A, where a directed arc (i, j) exists from node i to node j if there is a relationship from i to j. For our modeling purposes, there are three distinct types of nodes: trafficker nodes, victim nodes, and market nodes. A directed arc exists from a trafficker node to a victim node if that trafficker can control that victim. A directed arc exists from a victim node to a market node if that victim can participate in an illegal activity within that market. provides an example network where we have 1 trafficker, 3 victims, and 6 illegal markets. The red arcs highlight a daily action of the trafficker and their interactions with a victim: they force the left victim to work for 12 hours, eight of them selling sex at a strip club, two hours selling sex on the street, and two hours working in drug trafficking. Our data is based on examining weekly operations of a trafficking network by examining the network on a day-to-day basis. The set of arcs from victims to markets may vary from day to day, along with other characteristics of the trafficker(s), victims, and criminal markets. The key sets and parameters associated with the model are presented in and the Appendix. These sets and parameters are important since we gather data to populate the model in later sections.
Figure 3. An example of control where the trafficker forces the victim to work different illegal activities.
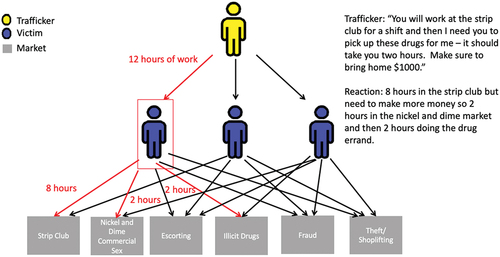
Table 2. An Overview of the Mathematical Notation Capturing the Inputted Data in an Instance of the Interdiction Model.
The actions of the trafficker are modeled as flow decisions on the arcs for each day. In particular, the flow decision on an arc from a trafficker to a victim on a particular day is how many hours that victim is forced to participate in criminal activities (in the Appendix, ). This is in line with the concept of modeling “flow as control” as introduced by Kosmas et al. (Citation2023). The flow decision on an arc from a victim to a market on a particular day is the number of hours that victim is forced to work in that criminal activity on that day (in the Appendix,
). Each hour a specific victim works in a particular criminal activity generates an hourly revenue for that activity. Each victim has a limited number of uptime hours, with uptime defined as participating in revenue-generating activities. We assume that the trafficker is interested in maximizing their profits, which is the objective function (Equation (1a) in the Formulation of the Trafficker Operations in the Appendix). These daily flow decisions are governed by a series of constraints that restrict the set of feasible decisions.
The daily constraints are as followsFootnote1 (1) There is a limit to the number of uptime hours of a victim, meaning that there is a limit to the number of hours the trafficker can force a victim to participate in illegal activities (Constraint (1b)). (2) There is an overall limit to the number of hours all victims can work in a particular criminal market (Constraint (1c)). (3) The number of hours the trafficker forces the victim to work in criminal markets must equal the number of hours the victim actually works (Constraint (1d)). (4) There is a limit to the number of hours a particular victim can participate in a particular illegal activity/market (Constraint (1e)). Finally, (5) there may be certain criminal activities that a victim must do on a particular day outside of their uptime limit (Constraint (1f)). Note that (4) helps to capture the amount of demand within a market, which will help us analyze interventions that can help disrupt a trafficking network by decreasing demand within these different criminal markets.
The model assumes that a trafficker makes decisions to maximize their overall revenue from the forced criminal activity over the course of a week (which can be easily extended to different time units), which is the objective function of the formulation (Equation (1a) in the Appendix). In addition to modeling the trafficking operations, we extend the model to understand where interventions can best disrupt the activities of the network. The goal of the interventions is to decrease the revenue the trafficker(s) receive from their operations as much as possible. In other words, the entity (or entities) intervening in trafficking seeks to minimize the maximum revenue of the trafficker. This type of network model is called an interdiction model, which is formally presented in the Appendix in the “an interdiction problem to disrupt the trafficking operations” section. In applying the model, we use the term “intervention,” as opposed to “interdiction,” to signify that we are thinking broadly about actions that can disrupt sex trafficking, especially those actions outside of law enforcement interdictions. We model two types of interventions: (i) the ability to remove victims from the trafficking network and (ii) a “market-level” disruption that decreases the daily capacity of one or more markets. The intervener has limited resources and, therefore, can only implement a limited number of these modeled interventions.
Model Assumptions
We have made many assumptions during this abstraction that limit the types of trafficking situations that are captured during our model. The assumptions that we have made on topics such as control are not true in all trafficking experiences and we recognize these limitations. Below, we present a summary of our key assumptions, along with a discussion of each.
Assumption: The trafficker fully controls the activities of each victim in that they tell the victim exactly how many hours to work in each criminal market. Discussion: This is not representative of all trafficking situations; for example, victims may be given the autonomy to choose which activities to enter as long as they bring a certain quota back to the trafficker. Therefore, our model is more applicable to situations where the trafficker very specifically tells each victim their expectations of what the victim will do on a particular day. However, in practice this may not be a meaningful distinction as our AG notes that typically in a trafficking situation a victim has autonomy only after they have internalized the trafficker’s goals and can be “trusted” by the trafficker to carryout appropriate activities, such as increasing revenues. These decisions by traffickers represent a balance of efforts across multiple victims. The limited evidence we have suggests that traffickers would generally like to maximize profits but the process to do so may vary. Our AG suggests that traffickers would like to minimize their own efforts and therefore building this trust could help accomplish this goal. Horning et al. (Citation2020) stated “There is much variation in terms of controlling behaviors, but they are not significantly related to economic rewards,” (p. 182) implying that this assumption may still provide insights to other models of controlling behavior.
Assumption: The trafficker makes decisions in order to maximize their profits and the intervener is focused on disrupting the profits of the trafficker. Discussion: Traffickers are often motivated by money and, therefore, this assumption captures these types of traffickers. The idea behind having an intervener focus on the revenues made by traffickers is that it will, ideally, shift the “steady state revenue” of trafficking down and make trafficking a less desirable choice for the trafficker.
Assumption: Our model does not include situations in which a victim is forced to engage in trafficking another person as a criminal activity. Discussion: We do not model situations where a trafficker forces a victim into criminal activity and then the victim traffics another victim. In terms of dynamics, these types of situations are especially complex and it is currently unclear how to capture this complexity within a mathematical model focusing on day-to-day or weekly operations.
Assumption: Our model includes only direct revenue-generating forced criminal activities. Discussion: The uptime capacity of the victim is focused on the number of hours they may spend generating revenue for the trafficker. This capacity could be based on subtracting the number of hours they are forced to do non-revenue generating activities from their overall uptime. Therefore, despite the model not including these types of activities, it can indeed factor these activities into the data inputted into the model.
Assumption: Our model does not consider the potential response of a trafficker to relocate to other, geographically distinct commercial sex markets. Discussion: Although geographic displacement of criminal activities in response to disruptions is well-documented in the literature, little is known about displacement in the context of our considered model. Given that the trafficker is interested in their profits and that victims are known to be forced into other revenue-generating criminal activities, a natural response of the trafficker will be to continue operating within the geographic area of the impact of the interventions by varying the criminal activities they force victims to participate in. Alternatively, this assumption also captures situations where the types of market-level interventions that we consider impact the criminal activities across the range of potential geographic relocations of the trafficker. Although this assumption is limiting, this model is an initial step in understanding the range of reactions that may be implemented by the trafficker.
Overall, the proposed model and our analysis focus mainly on situations where each of these assumptions can be applied without losing the key features of a particular trafficking experience. To apply the proposed model and conduct analysis, we need realistic data to populate it. As noted above, very little published data is available to populate this kind of modeling.
Data, Revenues and Resulting Instances
We first determined the set of markets that should be included in the model. Based on the original survey of the AG (see ), we included markets associated with drug trafficking, theft, and fraud. In addition, we decided to split the commercial sex market into three distinct markets: the nickel and dime market of commercial sex, selling sex in strip clubs, and escorting. These market types represent the wide range of activities and incomes across the commercial sex market. We have chosen to use the term “nickel and dime market” of commercial sex to represent the segment of the market that traditionally occurred on the streets but whose operational characteristics may be changing with the prevalence of online advertisements and cell phones. This is similar to the types of markets the pimps in Horning et al. (Citation2020) operated in. Further, we purposefully avoid terms like “low end” that could be interpreted as characterizing the victims in this market. The term “nickel and dime market” came from the AG and was chosen as it represents how commercial sex buyers attempt to control market prices through aggressive negotiations.
Opportunities to cross-validate the results of the AG survey with the literature were extremely limited, especially in the markets of selling sex in strip clubs and escorting. Therefore, our analysis focuses mainly on sex trafficking networks operating in the nickel and dime market. Still, we report our findings across the three markets as it provides insight into future research. As additional data are collected related to our efforts, the model can be refined and/or data can be created to analyze other types of sex trafficking networks.
The next step involved estimating the range of hourly revenues for an activity within each of the six illegal markets, a range for the number of hours a victim may work in a market in a day, and how often a victim will work in a market. Inputs for these ranges were originally provided by our AG and resulted in initial data for two specific types of sex trafficking networks: (1) a network composed of victims with substance use disorders working in the nickel and dime commercial sex market, and (2) a network composed of victims that can escort, sell sex in strip clubs, and work in the nickel and dime commercial sex market. We found literature related to the first network and integrated that knowledge with reports from our AG to produce reasonable data to analyze for these specific networks. However, literature on operations focuses on the second network (i.e., escorting and selling sex in strip clubs) is extremely limited and did not support our data collection efforts to a point where analysis could be done.
Data also came from the AG survey. The survey allowed AG members to share their significant experience with survivor support and advocacy as well as their extensive network of contacts across the United States who have experienced trafficking. Thus, although the sample size of the AG survey is N = 5, each member estimated being familiar with the stories and experiences of hundreds of trafficking victims. Therefore, their responses include their knowledge of a much broader range of experiences than the small sample size would suggest. provides survey results for networks with the first focus (i.e., the nickel and dime commercial sex market only). provides survey results for networks that operate across all three commercial sex markets.
Table 3. Initial Inputs for Networks with a Nickel and Dime Market Focus and Victims with Substance Abuse Disorders.
Table 4. Initial Inputs for Networks Where Victims Participate in Diverse Commercial Sex Markets.
In order to integrate the data gathered for networks with a nickel and dime focus with knowledge from the literature, we created procedures that would produce an expected weekly revenue of approximately $32,000 for the trafficker from commercial sex. The $32,000 estimate is similar to the average of the nine post-2005 cases in Atlanta and the average of the five post-2005 cases in Denver analyzed in Table 3.3 of Dank et al. (Citation2014) and the upper end responses reported by Horning et al. (Citation2020), after removing the highest outlier. We assume that the $32,000 includes activities within the commercial sex markets and activities outside of selling sex may increase the revenue for the trafficker.
After gathering these inputs, we needed a procedure to determine the hourly revenue of a day and the capacity on the number of hours for a victim and market combination. In order to determine the hourly revenue on day d of victim j in market m, we assigned probabilities that an hour would fall into the low, typical, and high revenue ranges. We then generated eight samples of hourly revenue based on these probabilities and set the hourly revenue equal to the average of these samples. These probabilities were determined to ensure that the expected weekly revenue, if victims could work all hours within all commercial sex markets, would be roughly $32,000, the estimate from Dank et al. (Citation2014) and the upper end responses of Horning et al. (Citation2020). We set the probabilities for the nickel and dime (ND) market in such a way that:
In our analysis, we focused on networks with the number of victims equal to five or six and a single trafficker. The number of victims equal to six is the average number of victims reported by Horning et al. (Citation2020). We analyze the results of applying our interdiction model to five instances of each number of victims to understand trends that may exist.
To determine the hourly revenues from drug trafficking, we took a similar approach as we did for the commercial sex markets. In particular, once we determined the appropriate probabilities for the low, typical, and high ranges in commercial sex, we used these probabilities for the low, typical, and high ranges for drug trafficking and took three samples to generate the hourly revenue on a particular day for this market. For the fraud activity, the response indicated that it was not always available in the weekly activities but, when it was, it would have a high hourly revenue. Therefore, we generated whether the fraud activity appeared for a victim at a rate of 1/52, so that over the course of the year each victim would likely participate in it once, and then randomly selected which day it occurred during that week. If the fraud activity was present for a victim, it was assigned a day to be done with an uptime parameter of eight hours. We assumed theft would generate low hourly revenues (for our model, $25 per hour) but the results would be similar as long as the hourly revenues for theft were less than the hourly revenues of all other activities.
To this point, we have described the data regarding the daily uptime parameters (in hours) for each victim j and market m pair and the corresponding hourly revenue of having victim j work in market m. Next, we describe the overall uptime parameters for a specific victim on a specific day. We assumed that these parameters were uniformly distributed over the integers from eight through 16. This assumption means that a victim often has enough uptime to complete all the hours in the commercial sex market and participate in several hours in another criminal activity. We also randomly determined if there would be a required activity in the commercial sex market for a victim on a day. In cases where the hourly revenue of the commercial sex market of a victim is larger than the hourly revenue of any other criminal activity (which is often the case), we could relax the “required” from this activity and the victim would still participate in it since it generates the most revenue.
The overall capacities of the markets were based on ensuring that the priorities of the trafficker could typically be met without any interventions into the network. For example, the capacity of the commercial sex market was chosen to be 30, where the sum of the expected uptime parameters for this market across all victims was either 24 (six victims) or 20 (five victims). This implies that there is enough demand in the market that the victims would often spend an amount of time equal to the uptime in commercial sex (since it is most profitable among the activities that are available on a day-to-day basis) which would make sense since the trafficker’s primary operation is commercial sex. We assumed that the theft market was readily available (i.e., high capacity) and that the drug market was at or slightly above the sum of the expected uptime parameters across all victims.
Analysis Using the Model
The focus of our analysis is to understand how market-level interventions could impact the operations of a sex trafficking network. A market-level intervention is one that disrupts the capacity of the markets (in terms of hours), implying that the trafficker may need to adapt their operations in response. For example, if enough of the commercial sex market is disrupted, then a trafficker may have available time for a victim to participate in other forced criminality. We focused on this since interventions that focus on removing victims often result in the trafficker recruiting new victims (e.g., Kosmas et al., Citation2023) and thus, have very little impact on their long-term revenues (Martin & Lotspeich, Citation2014). Our belief is that disrupting trafficking networks will require a multi-phase approach that includes removing victims from their trafficking experiences and impacting the motivation of traffickers to continue their operations. Therefore, our analysis is not advocating to leave current victims in trafficking experiences but provides a perspective of how to decrease the revenues generated for traffickers through their network operations. A decrease in revenues will ideally increase the opportunity costs to recruit new victims when one is removed from the trafficking networks and may, in the long-term, change the decision-making of the trafficker. Further, the focus on market-level interventions allows us to brainstorm how to design interventions with certain desired impacts as opposed to measuring the impact of existing interventions. In other words, our results could suggest where to focus efforts to design interventions to have effective impacts on sex trafficking networks.
The proposed impacts of different interventions and a practical example that could achieve them are provided in . Note that we considered that certain interventions may impact multiple markets, thus altering the number of available hours to the trafficking operation at multiple market-level nodes. We further assume that the impacts of these interventions are independent of one another and, therefore, their impacts sum together as more interventions are implemented. This assumption may be limiting in practice. However, our model could be adapted to situations where there are correlations between the impacts of different interventions (either enhancing the overall impact or decreasing it) through advanced integer programming modeling techniques. We also assume that the intervention needs to be fully implemented, which is a common assumption in network interdiction problems.
Table 5. Impacts, in Terms of Fractions, of Interventions on the Available Hours in Each Illegal Market.
We consider the impacts of these interventions on five instances of trafficking networks with six victims and five instances with five victims. We examine budget levels that allow for the implementation of one through six interventions to understand the priorities in terms of interventions and compare their relative impact. The instances were solved by implementing the single-level linear optimization formulation of the interdiction problem, discussed in the Appendix. All instances were solved using an academic license of Gurobi 9.5.2 on a MacBook Air with 8 GB of memory and 8 cores.
Before describing the analysis, we provide a summary of the data used to populate each instance. The reason for presenting the summary is that there is too much data to convey concisely for each instance. For example, for an instance of the six-victim network, there are 168 data points to describe the hourly revenue for each criminal activity for each victim and another 168 data points to describe the capacity of each victim to participate in the market. provides a summary of the data we were able to gather for trafficking networks composed of victims with substance use disorders and focusing on the nickel and dime commercial sex market; as well as its connection to the notation used in and the Appendix. This includes a summary of the justification for our data choices. An important note is that specific data were not available in relation to the interventions, which is a limitation of our analysis. We justify this choice since understanding the effectiveness of potential interventions into sex trafficking is in itself an important area of literature and gathering such data on numerous interventions is outside the scope of this study.
Table 6. Input Data into Our Instances and Its Justification.
Our analysis looks first at the behavior of the trafficker, such as the selected flow decisions and their revenues, i.e., the objective of the interdiction problem, as we increase the number of interventions that can be implemented. We find that decisions of traffickers tend to focus on forcing their victims to participate in the nickel and dime commercial sex market as much as possible, except for when there is a fraud activity available. We postulate that fraud becomes an attractive option in situations where the revenues from the fraud activity are higher than the expected revenues of the nickel and dime market, due to our assumptions about trafficker motivations focusing on maximizing profits and that their decision-making is rational according to this objective. We can view the parameter associated with the market capacity on a particular day, , as representing the current “market share” of the trafficker. This means that we assume that interventions that impact the nickel and dime commercial sex market will directly impact this market share, thus reducing the number of hours available for the trafficker to force their victims to participate in the nickel and dime market. In other words, interventions impact the “market nodes” (see, e.g., ).
provides an understanding of how the optimal interventions affect the trafficking operations of the first instance of the six-victim network. In particular, each entry in the table provides the total number of hours that victims are forced to participate in the nickel and dime market on a particular day and the second entry provides the current available hours in the market to the trafficking operation. When no interventions are implemented (budget level = 0), the bottleneck for the nickel and dime market is the total number of hours victims are available to work in the market, not . This represents the fact that the trafficker could expand (slightly) their operations. When one intervention is implemented, we select the nickel and dime focused intervention, which decreases the available number of hours by 20%. This results in there being 28.8 hours available to the trafficking operation in this market. We see that four of the days now have this upper bound as the bottleneck. When two interventions are implemented, the nickel and dime focused intervention and street-based criminal justice intervention are implemented, which decrease the available number of hours for the nickel and dime market by 35%, resulting in 23.4 hours of availability for the trafficking operation. At this point, six days have this as the bottleneck. For intervention budget levels of three and above, we see that the bottleneck in the trafficking operations is the available number of hours in the nickel and dime market, which we will soon see forces victims into other criminal activities. We do note that this trend associated with the flow decisions and how the trafficking network forces its victims into the nickel and dime market is similar for other instances.
Table 7. The Number of Hours Victims Were Forced to Work in the Nickel and Dime Market and the Number of Available Hours in the Nickel and Dime Market for Instance 1 of the Six Victim Network Analysis.
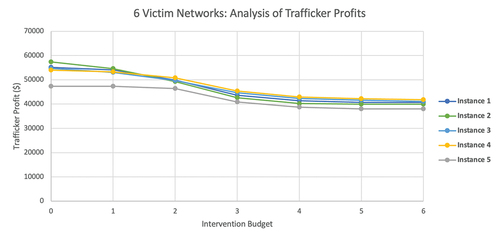
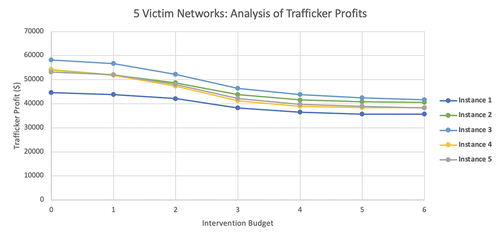
provide the impact on the trafficker revenues as the number of interventions increases for the six- and five-victim networks, respectively. In examining these results, we observe trends that are consistent for both six and five victim networks. The budget level of three interventions is when all interventions with significant impacts in the commercial sex market can be implemented (interventions I1-I3). For all instances considered, with a budget level of three, the optimal intervention decisions are to implement I1-I3. It is clear from these graphs that the impact is much more important than the interventions from the last three interventions. However, it is not always the case that we prioritize these interventions before others: it is their overall impact that is critical. provides an overview of the typical optimal intervention strategies as the budget changes, which were selected for eight of the 10 instances. The typical optimal intervention strategies prioritize interventions that impact the nickel and dime market, where we will tie-break based on impacts to other markets (e.g., we first implement I3 over I2 since I3 has the same impact to the nickel and dime market as I2 but also impacts drug trafficking). While this helps understand typical optimal intervention strategies, there are exceptions. For example, in instance 4 of the six-victim network, with a budget level of 1, the optimal intervention is to implement I5, which focuses on fraud reduction. This is because the fraud activity has a much higher hourly revenue than the commercial sex market for the day when fraud was present in these instances. Therefore, an intervention into disrupting the commercial sex market does not bring down its capacity (or demand) enough to disrupt the revenues of trafficking. This output is interesting in the sense that it offers an alternative approach to potentially disrupting sex trafficking networks and identifying victims – those that are committing some sort of fraud (e.g., benefits fraud, check cashing schemes). However, this is not always the case when fraud is present in the operation. For example, in instance 3 of the six-victim network, we do not prioritize fraud reduction early (it is implemented at budget level 5). The reason for this is that impacting the nickel and dime market, in this case, is more impactful due to a combination of the available hours and hourly revenues in this instance.
Table 8. Optimal Intervention Strategies as the Budget Increases for All Five Victim Networks and Instances 1, 2, and 5 for Sic Victim Networks.
Further analysis of also suggest that the ability to implement all three interventions I1-I3 simultaneously is important in many instances; the decrease in the trafficker’s revenues from zero interventions to two interventions is actually smaller than the decrease resulting from moving from two interventions to three interventions. This helps to justify more resources being invested into disrupting the commercial sex market, such as reducing the demand for commercial sex, as smaller investments do not have as high of a return on investment. It is important to note that it is not morally or ethically appropriate to do nothing to intervene, even a small improvement helps victims of sex trafficking. However, our results suggest that the approaches used to justify an initial small investment should be re-applied to justify larger investments since the return on larger investments is more significant. In other words, investment of more resources at one time will likely result in a much bigger positive impact for victims.
We can also examine the changes in forced criminality after implementing interventions. We examined how the sex trafficking networks operate at an intervention budget level of three, meaning that there has been investment into disrupting the commercial sex market (essentially shrinking its size by 50%). show the percentage changes in the amount of time victims spend in the activities of commercial sex, theft, and drug trafficking.
Figure 6. Percentage changes in forced illegal activities at three interventions for six victim networks.
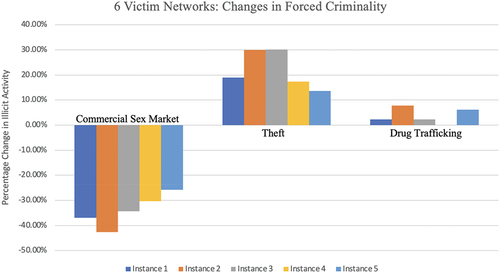
Figure 7. Percentage changes in forced illegal activities at three interventions for five victim networks.
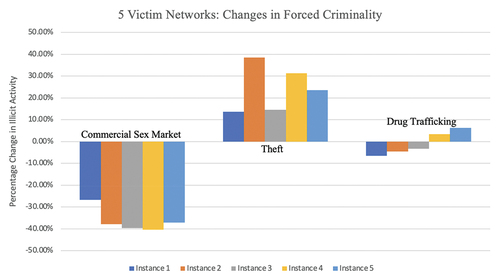
In this analysis, it is clear that victims are forced to commit theft at a much larger rate once the commercial sex market is disrupted. We see changes of between 10% and 40% across all instances in terms of the hours spent committing theft. This is an interesting result in that it could suggest ways to identify potential victims of sex trafficking after interventions are implemented in the commercial sex market: the reaction of the traffickers could be to force victims into theft. In terms of drug trafficking, we see a low rise in this activity for all of the six victim instances and do not see a discernible pattern for the five victim instances. Intervention I3 does impact the drug trafficking activity, implying that the capacity across all victims for certain instances of the five victim networks for this activity may be dropped to a point where the network needs to react and alter activities in both commercial sex and drug trafficking. However, for the six victim networks, where the capacity of drug trafficking was not impacted, we do see a rise in the activity (mainly because theft has a lower hourly revenue, so it would make sense for the trafficker to first force their victims into drug trafficking). This is another interesting result and might suggest that victims may be forced to participate in drug trafficking at a higher rate, after interventions to commercial sex.
Discussion
This paper describes an operational model of a sex trafficking network whose victims are forced to participate in a variety of different revenue-generating illegal activities. The motivation for such a model came from a survivor-centered advisory group who helped identify illegal activities of sex trafficking victims.
Our transdisciplinary research approach has combined OR modeling, participatory research, and lived experience to create a model, and data to populate it for a specific type of trafficking network, that aids in understanding how to intervene in trafficking networks that force victims to participate in multiple illegal activities. We elicited feedback on the assumptions of our model from the AG and identified data based on their collective expertise. The assumptions of the model were validated and verified through both their expertise and the existing literature on forced criminality. This project provides a salient example of how domain and lived experience expertise can be incorporated into computational modeling efforts and thus contributes to filling identified gaps in the literature (Dimas et al., Citation2022; Konrad et al., Citation2023). This is a novel approach to working around the severe data limitations in the human trafficking problem-space (Dimas et al., Citation2022; Russell, Citation2018; Zhang, Citation2009). The model presented here identifies important data needs for future work on disrupting trafficking. Specifically, modeling the revenue-based decision-making of traffickers requires a detailed understanding of both revenues and expenditures of sex trafficking operations. There is a paucity of this kind of data because the operations are illegal and the financials obfuscated and hidden by design (Farrell & Bright, Citation2016; Farrell & de Vries, Citation2019; Gerassi et al., Citation2017). Likewise, there is a limited literature on trafficker motivations (Barrick et al., Citation2023).
The model was extended to capture intervention situations aimed at disrupting the trafficking network and our analysis focused on disruptions that affect the size of the markets for the illegal activities. This paper contributes a new approach to thinking about decision-making in the absence of clear empirical data. Specifically, we find that forced criminality of sex trafficking victims outside of the commercial sex market offers the potential for successful disruption of trafficking. Further, disruptions in the commercial sex trafficking market may displace forced criminality into other activities, such as theft and drug trafficking.
In gathering data to populate our model, we triangulated survey responses from our advisory group with existing literature for trafficking situations whose focus was on the nickel and dime commercial sex market and victims with substance use disorders. Our model assumes a trafficking situation in which the trafficker exerts a great deal of control over victims. Our analysis and the results are therefore mainly focused on this type of trafficking. This model builds on research that seeks to understand the weekly revenues of sex traffickers, such as Dank et al. (Citation2014) and Horning et al. (Citation2020), by understanding how decision-making with respect to the activities of the victims influence these revenues. This modeling effort could offer a unique approach to understanding how interventions disrupt the profitability of sex trafficking operations, thereby decreasing one of the motivations for traffickers to operate in the space. We do note that our analysis focused on hypothetical interventions into criminal markets and more research is needed to understand the true impacts of such interventions. provides an overview of our overall approach, as summarized in this discussion. Our contributions have implications for both research and practice.
Implications for Research
This paper demonstrates how academic researchers from different backgrounds can integrate expertise from those with lived experiences to co-produce research questions and methods to address them. Within the space of analytics applied to sex trafficking, the model was built through domain expertise at several crucial phases of the OR modeling process (Sharkey et al., Citation2021). Within the sex trafficking domain, the research contributes to an emerging understanding of forced criminality of sex trafficking victims outside of commercial sex markets. It is clear that detailed research is needed on the inner-workings of the markets for commercial sex and other illegal activities. Future research in this area should focus on collecting data to better populate the model for other commercial sex markets, such as escorting or selling sex in strip clubs. This should focus on primary data collection, which is often a missing piece of applying OR models in this domain (Dimas et al., Citation2022). This type of data collection would allow for a better triangulation of data across multiple researchers, which would help to validate any results coming from the analysis produced by the model.
From a modeling perspective, capturing situations where the victims have quotas that they must meet but have more autonomy in how to meet them would be of interest. Further, understanding and modeling the tradeoff between maximizing revenues and minimizing risks from trafficking could yield better insights into disrupting operations. Within our model, we could view the upper bound on the number of hours victims are forced to work and the limit on the number of hours worked in a particular market as helping to model the exposure or risk of the trafficking operation. Therefore, sensitivity analysis could be conducted on these parameters to see how revenues increase or decrease as the trafficker becomes willing to increase or decrease their risk.
It is further clear that additional research is needed to better understand the details of potential market-level interventions and their effectiveness in impacting the market share of a particular trafficking network. This may be quite difficult and require collecting data on the trafficking network both pre- and post- implementation of a particular intervention.
Implications for Practice
Our analysis found that interventions that impact the commercial sex market, which could include demand reduction strategies, had the most impact on the revenues of the trafficker, which is unsurprising given the focus of the trafficking network. In other words, if more money could be made forcing victims to traffic drugs, traffickers would do so. Importantly, we found that theft committed by victims would likely significantly rise if interventions focused on commercial sex were implemented. This analysis could help understand alternative ways to potentially identify victims of sex trafficking after interventions are made in commercial sex markets. It also provides another approach demonstrating the importance of expungement and vacatur laws.
Sex trafficking survivors as well as legal scholars and others advocate for stronger vacatur and expungement statutes as a way to address the significant harms that accrue to trafficking victims from forced criminality and having a criminal record (Barnard, Citation2014; Jacobs & Richard, Citation2016; Roe-Sepowitz, Citation2019). To illustrate, in Minnesota, sex trafficking survivors and others have identified the need for stronger expungement laws and easier processes to help survivors recover (Martin et al., Citation2018). This and advocacy efforts for criminal justice reform resulted in Ramsey County and the Minnesota State Attorney developing procedures to help people seal their records (e.g. https://www.ag.state.mn.us/Office/Expungement.asp). Trafficking victims may also be forced to participate in the legal sex market (e.g., stripping and webcamming), effectively amounting to labor trafficking within these industries. More research is needed regarding how sex trafficking is interwoven into broader ecosystems and markets.
Findings here have implications for attainment of two sustainable development goals (SDG) 8.7 and 16.2. SDG 8 calls for “good jobs and economic growth,” with 8.7 calling for “effective measures to eradicate forced labor, end modern slavery and human trafficking.” SGD 16 called for “peace and justice,” with 16.2 calling to “end abuse, exploitation and trafficking in all forms of violence and torture against children.” Our model provides insights into the effectiveness and impact of measures to eradicate human trafficking, especially in efforts that focus on decreasing the profitability of exploitation networks. Our results suggest that vacatur and expungement for survivors is important due to the prevalence of forced criminality as a response to market interventions and will help to mitigate collateral consequences of victims’ trafficking experiences.
Limitations
This work has several limitations. The model itself focuses specifically on situations where a trafficker directly controls the activities of their victims. Our model, further, does not capture the issue of forced trafficking of others, i.e., when a victim is forced to traffic another victim. This is a complex trafficking experience and could be considered by later models that build upon this work. Further, our model does not account for forced labor within sex trafficking, which included activities such as childcare or household chores for the trafficker and their family. Our analysis is limited in that data were only able to be collected and triangulated on sex trafficking networks with a primary focus on the nickel and dime commercial sex market. Overall, there are limitations in the data and a need for detailed empirical data about these markets. Our design attempts to make reasonable estimates and assumptions based on very specific contexts.
In addition, there was some speculation in the implications of our analysis. Our focus on market-level interventions speculated that by decreasing trafficker revenues, in the longer-term may cause a trafficker to decrease the size of their operation and thus decrease victimization. We speculated on the impacts of the interventions modeled, with more research needed to measure the true impact and effectiveness of potential market-level interventions. Further, this is an initial step toward understanding the intersections between sex trafficking and other areas of forced criminality. Therefore, the broader effects of implementing the suggested impacts are not known and are beyond the scope of this study. It could be that these impacts would remove the primary source of income from some trafficking victims and could force them into more dangerous situations or criminal activities that carry higher penalties. Any future work should explore these potential unintended consequences and seek to address them.
Finally, the potential policy implications of this work are not yet apparent. It may be that the suggested interventions will decrease the activities within the commercial sex market but increase forced activities in other criminal markets and, therefore, could increase the number of people impacted by the criminal activities of the trafficking operation. We would argue that this would be beneficial to society overall since the other types of criminal activities may be significantly less severe than forcing victims into the commercial sex market. However, continued discussion is needed to weigh the potential impacts of sex trafficking as opposed to other criminal activities.
Conclusion
This paper helps to model and understand how interventions into various criminal markets can impact the revenues of a trafficker within a sex trafficking operation. The model was built through expertise across a variety of academic and non-academic backgrounds to account for the forced criminality of sex trafficking victims. Analysis was done with the model for trafficking networks that have a focus on the nickel and dime commercial sex market since data could be both collected through our AG and triangulated with academic sources. Our results suggest that a rise in theft activities would occur should significant interventions be made into the nickel and dime commercial sex market.
Appendix: Details of OR Modeling Approach
In the Appendix, we build out the details of our OR model and how we will go about solving it. We first introduce the Mathematical Notation that will be used throughout the Appendix. Our first modeling step is to build a mathematical representation of the trafficker operations, which focuses on the trafficker maximizing their profits subject to the practical constraints discussed in The Model section of the paper. We then introduce the mathematical model of our interdiction problem, which focuses on an intervener that will disrupt the trafficking network in order to minimize the maximum profits the trafficker can obtain. This formulation has a “min-max” structure since the intervener will seek to minimize the trafficker’s profits, while the trafficker will seek to maximize their profits. Therefore, we reformulate the interdiction problem as a single-level optimization problem by using the traditional duality-based technique for when the inner problem of an interdiction problem is a linear program. This reformulation allows us to implement it in a commercial software package and identify the optimal interventions, along with understanding the trafficker’s profits.
Acknowledgments
We would like to thank the anonymous reviewers for their feedback on the paper, which helped improve its presentation. This is especially true in terms of carefully discussing the limitations of our modeled interventions and presenting a summary of our overall approach ().
Disclosure Statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
Notes
1 Here, we provide the corresponding constraint which can be found in the Appendix, in the section on the Formulation of the Trafficker Operations.
References
- Barnard, A. M. (2014). The second chance they deserve: Vacating convictions of sex trafficking victims. Columbia Law Review, 114(6), 1463–1502.
- Barrick, K., Maass, K. L., Sharkey, T. C., Song, Y., & Martin, L. (2023). Expanding our understanding of traffickers and their operations: A review of the literature and path forward. Forthcoming in Trauma, Violence, & Abuse. https://doi.org/10.1177/15248380231210937
- Box, G. E. (1979). Robustness in the strategy of scientific model building. In R.L Launer & G.N. Wilkinson (Eds.), Robustness in statistics (pp. 201–236). Academic Press.
- Bradbury, H. (2015). Introduction: How to situate and define action research. In H. Bradbury (Ed.), The SAGE handbook of action research (Third Edition ed., pp. 1–12). SAGE.
- Brush, B. L., Mentz, G., Jensen, M., Jacobs, B., Saylor, K. M., Rowe, Z., Israel, B. A., & Lachance, L. (2020). Success in long-standing community-based participatory research (CBPR) partnerships: A scoping literature review. Health Education & Behavior, 47(4), 556–568. https://doi.org/10.1177/1090198119882989
- Caulkins, J. P., Kammer-Kerwick, M., Konrad, R., Maass, K. L., Martin, L., & Sharkey, T. C. (2019). A call to the engineering community to address human trafficking. The Bridge, 49(3), 67–73.
- Cockbain, E. (2018). Offender and victim networks in human trafficking. Routledge.
- Coxen, J., Castro, V., Carr, B., Bredin, G., & Guikema, S. (2023, February 19). COVID-19 pandemic’s impact on online sex advertising and sex trafficking Journal of Human Trafficking. https://doi.org/10.1080/23322705.2023.2215362
- Dank, M. L., Khan, B., Downey, P. M., Kotonias, C., Mayer, D., Owens, C., Pacific, L., & Yu, L. (2014). Estimating the size and structure of the underground commercial sex economy in eight major US cities. Urban Institute.
- Devaney, S. (2022). Justice for all? Impeding the villainization of human trafficking victims via the expansion of vacatur laws. Pepperdine Law Review, 49, 241–248. https://digitalcommons.pepperdine.edu/plr/vol49/iss1/5
- Dimas, G. L., Konrad, R. A., Maass, K. L., Trapp, A. C., & Kuo, Y.-H. (2022). Operations research and analytics to combat human trafficking: A systematic review of academic literature. PLoS One, 17(8), e0273708. https://doi.org/10.1371/journal.pone.0273708
- Dubrawski, A., Miller, K., Barnes, M., Boecking, B., & Kennedy, E. (2015). Leveraging publicly available data to discern patterns of human-trafficking activity. Journal of Human Trafficking, 1(1), 65–85. https://doi.org/10.1080/23322705.2015.1015342
- Farrell, A., & Bright, K. (2016). Human trafficking. In B. H. Huebner & T. S. Bynum(Eds.), The handbook of measurement issues in criminology and criminal justice (First ed.,) (pp. 111–130). John Wiley and Sons.
- Farrell, A., & de Vries, I. (2019). Measuring the nature and prevalence of human trafficking. In J. Winterdyk & J. Jones (Eds.), The Palgrave international handbook of human trafficking (pp. 147–162). Springer Nature.
- Gerassi, L., Edmond, T., & Nichols, A. (2017). Design strategies from sexual exploitation and sex work studies among women and girls: Methodological considerations in a hidden and vulnerable population. Action Research, 15(2), 161–176. https://doi.org/10.1177/1476750316630387
- Horning, A., Thomas, C., Marcus, A., & Sriken, J. (2020). Risky business: Harlem pimps’ work decisions and economic returns. Deviant Behavior, 41(2), 160–185. https://doi.org/10.1080/01639625.2018.1556863
- Jacobs, B., & Richard, S. (2016). National survivor network members survey: Impact of criminal arrest and detention on survivors of human trafficking. National Survivor Network.
- Keskin, B. B., Bott, G. J., & Freeman, N. K. (2021). Cracking sex trafficking: Data analysis, pattern recognition, and path prediction. Production and Operations Management, 30(4), 1110–1135. https://doi.org/10.1111/poms.13294
- Konrad, R., Maass, K. L., Dimas, G. L., & Trapp, A. C. (2023). Perspectives on how to conduct responsible anti-human trafficking research in operations and analytics. European Journal of Operational Research, 309(1), 319–329. https://doi.org/10.1016/j.ejor.2022.12.028
- Kosmas, D., Melander, C., Singerhouse, E., Sharkey, L., Barrick, K., Maass, K. L., & Martin, T. C. (2023). A transdisciplinary approach for generating synthetic but realistic domestic sex trafficking networks. Forthcoming in IISE Transactions, 1–15. https://doi.org/10.1080/24725854.2023.2169418
- Kosmas, D., Sharkey, T. C., Mitchell, J. E., Maass, K. L., & Martin, L. (2022). Multi-period max flow network interdiction with restructuring for disrupting domestic sex trafficking networks. Forthcoming in Annals of Operations Research. https://doi.org/10.1007/s10479-022-05087-3
- Martin, L., Gupta, M., Maass, K. L., Melander, C., Singerhouse, E., Barrick, K., Samad, T., Sharkey, T. C., Ayler, T., Forliti, T., Friedman, J., Nelson, C., & Sortillion, D. (2022). Learning each other’s language and building trust: Community-engaged transdisciplinary team building for research on human trafficking operations and disruption. International Journal of Qualitative Methods, 21, 16094069221101966. https://doi.org/10.1177/16094069221101966
- Martin, L., & Lotspeich, R. (2014). A benefit-cost framework for early intervention to prevent sex trading. Journal of Benefit-Cost Analysis, 5(1), 43–87. https://doi.org/10.1515/jbca-2013-0021
- Martin, L., Melander, C., Fritz Fogel, K., Saito, B., Garnett McKenzie, M., & Park, R. (2018). Safe harbor for all: Results from a statewide strategic planning process in Minnesota. https://uroc.umn.edu/research/safe-harbor-all-strategic-planning-process
- Mayorga, M., Tateosian, L., Velasquez, G., Amindarbari, R., & Caltagirone, S. (2019). Countering human trafficking using ISE/OR techniques. In H.B. Nembhard, E.A. Cudney, & K.M. Coperich (Eds.), Emerging frontiers in industrial and systems engineering (pp. 237–257). CRC Press.
- Mullins, K. (2019). A path to protection: Collateral crime vacatur for wisconsin’s victims of sex trafficking. SSRN Electronic Journal, 1551–1558. https://doi.org/10.2139/ssrn.3457956
- Rodríguez-López, S. (2020). Telling victims from criminals: Human trafficking for the purposes of criminal exploitation. In J. Winterdyk & J. Jones Q11 (Eds.), The Palgrave International Handbook of Human Trafficking (pp. 303–318). Springer Nature.
- Roe-Sepowitz, D. (2019). Child sex trafficking survivor roundtable. US Department of Justice, Office of Justice Programs AMBER Alert Training and Technical Assistance Program. https://socialwork.asu.edu/sites/default/files/2022-10/2019_aattap_cst_roundtable_final_report_0.pdf
- Roe-Sepowitz, D., Greene, E., Bruist, K., Dirks, S., Walters, J., Gallagher, J., Bracy, K., Hogan, K., Lul, B., Byun, J., & Duffield, V.(2020). Trick roll study: Forced criminality in sex trafficking situations.
- Russell, A. (2018). Human trafficking: A research synthesis on human-trafficking literature in academic journals from 2000–2014. Journal of Human Trafficking, 4(2), 114–136. https://doi.org/10.1080/23322705.2017.1292377
- Sharkey, T. C., Maass, K., Song, Y., Barrick, K. L., Farrell, A., & Martin, L. (2021). Better together: A transdisciplinary approach to disrupt human trafficking. ISE Magzine, 51(11), 34–39. https://doi.org/10.21428/cb6ab371.c4eb821a
- Smith, J. C. & Song, Y. (2020). A survey of network interdiction models and algorithms. European Journal of Operational Research, 283(3), 797–811.
- Tobey, M., Li, R., Özaltın, O. Y., Mayorga, M. E., & Caltagirone, S. (2022). Interpretable models for the automated detection of human trafficking in illicit massage businesses. IISE Transactions, 1–14. https://doi.org/10.1080/24725854.2022.2113187
- Wallerstein, N., Muhammad, M., Sanchez-Youngman, S., Rodriguez Espinosa, P., Avila, M., Baker, E. A., Barnett, S., Belone, L., Golub, M., Lucero, J., Mahdi, I., Noyes, E., Nguyen, T., Roubideaux, Y., Sigo, R., & Duran, B. (2019). Power dynamics in community-based participatory research: A multiple–case study analysis of partnering contexts, histories, and practices. Health Education & Behavior, 46(1_suppl), 19S–32S. https://doi.org/10.1177/1090198119852998
- Walton, S. E. (2020). Protecting sex trafficking victims through expungement and vacatur statutes: Will Virginia join the rest of the nation?. Journal of Global Justice and Public Policy, 6, 95. https://doi.org/10.2139/ssrn.3409345
- White, A., Guikema, S., & Carr, B. (2021). Why are you here? Modeling illicit massage business location characteristics with machine learning. Journal of Human Trafficking, 1–21. https://doi.org/10.1080/23322705.2021.1982238
- Xie, X., & Aros‐Vera, F. (2022). An interdependent network interdiction model for disrupting sex trafficking networks. Production and Operations Management, 31(6), 2695–2713. https://doi.org/10.1111/poms.13713
- Zhang, S. X. (2009). Beyond the Natasha story: A review and critique of current research on sex trafficking. Global Crime, 10(3), 178–195. https://doi.org/10.1080/17440570903079899
Mathematical Notation
We begin by discussing the sets, parameters, and decision variables that serve as the foundation of our modeling approaches.
Sets:
M Set of all markets, m
V Set of victims, j
A Set of intervention activities, i
T Set of traffickers, t
D Set of days, d
Rjd Set of required criminal activities of victim j for day d
Parameters:
Revenue generated in market m by victim j ($/hour) for day d
Capacity of trafficker t to control victim j (“up-time hours”) for day d
Market capacity (hours) for markets m for day d
Capacity of victim j to work in market m (hours) for day d
Resources required to remove victim j
Resources required to implement market-level intervention activity i
Percent of market m disrupted by intervention activity i
CArbitrarily large number
BOverall budget level for intervention activities
Interdiction Decision Variables:
Binary variable that represents whether or not intervention activity i is implemented
Binary variable if victim j is removed from the network
Initial Network Decision Variables:
Flow from trafficker t to victim j on day d
Flow from victim j to market m on day d
Dual Network Decision Variables:
Dual variable of victim j flow balance constraint on day d
Dual variable of market m capacity constraint on day d
Dual variable of the capacity constraint of flow from victim j to market m on day d
Dual variable of the required flow from victim j to market m on day d for
Dual variable of the capacity constraint of flow from trafficker t to victim j on day d
Linearization variable of the product of market level interdiction i and the dual variable associated with the capacity constraint of market m on day d
Linearization variable of the product of victim interdiction j and the dual variable associated with the flow capacity constraint between trafficker t and victim j on day d
Formulation of Traffickers Operations
We now present a formulation that models the trafficker’s profit-maximizing behavior, subject to constraints on the number of hours victims can work and the capacity of the markets.
Subject to:
Equation (1a) represents the objective of the initial model formulation. The objective maximizes the sum of the products of the revenue generated by victims working in different markets across the set of days. Constraints (1b) enforce that a trafficker cannot force a victim to work more hours than the upper bound control capacity limit for that day. Constraints (1c) ensures the total hours all the victims in a network work in a market does not exceed the market’s capacity for that day. For example, if a network has two victims that individually have the capacity to work market A for 10 hours on a day, but the market capacity is 15 hours on that day then one victim can work their full 10 hours in the market, but the other victim can only work 5 hours in that same market. Constraints (1d) reaffirms that the total number of hours a trafficker controls an individual victim on a day is equal to the total number of hours that individual victim will work the markets on that day. Constraints (1e) ensures that an individual victim does not work a particular market more than their capacity limits of that market on a day. Constraints (1 g) represents the non-negativity constraint for the variables.
It is important to note that our formulation and solution approach would be easily adapted to situations where there are lower bounds on the amount of time a victim needs to spend in a market (so constraint (1f) becomes a “”) to model the “required activities.” Further, it would not be difficult to extend the model, by adding an additional variable, to model a required activity in a market that generates a different revenue than standard activities within that market. These situations require a slight manipulation of the following reformulation.
An interdiction problem to disrupt the trafficking operations
We now consider an interdiction problem to disrupt the trafficking operations by removing victims from the network which then impacts the right-hand side of Constraints (1b) and implementing market-level disruption activities that reduce market capacity by impacting the right-hand side of Constraints (1c). We first define the set of feasible interdiction decisions as: . The initial interdiction formulation is:
Subject to:
Single-level linear optimization formulation of the interdiction problem
We now present the single-level linear optimization formulation of the interdiction problem. In particular, for a fixed set of interdiction decisions, the trafficker’s problem becomes a linear program. Therefore, we can take the dual of the linear programming formulation and then apply a standard linearization technique to the product of the dual variable and the interdiction variables. The single-level formulation is:
Subject to:
Equation (3a) represents the objective function of the dual of the inner problem (i.e., the problem faced by the trafficker once the interdiction decisions are fixed) where we have linearized the products of the interdiction decisions and the appropriate dual variables.
Constraints (3b) ensures that the sum of the budget’s used for removing victims from the network and executing intervention activities does not exceed the overall allotted budget for performing these actions. Constraints (3c) are the dual constraints associated with the flow variable, . Constraints (3d) are the dual constraints associated flow from a victim to a market,
, for markets that are not required to be worked by victim j on day d. Constraints (3e) are similar constraints for those markets that victim j must work on day d.
Constraints (3f)-(3 h) are the linearization constraints for the product of and
. Note that if
is equal to 0, the Constraints (3 g) force
to be zero as well. If
is equal to 1, Constraints (3f) and (3 h) imply that
is equal to
. Constraints (3i)-(3k) are the linearization constraints of
and
and have similar implications as the linearization constraints previously discussed when
is equal to 0 or to 1.
Constraints (3 m)-(3q) are the appropriate variable restrictions. This single-level reformulation will be how we solve the problem for various interdiction budget levels since we can solve it using commercial integer programming software. In our work, we implement the model in Python and solve it using Gurobi.